| File name: | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe |
| Full analysis: | https://app.any.run/tasks/a16ec9c2-3f0f-46c8-a9e2-d9b0567e587a |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2025, 01:47:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 89F04AF58444565D36B3DB5C75FB0C0E |
| SHA1: | 0257AFE2C49A1FA3D22D62E62ECF7B0844D06AAE |
| SHA256: | 58B405D695AFD36CC8E2666D65444ABCFB10B921ED5541520420AB83D1F8DA96 |
| SSDEEP: | 98304:XRRbb5dM0PO4pklpXDHdh68CJOmXZjENhDa5F8YQBkb9qZaMzdS0dWM7LwVBd/Ns:1U5f7GNwOv6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
The process creates files with name similar to system file names
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Executable content was dropped or overwritten
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Malware-specific behavior (creating "System.dll" in Temp)
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
There is functionality for taking screenshot (YARA)
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
- Uninstall.exe (PID: 5236)
Drops 7-zip archiver for unpacking
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Creates/Modifies COM task schedule object
- Uninstall.exe (PID: 5236)
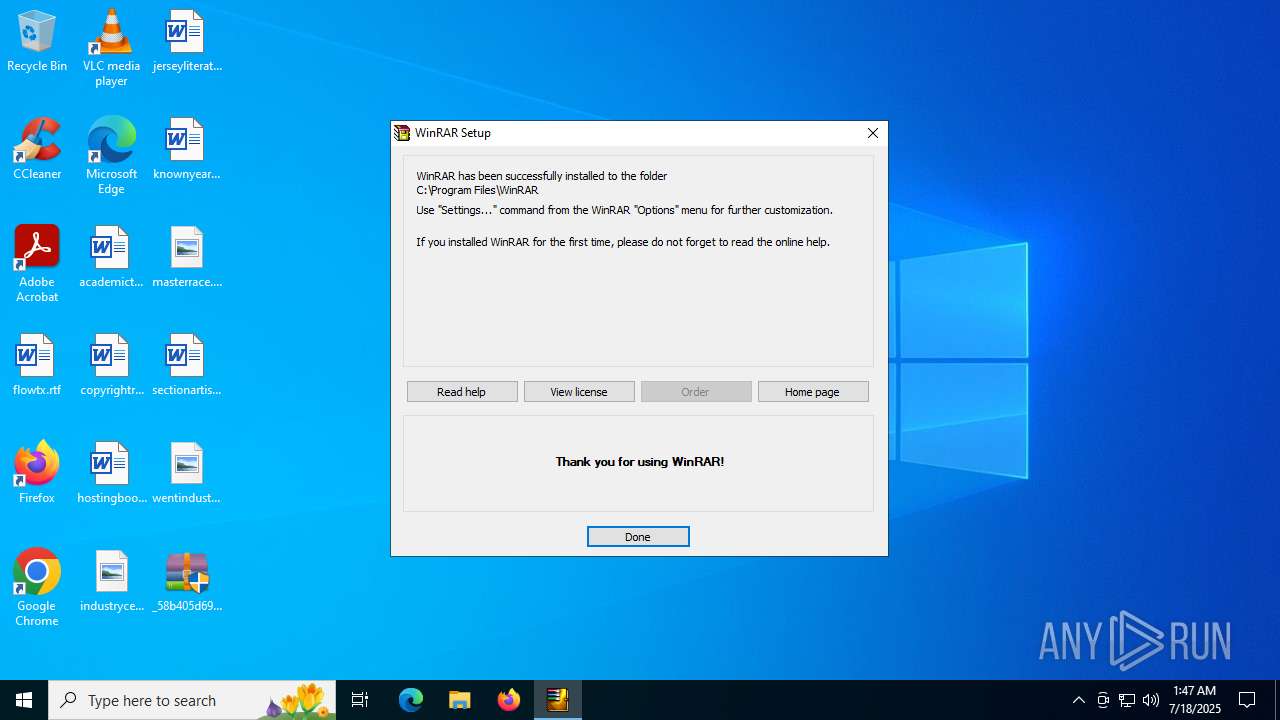
Creates a software uninstall entry
- Uninstall.exe (PID: 5236)
INFO
Reads the computer name
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
- Uninstall.exe (PID: 5236)
Create files in a temporary directory
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Checks supported languages
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
- Uninstall.exe (PID: 5236)
The sample compiled with english language support
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Creates files in the program directory
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
- Uninstall.exe (PID: 5236)
UPX packer has been detected
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
The sample compiled with russian language support
- _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe (PID: 2096)
Creates files or folders in the user directory
- Uninstall.exe (PID: 5236)
Checks proxy server information
- slui.exe (PID: 4476)
Reads the software policy settings
- slui.exe (PID: 4476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:19:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28672 |
| InitializedDataSize: | 445952 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x39e3 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.50.0.0 |
| ProductVersionNumber: | 5.50.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Alexander Roshal |
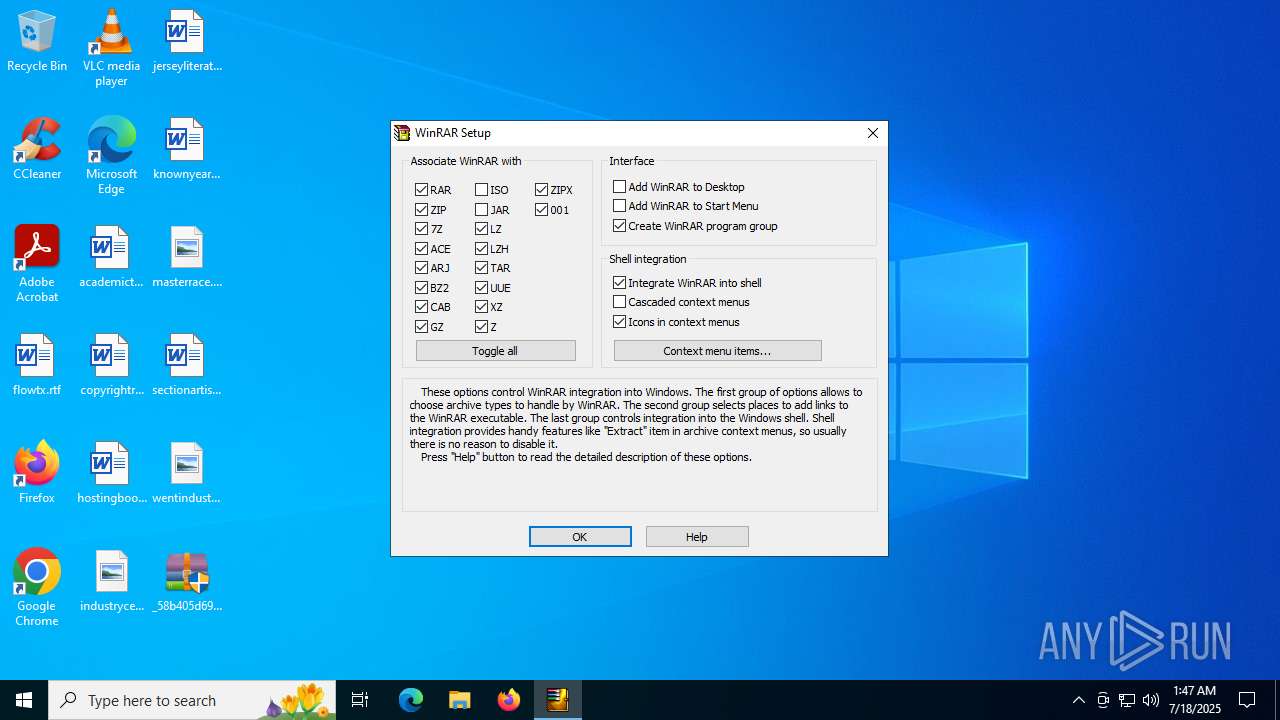
| FileDescription: | WinRAR v5.50 |
| FileVersion: | 5.50.0.0 |
| LegalCopyright: | © Alexander Roshal |
| ProductName: | WinRAR v5.50 |
Total processes
136
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | "C:\Users\admin\Desktop\_58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe" | C:\Users\admin\Desktop\_58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR v5.50 Version: 5.50.0.0 Modules
| |||||||||||||||
| 3788 | "C:\Users\admin\Desktop\_58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe" | C:\Users\admin\Desktop\_58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR v5.50 Exit code: 3221226540 Version: 5.50.0.0 Modules
| |||||||||||||||
| 4476 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\Program Files\WinRAR\Uninstall.exe" /setup | C:\Program Files\WinRAR\Uninstall.exe | — | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: Uninstall WinRAR Version: 5.50.0 Modules
| |||||||||||||||
Total events
3 921
Read events
3 844
Write events
75
Delete events
2
Modification events
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.rar |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.zip |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.cab |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.arj |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.lz |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.lzh |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.ace |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.7z |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.tar |
| Operation: | write | Name: | Set |
Value: 1 | |||
| (PID) Process: | (5236) Uninstall.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Setup\.gz |
| Operation: | write | Name: | Set |
Value: 1 | |||
Executable files
23
Suspicious files
1
Text files
14
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\newadvsplash.dll | executable | |
MD5:55A723E125AFBC9B3A41D46F41749068 | SHA256:0A70CC4B93D87ECD93E538CFBED7C9A4B8B5C6F1042C6069757BDA0D1279ED06 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\~DF101AA33C03AA1BA7.TMP | binary | |
MD5:C9BBEB9154EF92ABC9EBCCC4F5A2A954 | SHA256:8EF728BA97A3C5A9A141DC6EB24B4DAFFAFE1C143B0ECE564934DDA33FC89D47 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\LangDLL.dll | executable | |
MD5:A1CD3F159EF78D9ACE162F067B544FD9 | SHA256:47B9E251C9C90F43E3524965AECC07BD53C8E09C5B9F9862B44C306667E2B0B6 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\Aero.dll | executable | |
MD5:869C5949A10B32D3A31966CC5291301B | SHA256:B19961DE6CA07E08704D6372718542F70DBBB203E59BF9BBE3A58F6E069A625C | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\en.bmp | image | |
MD5:ED25F74135602D4F678F47C8A90B3927 | SHA256:572AFBBE22CE62759BC3B1D1E40BFD6F3914994F1EBAF4C93EF9D0ACA93CC6C4 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\nsProcess.dll | executable | |
MD5:F0438A894F3A7E01A4AAE8D1B5DD0289 | SHA256:30C6C3DD3CC7FCEA6E6081CE821ADC7B2888542DAE30BF00E881C0A105EB4D11 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\HiRu.exe | executable | |
MD5:FFB98EA49F8D3B558D856CBCB1CE6DDD | SHA256:C6A27F58808D169482545CB61B891782E33176EA32FA286EDCDA4D9C1448C0DD | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\ua.bmp | image | |
MD5:F7086FF90228A948D8409EAE0ADB2FB6 | SHA256:F28654F1B4089E01FC336D8813B4A8C07F1D85088E6FD134EB382F295BD81755 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\ru.bmp | image | |
MD5:ACBA4CB0FEE2EA0560DCE560D8BB1D00 | SHA256:A134FDAFE45A29C94295C6164C118B0166870807BFAFA94DB211BF61802EE432 | |||
| 2096 | _58b405d695afd36cc8e2666d65444abcfb10b921ed5541520420ab83d1f8da96.exe | C:\Users\admin\AppData\Local\Temp\nsuD83C.tmp\nsDialogs.dll | executable | |
MD5:4CCC4A742D4423F2F0ED744FD9C81F63 | SHA256:416133DD86C0DFF6B0FCAF1F46DFE97FDC85B37F90EFFB2D369164A8F7E13AE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4160 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4160 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4160 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4160 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4160 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |