| File name: | PCToaster.bin.zip |
| Full analysis: | https://app.any.run/tasks/0ffa12dd-7f59-47c4-b2f8-c54eccc8d174 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 14:24:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 777B743BF77996D93708078516BCBFB0 |
| SHA1: | D4B84EF7349E01DD89DFF3B3C1EC611ADF159C66 |
| SHA256: | 598ADEE81BAA3D9A1E22F56037A64758E0BEF6C1D1AF7FEFDCA031DF8EA11C37 |
| SSDEEP: | 1536:0C5bWsBUBfMHMPJVlo8LSy0IwzIoAblEZB6rxw:0AUV0uO7BA5EZEW |
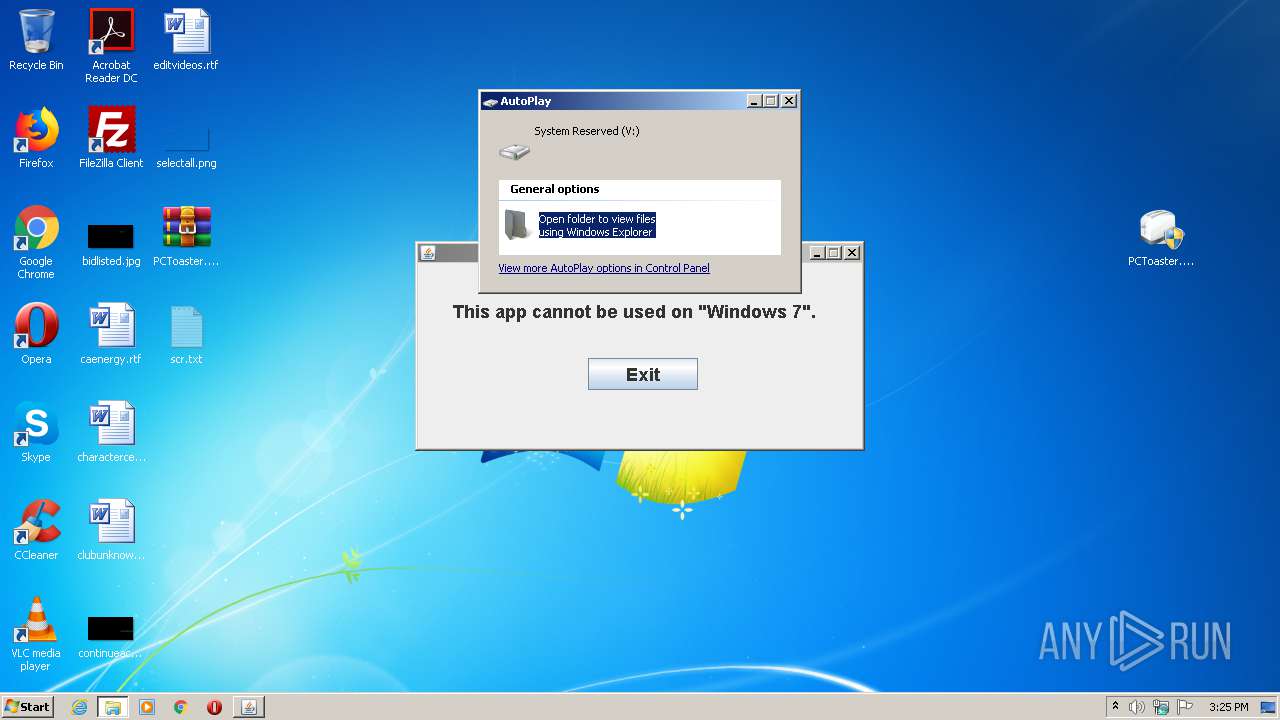
MALICIOUS
Application was dropped or rewritten from another process
- PCToaster.exe (PID: 2232)
- PCToaster.exe (PID: 3444)
SUSPICIOUS
Executes JAVA applets
- PCToaster.exe (PID: 2232)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 1860)
Executed via COM
- vdsldr.exe (PID: 2400)
Executed as Windows Service
- vds.exe (PID: 3160)
Low-level read access rights to disk partition
- vds.exe (PID: 3160)
INFO
Manual execution by user
- PCToaster.exe (PID: 3444)
- PCToaster.exe (PID: 2232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:15 12:24:12 |
| ZipCRC: | 0xbb833465 |
| ZipCompressedSize: | 62375 |
| ZipUncompressedSize: | 421699 |
| ZipFileName: | PCToaster.bin |
Total processes
54
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1352 | takeown /f V:\Recovery /r | C:\Windows\system32\takeown.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\PCToaster.exe" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | PCToaster.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2232 | "C:\Users\admin\Desktop\PCToaster.exe" | C:\Users\admin\Desktop\PCToaster.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2400 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2716 | takeown /f V:\Boot /r | C:\Windows\system32\takeown.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2888 | attrib +h C:\Users\admin\Desktop\scr.txt | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\PCToaster.bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3444 | "C:\Users\admin\Desktop\PCToaster.exe" | C:\Users\admin\Desktop\PCToaster.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3660 | diskpart /s C:\Users\admin\Desktop\scr.txt | C:\Windows\system32\diskpart.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DiskPart Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
355
Read events
333
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PCToaster.bin.zip | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3276.24338\PCToaster.bin | — | |
MD5:— | SHA256:— | |||
| 1860 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 1860 | javaw.exe | C:\Users\admin\Desktop\scr.txt | text | |
MD5:AD1869D6F0B2B809394605D3E73EEB74 | SHA256:7E9CDE40095F2A877375CB30FECD4F64CF328E3AB11BAED5242F73CBB94BD394 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report