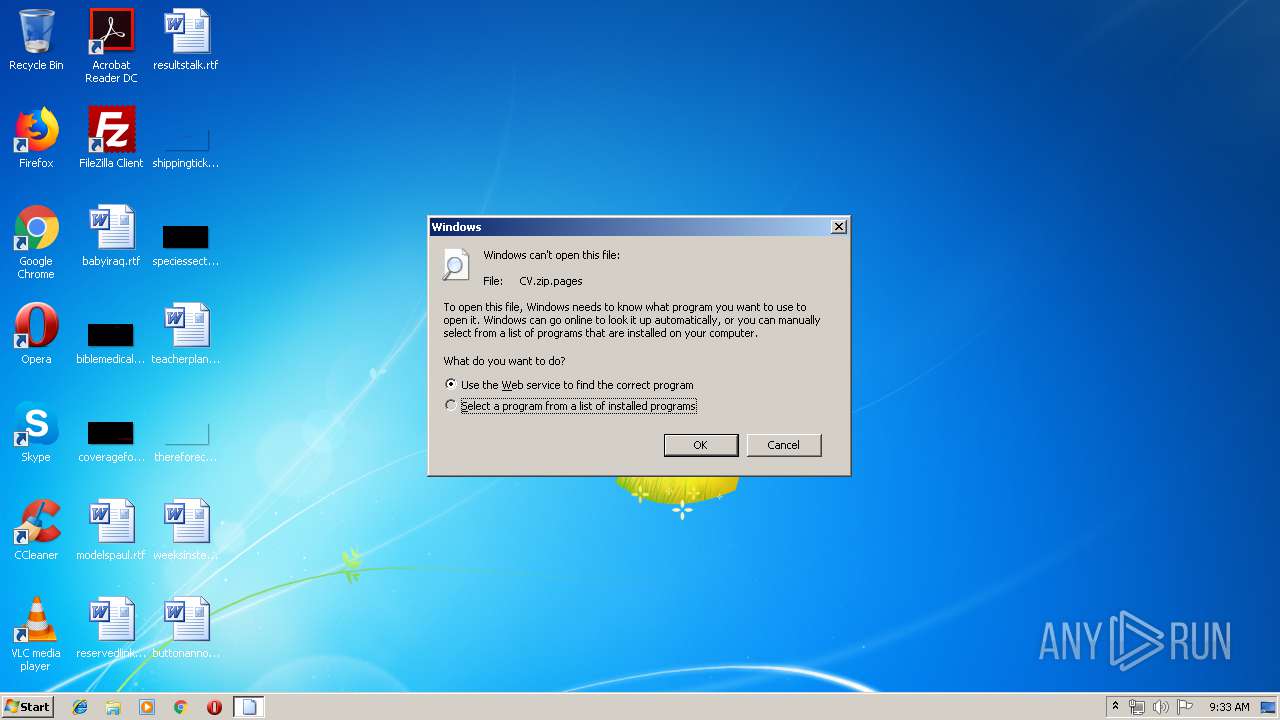
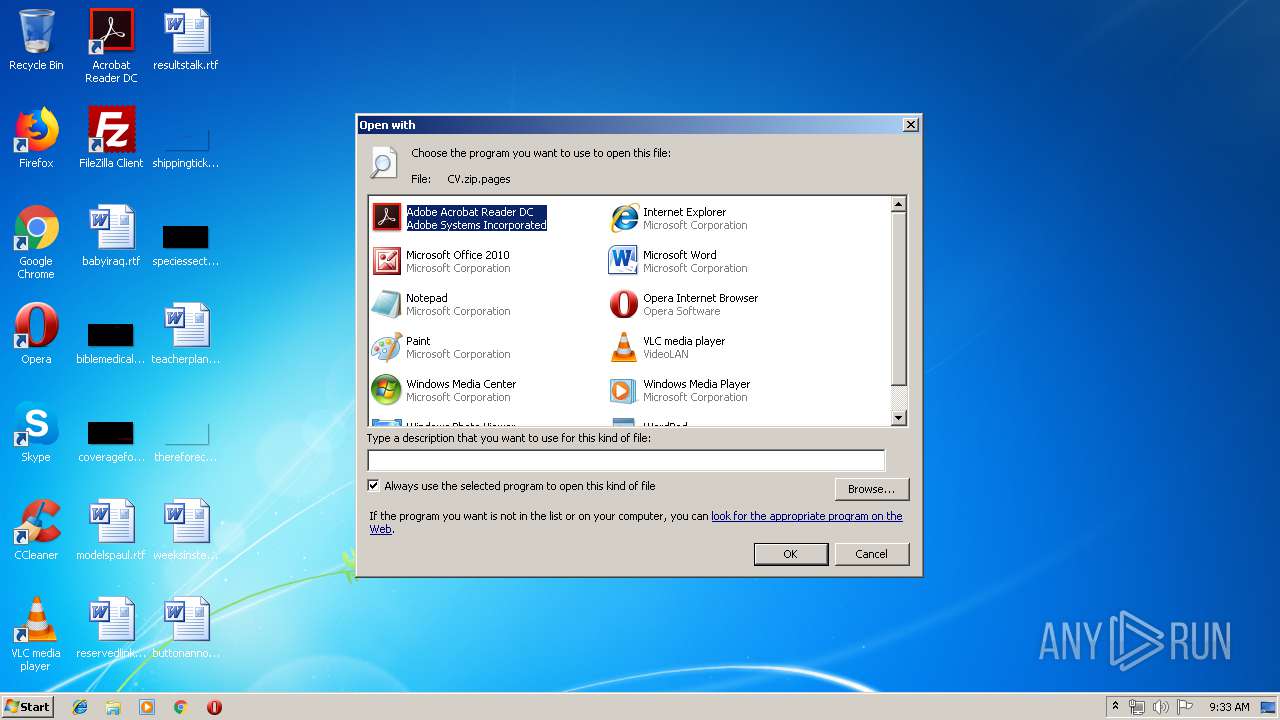
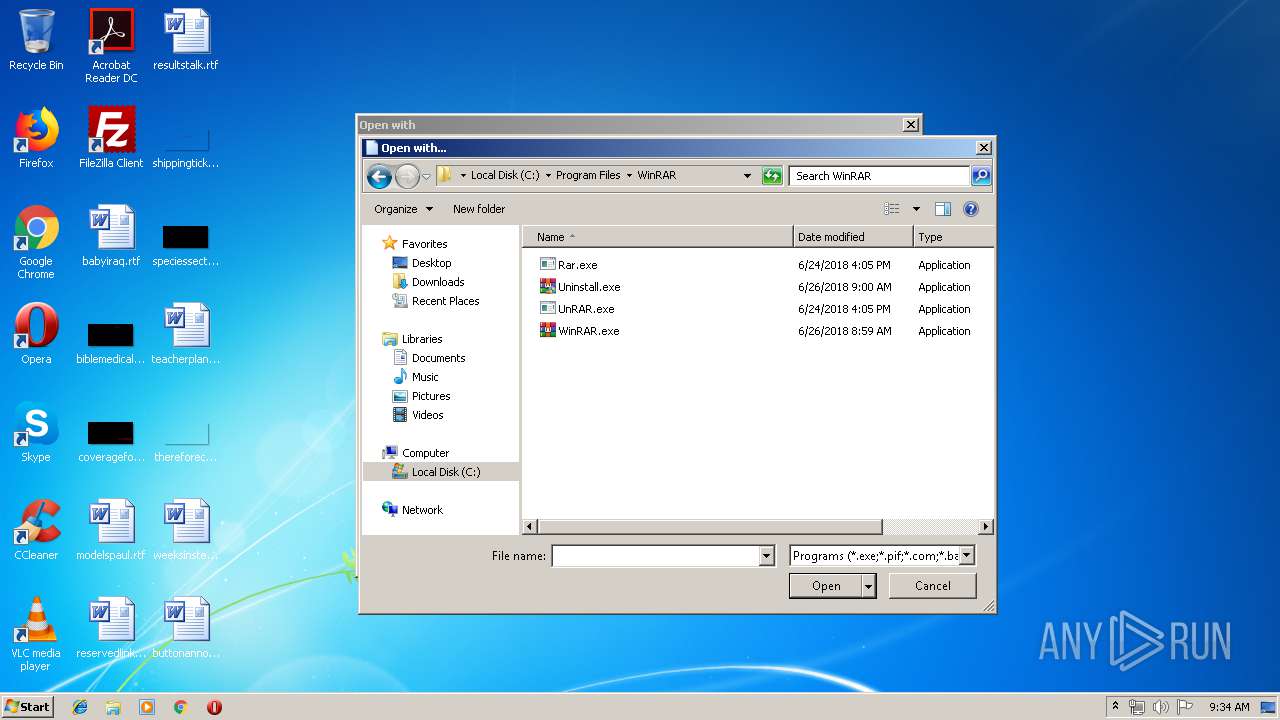
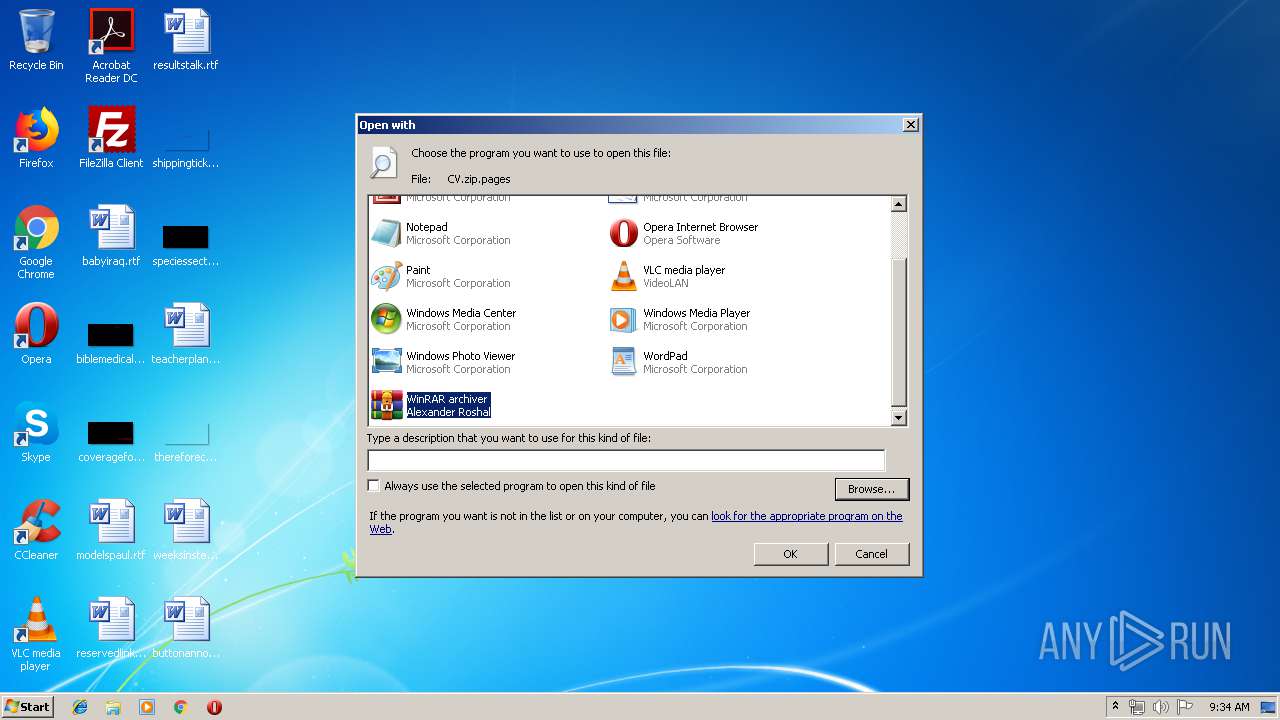
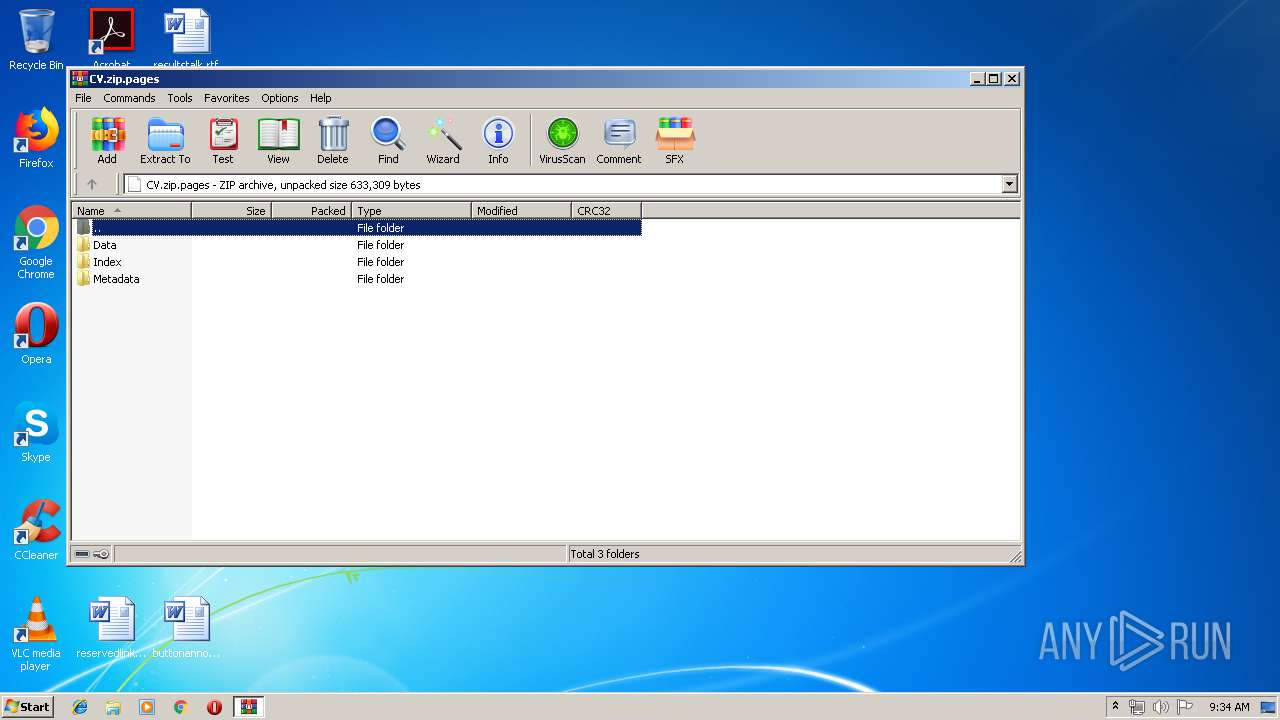
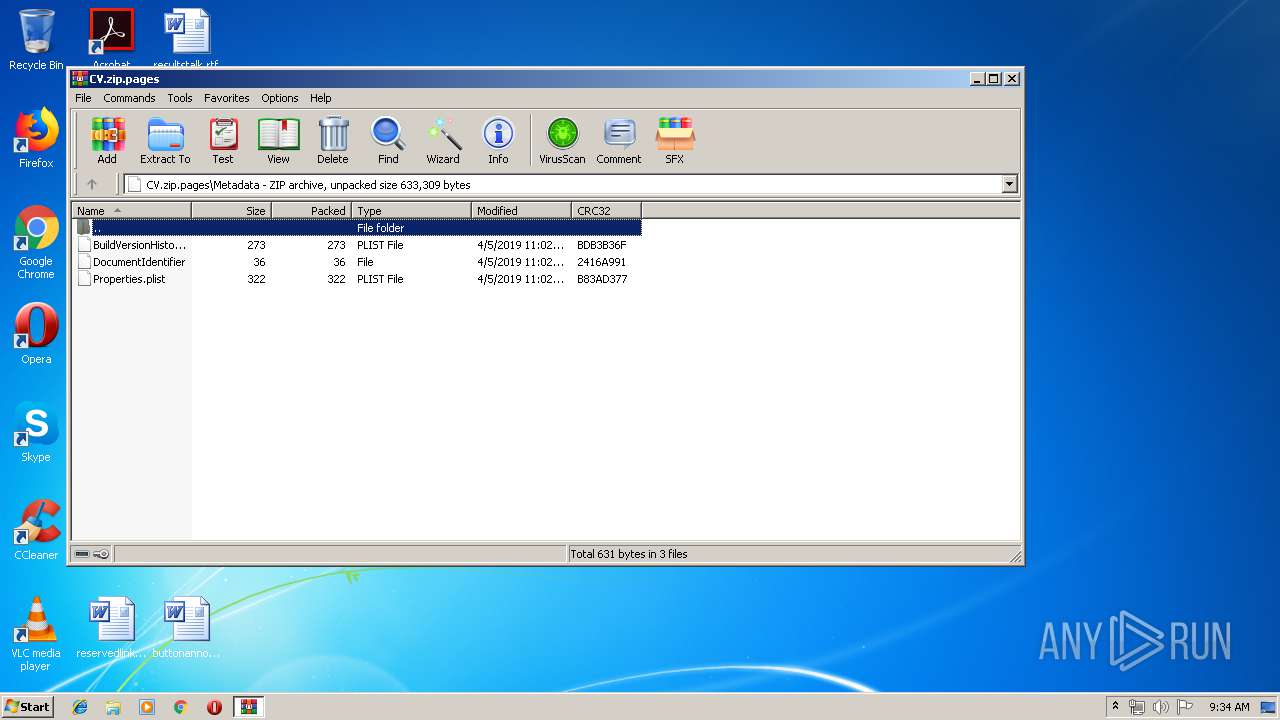
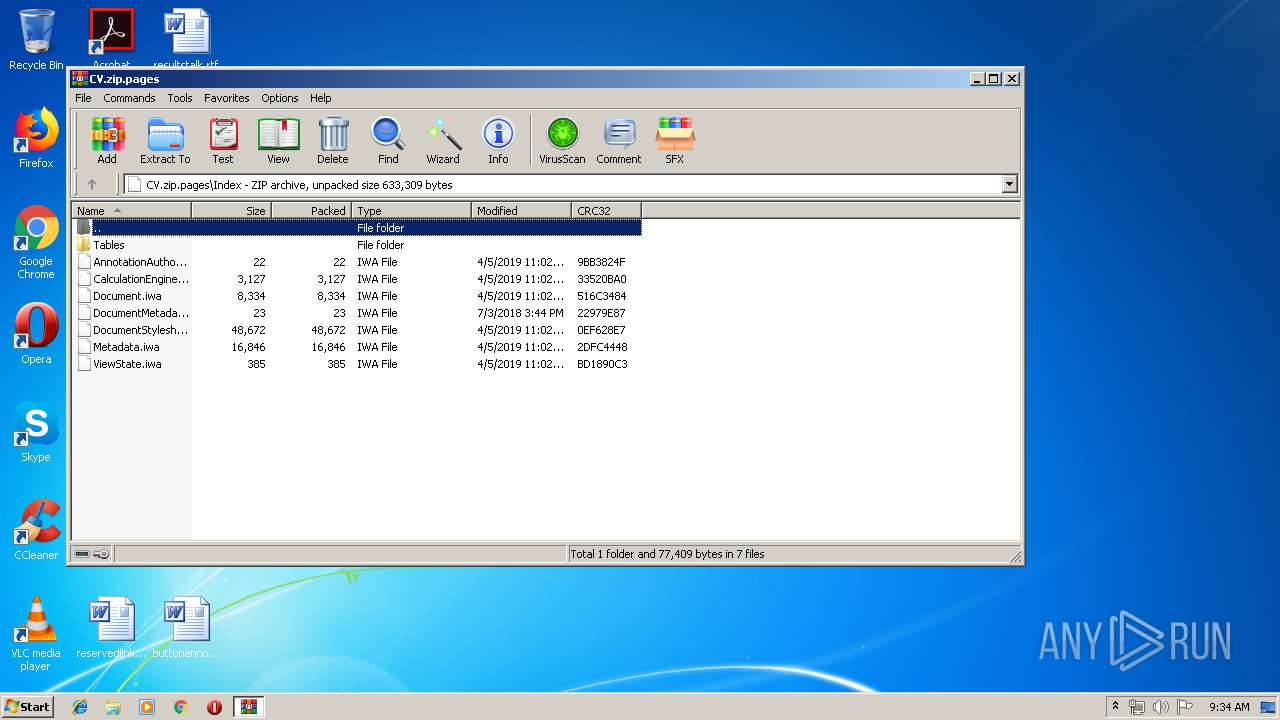
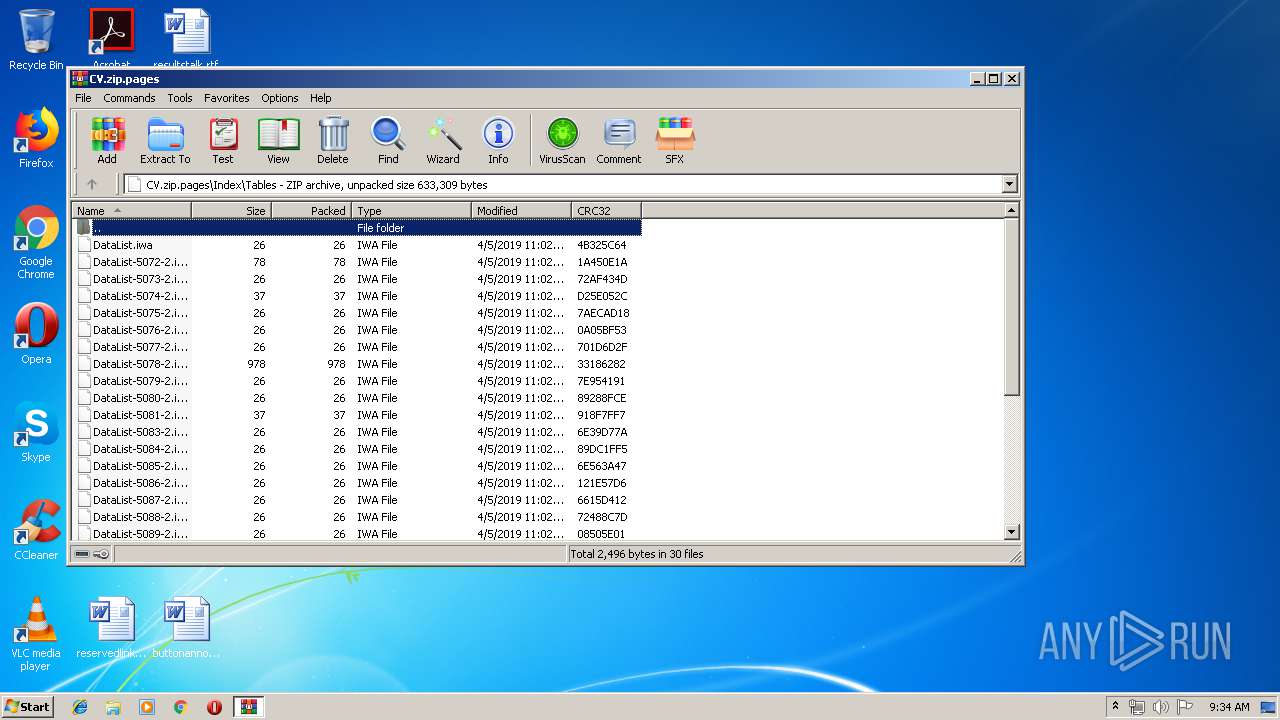
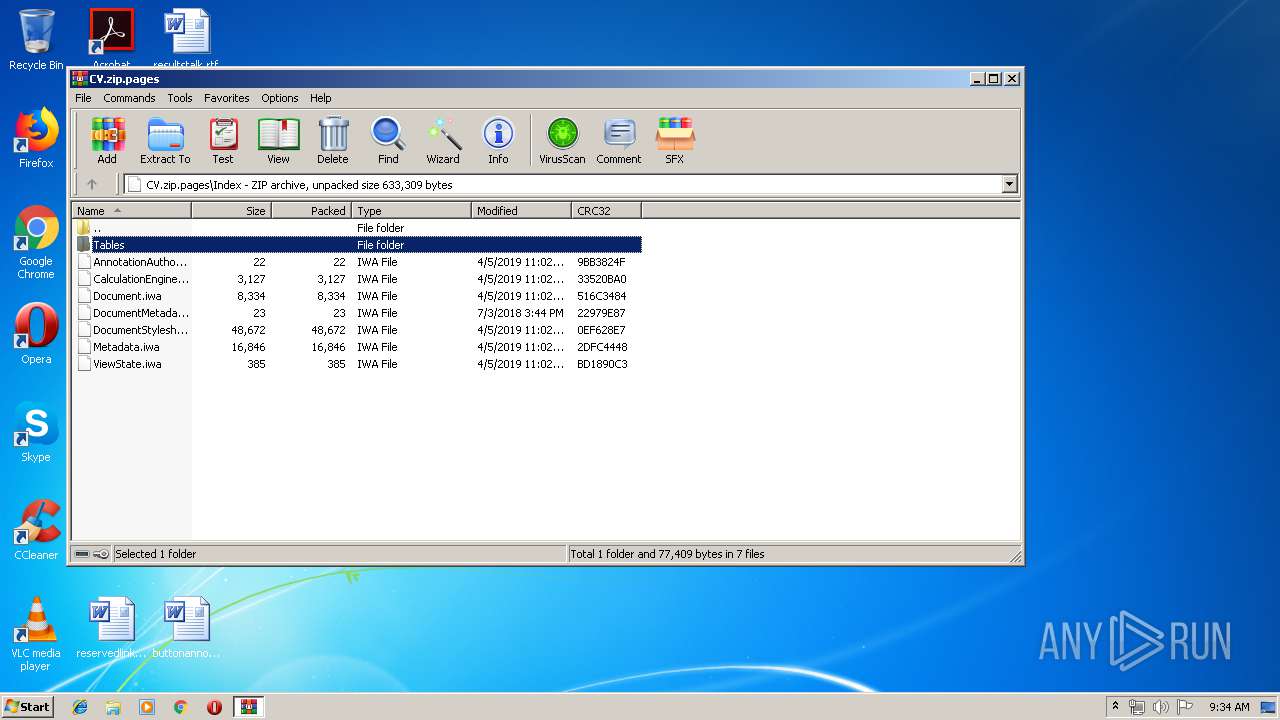
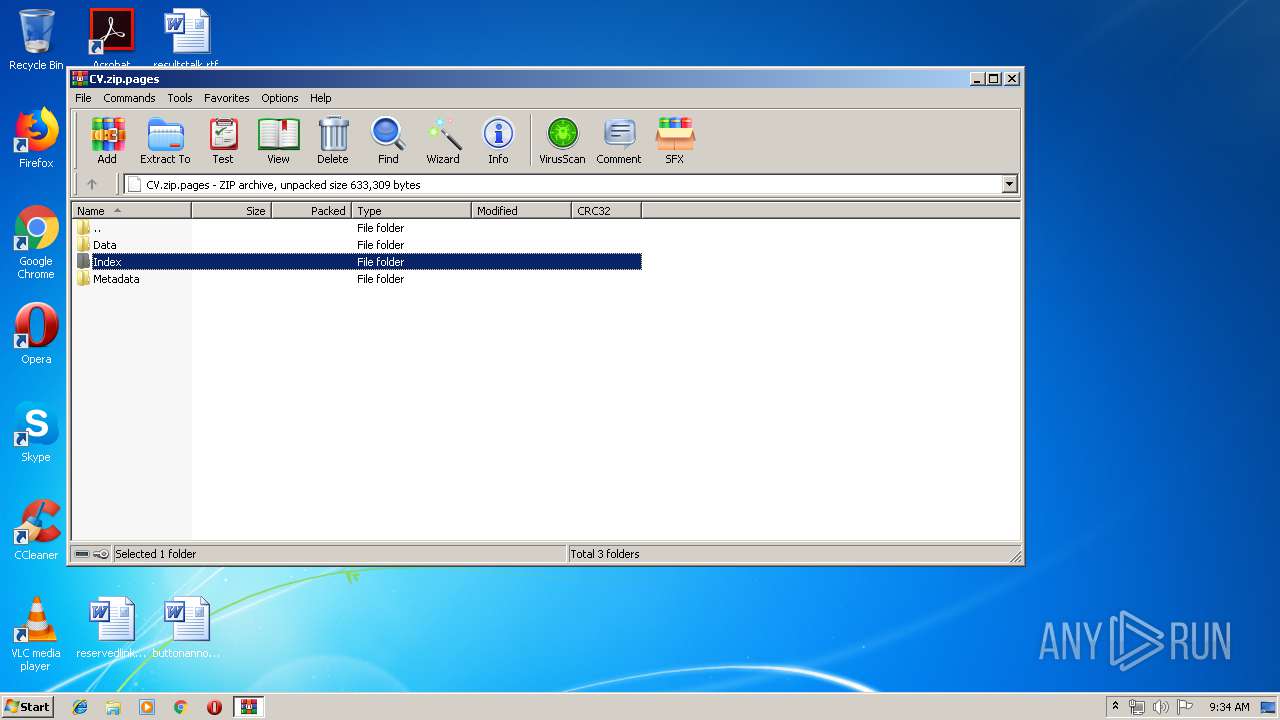
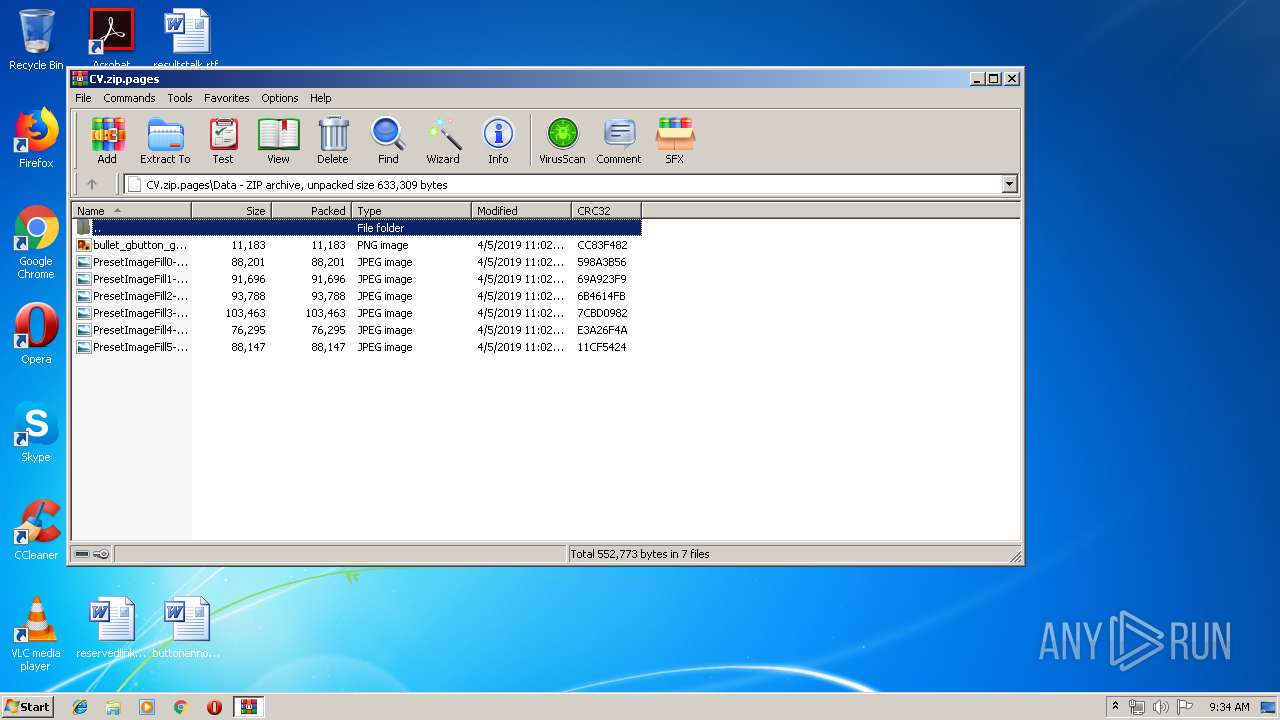
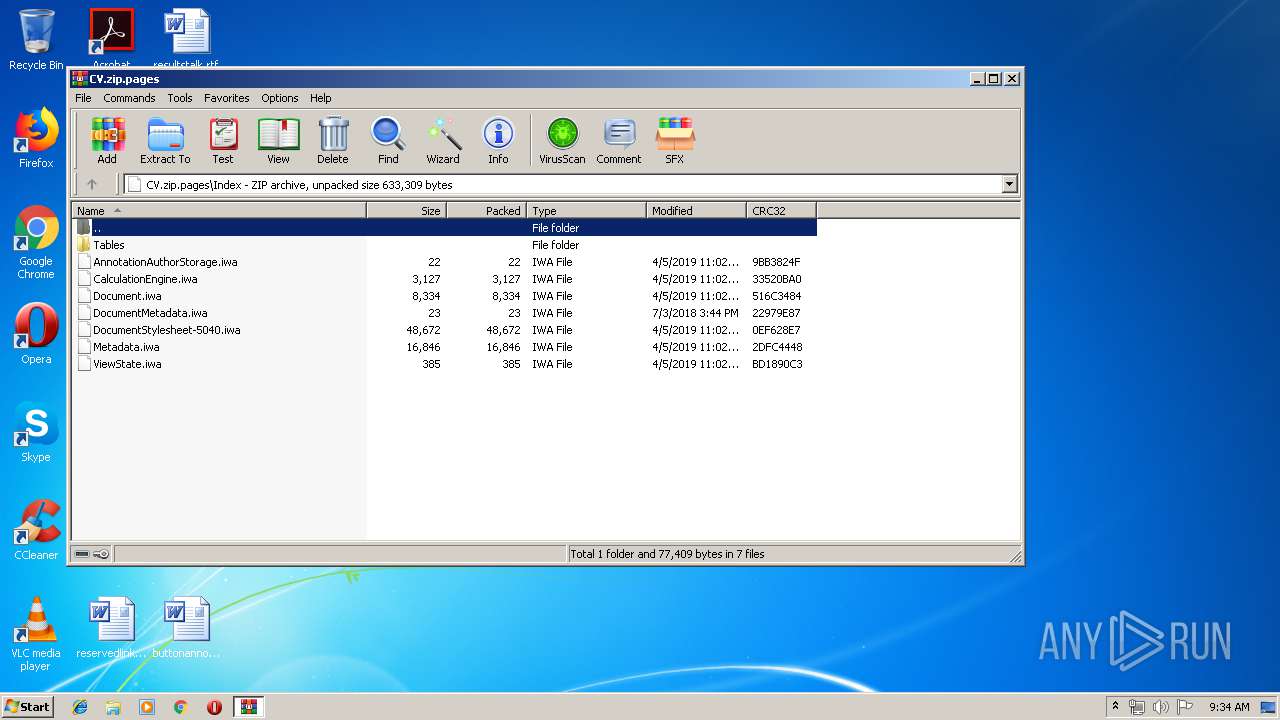
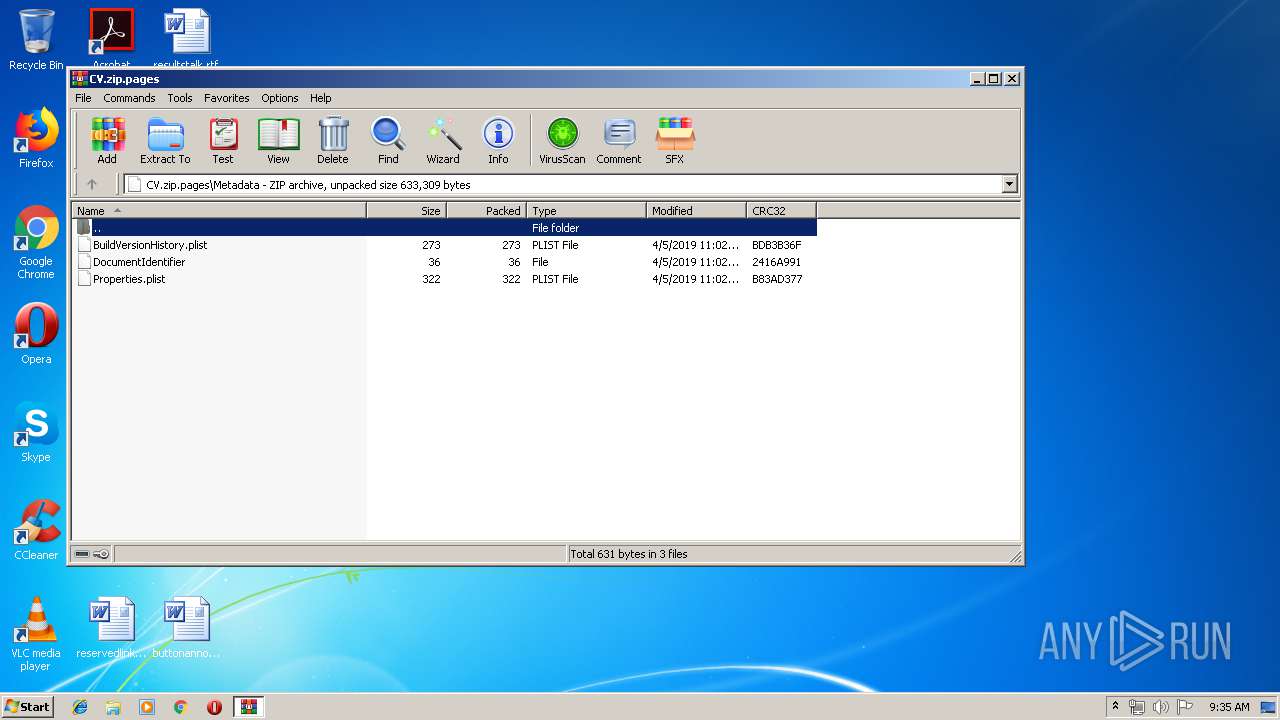
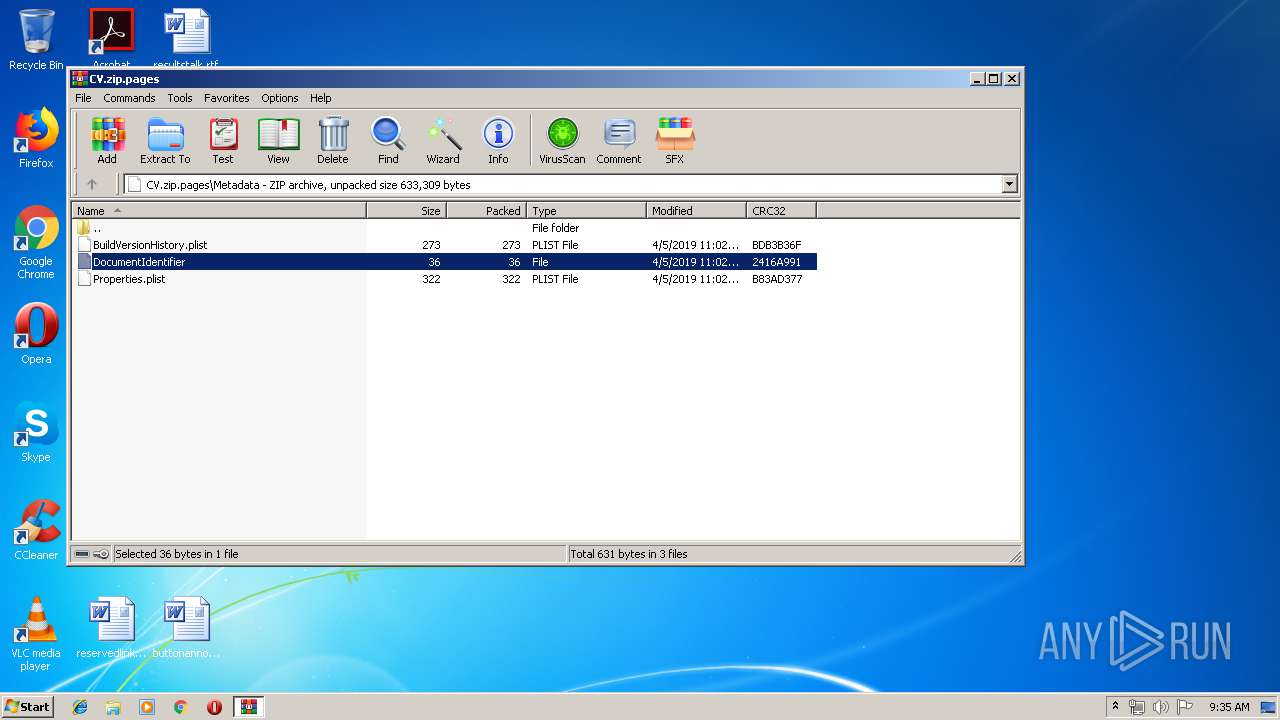
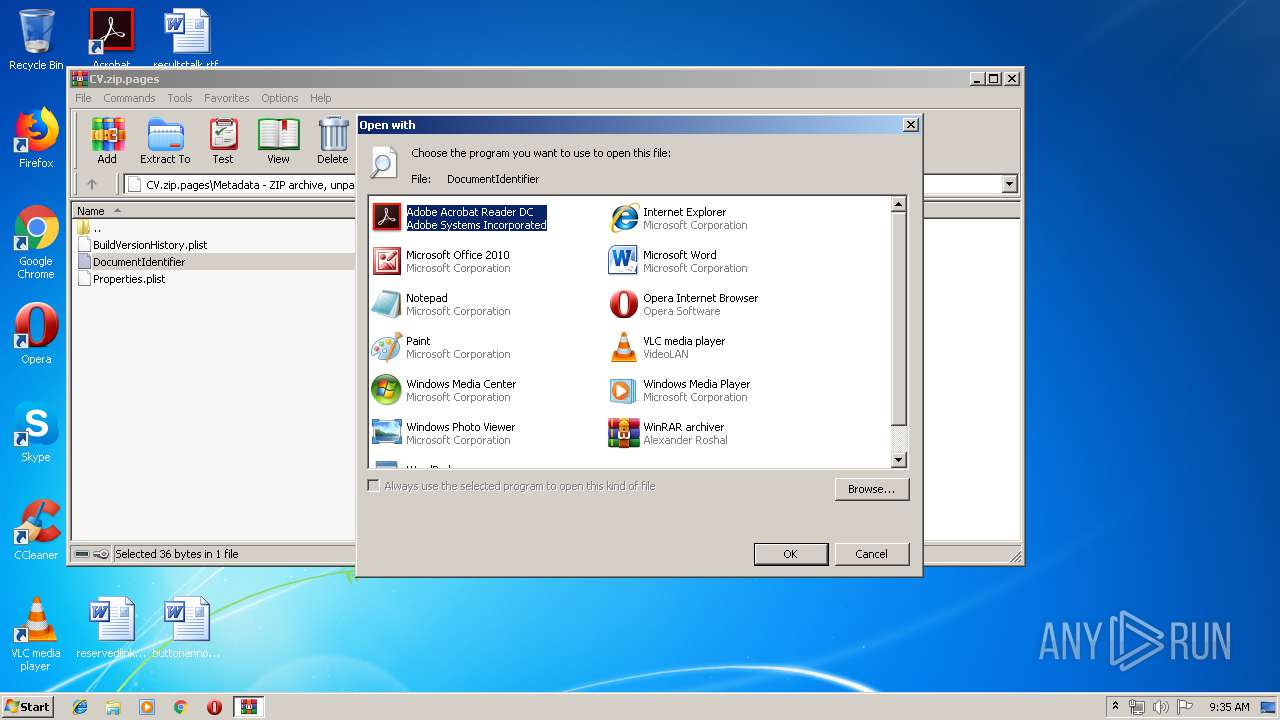
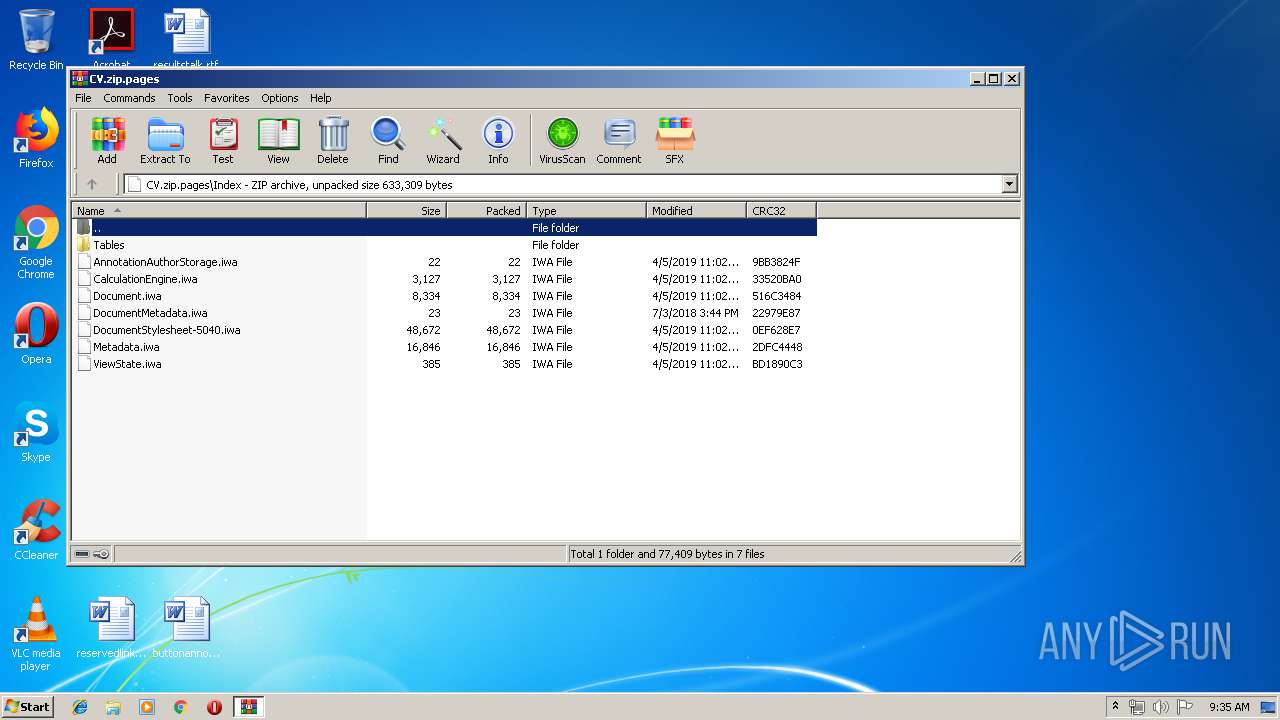
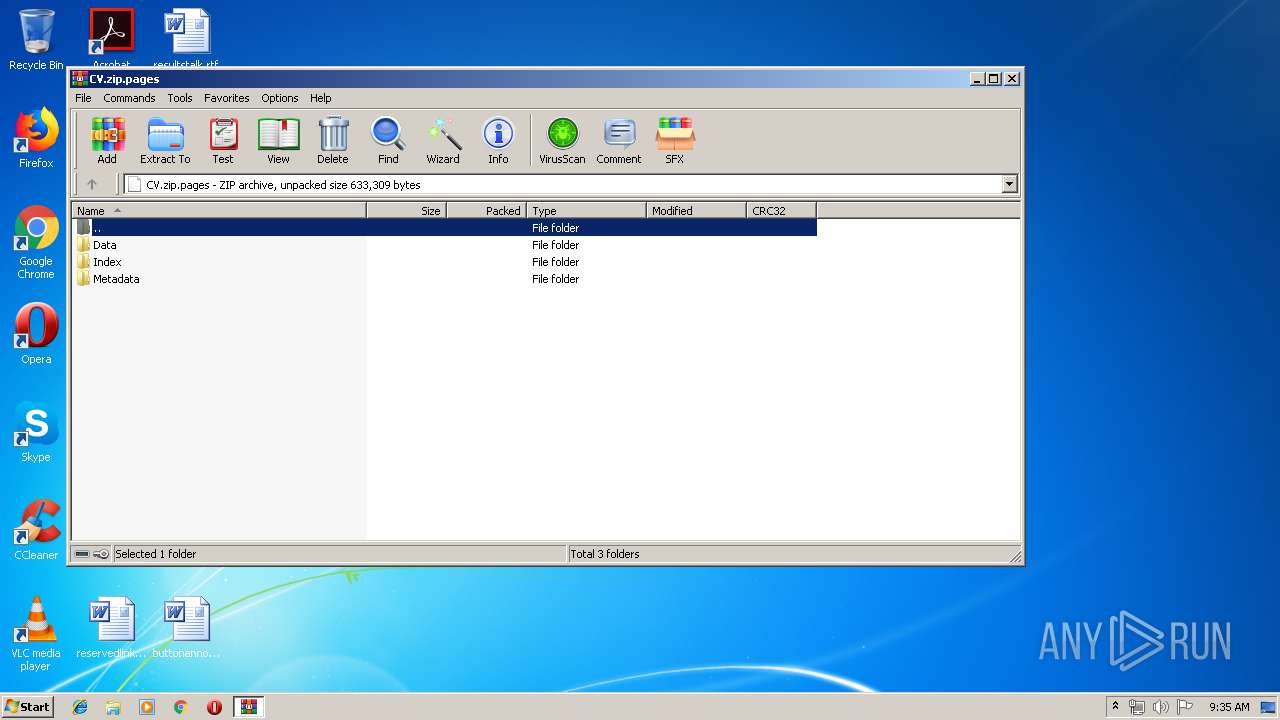
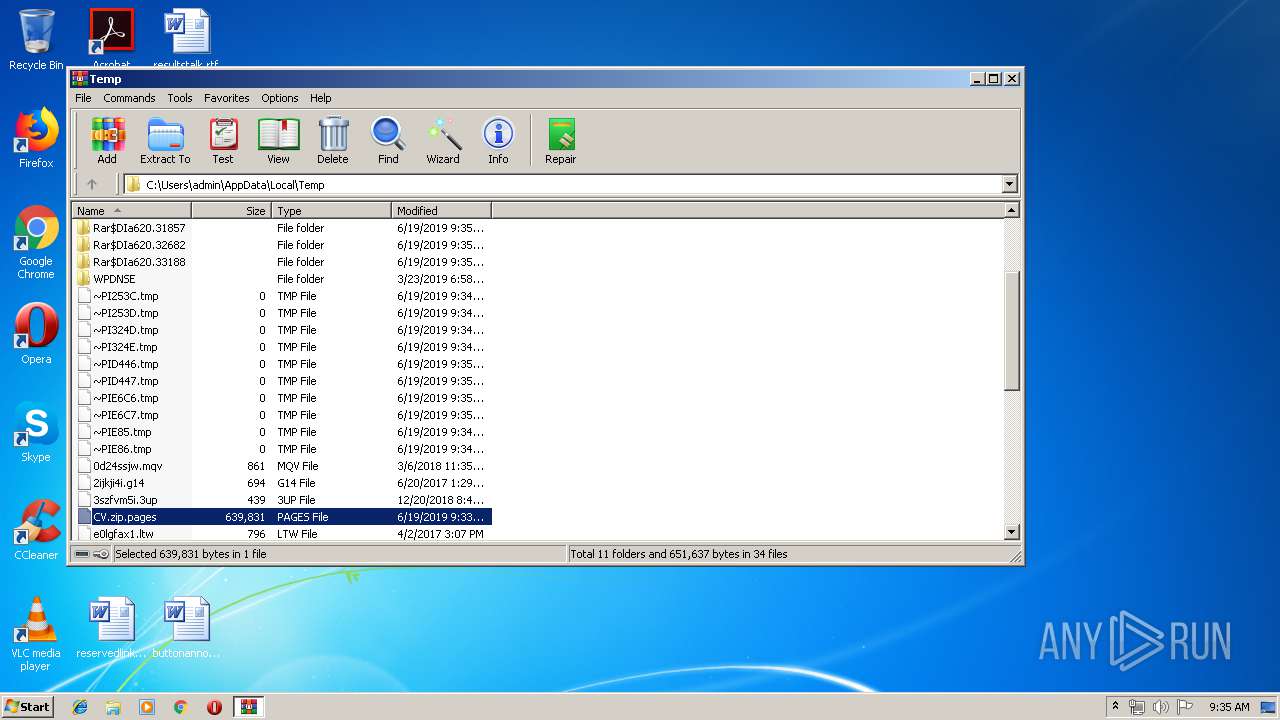
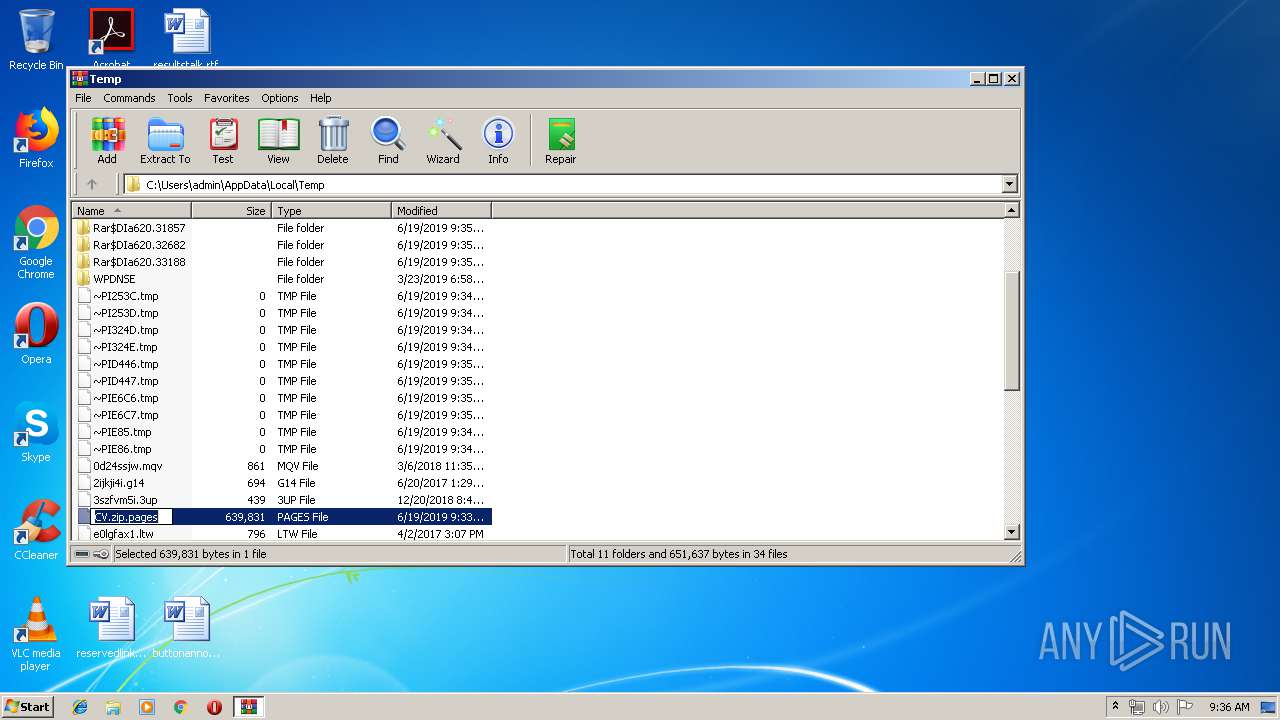
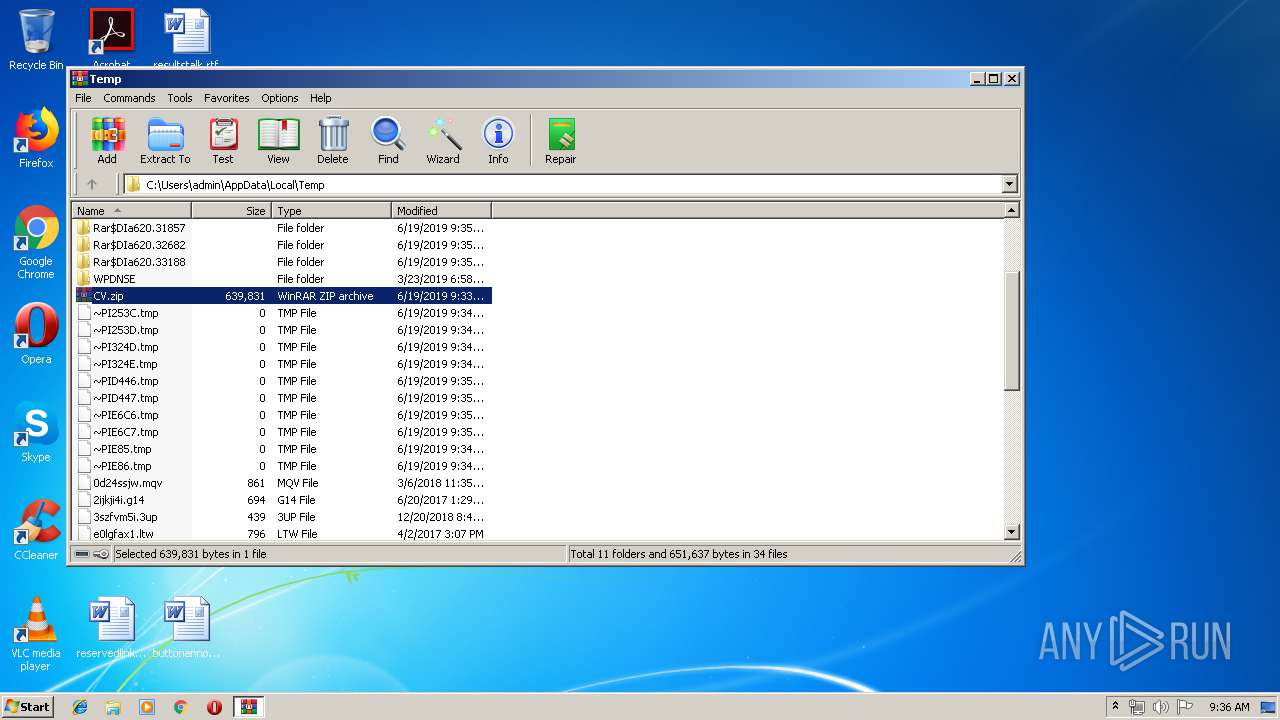
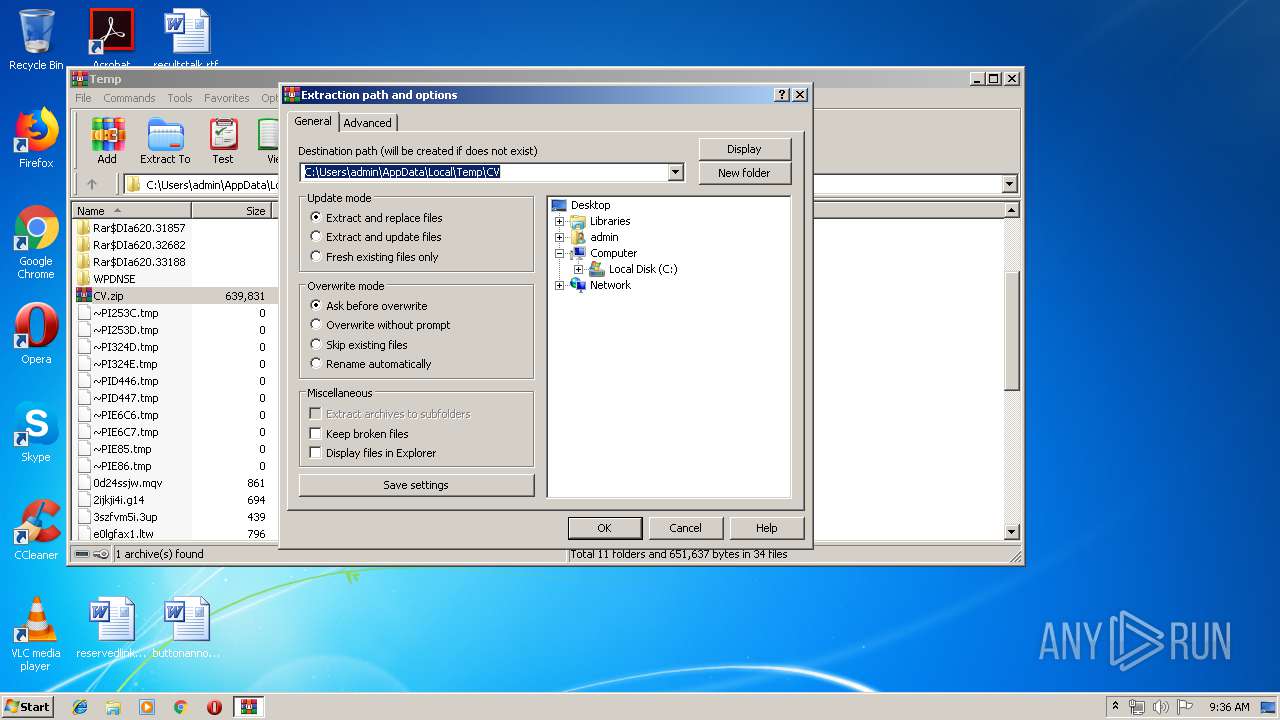
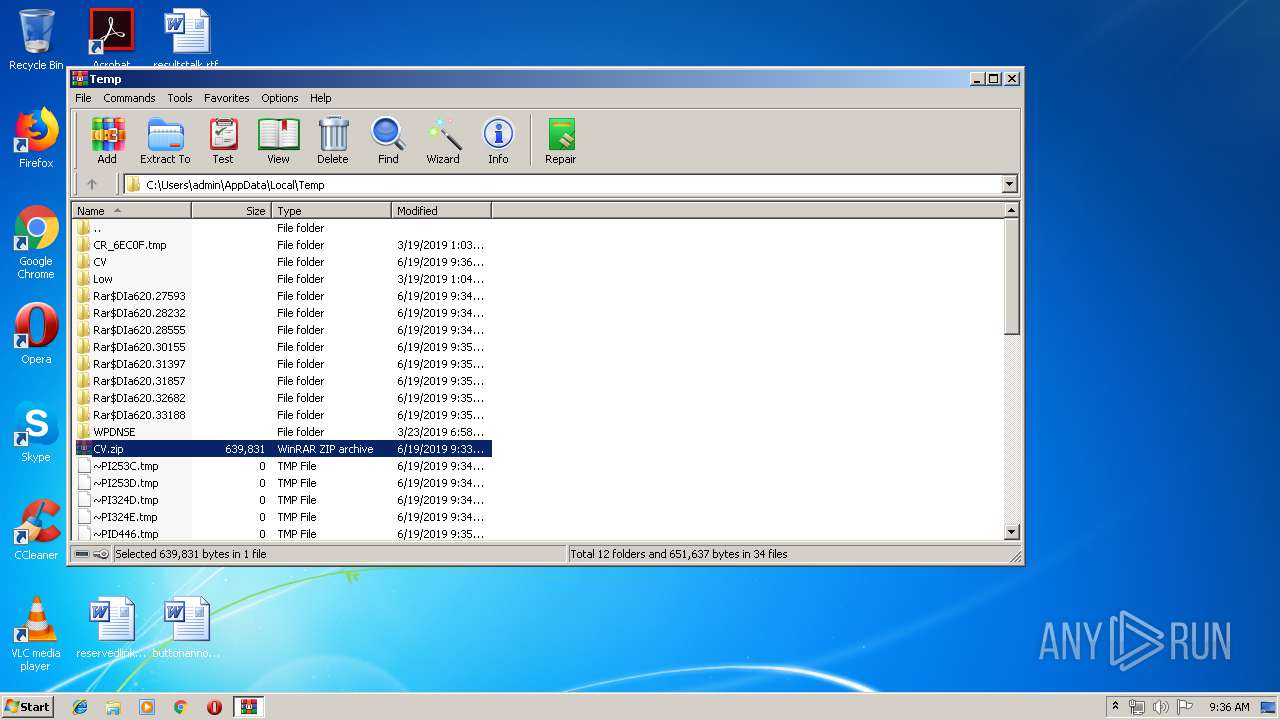
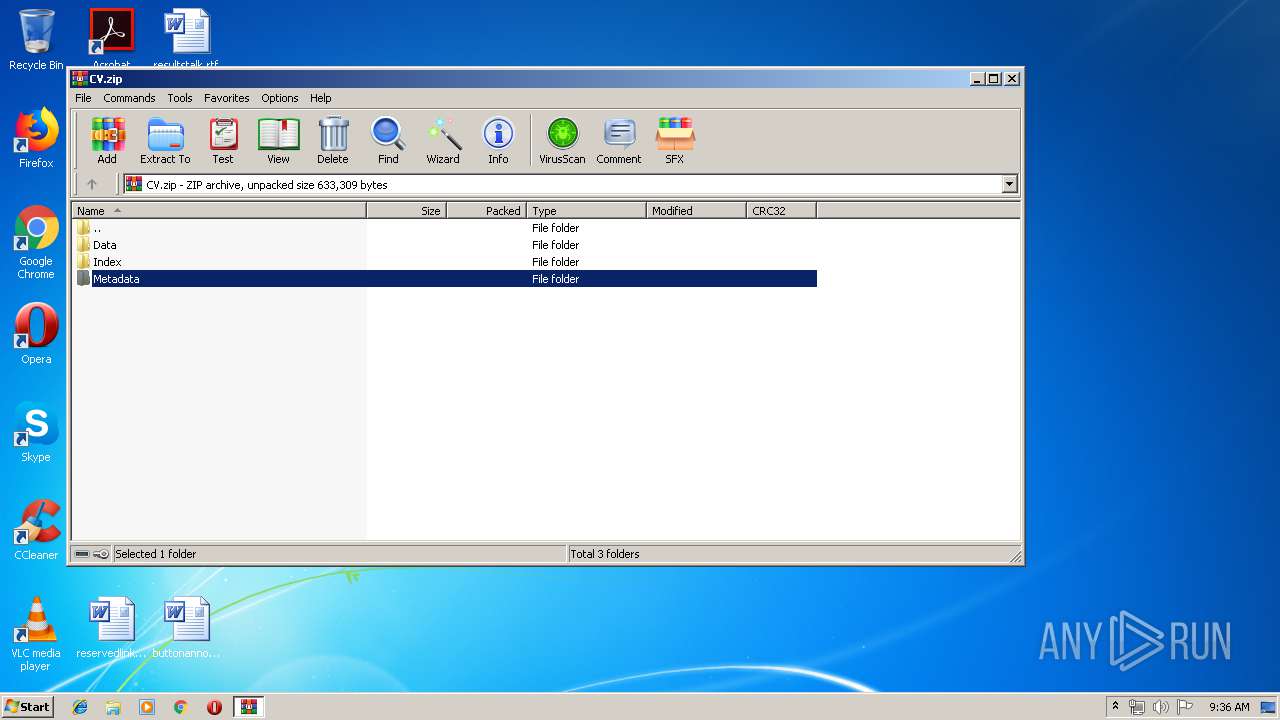
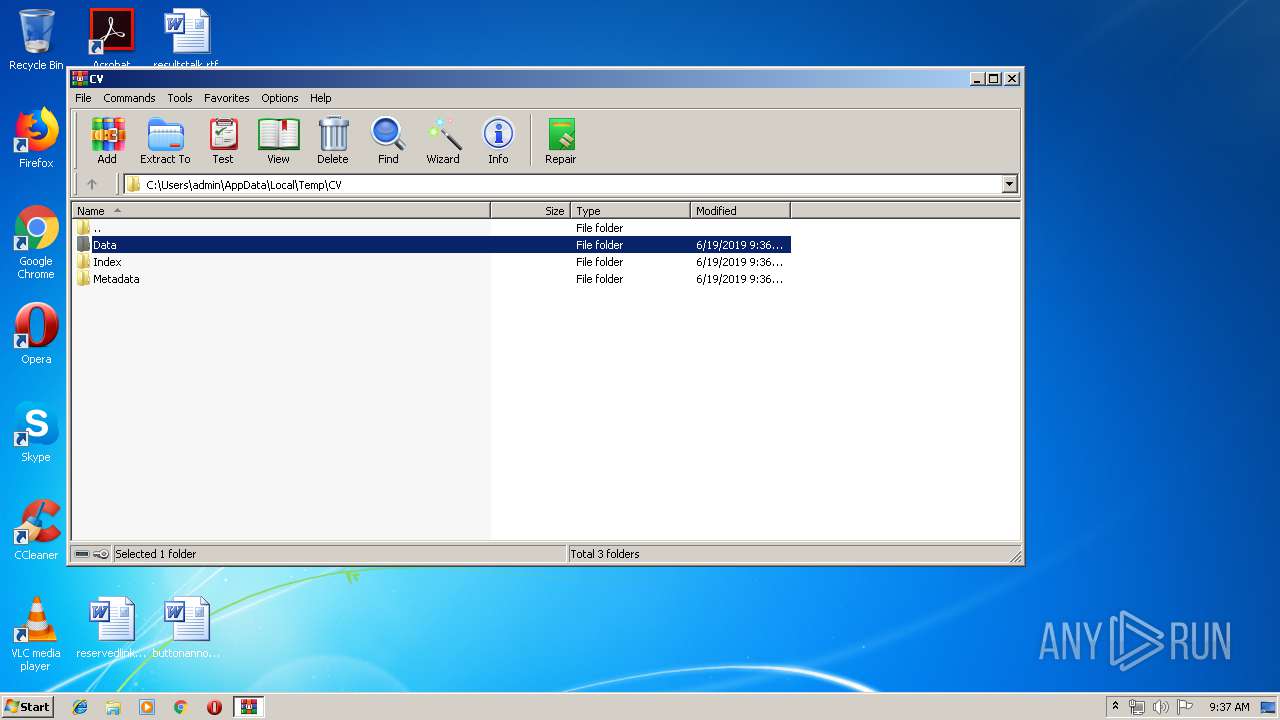
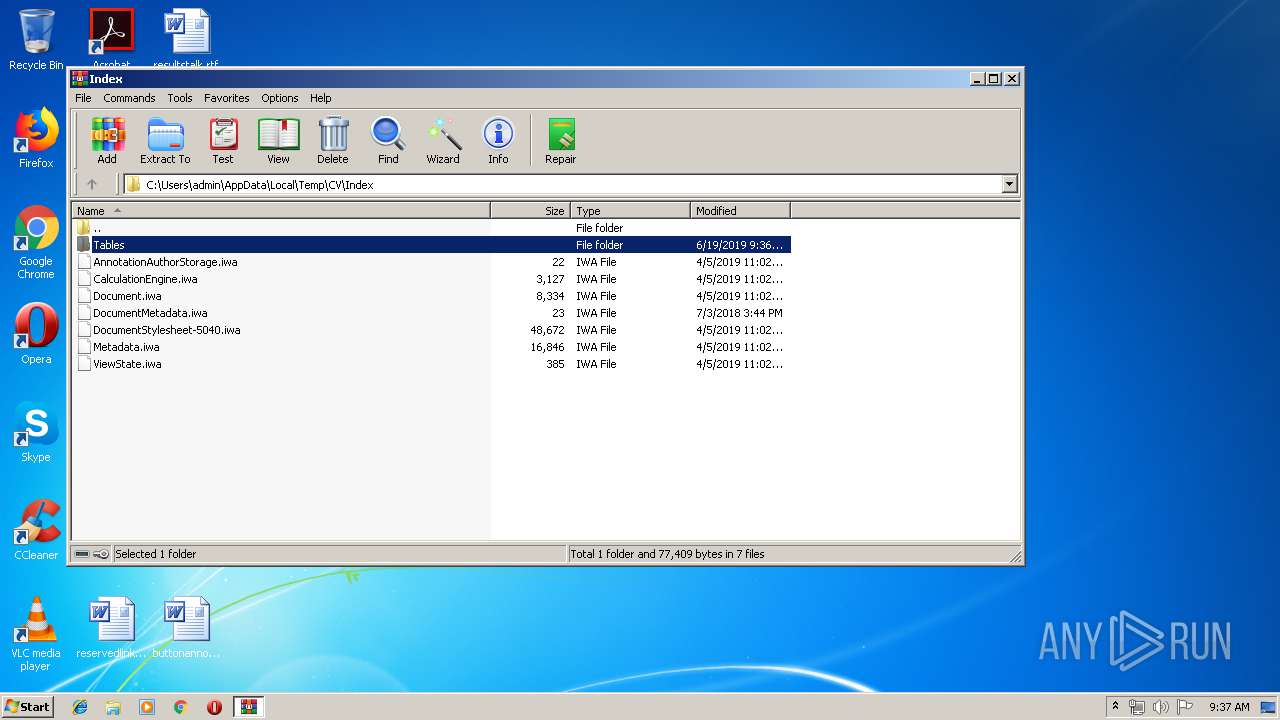
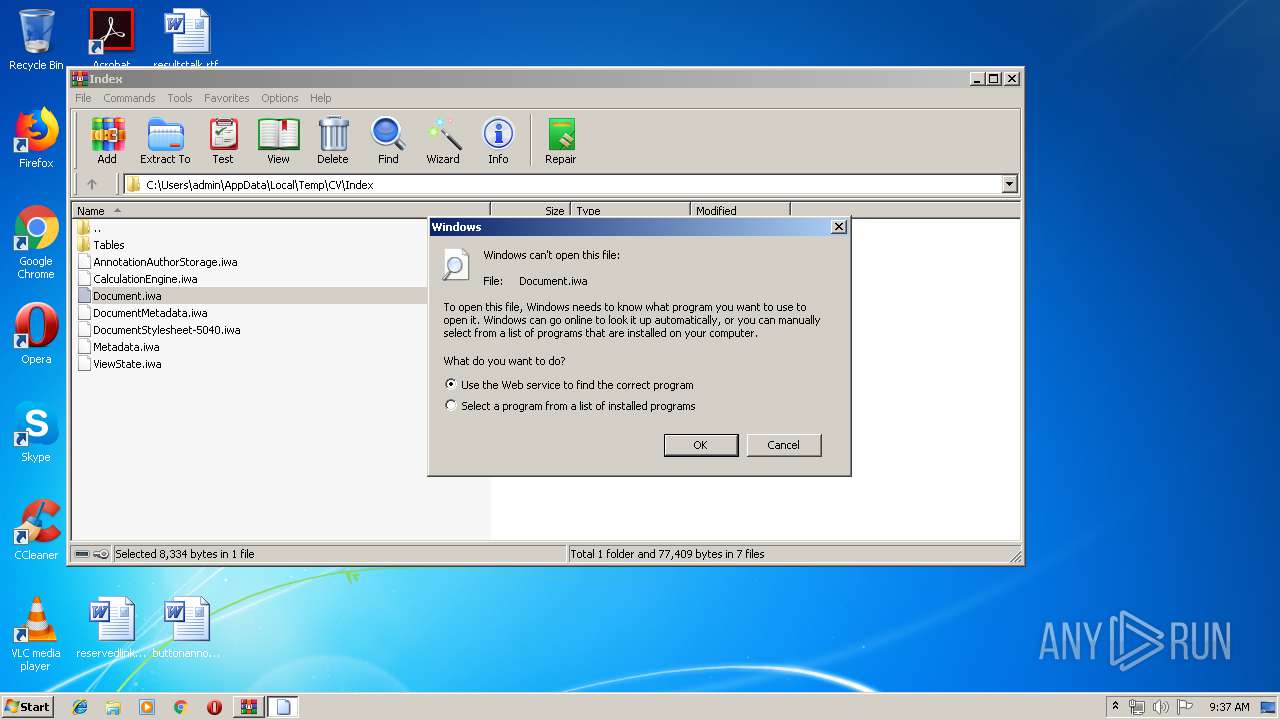
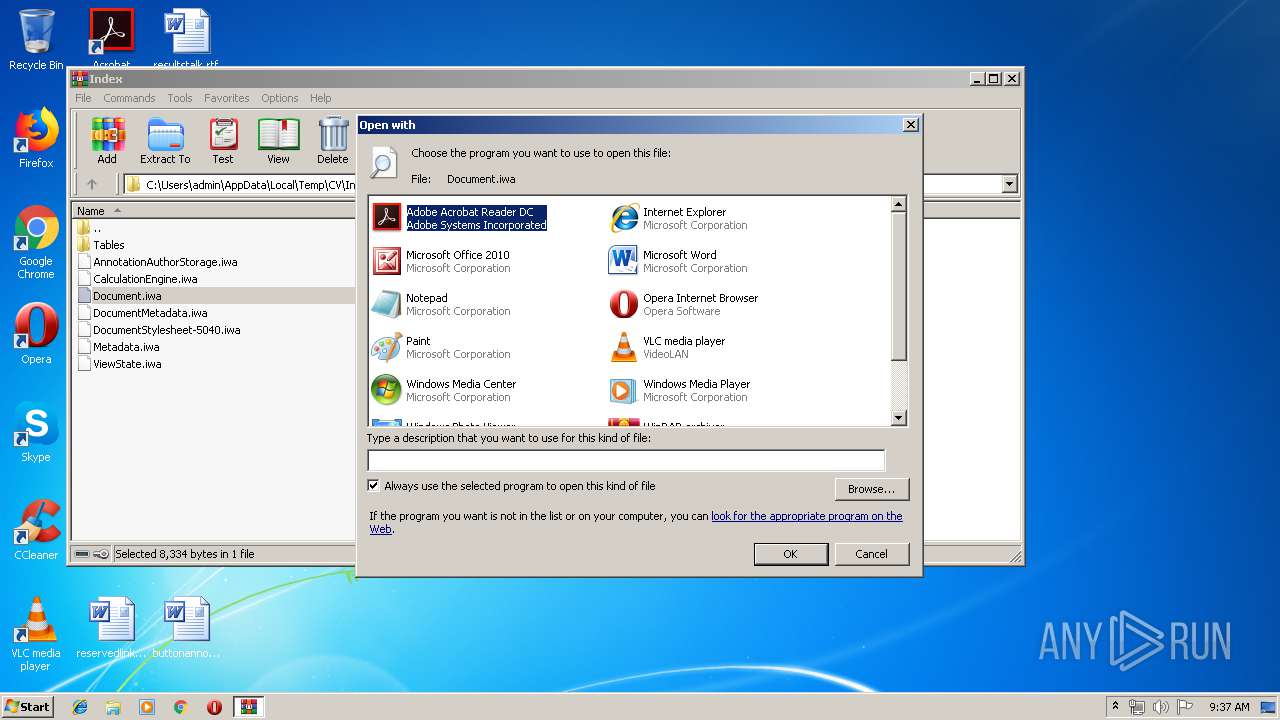
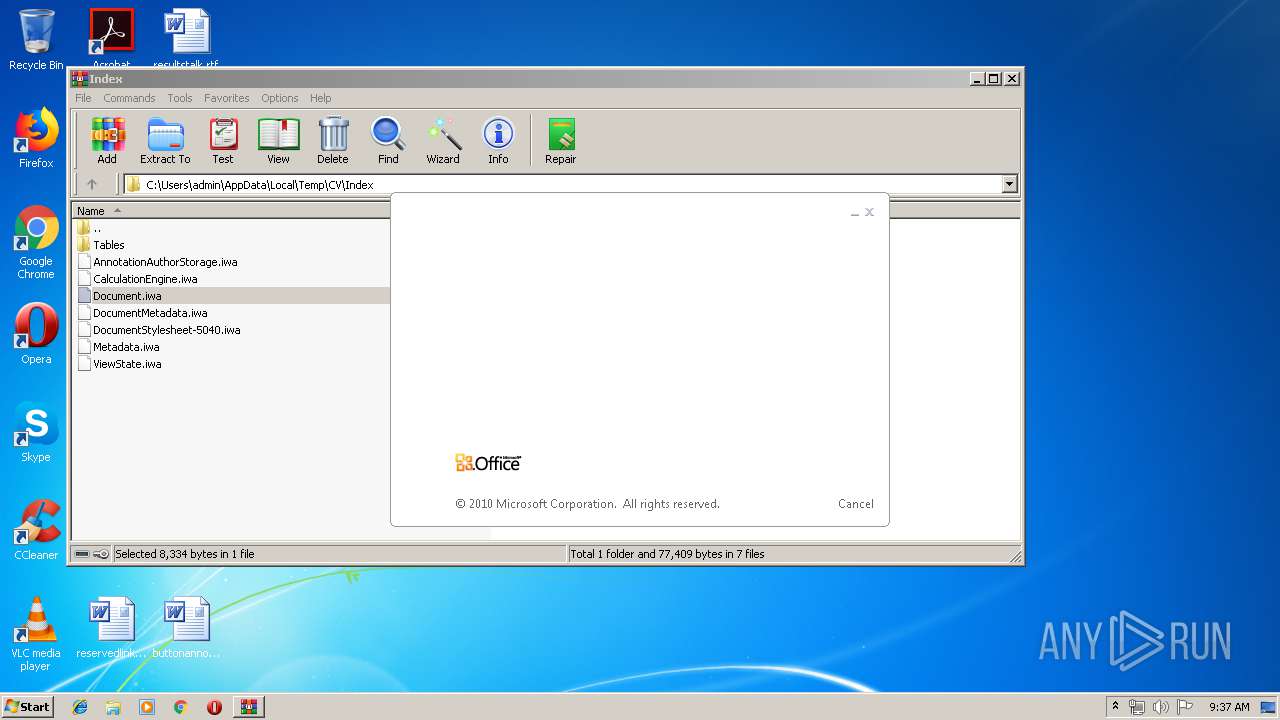
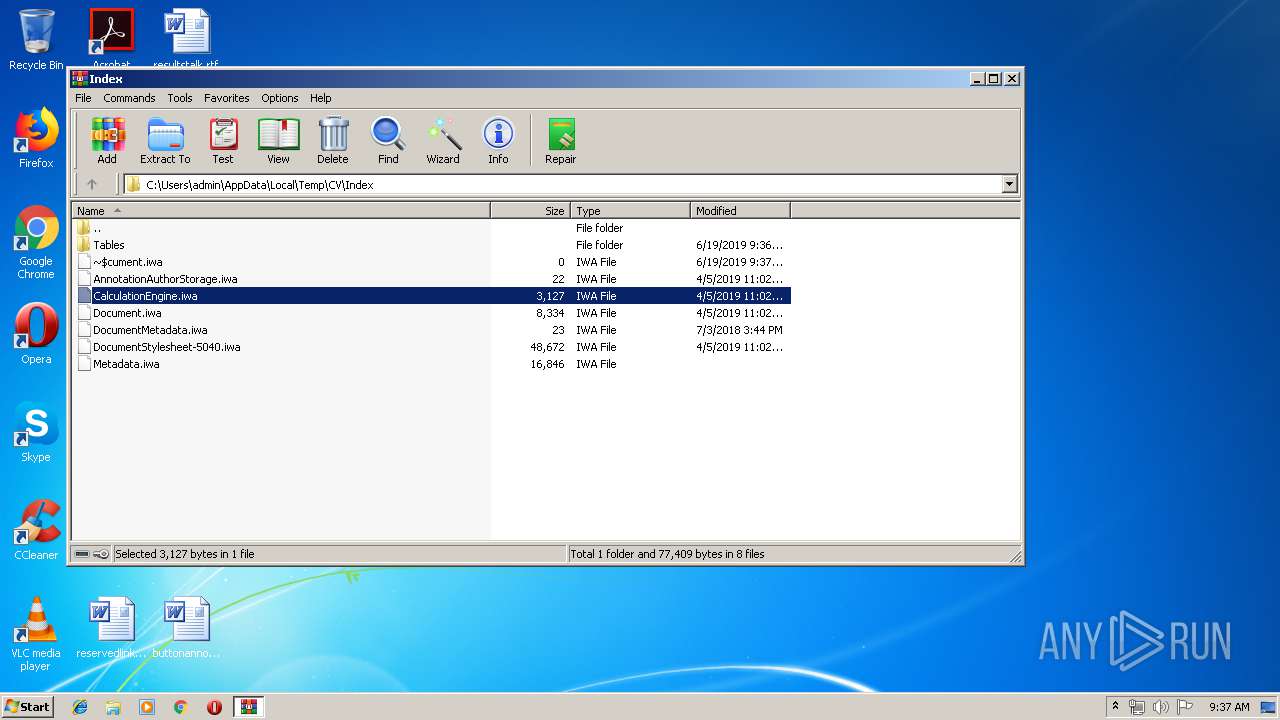
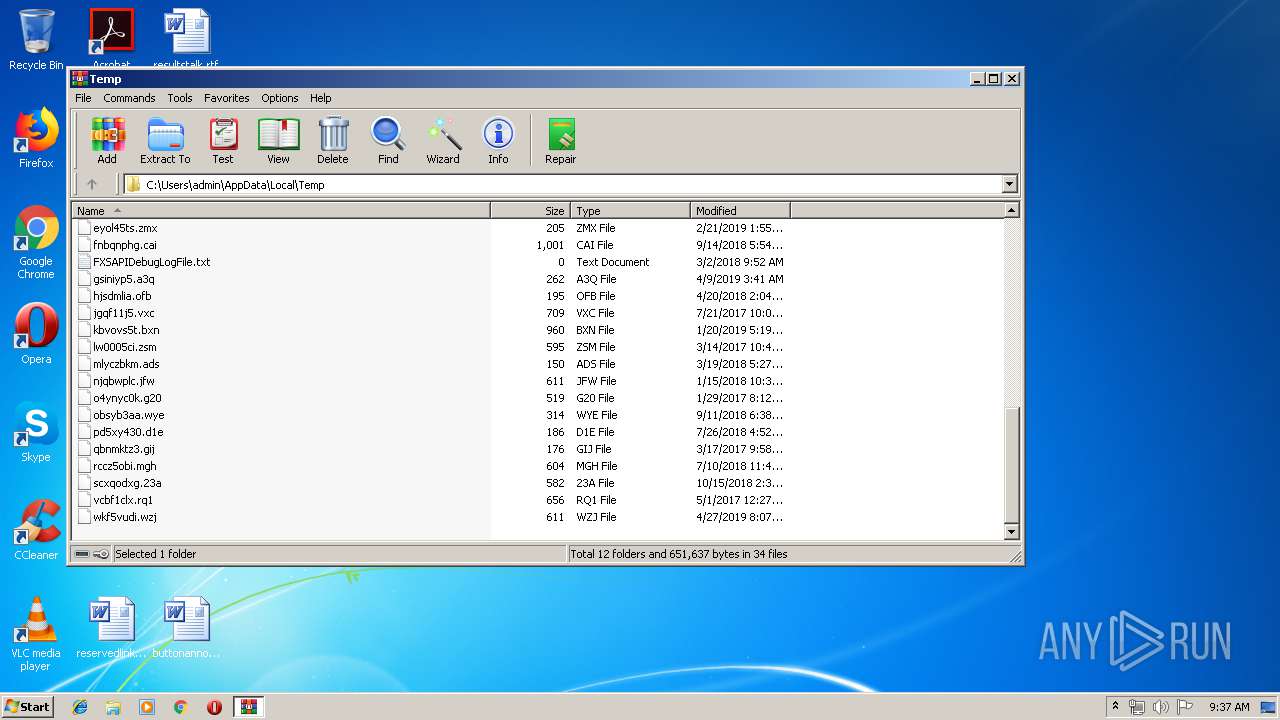
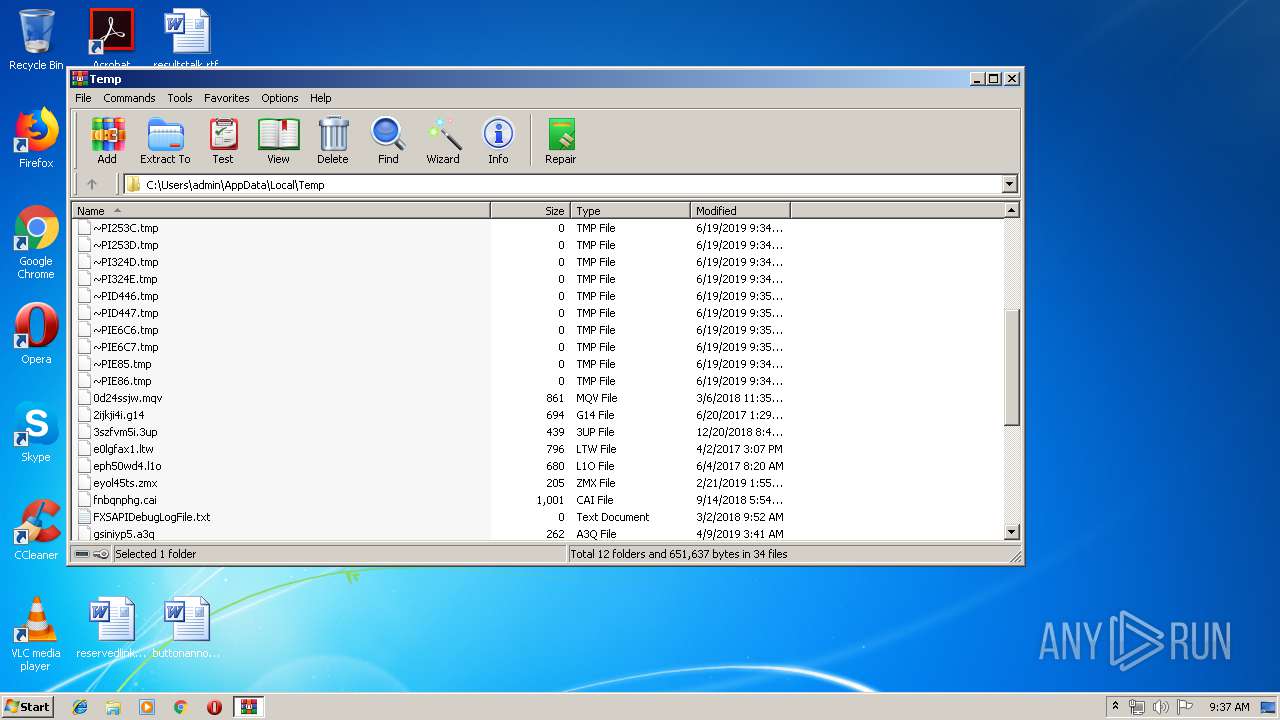
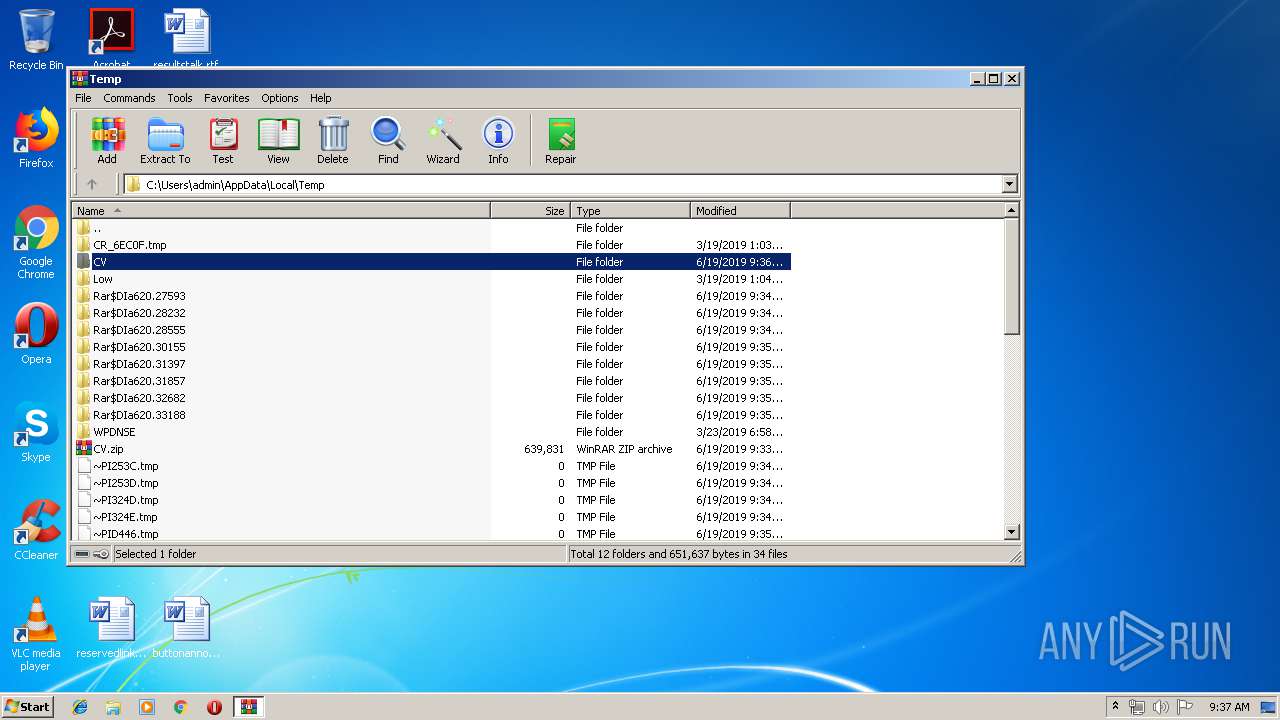
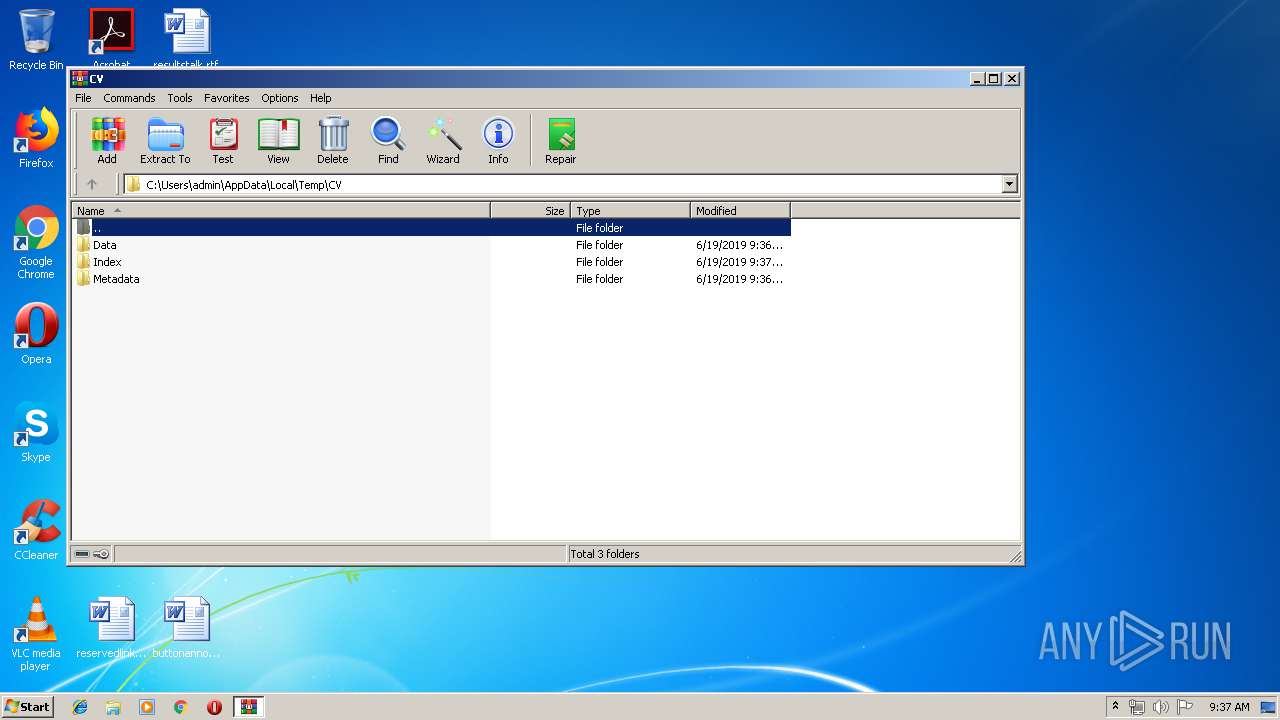
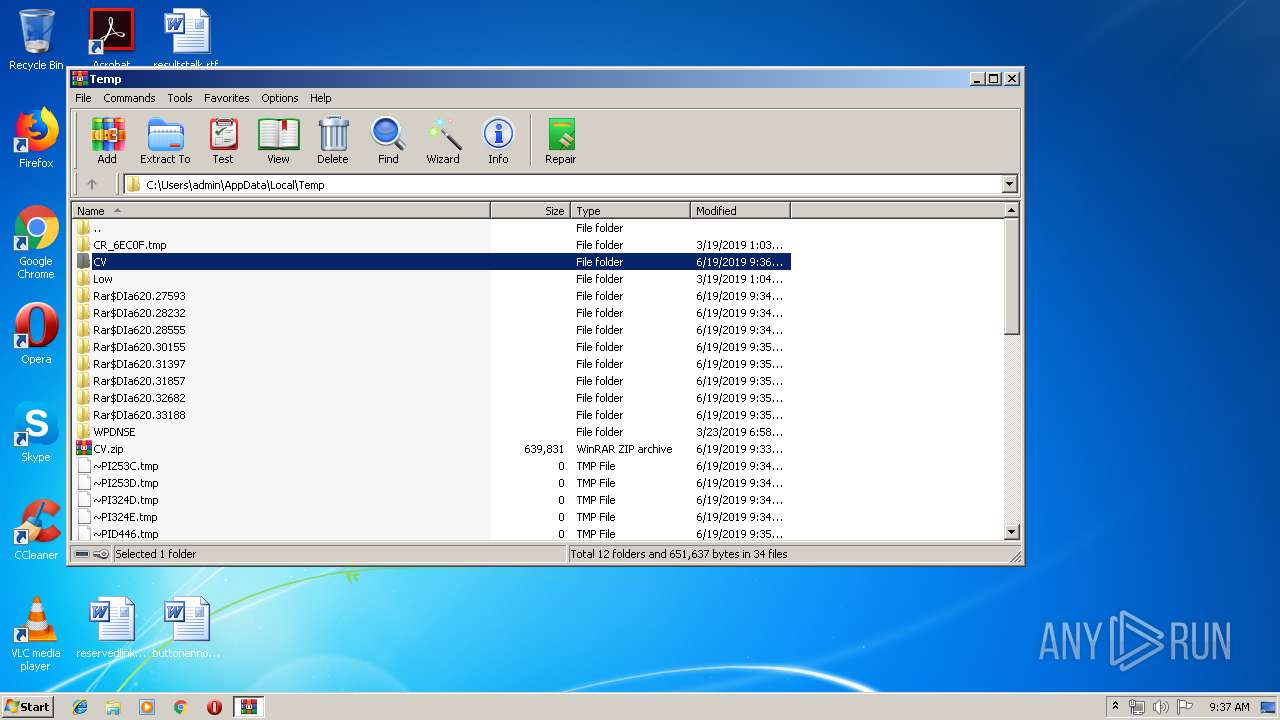
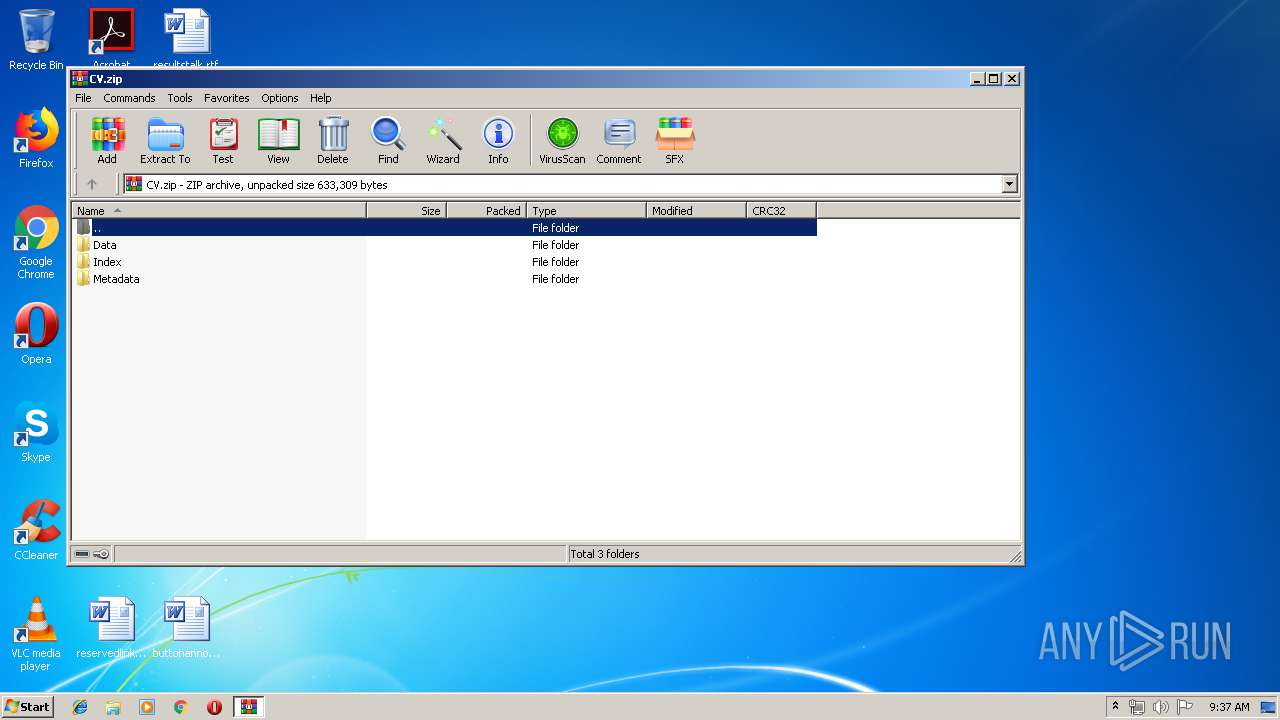
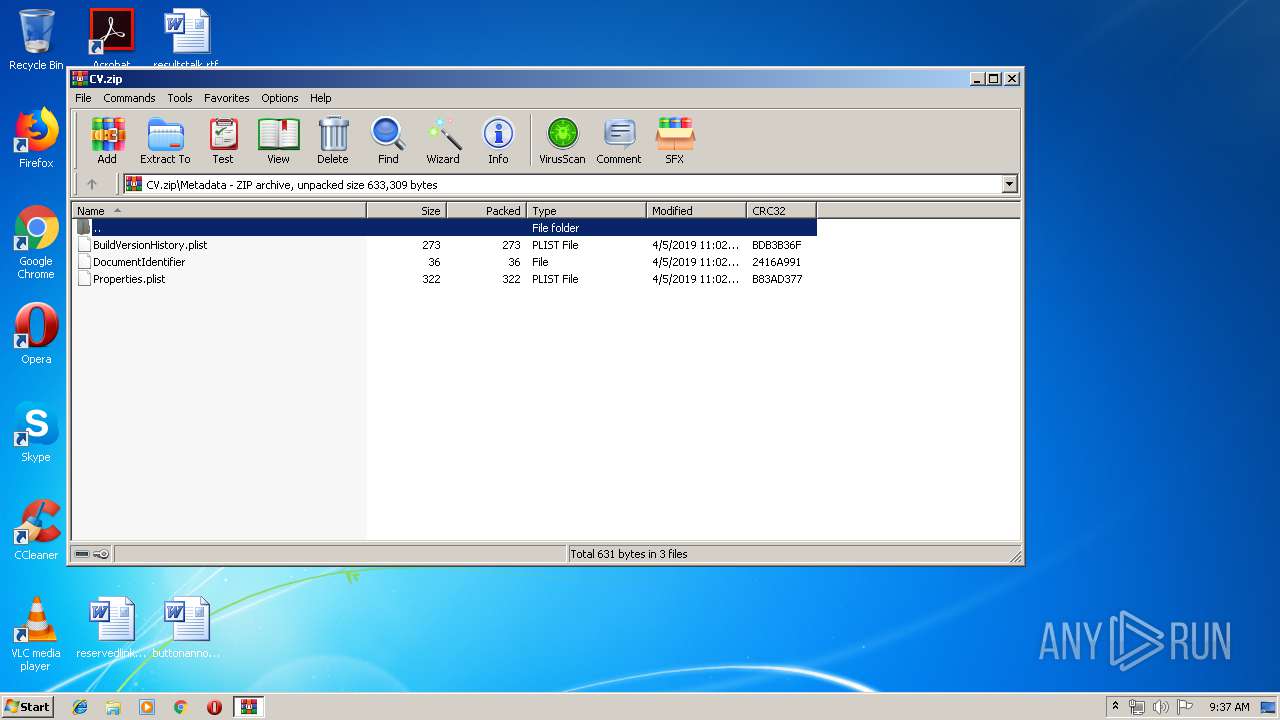
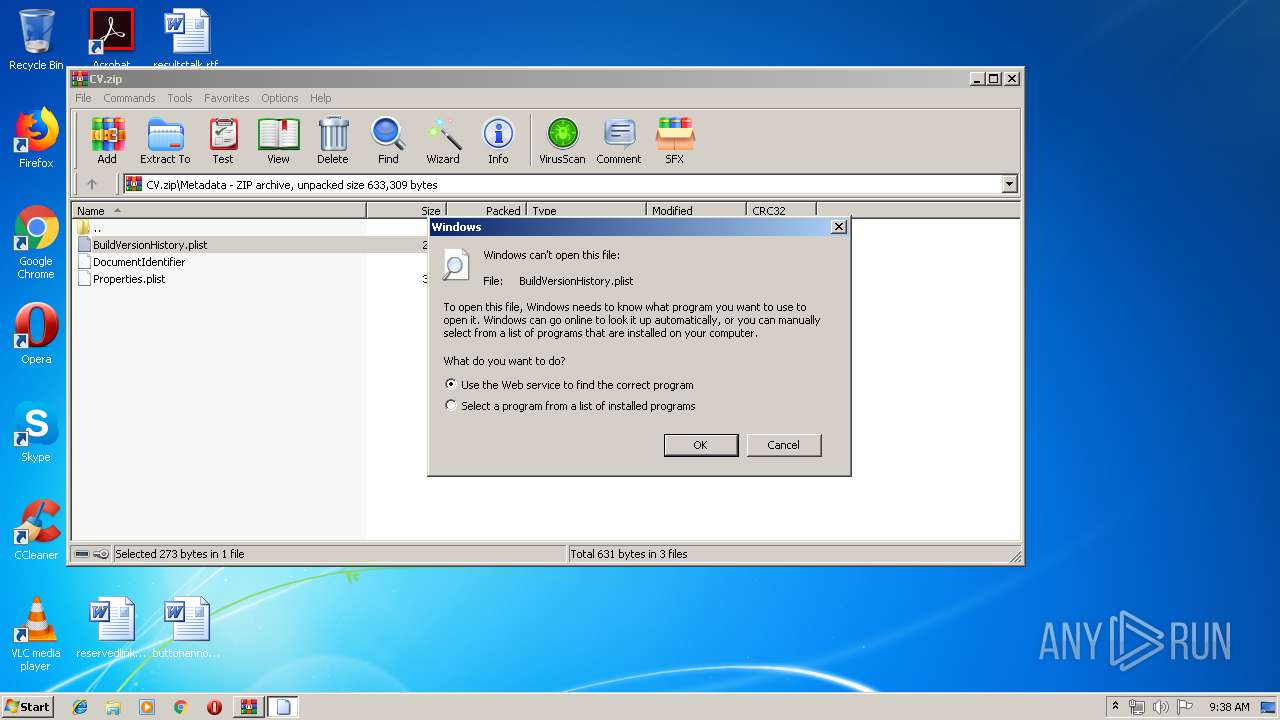
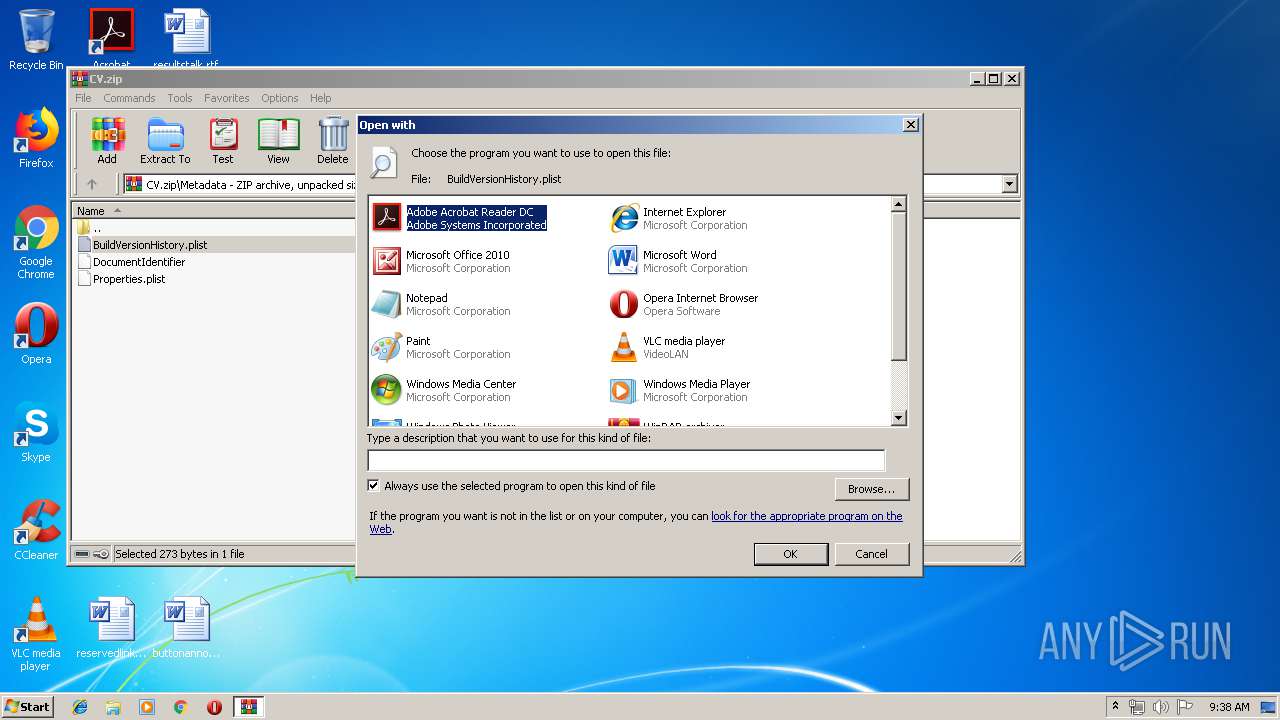
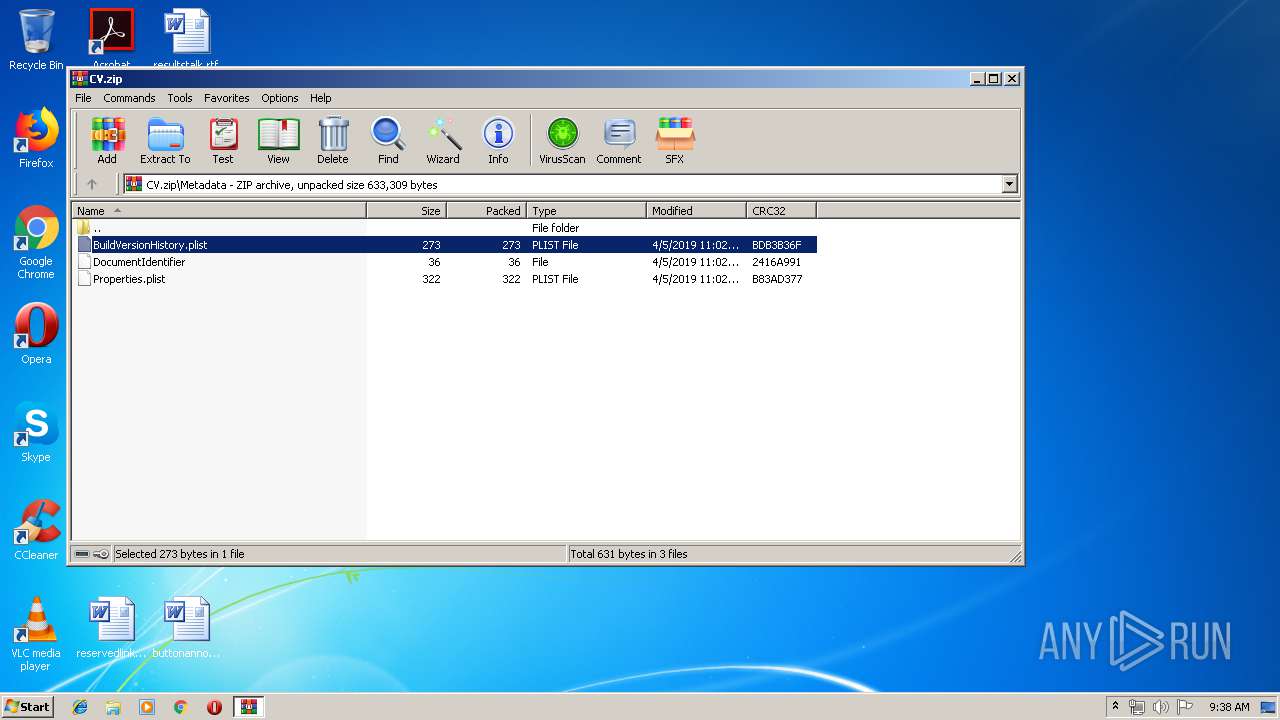
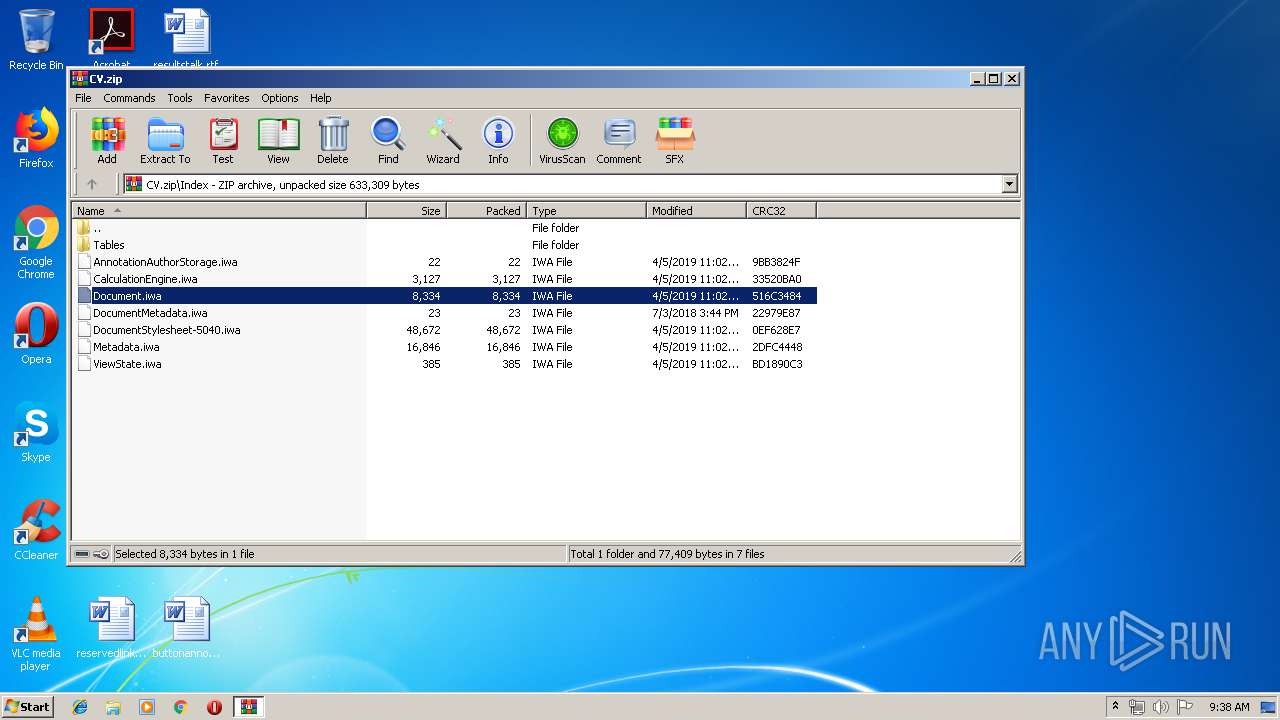
| File name: | CV.zip |
| Full analysis: | https://app.any.run/tasks/e638b895-f1ca-489c-ae02-a481bb19bc77 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 08:33:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6A34DB2A3ADECEA4F6BE3C684DDD76CA |
| SHA1: | 6D9F00AF4305E5456B030364B2781B5EEEDC0D05 |
| SHA256: | 58C15C193099FB4E43FF25D5463E52C46951716F013AD80EB94F5FEE6D971140 |
| SSDEEP: | 12288:uXYEjP5xpBF42cRL3/4zcE1crx3SBYSCpJycBbqAvIebu8XAf6qcaO3m0svFei:uoWxpr+RIcE1cl3m+poI6bcd3m0sR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 2480)
- DllHost.exe (PID: 920)
Starts Microsoft Office Application
- rundll32.exe (PID: 3528)
- rundll32.exe (PID: 3912)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 620)
Starts Internet Explorer
- rundll32.exe (PID: 3448)
INFO
Modifies the open verb of a shell class
- rundll32.exe (PID: 3540)
Creates files in the user directory
- WINWORD.EXE (PID: 2320)
- iexplore.exe (PID: 408)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2320)
- WINWORD.EXE (PID: 2544)
Changes internet zones settings
- iexplore.exe (PID: 2492)
Reads settings of System Certificates
- iexplore.exe (PID: 408)
- iexplore.exe (PID: 2492)
Reads Internet Cache Settings
- iexplore.exe (PID: 408)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2492)
Reads internet explorer settings
- iexplore.exe (PID: 408)
Changes settings of System certificates
- iexplore.exe (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pages | | | Pages document (83) |
|---|---|---|
| .zan | | | BlueEyes Animation (13) |
| .zip | | | ZIP compressed archive (3.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:04:05 11:02:08 |
| ZipCRC: | 0x7cbd0982 |
| ZipCompressedSize: | 103463 |
| ZipUncompressedSize: | 103463 |
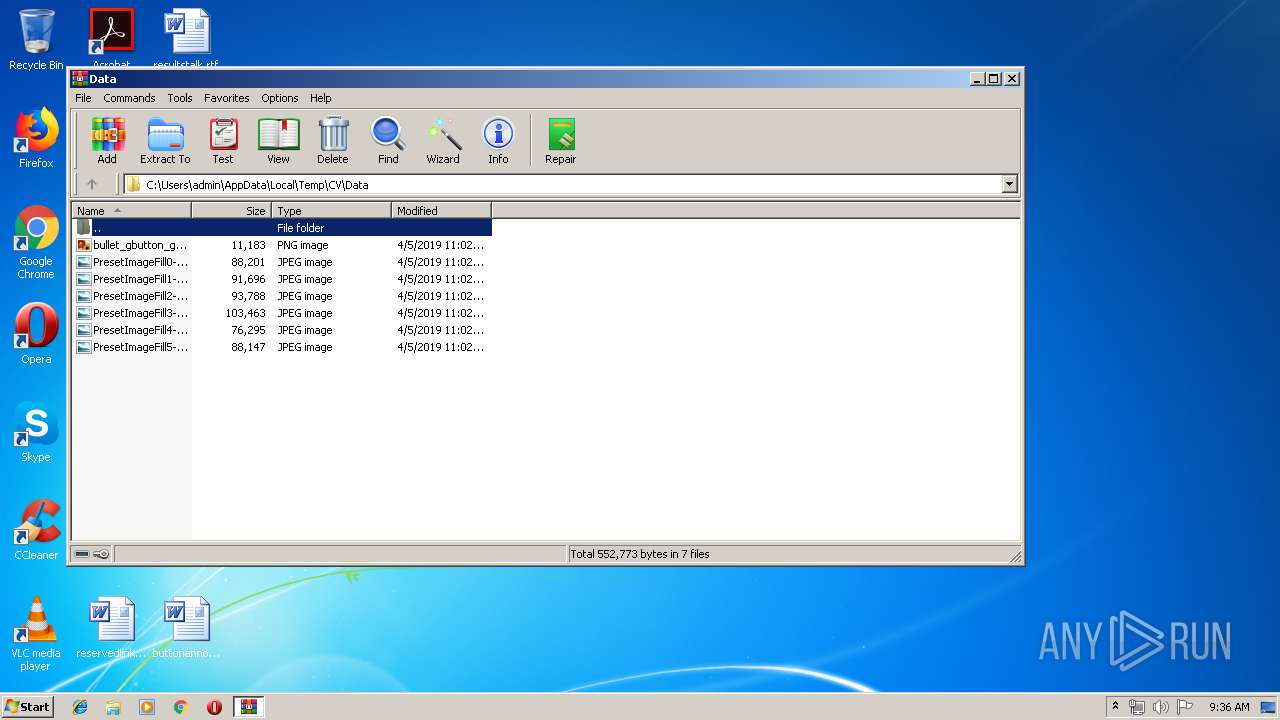
| ZipFileName: | Data/PresetImageFill3-13.jpg |
Total processes
48
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2492 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
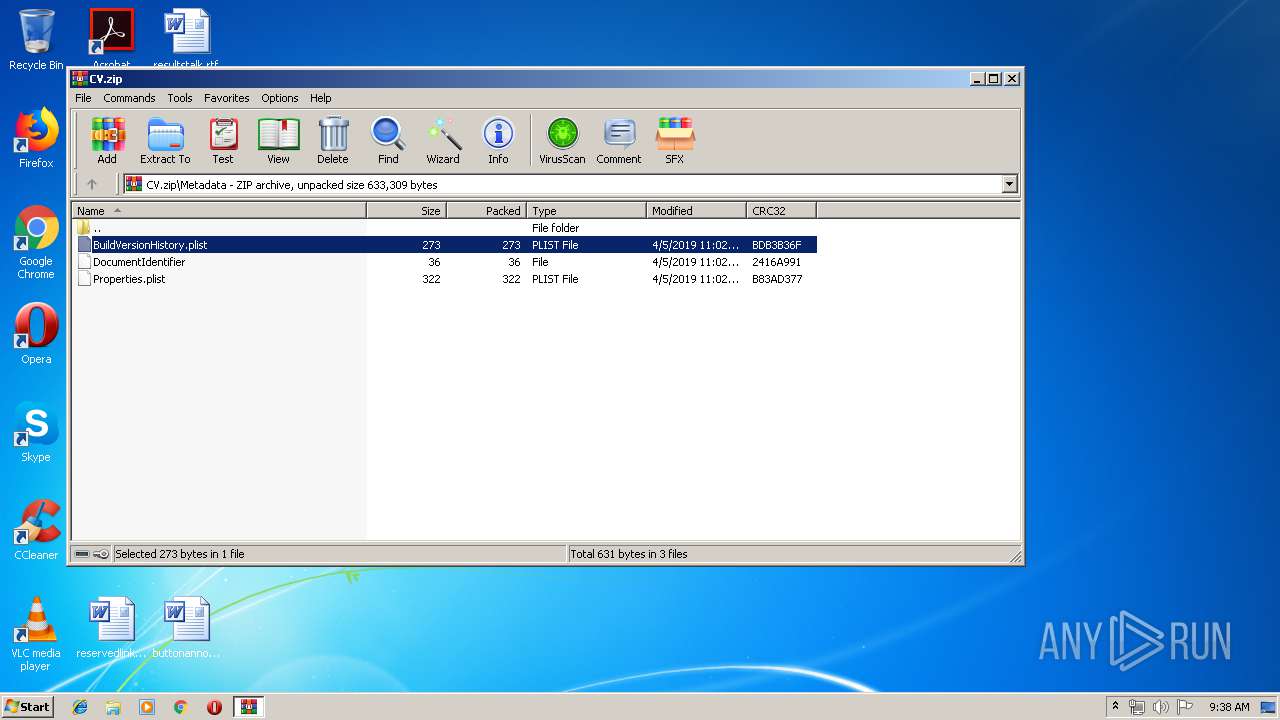
| 620 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CV.zip.pages" | C:\Program Files\WinRAR\WinRAR.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
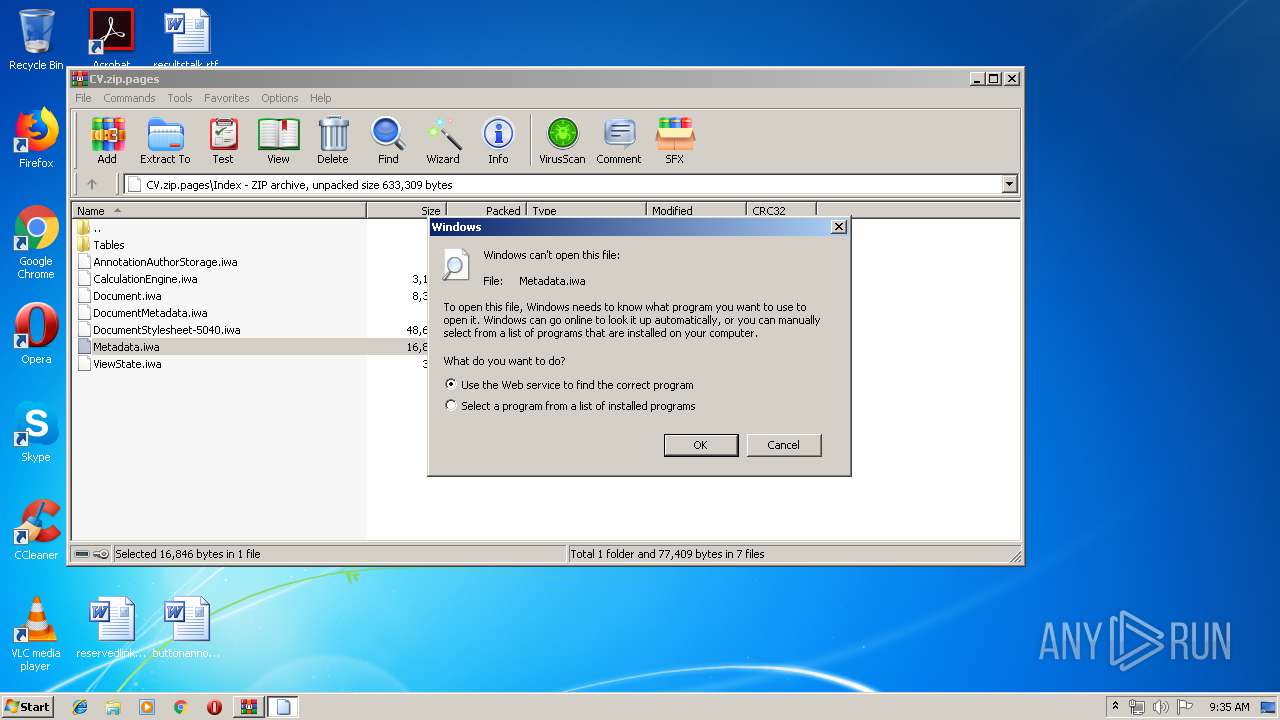
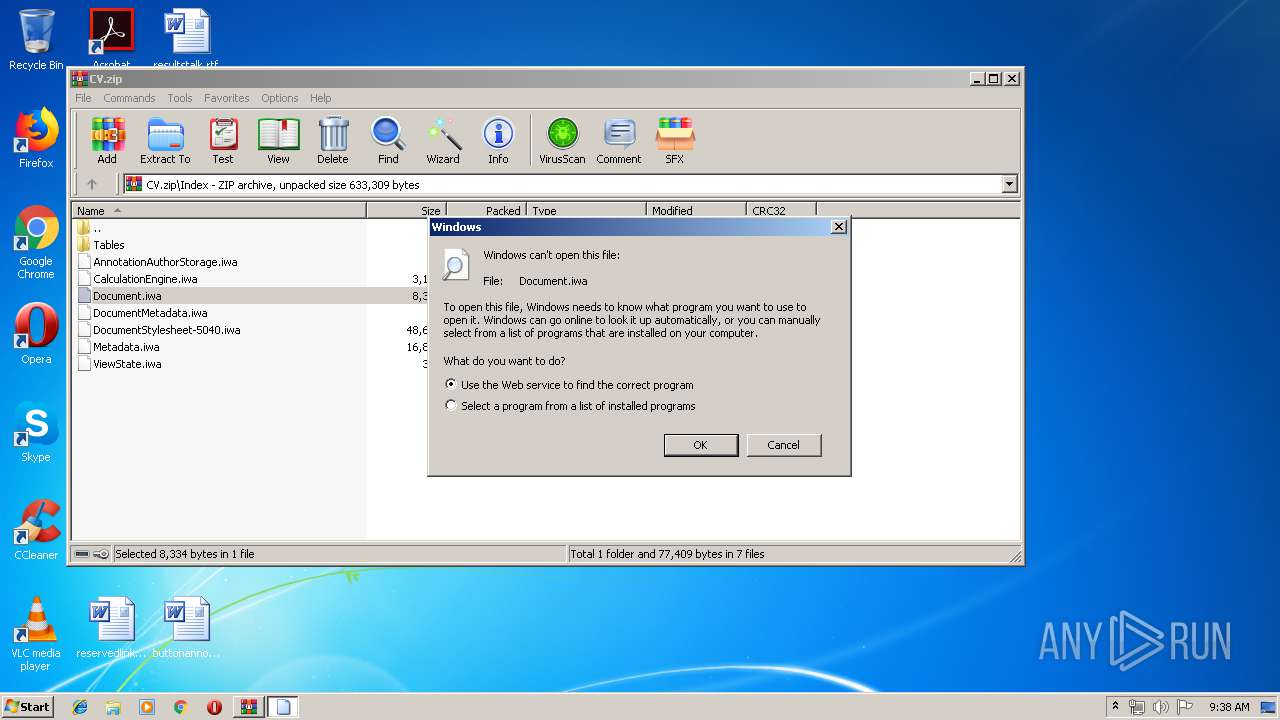
| 900 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa620.30155\Metadata.iwa | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
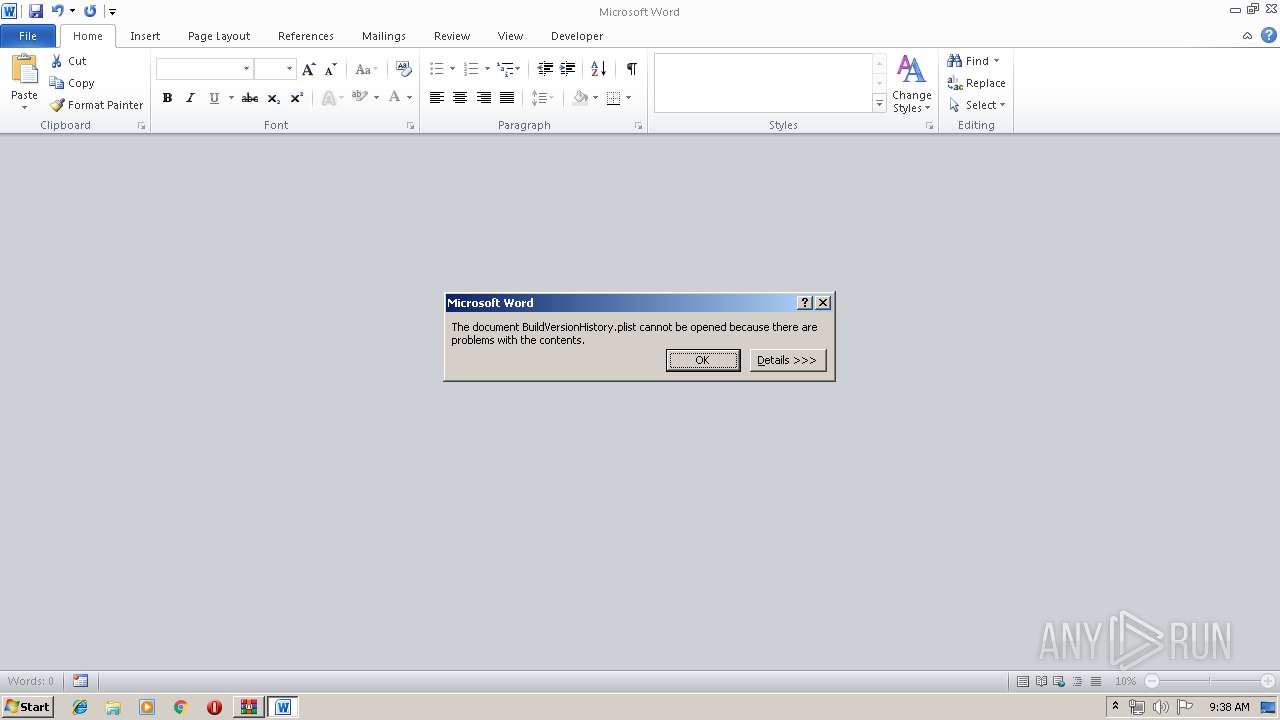
| 2132 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa620.31857\BuildVersionHistory.plist | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
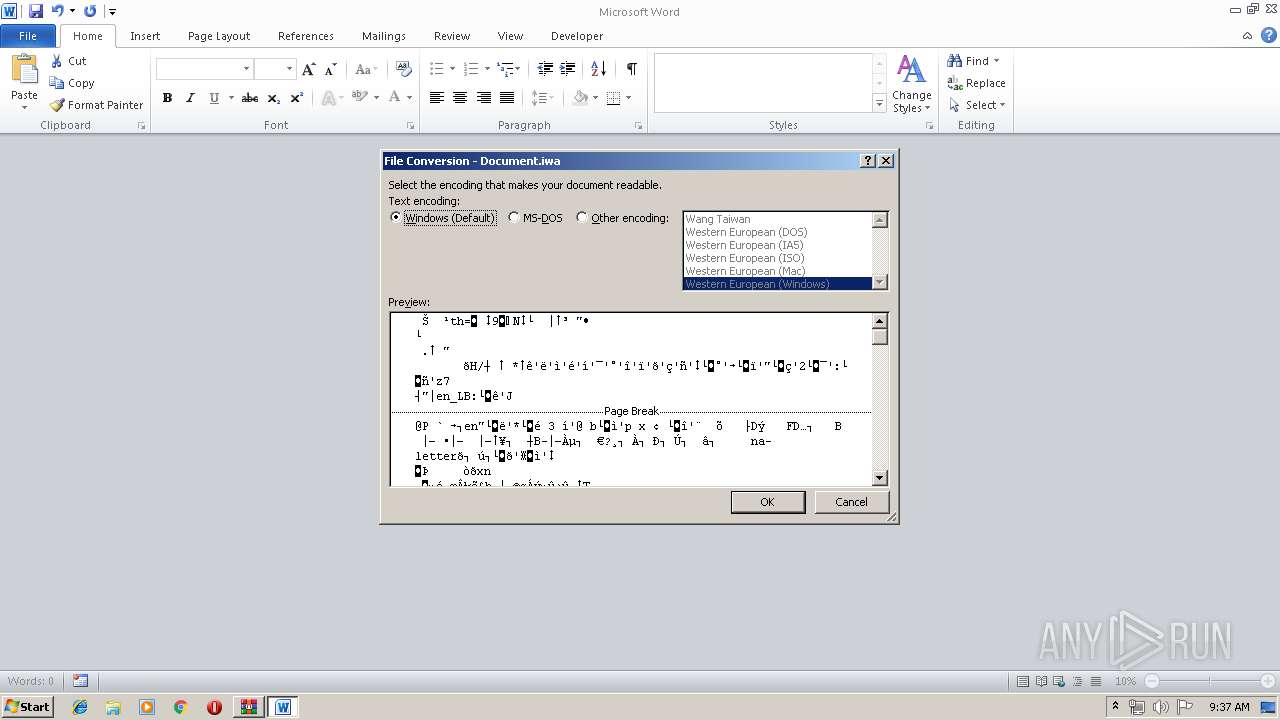
| 2320 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\CV\Index\Document.iwa" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2480 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIa620.48279\BuildVersionHistory.plist" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3448 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa620.263\Document.iwa | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 931
Read events
3 473
Write events
439
Delete events
19
Modification events
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3540) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
0
Suspicious files
39
Text files
44
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa620.28232\PresetImageFill0-10.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa620.31397\DocumentIdentifier | text | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa620.28555\PresetImageFill1-11.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill1-11.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill3-13.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa620.31857\BuildVersionHistory.plist | xml | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill2-12.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill5-15.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill0-10.jpg | image | |
MD5:— | SHA256:— | |||
| 620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CV\Data\PresetImageFill4-14.jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
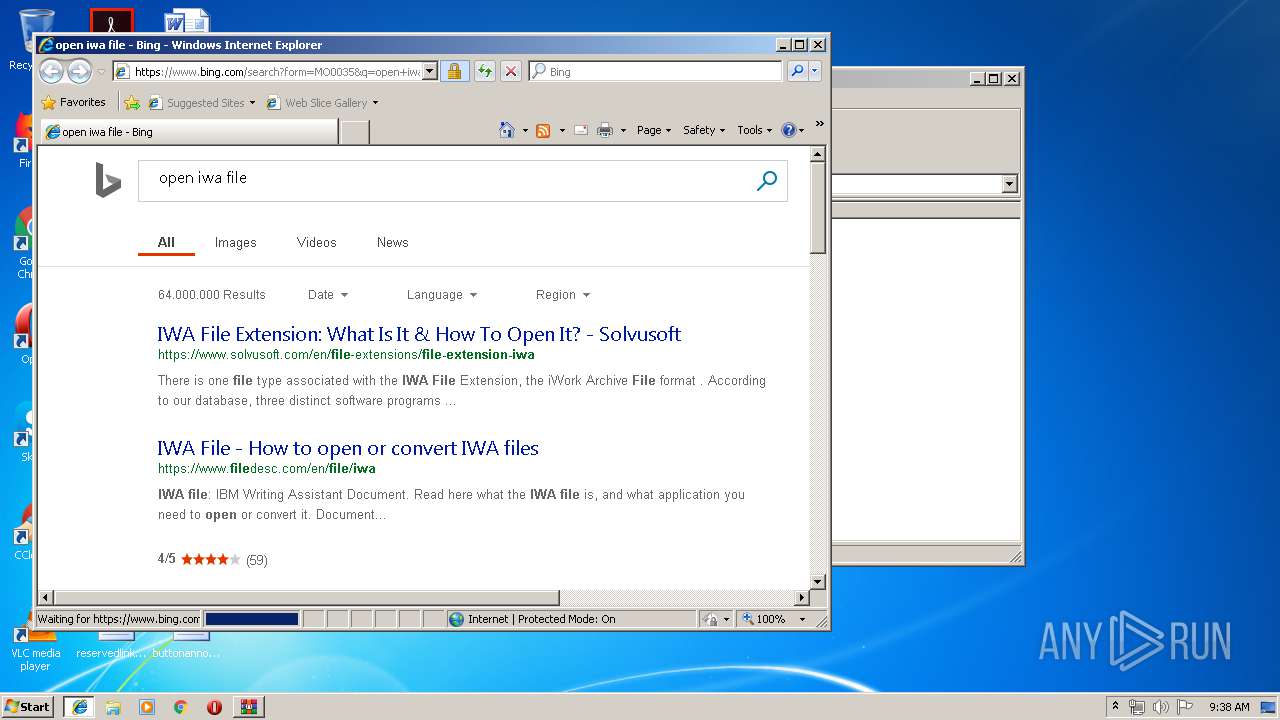
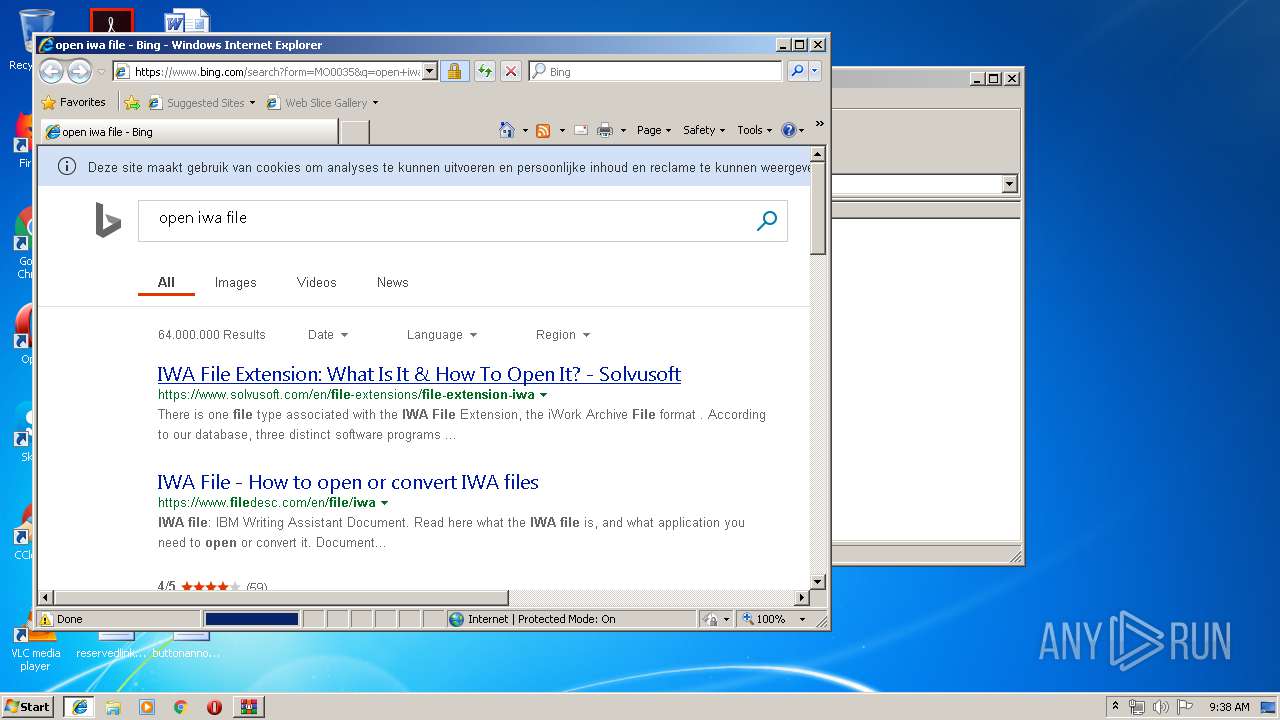
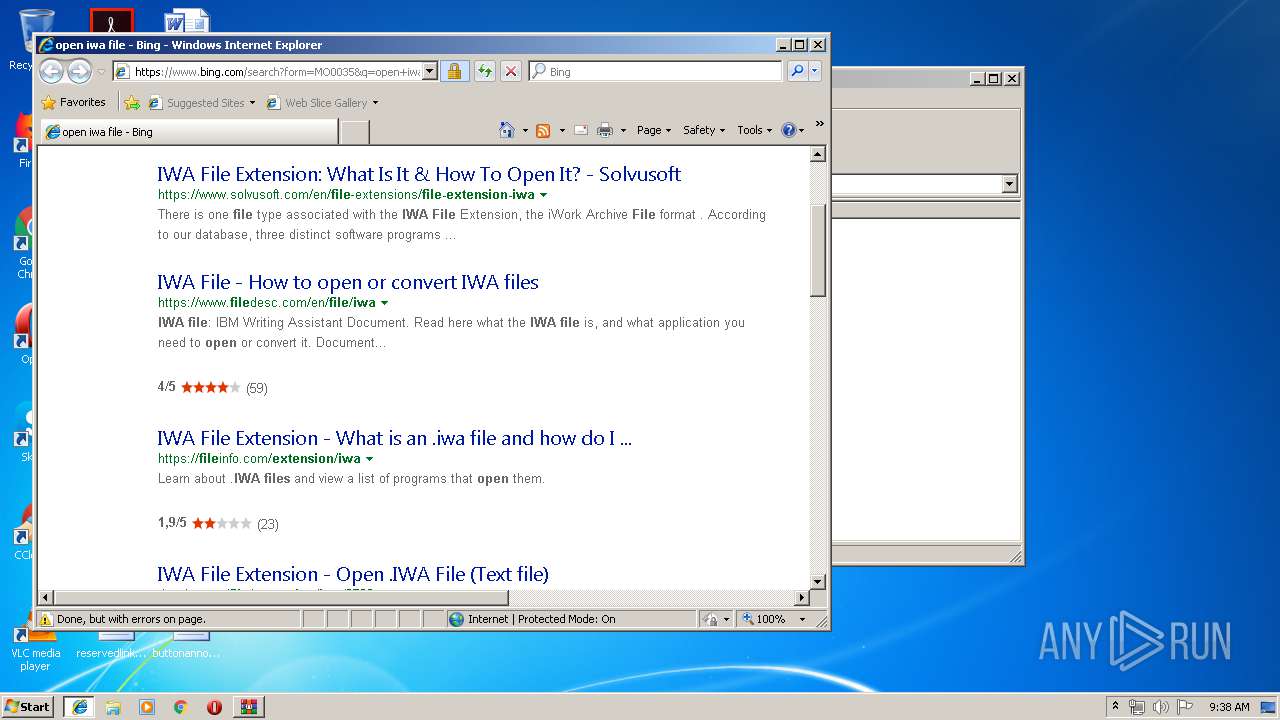
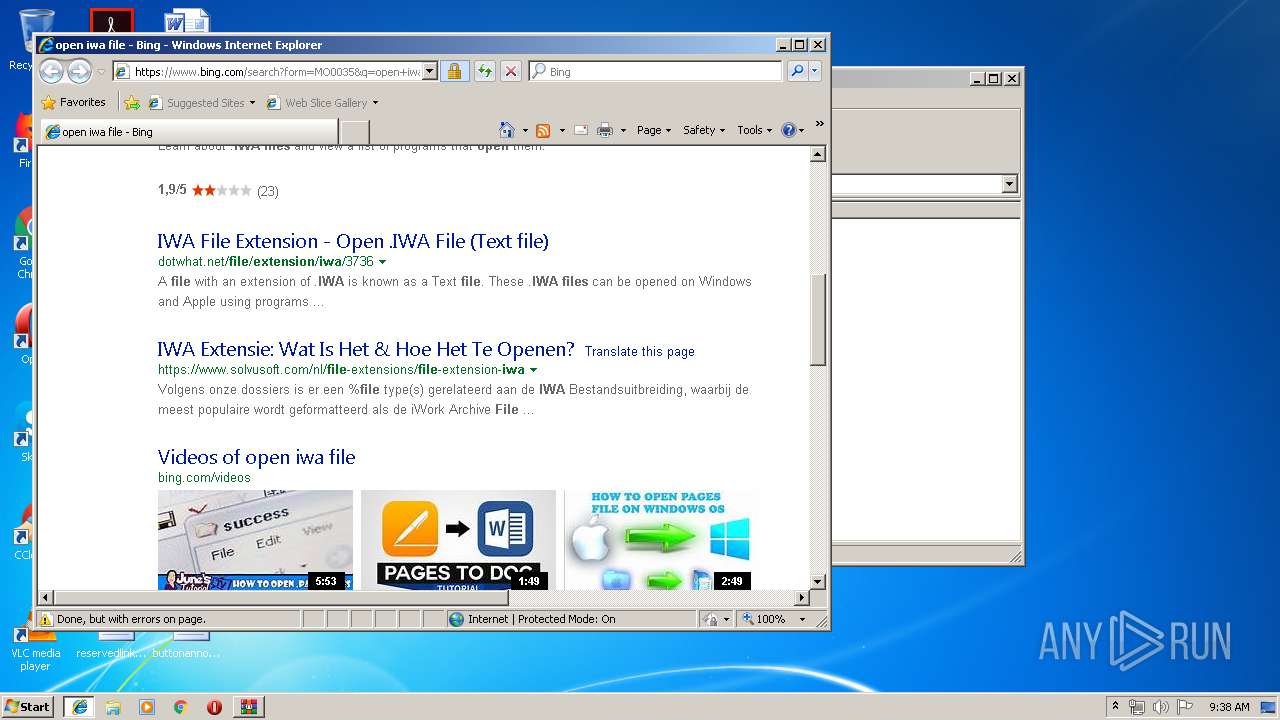
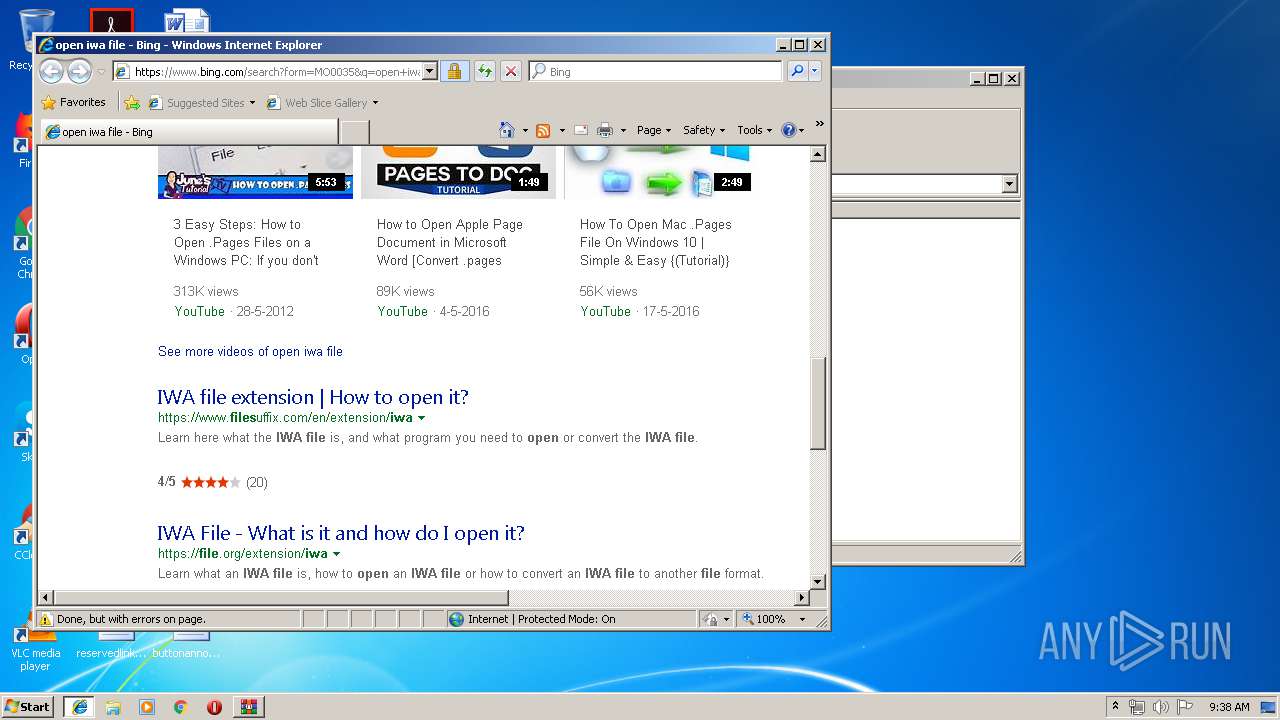
408 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=iwa | unknown | — | — | whitelisted |
408 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=iwa | unknown | — | — | whitelisted |
2492 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
408 | iexplore.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
2492 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
408 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
408 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2492 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
408 | iexplore.exe | 40.90.23.209:443 | login.live.com | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.live.com |
| whitelisted |