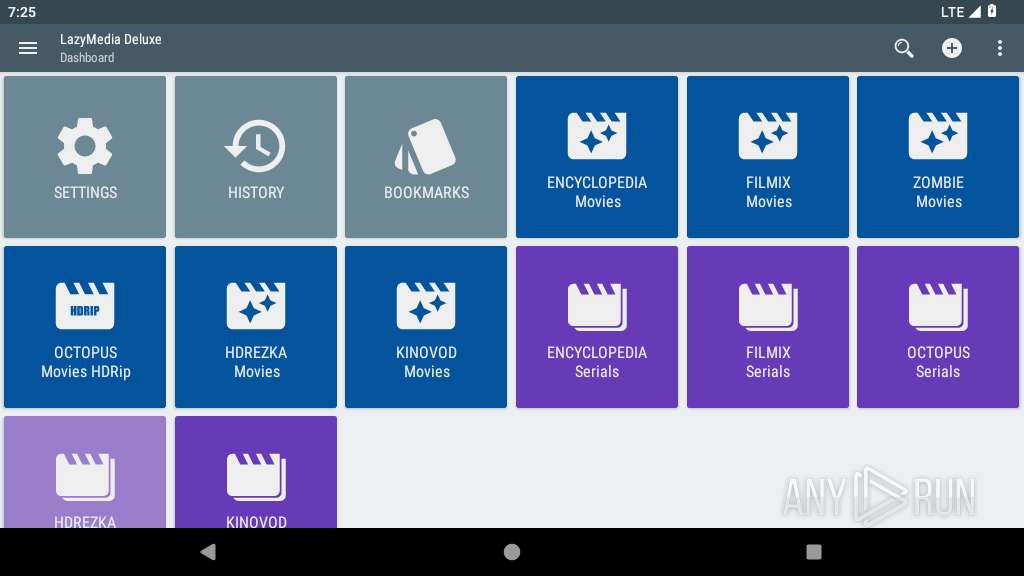
| File name: | LazyMedia+Deluxe+Pro+3.381-@EasyAPK.apk |
| Full analysis: | https://app.any.run/tasks/4e8376fd-6e45-4106-81ee-1e924d2ed89d |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | April 23, 2025, 19:24:36 |
| OS: | Android 14 |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FFD7CDDB5673C4659BC91D2E0B4AC8B9 |
| SHA1: | CB31EC736764045F824731631D2E98493BD7899A |
| SHA256: | 58CE1C37CBCD0BBB2797953580DA56435654A2AA9C2E0480E1548270E2375095 |
| SSDEEP: | 98304:VS+AaZ2XnDBlbkJLczdCZNOkEuz9KqNPa9lGtvDEGwXAwpEg5C9pKThacfyLdwVu:t091XnDFqHevtkdN91 |
MALICIOUS
Hides app icon from display
- app_process64 (PID: 2346)
SUSPICIOUS
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2273)
- app_process64 (PID: 2346)
Accesses system-level resources
- app_process64 (PID: 2346)
- app_process64 (PID: 2273)
Connects to the server without a host name
- app_process64 (PID: 2273)
- app_process64 (PID: 2346)
Checks for external IP
- netd (PID: 341)
- app_process64 (PID: 2273)
- app_process64 (PID: 2346)
Process requests binary or script from the Internet
- app_process64 (PID: 2346)
- app_process64 (PID: 2273)
Launches a new activity
- app_process64 (PID: 2346)
- app_process64 (PID: 2273)
Sets file permissions, owner, and group for a specified path
- app_process64 (PID: 2346)
INFO
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2273)
- app_process64 (PID: 2346)
Stores data using SQLite database
- app_process64 (PID: 2273)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2273)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2346)
Retrieves the value of a global system setting
- app_process64 (PID: 2346)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:20 10:28:44 |
| ZipCRC: | 0x4a754e02 |
| ZipCompressedSize: | 10380 |
| ZipUncompressedSize: | 58080 |
| ZipFileName: | AndroidManifest.xml |
Total processes
127
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 341 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN | ||||
| 2273 | com.lazycatsoftware.lmd | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2346 | com.lazycatsoftware.lmd | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2273 | app_process64 | /data/user/0/com.lazycatsoftware.lmd/no_backup/androidx.work.workdb-journal | binary | |
MD5:— | SHA256:— | |||
| 2273 | app_process64 | /data/user/0/com.lazycatsoftware.lmd/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2273 | app_process64 | /data/user/0/com.lazycatsoftware.lmd/cache/oat_primary/arm64/base.2273.tmp | binary | |
MD5:— | SHA256:— | |||
| 2346 | app_process64 | /data/user/0/com.lazycatsoftware.lmd/cache/oat_primary/arm64/base.art | binary | |
MD5:— | SHA256:— | |||
| 2346 | app_process64 | /data/user/0/com.lazycatsoftware.lmd/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
24
DNS requests
12
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 172.217.18.99:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
2273 | app_process64 | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | whitelisted |
2273 | app_process64 | GET | 200 | 81.171.24.23:80 | http://lazycatsoftware.com/lazymediadeluxe/urls_lmd.json | unknown | — | — | unknown |
2273 | app_process64 | POST | 200 | 5.61.56.18:80 | http://5.61.56.18/partner_api/request-token | unknown | — | — | unknown |
2273 | app_process64 | GET | 200 | 5.61.56.18:80 | http://5.61.56.18/partner_api/profile/login | unknown | — | — | unknown |
2346 | app_process64 | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | whitelisted |
2346 | app_process64 | GET | 200 | 81.171.24.23:80 | http://lazycatsoftware.com/lazymediadeluxe/urls_lmd.json | unknown | — | — | unknown |
2346 | app_process64 | POST | 200 | 5.61.56.18:80 | http://5.61.56.18/partner_api/request-token | unknown | — | — | unknown |
2346 | app_process64 | GET | 200 | 5.61.56.18:80 | http://5.61.56.18/partner_api/profile/login | unknown | — | — | unknown |
2346 | app_process64 | GET | 200 | 81.171.24.23:80 | http://lazycatsoftware.com/lazymediadeluxe/update_lmd.json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
445 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 172.217.18.99:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.132:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 64.233.184.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
— | — | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
2273 | app_process64 | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
2273 | app_process64 | 81.171.24.23:80 | lazycatsoftware.com | LeaseWeb Netherlands B.V. | NL | unknown |
2273 | app_process64 | 104.26.12.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
2273 | app_process64 | 5.61.56.18:80 | — | Scalaxy B.V. | NL | unknown |
2273 | app_process64 | 82.221.128.102:443 | hdrzk.org | Advania Island ehf | IS | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
ip-api.com |
| whitelisted |
lazycatsoftware.com |
| unknown |
api.ipify.org |
| shared |
hdrzk.org |
| unknown |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
341 | netd | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
341 | netd | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2273 | app_process64 | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
341 | netd | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2273 | app_process64 | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
341 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2346 | app_process64 | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2346 | app_process64 | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
341 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |