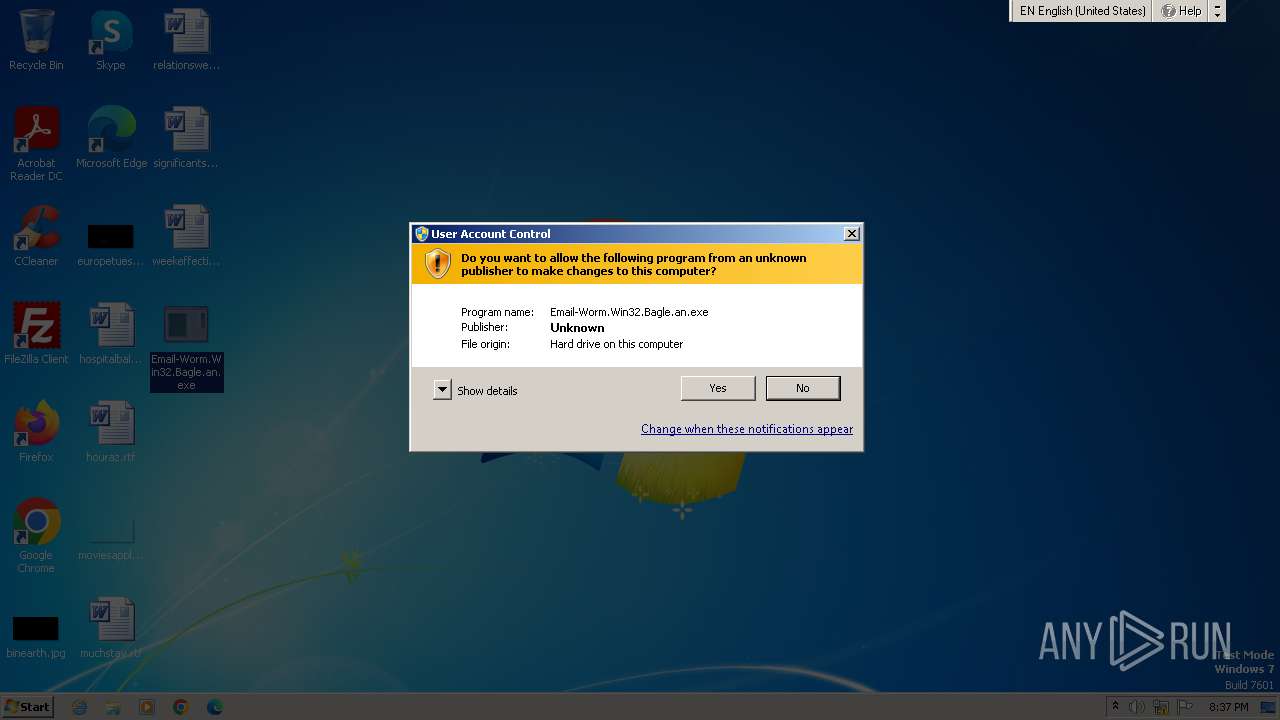
| download: | /vir/Email-Worm.Win32.Bagle.an |
| Full analysis: | https://app.any.run/tasks/e5ac672e-d44e-4902-9c47-257bd25e131c |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 20:37:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | B03B75D13384F1A1DED3074C13359203 |
| SHA1: | 15E692F9ED98450CE6F546781A507EB829363501 |
| SHA256: | 595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D |
| SSDEEP: | 384:VpD4N5i2jnx9o3f7bvu+xVK6cBo9qR6CKcUokVWGRveyys+KV:VYU2jnr0Tbvu+xo65qRIBokzeds+o |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts itself from another location
- Email-Worm.Win32.Bagle.an.exe (PID: 1236)
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
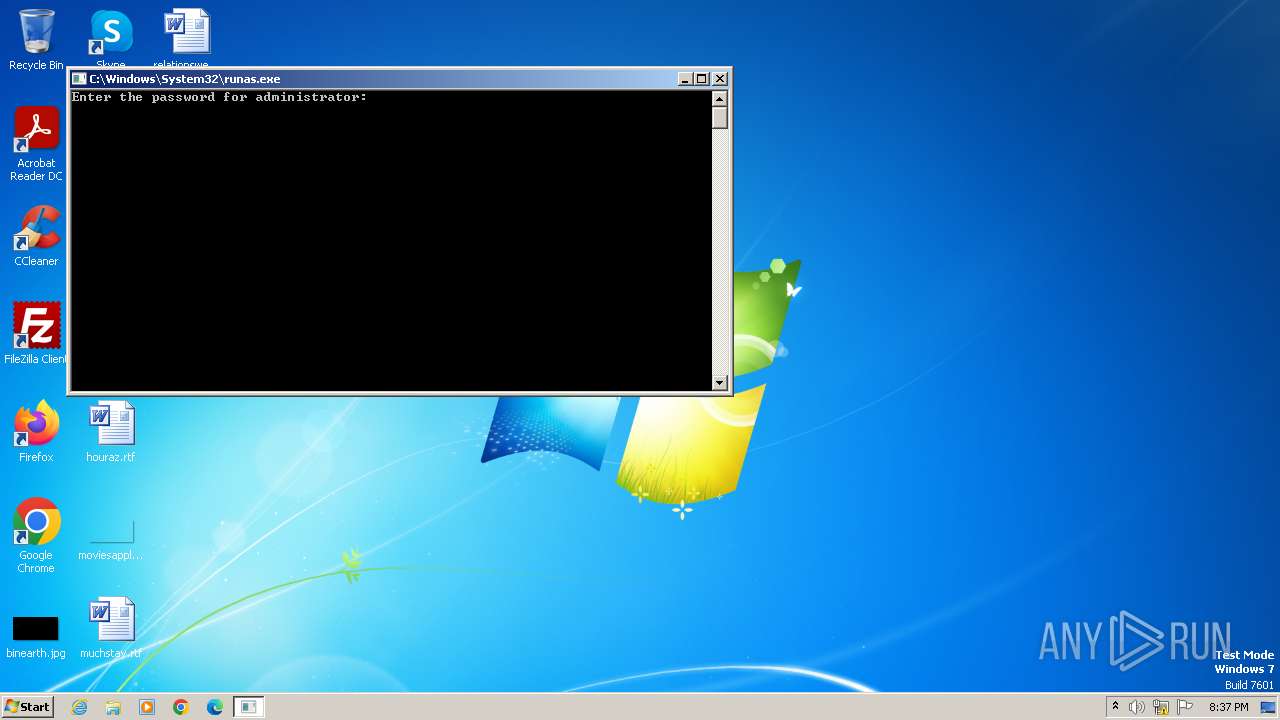
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 1824)
Executable content was dropped or overwritten
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- windll.exe (PID: 3388)
- windll.exe (PID: 1740)
Reads security settings of Internet Explorer
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
Reads the Internet Settings
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- control.exe (PID: 3004)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 3004)
Potential Corporate Privacy Violation
- windll.exe (PID: 3388)
Connects to SMTP port
- windll.exe (PID: 3388)
INFO
Checks supported languages
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- windll.exe (PID: 1740)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
- windll.exe (PID: 1080)
Reads the computer name
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- windll.exe (PID: 1740)
- windll.exe (PID: 1080)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
The process uses the downloaded file
- Email-Worm.Win32.Bagle.an.exe (PID: 1792)
- control.exe (PID: 3004)
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
Manual execution by a user
- Email-Worm.Win32.Bagle.an.exe (PID: 3264)
- control.exe (PID: 3004)
Reads security settings of Internet Explorer
- control.exe (PID: 3004)
Reads the time zone
- rundll32.exe (PID: 3008)
Checks transactions between databases Windows and Oracle
- rundll32.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | - |
| CodeSize: | 12800 |
| InitializedDataSize: | 14336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
54
Monitored processes
10
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Windows\system32\windll.exe" | C:\Windows\System32\windll.exe | — | Email-Worm.Win32.Bagle.an.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe" | C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1740 | "C:\Windows\system32\windll.exe" | C:\Windows\System32\windll.exe | Email-Worm.Win32.Bagle.an.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1792 | C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe | C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1824 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1940 | C:\Windows\system32\DllHost.exe /Processid:{9DF523B0-A6C0-4EA9-B5F1-F4565C3AC8B8} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3004 | "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl", | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl", | C:\Windows\System32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe" | C:\Users\admin\Desktop\Email-Worm.Win32.Bagle.an.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3388 | "C:\Windows\system32\windll.exe" | C:\Windows\System32\windll.exe | Email-Worm.Win32.Bagle.an.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
1 125
Read events
933
Write events
24
Delete events
168
Modification events
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | My AV |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | My AV |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Zone Labs Client Ex |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Zone Labs Client Ex |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | 9XHtProtect |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | 9XHtProtect |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Antivirus |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Antivirus |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Special Firewall Service |
Value: | |||
| (PID) Process: | (1792) Email-Worm.Win32.Bagle.an.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ru1n |
| Operation: | delete value | Name: | Special Firewall Service |
Value: | |||
Executable files
326
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\ACDSee 9.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\WinAmp 6 New!.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Microsoft Office XP working Crack, Keygen.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Microsoft Office 2003 Crack, Working!.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Microsoft Windows XP, WinXP Crack, working Keygen.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Porno Screensaver.scr | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Serials.txt.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Kaspersky Antivirus 5.0 | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Porno pics arhive, xxx.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
| 3388 | windll.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\static\js\plugins\unified-share\Windown Longhorn Beta Leak.exe | executable | |
MD5:B03B75D13384F1A1DED3074C13359203 | SHA256:595CE6C6FE34FCCB26B1BFC94B770F0B4903979FAC923754DAF10E3B9DAD651D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
226
DNS requests
630
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3388 | windll.exe | 17.57.170.2:25 | mx-in.g.apple.com | APPLE-ENGINEERING | US | whitelisted |
3388 | windll.exe | 51.81.232.218:25 | mx03.earthlink-vadesecure.net | OVH SAS | US | unknown |
3388 | windll.exe | 103.168.172.221:25 | in1-smtp.messagingengine.com | Cloudflare London, LLC | AU | unknown |
3388 | windll.exe | 194.104.110.22:25 | de-smtp-inbound-2.mimecast.com | Mimecast Services Limited | DE | suspicious |
3388 | windll.exe | 131.111.8.147:25 | mx.cam.ac.uk | Jisc Services Limited | GB | whitelisted |
3388 | windll.exe | 64.29.151.236:25 | ismtp.sitestar.everyone.net | INFB2-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
apple.com |
| whitelisted |
mx-in.g.apple.com |
| whitelisted |
pobox.com |
| unknown |
in1-smtp.messagingengine.com |
| unknown |
netcom.com |
| unknown |
mx03.earthlink-vadesecure.net |
| unknown |
northcoast.com |
| unknown |
cl.cam.ac.uk |
| whitelisted |
de-smtp-inbound-2.mimecast.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3388 | windll.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3388 | windll.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to network scan inside a home network |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3388 | windll.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to network scan inside a home network |