| URL: | ppo.webredirect.org |
| Full analysis: | https://app.any.run/tasks/72127bc2-e7f1-4fe0-bbf8-50eab5eabc5a |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 06:58:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A8D4B1879C5C4CBF714117A1DBD0F78B |
| SHA1: | 2C62AA2B473E08A6C14A26910E49C8CCAF092691 |
| SHA256: | 58CB67BAE1E6A8EB60AFB7265E5D684763B0A477525ED09D491707BBE047EADD |
| SSDEEP: | 3:viXA6XA7S:viiO |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 2312)
Checks supported languages
- wmpnscfg.exe (PID: 2312)
Application launched itself
- iexplore.exe (PID: 3972)
Manual execution by a user
- wmpnscfg.exe (PID: 2312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2312 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Internet Explorer\iexplore.exe" "ppo.webredirect.org" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3972 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
18 326
Read events
18 200
Write events
91
Delete events
35
Modification events
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 581100176 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31104094 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 881420176 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31104094 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
21
Text files
39
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\TYX336G5.htm | html | |
MD5:A21053A190E02BB3915184E07A024034 | SHA256:D2EA3A8230301DB5FC74F06D2CEFF1F9C09C973369D753FFF3EC2A0347F61E42 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ltr[1].css | text | |
MD5:B2614E79E613F992A686CC22BE4FB227 | SHA256:2CD1EFC1A5E8BE71C8C8B2120C2D6BA037392D7C92CF7A22EA34D2A0D4EFD343 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\main[1].css | text | |
MD5:CB0062449FE9952D067117A91F14ECE5 | SHA256:C0C2730AA9B3020C67D0015F094F8C50393BCE6DBE9817A2CE1AD3F1CEF51458 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\animate[1].css | text | |
MD5:D96B2083B0ACBB11911BB4F068158299 | SHA256:8150A6E66442996F64560B128D0EFFE532ED5EABDF0A8C6176C8C4E8ED502E6F | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery-1.8.1.min[1].js | s | |
MD5:E7155EE7C8C9898B6D4F2A9A12A1288E | SHA256:FC184F96DD18794E204C41075A00923BE7E8E568744231D74F2FDF8921F78D29 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\custom[1].js | binary | |
MD5:09B9BE2CE6C6AE9F0A0596641DCE6722 | SHA256:2D0B26C6F46575140B0DF2CFE9201999FD55F5A5E4992E3788E858CC2ECF9782 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D40A17D8FD35E460639BCC3AC7B0D079 | SHA256:61FD6009CC59F6FC5A28A05BD50B159541F845D5DEE27CCA77D83CC55DF90688 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\s-world[1].png | image | |
MD5:1A78ACBB008D1D2A562D11C27B85B3F4 | SHA256:C2232738BEE5BB9F86CA6CC6833B5426FB5A39B22FA7127FDB1B7B98E5EDAA07 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\layerslider[1].css | text | |
MD5:8FA51CA4B04B369D34D5A12C57CB9C03 | SHA256:5E1C8334F722E390A1F1F45D896EB36668C5339478CE9C929DBFEFB3FF1625DB | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:1954F91D1857433A6E671FC2134627C4 | SHA256:1900C86CF885B5A30F4C6978DB628CAA35291D0EA1C37ADA12638FADADB66467 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
42
DNS requests
21
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
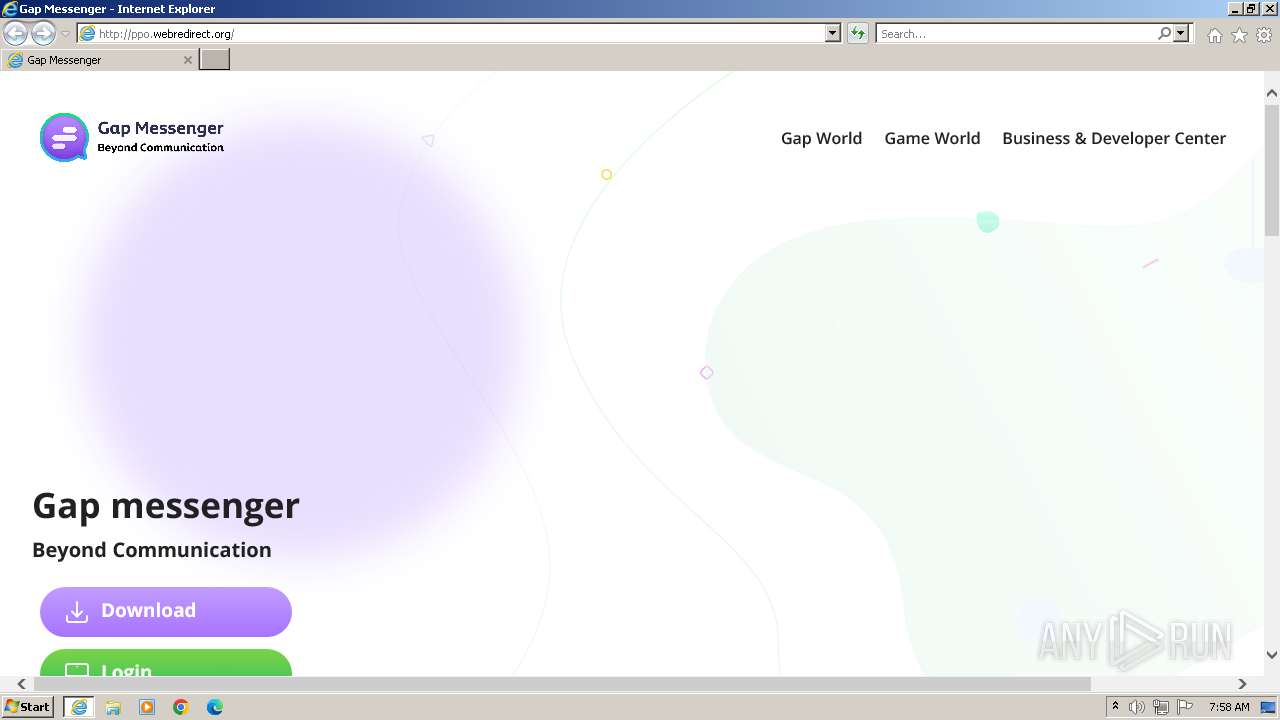
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/images/page_bg.png | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/ | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/css/main.css | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/css/animate.css | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/css/layerslider.css | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/css/ltr.css | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/js/jquery-1.8.1.min.js | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/images/s-world.png | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/js/custom.js | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 216.9.224.179:80 | http://ppo.webredirect.org/gap-site/js/greensock.js | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4028 | iexplore.exe | 216.9.224.179:80 | ppo.webredirect.org | ATT-INTERNET4 | US | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | iexplore.exe | 172.217.18.8:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
4028 | iexplore.exe | 2.21.240.240:80 | ctldl.windowsupdate.com | Akamai International B.V. | SE | unknown |
4028 | iexplore.exe | 2.21.240.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | SE | unknown |
4028 | iexplore.exe | 142.250.74.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
4028 | iexplore.exe | 142.250.184.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ppo.webredirect.org |
| unknown |
www.googletagmanager.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google-analytics.com |
| whitelisted |
region1.analytics.google.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.de |
| whitelisted |
www.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |
4028 | iexplore.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.webredirect .org Domain |