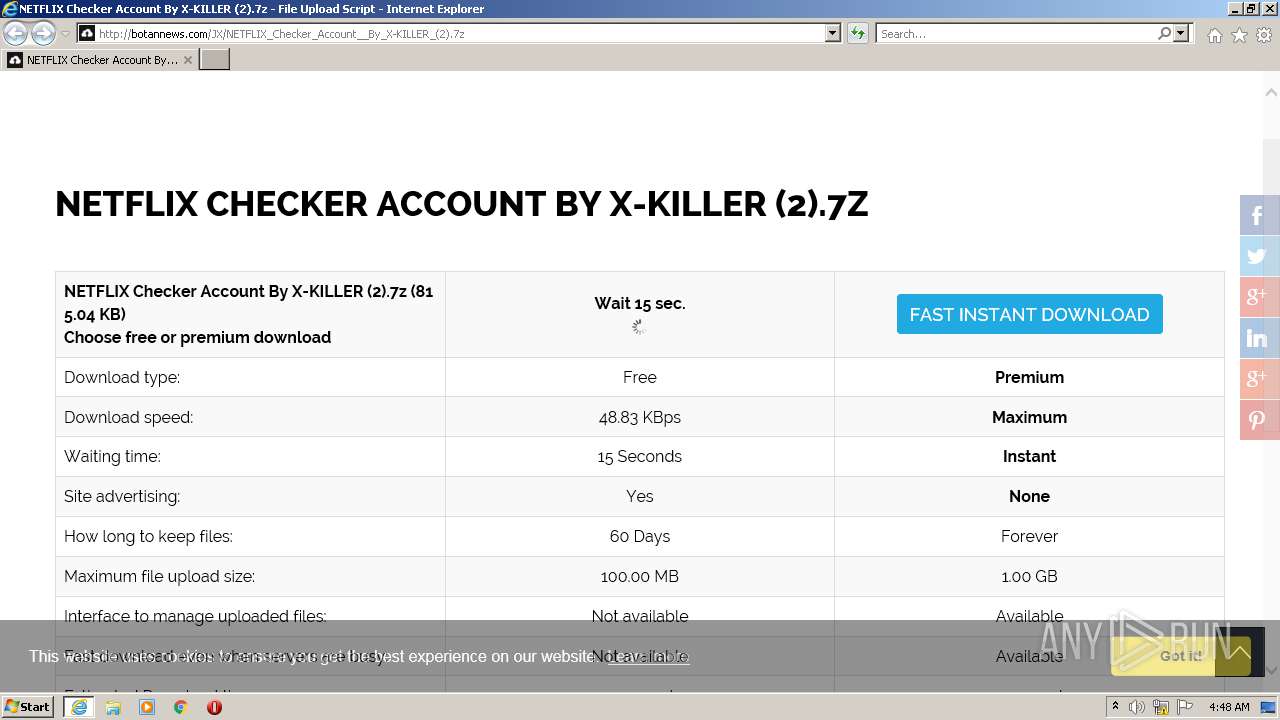
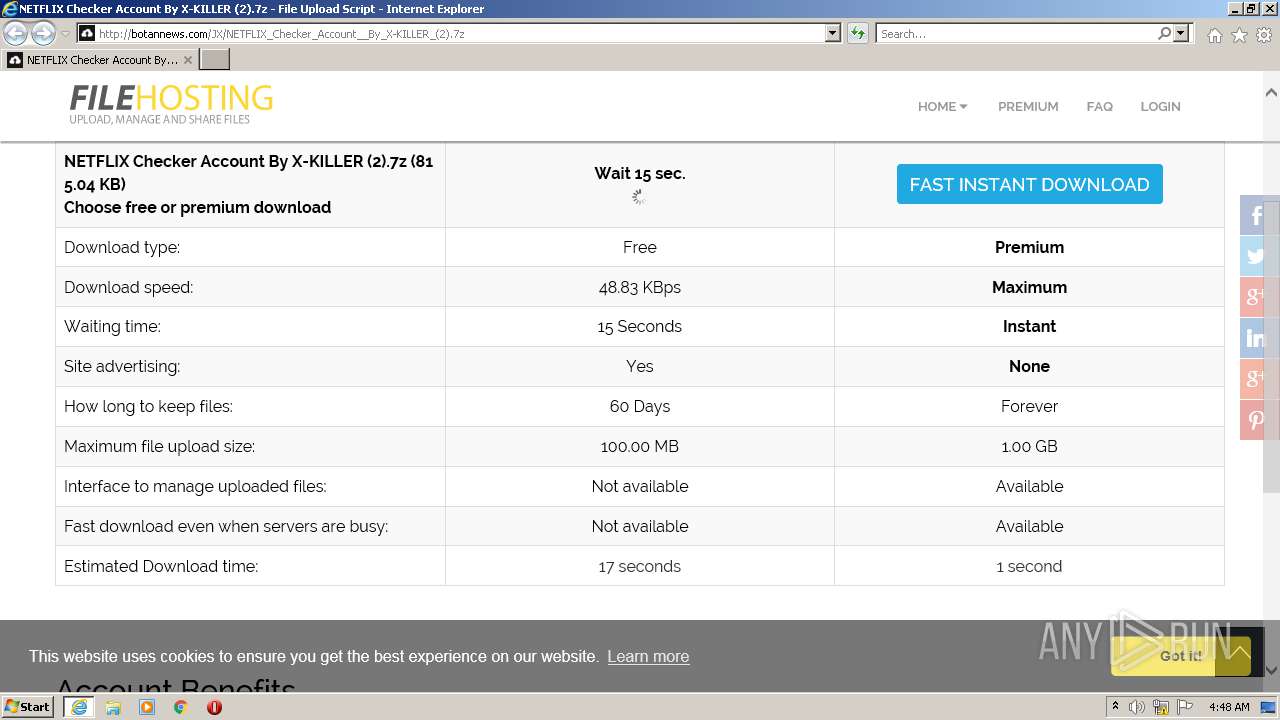
| URL: | http://botannews.com/JX/NETFLIX_Checker_Account__By_X-KILLER_(2).7z |
| Full analysis: | https://app.any.run/tasks/5afaa4bf-c195-430c-9d8d-5466f2a7315d |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2021, 04:48:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9595FF63642B0942CBE48CD4A19505FD |
| SHA1: | 42E7F4311F7BF24D8BD359216651C3775DD9305A |
| SHA256: | 59585C64E35769394FED01BE2E1EFEA72F35FE2901E330C60BA217515397F1AF |
| SSDEEP: | 3:N1Kcf/AlLGGlHcEKsQLRBGJ2Ls:CcwlUEjevG4Ls |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2732)
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2216)
Checks supported languages
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2216)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2216)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2216)
INFO
Reads the computer name
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 2732)
- iexplore.exe (PID: 572)
Checks supported languages
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2732)
- iexplore.exe (PID: 3276)
Creates files in the user directory
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2732)
- iexplore.exe (PID: 3276)
Checks Windows Trust Settings
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2732)
Reads settings of System Certificates
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2732)
Reads the date of Windows installation
- iexplore.exe (PID: 3276)
Application launched itself
- iexplore.exe (PID: 3276)
Changes internet zones settings
- iexplore.exe (PID: 3276)
Reads internet explorer settings
- iexplore.exe (PID: 2732)
- iexplore.exe (PID: 572)
Changes settings of System certificates
- iexplore.exe (PID: 3276)
Reads CPU info
- iexplore.exe (PID: 2732)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3276)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3276 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2216 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe� Flash� Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3276 CREDAT:2495751 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3276 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://botannews.com/JX/NETFLIX_Checker_Account__By_X-KILLER_(2).7z" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
47 403
Read events
47 049
Write events
350
Delete events
4
Modification events
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30926044 | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30926044 | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
43
Text files
147
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 572 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\KIFXNKAM.txt | text | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\NETFLIX_Checker_Account__By_X-KILLER_(2)[1].htm | html | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\All-stylesheets[1].css | text | |
MD5:0317F0C3C8EF4BFDA620908A7C05988B | SHA256:35E93B818DFF2F3AC20CE42E50D2A6EB9E7412605421DECAA95CA9BF604A9DBC | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\custom[1].css | text | |
MD5:76ABA44FECBC5383ABD385540997E4D7 | SHA256:AEE1473684074D8D262B2240921B5450F5D528948EE36741FEB42D63D6DD727D | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\socialsider-v1.0[1].css | text | |
MD5:615432B34216CE48AA41B027C9B08F6A | SHA256:F5AF895F7BEB65666327D0629ED30CEBE00DDDEBABBE9D25BE29106234E827A5 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\responsive[1].css | text | |
MD5:7F090C009C854FDA38795874DD7CFCF3 | SHA256:244C04A213BDB0E13F0D9FA71AF6760886AD9D533F80C1F60E21F632096F5E33 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\fonts[1].css | text | |
MD5:FDDCEFAAB6F97068221E3A5A903C049C | SHA256:61A41176D3175622252D5C00B2BAB632E4B35D8828380DC4C72DD5EFE3A53D73 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\bootstrap.min[1].css | text | |
MD5:C70437E19E8A82761F209A31509C031F | SHA256:4F8B8A42A8E86285E135EEA9FA46FEF3D5D60332A1C93C92DDEEFF328D56A132 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\file-upload[1].css | text | |
MD5:CB955FDB824B31E9B744B6AEF1F99DFE | SHA256:B6264C4C05C786E5215A5FA9FEB5A99A81C924BC26B3E962EEFF230750A2D134 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\jquery.tmpl.min[1].js | text | |
MD5:411DF7E2BC659D35015F7FDB7432B331 | SHA256:9509C1E67BEDBADED059D0AA8D5CEE65CEE3C9E3F43A5952A7A233CBC10810AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
105
TCP/UDP connections
131
DNS requests
56
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/JX/NETFLIX_Checker_Account__By_X-KILLER_(2).7z | US | html | 24.7 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/colors/flow.css | US | text | 579 b | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/custom.css | US | text | 3.22 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/fonts.css | US | text | 282 b | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/styles/cookieconsent.min.css | US | text | 1.15 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/bootstrap/bootstrap.min.css | US | text | 17.4 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/responsive.css | US | text | 1.14 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/rs-plugin/css/settings.css | US | text | 7.16 Kb | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/css/All-stylesheets.css | US | text | 180 b | malicious |
572 | iexplore.exe | GET | 200 | 172.67.200.29:80 | http://botannews.com/themes/flow/frontend_assets/socialsider-v1.0/_css/socialsider-v1.0.css | US | text | 4.00 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
572 | iexplore.exe | 172.67.200.29:80 | botannews.com | — | US | unknown |
572 | iexplore.exe | 104.21.68.54:443 | cdn.popmyads.com | Cloudflare Inc | US | unknown |
572 | iexplore.exe | 104.19.131.80:443 | jsc.adskeeper.co.uk | Cloudflare Inc | US | unknown |
572 | iexplore.exe | 104.20.229.67:443 | www.statcounter.com | Cloudflare Inc | US | unknown |
572 | iexplore.exe | 142.250.185.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
572 | iexplore.exe | 142.250.185.168:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
572 | iexplore.exe | 95.100.146.72:80 | ctldl.windowsupdate.com | Akamai Technologies, Inc. | — | suspicious |
572 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
572 | iexplore.exe | 172.67.187.188:443 | cdn.popmyads.com | — | US | unknown |
572 | iexplore.exe | 104.18.30.182:80 | ocsp.usertrust.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
botannews.com |
| malicious |
cdn.popmyads.com |
| malicious |
jsc.adskeeper.co.uk |
| whitelisted |
www.statcounter.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
popmyads.com |
| malicious |