| URL: | https://www.urban-vpn.com/thank-you/ |
| Full analysis: | https://app.any.run/tasks/9bef0bd9-e59a-4338-8d56-f47c46a828a0 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 17:55:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E61314DA51165150D1CDDB97ADBC546B |
| SHA1: | F0232E1B9CD69796B0CE44073E985CFB7A6394F1 |
| SHA256: | 58EC7210ACF7D407255EE0CBCFF87782A3517B6D3252985BE2F75F7BB2D62FB9 |
| SSDEEP: | 3:N8DSLEUKNiOcn:2OLEW |
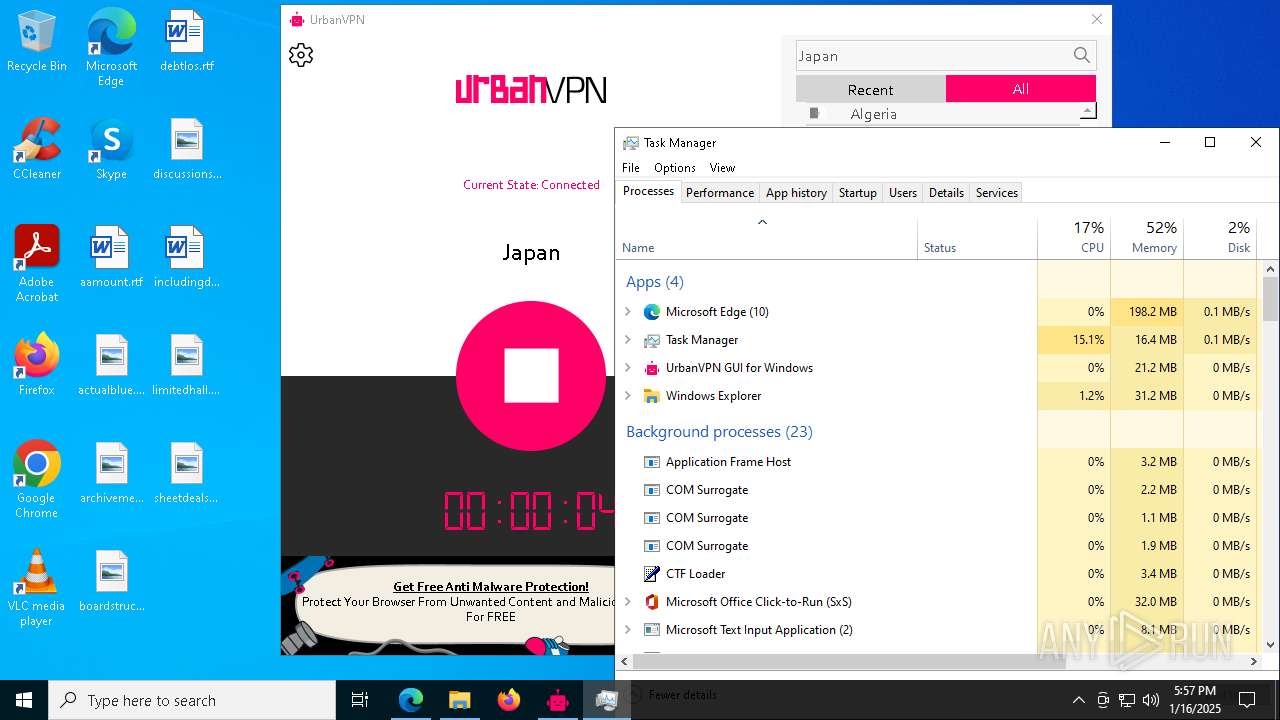
MALICIOUS
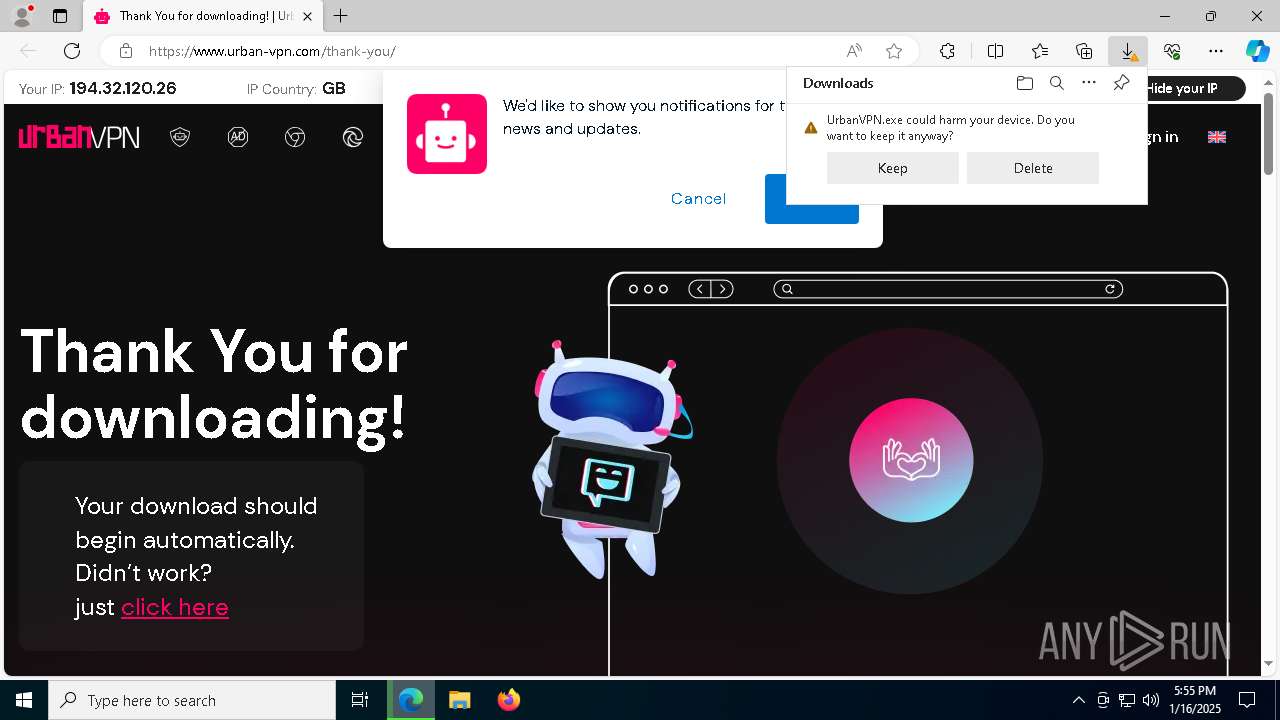
Executing a file with an untrusted certificate
- urbanvpn-gui.exe (PID: 7416)
SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- UrbanVPN.exe (PID: 5576)
Reads the Windows owner or organization settings
- UrbanVPN.exe (PID: 5576)
- msiexec.exe (PID: 6868)
Executable content was dropped or overwritten
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
- MSI2CC1.tmp (PID: 3260)
- tapinstall.exe (PID: 7392)
- drvinst.exe (PID: 7328)
- drvinst.exe (PID: 6644)
Checks for Java to be installed
- msiexec.exe (PID: 7688)
Process drops legitimate windows executable
- msiexec.exe (PID: 7688)
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
Reads Internet Explorer settings
- UrbanVPN.exe (PID: 5576)
Reads security settings of Internet Explorer
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
- tapinstall.exe (PID: 7392)
- MSI3560.tmp (PID: 6812)
Application launched itself
- UrbanVPN.exe (PID: 5576)
Executes as Windows Service
- VSSVC.exe (PID: 7668)
- urbanvpnserv.exe (PID: 7248)
Connects to unusual port
- msiexec.exe (PID: 7816)
- urbanvpnserv.exe (PID: 7248)
Malware-specific behavior (creating "System.dll" in Temp)
- MSI2CC1.tmp (PID: 3260)
Drops a system driver (possible attempt to evade defenses)
- MSI2CC1.tmp (PID: 3260)
- tapinstall.exe (PID: 7392)
- drvinst.exe (PID: 7328)
- drvinst.exe (PID: 6644)
Checks Windows Trust Settings
- tapinstall.exe (PID: 7392)
- drvinst.exe (PID: 7328)
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
Creates a software uninstall entry
- MSI2CC1.tmp (PID: 3260)
INFO
Checks supported languages
- identity_helper.exe (PID: 7456)
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
- msiexec.exe (PID: 7688)
- msiexec.exe (PID: 6868)
- msiexec.exe (PID: 7816)
- drvinst.exe (PID: 7328)
- MSI3560.tmp (PID: 6812)
Executable content was dropped or overwritten
- msedge.exe (PID: 6332)
- msedge.exe (PID: 3848)
- msiexec.exe (PID: 7688)
- msiexec.exe (PID: 6868)
The sample compiled with english language support
- msedge.exe (PID: 3848)
- msedge.exe (PID: 6332)
- msiexec.exe (PID: 7688)
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
- msiexec.exe (PID: 6868)
- MSI2CC1.tmp (PID: 3260)
- tapinstall.exe (PID: 7392)
- drvinst.exe (PID: 7328)
- drvinst.exe (PID: 6644)
Creates files or folders in the user directory
- UrbanVPN.exe (PID: 5576)
Reads Environment values
- identity_helper.exe (PID: 7456)
- UrbanVPN.exe (PID: 5576)
- msiexec.exe (PID: 7688)
- msiexec.exe (PID: 7124)
- UrbanVPNUpdater.exe (PID: 5400)
- UrbanVPN.exe (PID: 4520)
Reads the computer name
- identity_helper.exe (PID: 7456)
- UrbanVPN.exe (PID: 5576)
- msiexec.exe (PID: 7816)
- drvinst.exe (PID: 6644)
- UrbanVPN.exe (PID: 4520)
Checks proxy server information
- UrbanVPN.exe (PID: 5576)
- MSI3560.tmp (PID: 6812)
The process uses the downloaded file
- msedge.exe (PID: 3848)
- UrbanVPN.exe (PID: 5576)
- MSI3560.tmp (PID: 6812)
Reads the software policy settings
- UrbanVPN.exe (PID: 5576)
- UrbanVPNUpdater.exe (PID: 5400)
- urbanvpn-gui.exe (PID: 7416)
- UrbanVPN.exe (PID: 4520)
Application launched itself
- msedge.exe (PID: 3848)
- msiexec.exe (PID: 6868)
Reads Microsoft Office registry keys
- msiexec.exe (PID: 7688)
Create files in a temporary directory
- UrbanVPN.exe (PID: 5576)
- msiexec.exe (PID: 7688)
- msiexec.exe (PID: 7124)
- MSI2CC1.tmp (PID: 3260)
- tapinstall.exe (PID: 7392)
- UrbanVPN.exe (PID: 4520)
Process checks computer location settings
- UrbanVPN.exe (PID: 5576)
Manages system restore points
- SrTasks.exe (PID: 3988)
Starts application with an unusual extension
- msiexec.exe (PID: 6868)
Creates files in the program directory
- MSI2CC1.tmp (PID: 3260)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 7392)
- drvinst.exe (PID: 7328)
- UrbanVPN.exe (PID: 5576)
- UrbanVPN.exe (PID: 4520)
Local mutex for internet shortcut management
- MSI3560.tmp (PID: 6812)
Manual execution by a user
- UrbanVPNUpdater.exe (PID: 5400)
- Taskmgr.exe (PID: 8152)
- Taskmgr.exe (PID: 7972)
Creates a software uninstall entry
- msiexec.exe (PID: 6868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
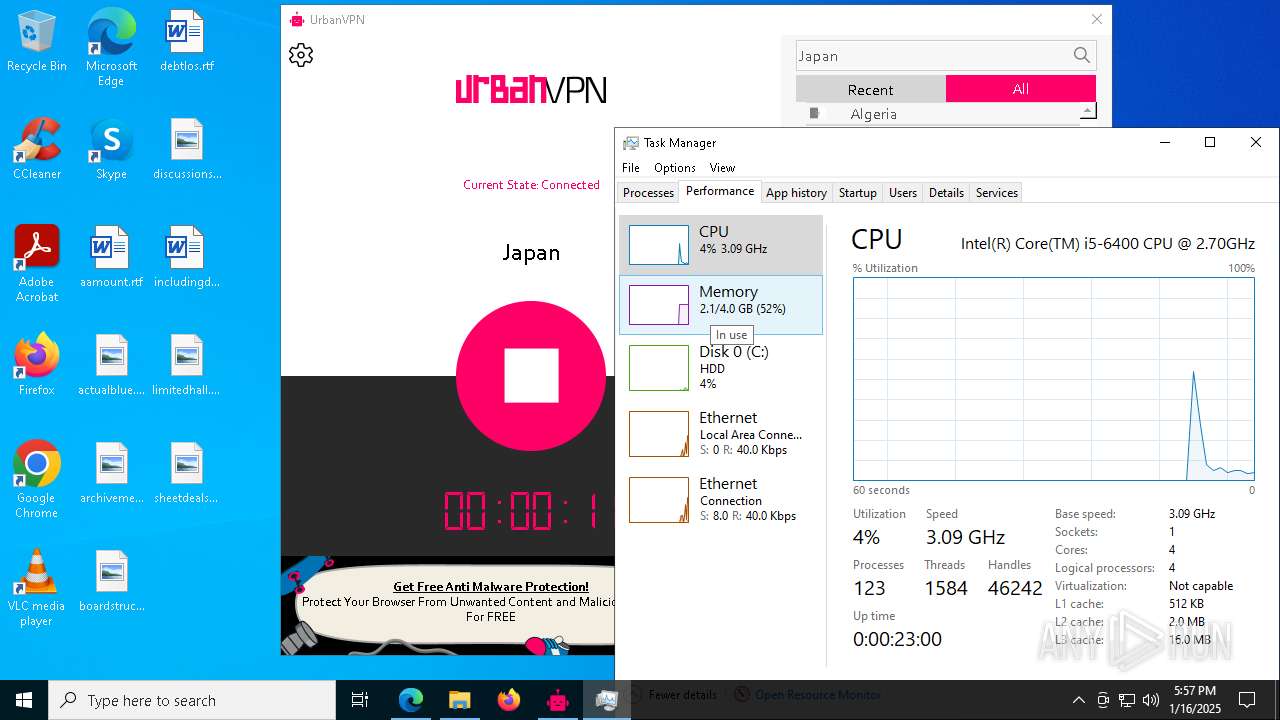
Total processes
212
Monitored processes
77
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6736 --field-trial-handle=2344,i,15245216446867080198,14345922461469404469,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 836 | "C:\Users\admin\Downloads\UrbanVPN.exe" | C:\Users\admin\Downloads\UrbanVPN.exe | — | msedge.exe | |||||||||||
User: admin Company: Urban Security Integrity Level: MEDIUM Description: UrbanVPN Installer Exit code: 3221226540 Version: 2.3.0.3 Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=6972 --field-trial-handle=2344,i,15245216446867080198,14345922461469404469,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | urbanvpn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | urbanvpn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2736 | "C:\Program Files\TAP-Windows\bin\tapinstall.exe" hwids tap0901 | C:\Program Files\TAP-Windows\bin\tapinstall.exe | — | MSI2CC1.tmp | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10011.16384 Modules
| |||||||||||||||
| 3260 | "C:\WINDOWS\Installer\MSI2CC1.tmp" /S /SELECT_UTILITIES=1 | C:\Windows\Installer\MSI2CC1.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3364 | urbanvpn --version | C:\Program Files\UrbanVPN\bin\urbanvpn.exe | — | urbanvpn-gui.exe | |||||||||||
User: admin Company: Urban Cyber Security Inc. Integrity Level: MEDIUM Description: UrbanVPN Daemon Exit code: 1 Version: 2.3.0.0 Modules
| |||||||||||||||
Total events
36 896
Read events
36 404
Write events
461
Delete events
31
Modification events
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3CA8A7C76C8A2F00 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3100B0C76C8A2F00 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263006 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3FEB19B7-BC3A-498F-A504-24DB6A7BEA73} | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263006 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5F51AA0F-FA50-46DE-A4CC-E9FBF891D79E} | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 4B43E1C76C8A2F00 | |||
| (PID) Process: | (3848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263006 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5514F6F8-1840-4558-96A0-59E2BE123C68} | |||
Executable files
110
Suspicious files
371
Text files
95
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135392.TMP | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1353a1.TMP | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1353d0.TMP | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1353ef.TMP | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135392.TMP | — | |
MD5:— | SHA256:— | |||
| 3848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
179
DNS requests
118
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5576 | UrbanVPN.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5576 | UrbanVPN.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAN8OBm6V%2FQ712OcDUKDCyI%3D | unknown | — | — | whitelisted |
7792 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7816 | msiexec.exe | POST | 200 | 148.72.165.78:40004 | http://analytics.urban-vpn.com:40004/tickets | unknown | — | — | unknown |
5576 | UrbanVPN.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7792 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6332 | msedge.exe | 157.240.0.6:443 | connect.facebook.net | — | — | whitelisted |
6332 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6332 | msedge.exe | 142.250.186.99:443 | fonts.gstatic.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.urban-vpn.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7248 | urbanvpnserv.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
7248 | urbanvpnserv.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
7248 | urbanvpnserv.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
Process | Message |
|---|---|
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
UrbanVPNUpdater.exe | Logger::SetLogFile( C:\ProgramData\UrbanVPN\updates\updater.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
UrbanVPNUpdater.exe | Logger::SetLogFile( C:\ProgramData\UrbanVPN\updates\updater.log ) while OLD path is: |
urbanvpn-gui.exe | First instance of UrbanVPN was started.
|