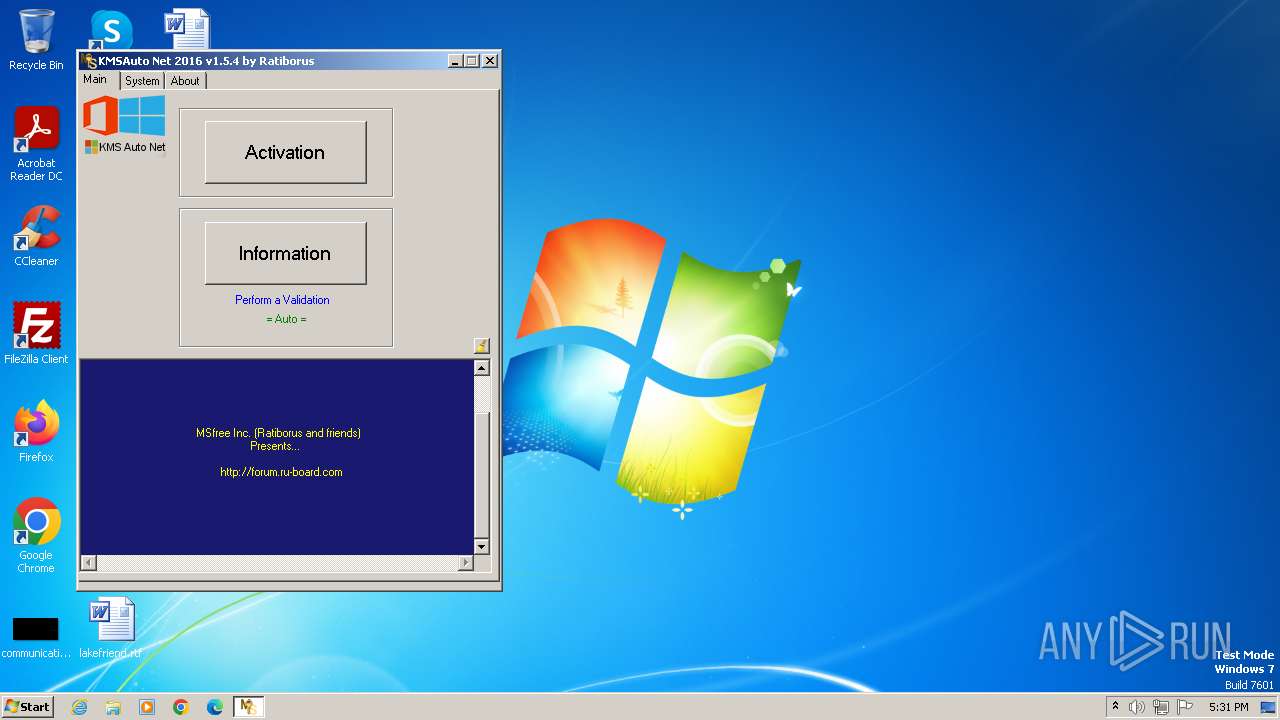
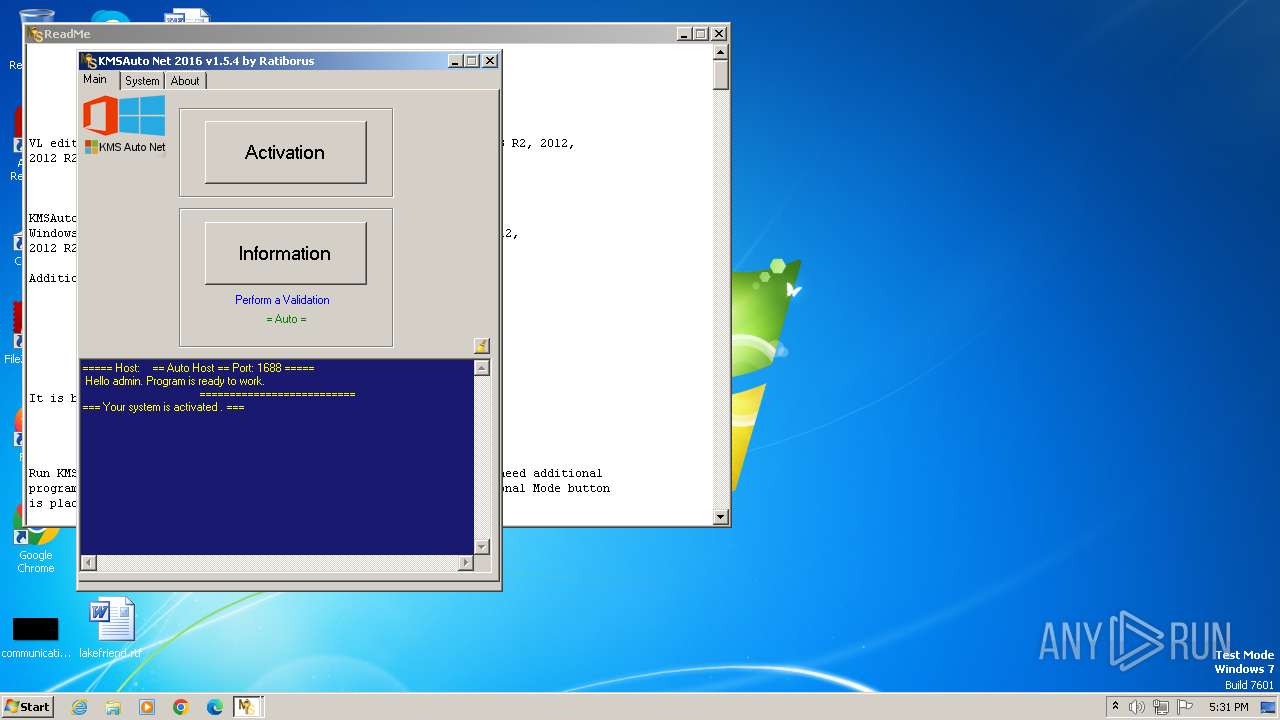
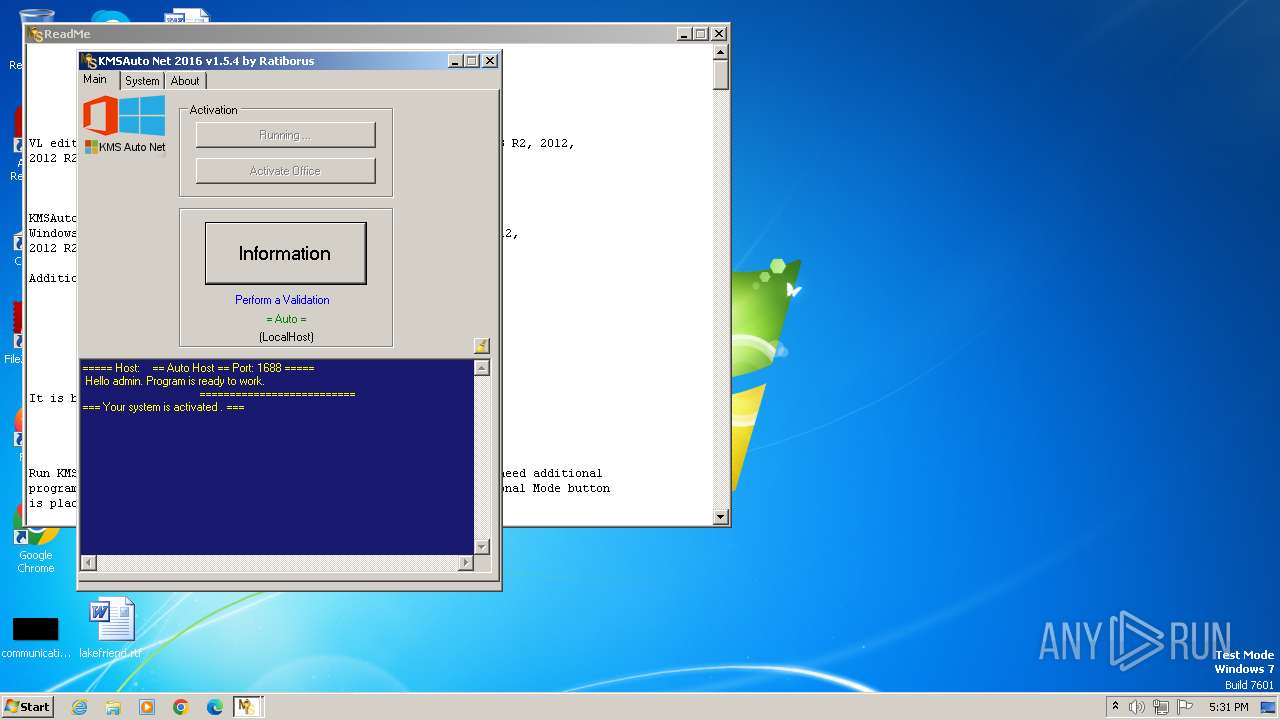
| File name: | KMSAuto Net.exe |
| Full analysis: | https://app.any.run/tasks/03102ab1-7be3-4518-9e5a-ffe1ba43b5fd |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2023, 16:31:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F1FE671BCEFD4630E5ED8B87C9283534 |
| SHA1: | 9FF0546074213231E695E67324ABA64E2E65D2C2 |
| SHA256: | 58D6FEC4BA24C32D38C9A0C7C39DF3CB0E91F500B323E841121D703C7B718681 |
| SSDEEP: | 196608:C38lywCAfywOweqyw3ywsywXywZywnywZywBywEyw4ywwywmIBywyywsyw/ywiyj:EDwCAqwUnwiwxwCwUwywUw8wJwVwtwie |
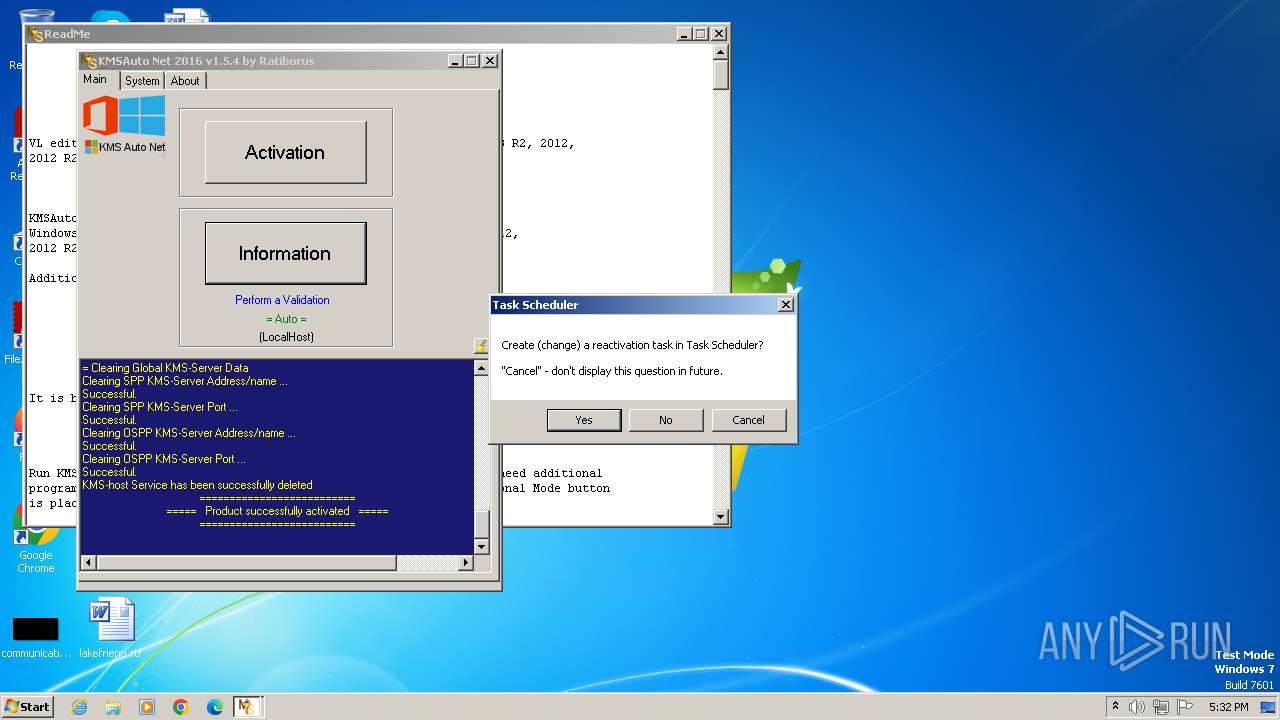
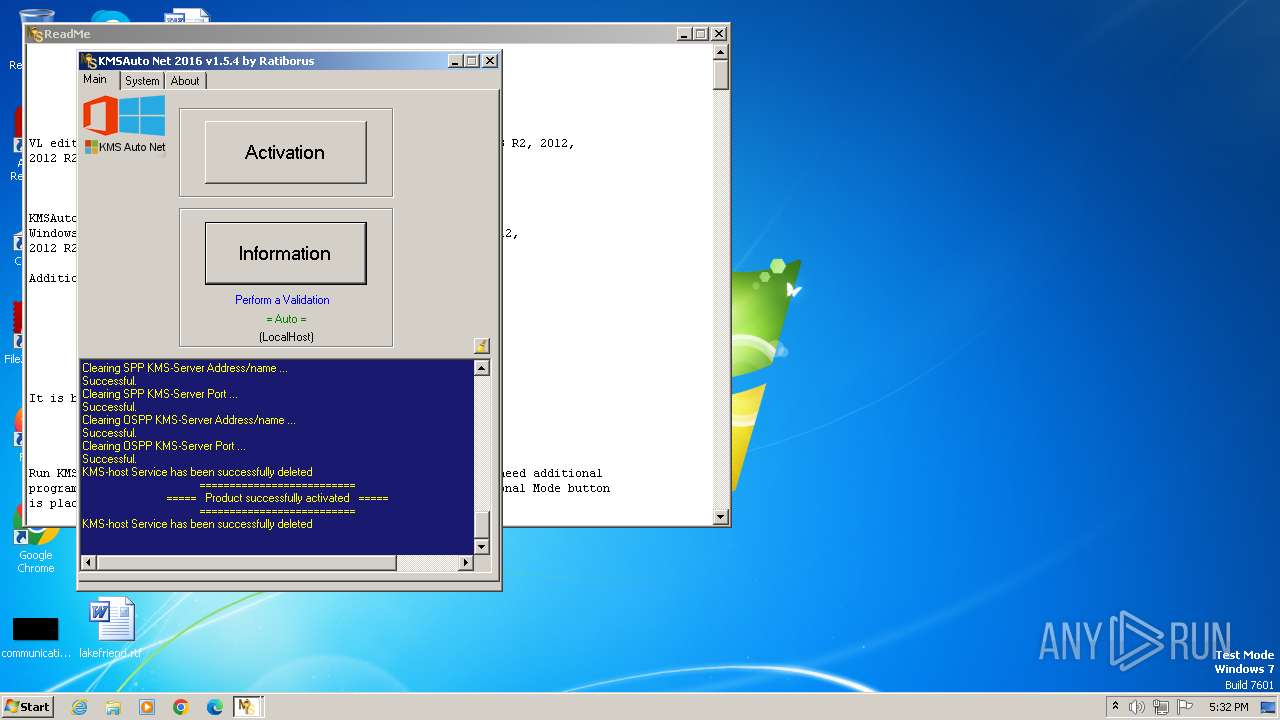
MALICIOUS
Drops the executable file immediately after the start
- wzt.dat (PID: 3284)
- bin.dat (PID: 1560)
- AESDecoder.exe (PID: 2372)
- bin_x86.dat (PID: 2648)
- wzt.dat (PID: 2420)
- AESDecoder.exe (PID: 3832)
- bin.dat (PID: 3840)
- KMSAuto Net.exe (PID: 2184)
- bin_x86.dat (PID: 3564)
Application was dropped or rewritten from another process
- wzt.dat (PID: 3284)
- certmgr.exe (PID: 3296)
- certmgr.exe (PID: 3812)
- bin_x86.dat (PID: 2648)
- bin.dat (PID: 1560)
- KMSSS.exe (PID: 948)
- AESDecoder.exe (PID: 2372)
- wzt.dat (PID: 2420)
- bin.dat (PID: 3840)
- certmgr.exe (PID: 3636)
- certmgr.exe (PID: 2800)
- AESDecoder.exe (PID: 3832)
- bin_x86.dat (PID: 3564)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3008)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 1232)
- cmd.exe (PID: 120)
SUSPICIOUS
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 2184)
- cmd.exe (PID: 3168)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 2184)
Process drops legitimate windows executable
- wzt.dat (PID: 3284)
- bin_x86.dat (PID: 2648)
- wzt.dat (PID: 2420)
- bin_x86.dat (PID: 3564)
Starts application with an unusual extension
- cmd.exe (PID: 1632)
- cmd.exe (PID: 2752)
- cmd.exe (PID: 3540)
- cmd.exe (PID: 888)
- cmd.exe (PID: 1240)
- cmd.exe (PID: 2212)
Drops a system driver (possible attempt to evade defenses)
- bin_x86.dat (PID: 2648)
- bin_x86.dat (PID: 3564)
Application launched itself
- cmd.exe (PID: 3168)
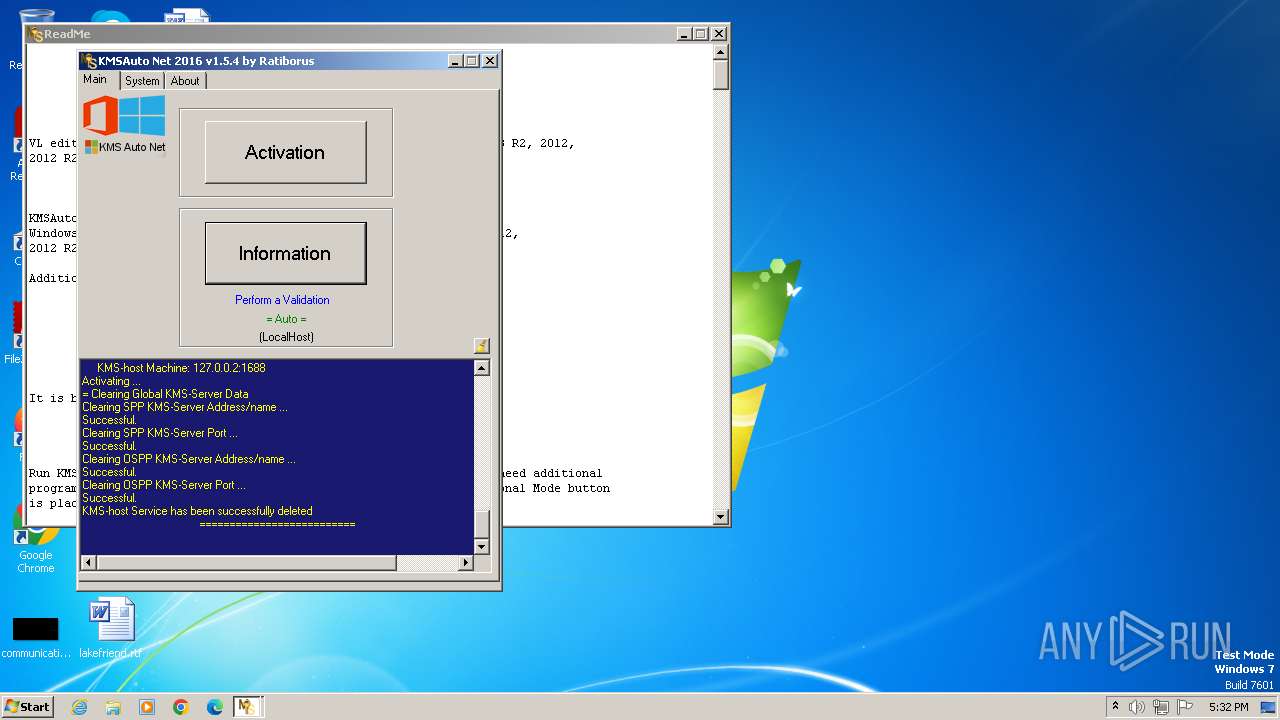
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2184)
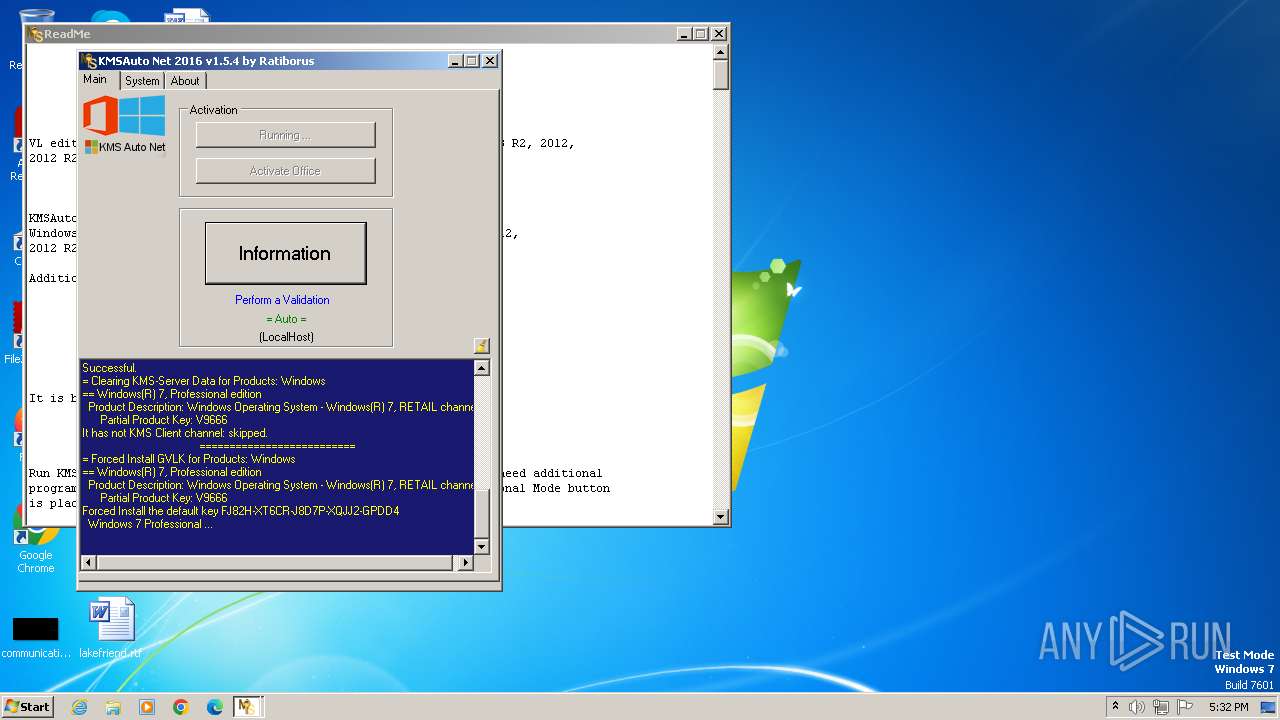
Executes as Windows Service
- KMSSS.exe (PID: 948)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 2184)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 2184)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2184)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 2184)
- cmd.exe (PID: 3244)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 2184)
INFO
Reads the computer name
- KMSAuto Net.exe (PID: 2184)
- KMSSS.exe (PID: 948)
- wmpnscfg.exe (PID: 3084)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 2184)
Checks supported languages
- KMSAuto Net.exe (PID: 2184)
- wzt.dat (PID: 3284)
- certmgr.exe (PID: 3812)
- bin.dat (PID: 1560)
- certmgr.exe (PID: 3296)
- AESDecoder.exe (PID: 2372)
- bin_x86.dat (PID: 2648)
- KMSSS.exe (PID: 948)
- wmpnscfg.exe (PID: 3084)
- wzt.dat (PID: 2420)
- certmgr.exe (PID: 3636)
- certmgr.exe (PID: 2800)
- bin.dat (PID: 3840)
- AESDecoder.exe (PID: 3832)
- bin_x86.dat (PID: 3564)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 2184)
- KMSSS.exe (PID: 948)
- wmpnscfg.exe (PID: 3084)
Reads Environment values
- KMSAuto Net.exe (PID: 2184)
Creates files in the program directory
- cmd.exe (PID: 3476)
- AESDecoder.exe (PID: 2372)
- bin.dat (PID: 1560)
- bin_x86.dat (PID: 2648)
- KMSSS.exe (PID: 948)
- cmd.exe (PID: 2388)
- wzt.dat (PID: 2420)
- bin.dat (PID: 3840)
- AESDecoder.exe (PID: 3832)
- KMSAuto Net.exe (PID: 2184)
- wzt.dat (PID: 3284)
- bin_x86.dat (PID: 3564)
Manual execution by a user
- wmpnscfg.exe (PID: 3084)
Reads product name
- KMSAuto Net.exe (PID: 2184)
Create files in a temporary directory
- KMSAuto Net.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (33.3) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (32.6) |
| .scr | | | Windows screen saver (15.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.9) |
| .exe | | | Win32 Executable (generic) (5.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:10:15 08:57:50+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 8259584 |
| InitializedDataSize: | 49152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7e2656 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.4.0 |
| ProductVersionNumber: | 1.5.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | MSFree Inc. |
| FileDescription: | KMSAuto Net |
| FileVersion: | 1.5.4 |
| InternalName: | KMSAuto Net.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | KMSAuto Net.exe |
| ProductName: | KMSAuto Net |
| ProductVersion: | 1.5.4 |
| AssemblyVersion: | 1.5.4.0 |
Total processes
183
Monitored processes
83
Malicious processes
21
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\System32\cmd /c schtasks.exe /change /TN KMSAutoNet /RI 14400 | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 240 | C:\Windows\System32\cmd.exe /D /c del /F /Q "test.test" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 888 | C:\Windows\System32\cmd.exe /D /c bin.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 940 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55C92734-D682-4D71-983E-D6EC3F16059F" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\ProgramData\KMSAuto\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID -AI 43200 -RI 43200 -Log -IP | C:\ProgramData\KMSAuto\bin\KMSSS.exe | — | services.exe | |||||||||||
User: SYSTEM Company: MSFree Inc. Integrity Level: SYSTEM Description: KMS emulator by Ratiborus. Exit code: 0 Version: 2.0.7.0 Modules
| |||||||||||||||
| 1048 | C:\Windows\System32\cmd.exe /D /c del /F /Q "kmsauto.ini" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | C:\Windows\System32\cmd /c schtasks.exe /create /TN KMSAutoNet /XML xmlfile.xml | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1240 | C:\Windows\System32\cmd.exe /D /c bin_x86.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1536 | C:\Windows\System32\cmd.exe /D /c del /F /Q "bin_x86.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1560 | bin.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin.dat | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
Total events
5 793
Read events
5 603
Write events
177
Delete events
13
Modification events
| (PID) Process: | (1836) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3560) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
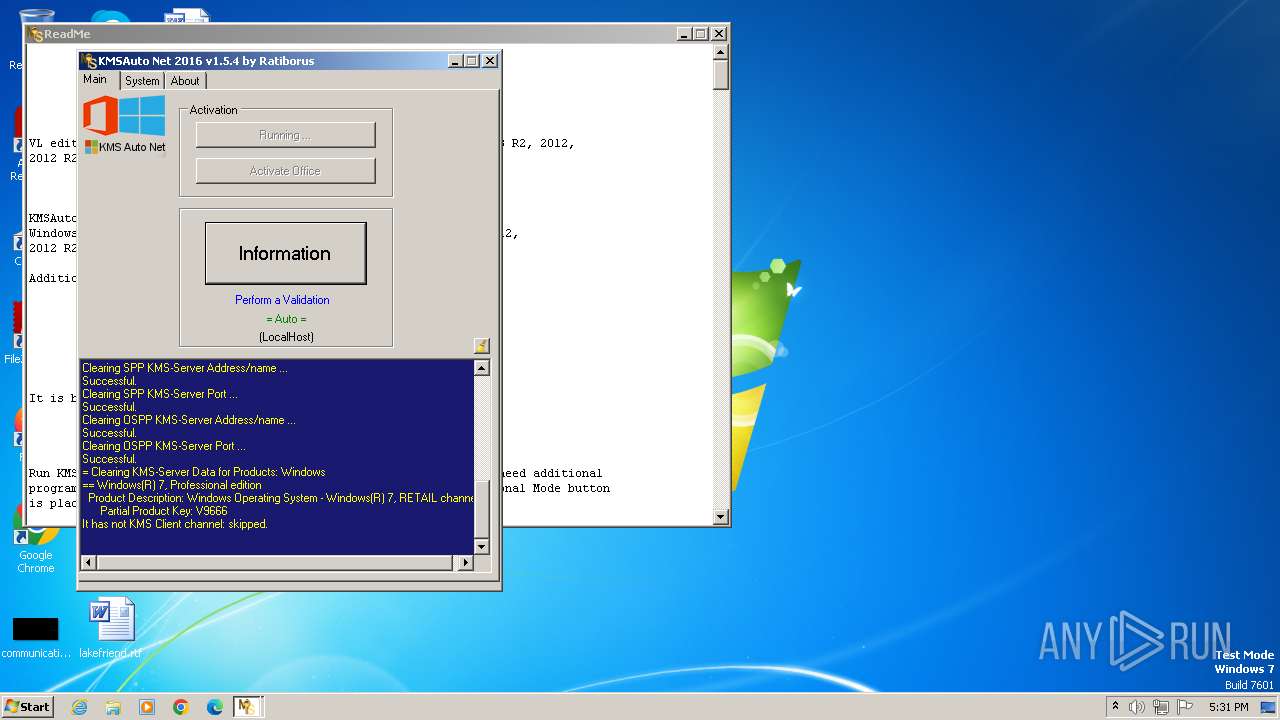
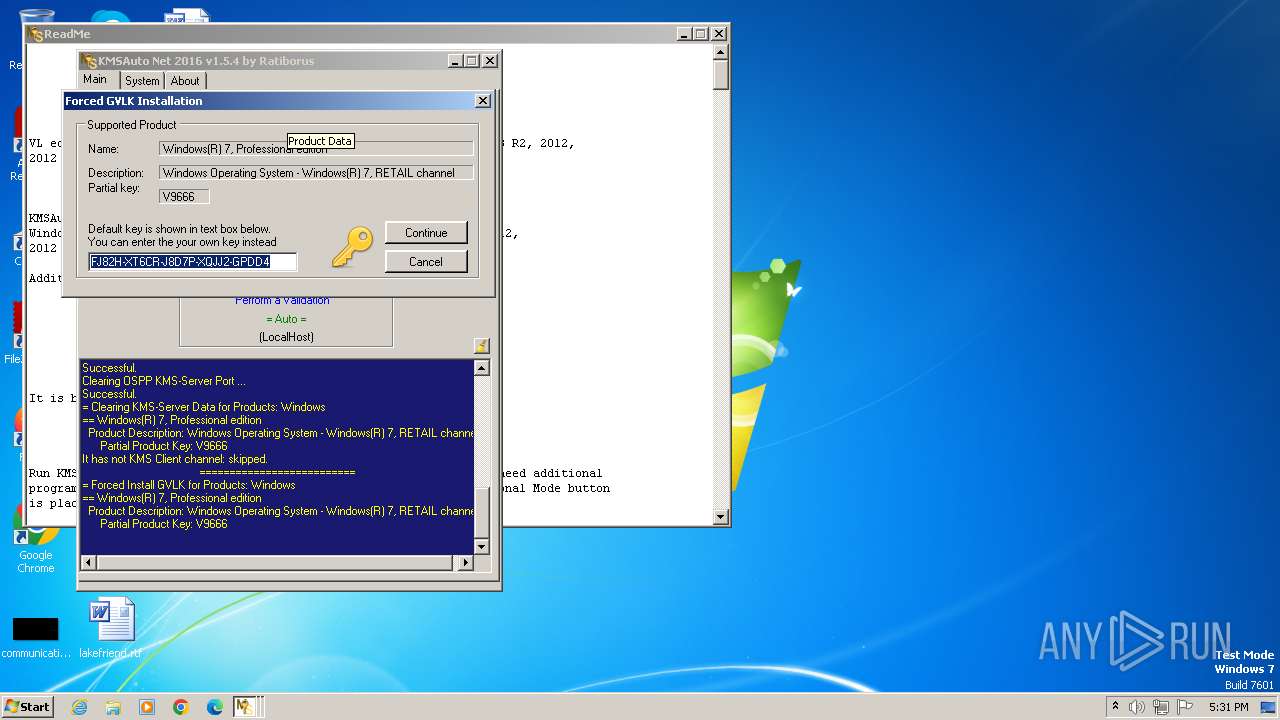
| (PID) Process: | (2184) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\KMSEmulator |
| Operation: | write | Name: | ImagePath |
Value: temp.exe | |||
| (PID) Process: | (2184) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | delete value | Name: | KeyManagementServiceName |
Value: 127.0.0.2 | |||
| (PID) Process: | (2184) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | delete value | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (2184) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform |
| Operation: | delete value | Name: | KeyManagementServiceName |
Value: 127.0.0.2 | |||
| (PID) Process: | (2184) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform |
| Operation: | delete value | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (3084) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1C2A8177-C7BE-45DA-9B6D-A1620AD897FD}\{61E6F204-A64F-48CD-9794-31014319A722} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3084) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1C2A8177-C7BE-45DA-9B6D-A1620AD897FD} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3084) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{DFB335DC-4680-48EA-90A1-73C5C494D93F} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
36
Suspicious files
17
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 2184 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin.dat | executable | |
MD5:4D2E5AFFE6D1CCB42F6650FD57448A9B | SHA256:3CBF7C0231B3266B4A6946DCF9AAA39C2BF077F6E459CA9EAD39C516CBFCE74C | |||
| 2184 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 3284 | wzt.dat | C:\ProgramData\KMSAuto\wzt\certmgr.exe | executable | |
MD5:9D4F1124B2D870583268D19317D564AE | SHA256:EBAD2237B3E7CDF65385CCCE5099E82C7EC5080E737C97CE4E542CDBEA8D418D | |||
| 3284 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | binary | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
| 2844 | cmd.exe | C:\Users\admin\AppData\Local\Temp\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 2184 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin_x86.dat | executable | |
MD5:6C227B04F0605AF1A1B75F8FE16D1424 | SHA256:DCFDAB4ED4F5E5A821EB8FF9E85453A426AF3E725A0849CC4B0599746C879456 | |||
| 2648 | bin_x86.dat | C:\ProgramData\KMSAuto\bin\driver\x86TAP2\tapoas.cat | binary | |
MD5:F06DEB48D9149B3227C09FE4B9C3615E | SHA256:EC8A15EBD17E56F60851C557119E81A7F6EAAAB871ABFE9685926DF0C7AA6D4E | |||
| 2648 | bin_x86.dat | C:\ProgramData\KMSAuto\bin\driver\oas_sert.cer | binary | |
MD5:0041584E5F66762B1FA9BE8910D0B92B | SHA256:BB27684B569CBB72DEC63EA6FDEF8E5F410CDAEB73717EEE1B36478DBCFF94CC | |||
| 2648 | bin_x86.dat | C:\ProgramData\KMSAuto\bin\driver\x86TAP2\oas_sert.cer | binary | |
MD5:0041584E5F66762B1FA9BE8910D0B92B | SHA256:BB27684B569CBB72DEC63EA6FDEF8E5F410CDAEB73717EEE1B36478DBCFF94CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |