| File name: | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe |
| Full analysis: | https://app.any.run/tasks/7faf311f-dbcc-4771-8370-a14a7b2ecbb5 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 02:22:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F82EC02D4A0896965C6911023F87B44E |
| SHA1: | 091EDEB7FA245D31361B3A527C837169FA389AD2 |
| SHA256: | 597F2DB857EB2284619430336A018D49E433AC2DED7B12DE47202556CB0900FD |
| SSDEEP: | 98304:oQ6ZQMb2K9PhIKgcNVjNlO8N2sepib7oMHxP5GRbJQJ1dPlpvhcVTZxS+amQRTfn:v6gRlp0WrEguvlN/FQ92tr29Z+NSsY+ |
MALICIOUS
Drops the executable file immediately after the start
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- Installer.exe (PID: 6460)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- msiexec.exe (PID: 4752)
- TiWorker.exe (PID: 3592)
Steals credentials from Web Browsers
- Installer.exe (PID: 6460)
Actions looks like stealing of personal data
- Installer.exe (PID: 6460)
Registers / Runs the DLL via REGSVR32.EXE
- Installer.exe (PID: 6460)
Uses Task Scheduler to autorun other applications
- Installer.exe (PID: 6460)
Creates a writable file in the system directory
- dllhost.exe (PID: 6688)
SUSPICIOUS
Reads security settings of Internet Explorer
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- Installer.exe (PID: 6460)
- RegAsm.exe (PID: 4856)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Executable content was dropped or overwritten
- Installer.exe (PID: 6460)
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- TiWorker.exe (PID: 3592)
Reads the Windows owner or organization settings
- Installer.exe (PID: 6460)
- msiexec.exe (PID: 4752)
Reads browser cookies
- Installer.exe (PID: 6460)
Reads the date of Windows installation
- Installer.exe (PID: 6460)
Process drops legitimate windows executable
- Installer.exe (PID: 6460)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- msiexec.exe (PID: 4752)
- TiWorker.exe (PID: 3592)
Starts a Microsoft application from unusual location
- vcredist_2008_SP1_x64.exe (PID: 7056)
Checks Windows Trust Settings
- msiexec.exe (PID: 4752)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
The process drops C-runtime libraries
- TiWorker.exe (PID: 3592)
- msiexec.exe (PID: 4752)
Drops a system driver (possible attempt to evade defenses)
- Installer.exe (PID: 6460)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6700)
- regsvr32.exe (PID: 3960)
- regsvr32.exe (PID: 1604)
- RegAsm.exe (PID: 4856)
Creates a software uninstall entry
- Installer.exe (PID: 6460)
Executes as Windows Service
- WmiApSrv.exe (PID: 6380)
The process checks if it is being run in the virtual environment
- Updater.exe (PID: 5004)
INFO
Create files in a temporary directory
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- Installer.exe (PID: 6460)
- install.exe (PID: 3976)
Checks proxy server information
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- Installer.exe (PID: 6460)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Reads the computer name
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- Installer.exe (PID: 6460)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- install.exe (PID: 3976)
- msiexec.exe (PID: 4752)
- RegAsm.exe (PID: 4856)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Checks supported languages
- Installer.exe (PID: 6460)
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- install.exe (PID: 3976)
- msiexec.exe (PID: 4752)
- RegAsm.exe (PID: 4856)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Reads the machine GUID from the registry
- Installer.exe (PID: 6460)
- vcredist_2008_SP1_x64.exe (PID: 7056)
- msiexec.exe (PID: 4752)
- RegAsm.exe (PID: 4856)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Process checks computer location settings
- Installer.exe (PID: 6460)
- 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe (PID: 6400)
Creates files in the program directory
- Installer.exe (PID: 6460)
- dllhost.exe (PID: 6688)
Reads Environment values
- Installer.exe (PID: 6460)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Reads the software policy settings
- Installer.exe (PID: 6460)
- msiexec.exe (PID: 4752)
- Updater.exe (PID: 5428)
- Updater.exe (PID: 5004)
Reads Microsoft Office registry keys
- Installer.exe (PID: 6460)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4752)
Creates files or folders in the user directory
- msiexec.exe (PID: 4752)
- Updater.exe (PID: 5428)
Creates a software uninstall entry
- msiexec.exe (PID: 4752)
Reads the time zone
- Updater.exe (PID: 5004)
Reads CPU info
- Updater.exe (PID: 5004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:05:26 11:18:03+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 143872 |
| InitializedDataSize: | 330240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24530 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.2.62618 |
| ProductVersionNumber: | 4.1.2.62618 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
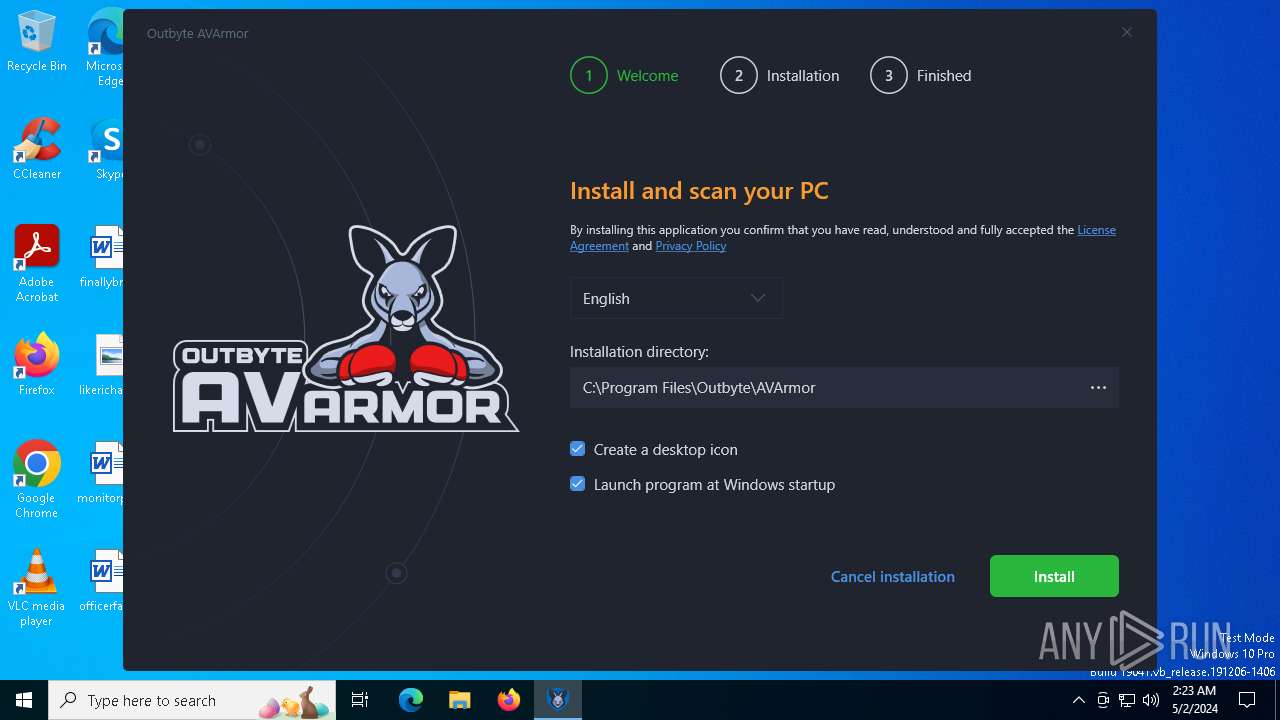
| Comments: | AVArmor |
| CompanyName: | Outbyte |
| FileDescription: | Outbyte AVArmor Installation File |
| FileVersion: | 4.1.2.62618 |
| LegalCopyright: | Copyright © 2016-2021 Outbyte Computing Pty Ltd |
| OriginalFileName: | Outbyte-avarmor-setup.exe |
| ProductName: | AVArmor |
| ProductVersion: | 4.x |
Total processes
148
Monitored processes
23
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Windows\System32\schtasks.exe" /CREATE /TN "Outbyte\AVArmor\Start Outbyte AVArmor automatic scanning" /TR "C:\Program Files\Outbyte\AVArmor\AVArmor.exe /Scheduler /SchedulerLogon /UseTray" /SC ONLOGON /RL HIGHEST /F | C:\Windows\SysWOW64\schtasks.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | /s "C:\Program Files\Outbyte\AVArmor\Helper.AntiMalware.Update.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Updater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3592 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3960 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files\Outbyte\AVArmor\BrowserHelper.Agent.x64.dll" | C:\Windows\System32\regsvr32.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3976 | c:\f93384f0c3e45cf0b7fc\.\install.exe /q | C:\f93384f0c3e45cf0b7fc\install.exe | — | vcredist_2008_SP1_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: External Installer Exit code: 0 Version: 9.0.30729.5677 built by: QFE Modules
| |||||||||||||||
| 4752 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4856 | "C:\WINDOWS\Microsoft.Net\Framework64\v4.0.30319\regasm.exe" "C:\Program Files\Outbyte\AVArmor\ShellExtension.dll" /codebase | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\RegAsm.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5004 | "C:\Program Files\Outbyte\AVArmor\Updater.exe" /update | C:\Program Files\Outbyte\AVArmor\Updater.exe | Installer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Updater Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
28 550
Read events
27 919
Write events
550
Delete events
81
Modification events
| (PID) Process: | (6400) 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Outbyte\AVArmor\4.x\Settings |
| Operation: | write | Name: | General.CustomClientId |
Value: {7AF497BF-A264-448C-8581-DCA25AA453AD} | |||
| (PID) Process: | (6400) 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Outbyte\AVArmor\4.x\Settings |
| Operation: | write | Name: | General.URLClientId |
Value: {7AF497BF-A264-448C-8581-DCA25AA453AD} | |||
| (PID) Process: | (6400) 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6400) 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6400) 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6460) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Outbyte\AVArmor\4.x\Settings |
| Operation: | write | Name: | SendLogWindowShown_Installer |
Value: 0 | |||
| (PID) Process: | (6460) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Outbyte\AVArmor\4.x\Settings |
| Operation: | write | Name: | General.Language |
Value: ENU | |||
| (PID) Process: | (6460) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Outbyte\AVArmor\4.x\Settings |
| Operation: | write | Name: | Installer.Type |
Value: lite | |||
| (PID) Process: | (6460) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6460) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Installer_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
153
Suspicious files
58
Text files
109
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\SetupHelper.dll | executable | |
MD5:8A68FD9A4C1553ADDE687A821E4916E5 | SHA256:F9EFB9C3E3E799AB58D50E44CE8FB1C988E2C0C29501B42FCD0D849153012ED3 | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Helper.WebBrowsers.dll | executable | |
MD5:E9D97F763910B34583B065FF0D438B98 | SHA256:3E5B0299EC4227770E28712B2E3364FCA50F221C7D159B3DB6BEC26BCD8A1081 | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Helper.Localizer.dll | executable | |
MD5:77163FC110D6E351C2A31819C0286BFD | SHA256:A303831EB1BCD4E3595ADC5F1711056102BF32DA0BE3CB8BDCE779B488E4D9E2 | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Lang\enu.lng | binary | |
MD5:A7DEB5FDBFC6F978A1F95E2A97603133 | SHA256:968C6519045CCD37A3D9B95CD88197714FB6713DC6A6653997EA31786F7F2310 | |||
| 7056 | vcredist_2008_SP1_x64.exe | C:\f93384f0c3e45cf0b7fc\vc_red.cab | — | |
MD5:— | SHA256:— | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Installer.exe | executable | |
MD5:15BECFE9B5DC3D31A7862B79738B32B2 | SHA256:04FDCA25088EDE7AA15358E12E01139F0479FD3FE04C37C1845357CA6E86690B | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Newtonsoft.Json.dll | executable | |
MD5:578517DE4BC8B9C092BFE57DB5472EC7 | SHA256:EA0E62514E72E9D4026A5731B3D8B5ADA6F27EC7B22F89148F3007600579C6AE | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Helper.MVVM.dll | executable | |
MD5:5D46F8C26A10D4D4D097B785D78F884A | SHA256:F0B770E5A1A3B74259434FBBB625EE4BB1170712EEACC3B67C98F000B0CB8836 | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Helper.Rtl.dll | executable | |
MD5:478EFC6CFC2AF0E6F0381E606AEB67F3 | SHA256:F6285F7E0E3F781969A2F45E6CA80514E584BBE16ED278227EB8DF0FCE16C480 | |||
| 6400 | 597f2db857eb2284619430336a018d49e433ac2ded7b12de47202556cb0900fd.exe | C:\Users\admin\AppData\Local\Temp\is-30411404.tmp\Helper.GA.dll | executable | |
MD5:8AC085F5DFFED13358EA042CBE147171 | SHA256:DB9A38FA47F1456BE0BCB1E2AD074559D9B5D8E5347A08E510E1A60187A1AC01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
60
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4264 | svchost.exe | GET | 200 | 23.48.10.36:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
6460 | Installer.exe | POST | 200 | 142.250.186.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4264 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4232 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4264 | svchost.exe | 23.48.10.36:80 | www.microsoft.com | Akamai International B.V. | US | unknown |
6460 | Installer.exe | 45.33.97.245:443 | outbyte.com | Linode, LLC | US | unknown |
6460 | Installer.exe | 142.250.186.174:80 | www.google-analytics.com | GOOGLE | US | whitelisted |
6460 | Installer.exe | 23.49.244.196:443 | download.microsoft.com | AKAMAI-AS | PT | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
outbyte.com |
| unknown |
www.google-analytics.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |