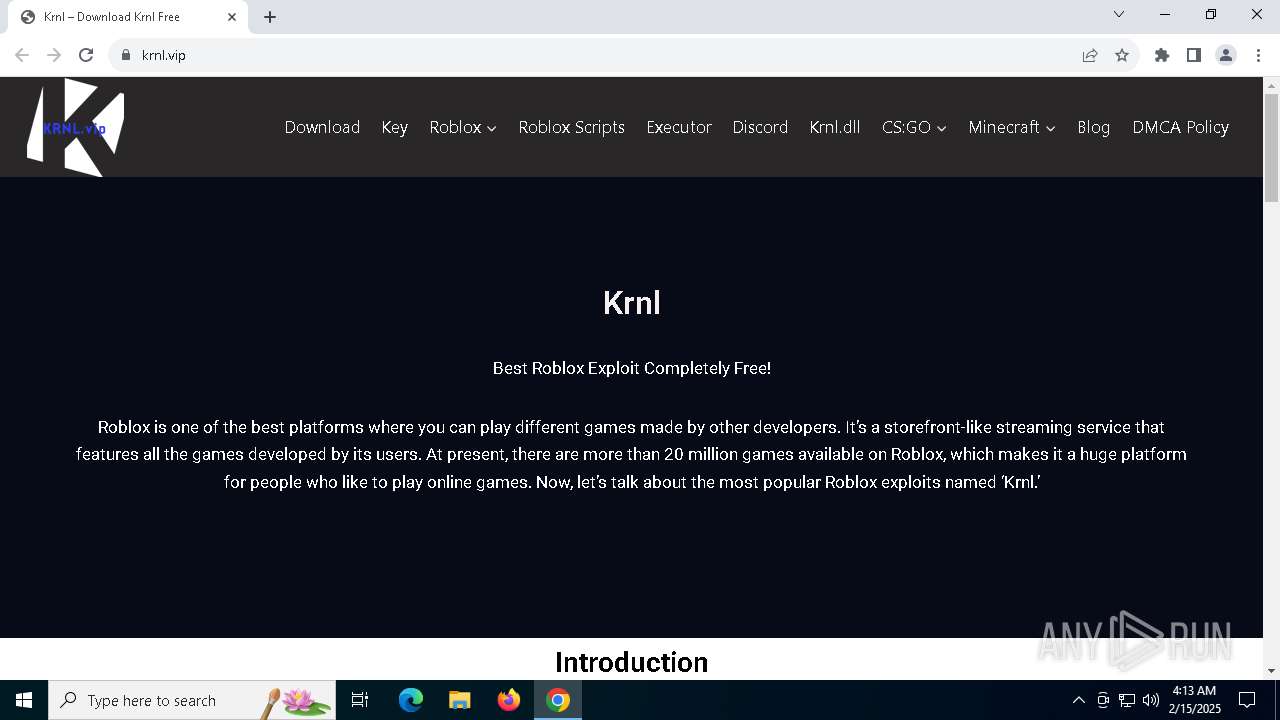
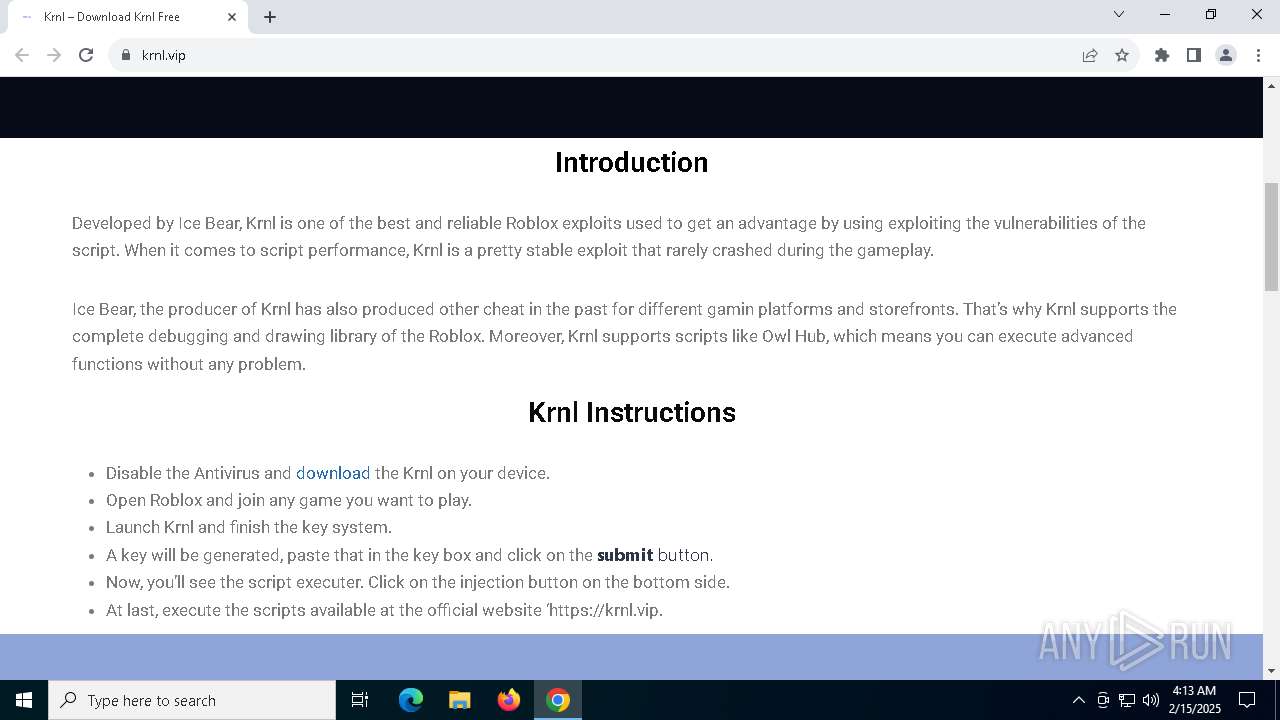
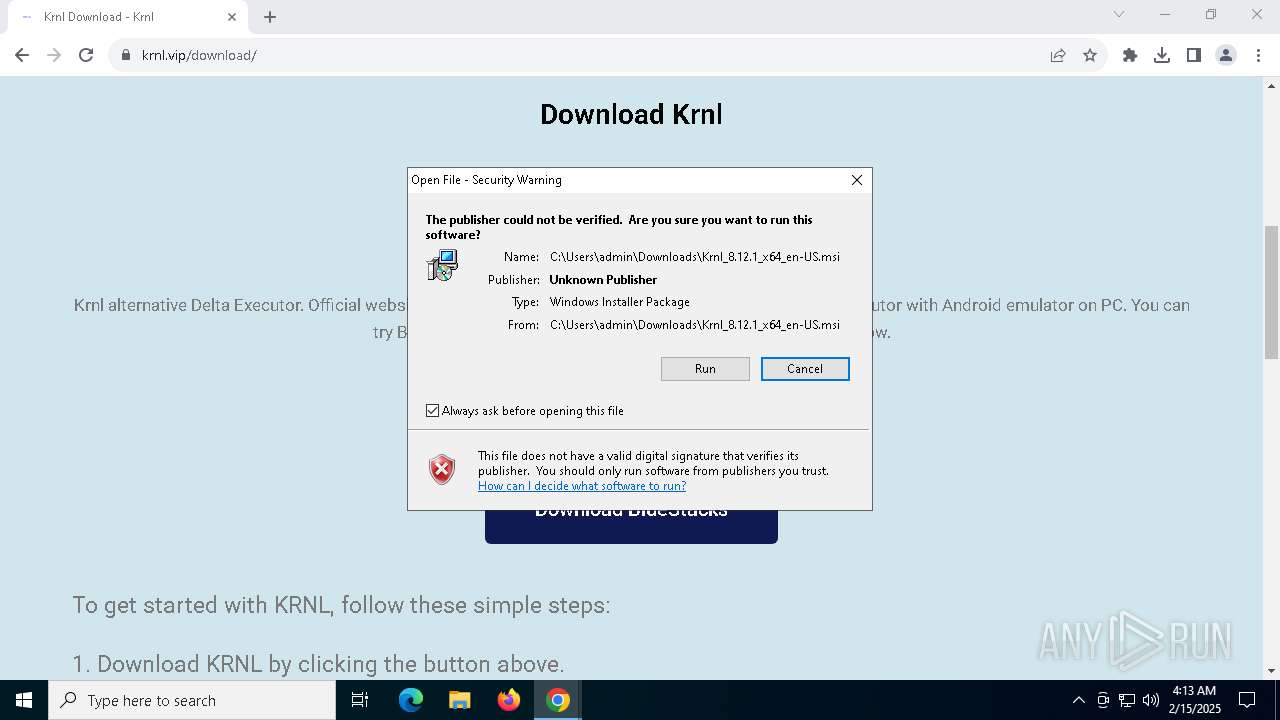
| URL: | https://krnl.vip/ |
| Full analysis: | https://app.any.run/tasks/c2799620-c373-4140-aa6f-acc08eff444e |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2025, 04:13:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | EEF9303CC63CAFF14A1A8CA2730D013B |
| SHA1: | 94DDEC8B83DD9A472401C6B3F6AE802D1A77990B |
| SHA256: | 58931F25D2CC31124813B91D1F6F094CCAD6522E478FE62C6B3A44FD0AC4C495 |
| SSDEEP: | 3:N8S9T:2S9T |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4320)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 7040)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 396)
Manipulates environment variables
- powershell.exe (PID: 4320)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 2160)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 2160)
Starts process via Powershell
- powershell.exe (PID: 4320)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2160)
Downloads file from URI via Powershell
- powershell.exe (PID: 4320)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4320)
Executable content was dropped or overwritten
- powershell.exe (PID: 4320)
- MicrosoftEdgeUpdate.exe (PID: 7040)
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
Process drops legitimate windows executable
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
- MicrosoftEdgeUpdate.exe (PID: 7040)
- powershell.exe (PID: 4320)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 7040)
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdate.exe (PID: 7084)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1400)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3532)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1888)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7040)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 7040)
INFO
Reads the computer name
- msiexec.exe (PID: 2160)
- msiexec.exe (PID: 2076)
- MicrosoftEdgeUpdate.exe (PID: 7040)
- MicrosoftEdgeUpdate.exe (PID: 7084)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1400)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3532)
- MicrosoftEdgeUpdate.exe (PID: 5920)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1888)
- MicrosoftEdgeUpdate.exe (PID: 7044)
- MicrosoftEdgeUpdate.exe (PID: 7188)
Application launched itself
- chrome.exe (PID: 6256)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6256)
Checks supported languages
- msiexec.exe (PID: 2160)
- msiexec.exe (PID: 2076)
- MicrosoftEdgeUpdate.exe (PID: 7040)
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
- MicrosoftEdgeUpdate.exe (PID: 7084)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1888)
- MicrosoftEdgeUpdate.exe (PID: 5920)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1400)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3532)
- MicrosoftEdgeUpdate.exe (PID: 7044)
- MicrosoftEdgeUpdate.exe (PID: 7188)
Creates a software uninstall entry
- msiexec.exe (PID: 2160)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2160)
- msiexec.exe (PID: 7120)
Disables trace logs
- powershell.exe (PID: 4320)
Manages system restore points
- SrTasks.exe (PID: 5080)
Checks proxy server information
- powershell.exe (PID: 4320)
- MicrosoftEdgeUpdate.exe (PID: 7188)
- MicrosoftEdgeUpdate.exe (PID: 5920)
The sample compiled with english language support
- powershell.exe (PID: 4320)
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
- MicrosoftEdgeUpdate.exe (PID: 7040)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 4640)
- MicrosoftEdgeUpdate.exe (PID: 7040)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 7040)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 5920)
- MicrosoftEdgeUpdate.exe (PID: 7188)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 5920)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 7040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
162
Monitored processes
30
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1400 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4476 --field-trial-handle=1936,i,14932118017790097142,6655978348636342536,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4488 --field-trial-handle=1936,i,14932118017790097142,6655978348636342536,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1888 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 2076 | C:\Windows\syswow64\MsiExec.exe -Embedding D96C0BD78A60F7925F096839A81AA7C4 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
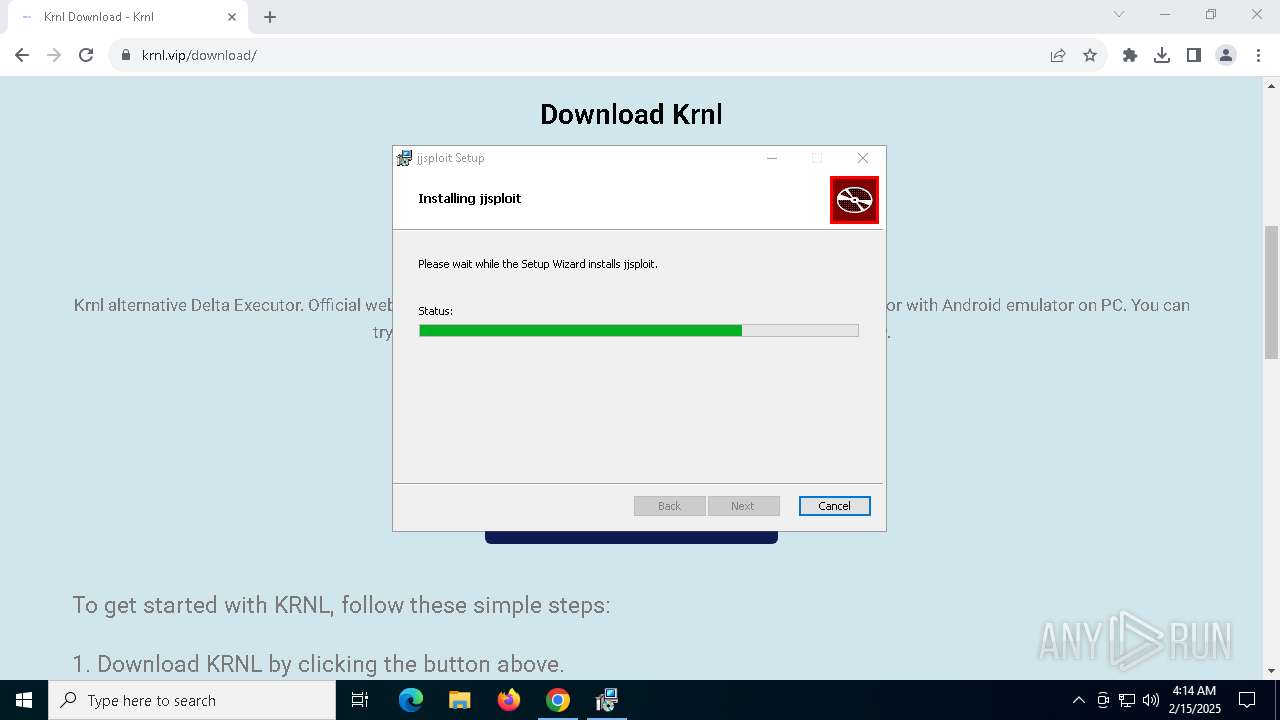
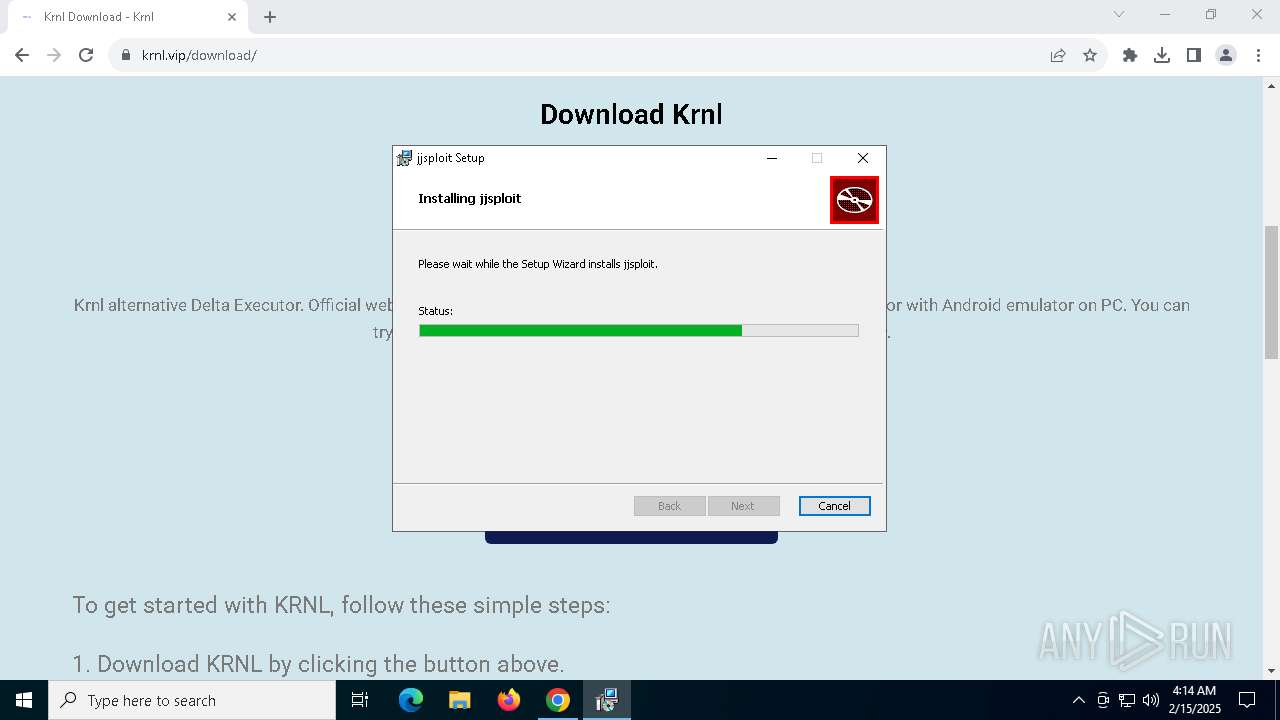
| 4320 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=5716 --field-trial-handle=1936,i,14932118017790097142,6655978348636342536,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
15 303
Read events
14 674
Write events
586
Delete events
43
Modification events
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1804) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000ED43F106607FDB01 | |||
| (PID) Process: | (6256) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (2160) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000B54580D607FDB0170080000D4150000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2160) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000004405580D607FDB0170080000D4150000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2160) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000370AA70D607FDB0170080000D4150000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
204
Suspicious files
57
Text files
38
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF134b06.TMP | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF134b06.TMP | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF134b16.TMP | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF134b16.TMP | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF134b25.TMP | — | |
MD5:— | SHA256:— | |||
| 6256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
65
DNS requests
64
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7004 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7276 | svchost.exe | GET | — | 217.20.57.35:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/af8e5f2c-8b7f-478f-8f6c-f1dc567e0d65?P1=1740197672&P2=404&P3=2&P4=N0J6rT%2fWMMdJMEYVOhZ74Xos5%2fE2kzDSBmZiYq%2fHrN2etXGvbvmSEeOIQHtVRdvg5KC4L3zLjOxawcYlSL8mdQ%3d%3d | unknown | — | — | whitelisted |
7276 | svchost.exe | HEAD | 200 | 217.20.57.35:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/af8e5f2c-8b7f-478f-8f6c-f1dc567e0d65?P1=1740197672&P2=404&P3=2&P4=N0J6rT%2fWMMdJMEYVOhZ74Xos5%2fE2kzDSBmZiYq%2fHrN2etXGvbvmSEeOIQHtVRdvg5KC4L3zLjOxawcYlSL8mdQ%3d%3d | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2132 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
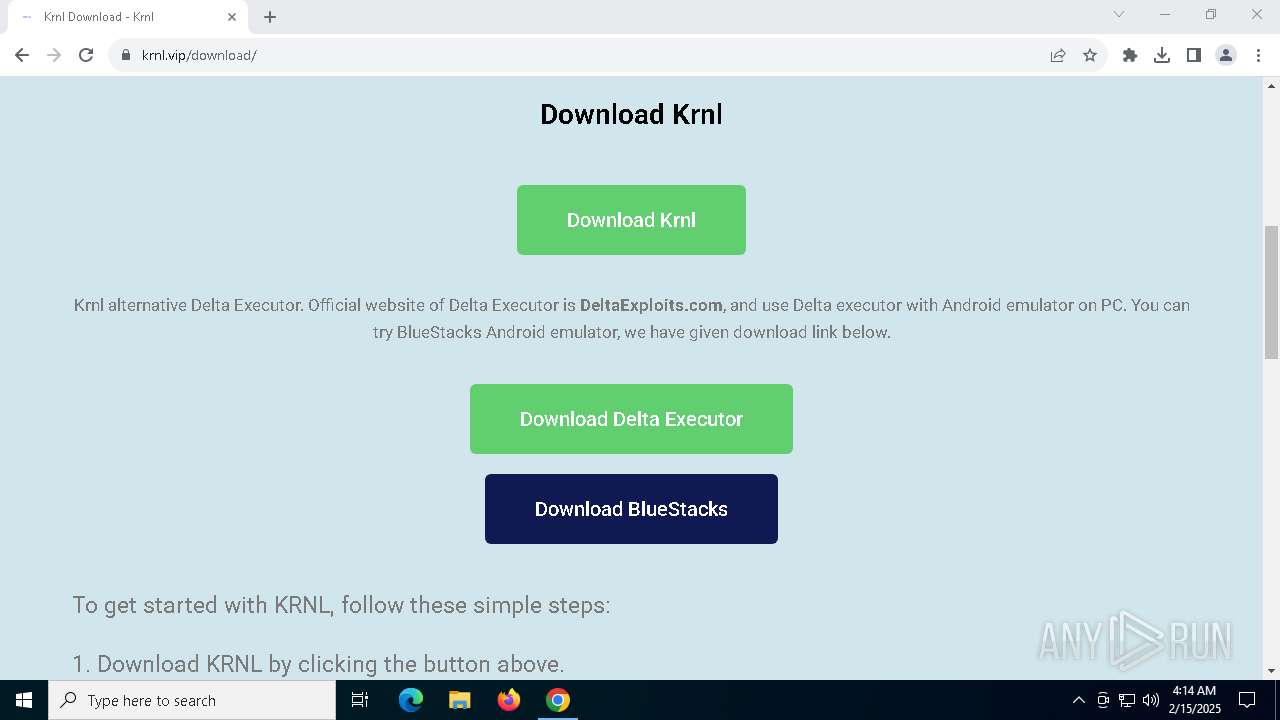
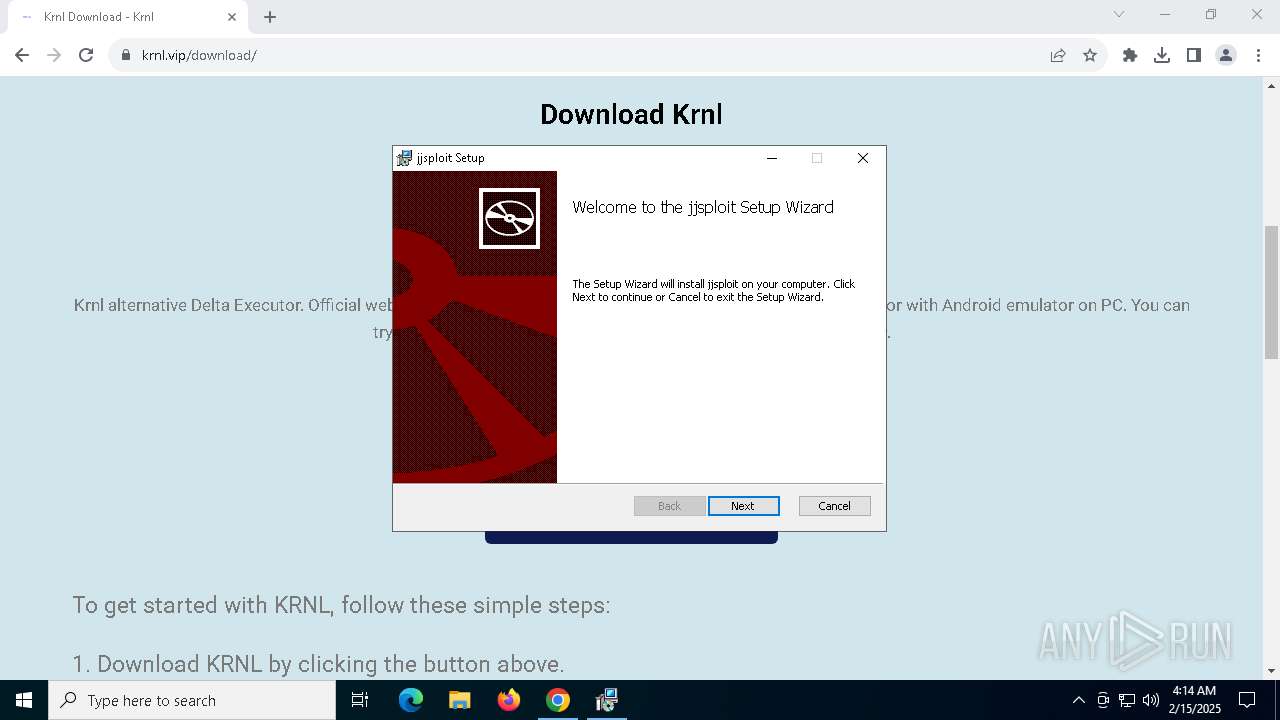
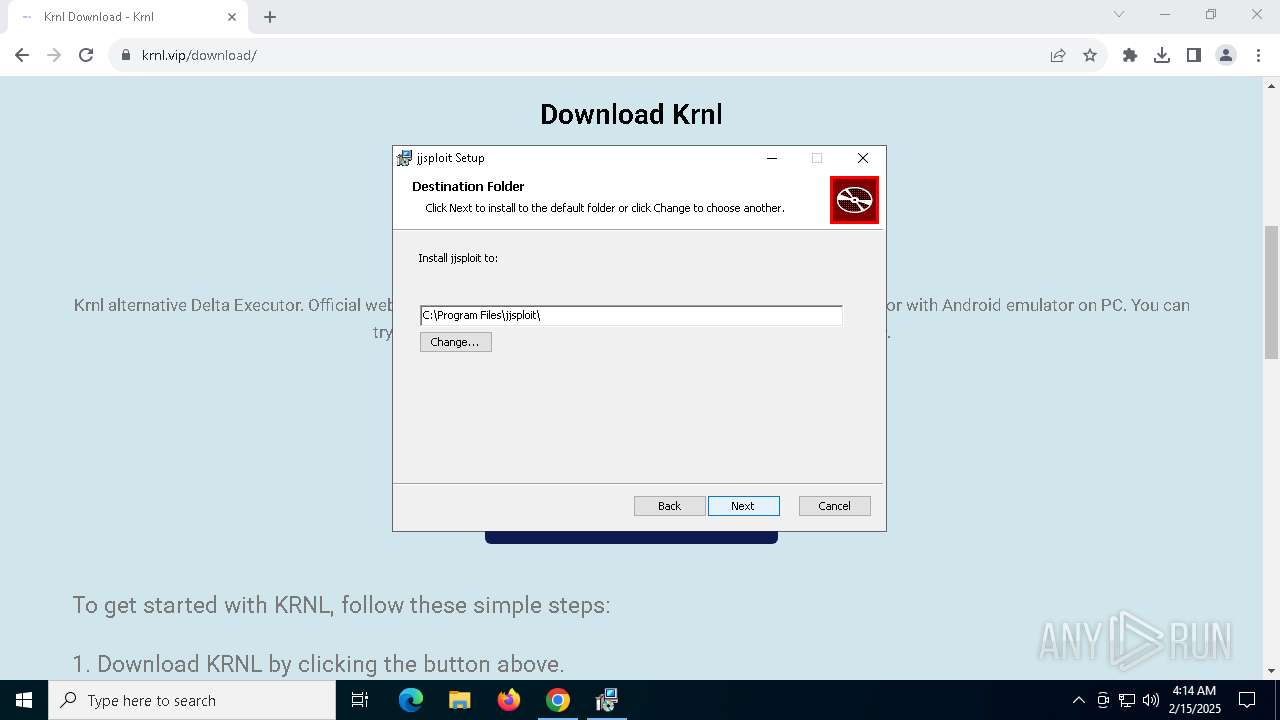
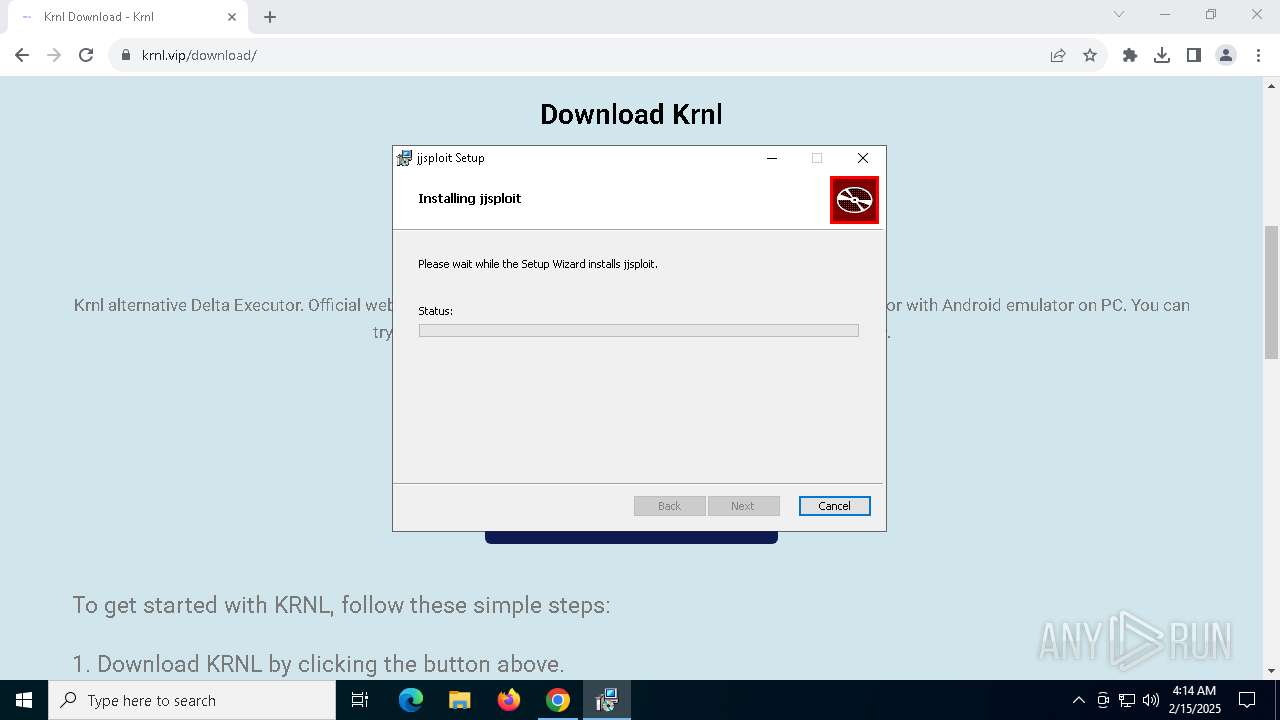
6552 | chrome.exe | 104.21.46.75:443 | krnl.vip | CLOUDFLARENET | — | suspicious |
6256 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6552 | chrome.exe | 142.250.145.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6552 | chrome.exe | 142.250.185.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
6552 | chrome.exe | 142.250.185.195:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
6552 | chrome.exe | 142.250.185.226:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
krnl.vip |
| unknown |
accounts.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7276 | svchost.exe | Misc activity | ET INFO Packed Executable Download |