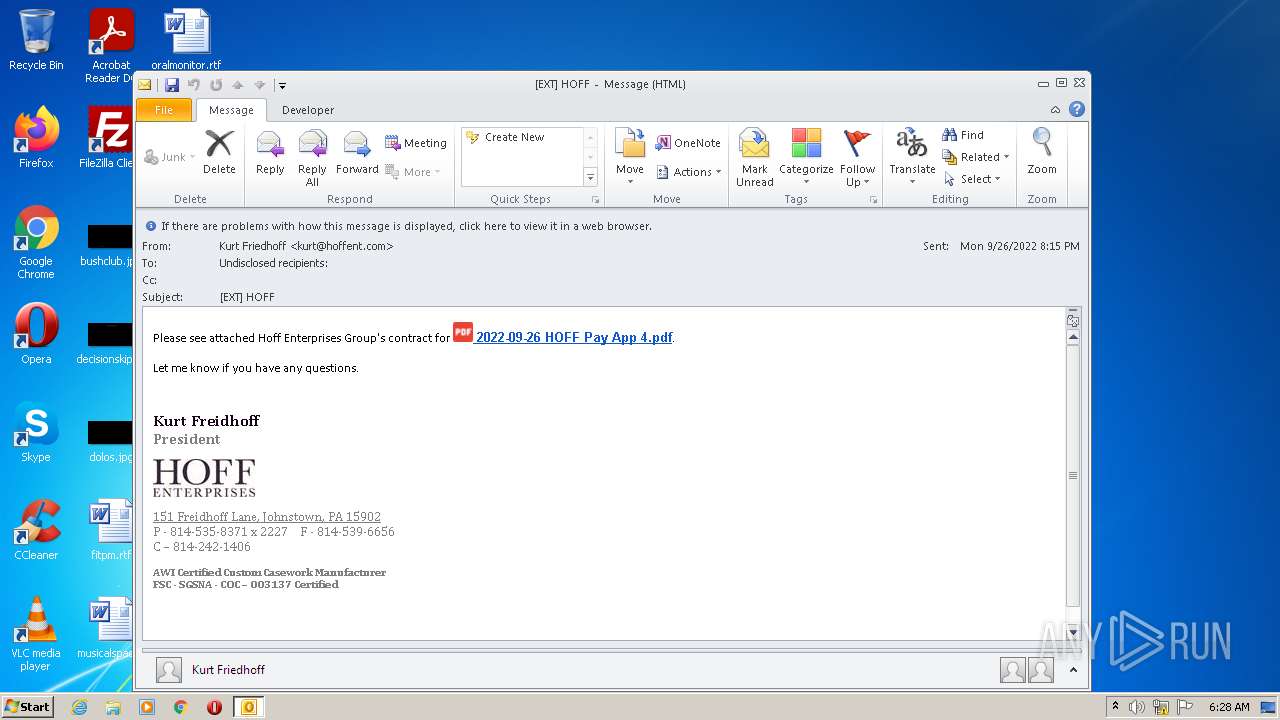
| File name: | raw.eml |
| Full analysis: | https://app.any.run/tasks/550d05ba-4722-4dc8-b7bc-ba59c453d0ee |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 05:28:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | B5698B3AD272AC233DD40076B85F7BA4 |
| SHA1: | 95E345ECA43926EB26B7DE04B5188B2660010DC8 |
| SHA256: | 58892500A1D6E7058F4565698C764655C5CBCA4E142AE2BF5AB7D8C83E89B1F9 |
| SSDEEP: | 384:T71oqjZvztRFGRMMynZnp/6YzaFEcR0CP+bQtDURKjaGqaPX6l6a0Iel3BUofgrx:T71oynZn1zkR0AHARw0z+hl3G0/TWqA5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
41
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1872 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2588 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
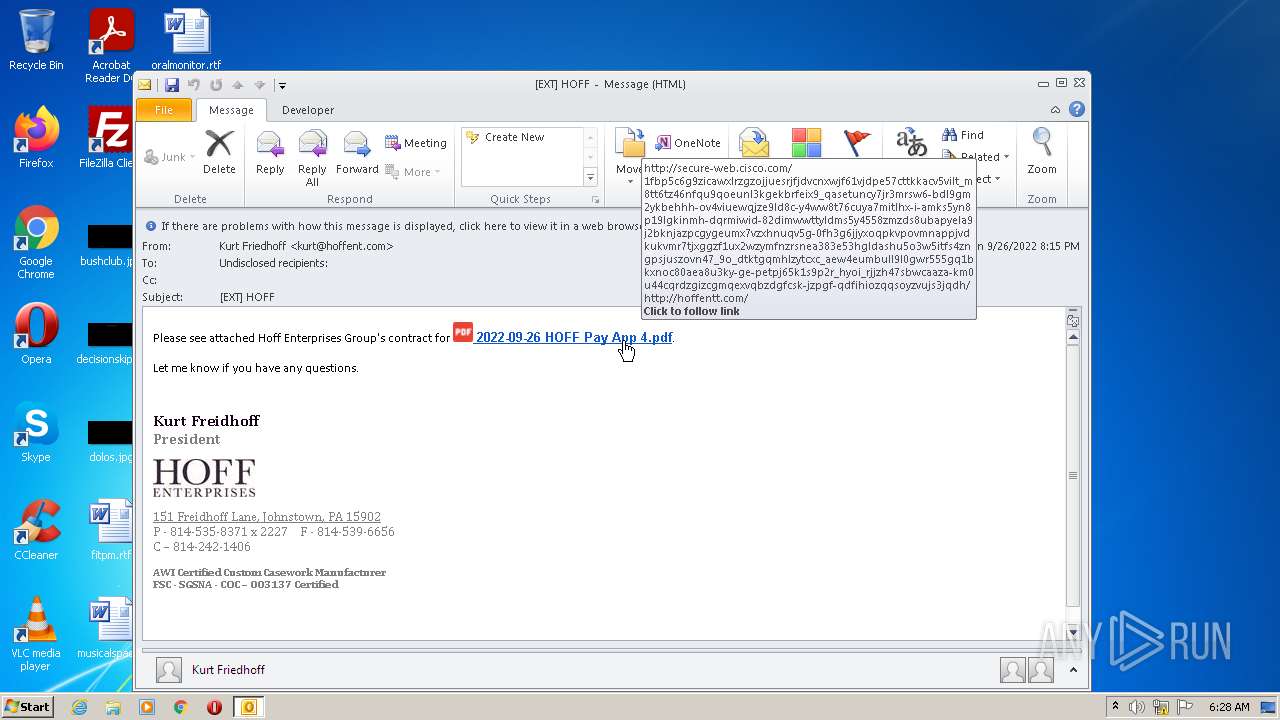
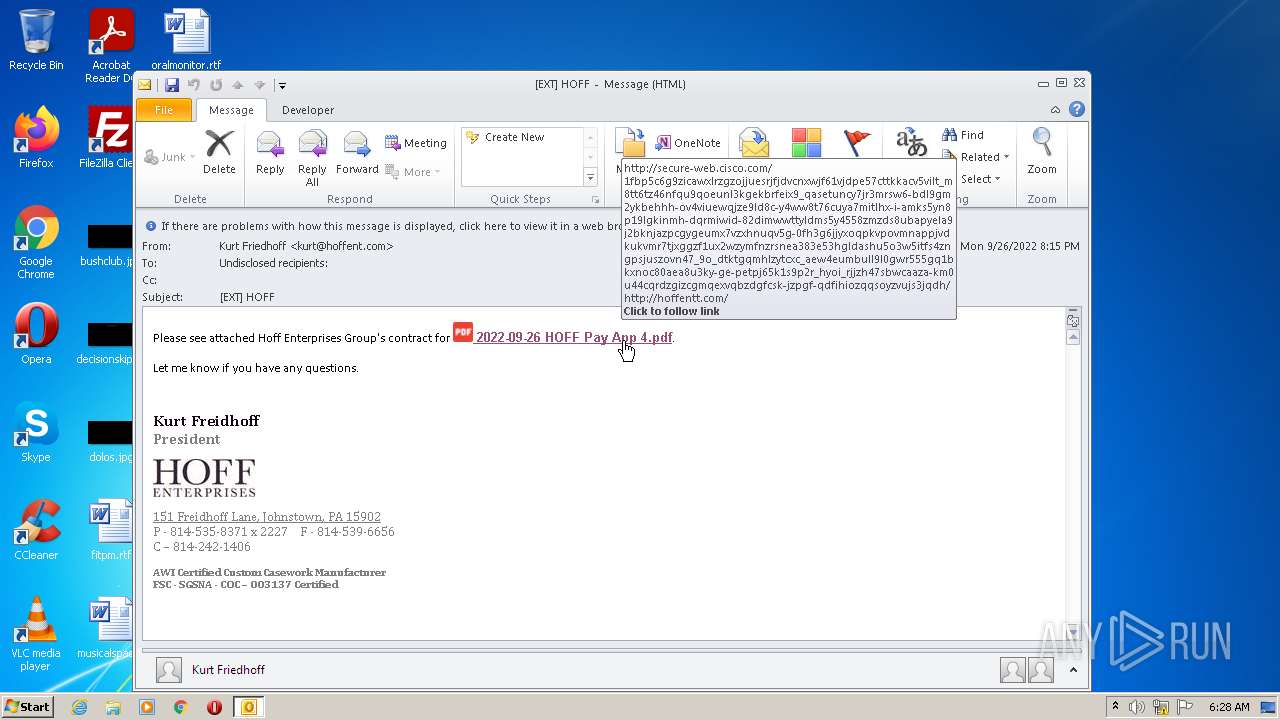
| 2588 | "C:\Program Files\Internet Explorer\iexplore.exe" http://secure-web.cisco.com/1fBP5C6g9ZIcAwXLRzgzOjJuESRjFjDvcNxwJf61VJdPe57cttKKaCV5VIlT_m8tT6Tz46NfQU9qoEunl3KGeKBrfeIx9_qASETUncy7jR3mrsW6-BDL9GM2YKbeHhH-Ov4ViuEwQjZE9LD8c-y4ww8t76cuya7MiTLHX-I-aMKs5yn8P19lgKinmh-dQRMIwid-82DiMwwTtyLDMS5y4558ZMZdS8Ubapyela9j2bKnjazPcgyGeUmX7VZxHnuQv5g-0FH3G6jjyxoQpKvpoVmNAppJVDKuKvmr7tJXgGZF1Ux2wZyMFNZrSNEa383e53hGLdaSHU5o3W5ITfS4zNGpsjusZOVN47_9o_DTkTGQmhLzyTcXC_aew4euMbUlL9l0gWR555gq1BkxnOc80AeA8u3ky-ge-peTPj65K1s9p2r_HYoi_RJJZh47SbWcaAza-km0U44CQrdZgIzcgmqeXVqbzdgFCSK-jzpgF-qDFIHiOZQQSOYzVUjS3jqDH/http%3A%2F%2Fhoffentt.com%2F | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3536 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\raw.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
45 760
Read events
45 010
Write events
726
Delete events
24
Modification events
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
20
Text files
79
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRBEDD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CE690500.dat | image | |
MD5:— | SHA256:— | |||
| 2588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 2588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ConversationPrefs_2_732439E16705714E8E77598960B26D84.dat | xml | |
MD5:57F30B1BCA811C2FCB81F4C13F6A927B | SHA256:612BAD93621991CB09C347FF01EC600B46617247D5C041311FF459E247D8C2D3 | |||
| 3536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{3502FCC4-6DC6-4629-9733-0A750C55551A}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
73
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3536 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
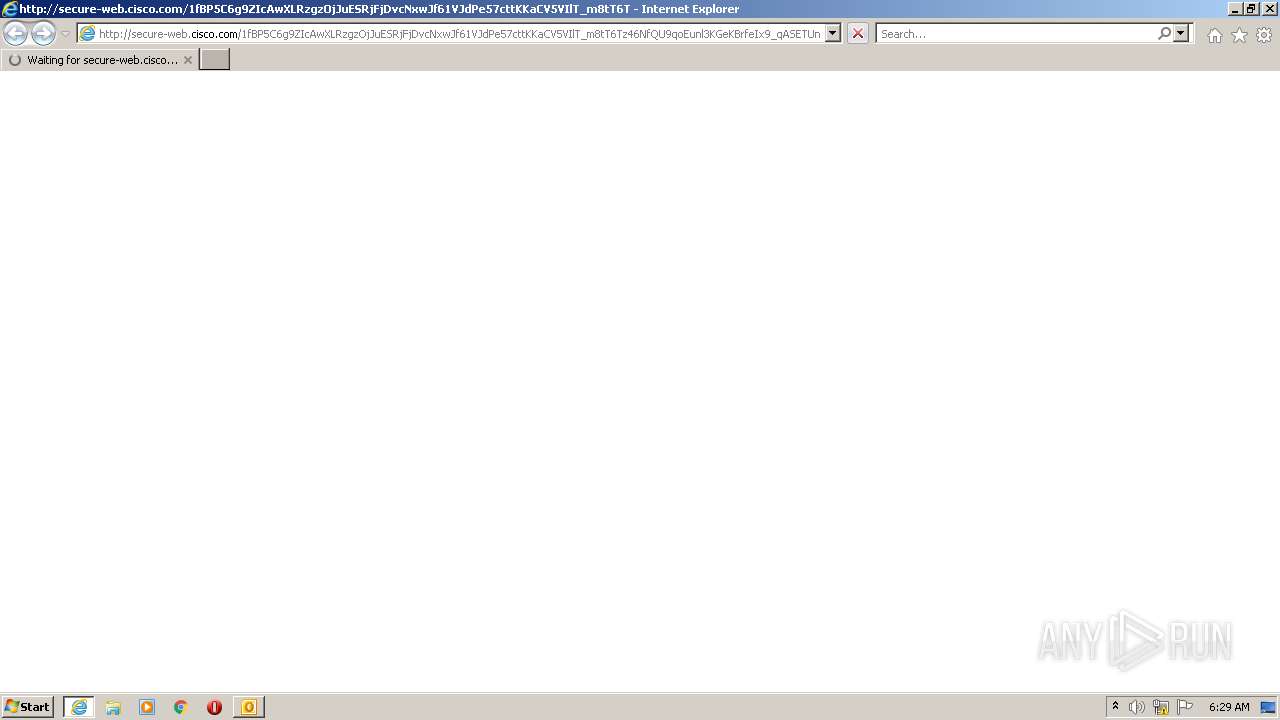
1872 | iexplore.exe | GET | 302 | 146.112.255.69:80 | http://secure-web.cisco.com/1fBP5C6g9ZIcAwXLRzgzOjJuESRjFjDvcNxwJf61VJdPe57cttKKaCV5VIlT_m8tT6Tz46NfQU9qoEunl3KGeKBrfeIx9_qASETUncy7jR3mrsW6-BDL9GM2YKbeHhH-Ov4ViuEwQjZE9LD8c-y4ww8t76cuya7MiTLHX-I-aMKs5yn8P19lgKinmh-dQRMIwid-82DiMwwTtyLDMS5y4558ZMZdS8Ubapyela9j2bKnjazPcgyGeUmX7VZxHnuQv5g-0FH3G6jjyxoQpKvpoVmNAppJVDKuKvmr7tJXgGZF1Ux2wZyMFNZrSNEa383e53hGLdaSHU5o3W5ITfS4zNGpsjusZOVN47_9o_DTkTGQmhLzyTcXC_aew4euMbUlL9l0gWR555gq1BkxnOc80AeA8u3ky-ge-peTPj65K1s9p2r_HYoi_RJJZh47SbWcaAza-km0U44CQrdZgIzcgmqeXVqbzdgFCSK-jzpgF-qDFIHiOZQQSOYzVUjS3jqDH/http%3A%2F%2Fhoffentt.com%2F | unknown | — | — | whitelisted |
1872 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
1872 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDs1Hdi6lxqqEmmfu2QOiiI%3D | US | der | 471 b | whitelisted |
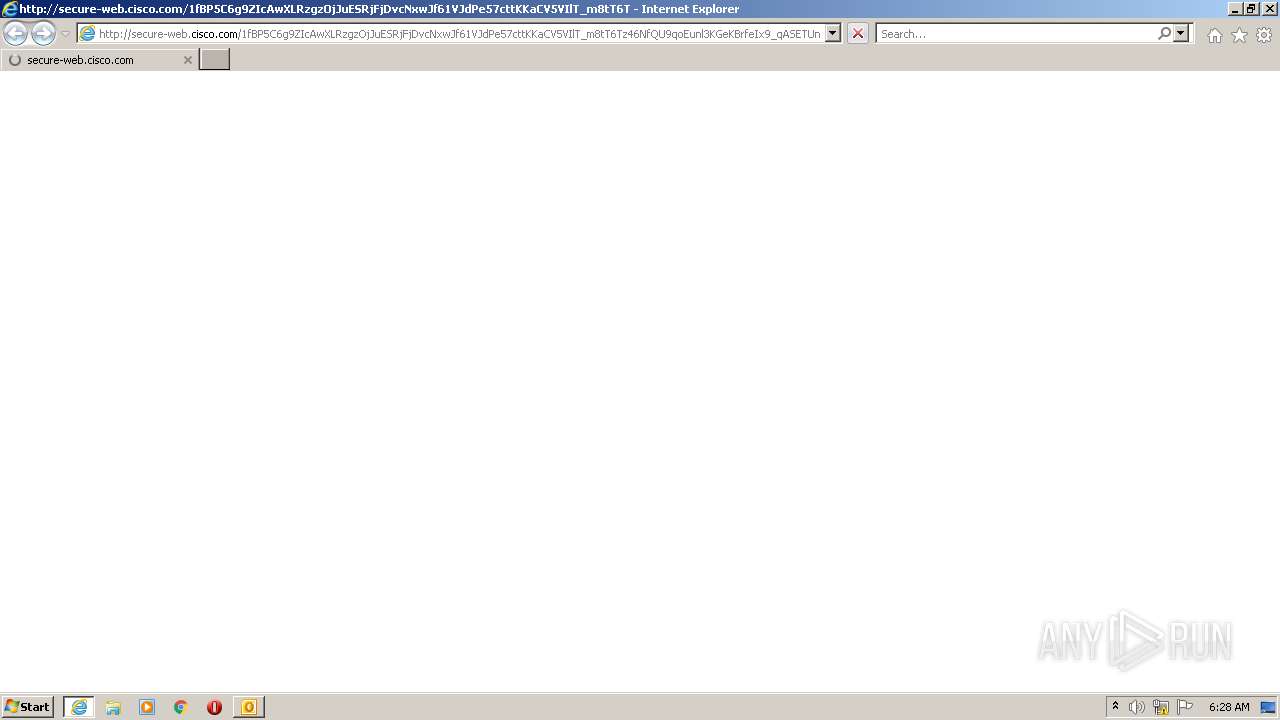
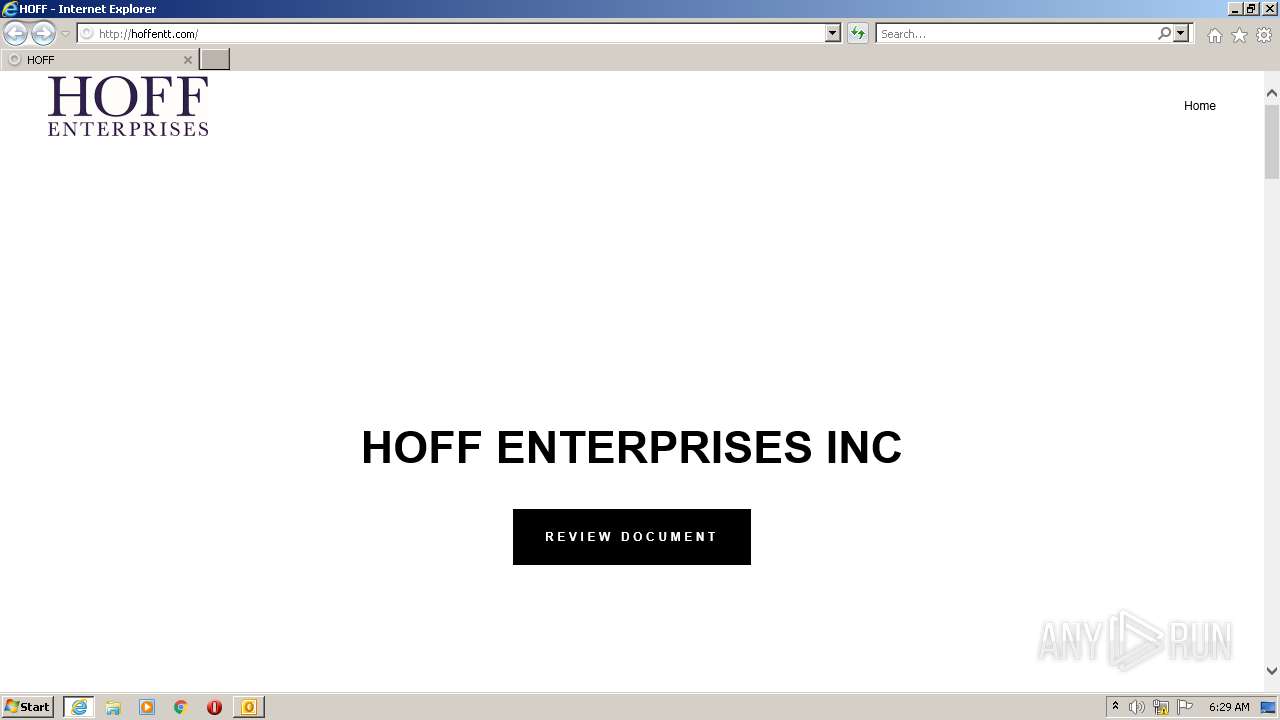
1872 | iexplore.exe | GET | 200 | 34.96.116.138:80 | http://hoffentt.com/ | US | html | 22.5 Kb | suspicious |
1872 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
1872 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
1872 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECY%2B0YL3%2ByMOCtPdrqPffYg%3D | US | der | 471 b | whitelisted |
2588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
1872 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3536 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 146.112.255.69:80 | secure-web.cisco.com | OPENDNS | US | suspicious |
1872 | iexplore.exe | 34.96.116.138:80 | hoffentt.com | GOOGLE | US | malicious |
— | — | 192.168.100.2:53 | — | — | — | whitelisted |
2588 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
1872 | iexplore.exe | 146.112.255.69:80 | secure-web.cisco.com | OPENDNS | US | suspicious |
1872 | iexplore.exe | 142.250.186.142:443 | www.youtube.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.142:443 | www.youtube.com | GOOGLE | US | whitelisted |
1872 | iexplore.exe | 172.217.18.20:443 | imos006-dot-im--os.appspot.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.20:443 | imos006-dot-im--os.appspot.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
config.messenger.msn.com |
| whitelisted |
secure-web.cisco.com |
| whitelisted |
hoffentt.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.youtube.com |
| whitelisted |
imos006-dot-im--os.appspot.com |
| suspicious |