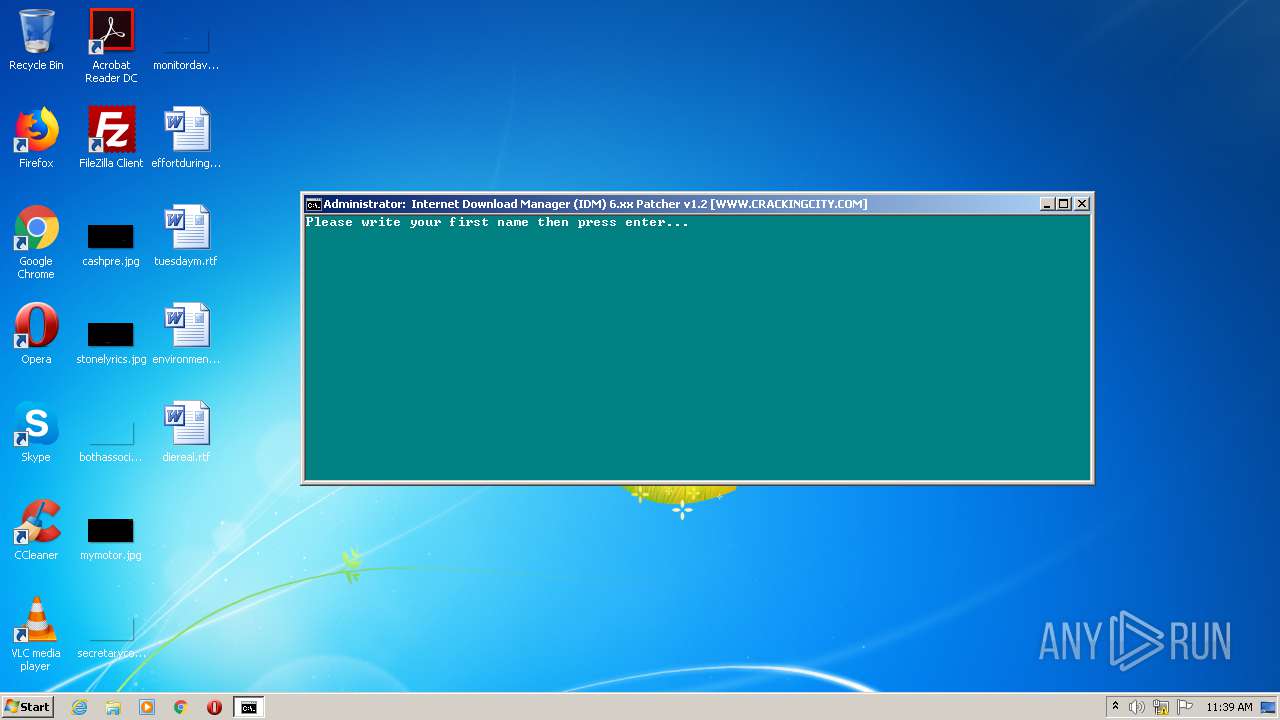
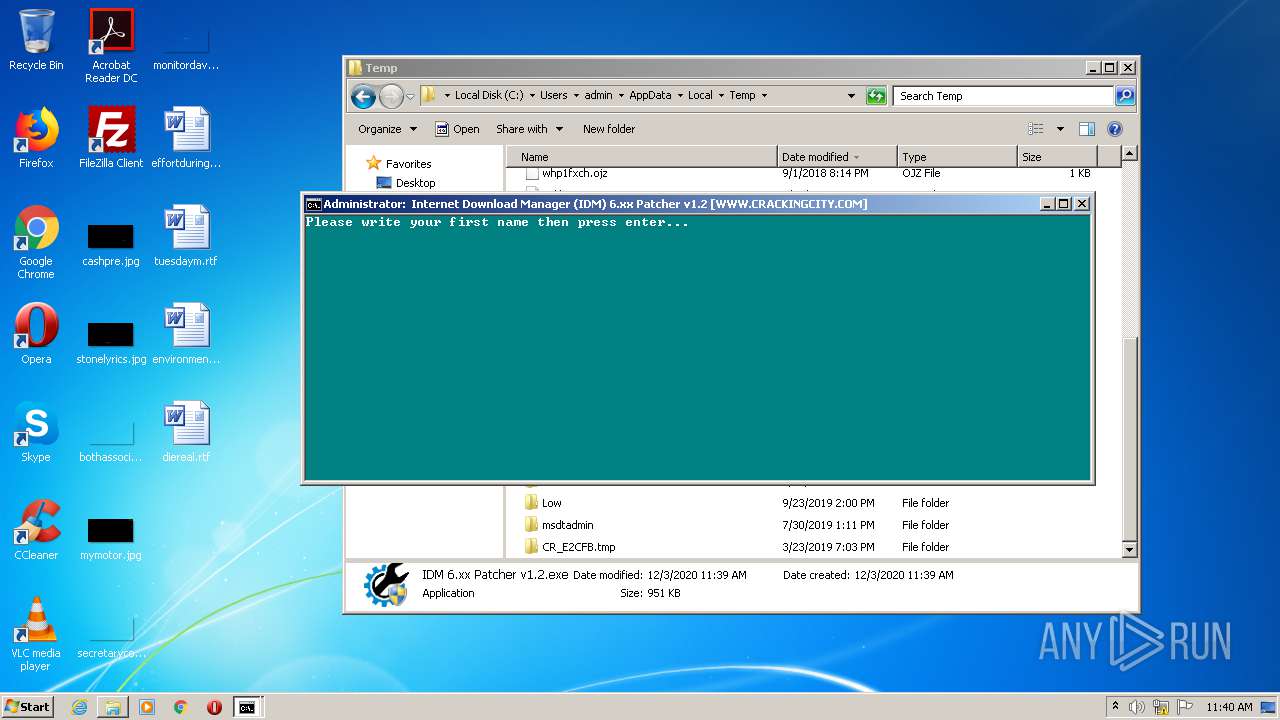
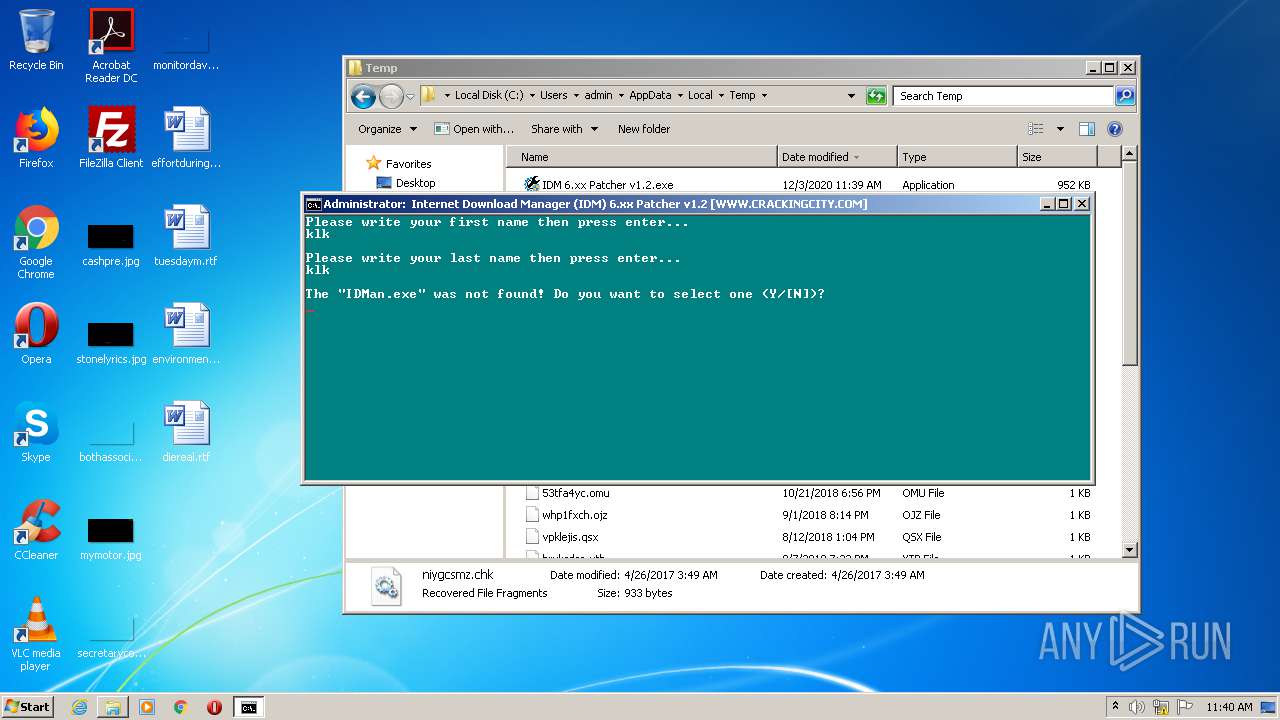
| File name: | IDM 6.xx Patcher v1.2.exe |
| Full analysis: | https://app.any.run/tasks/6b096f7f-639a-4b07-8063-d74a16a0101f |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2020, 11:39:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C4D04F1E549455F215BDFEE14C8B3649 |
| SHA1: | E3B5450B12FEAD30D3ABC04A31E1FD7AFD470C35 |
| SHA256: | 5953E4749144D30CA28C0462419DC8782467CC0F59536439DE8E487AF4DA7AF0 |
| SSDEEP: | 24576:32yQPrU0bkmtKK+w1xw/V6j6N3CjIFIDtppPEz:3pxlmtKS1xU5NyjCz |
MALICIOUS
Drops executable file immediately after starts
- IDM 6.xx Patcher v1.2.exe (PID: 2760)
- 7za.exe (PID: 3412)
- IDM 6.xx Patcher v1.2.exe (PID: 1396)
- 7za.exe (PID: 120)
- 7za.exe (PID: 3844)
Application was dropped or rewritten from another process
- 7za.exe (PID: 3820)
- 7za.exe (PID: 1592)
- 7za.exe (PID: 3412)
- AB2EF.exe (PID: 1916)
- AB2EF.exe (PID: 2684)
- AB2EF.exe (PID: 1848)
- AB2EF.exe (PID: 1504)
- AB2EF.exe (PID: 3480)
- AB2EF.exe (PID: 656)
- AB2EF.exe (PID: 2648)
- 7za.exe (PID: 1888)
- 7za.exe (PID: 120)
- AB2EF.exe (PID: 1956)
- 7za.exe (PID: 3556)
- 7za.exe (PID: 3844)
- AB2EF.exe (PID: 1248)
- AB2EF.exe (PID: 836)
- AB2EF.exe (PID: 3792)
- AB2EF.exe (PID: 3564)
Actions looks like stealing of personal data
- setup.exe (PID: 2988)
SUSPICIOUS
Executable content was dropped or overwritten
- IDM 6.xx Patcher v1.2.exe (PID: 2760)
- 7za.exe (PID: 3412)
- 7za.exe (PID: 120)
- IDM 6.xx Patcher v1.2.exe (PID: 1396)
- 7za.exe (PID: 3844)
Starts CMD.EXE for commands execution
- IDM 6.xx Patcher v1.2.exe (PID: 2760)
- cmd.exe (PID: 2840)
- IDM 6.xx Patcher v1.2.exe (PID: 1396)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2740)
- cmd.exe (PID: 3584)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2840)
- cmd.exe (PID: 2756)
- cmd.exe (PID: 2952)
- cmd.exe (PID: 1204)
- cmd.exe (PID: 2196)
Application launched itself
- cmd.exe (PID: 2840)
- setup.exe (PID: 2988)
- chrmstp.exe (PID: 1340)
Executed via COM
- DllHost.exe (PID: 2200)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3536)
INFO
Reads CPU info
- reg.exe (PID: 3452)
- reg.exe (PID: 1840)
- reg.exe (PID: 1844)
- reg.exe (PID: 2968)
Manual execution by user
- explorer.exe (PID: 2724)
- IDM 6.xx Patcher v1.2.exe (PID: 3360)
- IDM 6.xx Patcher v1.2.exe (PID: 1396)
- setup.exe (PID: 2988)
Reads the hosts file
- chrome.exe (PID: 3536)
- chrome.exe (PID: 3944)
Reads settings of System Certificates
- chrome.exe (PID: 3944)
Application launched itself
- chrome.exe (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:06:27 09:06:38+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 70656 |
| InitializedDataSize: | 110080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11def |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.0 |
| ProductVersionNumber: | 1.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | IDM 6.xx Patcher - CrackingCity.com |
| CompanyName: | CrackingCity.com |
| FileDescription: | IDM 6.xx Patcher |
| FileVersion: | 1.2.0.0 |
| InternalName: | IDM 6.xx Patcher.exe |
| LegalCopyright: | Copyright © 2020 CrackingCity.com |
| OriginalFileName: | IDM 6.xx Patcher.exe |
| ProductName: | IDM 6.xx Patcher |
| ProductVersion: | 1.2.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Jun-2010 07:06:38 |
| Detected languages: |
|
| Comments: | IDM 6.xx Patcher - CrackingCity.com |
| CompanyName: | CrackingCity.com |
| FileDescription: | IDM 6.xx Patcher |
| FileVersion: | 1.2.0.0 |
| InternalName: | IDM 6.xx Patcher.exe |
| LegalCopyright: | Copyright © 2020 CrackingCity.com |
| OriginalFilename: | IDM 6.xx Patcher.exe |
| ProductName: | IDM 6.xx Patcher |
| ProductVersion: | 1.2.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0060 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000060 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 27-Jun-2010 07:06:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00011317 | 0x00011400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.57699 |
.rdata | 0x00013000 | 0x000030EA | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.54943 |
.data | 0x00017000 | 0x0000292C | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.65832 |
.rsrc | 0x0001A000 | 0x000172AB | 0x00017400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.74767 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.04909 | 635 | Latin 1 / Western European | English - United States | RT_MANIFEST |
101 | 1.98048 | 20 | Latin 1 / Western European | Russian - Russia | RT_GROUP_ICON |
Imports
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
187
Monitored processes
135
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | 7za e files.tmp -pidm@idm420 -aoa "AB2EF.exe" | C:\Users\admin\AppData\Local\Temp\ytmp\7za.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,5418038833942737830,15884998154230182879,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3399280466481441710 --mojo-platform-channel-handle=4460 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,5418038833942737830,15884998154230182879,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7295229888731768727 --mojo-platform-channel-handle=4220 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 576 | FIND /I "ppd" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | AB2EF g93Xcv53d5 | C:\Users\admin\AppData\Local\Temp\ytmp\AB2EF.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,5418038833942737830,15884998154230182879,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8707541827704454370 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2240 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 836 | AB2EF j6NM4Cxfv3 | C:\Users\admin\AppData\Local\Temp\ytmp\AB2EF.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,5418038833942737830,15884998154230182879,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8466759266231068093 --mojo-platform-channel-handle=3468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 960 | ATTRIB -S +H . | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,5418038833942737830,15884998154230182879,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5198156819351597983 --mojo-platform-channel-handle=4044 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 930
Read events
1 746
Write events
173
Delete events
11
Modification events
| (PID) Process: | (2760) IDM 6.xx Patcher v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2760) IDM 6.xx Patcher v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1396) IDM 6.xx Patcher v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1396) IDM 6.xx Patcher v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2988) setup.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | InstallerProgress |
Value: 18 | |||
| (PID) Process: | (2988) setup.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | InstallerResult |
Value: 1 | |||
| (PID) Process: | (2988) setup.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | InstallerError |
Value: 3 | |||
| (PID) Process: | (2988) setup.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | InstallerResultUIString |
Value: Google Chrome is already installed for all users on your computer. | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
Executable files
5
Suspicious files
20
Text files
859
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FC8CEB7-DD0.pma | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2988 | setup.exe | C:\Users\admin\AppData\Local\Temp\chrome_installer.log | text | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 2760 | IDM 6.xx Patcher v1.2.exe | C:\Users\admin\AppData\Local\Temp\ytmp\files.tmp | compressed | |
MD5:56517AB77352D7F115455B4FD4F04507 | SHA256:0DC7798D72C83369418CE7BC38B55D8DB7FE02679E81DE31D43E38B212686921 | |||
| 3412 | 7za.exe | C:\Users\admin\AppData\Local\Temp\ytmp\AB2EF.exe | executable | |
MD5:8CF23FA804804EB416F7F395D5F0647F | SHA256:C69B39AD2739DAB03DBEE316BB9B921883AA8880A4E4E9BDDE7723E75A178B21 | |||
| 2988 | setup.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3820 | 7za.exe | C:\Users\admin\AppData\Local\Temp\ytmp\IDM0.bat | text | |
MD5:69C3EDFE8C7003F905F19969922D2626 | SHA256:D90A40FCEF70925252CAF6722C29E95C4B904A19771E6E60AB39F00B161B8464 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3944 | chrome.exe | GET | 200 | 159.148.69.142:80 | http://r3---sn-a5uoxu-gpme.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=159.148.186.185&mm=28&mn=sn-a5uoxu-gpme&ms=nvh&mt=1606995381&mv=m&mvi=3&pl=24&shardbypass=yes | LV | crx | 293 Kb | whitelisted |
3944 | chrome.exe | GET | 200 | 159.148.69.142:80 | http://r3---sn-a5uoxu-gpme.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=159.148.186.185&mm=28&mn=sn-a5uoxu-gpme&ms=nvh&mt=1606995381&mv=m&mvi=3&pcm2cms=yes&pl=24&shardbypass=yes | LV | crx | 293 Kb | whitelisted |
3944 | chrome.exe | GET | 302 | 108.177.14.138:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 527 b | whitelisted |
3944 | chrome.exe | GET | 302 | 108.177.14.138:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 543 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3944 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 216.58.206.1:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 108.177.14.138:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 159.148.69.142:80 | r3---sn-a5uoxu-gpme.gvt1.com | LATNET SERVISS Ltd. | LV | whitelisted |
3944 | chrome.exe | 172.217.16.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 64.233.165.138:443 | clients2.google.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 216.58.212.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3944 | chrome.exe | 64.233.165.100:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r3---sn-a5uoxu-gpme.gvt1.com |
| whitelisted |
www.gstatic.com |
| whitelisted |