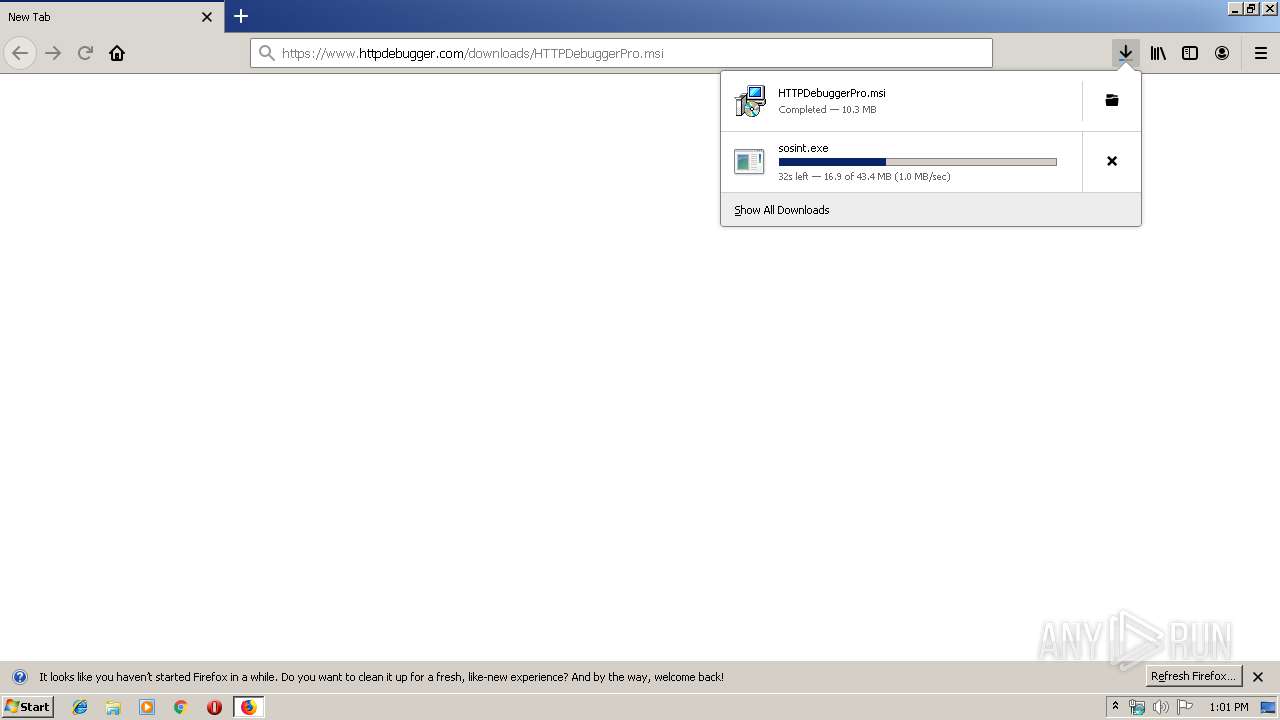
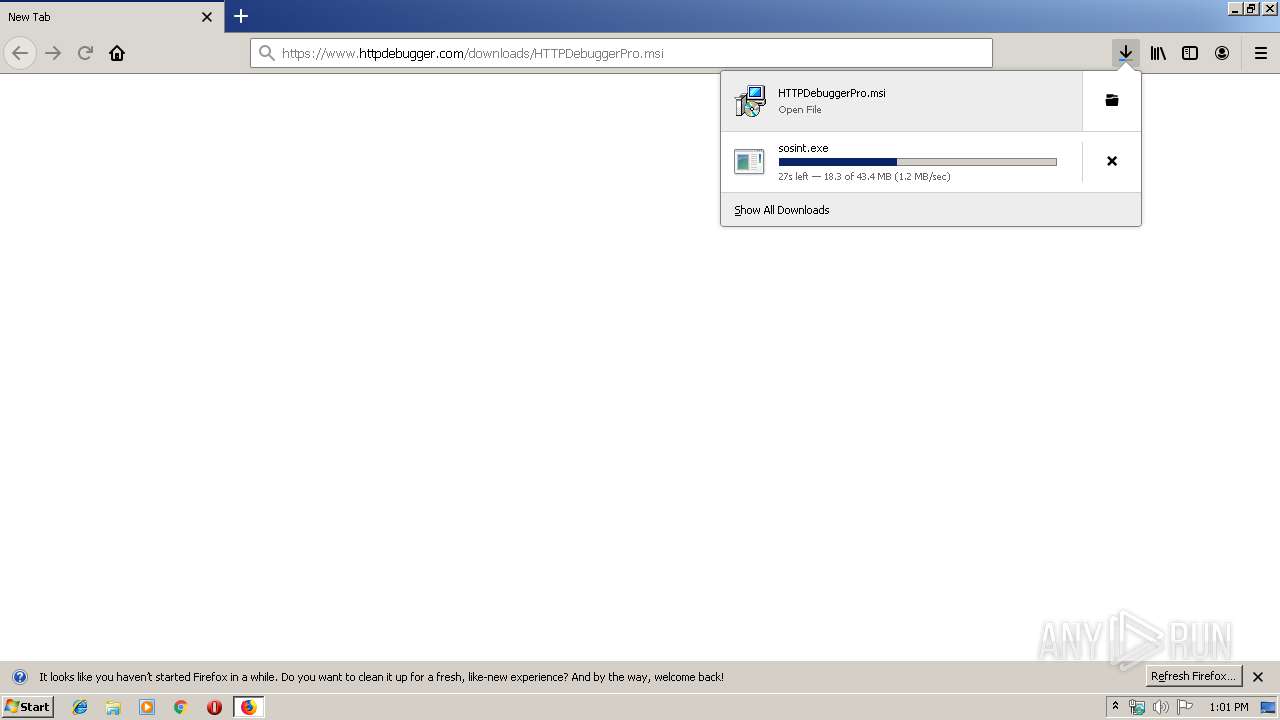
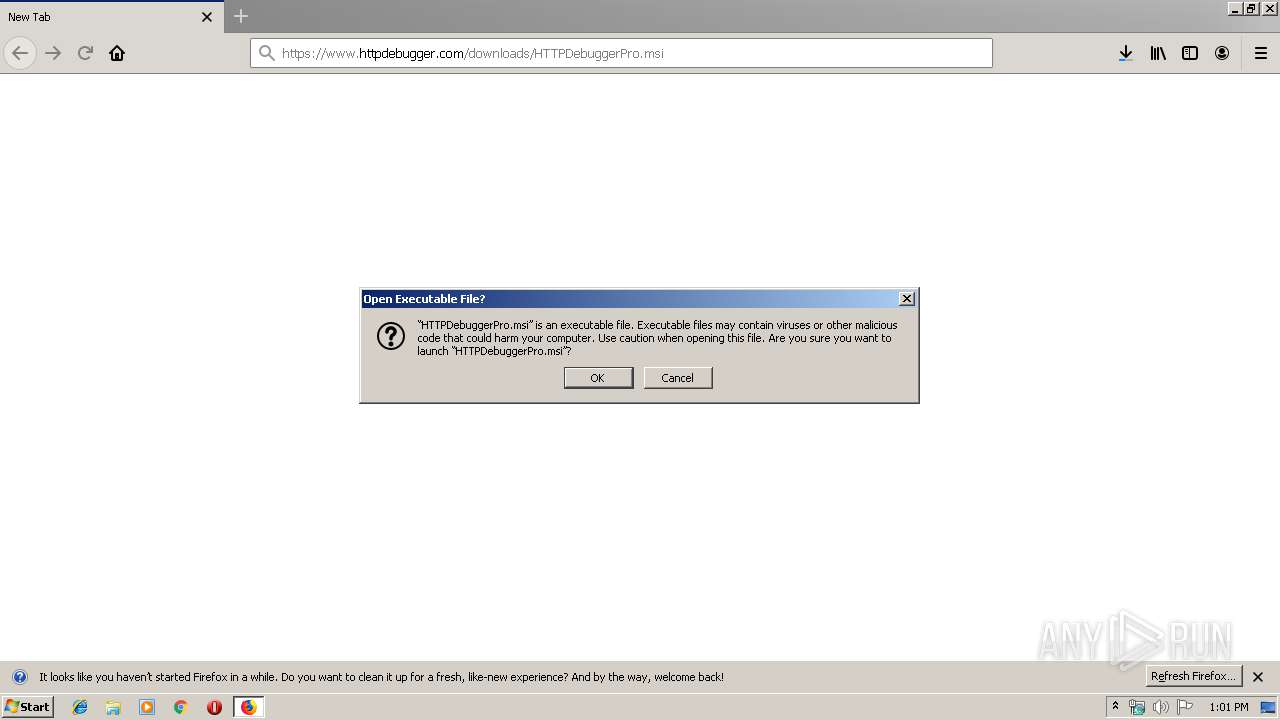
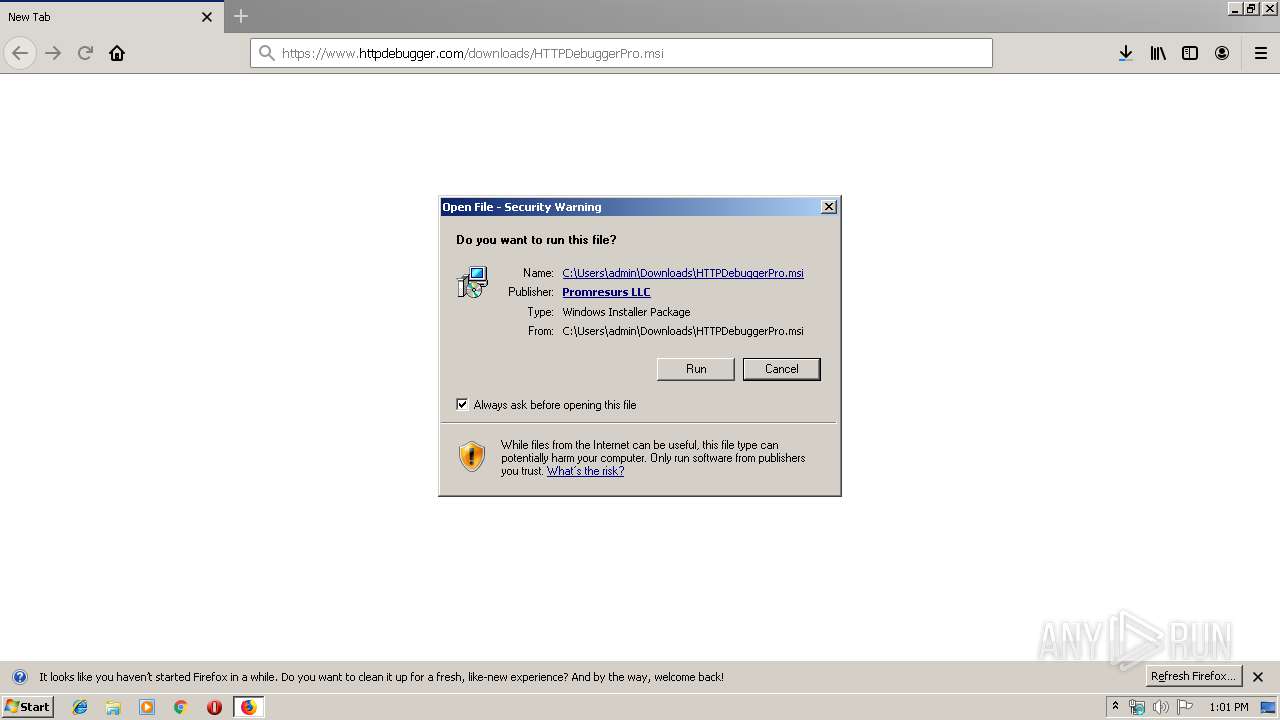
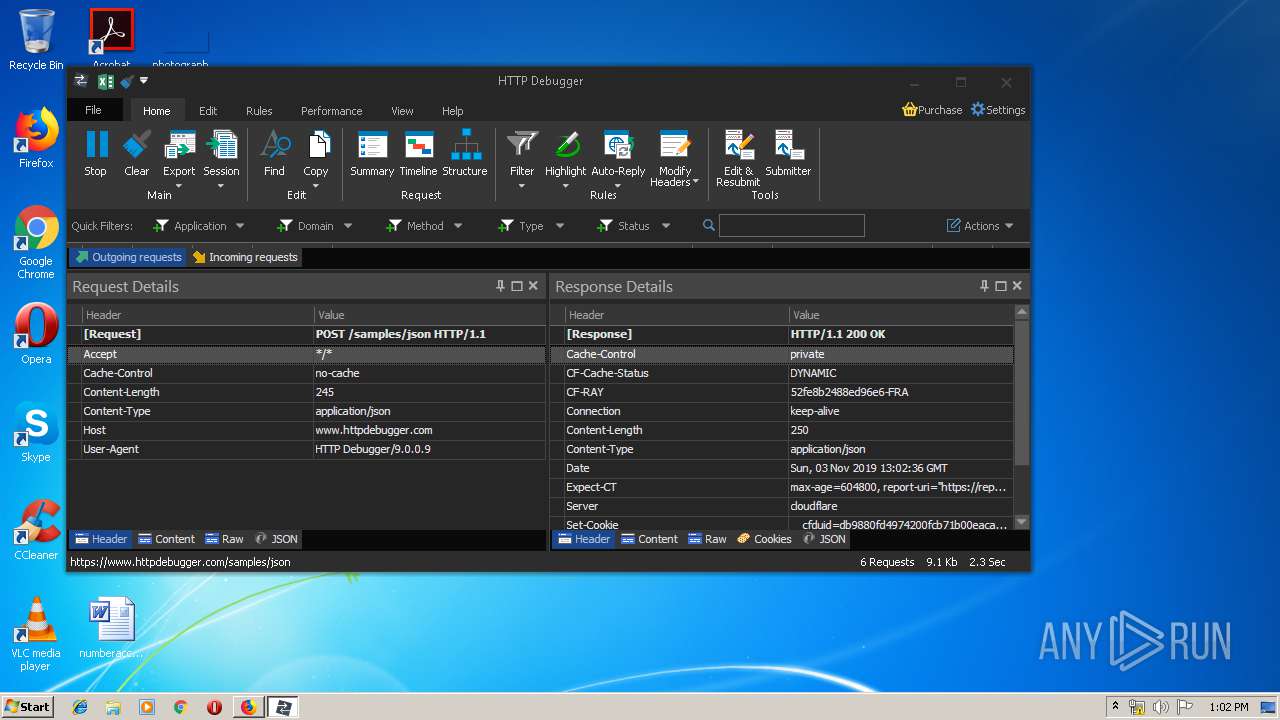
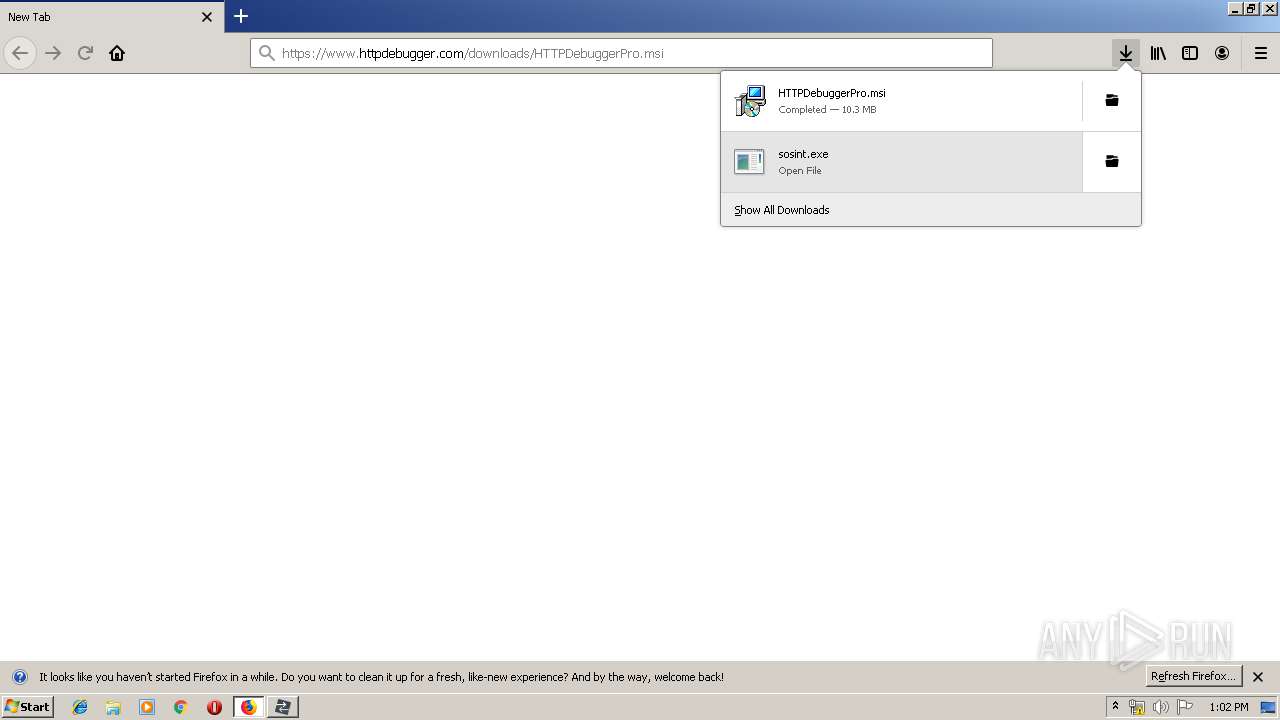
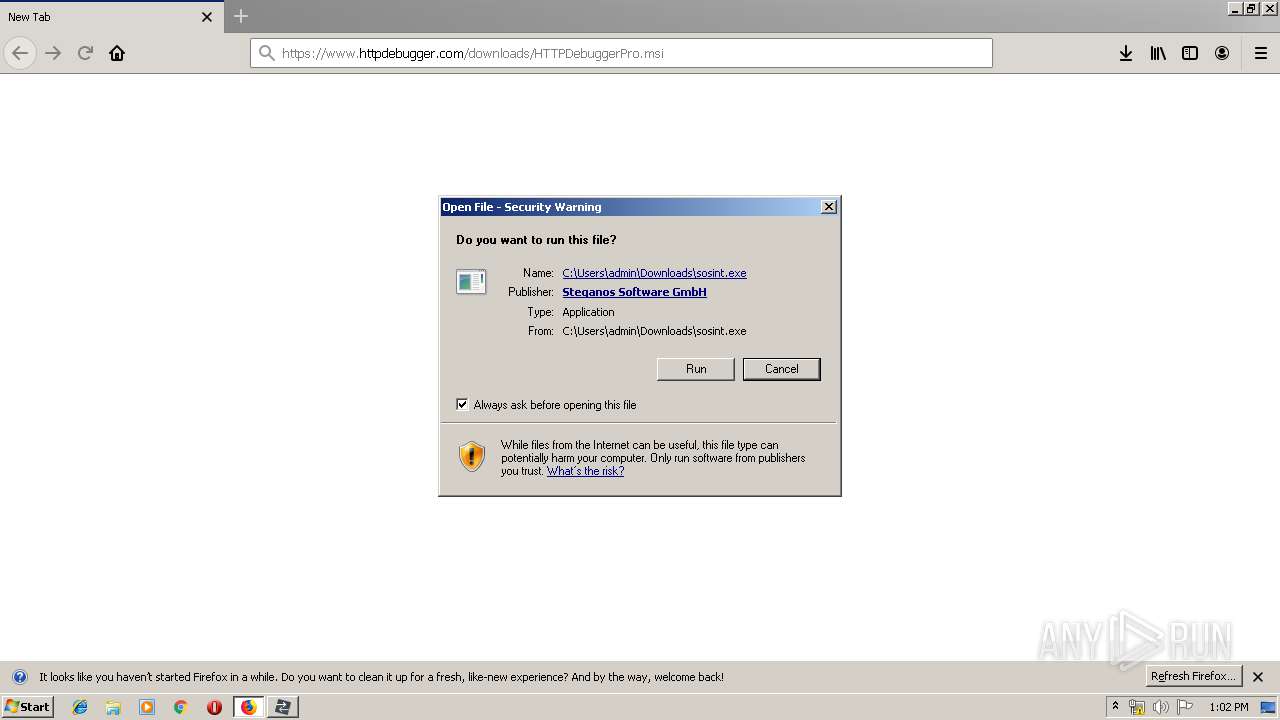
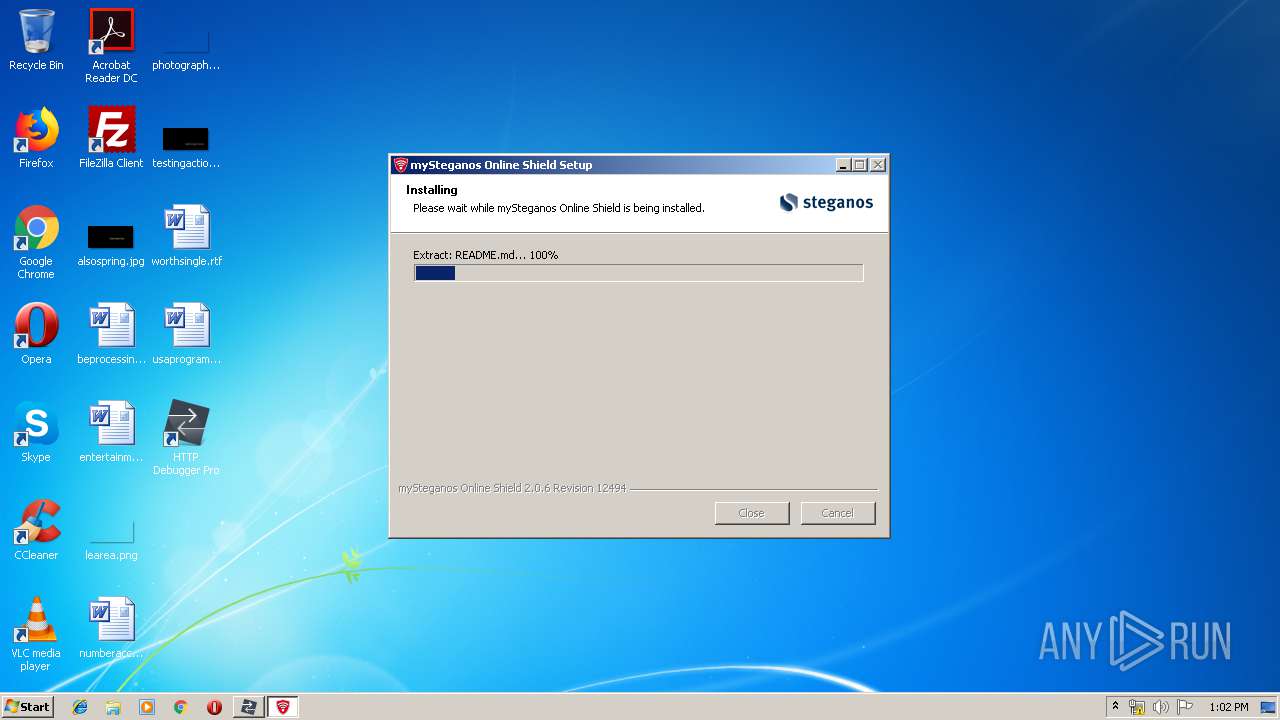
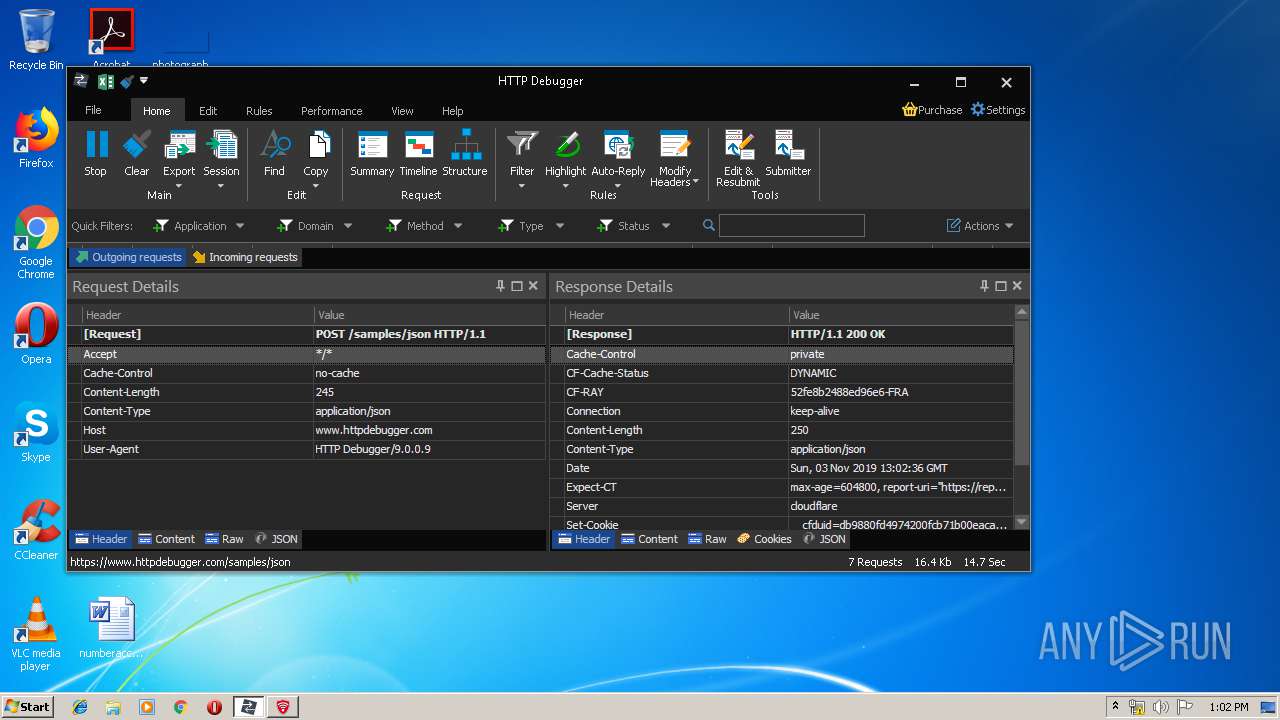
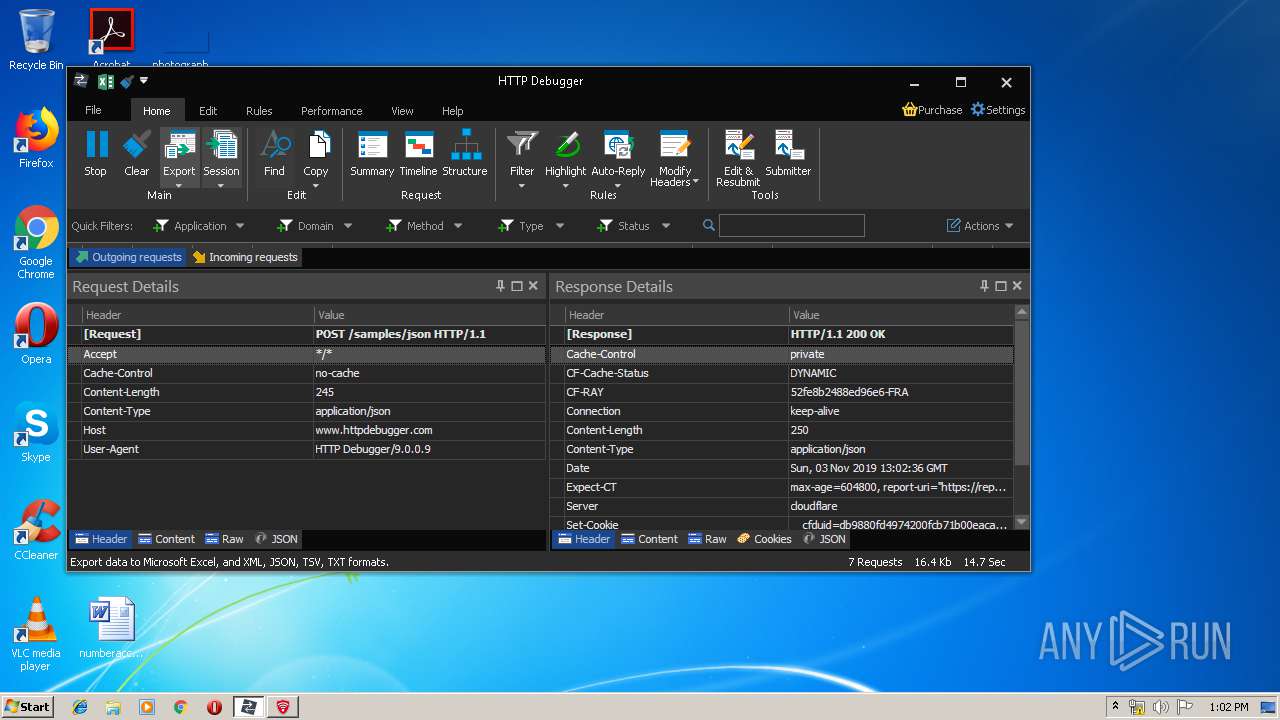
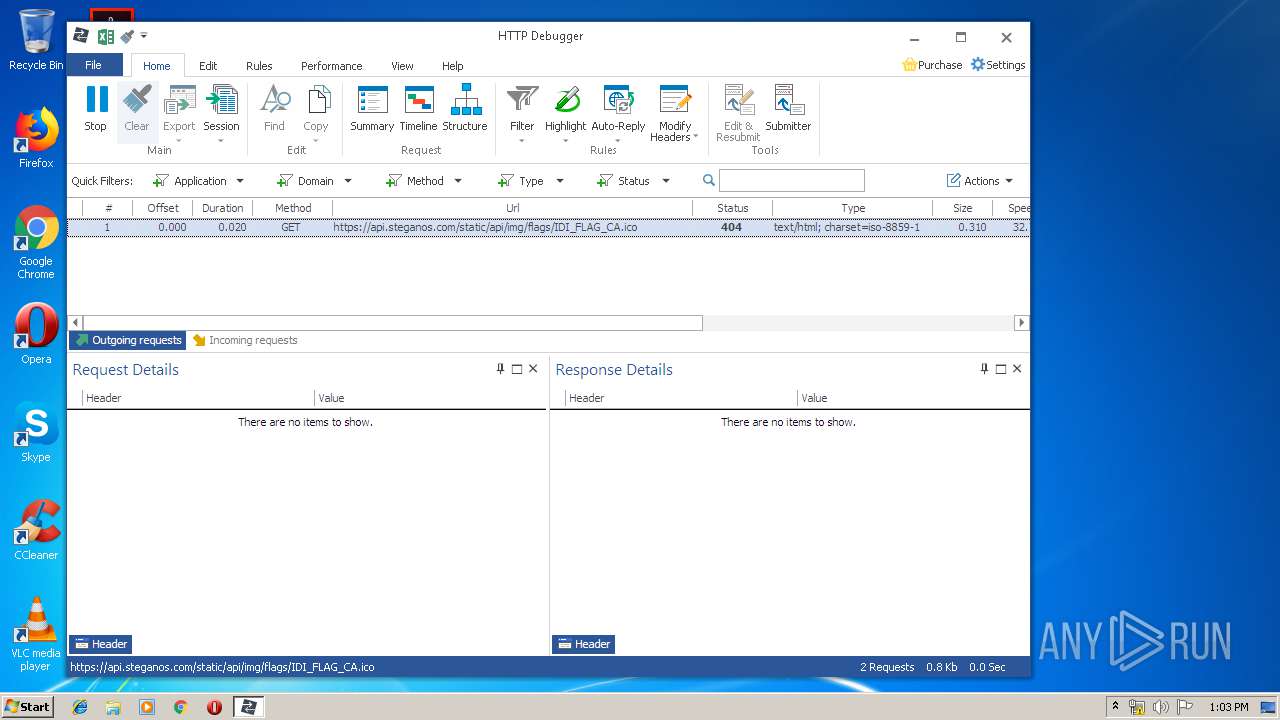
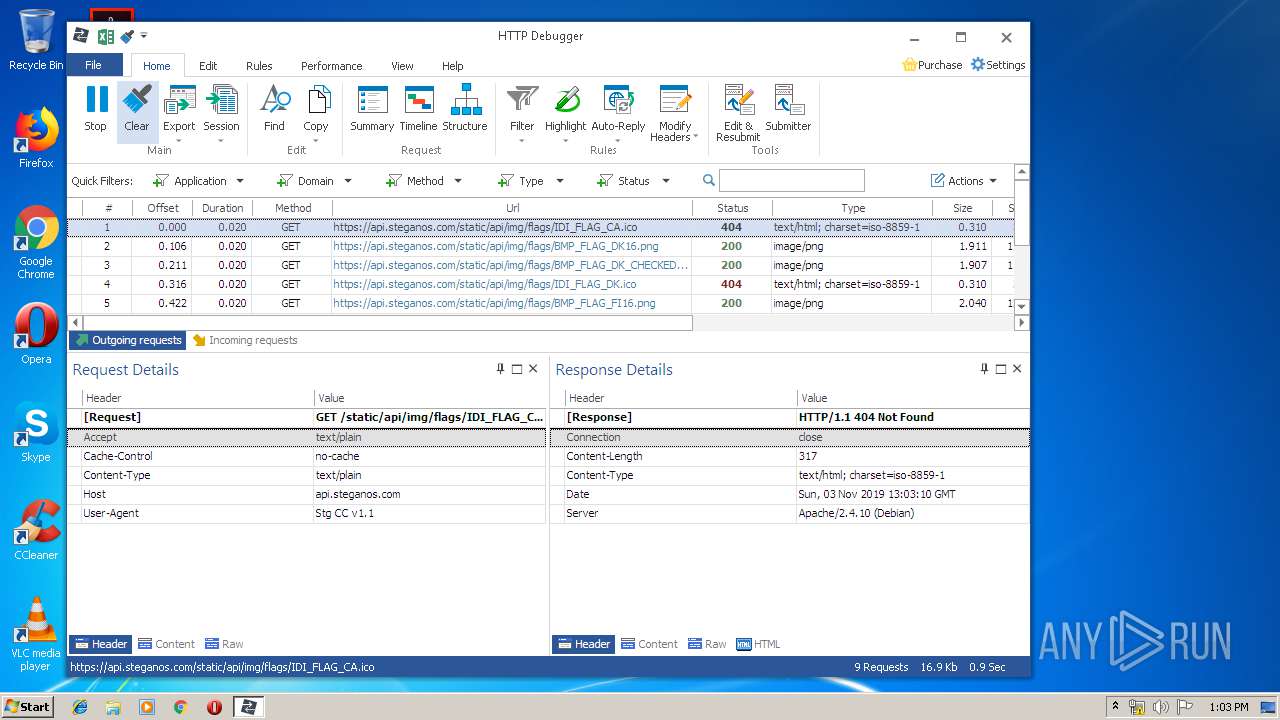
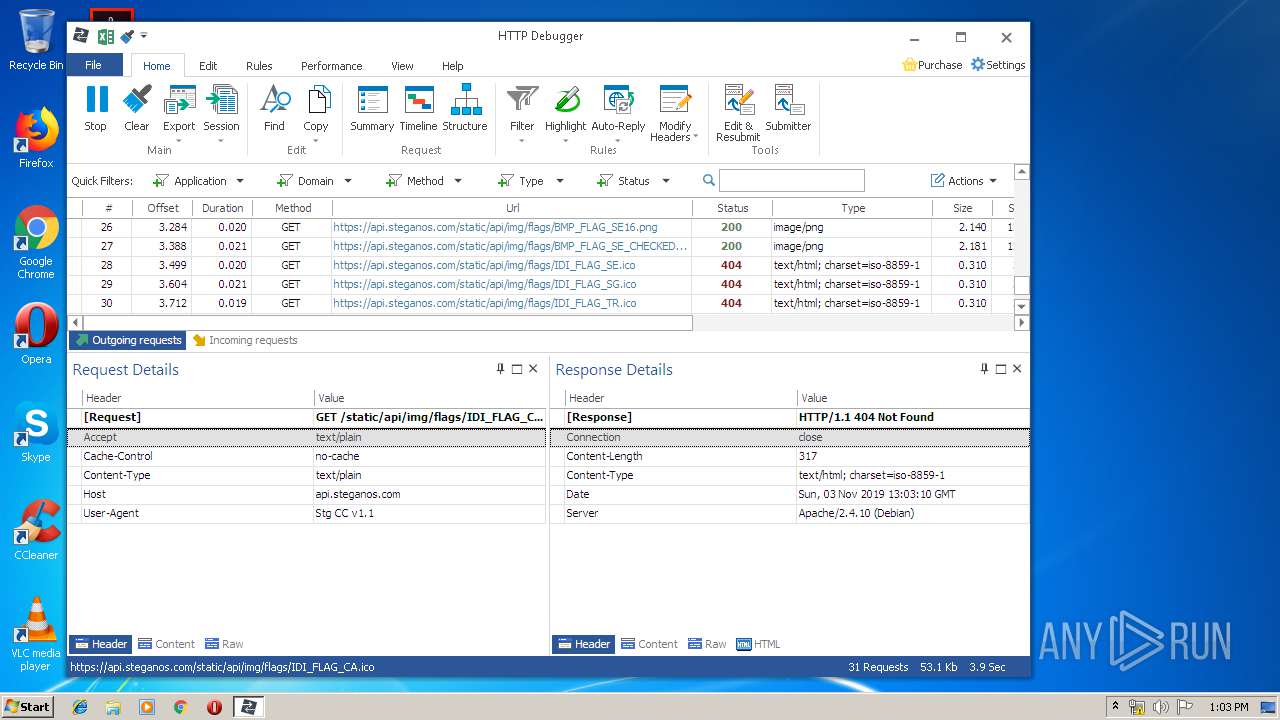
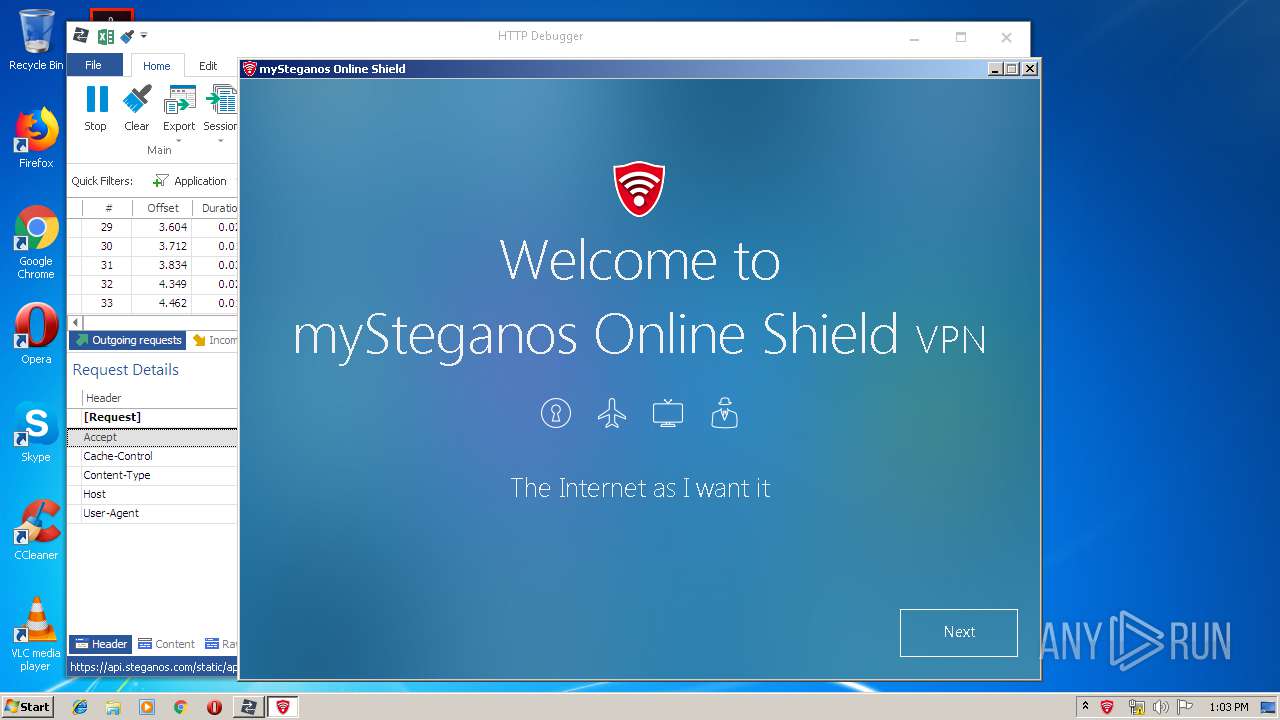
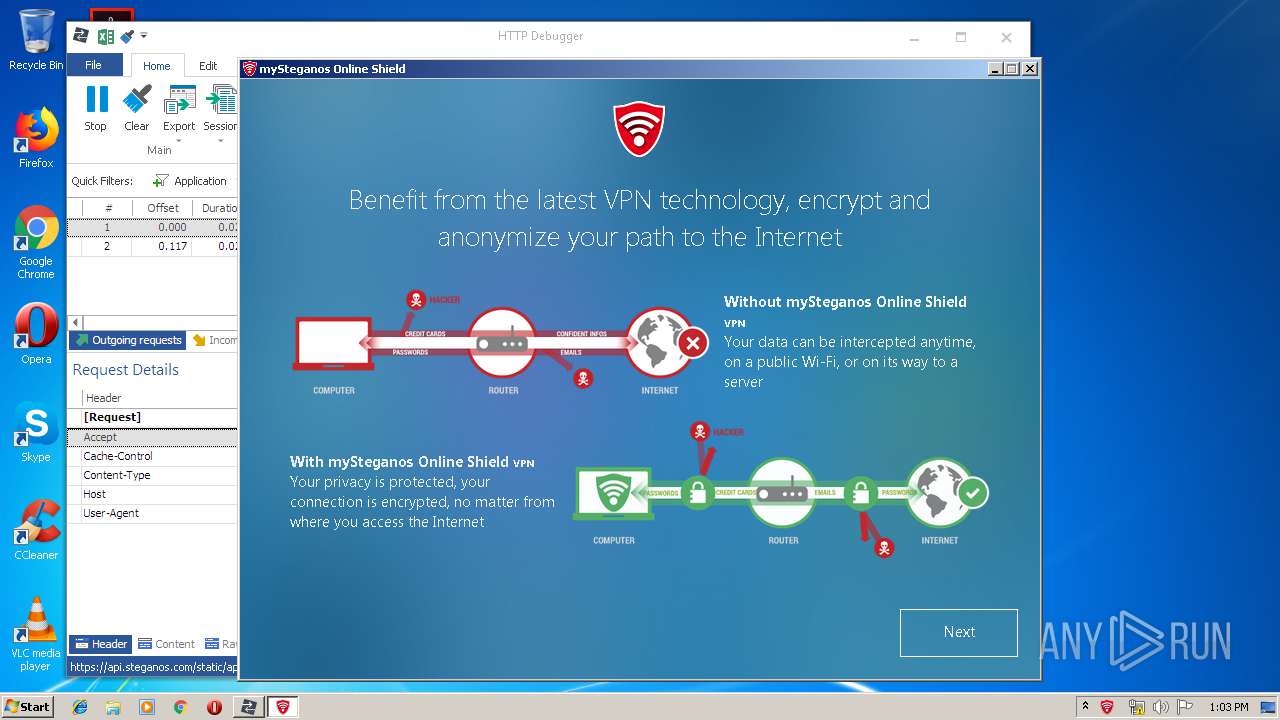
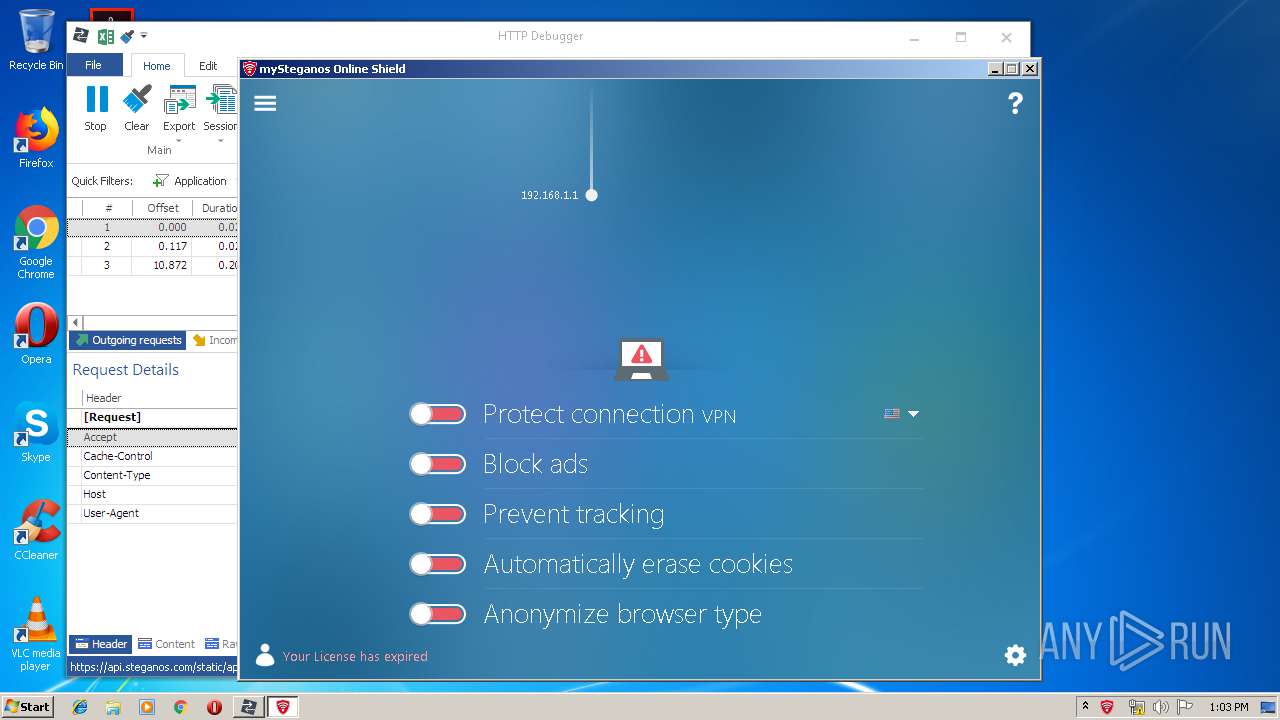
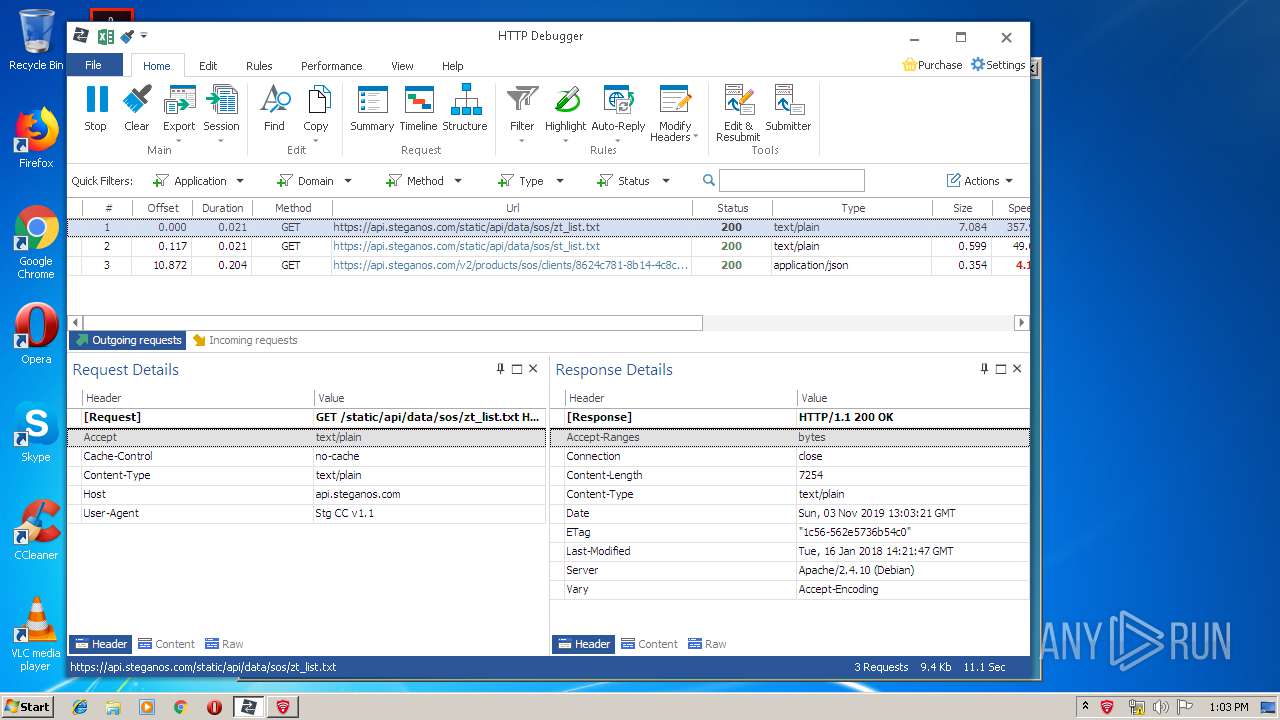
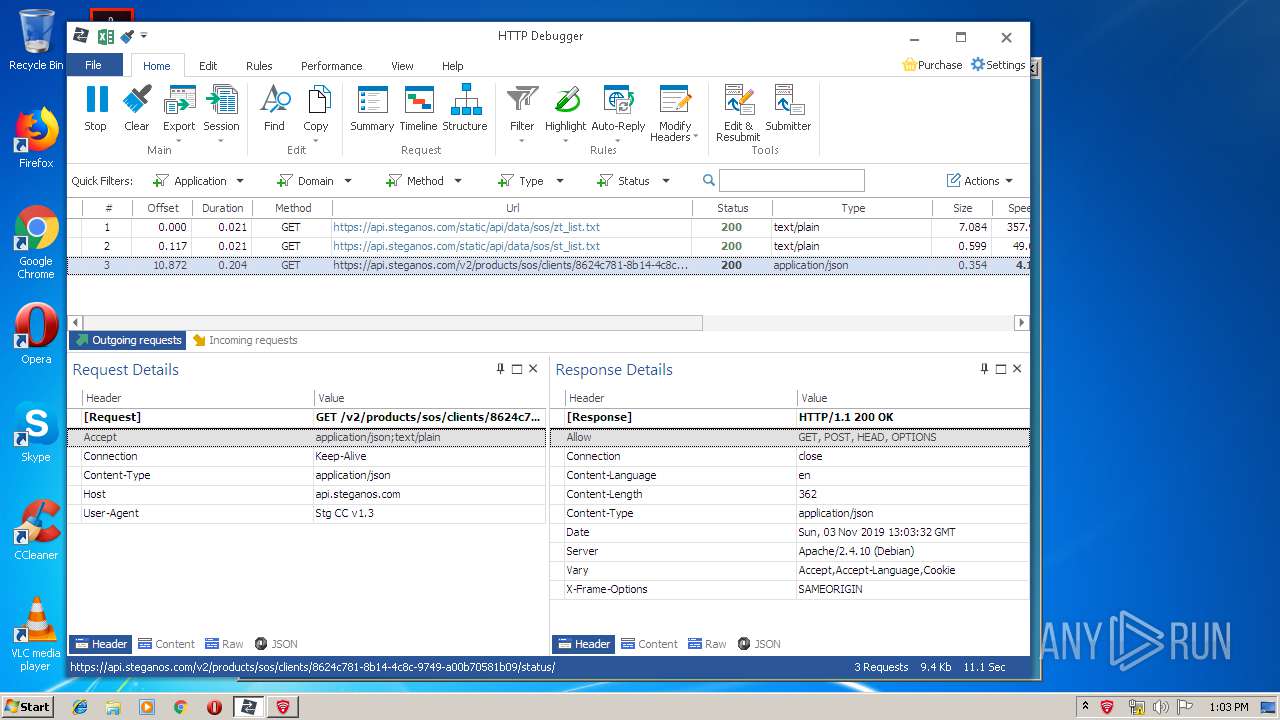
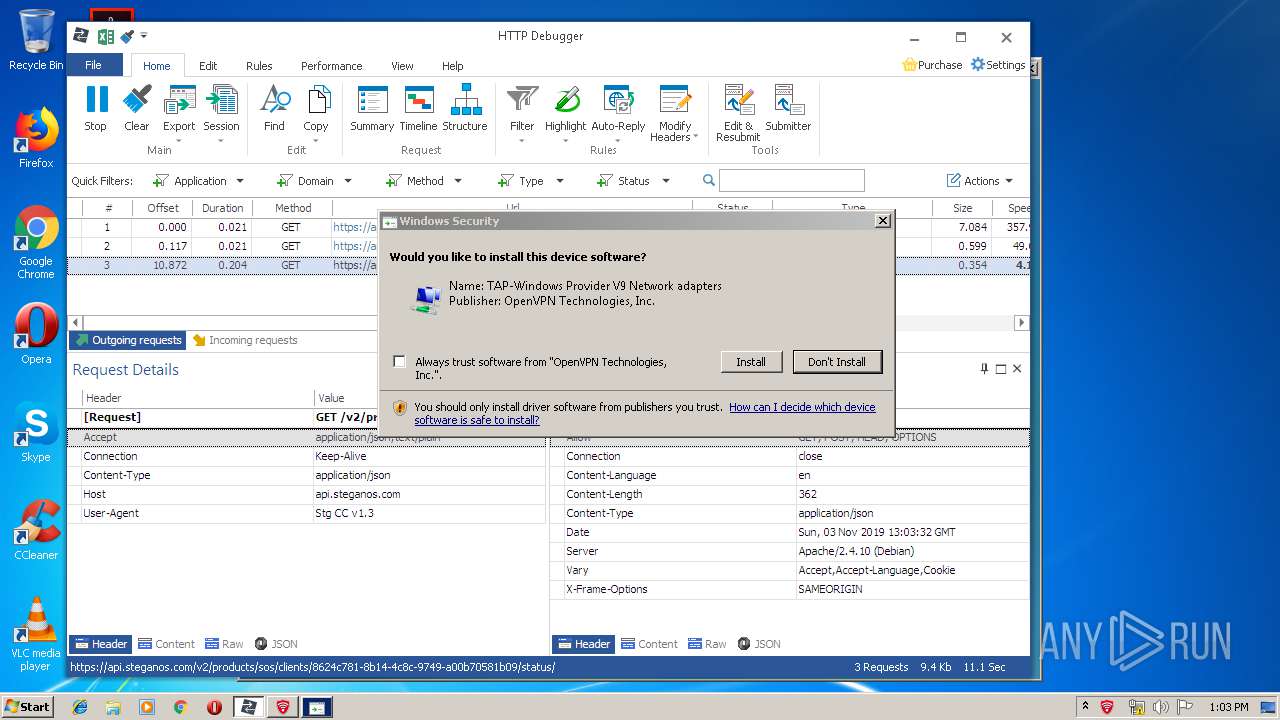
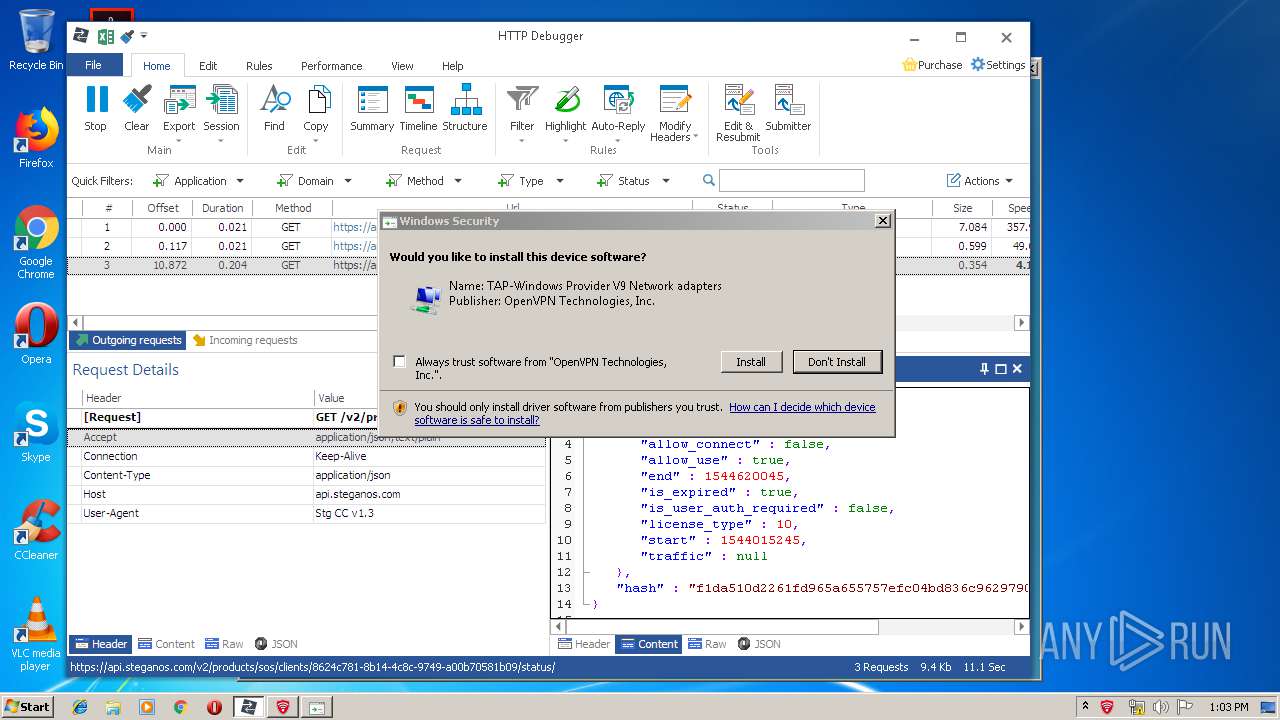
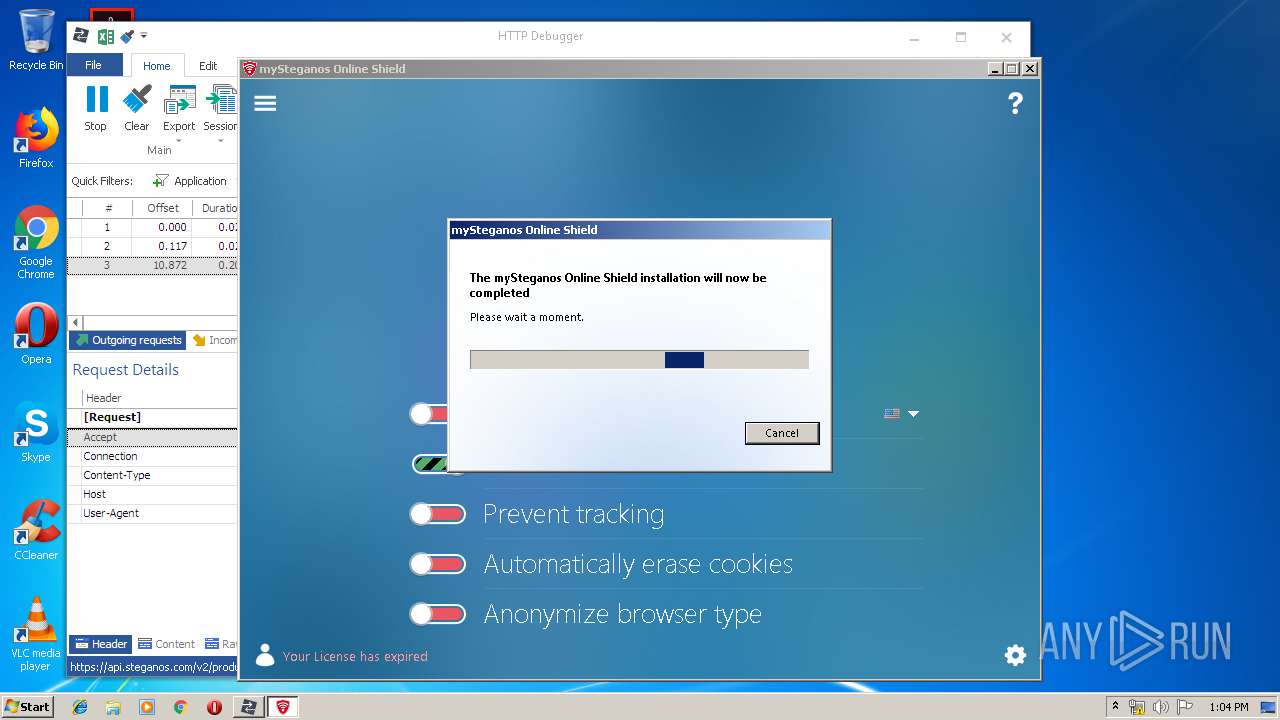
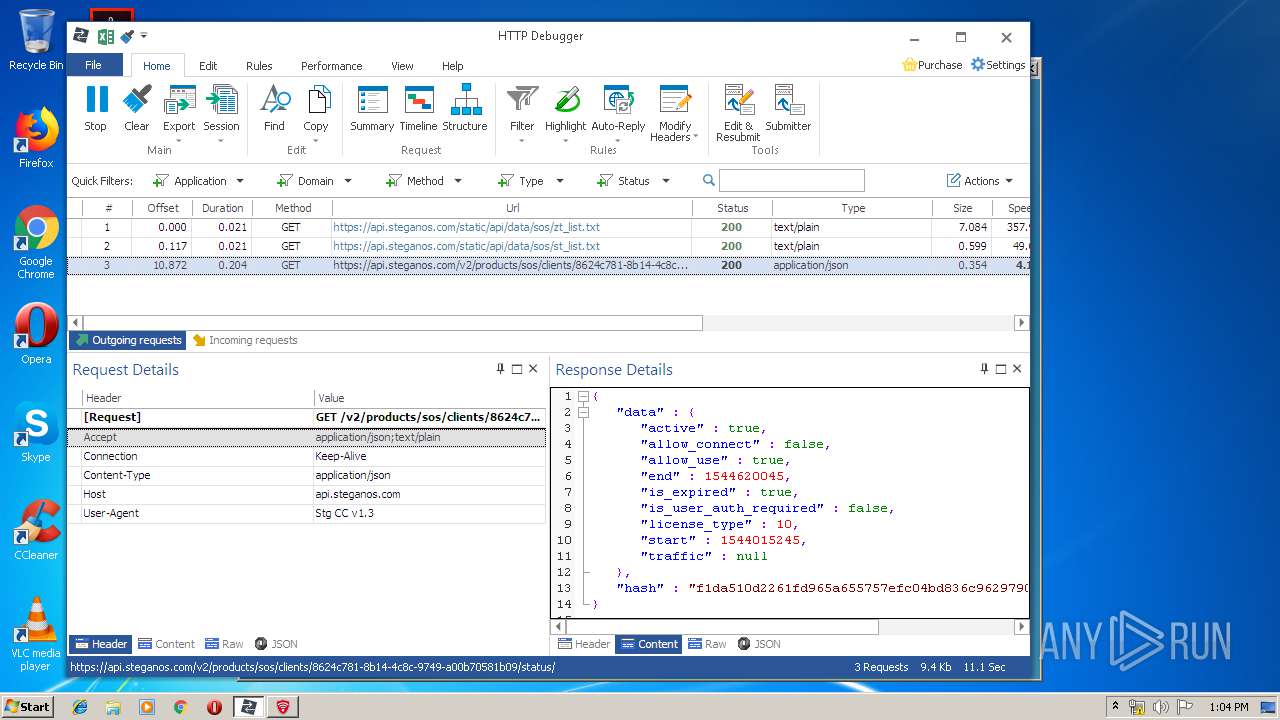
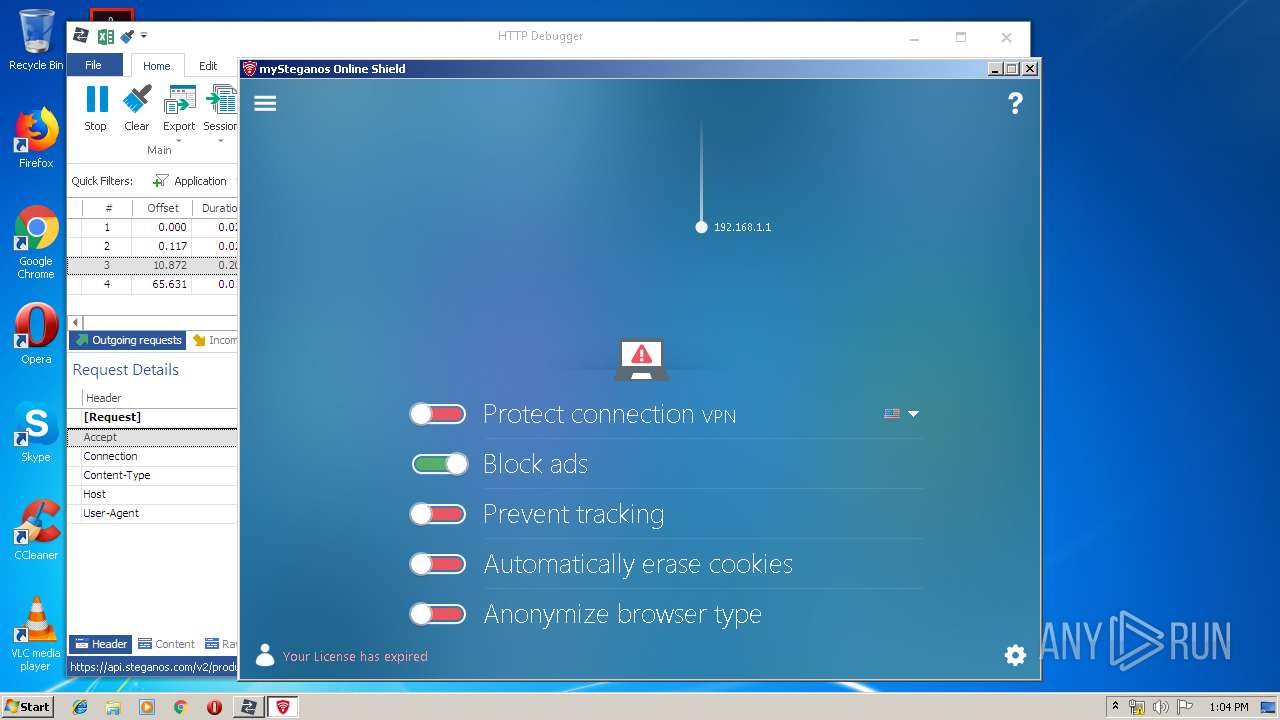
| URL: | https://file.steganos.com/software/sosint.exe |
| Full analysis: | https://app.any.run/tasks/b19eb97a-32be-4851-9b2e-2d3d29bf1053 |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2019, 13:00:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3AC155521D14BB6E8D15AB51F1C8662C |
| SHA1: | 66D8D1B0F22B3A937BF86140392758C25A6F4740 |
| SHA256: | 590910BC471AD944D088D5F00E9E3E5E38765BCA36989F9C5677A24E57B88451 |
| SSDEEP: | 3:N8OK6A:2OY |
MALICIOUS
Application was dropped or rewritten from another process
- HTTPDebuggerSvc.exe (PID: 1856)
- HTTPDebuggerSvc.exe (PID: 3408)
- certutil.exe (PID: 956)
- sosint.exe (PID: 3288)
- sosint.exe (PID: 3836)
- HTTPDebuggerUI.exe (PID: 2128)
- devcon.exe (PID: 3204)
- devcon.exe (PID: 3696)
- devcon.exe (PID: 2748)
- OnlineShieldService.exe (PID: 3692)
- OnlineShieldClient.exe (PID: 3468)
- OnlineShieldClient.exe (PID: 1780)
- Notifier.exe (PID: 736)
- ns2A8E.tmp (PID: 2512)
- ns2945.tmp (PID: 2888)
- ns2C45.tmp (PID: 3932)
- Updater.exe (PID: 2248)
- awesomium_process.exe (PID: 2648)
- Updater.exe (PID: 2152)
- setuptool.exe (PID: 3872)
- devcon.exe (PID: 3376)
- devcon.exe (PID: 2528)
- devcon.exe (PID: 2840)
- node.exe (PID: 3712)
- OnlineShieldClient.exe (PID: 5944)
- ResetPendingMoves.exe (PID: 788)
Changes settings of System certificates
- HTTPDebuggerSvc.exe (PID: 1856)
- devcon.exe (PID: 2840)
Loads dropped or rewritten executable
- certutil.exe (PID: 956)
- MsiExec.exe (PID: 2732)
- sosint.exe (PID: 3836)
- sosint.exe (PID: 3288)
- OnlineShieldClient.exe (PID: 3468)
- OnlineShieldService.exe (PID: 3692)
- HTTPDebuggerUI.exe (PID: 2128)
- OnlineShieldClient.exe (PID: 1780)
- awesomium_process.exe (PID: 2648)
- OnlineShieldClient.exe (PID: 5944)
Changes the autorun value in the registry
- OnlineShieldClient.exe (PID: 3468)
- sosint.exe (PID: 3836)
- OnlineShieldClient.exe (PID: 1780)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 3968)
- HTTPDebuggerSvc.exe (PID: 1856)
- sosint.exe (PID: 3836)
Executable content was dropped or overwritten
- firefox.exe (PID: 3968)
- msiexec.exe (PID: 1892)
- HTTPDebuggerSvc.exe (PID: 1856)
- msiexec.exe (PID: 3880)
- sosint.exe (PID: 3288)
- sosint.exe (PID: 3836)
- OnlineShieldClient.exe (PID: 3468)
- OnlineShieldClient.exe (PID: 1780)
- devcon.exe (PID: 2840)
- DrvInst.exe (PID: 2364)
- DrvInst.exe (PID: 2160)
Cleans NTFS data-stream (Zone Identifier)
- firefox.exe (PID: 3968)
Starts Microsoft Installer
- firefox.exe (PID: 3968)
Executed as Windows Service
- vssvc.exe (PID: 3396)
- HTTPDebuggerSvc.exe (PID: 1856)
- OnlineShieldService.exe (PID: 3692)
Creates COM task schedule object
- MsiExec.exe (PID: 2732)
Creates or modifies windows services
- HTTPDebuggerSvc.exe (PID: 1856)
Creates files in the Windows directory
- HTTPDebuggerSvc.exe (PID: 1856)
- DrvInst.exe (PID: 2364)
- DrvInst.exe (PID: 2160)
Creates files in the driver directory
- HTTPDebuggerSvc.exe (PID: 1856)
- DrvInst.exe (PID: 2364)
- DrvInst.exe (PID: 2160)
Reads internet explorer settings
- HTTPDebuggerUI.exe (PID: 2128)
Application launched itself
- sosint.exe (PID: 3288)
Starts application with an unusual extension
- sosint.exe (PID: 3836)
Creates files in the user directory
- sosint.exe (PID: 3836)
- Notifier.exe (PID: 736)
- OnlineShieldClient.exe (PID: 1780)
- Updater.exe (PID: 2248)
- setuptool.exe (PID: 3872)
- OnlineShieldClient.exe (PID: 3468)
Creates a software uninstall entry
- sosint.exe (PID: 3836)
Changes IE settings (feature browser emulation)
- Notifier.exe (PID: 736)
Starts Internet Explorer
- Updater.exe (PID: 2248)
Uses RUNDLL32.EXE to load library
- OnlineShieldClient.exe (PID: 1780)
- DrvInst.exe (PID: 2364)
Reads Internet Cache Settings
- rundll32.exe (PID: 592)
- rundll32.exe (PID: 1016)
- rundll32.exe (PID: 1560)
- rundll32.exe (PID: 1876)
- rundll32.exe (PID: 252)
- rundll32.exe (PID: 1424)
Executed via COM
- DrvInst.exe (PID: 2364)
- DrvInst.exe (PID: 2160)
Removes files from Windows directory
- DrvInst.exe (PID: 2364)
- DrvInst.exe (PID: 2160)
Starts CMD.EXE for commands execution
- node.exe (PID: 3712)
INFO
Application launched itself
- firefox.exe (PID: 2088)
- firefox.exe (PID: 3968)
- msiexec.exe (PID: 1892)
- chrome.exe (PID: 5364)
Creates files in the user directory
- firefox.exe (PID: 3968)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3968)
- sosint.exe (PID: 3836)
- OnlineShieldClient.exe (PID: 3468)
- OnlineShieldClient.exe (PID: 1780)
Reads CPU info
- firefox.exe (PID: 3968)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3396)
Searches for installed software
- msiexec.exe (PID: 1892)
- DrvInst.exe (PID: 2364)
Reads settings of System Certificates
- firefox.exe (PID: 3968)
- Updater.exe (PID: 2248)
- Updater.exe (PID: 2152)
Creates files in the program directory
- msiexec.exe (PID: 1892)
Creates a software uninstall entry
- msiexec.exe (PID: 1892)
Dropped object may contain TOR URL's
- sosint.exe (PID: 3836)
- OnlineShieldClient.exe (PID: 3468)
- OnlineShieldClient.exe (PID: 1780)
Changes settings of System certificates
- pingsender.exe (PID: 2980)
Changes internet zones settings
- iexplore.exe (PID: 2380)
Reads Internet Cache Settings
- iexplore.exe (PID: 3152)
Manual execution by user
- OnlineShieldClient.exe (PID: 5944)
- chrome.exe (PID: 5364)
Reads the hosts file
- chrome.exe (PID: 5364)
- chrome.exe (PID: 4848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
80
Malicious processes
14
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | OnlineShieldClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | OnlineShieldClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Program Files\Steganos Online Shield\Notifier.exe" | C:\Program Files\Steganos Online Shield\Notifier.exe | — | sosint.exe | |||||||||||
User: admin Company: Steganos Software GmbH Integrity Level: MEDIUM Description: Steganos Notifier Exit code: 0 Version: 2.0.6.12494 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Steganos Online Shield\ResetPendingMoves.exe" "mySteganos Online Shield" | C:\Program Files\Steganos Online Shield\ResetPendingMoves.exe | — | sosint.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 956 | nss\certutil -A -t "TCu" -i "C:\ProgramData\HTTPDebuggerPro\Cert\SSL\HTTP DEBUGGER CA for DEBUG ONLY 2.cer" -n "HTTP DEBUGGER CA for DEBUG ONLY 2" -d sql:"C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\QLDYZ5~1.DEF"-f pwfile | C:\Program Files\HTTPDebuggerPro\nss\certutil.exe | — | HTTPDebuggerSvc.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 255 Modules
| |||||||||||||||
| 1016 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | OnlineShieldClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | OnlineShieldClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,11358666201595454501,9424760788243052422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17526346487129223308 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3396 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,11358666201595454501,9424760788243052422,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13070908291690081772 --mojo-platform-channel-handle=4104 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1560 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | OnlineShieldClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 202
Read events
3 605
Write events
5 133
Delete events
464
Modification events
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AD5F0D1803000000 | |||
| (PID) Process: | (2088) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 0AA70A1803000000 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
Executable files
106
Suspicious files
805
Text files
917
Unknown types
73
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flashsubdoc-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flashsubdoc-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\except-flash-digest256.pset | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
127
DNS requests
135
Threats
0
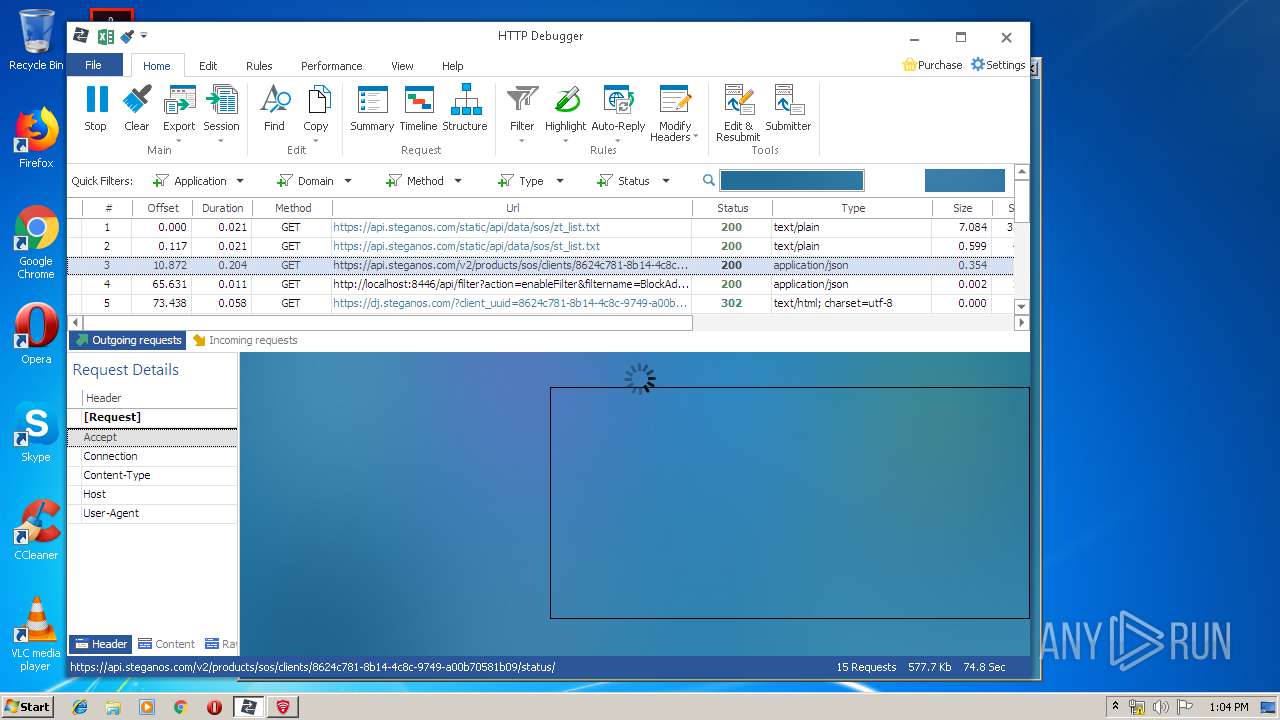
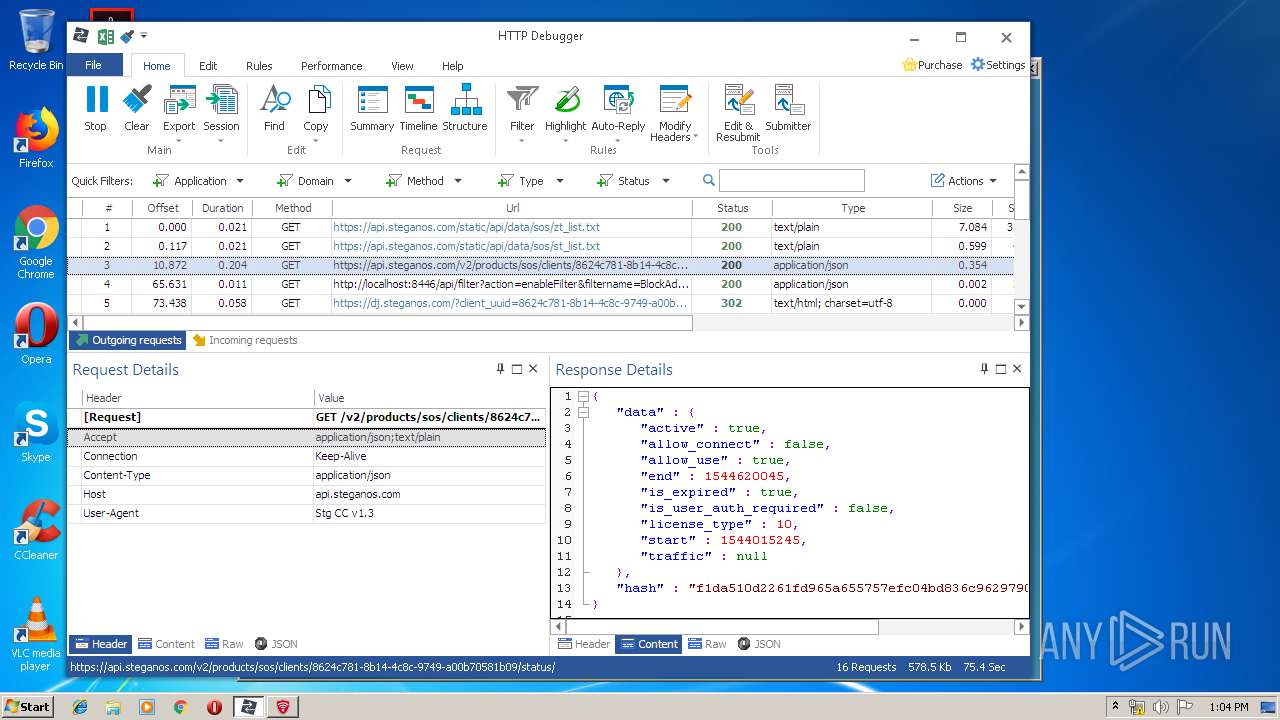
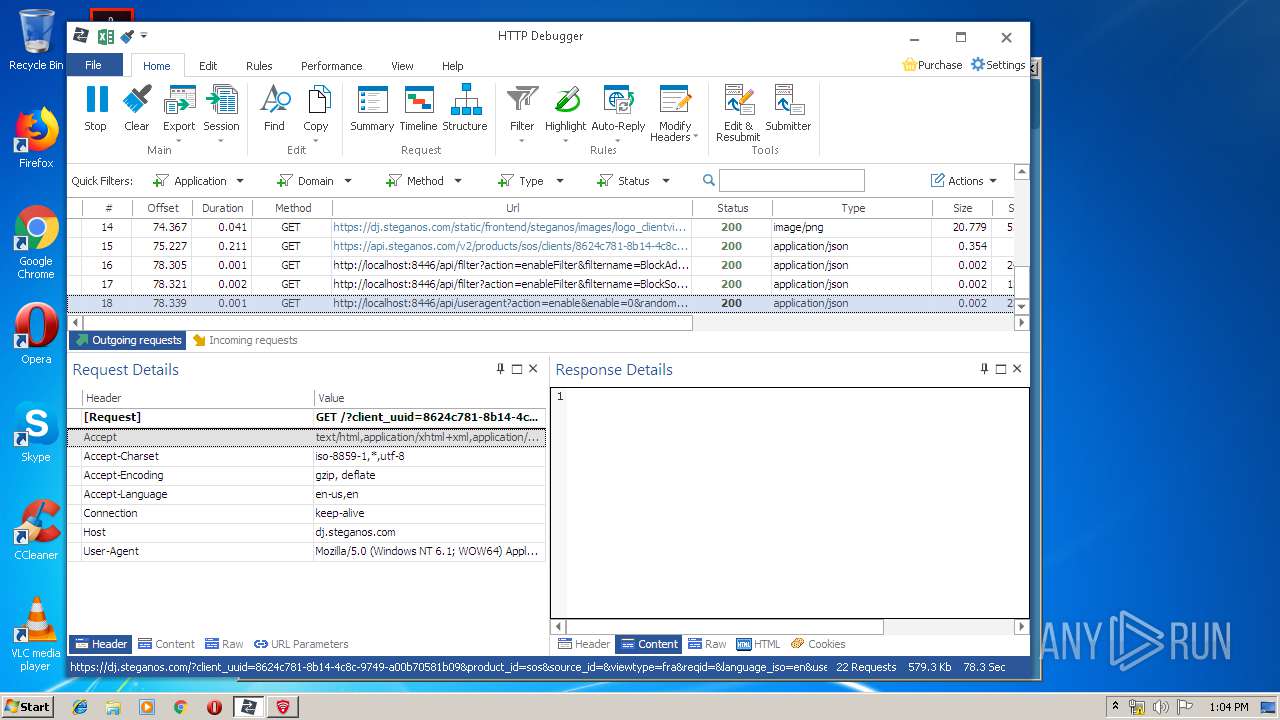
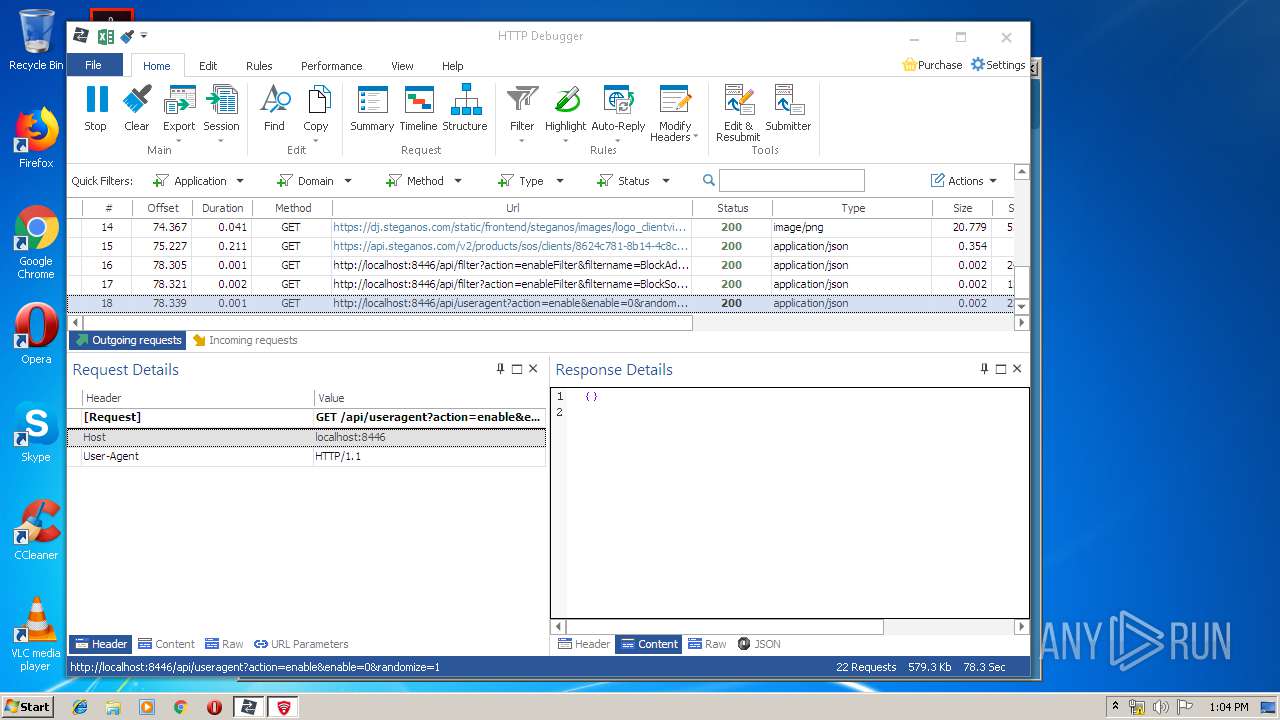
HTTP requests
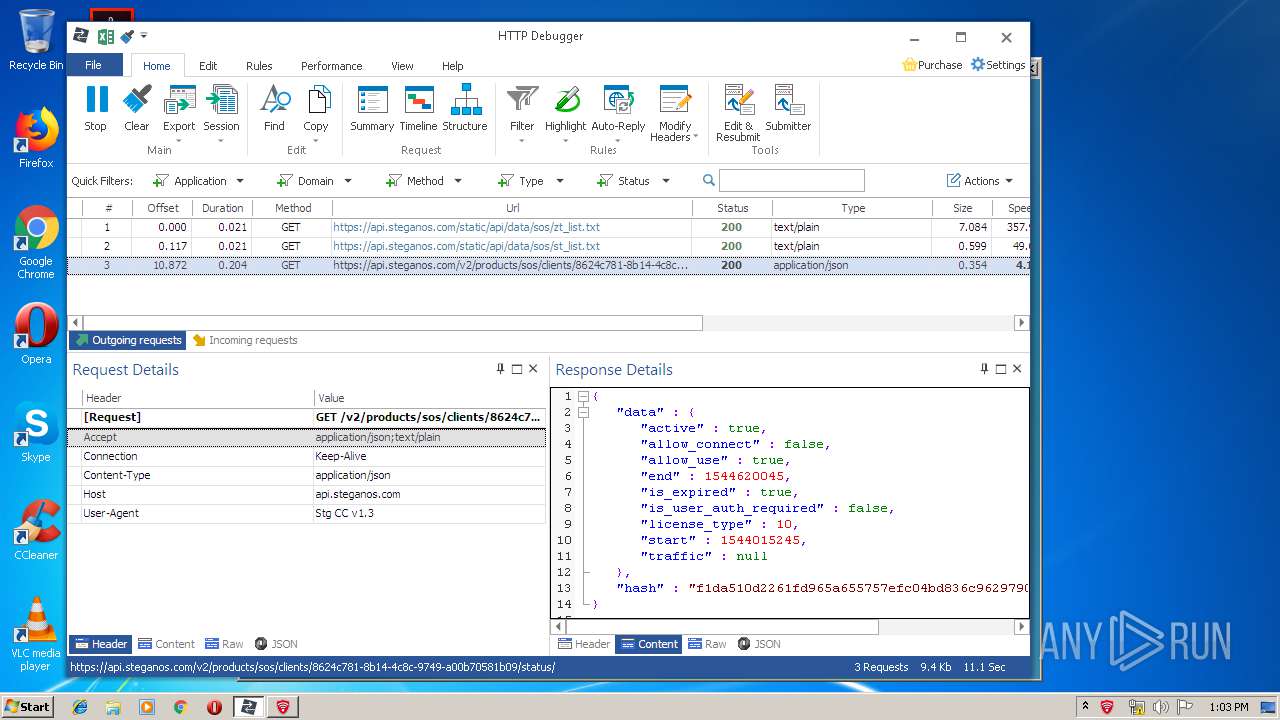
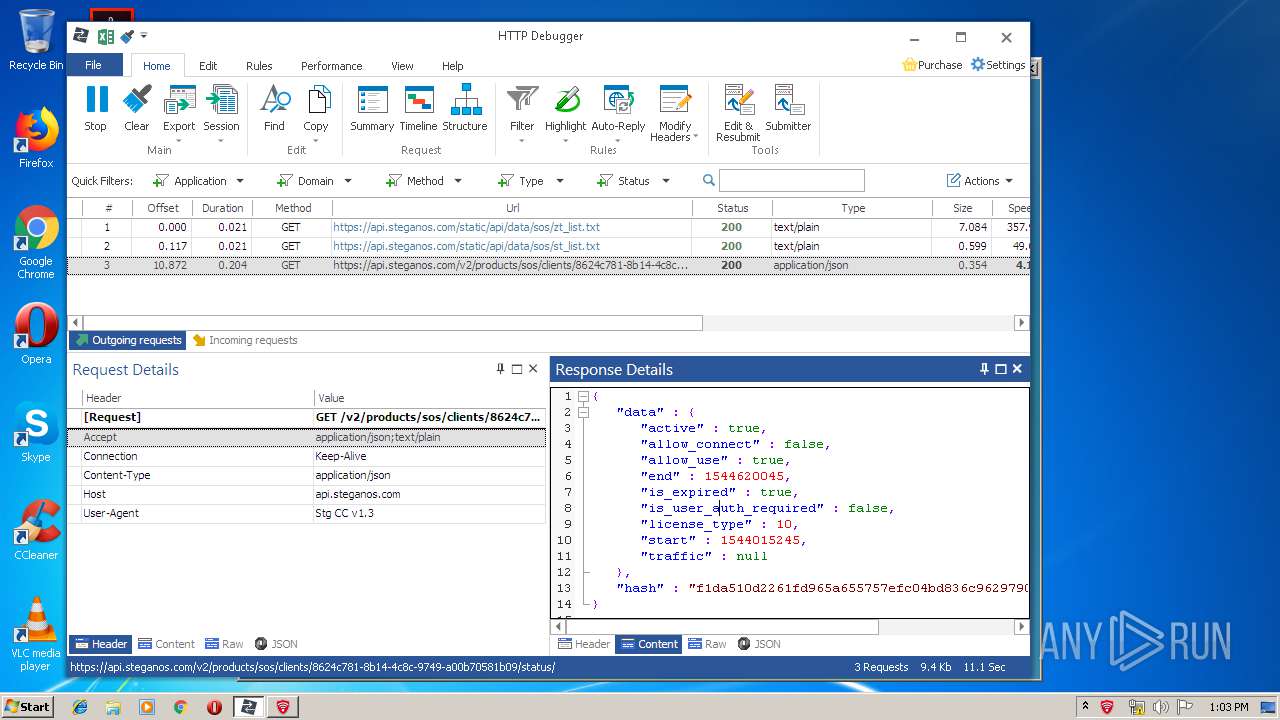
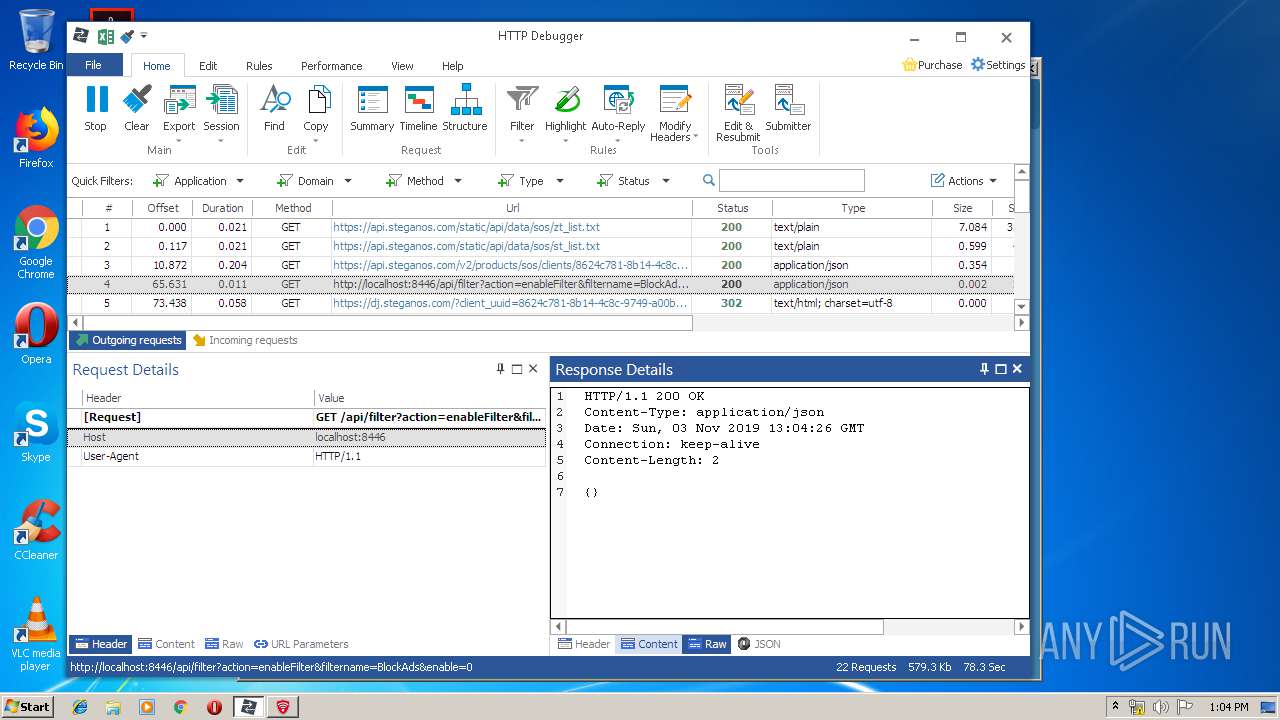
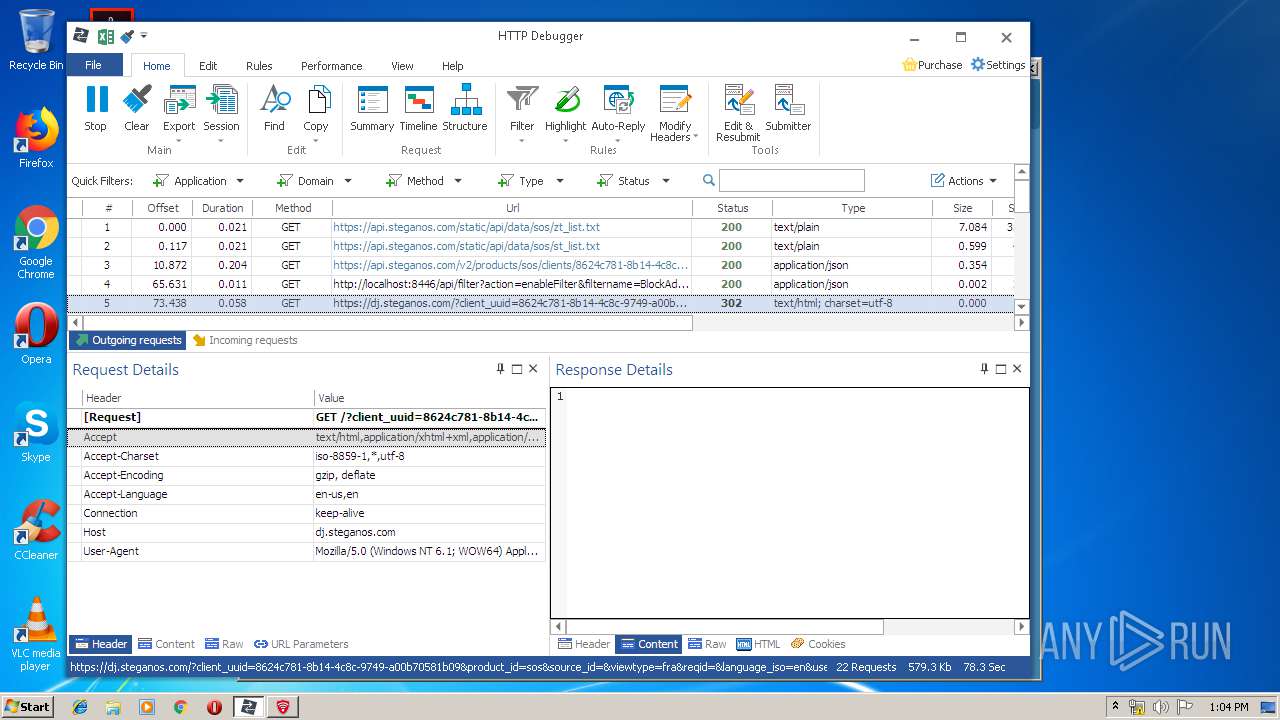
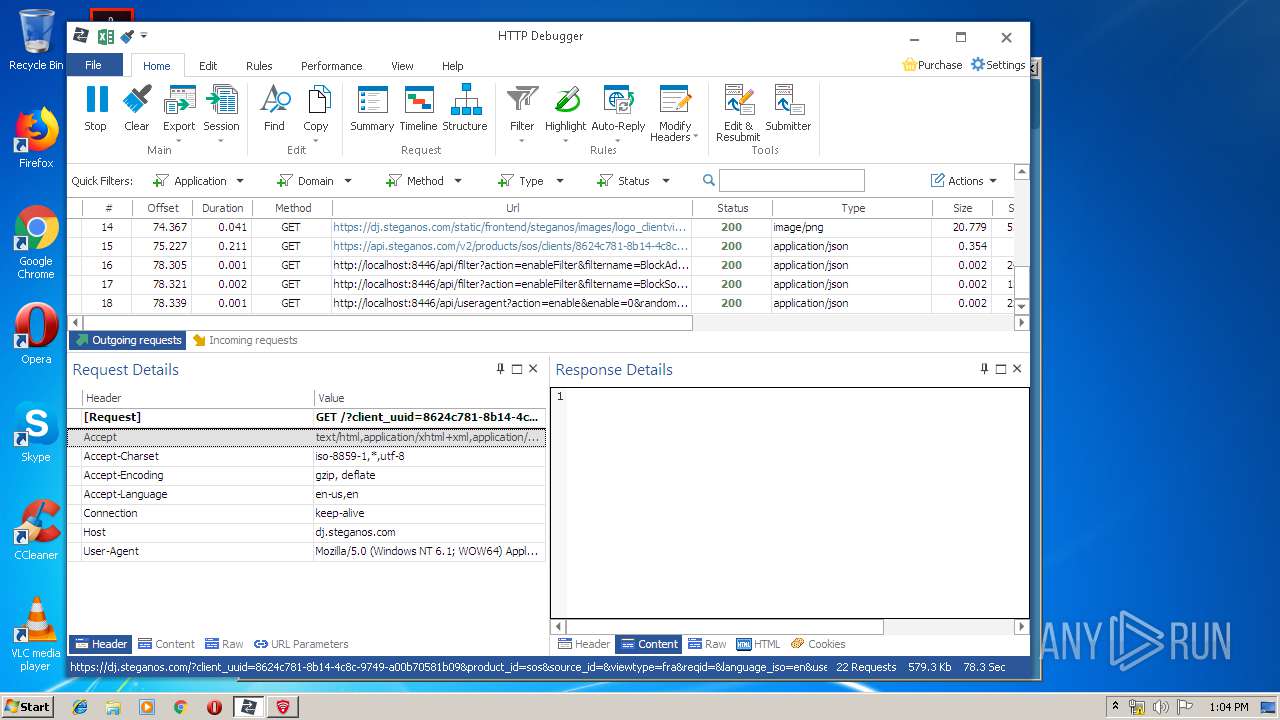
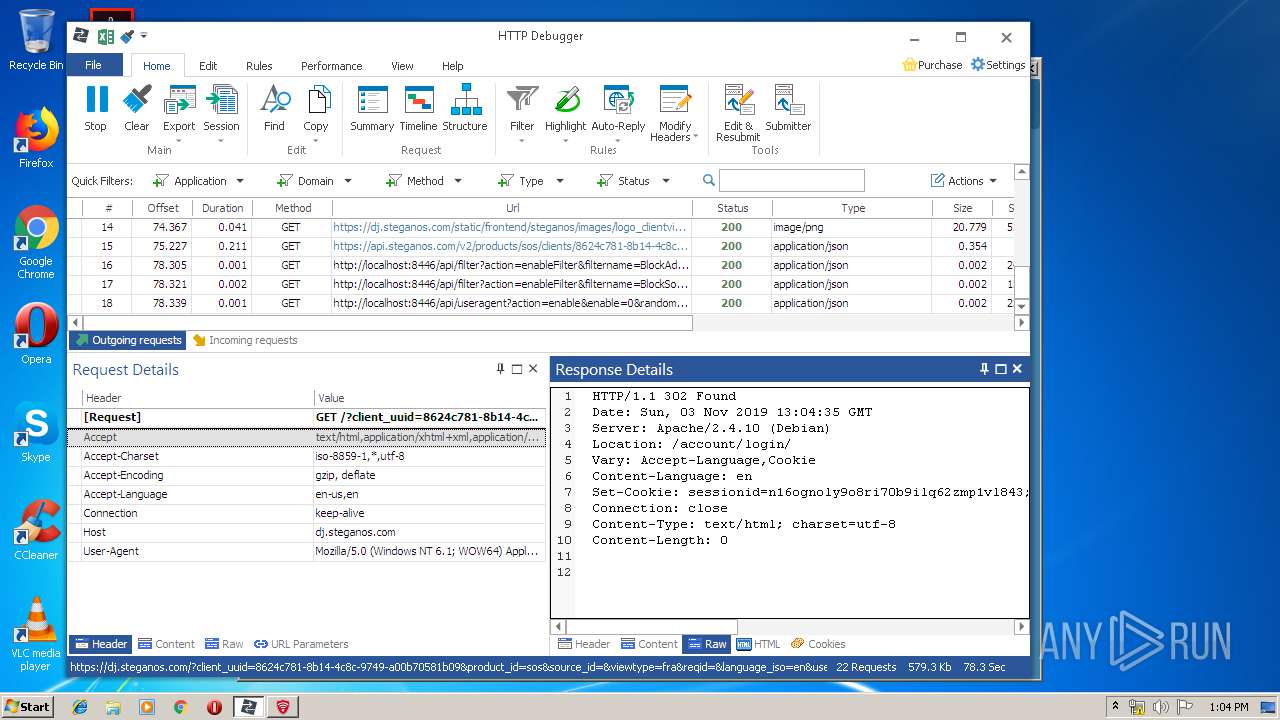
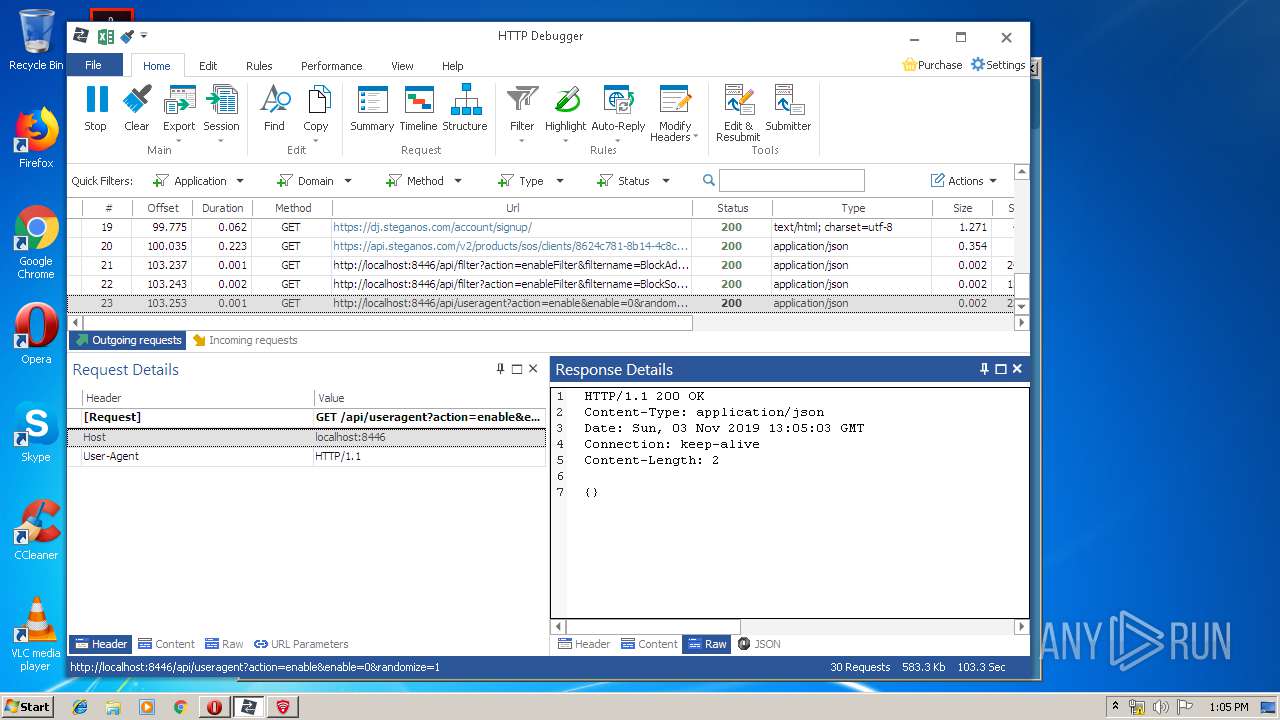
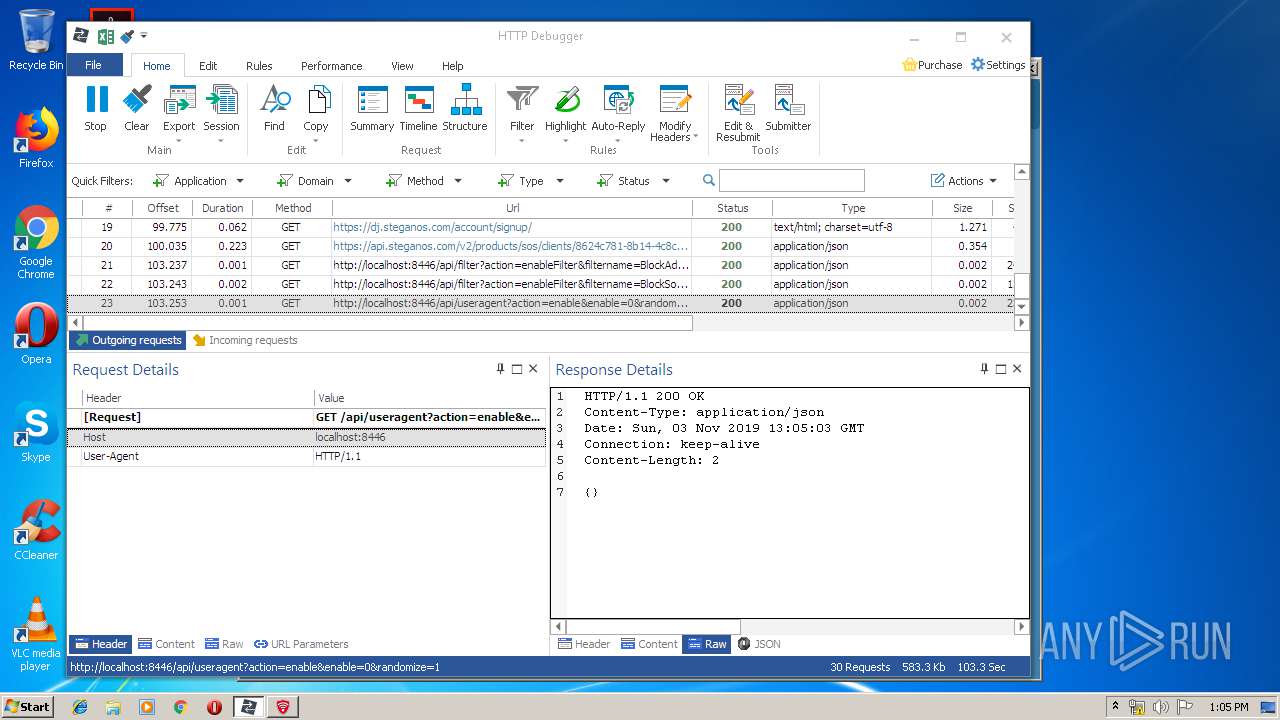
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
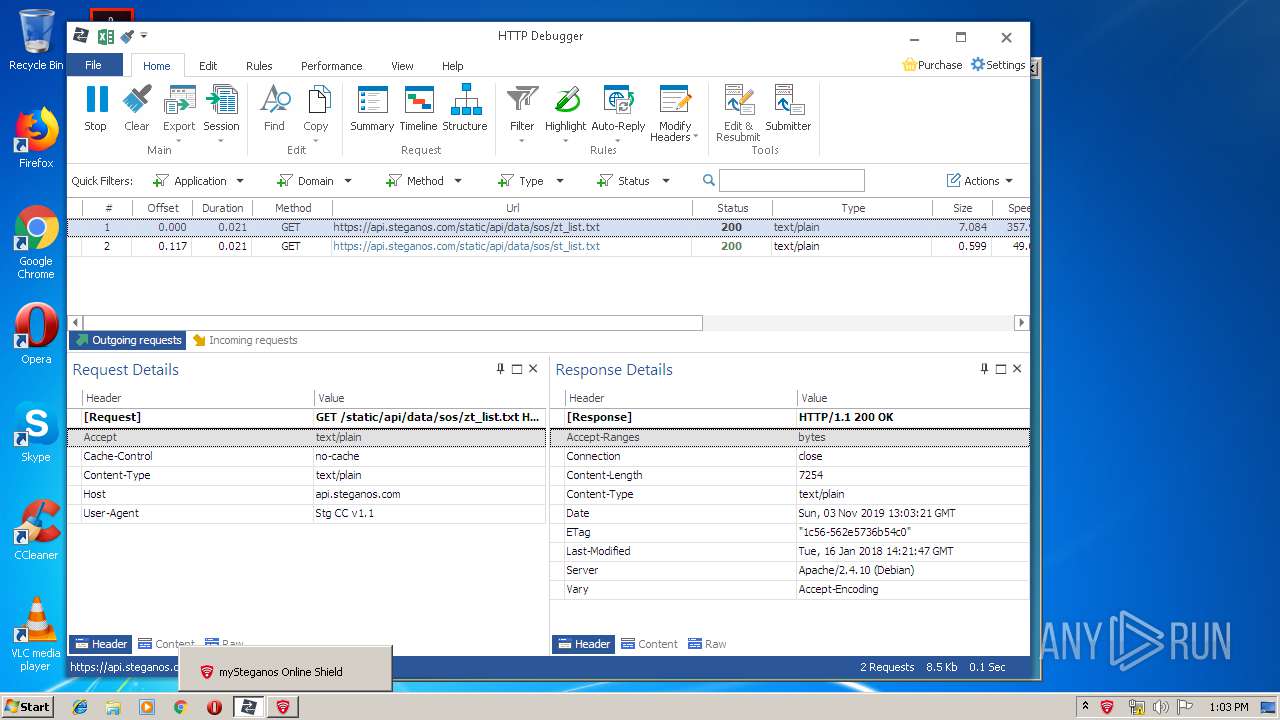
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
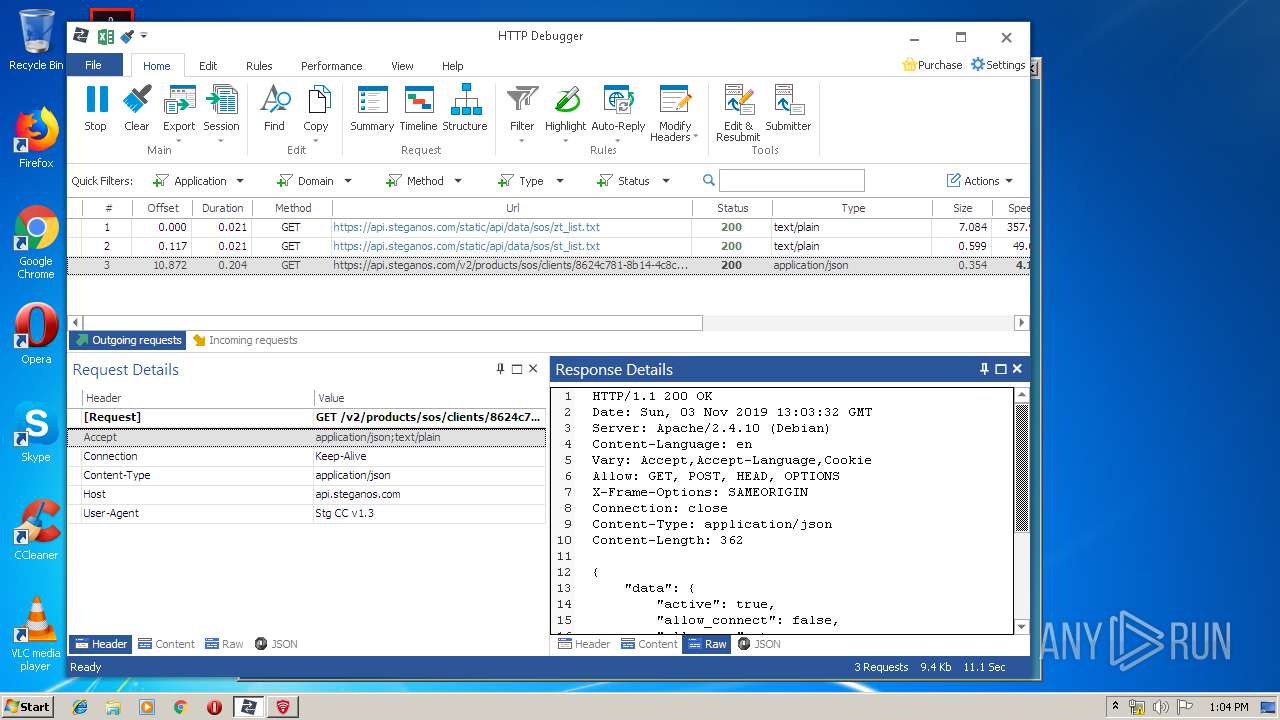
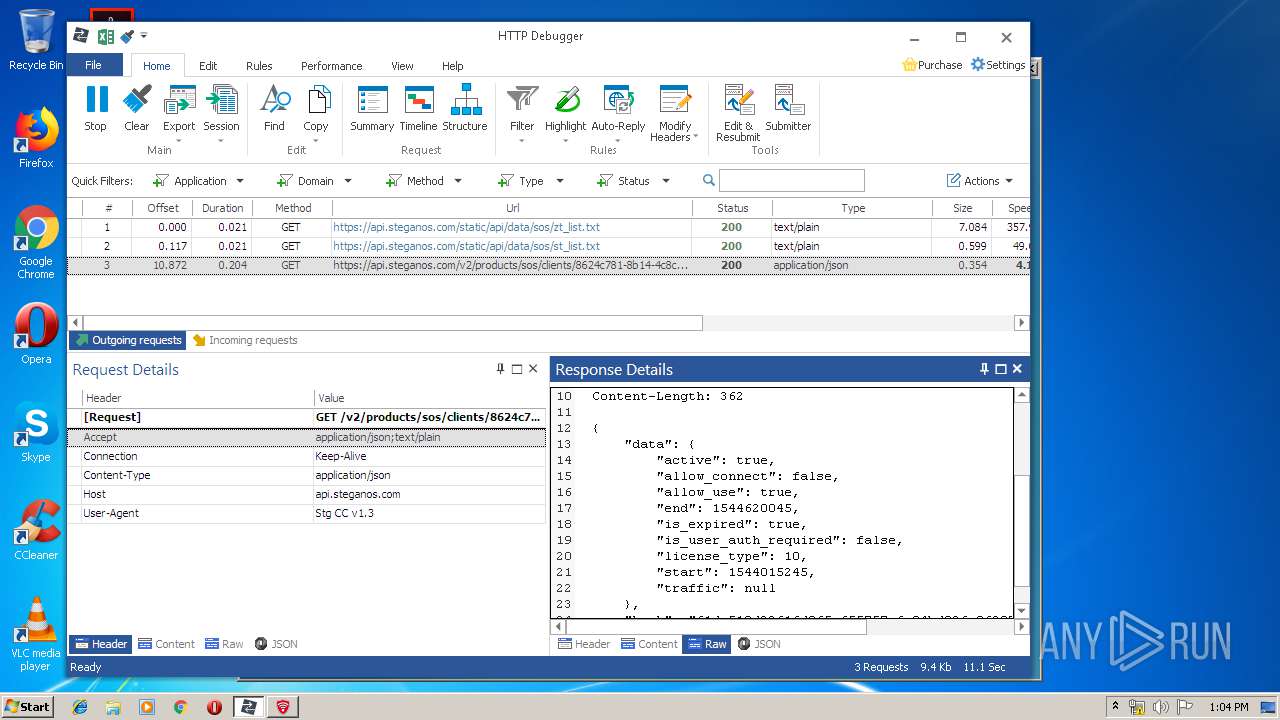
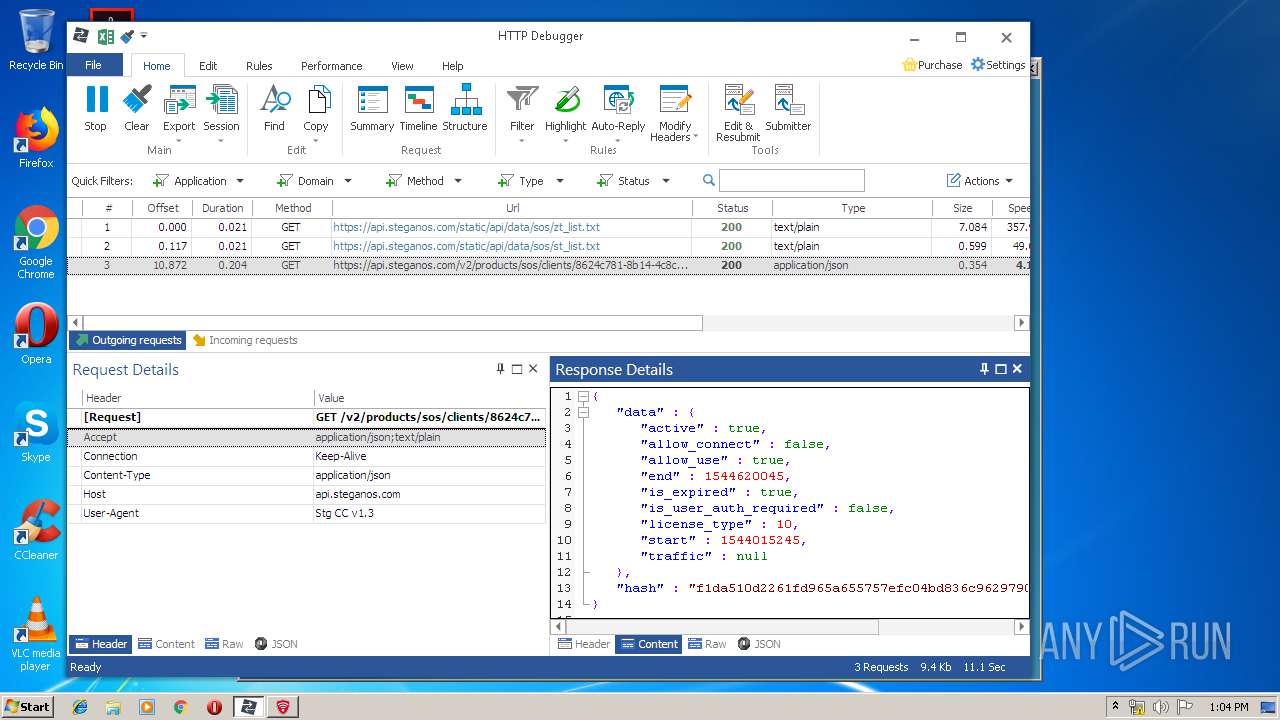
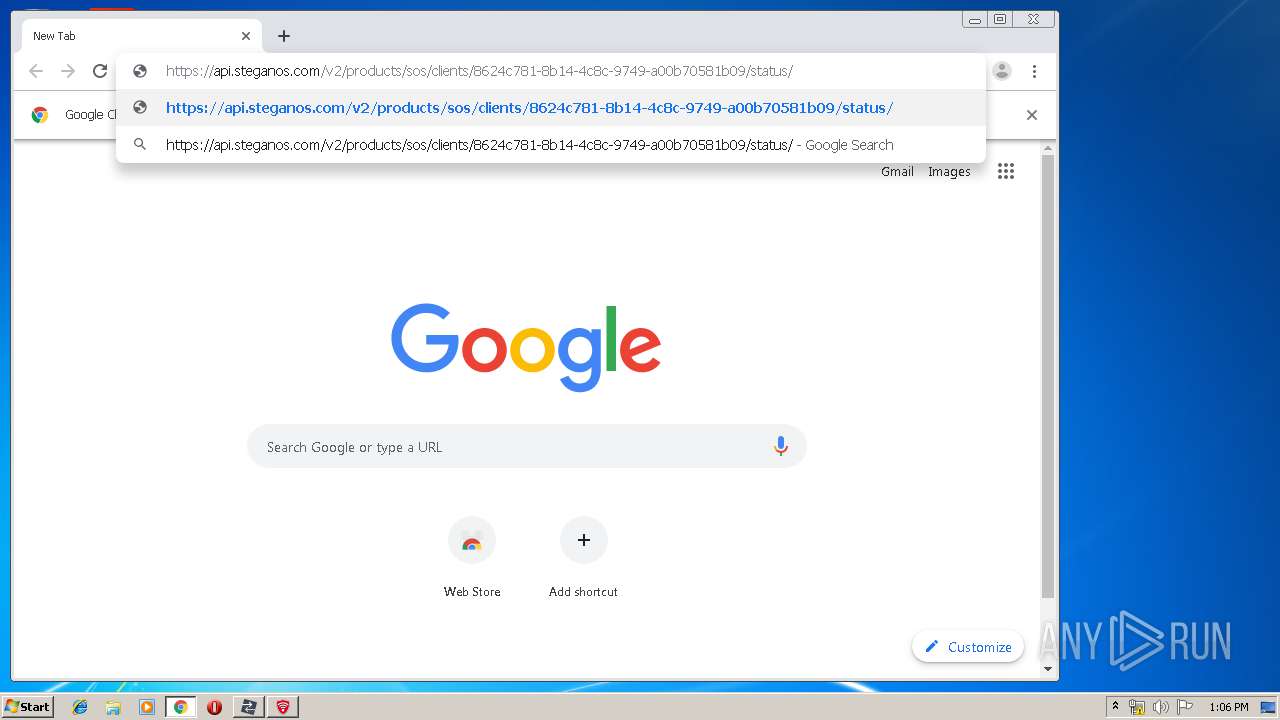
4848 | chrome.exe | GET | 200 | 37.208.109.225:80 | http://api.steganos.com/v2/products/sos/clients/8624c781-8b14-4c8c-9749-a00b70581b09/status/ | DE | text | 362 b | suspicious |
3968 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2380 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
4848 | chrome.exe | GET | 200 | 173.194.188.135:80 | http://r2---sn-4g5ednsz.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=89.187.165.52&mm=28&mn=sn-4g5ednsz&ms=nvh&mt=1572786264&mv=m&mvi=1&pl=25&shardbypass=yes | US | crx | 862 Kb | whitelisted |
3968 | firefox.exe | POST | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsalphasha2g2 | US | der | 1.49 Kb | whitelisted |
4848 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 514 b | whitelisted |
3968 | firefox.exe | POST | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
4848 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 509 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3968 | firefox.exe | 52.89.218.39:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3968 | firefox.exe | 52.24.113.72:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3968 | firefox.exe | 37.208.111.94:443 | file.steganos.com | uvensys GmbH | DE | suspicious |
3968 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3968 | firefox.exe | 172.217.23.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3968 | firefox.exe | 13.35.253.14:443 | snippets.cdn.mozilla.net | — | US | unknown |
3968 | firefox.exe | 172.217.22.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3968 | firefox.exe | 104.18.21.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
3968 | firefox.exe | 52.222.157.226:443 | firefox.settings.services.mozilla.com | Amazon.com, Inc. | US | whitelisted |
3968 | firefox.exe | 13.32.158.121:443 | content-signature-2.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
file.steganos.com |
| suspicious |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
Threats
Process | Message |
|---|---|
OnlineShieldService.exe | +++ CheckDanglingOpenVPN() |
OnlineShieldService.exe | g_nProxyWatcherTimerID: 1 g_bProxyCheckOnHold: 1 g_dwAutoOn: 0 g_dwRunning: 0 |
OnlineShieldService.exe | CMSETPROXYHOLD:
CMTRM:
|
OnlineShieldService.exe | CServiceParser::ParseProxy() |
OnlineShieldClient.exe | *** Normal IP: |
OnlineShieldClient.exe | 89.187.165.52 |
OnlineShieldClient.exe | *** Anonymous IP (https): |
OnlineShieldClient.exe | 89.187.165.52 |
OnlineShieldService.exe | CMSETRUNNING:
CMTRM:
|
OnlineShieldService.exe | CMSETRUNNING: |