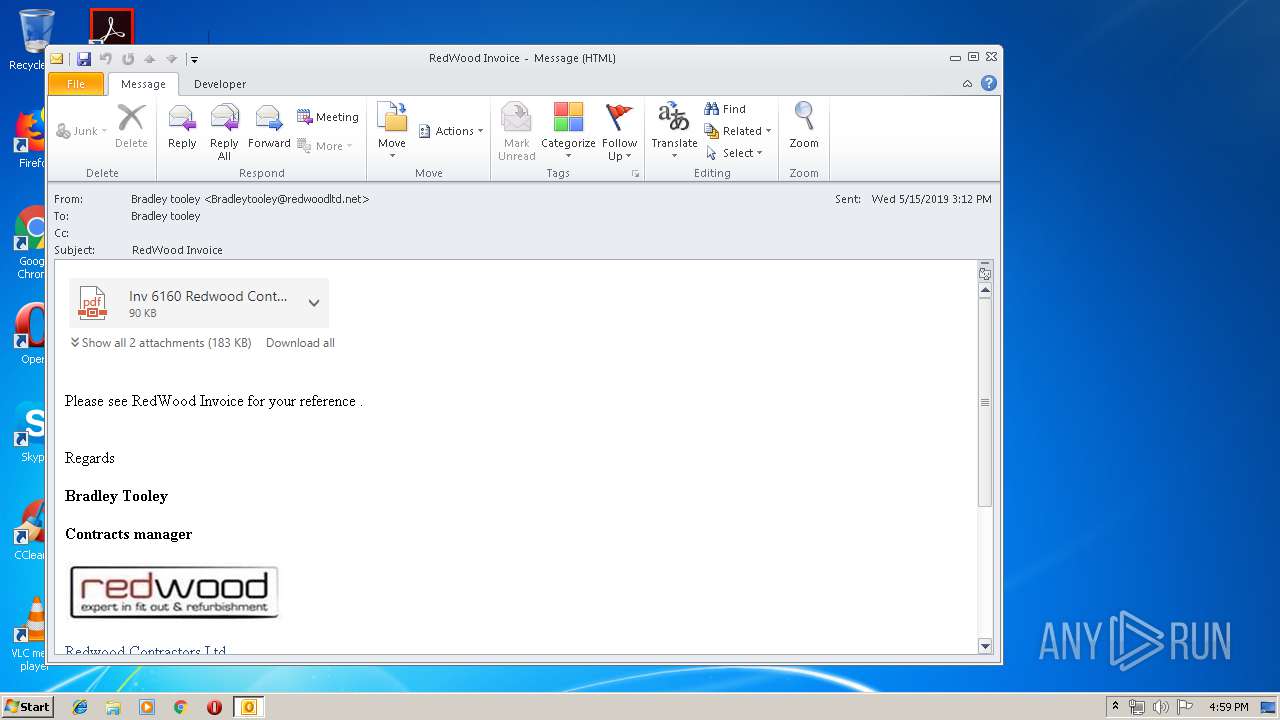
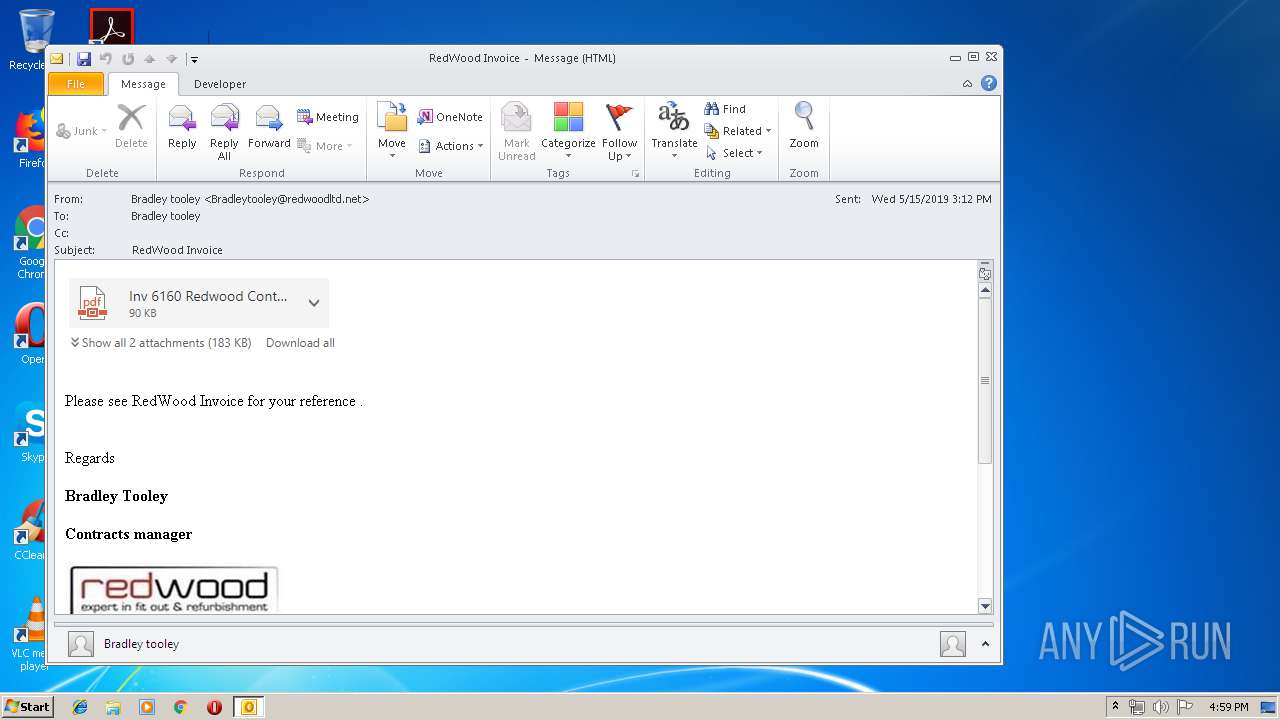
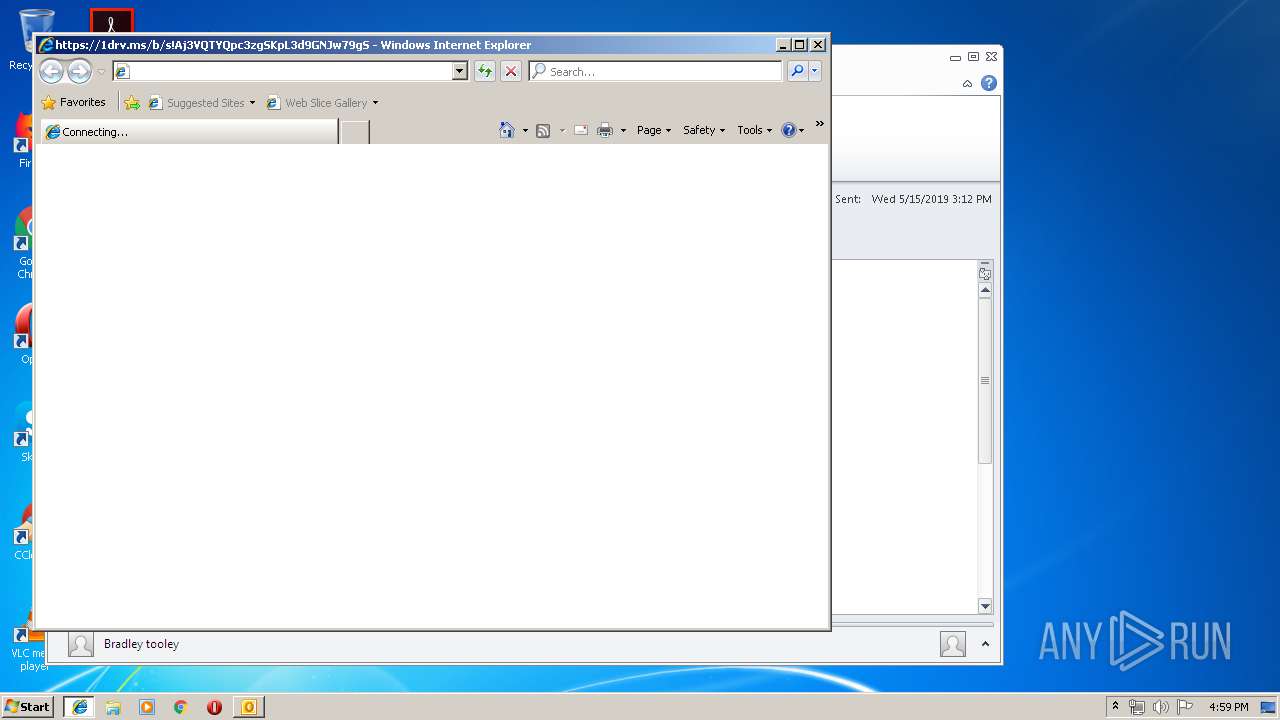
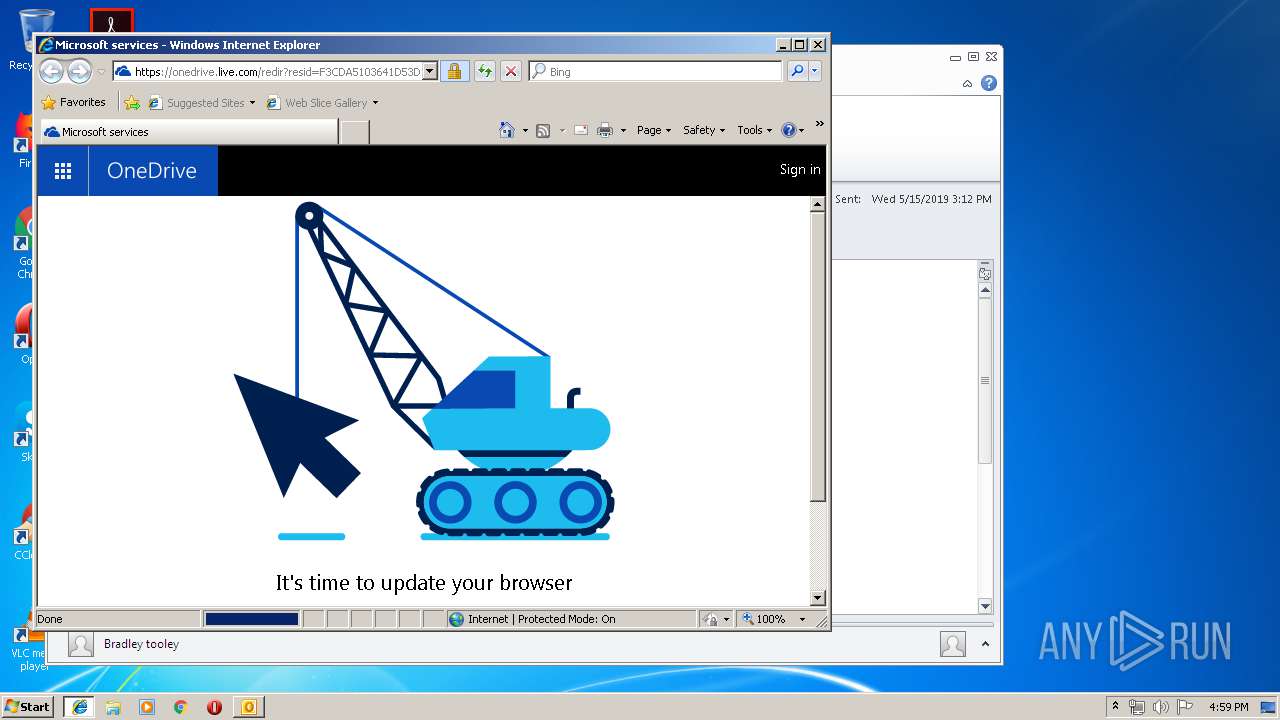
| File name: | Test.msg |
| Full analysis: | https://app.any.run/tasks/8b477026-d344-450f-aad0-ea533a818c53 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 15:58:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | CDC611E1EF0204DBC5CCFC2E19CAAC8A |
| SHA1: | E3AEB24AD508C93E380D44B7CE25E62C64B45DAA |
| SHA256: | 58C85D50C1B3D3E396B46F763F36272F6BBCE47B7848EE5058B8C4636621A099 |
| SSDEEP: | 768:EAQpPFSh2ZsKzsK1mVJYjzritp4aCKtEr287:MtShGL93itmaCR |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2888)
SUSPICIOUS
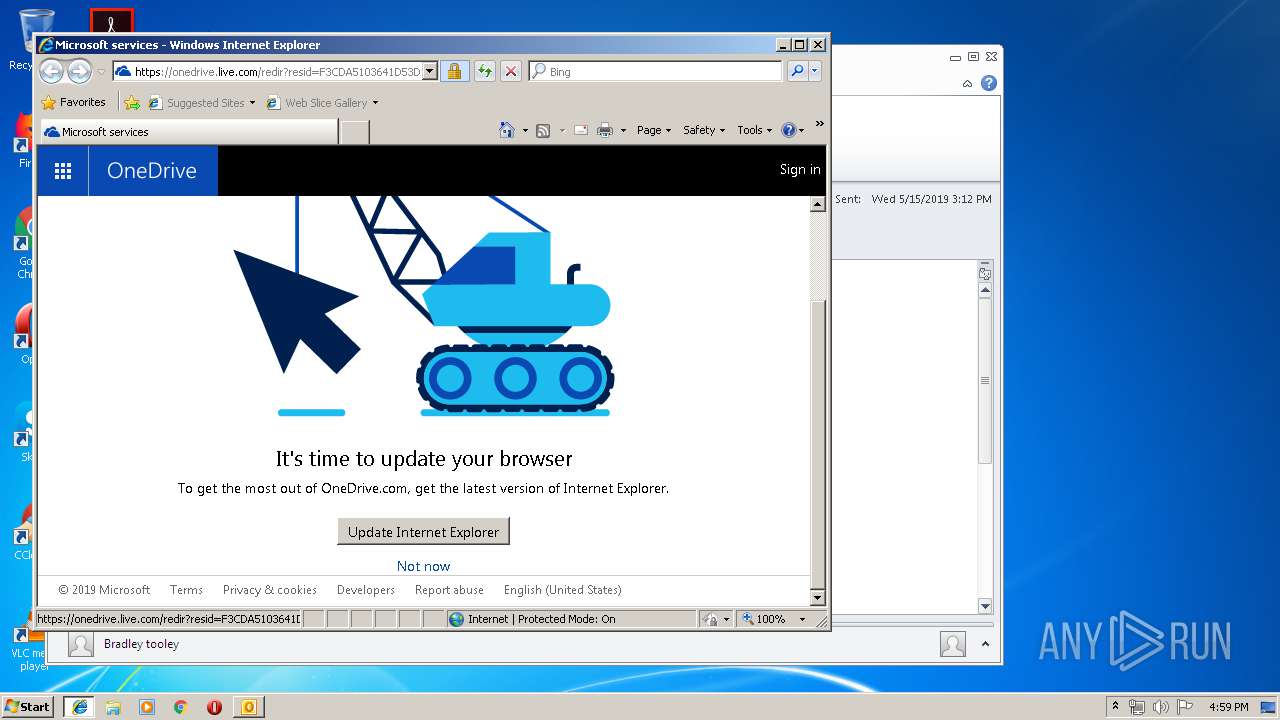
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2888)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2888)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2888)
Creates files in the program directory
- AdobeARM.exe (PID: 4084)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2888)
Creates files in the user directory
- iexplore.exe (PID: 764)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3104)
Reads settings of System Certificates
- iexplore.exe (PID: 3104)
Reads internet explorer settings
- iexplore.exe (PID: 764)
- iexplore.exe (PID: 3040)
Reads Internet Cache Settings
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 764)
Application launched itself
- iexplore.exe (PID: 3104)
- AcroRd32.exe (PID: 3148)
- RdrCEF.exe (PID: 2176)
Changes settings of System certificates
- iexplore.exe (PID: 3104)
Changes internet zones settings
- iexplore.exe (PID: 3104)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
47
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3104 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2176.1.1440383222\1065941499" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
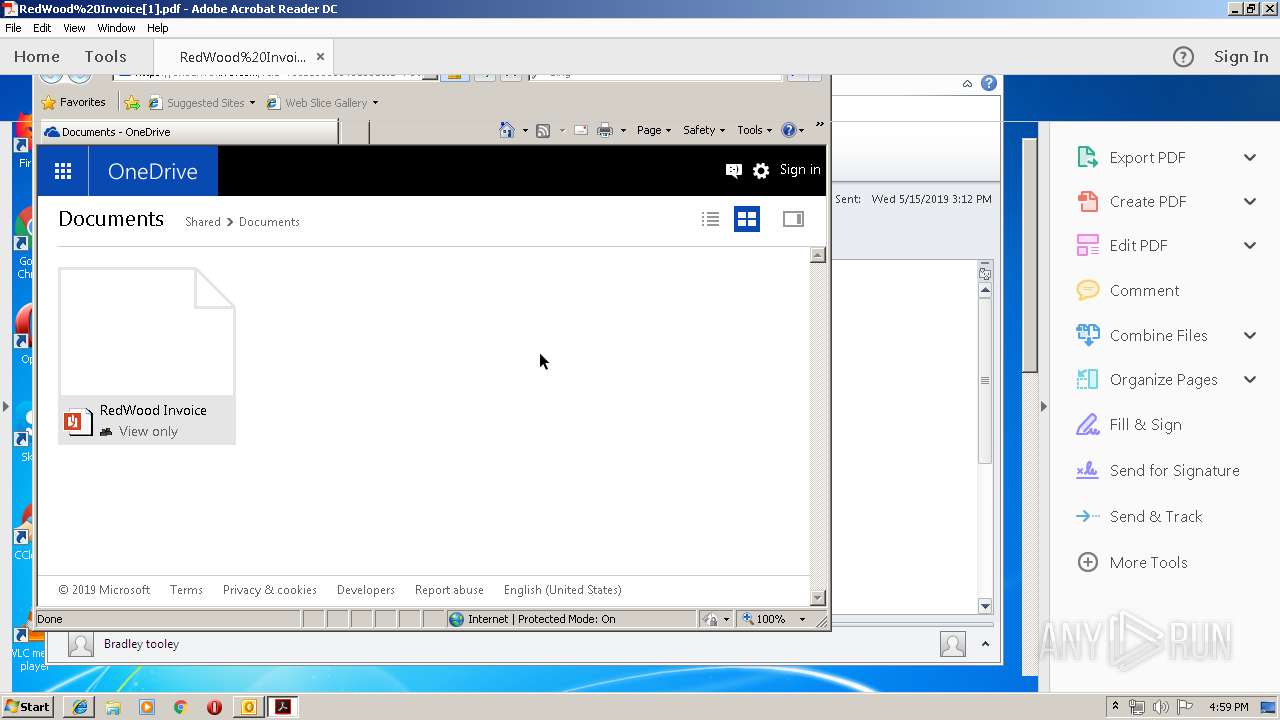
| 2888 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Test.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3104 CREDAT:6405 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
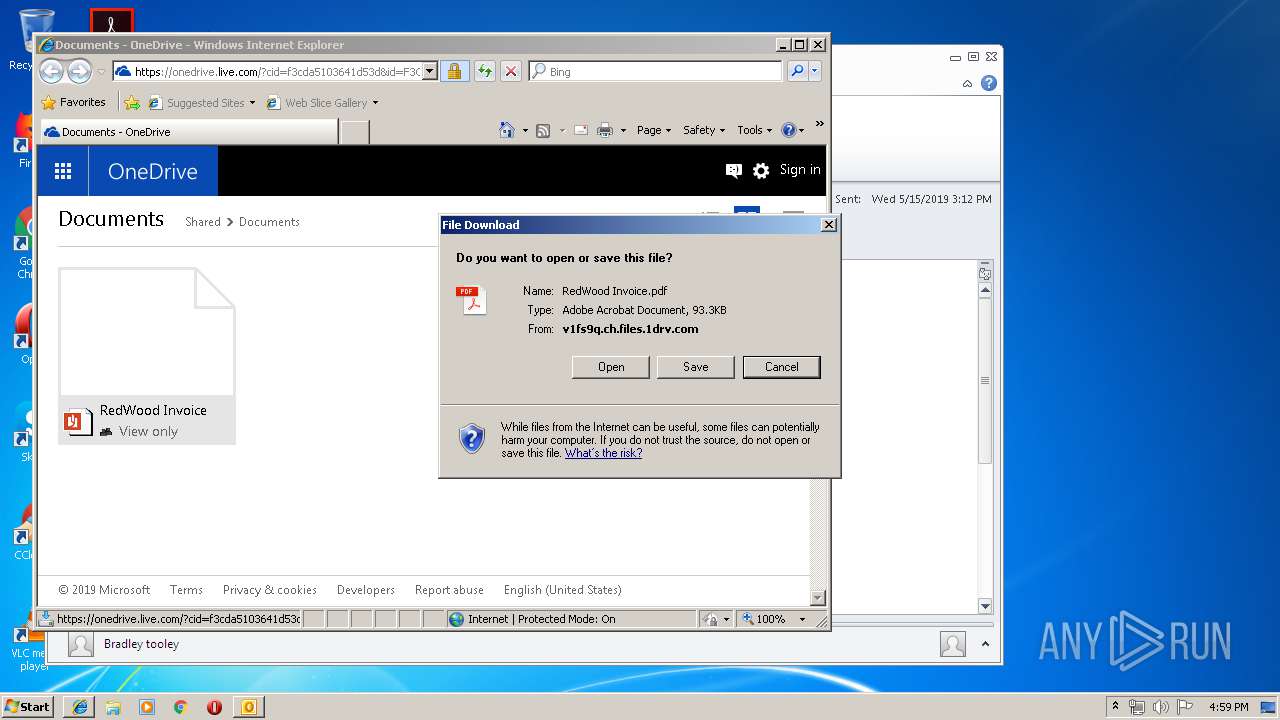
| 3064 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PFCRR637\RedWood%20Invoice[1].pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
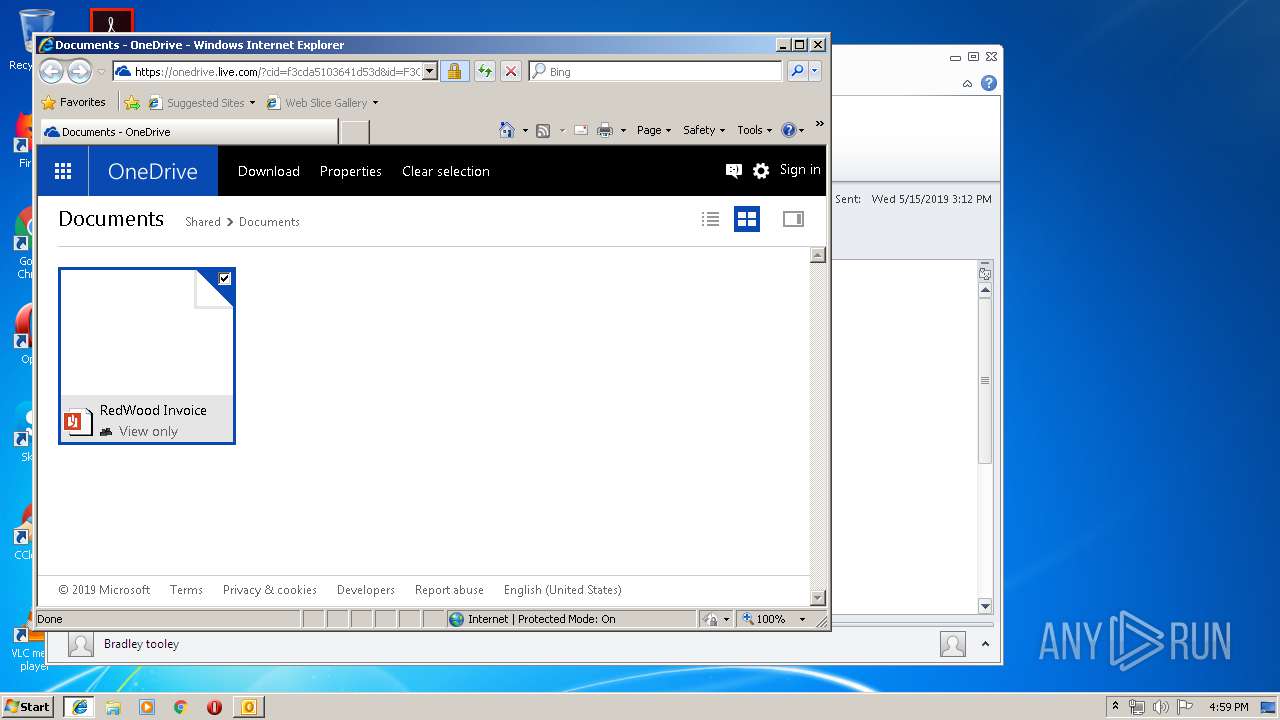
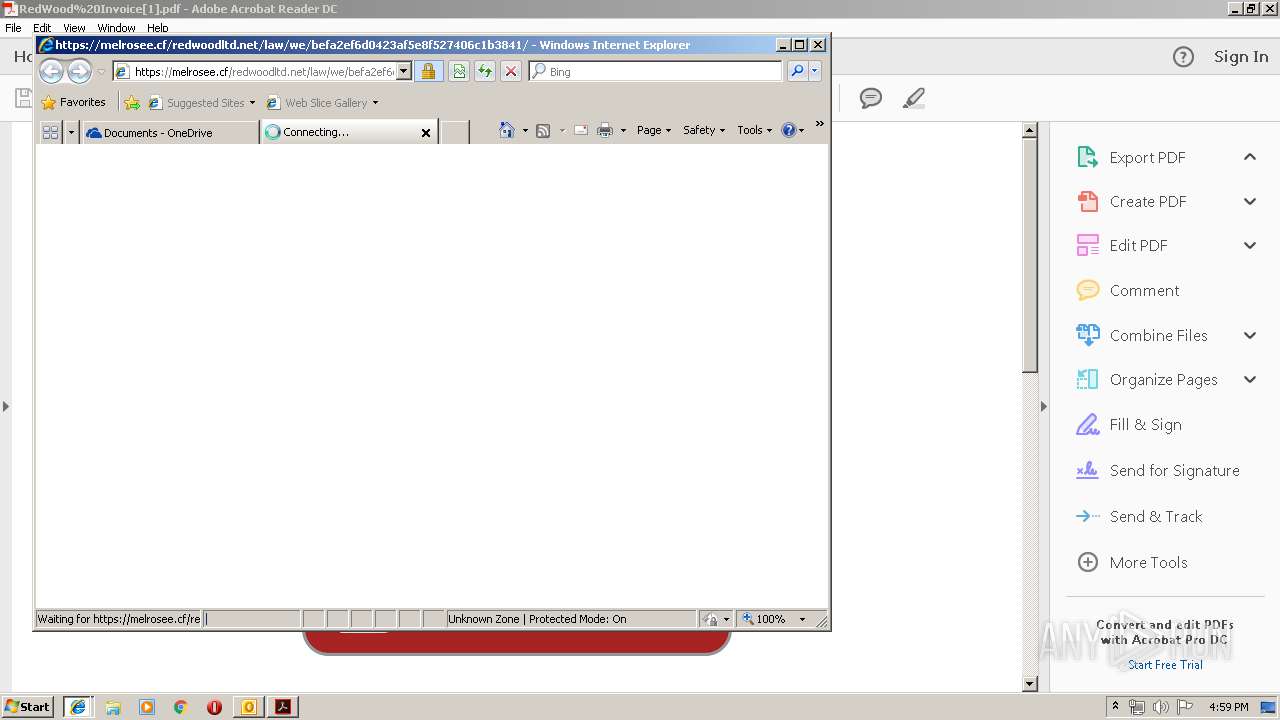
| 3104 | "C:\Program Files\Internet Explorer\iexplore.exe" https://1drv.ms/b/s!Aj3VQTYQpc3zgSKpL3d9GNJw79gS | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3148 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PFCRR637\RedWood%20Invoice[1].pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | iexplore.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3440 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2176.0.628110160\1560776853" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
2 409
Read events
1 862
Write events
523
Delete events
24
Modification events
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | j< |
Value: 206A3C00480B0000010000000000000000000000 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 480B0000CEA4701C370BD50100000000 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220039200 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2888) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1320091669 | |||
Executable files
0
Suspicious files
2
Text files
138
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRFE91.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3E136AD5.dat | image | |
MD5:— | SHA256:— | |||
| 3104 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3104 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\525A4AD2.dat | image | |
MD5:— | SHA256:— | |||
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_DC59F3F4F29BF54988B1C0DCDB433A5F.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 2888 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{E577EE1C-8D95-433B-BBFC-558A5FC55534}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
| 764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\SZFFNSTM\redir[1].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
39
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2888 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3148 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3148 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
3148 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
3148 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3148 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3104 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2888 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
764 | iexplore.exe | 23.43.112.150:443 | r3.res.outlook.com | Akamai International B.V. | NL | whitelisted |
764 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
764 | iexplore.exe | 40.90.136.179:443 | skyapi.onedrive.live.com | Microsoft Corporation | US | whitelisted |
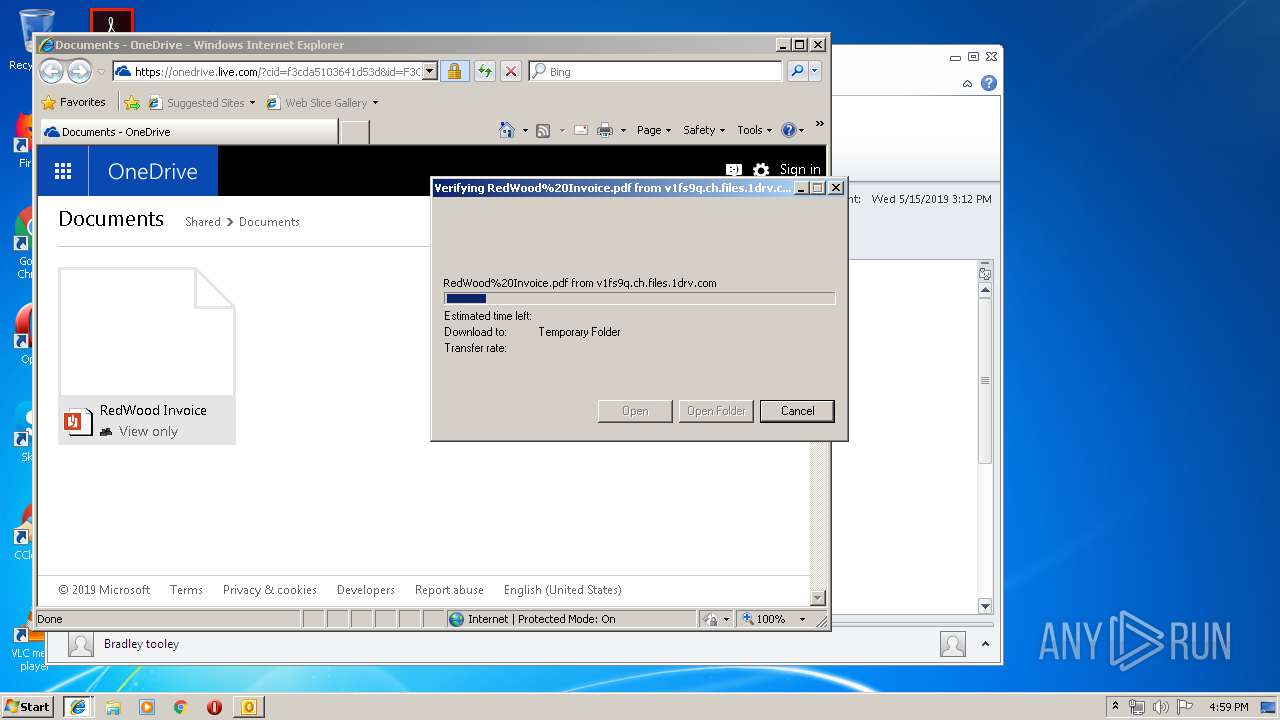
764 | iexplore.exe | 13.107.43.12:443 | v1fs9q.ch.files.1drv.com | Microsoft Corporation | US | suspicious |
3148 | AcroRd32.exe | 2.21.36.203:443 | armmf.adobe.com | GTT Communications Inc. | FR | suspicious |
— | — | 104.111.214.232:443 | ardownload2.adobe.com | Akamai International B.V. | NL | whitelisted |
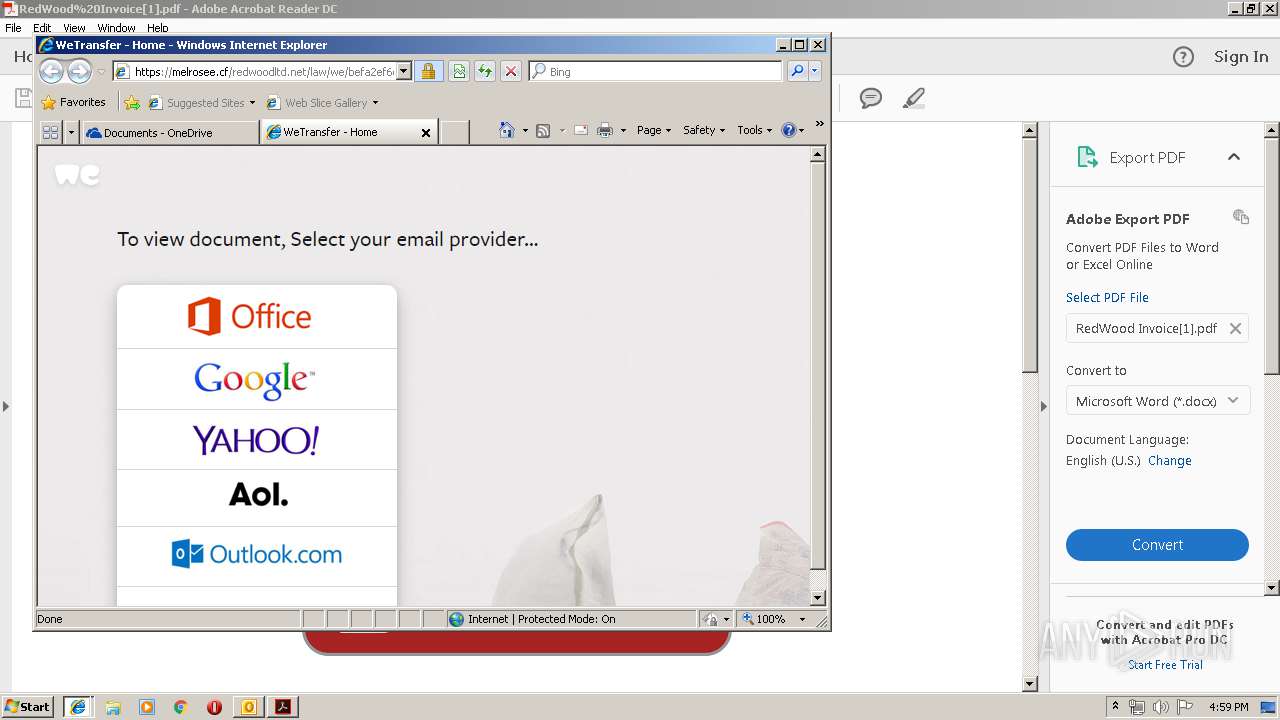
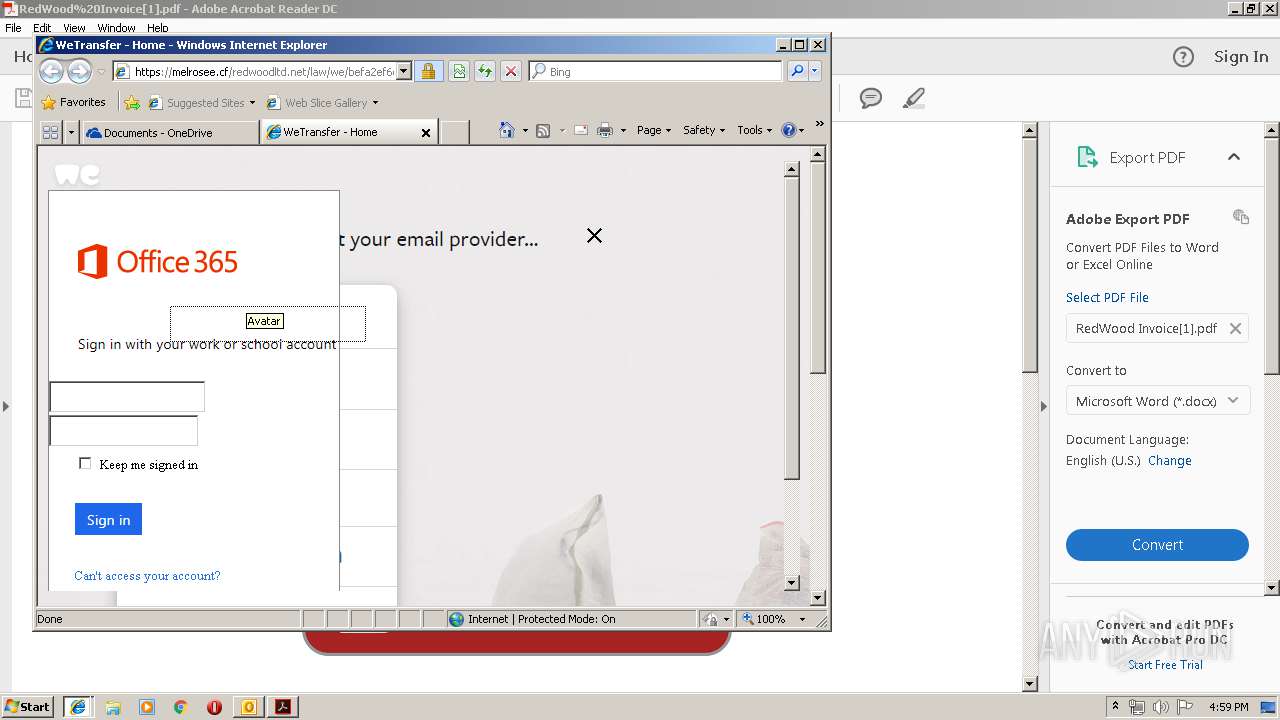
3040 | iexplore.exe | 104.27.140.56:443 | melrosee.cf | Cloudflare Inc | US | shared |
3104 | iexplore.exe | 104.27.140.56:443 | melrosee.cf | Cloudflare Inc | US | shared |
3148 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
1drv.ms |
| shared |
www.bing.com |
| whitelisted |
onedrive.live.com |
| shared |
spoprod-a.akamaihd.net |
| whitelisted |
p.sfx.ms |
| whitelisted |
c.live.com |
| whitelisted |
c.bing.com |
| whitelisted |
r3.res.outlook.com |
| whitelisted |
skyapi.onedrive.live.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .cf Domain |
3040 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.cf) in TLS SNI |