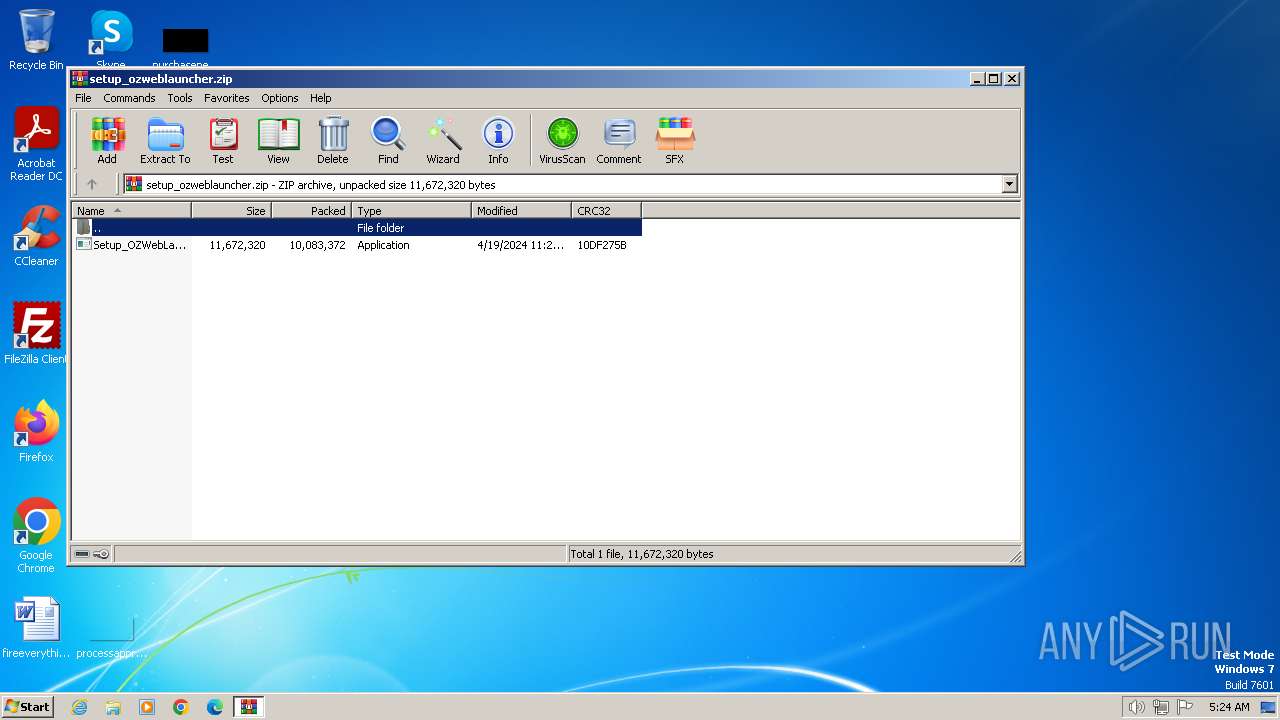
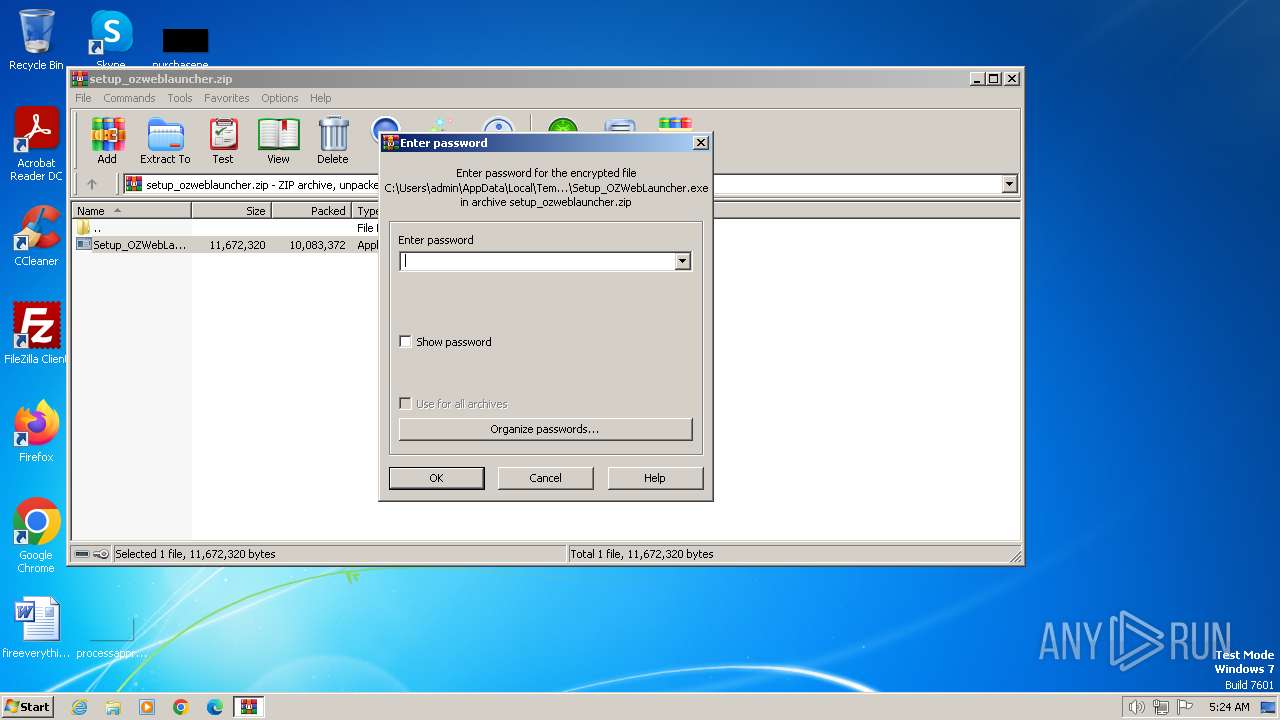
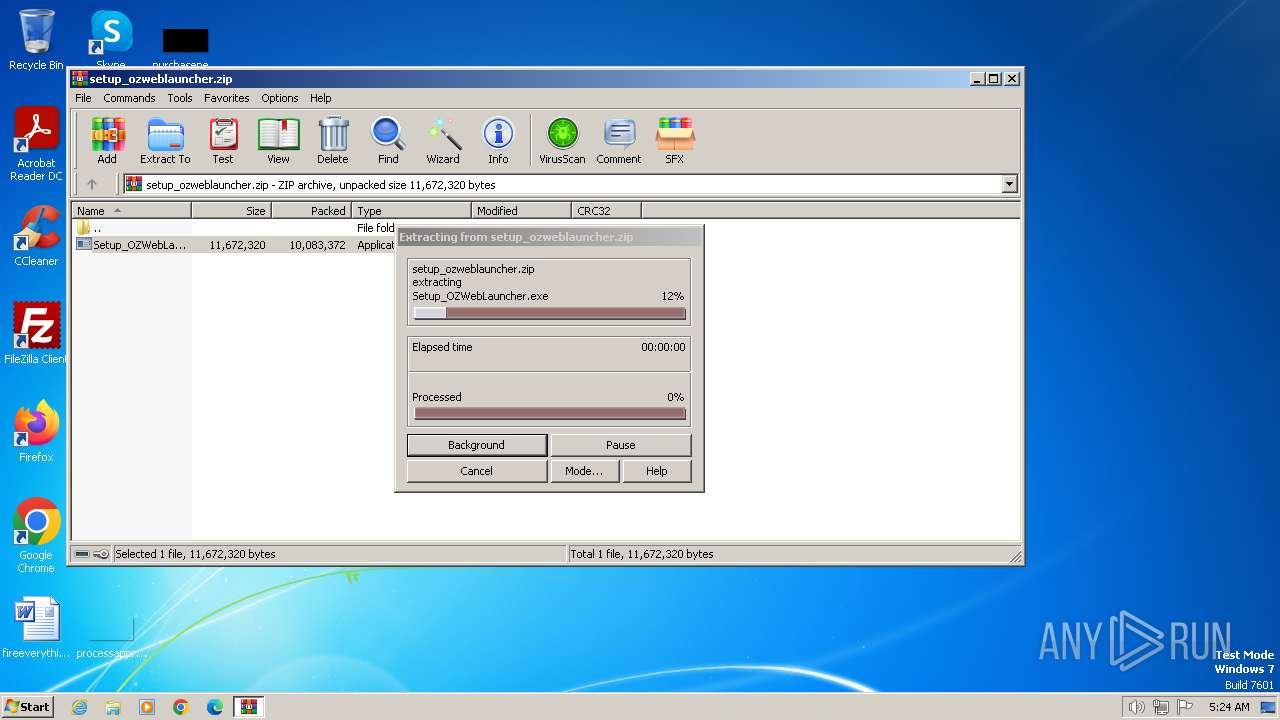
| File name: | setup_ozweblauncher.zip |
| Full analysis: | https://app.any.run/tasks/7792cfdc-988d-4a4d-bf6b-b0f763f18aef |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2024, 04:24:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5238D5CECB37D4F81EB10CE8940FFF46 |
| SHA1: | FFBEE137723E282E199F2BE9A0535975F26B9819 |
| SHA256: | 593DF85A798529F77F78F53B1941C3FDB63964F9E585E3D100854E32466CE101 |
| SSDEEP: | 98304:hchZvTLlQC54F+AQhJhwPEt9NLgb301RlhbT6PScR3vU3lhueHUNHT5la1hKQLBS:mE6VW9w6xb3tMtvIbRJp |
MALICIOUS
Drops the executable file immediately after the start
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
Create files in the Startup directory
- setup.exe (PID: 3968)
Registers / Runs the DLL via REGSVR32.EXE
- setup.exe (PID: 3968)
- cmd.exe (PID: 1308)
Creates a writable file in the system directory
- OZWebLauncherUtil.exe (PID: 3536)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1288)
- OZWebLauncher.exe (PID: 2036)
Executable content was dropped or overwritten
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
Searches for installed software
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
Process drops legitimate windows executable
- setup.exe (PID: 3968)
Reads the Windows owner or organization settings
- setup.exe (PID: 3968)
Executes as Windows Service
- VSSVC.exe (PID: 3604)
- OZWLService.exe (PID: 3716)
Creates a software uninstall entry
- setup.exe (PID: 3968)
Adds/modifies Windows certificates
- setup.exe (PID: 3968)
- OZWebLauncherUtil.exe (PID: 3536)
Creates/Modifies COM task schedule object
- setup.exe (PID: 3968)
- regsvr32.exe (PID: 2240)
- regsvr32.exe (PID: 1336)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2244)
Executing commands from a ".bat" file
- setup.exe (PID: 3968)
Starts CMD.EXE for commands execution
- setup.exe (PID: 3968)
Uses TIMEOUT.EXE to delay execution
- setup.exe (PID: 3968)
Reads settings of System Certificates
- OZWebLauncher.exe (PID: 2036)
Reads the Internet Settings
- OZWebLauncher.exe (PID: 2036)
Checks Windows Trust Settings
- OZWebLauncher.exe (PID: 2036)
- OZWebLauncherUtil.exe (PID: 3536)
INFO
Reads the computer name
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
- OZWebLauncherUtil.exe (PID: 3536)
- OZWLService.exe (PID: 3716)
- OZWebLauncher.exe (PID: 2036)
Checks supported languages
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
- CloseOZWLBridge.exe (PID: 1428)
- CloseOZWebLauncher.exe (PID: 884)
- OZWLService.exe (PID: 3716)
- OZWebLauncherUtil.exe (PID: 3536)
- OZWebLauncher.exe (PID: 2036)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1288)
Create files in a temporary directory
- Setup_OZWebLauncher.exe (PID: 2880)
- setup.exe (PID: 3968)
- OZWebLauncher.exe (PID: 2036)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1288)
Reads the machine GUID from the registry
- setup.exe (PID: 3968)
- OZWebLauncher.exe (PID: 2036)
- OZWebLauncherUtil.exe (PID: 3536)
Creates files in the program directory
- setup.exe (PID: 3968)
- OZWebLauncherUtil.exe (PID: 3536)
Creates files or folders in the user directory
- OZWebLauncher.exe (PID: 2036)
Reads the software policy settings
- OZWebLauncher.exe (PID: 2036)
- OZWebLauncherUtil.exe (PID: 3536)
Reads Environment values
- OZWebLauncherUtil.exe (PID: 3536)
Manual execution by a user
- chrome.exe (PID: 1692)
Application launched itself
- chrome.exe (PID: 1692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:04:19 11:26:40 |
| ZipCRC: | 0x10df275b |
| ZipCompressedSize: | 10083372 |
| ZipUncompressedSize: | 11672320 |
| ZipFileName: | Setup_OZWebLauncher.exe |
Total processes
71
Monitored processes
29
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | C:\Users\admin\AppData\Local\Temp\{ED9184D2-D034-4323-9DEE-DBA7D0441A7F}\{E57AA2E7-1A7E-47FB-B362-ED04768595E6}\CloseOZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{ED9184D2-D034-4323-9DEE-DBA7D0441A7F}\{E57AA2E7-1A7E-47FB-B362-ED04768595E6}\CloseOZWebLauncher.exe | — | setup.exe | |||||||||||
User: admin Company: TODO: <회사 이름> Integrity Level: HIGH Description: TODO: <파일 설명> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 980 | C:\Windows\system32\regsvr32 /s /uC:\Windows\ZTransferXUAC.dll | C:\Windows\System32\regsvr32.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3644 --field-trial-handle=1156,i,1786019637717392424,1371263885751024320,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1288 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\setup_ozweblauncher.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1308 | C:\Windows\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\{ED9184D2-D034-4323-9DEE-DBA7D0441A7F}\{E57AA2E7-1A7E-47FB-B362-ED04768595E6}\ZTransferXUAC.bat /s /v/q | C:\Windows\System32\cmd.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1336 | regsvr32 /s c:\Windows\ZTransferXUAC.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1428 | C:\Users\admin\AppData\Local\Temp\{ED9184D2-D034-4323-9DEE-DBA7D0441A7F}\{E57AA2E7-1A7E-47FB-B362-ED04768595E6}\CloseOZWLBridge.exe | C:\Users\admin\AppData\Local\Temp\{ED9184D2-D034-4323-9DEE-DBA7D0441A7F}\{E57AA2E7-1A7E-47FB-B362-ED04768595E6}\CloseOZWLBridge.exe | — | setup.exe | |||||||||||
User: admin Company: TODO: <회사 이름> Integrity Level: HIGH Description: TODO: <파일 설명> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2152 --field-trial-handle=1156,i,1786019637717392424,1371263885751024320,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\FORCS\OZWebLauncher\OZWebLauncher.exe" | C:\Program Files\FORCS\OZWebLauncher\OZWebLauncher.exe | OZWLService.exe | ||||||||||||
User: admin Company: forcs Integrity Level: HIGH Description: OZWebLauncher (2011) Version: 80.2022.0304.100 Modules
| |||||||||||||||
Total events
21 025
Read events
20 650
Write events
350
Delete events
25
Modification events
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\setup_ozweblauncher.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
41
Suspicious files
24
Text files
41
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\0x0411.ini | text | |
MD5:831FE6D667B6F53826290536C987FE2B | SHA256:9E6D74A5CD777C12767959CD684A5A277930FC6FB109A0641E8D65570A7422D2 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\0x0412.ini | text | |
MD5:73E70A6B9354E80237C8E2B3170830A0 | SHA256:316577CF74D3545D632B0DE55513A3511D654849655157CB84821B871EC081E9 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\layout.bin | binary | |
MD5:82A5F1DF136EDF55A1D372955F21D9E2 | SHA256:A5261C521DA4FD32BF5A1DAB06F0FFF23274C49FE1CD6E5355FBD004FFAD9CE1 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\data1.hdr | compressed | |
MD5:B8FDE6DB13E1116AA10C8CD80FAC0B18 | SHA256:166BBD648860E9DE5E55F43C8F82E91F1EBAEABE60E0D81B716D985668DAE33B | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\ISSetup.dll | — | |
MD5:40FEFC3D907D44A9ADC84475AB073A6E | SHA256:C51699CBF0B433C4F7B687C8520192AD5EA519214BFDE6732453FF194BC2FFD9 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\setup.exe | executable | |
MD5:8FAD4D62044E0378AB6CD05999C67603 | SHA256:E3D12B06193727FC504BF418D4C18D89853C7AA7E5FED668E5CCA24BECC94179 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\setup.ini | text | |
MD5:9D52A282131FF272712BD5BA4B800EC1 | SHA256:9BF8191859390A998D26F7DB3CEF636C13A3EA152848071C118252AC73CACF1E | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\setup.ini | text | |
MD5:9D52A282131FF272712BD5BA4B800EC1 | SHA256:9BF8191859390A998D26F7DB3CEF636C13A3EA152848071C118252AC73CACF1E | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\0x0409.ini | — | |
MD5:8586214463BD73E1C2716113E5BD3E13 | SHA256:089D3068E42958DD2C0AEC668E5B7E57B7584ACA5C77132B1BCBE3A1DA33EF54 | |||
| 2880 | Setup_OZWebLauncher.exe | C:\Users\admin\AppData\Local\Temp\{F93C0026-BF84-41B3-AC71-E8E8B96F3C21}\Disk1\setup.inx | binary | |
MD5:67DDB774D7DA627B84F198B42E8CC7BE | SHA256:136EAB3DBE5C0B6E23CA5BF55D6D6DED343AF96122EDCA9A4C8C81F8D5C4375D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
12
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3536 | OZWebLauncherUtil.exe | GET | 304 | 2.22.242.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?06897c3a7da52b10 | unknown | — | — | unknown |
3536 | OZWebLauncherUtil.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
3536 | OZWebLauncherUtil.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAYSDigr%2FWlJJvJK0SS5VDM%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3536 | OZWebLauncherUtil.exe | 2.22.242.105:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3536 | OZWebLauncherUtil.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1692 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2792 | chrome.exe | 142.250.186.100:443 | www.google.com | GOOGLE | US | whitelisted |
2792 | chrome.exe | 142.250.184.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2792 | chrome.exe | 74.125.206.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
update.googleapis.com |
| unknown |
Threats
Process | Message |
|---|---|
OZWebLauncher.exe | OZWebLauncher.exe Information: 0 : |
OZWebLauncher.exe | OZWebLauncher.exe Warning: 0 : |
OZWebLauncher.exe | 4/19/2024 5:25:13 AM : Web root: C:\Program Files\FORCS\OZWebLauncher\
|
OZWebLauncher.exe | 4/19/2024 5:25:13 AM : Webroot folder not found. Using application base directory: C:\Program Files\FORCS\OZWebLauncher\
|
OZWebLauncherUtil.exe | 4/19/2024 5:25:13 AM : Web root: C:\Program Files\FORCS\OZWebLauncher\
|
OZWebLauncherUtil.exe | 4/19/2024 5:25:13 AM : Webroot folder not found. Using application base directory: C:\Program Files\FORCS\OZWebLauncher\
|
OZWebLauncherUtil.exe | OZWebLauncherUtil.exe Warning: 0 : |
OZWebLauncherUtil.exe | OZWebLauncherUtil.exe Information: 0 : |