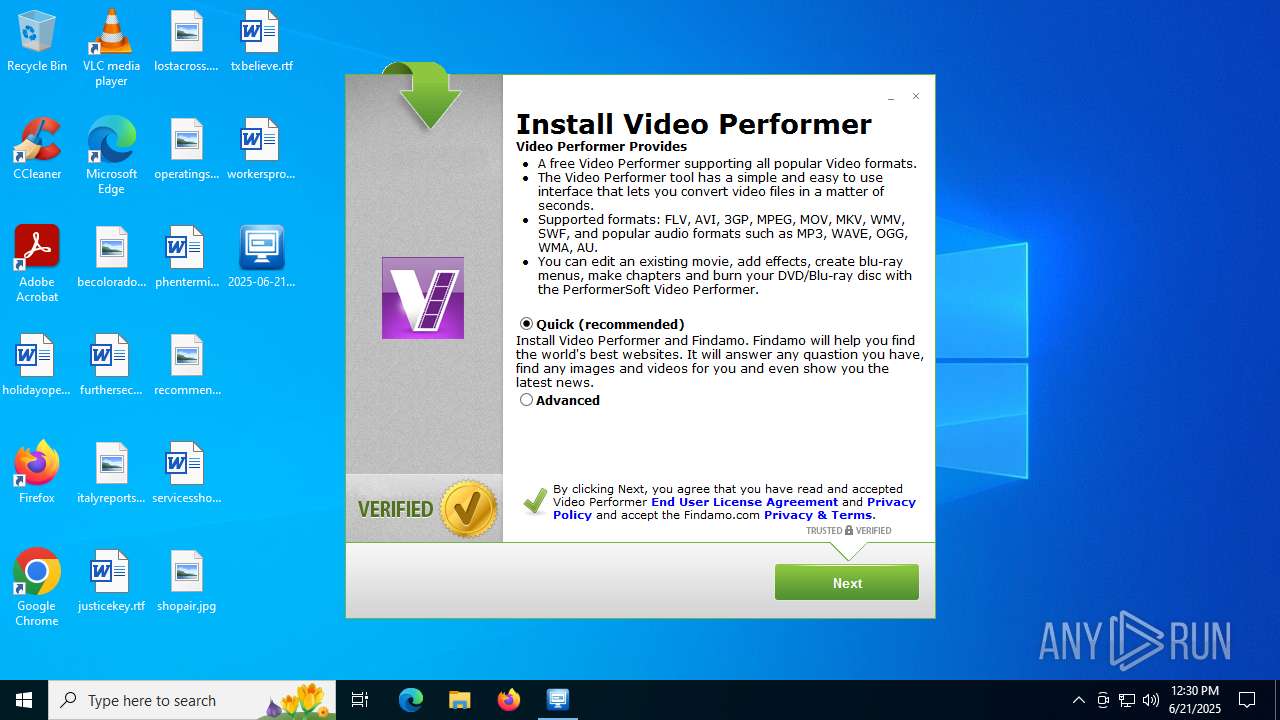
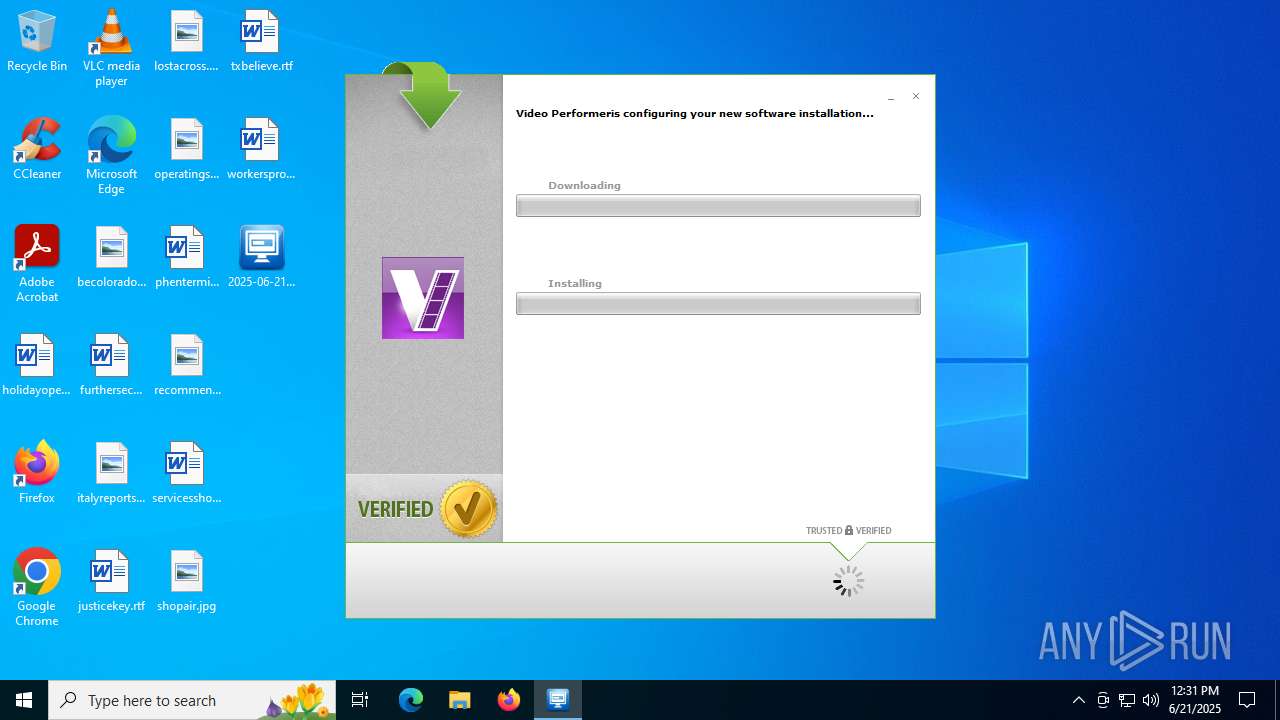
| File name: | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys |
| Full analysis: | https://app.any.run/tasks/2a2956ec-ac28-4288-b913-3fc7aba4d6b0 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 12:30:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 8B93A5C994C7A4703BE5EEA6D62438D7 |
| SHA1: | 44FB1E01757A7555D4E68D79027D40180847BB28 |
| SHA256: | 5974DBC08324CAB2444CAFE3E42864FBF710D47E2D5B512F0158E7F63CBC9A1F |
| SSDEEP: | 49152:zsEGTM9E0NVxY8JqOLkl17fCKfKf7rmFIxhCC5E9kM0TdeRavRNqZ1tP2wTmprs8:zrYM9E0NwlOkl17f3fiQmw+BMTRoOJmj |
MALICIOUS
XORed URL has been found (YARA)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Drops 7-zip archiver for unpacking
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Reads security settings of Internet Explorer
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Application launched itself
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
Searches for installed software
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Reads Microsoft Outlook installation path
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Reads Internet Explorer settings
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
There is functionality for taking screenshot (YARA)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
INFO
Checks supported languages
- tmppack.exe (PID: 6640)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
- tmppack.exe (PID: 6868)
The sample compiled with english language support
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Create files in a temporary directory
- tmppack.exe (PID: 6640)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- tmppack.exe (PID: 6868)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Reads the computer name
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Process checks computer location settings
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 1068)
Reads the machine GUID from the registry
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
Checks proxy server information
- 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe (PID: 3048)
- slui.exe (PID: 1100)
Manual execution by a user
- wscript.exe (PID: 2620)
- wscript.exe (PID: 6652)
- wscript.exe (PID: 768)
- wscript.exe (PID: 1816)
- wscript.exe (PID: 6940)
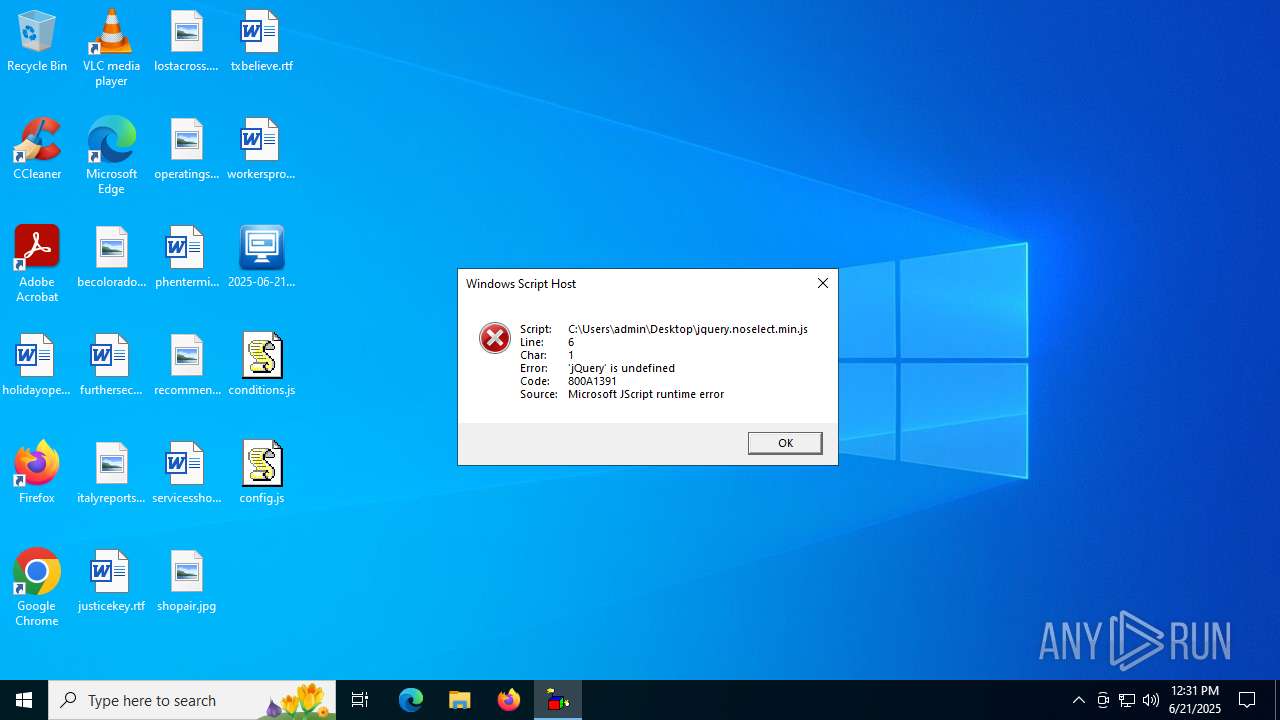
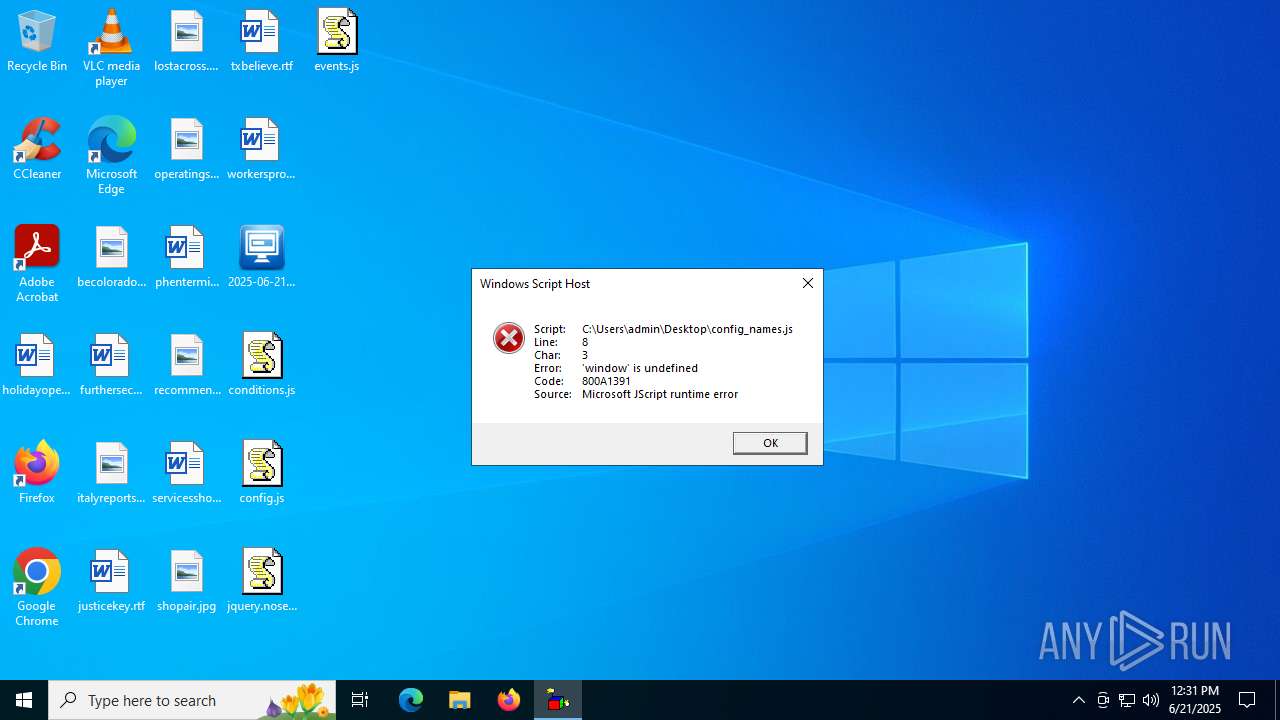
JScript runtime error (SCRIPT)
- wscript.exe (PID: 768)
- wscript.exe (PID: 6940)
Reads the software policy settings
- slui.exe (PID: 1100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(1068) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe
Decrypted-URLs (2)http://api.ibario.com/events
http://www.appdint.com/installer/603/start.cf]]
(PID) Process(3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe
Decrypted-URLs (2)http://api.ibario.com/events
http://www.appdint.com/installer/603/start.cf]]
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:08:20 08:24:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 104960 |
| InitializedDataSize: | 52224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a81f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.9.13.20 |
| ProductVersionNumber: | 14.9.13.20 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 14.9.13.20 |
| InternalName: | - |
| LegalCopyright: | Copyright 2014 |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 14.9.13.20 |
Total processes
144
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 768 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\jquery.noselect.min.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\Desktop\2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe" | C:\Users\admin\Desktop\2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 14.9.13.20 Modules
xor-url(PID) Process(1068) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe Decrypted-URLs (2)http://api.ibario.com/events http://www.appdint.com/installer/603/start.cf]] | |||||||||||||||
| 1100 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\events.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2620 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\conditions.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tmppack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3048 | "C:\Users\admin\Desktop\2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe" | C:\Users\admin\Desktop\2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 14.9.13.20 Modules
xor-url(PID) Process(3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe Decrypted-URLs (2)http://api.ibario.com/events http://www.appdint.com/installer/603/start.cf]] | |||||||||||||||
| 4544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tmppack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | -y | C:\Users\admin\AppData\Local\Temp\CRQCBXSFPOOPBD\tmppack.exe | — | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z Console SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 6652 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\config.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
6 689
Read events
6 681
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (3048) 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 4272170000000000 | |||
| (PID) Process: | (2620) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 511E180000000000 | |||
Executable files
2
Suspicious files
19
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6868 | tmppack.exe | C:\Users\admin\AppData\Local\Temp\ENEAJFOQTEFPW\installer.pak | binary | |
MD5:A4A7F8CB2DBEFE97901CF657F6ED5CA4 | SHA256:BABACF1CA8865E86EA715364C43B24C1E450A094CAB0852DEC1B3E26A42978A2 | |||
| 1068 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\CRQCBXSFPOOPBD\tmppack.exe | executable | |
MD5:D2F31D4BCB2F93E137EED54A8F4C8874 | SHA256:473AB84307C6D9CC7907598705DD2704360557C0BA0BECF5A090B269A81D087C | |||
| 6640 | tmppack.exe | C:\Users\admin\AppData\Local\Temp\CRQCBXSFPOOPBD\installer.pak | binary | |
MD5:A4A7F8CB2DBEFE97901CF657F6ED5CA4 | SHA256:BABACF1CA8865E86EA715364C43B24C1E450A094CAB0852DEC1B3E26A42978A2 | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\51v01265\gui\img\ajax-loader.gif | image | |
MD5:A51C5608D01ACF32DF728F299767F82B | SHA256:AEBC793D0064383EE6B1625BF3BB32532EC30A5C12BF9117066107D412119123 | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\ENEAJFOQTEFPW\tmppack.exe | executable | |
MD5:D2F31D4BCB2F93E137EED54A8F4C8874 | SHA256:473AB84307C6D9CC7907598705DD2704360557C0BA0BECF5A090B269A81D087C | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\51v01265\gui\ib\arrow.gif | image | |
MD5:E59393726E591E7688132D3E467F9D58 | SHA256:0FFC76E625E851402C6C1E56919E6B32E794C1F75B6EC9EF7AF4F8EEAC4A6A83 | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\51v01265\gui\ib\b4.gif | image | |
MD5:E63B91A6E84FCCFD575A7E36A441FD78 | SHA256:C4A77216A63902BEC0673E7715718802A5D97F56CED75EF6F968B0CA35B801ED | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\51v01265\gui\img\ajax-loader2.gif | image | |
MD5:F6DA23A955B4C5F6888B78D6704BFD83 | SHA256:2F5BA5BEAE156603313BC1150BAF6351BB7C6302131E871ACECF638E69FA43A3 | |||
| 3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\51v01265\gui\ib\b3.gif | image | |
MD5:5F7B5A10F11354787E7D52CE00B5E760 | SHA256:FB3EEF742EF0351DE606FC25B2517EFE9468FC44C664D72419D7425A1E71259F | |||
| 1068 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\~17A.tmp | binary | |
MD5:0D1A78EFFF090C6CC066C0D55533BDBF | SHA256:69A5460BC57288187D45CCD453D2AAFEDDD2A2B06EF1FCB2AFFE73053C4A7739 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
22
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
472 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | POST | — | 174.36.241.171:80 | http://api.ibario.com/events | unknown | — | — | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | POST | — | 174.36.241.171:80 | http://api.ibario.com/events | unknown | — | — | malicious |
3048 | 2025-06-21_8b93a5c994c7a4703be5eea6d62438d7_elex_mafia_rhadamanthys.exe | POST | — | 174.36.241.171:80 | http://api.ibario.com/events | unknown | — | — | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
472 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
472 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.ibario.com |
| unknown |
www.namnamtech.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |