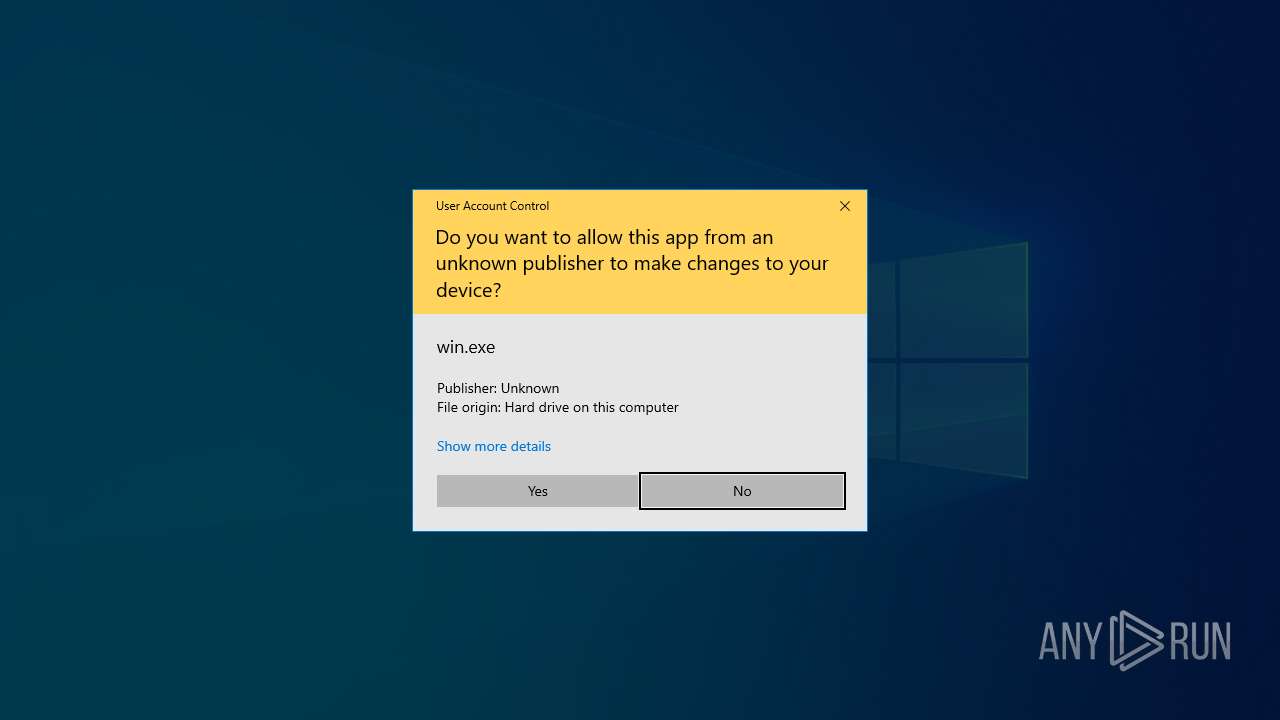
| File name: | win.exe |
| Full analysis: | https://app.any.run/tasks/593504f8-3913-4799-b7f1-24440e157ab5 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 01:50:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed, 3 sections |
| MD5: | 437D4CBF0B72C02E8C630E586816F6F3 |
| SHA1: | 8DBD45C7F06DE4E07149D44897232C04734BF2BE |
| SHA256: | 58D81F355D2C36E5B669CEFFDF7D42615BF1585BE94AE560E38B1FC6C13C9D7C |
| SSDEEP: | 98304:U/0l0uvtJXv1hsbcao2zD8P8AHOgSiSHTqd82deGJTHb4yCjVFkVif4GpfAHj5re:/S |
MALICIOUS
GENERIC has been found (auto)
- win.exe (PID: 3888)
Changes the autorun value in the registry
- win.exe (PID: 3888)
SUSPICIOUS
Executable content was dropped or overwritten
- win.exe (PID: 3888)
The process creates files with name similar to system file names
- win.exe (PID: 3888)
Connects to unusual port
- win.exe (PID: 3888)
Connects to SSH
- win.exe (PID: 3888)
INFO
Launching a file from a Registry key
- win.exe (PID: 3888)
Creates files in the program directory
- win.exe (PID: 3888)
Reads the computer name
- win.exe (PID: 3888)
Checks supported languages
- win.exe (PID: 3888)
Manual execution by a user
- csrss.exe (PID: 3780)
UPX packer has been detected
- win.exe (PID: 3888)
Application based on Golang
- win.exe (PID: 3888)
Detects GO elliptic curve encryption (YARA)
- win.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 1888256 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 3784704 |
| EntryPoint: | 0x569e00 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3780 | C:\ProgramData\Microsoft\csrss.exe | C:\ProgramData\Microsoft\csrss.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3888 | "C:\Users\admin\Desktop\win.exe" | C:\Users\admin\Desktop\win.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
280
Read events
279
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3888) win.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Administrator |
Value: C:\ProgramData\Microsoft\csrss.exe | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | win.exe | C:\ProgramData\Microsoft\csrss.exe | executable | |
MD5:437D4CBF0B72C02E8C630E586816F6F3 | SHA256:58D81F355D2C36E5B669CEFFDF7D42615BF1585BE94AE560E38B1FC6C13C9D7C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
32
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3888 | win.exe | GET | 200 | 156.225.31.188:808 | http://156.225.31.188:808/password.txt | unknown | — | — | malicious |
3740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | win.exe | 156.225.31.188:808 | — | Sun Network Hong Kong Limited - HongKong Backbone | HK | malicious |
3888 | win.exe | 156.225.31.188:8011 | — | Sun Network Hong Kong Limited - HongKong Backbone | HK | malicious |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4944 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 184.24.77.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3888 | win.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
3888 | win.exe | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |