| URL: | https://libgen.li/edition.php?id=138745301 |
| Full analysis: | https://app.any.run/tasks/58a830a7-2ce2-4f27-956b-0889f6df5c0b |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2024, 19:09:24 |
| OS: | Ubuntu 22.04.2 |
| MD5: | D0C5AA32100E0E8BB53954126F5CC809 |
| SHA1: | 26534430B0331CA96E8DE2455130E85E5180762A |
| SHA256: | 5928F6B08E4A5258400D24E0B12AFB31F1F90F4430253C7A2EE7FEFF502250BB |
| SSDEEP: | 3:N8MHXuawMbWdSTU:2M3Jw2Wd+U |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
441
Monitored processes
83
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
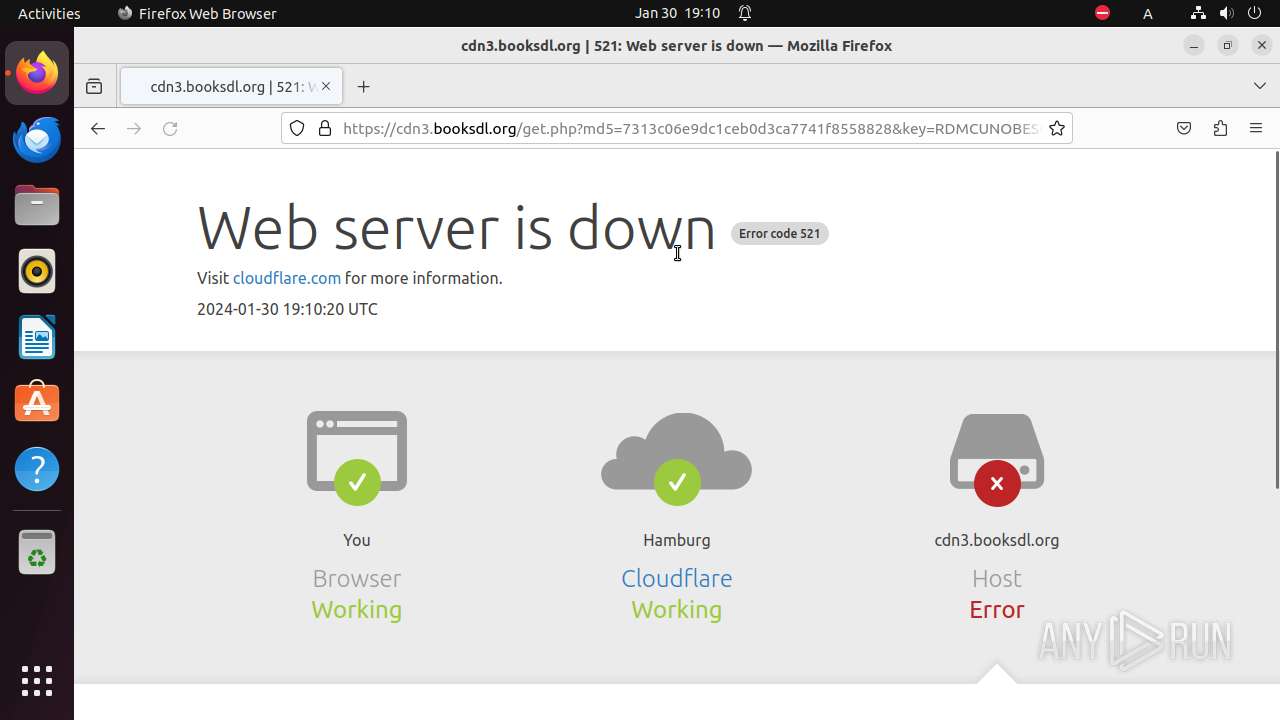
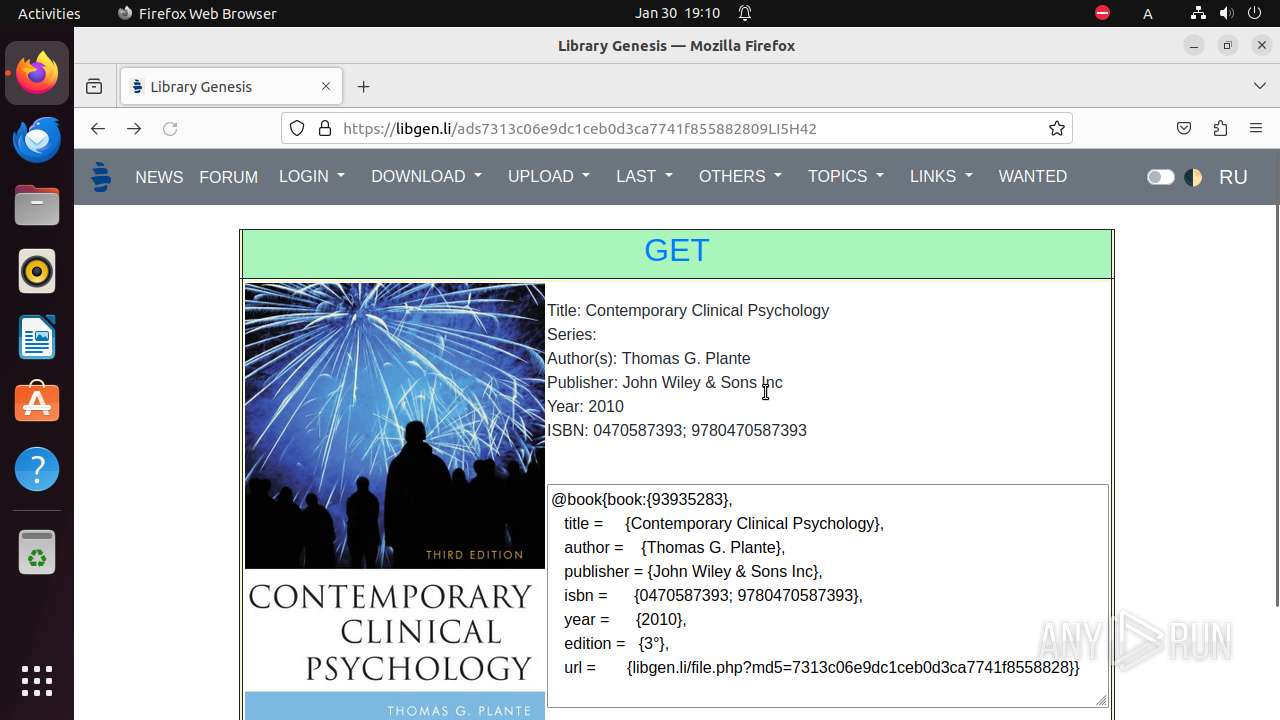
| 6850 | /bin/sh -c "DISPLAY=:0 sudo -iu user firefox \"https://libgen\.li/edition\.php?id=138745301\" " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6851 | sudo -iu user firefox https://libgen.li/edition.php?id=138745301 | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6852 | /snap/firefox/3358/usr/lib/firefox/firefox https://libgen.li/edition.php?id=138745301 | /snap/firefox/3358/usr/lib/firefox/firefox | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6853 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6864 | /snap/snapd/20290/usr/lib/snapd/snap-seccomp version-info | /snap/snapd/20290/usr/lib/snapd/snap-seccomp | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6872 | /snap/snapd/20290/usr/lib/snapd/snap-confine --base core22 snap.firefox.firefox /usr/lib/snapd/snap-exec firefox https://libgen.li/edition.php?id=138745301 | /snap/snapd/20290/usr/lib/snapd/snap-confine | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6873 | /snap/snapd/20290/usr/lib/snapd/snap-confine --base core22 snap.firefox.firefox /usr/lib/snapd/snap-exec firefox https://libgen.li/edition.php?id=138745301 | /snap/snapd/20290/usr/lib/snapd/snap-confine | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6874 | snap-update-ns --from-snap-confine --user-mounts firefox | /dev/fd/5 | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6885 | date +%s.%N | /usr/bin/date | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6886 | chmod 700 /home/user/snap/firefox/3358/.config | /usr/bin/chmod | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6852 | firefox | /tmp/snap-private-tmp/snap.firefox/tmp/firefox/.parentlock | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.cache/mozilla/firefox/roxl94gw.default/.startup-incomplete | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/cert9.db-journal | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/storage.sqlite-journal | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/protections.sqlite-journal | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/content-prefs.sqlite-journal | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.mozilla/firefox/roxl94gw.default/prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.cache/mozilla/firefox/roxl94gw.default/cache2/entries/09B20518D9345274CC2E2934FF4ED0FF2BD0D5E6 | — | |
MD5:— | SHA256:— | |||
| 6852 | firefox | /home/user/snap/firefox/common/.cache/mozilla/firefox/roxl94gw.default/cache2/entries/8152854A5EBF9CD17E5F06DDF4DB29D66A7AC9AE | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
48
DNS requests
99
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 34.122.121.32:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
— | — | GET | 204 | 35.232.111.17:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
— | — | POST | 200 | 95.101.54.195:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
— | — | POST | 200 | 18.238.246.206:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | binary | 471 b | unknown |
— | — | POST | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
— | — | POST | 200 | 95.101.54.195:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
— | — | POST | 200 | 95.101.54.195:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
— | — | POST | 200 | 95.101.54.195:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 34.122.121.32:80 | — | GOOGLE-CLOUD-PLATFORM | US | unknown |
— | — | 91.189.91.49:80 | — | Canonical Group Limited | US | unknown |
— | — | 185.125.190.17:80 | — | Canonical Group Limited | GB | unknown |
— | — | 212.102.56.179:443 | — | Datacamp Limited | DE | unknown |
— | — | 35.232.111.17:80 | — | GOOGLE-CLOUD-PLATFORM | US | unknown |
— | — | 104.21.57.230:443 | libgen.li | CLOUDFLARENET | — | unknown |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | unknown |
— | — | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
— | — | 3.208.221.93:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
libgen.li |
| unknown |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| unknown |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
r3.o.lencr.org |
| shared |
content-signature-2.cdn.mozilla.net |
| whitelisted |
ocsp.r2m02.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |