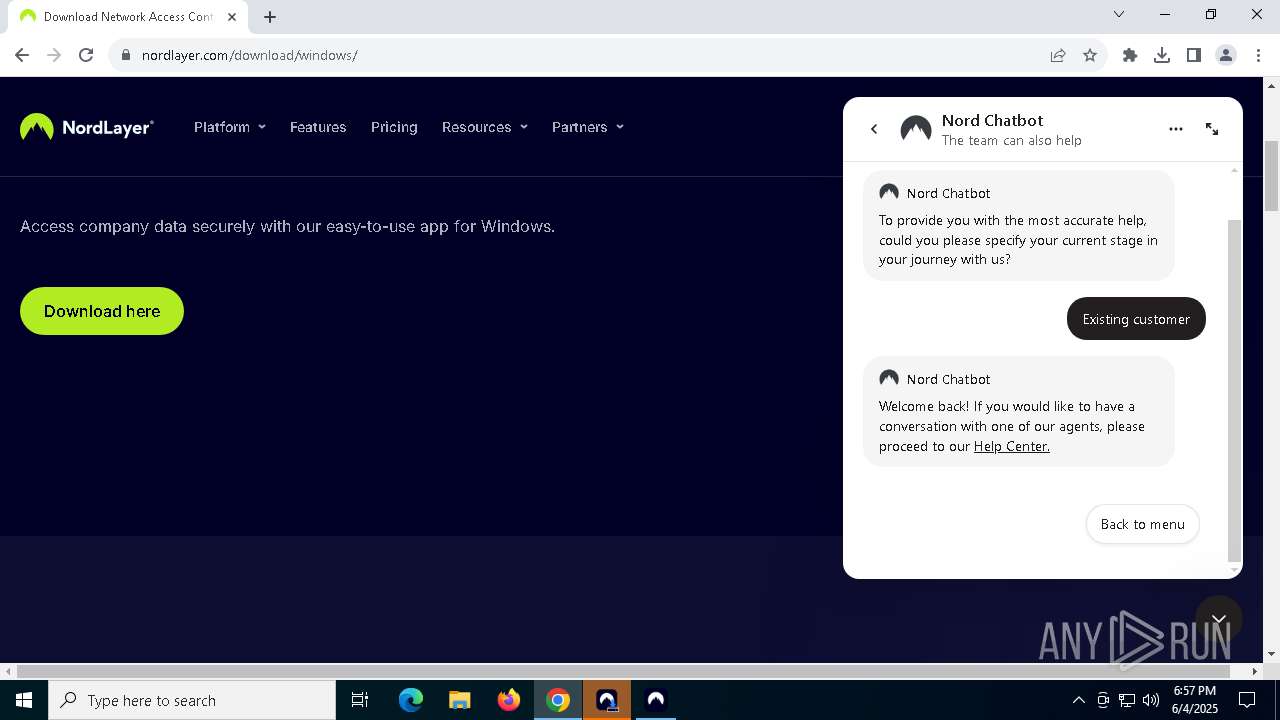
| URL: | https://nordlayer.com/download/macos/ |
| Full analysis: | https://app.any.run/tasks/9f94233b-0ae8-4fc4-bac8-10e99416f004 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 18:55:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 18B4B55A44F9AD07B26659C1D415057B |
| SHA1: | 859ED6737E4FB469E7581D671DCAFF3242625199 |
| SHA256: | 593254E9911A3DB510576F32762FF937D7482670BCCCDD5F611FC8B3925E1150 |
| SSDEEP: | 3:N8KEtKL5T:2ftKVT |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 7268)
- msiexec.exe (PID: 3036)
- msiexec.exe (PID: 8108)
Bypass execution policy to execute commands
- powershell.exe (PID: 1284)
- powershell.exe (PID: 7520)
- powershell.exe (PID: 7848)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 760)
- powershell.exe (PID: 1056)
- powershell.exe (PID: 8036)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 8080)
- powershell.exe (PID: 8228)
- powershell.exe (PID: 7204)
Starts Visual C# compiler
- powershell.exe (PID: 6572)
SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- NordLayerSetup.exe (PID: 7544)
Adds/modifies Windows certificates
- NordLayerSetup.exe (PID: 7544)
Reads security settings of Internet Explorer
- NordLayerSetup.exe (PID: 7544)
- vc_redist.x64.exe (PID: 8180)
Reads the Windows owner or organization settings
- NordLayerSetup.exe (PID: 7544)
Executable content was dropped or overwritten
- NordLayerSetup.exe (PID: 7544)
- vc_redist.x64.exe (PID: 8180)
- vc_redist.x64.exe (PID: 472)
- VC_redist.x64.exe (PID: 4040)
- VC_redist.x64.exe (PID: 864)
- NordLayerSetup.exe (PID: 1764)
- NordLayerSetup.exe (PID: 2316)
- VC_redist.x64.exe (PID: 132)
- csc.exe (PID: 3176)
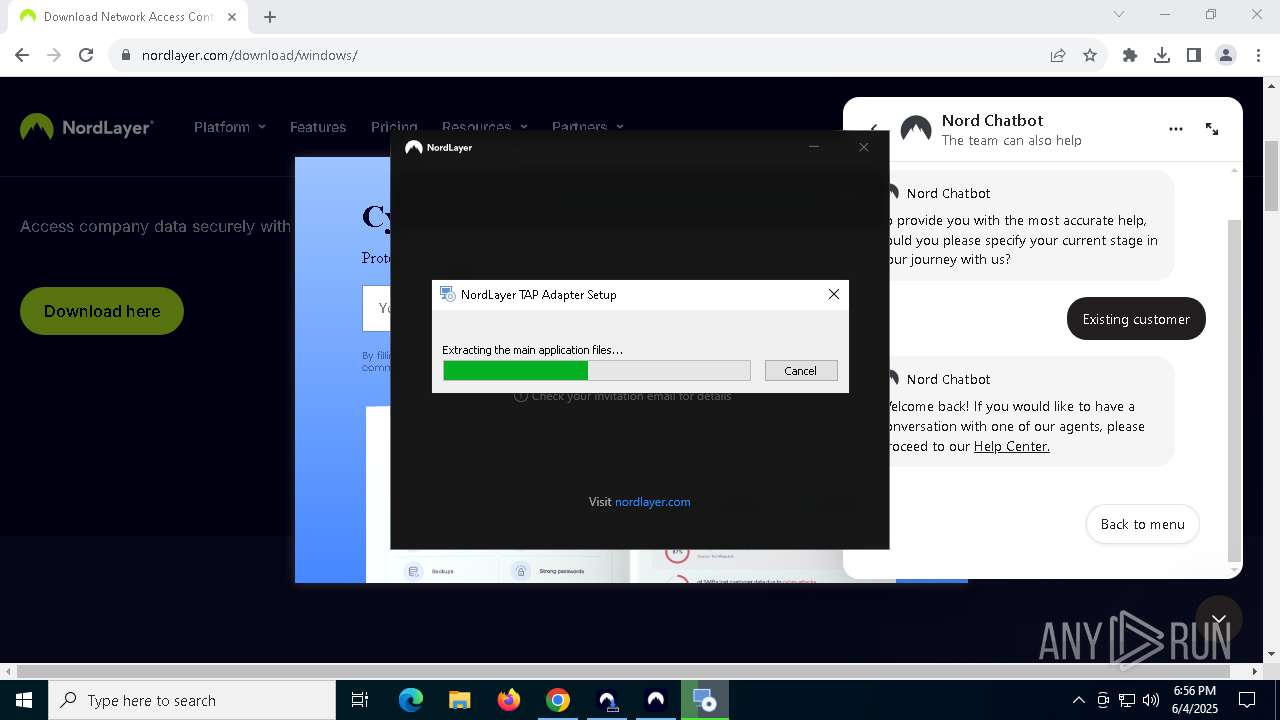
- NordLayerTapAdapterSetup.exe (PID: 7512)
- rundll32.exe (PID: 5428)
- drvinst.exe (PID: 8160)
- drvinst.exe (PID: 4284)
- devcon.exe (PID: 1056)
Process drops legitimate windows executable
- NordLayerSetup.exe (PID: 7544)
- vc_redist.x64.exe (PID: 8180)
- vc_redist.x64.exe (PID: 472)
- VC_redist.x64.exe (PID: 4040)
- msiexec.exe (PID: 656)
- msiexec.exe (PID: 5624)
- NordLayerSetup.exe (PID: 2316)
- VC_redist.x64.exe (PID: 132)
- NordLayerTapAdapterSetup.exe (PID: 7512)
- msiexec.exe (PID: 8108)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 8180)
- VC_redist.x64.exe (PID: 4040)
Starts itself from another location
- vc_redist.x64.exe (PID: 8180)
Searches for installed software
- vc_redist.x64.exe (PID: 8180)
- dllhost.exe (PID: 6644)
Detects AdvancedInstaller (YARA)
- NordLayerSetup.exe (PID: 7544)
The process drops C-runtime libraries
- msiexec.exe (PID: 656)
Application launched itself
- VC_redist.x64.exe (PID: 5376)
- VC_redist.x64.exe (PID: 864)
- NordLayerSetup.exe (PID: 7544)
Executes as Windows Service
- VSSVC.exe (PID: 8088)
- NordLayer.Service.exe (PID: 7136)
There is functionality for taking screenshot (YARA)
- NordLayerSetup.exe (PID: 7544)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 7268)
- msiexec.exe (PID: 3036)
- msiexec.exe (PID: 8108)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 3036)
- msiexec.exe (PID: 7268)
- msiexec.exe (PID: 8108)
The process executes Powershell scripts
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 7268)
- msiexec.exe (PID: 3036)
- msiexec.exe (PID: 8108)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 7268)
- msiexec.exe (PID: 3036)
- msiexec.exe (PID: 8108)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 656)
- msiexec.exe (PID: 8108)
- devcon.exe (PID: 1056)
- drvinst.exe (PID: 4284)
- drvinst.exe (PID: 8160)
- rundll32.exe (PID: 5428)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 656)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3176)
Uses .NET C# to load dll
- powershell.exe (PID: 6572)
INFO
Application launched itself
- chrome.exe (PID: 6988)
- msedge.exe (PID: 8416)
Creates files in the program directory
- NordLayerSetup.exe (PID: 7544)
Reads Environment values
- NordLayerSetup.exe (PID: 7544)
- msiexec.exe (PID: 8060)
Checks supported languages
- NordLayerSetup.exe (PID: 7544)
- msiexec.exe (PID: 656)
- msiexec.exe (PID: 8060)
- vc_redist.x64.exe (PID: 8180)
- VC_redist.x64.exe (PID: 4040)
- vc_redist.x64.exe (PID: 472)
Reads the computer name
- NordLayerSetup.exe (PID: 7544)
- msiexec.exe (PID: 656)
- msiexec.exe (PID: 8060)
- vc_redist.x64.exe (PID: 472)
- vc_redist.x64.exe (PID: 8180)
- VC_redist.x64.exe (PID: 4040)
Reads the machine GUID from the registry
- NordLayerSetup.exe (PID: 7544)
Checks proxy server information
- NordLayerSetup.exe (PID: 7544)
Executable content was dropped or overwritten
- chrome.exe (PID: 6988)
- msiexec.exe (PID: 656)
- msiexec.exe (PID: 5624)
- msiexec.exe (PID: 8108)
Creates files or folders in the user directory
- NordLayerSetup.exe (PID: 7544)
Reads the software policy settings
- NordLayerSetup.exe (PID: 7544)
Create files in a temporary directory
- NordLayerSetup.exe (PID: 7544)
- vc_redist.x64.exe (PID: 8180)
The sample compiled with english language support
- NordLayerSetup.exe (PID: 7544)
- vc_redist.x64.exe (PID: 472)
- vc_redist.x64.exe (PID: 8180)
- VC_redist.x64.exe (PID: 4040)
- msiexec.exe (PID: 656)
- VC_redist.x64.exe (PID: 864)
- msiexec.exe (PID: 5624)
- NordLayerSetup.exe (PID: 1764)
- NordLayerSetup.exe (PID: 2316)
- VC_redist.x64.exe (PID: 132)
- NordLayerTapAdapterSetup.exe (PID: 7512)
- msiexec.exe (PID: 8108)
- devcon.exe (PID: 1056)
- drvinst.exe (PID: 4284)
- drvinst.exe (PID: 8160)
- rundll32.exe (PID: 5428)
Process checks computer location settings
- vc_redist.x64.exe (PID: 8180)
- NordLayerSetup.exe (PID: 7544)
Manages system restore points
- SrTasks.exe (PID: 6572)
- SrTasks.exe (PID: 6668)
Starts application with an unusual extension
- msiexec.exe (PID: 656)
Manual execution by a user
- msedge.exe (PID: 8416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
257
Monitored processes
110
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -q -burn.elevated BurnPipe.{4175DB16-5C47-4C72-9EEC-96EC04D9CCA3} {0F6A8873-FAA6-4F31-B94F-4812B4811EAB} 864 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6568 --field-trial-handle=2524,i,16702338173470865630,18055413870777548874,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
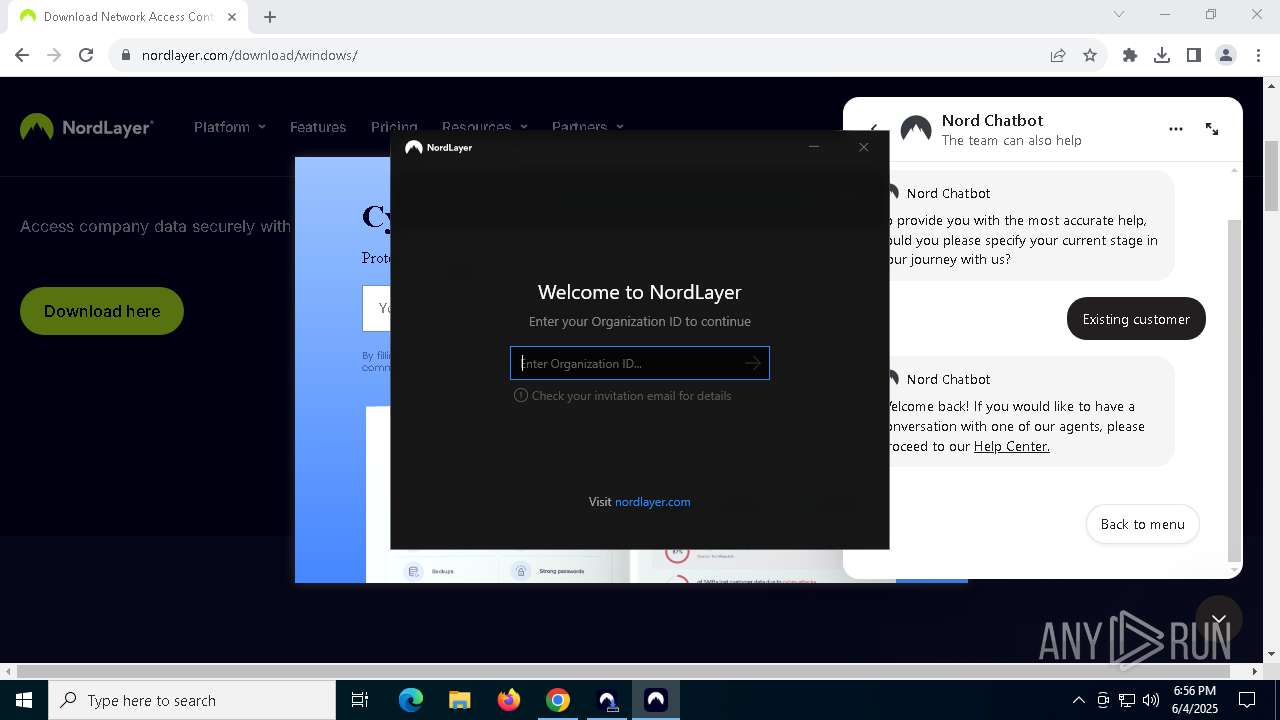
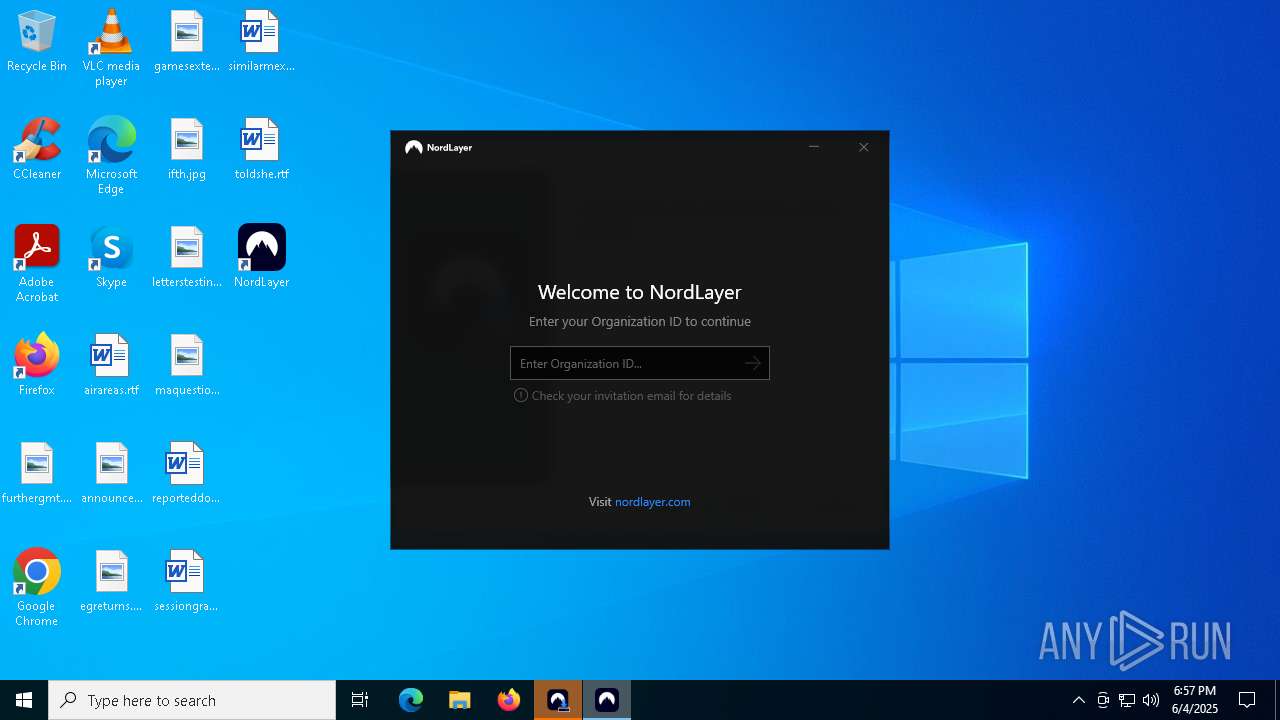
| 232 | "C:\Users\admin\Downloads\NordLayerSetup.exe" | C:\Users\admin\Downloads\NordLayerSetup.exe | — | chrome.exe | |||||||||||
User: admin Company: NordLayer Integrity Level: MEDIUM Description: NordLayer Installer Exit code: 3221226540 Version: 3.5.2.0 Modules
| |||||||||||||||
| 472 | "C:\ProgramData\NordLayer\Install\prerequisites\Visual C++ Redistributable\vc_redist.x64.exe" /quiet /norestart | C:\ProgramData\NordLayer\Install\prerequisites\Visual C++ Redistributable\vc_redist.x64.exe | NordLayerSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.44.35208 Exit code: 3010 Version: 14.44.35208.0 Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 656 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss3D19.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi3D16.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr3D17.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr3D18.txt" -propSep " :<->: " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.clean.room="C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.filehandle.attached=532 -burn.filehandle.self=552 -uninstall -quiet -burn.related.upgrade -burn.ancestors={9387bec2-2f2b-48d1-a0ce-692c5df7042d} -burn.filehandle.self=1220 -burn.embedded BurnPipe.{F931BC3F-207C-4BCE-A454-CD7C79A4BCFD} {D5327989-0D01-4E7D-ABDD-6EFF7CAAD26F} 4040 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 924 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | /minimized | C:\Program Files (x86)\NordLayer\NordLayer.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: NordLayer Version: 3.5.2 Modules
| |||||||||||||||
Total events
135 516
Read events
133 826
Write events
1 251
Delete events
439
Modification events
| (PID) Process: | (6988) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6988) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6988) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6988) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6988) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000002721E93E82D5DB01 | |||
| (PID) Process: | (7544) NordLayerSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 4EFC31460C619ECAE59C1BCE2C008036D94C84B8 |
Value: | |||
| (PID) Process: | (7544) NordLayerSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\4EFC31460C619ECAE59C1BCE2C008036D94C84B8 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000E94FB54871208C00DF70F708AC47085B0F0000000100000030000000C130BBA37B8B350E89FD5ED76B4F78777FEEE220D3B9E729042BEF6AF46E8E4C1B252E32B3080C681BC9A8A1AFDD0A3C0300000001000000140000004EFC31460C619ECAE59C1BCE2C008036D94C84B809000000010000000C000000300A06082B060105050703031D00000001000000100000005467B0ADDE8D858E30EE517B1A19ECD91400000001000000140000001F00BF46800AFC7839B7A5B443D95650BBCE963B53000000010000001F000000301D301B060567810C010330123010060A2B0601040182373C0101030200C06200000001000000200000007B9D553E1C92CB6E8803E137F4F287D4363757F5D44B37D52F9FCA22FB97DF860B000000010000004200000047006C006F00620061006C005300690067006E00200043006F006400650020005300690067006E0069006E006700200052006F006F007400200052003400350000001900000001000000100000005D1B8FF2C30F63F5B536EDD400F7F9B4200000000100000076050000308205723082035AA00302010202107653FEAC75464893F5E5D74A483A4EF8300D06092A864886F70D01010C05003053310B300906035504061302424531193017060355040A1310476C6F62616C5369676E206E762D73613129302706035504031320476C6F62616C5369676E20436F6465205369676E696E6720526F6F7420523435301E170D3230303331383030303030305A170D3435303331383030303030305A3053310B300906035504061302424531193017060355040A1310476C6F62616C5369676E206E762D73613129302706035504031320476C6F62616C5369676E20436F6465205369676E696E6720526F6F742052343530820222300D06092A864886F70D01010105000382020F003082020A0282020100B62DC530DD7AE8AB903D0372B03A4B991661B2E5FFA5671D371CE57EEC9383AA84F5A3439B98458AB863575D9B00880425E9F868924B82D84BC94A03F3A87F6A8F8A6127BDA144D0FDF53F22C2A34F918DB305B22882915DFB5988050B9706C298F82CA73324EE503A41CCF0A0B07B1D4DD2A8583896E9DFF91B91BB8B102CD2C7431DA20974A180AF7BE6330A0C596B8EBCF4AB5A977B7FAE55FB84F080FE844CD7E2BABDC475A16FBD61107444B29807E274ABFF68DC6C263EE91FE5E00487AD30D30C8D037C55B816705C24782025EB676788ABBA4E34986B7011DE38CAD4BEA1C09CE1DF1E0201D83BE1674384B6CFFC74B72F84A3BFBA09373D676CB1455C1961AB4183F5AC1DEB770D464773CEBFBD9595ED9D2B8810FEFA58E8A757E1B3CFA85AE907259B12C49E80723D93DC8C94DF3B44E62680FCD2C303F08C0CD245D62EE78F989EE604EE426E677E42167162E704F960C664A1B69C81214E2BC66D689486C699747367317A91F2D48C796E7CA6BB7E466F4DC585122BCF9A224408A88537CE07615706171224C0C43173A1983557477E103A45D92DA4519098A9A00737C4651AAA1C6B1677F7A797EC3F1930996F31FBEA40B2E7D2C4FAC9D0F050767459FA8D6D1732BEF8E97E03F4E787759AD44A912C850313022B4280F2896A36CFC84CA0CE9EF8CB8DAD16A7D3DED59B18A7C6923AF18263F12E0E2464DF0203010001A3423040300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E041604141F00BF46800AFC7839B7A5B443D95650BBCE963B300D06092A864886F70D01010C050003820201005E2BBA749734445F764828408493EE016EE9A1B3D68025E67BE4BC09913D0FFC76ADD7D43020BB8F60D091D61CF29CEF781A2B943202C12496525202D0F3D1FCF29B396E99E11F8E43417D9A1E5BC95D9A84FC26E687F3747226ADA41BD93D3B6A52A03C091E2F1E7BB333B445C7F7ACB1AF9360AD76AEB8B21578EB836AEBFFDB46AB24E5EE02FA901F59C02F5DD6B75DA45C10B77253F8414ECCFA781A254ACAFE85624361C3B437AA81D2F4D63A0FBD8D597E3047DE2B6BE72150335FD4679BD4B8679F3C279903FF85438E7312CA20CDE861D5B166DC17D6396D0FDBCF2337A182894E1C6B3FD6A0CDAA079D3E4226AAD70CEEFA47BF1A527ED17581D3C98A62176D4F88A021A0263EAF6DD962301FE99828AE6E8DD58E4C726693808D2AE355C760679042565C22510FB3DC4E39EE4DDDD91D7810543B6ED0976F03B51EB22373C612B29A64D0FC958524A8FFDFA1B0DC9140AEDF0933ABB9DD92B7F1CC91743B69EB67971B90BFE7C7A06F71BB57BFB78F5AED7A406A16CD80842D2FE102D4249443B315FC0C2B1BFD716FFCCBBC75173A5E83D2C9B32F1BD59C8D7F54FE7E7EE456A387A79DE1595294418F6D5BBE86959AFF1A76DD40D2514A70B41F336323773FEC271E59E40887ED34824A0F3FFEA01DC1F56773458678F4AA29E92787C619DBC61314C33949874DA097E06513F59D7756E9DAB358C73AF2C0CD82 | |||
| (PID) Process: | (7544) NordLayerSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\4EFC31460C619ECAE59C1BCE2C008036D94C84B8 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000001900000001000000100000005D1B8FF2C30F63F5B536EDD400F7F9B40B000000010000004200000047006C006F00620061006C005300690067006E00200043006F006400650020005300690067006E0069006E006700200052006F006F007400200052003400350000006200000001000000200000007B9D553E1C92CB6E8803E137F4F287D4363757F5D44B37D52F9FCA22FB97DF8653000000010000001F000000301D301B060567810C010330123010060A2B0601040182373C0101030200C01400000001000000140000001F00BF46800AFC7839B7A5B443D95650BBCE963B1D00000001000000100000005467B0ADDE8D858E30EE517B1A19ECD909000000010000000C000000300A06082B060105050703030300000001000000140000004EFC31460C619ECAE59C1BCE2C008036D94C84B80F0000000100000030000000C130BBA37B8B350E89FD5ED76B4F78777FEEE220D3B9E729042BEF6AF46E8E4C1B252E32B3080C681BC9A8A1AFDD0A3C040000000100000010000000E94FB54871208C00DF70F708AC47085B200000000100000076050000308205723082035AA00302010202107653FEAC75464893F5E5D74A483A4EF8300D06092A864886F70D01010C05003053310B300906035504061302424531193017060355040A1310476C6F62616C5369676E206E762D73613129302706035504031320476C6F62616C5369676E20436F6465205369676E696E6720526F6F7420523435301E170D3230303331383030303030305A170D3435303331383030303030305A3053310B300906035504061302424531193017060355040A1310476C6F62616C5369676E206E762D73613129302706035504031320476C6F62616C5369676E20436F6465205369676E696E6720526F6F742052343530820222300D06092A864886F70D01010105000382020F003082020A0282020100B62DC530DD7AE8AB903D0372B03A4B991661B2E5FFA5671D371CE57EEC9383AA84F5A3439B98458AB863575D9B00880425E9F868924B82D84BC94A03F3A87F6A8F8A6127BDA144D0FDF53F22C2A34F918DB305B22882915DFB5988050B9706C298F82CA73324EE503A41CCF0A0B07B1D4DD2A8583896E9DFF91B91BB8B102CD2C7431DA20974A180AF7BE6330A0C596B8EBCF4AB5A977B7FAE55FB84F080FE844CD7E2BABDC475A16FBD61107444B29807E274ABFF68DC6C263EE91FE5E00487AD30D30C8D037C55B816705C24782025EB676788ABBA4E34986B7011DE38CAD4BEA1C09CE1DF1E0201D83BE1674384B6CFFC74B72F84A3BFBA09373D676CB1455C1961AB4183F5AC1DEB770D464773CEBFBD9595ED9D2B8810FEFA58E8A757E1B3CFA85AE907259B12C49E80723D93DC8C94DF3B44E62680FCD2C303F08C0CD245D62EE78F989EE604EE426E677E42167162E704F960C664A1B69C81214E2BC66D689486C699747367317A91F2D48C796E7CA6BB7E466F4DC585122BCF9A224408A88537CE07615706171224C0C43173A1983557477E103A45D92DA4519098A9A00737C4651AAA1C6B1677F7A797EC3F1930996F31FBEA40B2E7D2C4FAC9D0F050767459FA8D6D1732BEF8E97E03F4E787759AD44A912C850313022B4280F2896A36CFC84CA0CE9EF8CB8DAD16A7D3DED59B18A7C6923AF18263F12E0E2464DF0203010001A3423040300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E041604141F00BF46800AFC7839B7A5B443D95650BBCE963B300D06092A864886F70D01010C050003820201005E2BBA749734445F764828408493EE016EE9A1B3D68025E67BE4BC09913D0FFC76ADD7D43020BB8F60D091D61CF29CEF781A2B943202C12496525202D0F3D1FCF29B396E99E11F8E43417D9A1E5BC95D9A84FC26E687F3747226ADA41BD93D3B6A52A03C091E2F1E7BB333B445C7F7ACB1AF9360AD76AEB8B21578EB836AEBFFDB46AB24E5EE02FA901F59C02F5DD6B75DA45C10B77253F8414ECCFA781A254ACAFE85624361C3B437AA81D2F4D63A0FBD8D597E3047DE2B6BE72150335FD4679BD4B8679F3C279903FF85438E7312CA20CDE861D5B166DC17D6396D0FDBCF2337A182894E1C6B3FD6A0CDAA079D3E4226AAD70CEEFA47BF1A527ED17581D3C98A62176D4F88A021A0263EAF6DD962301FE99828AE6E8DD58E4C726693808D2AE355C760679042565C22510FB3DC4E39EE4DDDD91D7810543B6ED0976F03B51EB22373C612B29A64D0FC958524A8FFDFA1B0DC9140AEDF0933ABB9DD92B7F1CC91743B69EB67971B90BFE7C7A06F71BB57BFB78F5AED7A406A16CD80842D2FE102D4249443B315FC0C2B1BFD716FFCCBBC75173A5E83D2C9B32F1BD59C8D7F54FE7E7EE456A387A79DE1595294418F6D5BBE86959AFF1A76DD40D2514A70B41F336323773FEC271E59E40887ED34824A0F3FFEA01DC1F56773458678F4AA29E92787C619DBC61314C33949874DA097E06513F59D7756E9DAB358C73AF2C0CD82 | |||
| (PID) Process: | (7544) NordLayerSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D69B561148F01C77C54578C10926DF5B856976AD |
Value: | |||
Executable files
230
Suspicious files
582
Text files
287
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF11f22d.TMP | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF11f23d.TMP | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF11f24c.TMP | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF11f24c.TMP | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF11f23d.TMP | — | |
MD5:— | SHA256:— | |||
| 6988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF11f25c.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
212
DNS requests
269
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8120 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8120 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7544 | NordLayerSetup.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
7544 | NordLayerSetup.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDGLN%2BBiNNqTPN6M0%2FQ%3D%3D | unknown | — | — | whitelisted |
7544 | NordLayerSetup.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
7544 | NordLayerSetup.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7544 | NordLayerSetup.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6988 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5972 | chrome.exe | 74.125.206.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5972 | chrome.exe | 104.22.79.241:443 | nordlayer.com | CLOUDFLARENET | — | unknown |
5972 | chrome.exe | 95.100.110.30:443 | consent.cookiebot.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
accounts.google.com |
| whitelisted |
nordlayer.com |
| unknown |
consent.cookiebot.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
www.facebook.com |
| whitelisted |
content.nordlayer.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5972 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .co) |
5972 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .co) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5972 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|