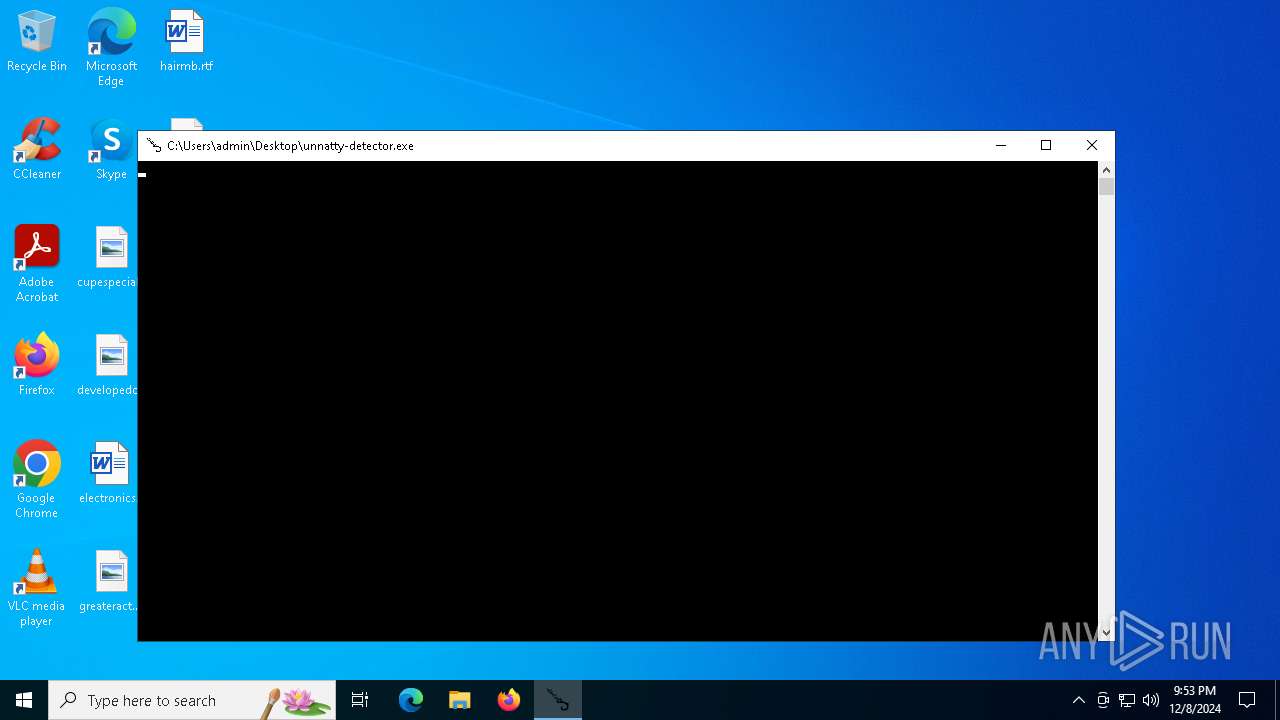
| File name: | unnatty-detector.exe |
| Full analysis: | https://app.any.run/tasks/6e8819cc-de5c-4bb3-82c5-21cd4b7a6d3e |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2024, 21:53:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 11 sections |
| MD5: | C457E96B88D39726226E1D352770C786 |
| SHA1: | 3FAF0A10636E5323B05C39D3F1735E3D669B54B2 |
| SHA256: | 5984962018AEA528C179B45F28519B0586379D1738A16B8887147E0C3F89DB99 |
| SSDEEP: | 98304:PO6J9mqXO76buTbZGMaYp7+3J1osffJCzS4fXpCyoXWMaYitGs6aN5EhNeRnGD8P:PnWGfs9ixhcYAKS2zWdADkfu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- unnatty-detector.exe (PID: 5712)
Process drops legitimate windows executable
- unnatty-detector.exe (PID: 5712)
Process drops python dynamic module
- unnatty-detector.exe (PID: 5712)
The process drops C-runtime libraries
- unnatty-detector.exe (PID: 5712)
Executable content was dropped or overwritten
- unnatty-detector.exe (PID: 5712)
Loads Python modules
- main.exe (PID: 4468)
INFO
Checks supported languages
- unnatty-detector.exe (PID: 5712)
- main.exe (PID: 4468)
Create files in a temporary directory
- unnatty-detector.exe (PID: 5712)
Reads the machine GUID from the registry
- main.exe (PID: 4468)
Reads the computer name
- main.exe (PID: 4468)
Checks proxy server information
- main.exe (PID: 4468)
Themida protector has been detected
- unnatty-detector.exe (PID: 5712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:08 21:20:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 133120 |
| InitializedDataSize: | 10253824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xffe058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Oracle |
| ProductName: | Discord Hook Detector |
| FileDescription: | Discord Hook Detector |
| ProductVersion: | 1.0.0.0 |
| FileVersion: | 1.0.0.0 |
| OriginalFileName: | main.exe |
| InternalName: | main |
Total processes
119
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4468 | C:\Users\admin\Desktop\unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\main.exe | unnatty-detector.exe | ||||||||||||
User: admin Company: Oracle Integrity Level: MEDIUM Description: Discord Hook Detector Version: 1.0.0.0 Modules
| |||||||||||||||
| 5628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | unnatty-detector.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5712 | "C:\Users\admin\Desktop\unnatty-detector.exe" | C:\Users\admin\Desktop\unnatty-detector.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Integrity Level: MEDIUM Description: Discord Hook Detector Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
348
Read events
348
Write events
0
Delete events
0
Modification events
Executable files
27
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_decimal.pyd | executable | |
MD5:CE4DF4DFE65AB8DC7AE6FCDEBAE46112 | SHA256:FFBE84F0A1EAB363CA9CF73EFB7518F2ABD52C0893C7CC63266613C930855E96 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\libssl-1_1.dll | executable | |
MD5:BC778F33480148EFA5D62B2EC85AAA7D | SHA256:9D4CF1C03629F92662FC8D7E3F1094A7FC93CB41634994464B853DF8036AF843 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_cffi_backend.pyd | executable | |
MD5:1D426469974F80F68CFFEA594560D10B | SHA256:FB759CB37C785BC286F8DE4CA4679E887FB3981A74F458449553E0DF6956CFA9 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_ctypes.pyd | executable | |
MD5:29DA9B022C16DA461392795951CE32D9 | SHA256:3B4012343EF7A266DB0B077BBB239833779192840D1E2C43DFCBC48FFD4C5372 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\libffi-7.dll | executable | |
MD5:EEF7981412BE8EA459064D3090F4B3AA | SHA256:F60DD9F2FCBD495674DFC1555EFFB710EB081FC7D4CAE5FA58C438AB50405081 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_queue.pyd | executable | |
MD5:4AB2CEB88276EBA7E41628387EACB41E | SHA256:D82AB111224C54BAB3EEFDCFEB3BA406D74D2884518C5A2E9174E5C6101BD839 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_lzma.pyd | executable | |
MD5:B5355DD319FB3C122BB7BF4598AD7570 | SHA256:B9BC7F1D8AA8498CB8B5DC75BB0DBB6E721B48953A3F295870938B27267FB5F5 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_elementtree.pyd | executable | |
MD5:048EA61F0C0F7FD42DFE8CA3203D5E99 | SHA256:9B9ABF5672BEC167B854A106EB25701433B34A0C877ED5E363202247E5BADA58 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_socket.pyd | executable | |
MD5:F5DD9C5922A362321978C197D3713046 | SHA256:4494992665305FC9401ED327398EE40064FE26342FE44DF11D89D2AC1CC6F626 | |||
| 5712 | unnatty-detector.exe | C:\Users\admin\AppData\Local\Temp\onefile_5712_133781683974854411\_uuid.pyd | executable | |
MD5:C9D5A1A4B6186B5AD1242E6C5CCA31E5 | SHA256:EEC57D615873E2065ED83DA6164774B9396B4984AD39E1C2166F2C9B45626272 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2548 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |