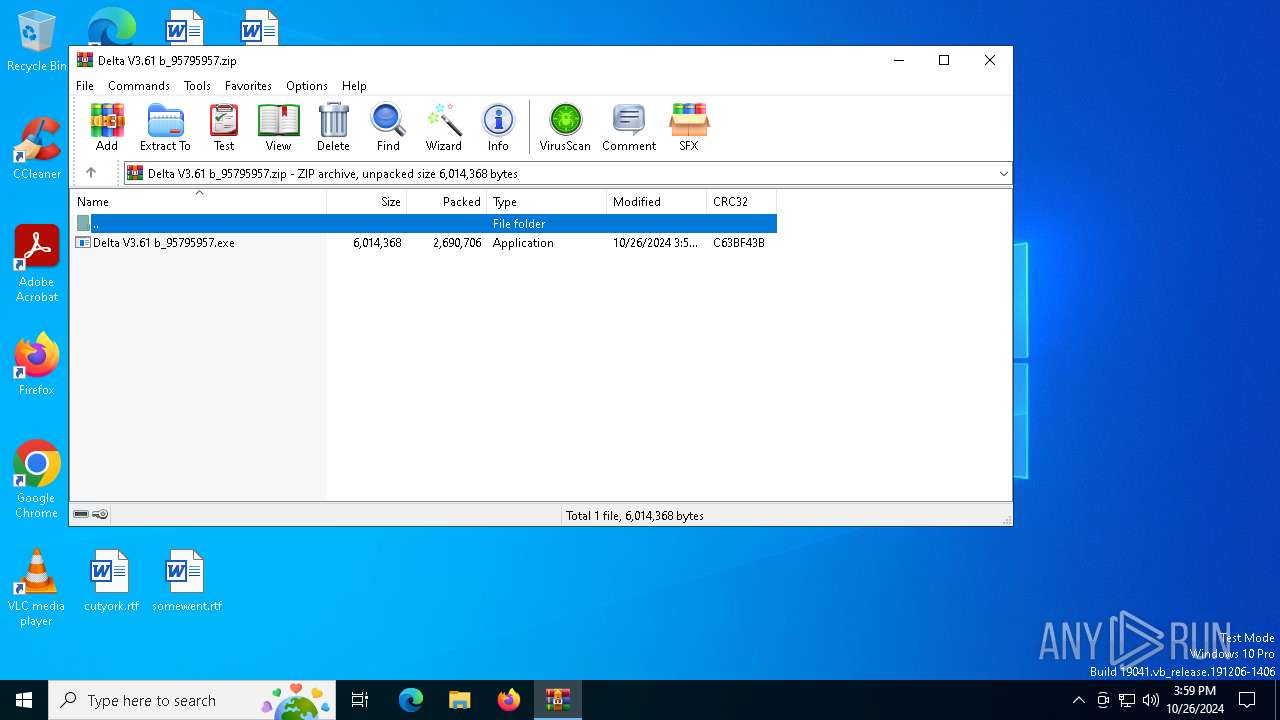
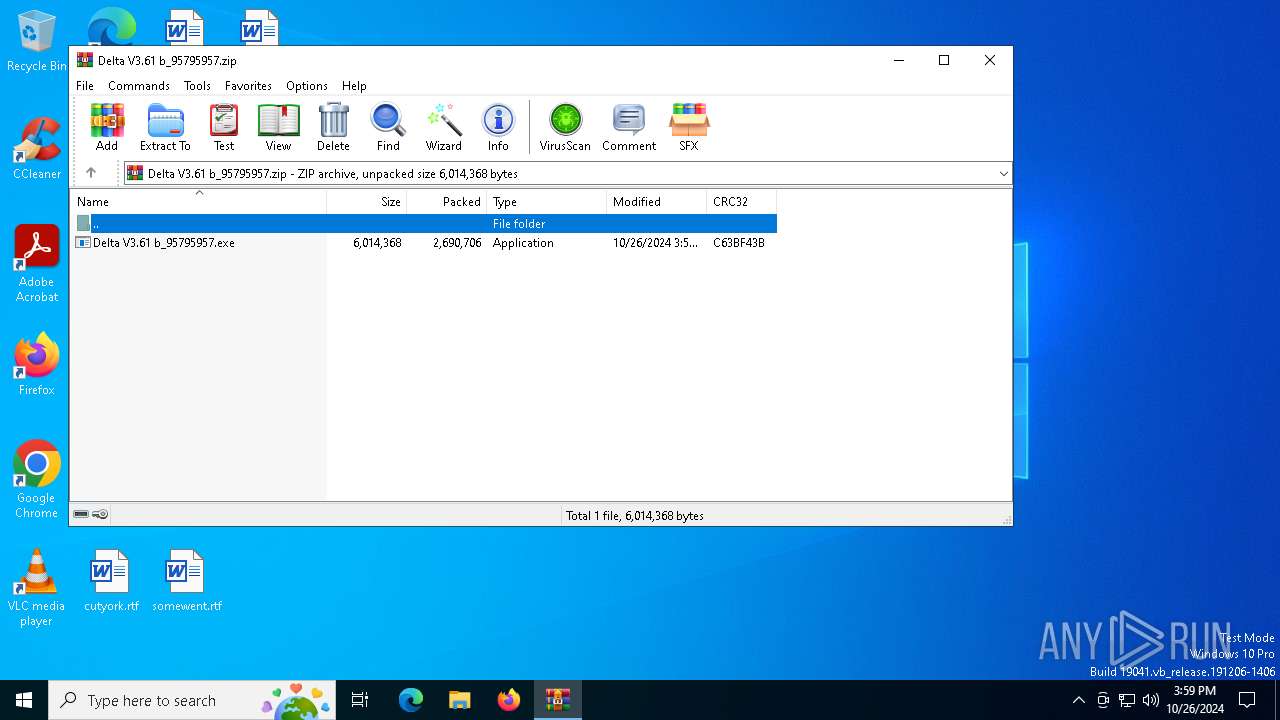
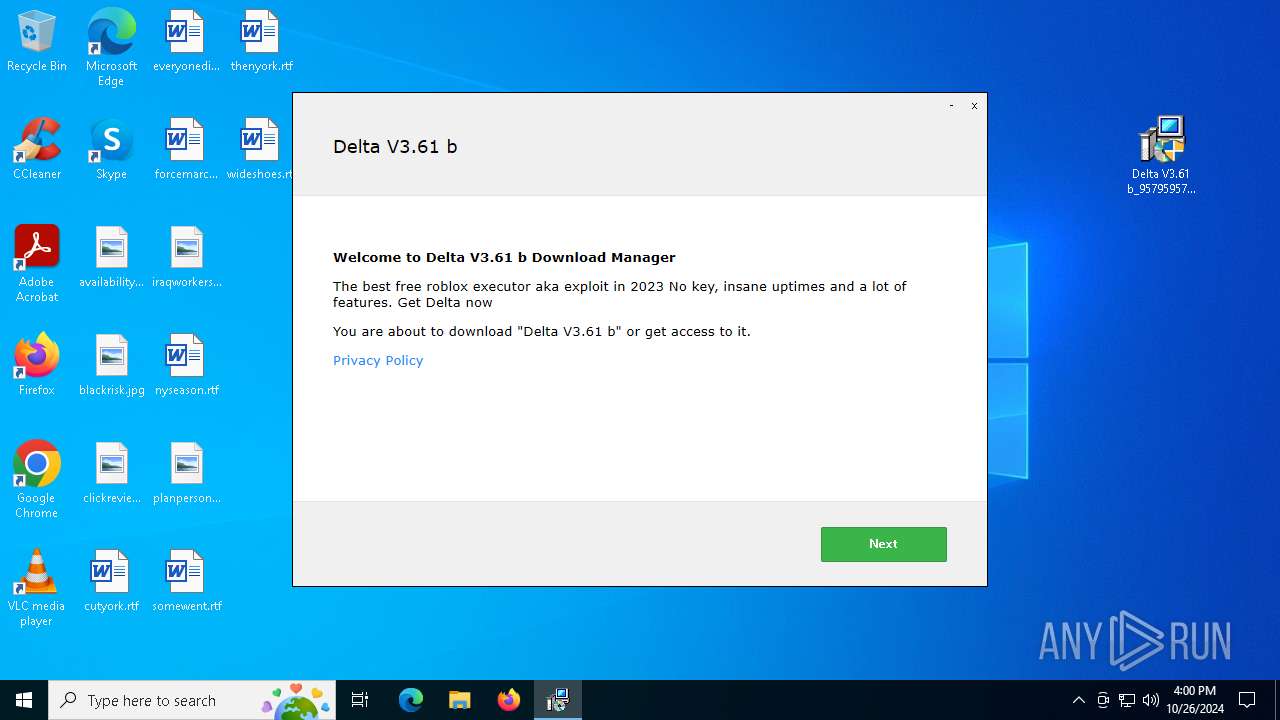
| File name: | Delta V3.61 b_95795957.zip |
| Full analysis: | https://app.any.run/tasks/7fea0d8f-4636-4abe-bcc8-a5fa22e3bb2c |
| Verdict: | Malicious activity |
| Analysis date: | October 26, 2024, 15:59:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C98302E831CABF9838ED08CD7609E603 |
| SHA1: | 2AB4D7C279CF09DC46CD22C21A34ECFCB4CE2F23 |
| SHA256: | 597EA52CE7BC05C98347D38F3419B25DF68DD14E9317666E7F71FAEFFF800129 |
| SSDEEP: | 98304:wHntobDS5TEQDNPszENnysk250FJTP5xfdeohobHnl80dVO8r88zF/KE4kRZ907M:wmLLbA |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5832)
SUSPICIOUS
Reads security settings of Internet Explorer
- Delta V3.61 b_95795957.exe (PID: 6960)
Checks Windows Trust Settings
- Delta V3.61 b_95795957.exe (PID: 6960)
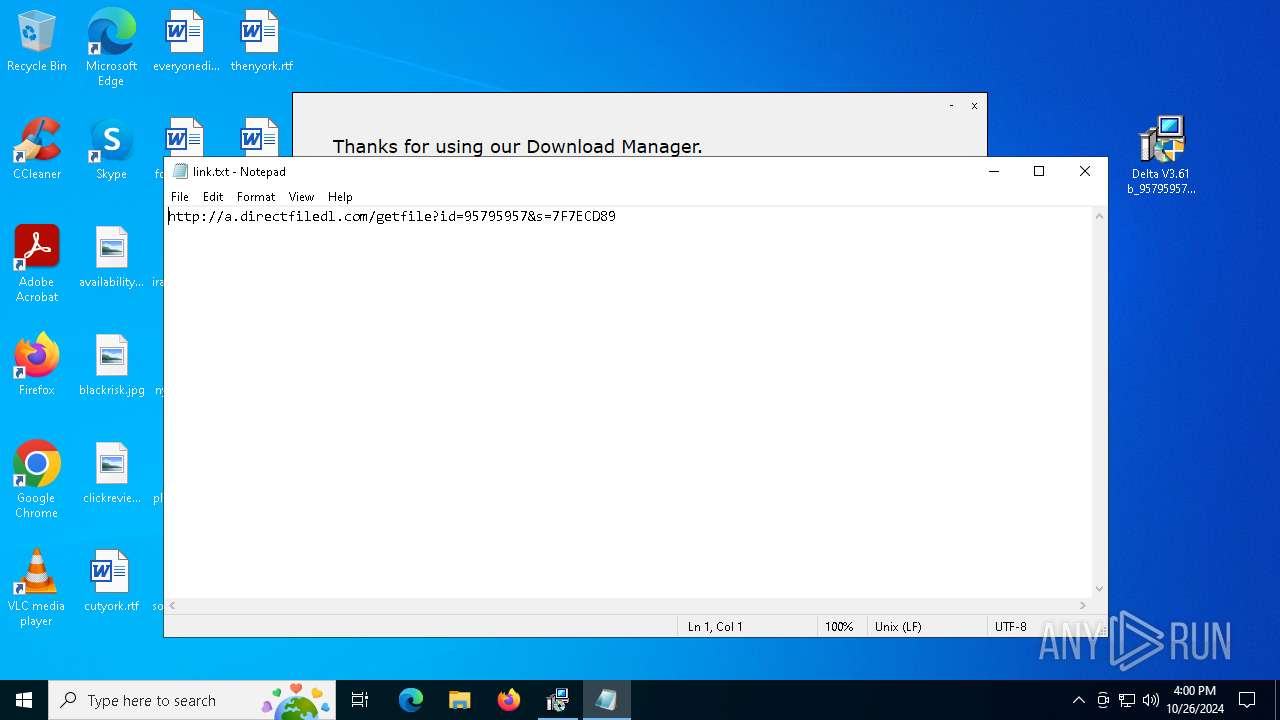
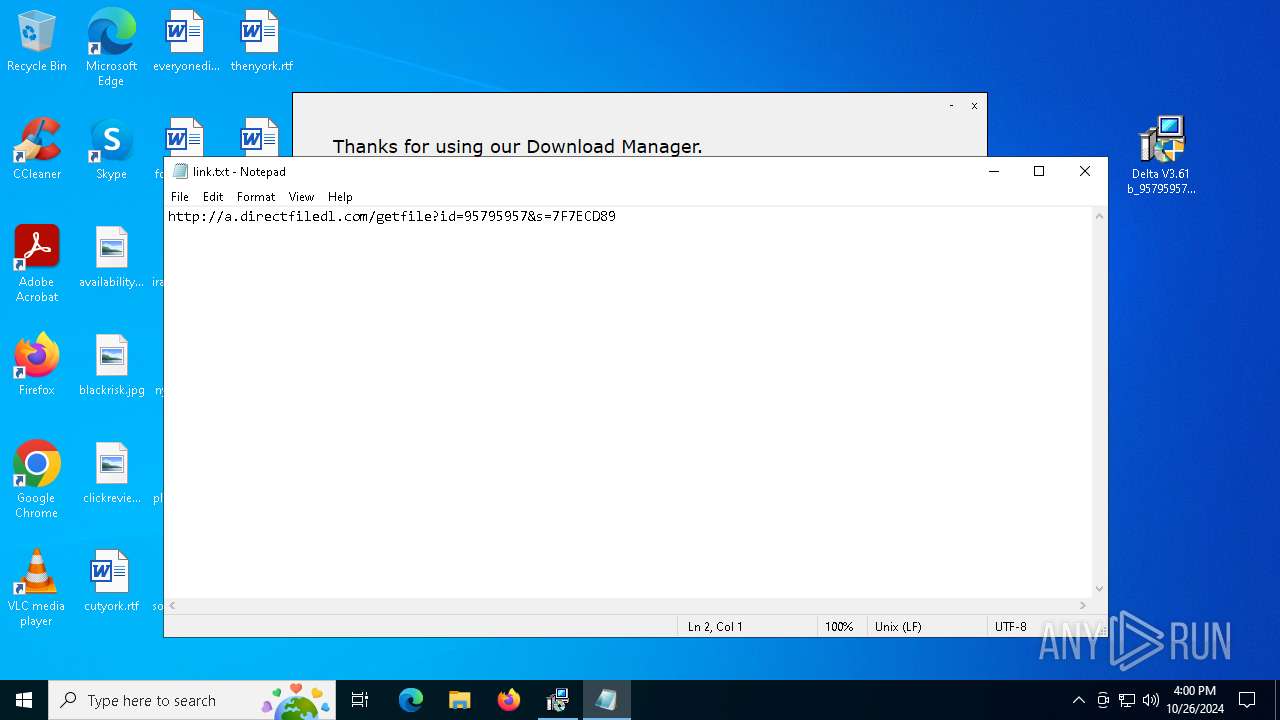
Start notepad (likely ransomware note)
- Delta V3.61 b_95795957.exe (PID: 6960)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5832)
- Delta V3.61 b_95795957.exe (PID: 6960)
Checks supported languages
- Delta V3.61 b_95795957.exe (PID: 6960)
Manual execution by a user
- Delta V3.61 b_95795957.exe (PID: 3964)
- Delta V3.61 b_95795957.exe (PID: 6960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5832)
Reads the machine GUID from the registry
- Delta V3.61 b_95795957.exe (PID: 6960)
Reads the computer name
- Delta V3.61 b_95795957.exe (PID: 6960)
Creates files or folders in the user directory
- Delta V3.61 b_95795957.exe (PID: 6960)
Sends debugging messages
- Delta V3.61 b_95795957.exe (PID: 6960)
Checks proxy server information
- Delta V3.61 b_95795957.exe (PID: 6960)
Reads the software policy settings
- Delta V3.61 b_95795957.exe (PID: 6960)
Process checks computer location settings
- Delta V3.61 b_95795957.exe (PID: 6960)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:26 17:52:46 |
| ZipCRC: | 0xc63bf43b |
| ZipCompressedSize: | 2690706 |
| ZipUncompressedSize: | 6014368 |
| ZipFileName: | Delta V3.61 b_95795957.exe |
Total processes
131
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3964 | "C:\Users\admin\Desktop\Delta V3.61 b_95795957.exe" | C:\Users\admin\Desktop\Delta V3.61 b_95795957.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 5532 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\SysWOW64\notepad.exe | — | Delta V3.61 b_95795957.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Delta V3.61 b_95795957.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6960 | "C:\Users\admin\Desktop\Delta V3.61 b_95795957.exe" | C:\Users\admin\Desktop\Delta V3.61 b_95795957.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Download Manager Exit code: 0 Version: 1 Modules
| |||||||||||||||
Total events
3 180
Read events
3 160
Write events
20
Delete events
0
Modification events
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Delta V3.61 b_95795957.zip | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
1
Suspicious files
16
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:AC8BC48B6912B01E2E39B3D740ADF28A | SHA256:67265117A772A65266A363D31156889EE722AA85993778B2DBF35B64864D91D0 | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:D988B482E25C437895832B9BF13EBC80 | SHA256:03797DC23D7F47177E8EB91C29FB1E8BB91F845E9D95DE607A3DFB0CD719634D | |||
| 5832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5832.20989\Delta V3.61 b_95795957.exe | executable | |
MD5:15D1C495FF66BF7CEA8A6D14BFDF0A20 | SHA256:61C2C4A5D7C14F77EE88871DED4CC7F1E49DAE3E4EF209504C66FEDF4D22DE42 | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\service[1].htm | text | |
MD5:F9D4655BBB31D3745D1D1671E3A09F4A | SHA256:C09DC2BA6150D341E056631E8FBC1A91AFCD6D87759BDE08E75A1FC506641203 | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:67E486B2F148A3FCA863728242B6273E | SHA256:FACAF1C3A4BF232ABCE19A2D534E495B0D3ADC7DBE3797D336249AA6F70ADCFB | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:AD9EAEBF8C2B35CD2C5674CE9F47CF64 | SHA256:E00FA6DC6DD6FAB3116795644453F89864BB5C0C2FCE77E55226F877EB2B7D3B | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F53EB4E574DE32C870452087D92DBEBB_6D263F6DDB7D7C531B75FF66E0A31295 | binary | |
MD5:64616F1C03C16935CC59B285F21B90CD | SHA256:1677EA20A7282AABA27FB1BE17EB75159A0E76F9F50746DB8355618B6D1E993B | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:D9B301CC05A43767EB468F9CF69FF42B | SHA256:1451042F30CF10B28E7CBD78F1B558B23A85675D0FB54038CE846A9DDD23A89F | |||
| 6960 | Delta V3.61 b_95795957.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:40F291E3FF34296B72C05076808058B1 | SHA256:E8D9730E60422B33B5E6CA4A118E9C1DAABB0CE3F44EF48DAD110F067B8B6AB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
30
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.21.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4836 | RUXIMICS.exe | GET | 200 | 2.21.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.21.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.41.213.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4836 | RUXIMICS.exe | GET | 200 | 23.41.213.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6960 | Delta V3.61 b_95795957.exe | GET | 200 | 172.217.23.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6960 | Delta V3.61 b_95795957.exe | GET | 200 | 172.217.23.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6960 | Delta V3.61 b_95795957.exe | GET | 200 | 172.217.168.195:80 | http://o.pki.goog/s/wr3/P5k/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCED%2BZ8T58jUdVEjMJ%2F%2B4wrmA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.41.213.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4836 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 95.100.95.191:443 | www.bing.com | Akamai International B.V. | FR | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.21.23.191:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4836 | RUXIMICS.exe | 2.21.23.191:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.dlsft.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
Threats
Process | Message |
|---|---|
Delta V3.61 b_95795957.exe | Error: (undefined) has no property - value
|
Delta V3.61 b_95795957.exe | |
Delta V3.61 b_95795957.exe | |
Delta V3.61 b_95795957.exe | at initializeDynamicVariables (this://app/main.html(351))
|
Delta V3.61 b_95795957.exe | at getFileInfo.@307@46 (this://app/main.html(329))
|
Delta V3.61 b_95795957.exe | scanning node question /questions/question
|
Delta V3.61 b_95795957.exe | scanning node questions /questions
|
Delta V3.61 b_95795957.exe | scanning node question /questions/question
|
Delta V3.61 b_95795957.exe | scanning node question /questions/question
|
Delta V3.61 b_95795957.exe | scanning node question /questions/question
|