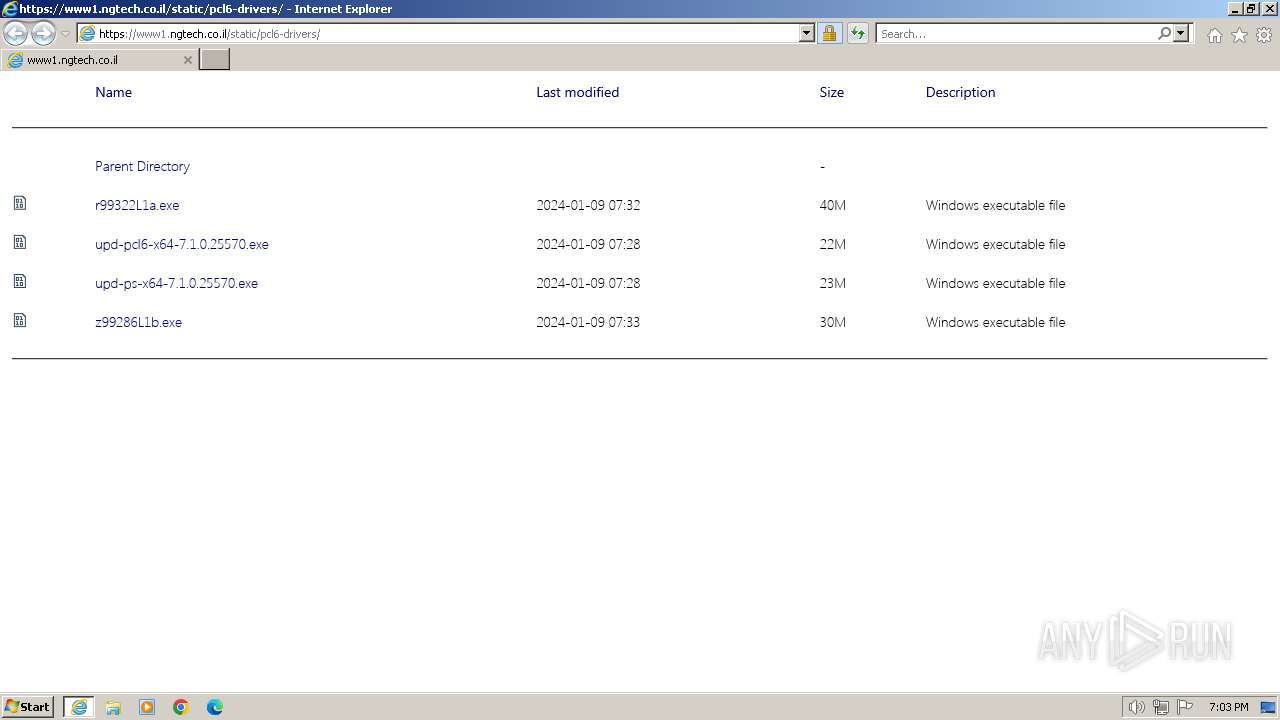
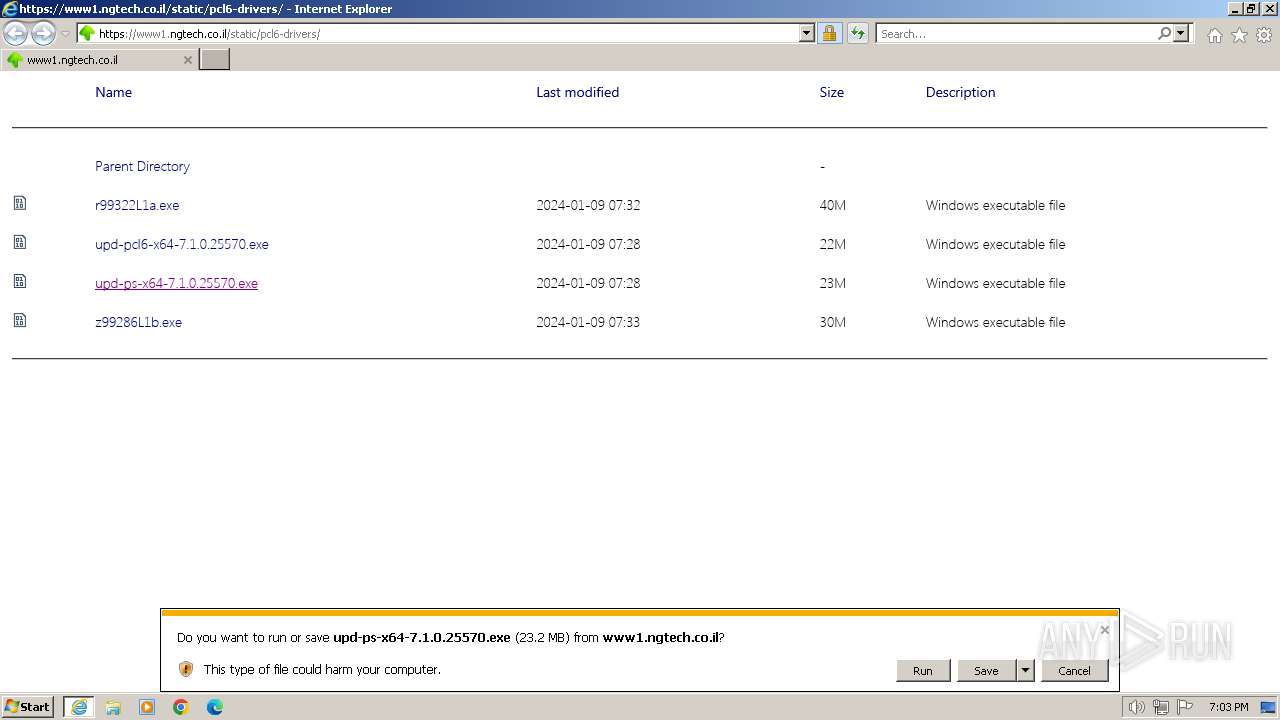
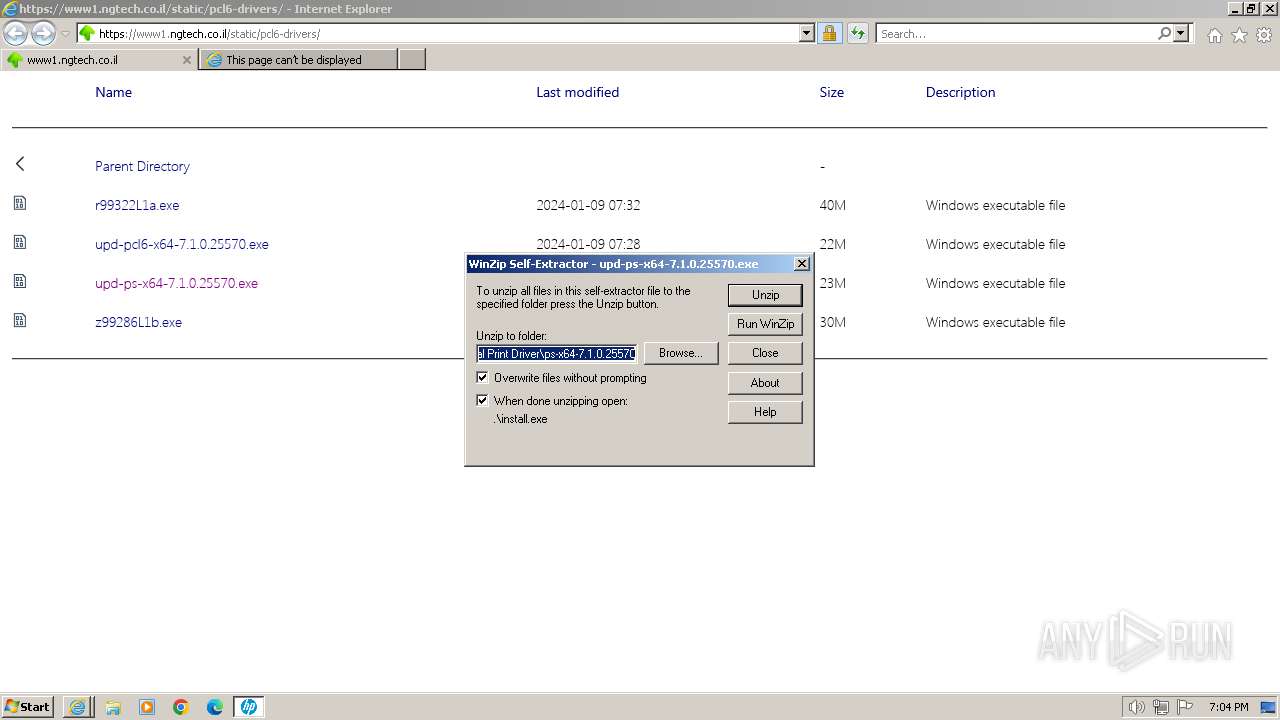
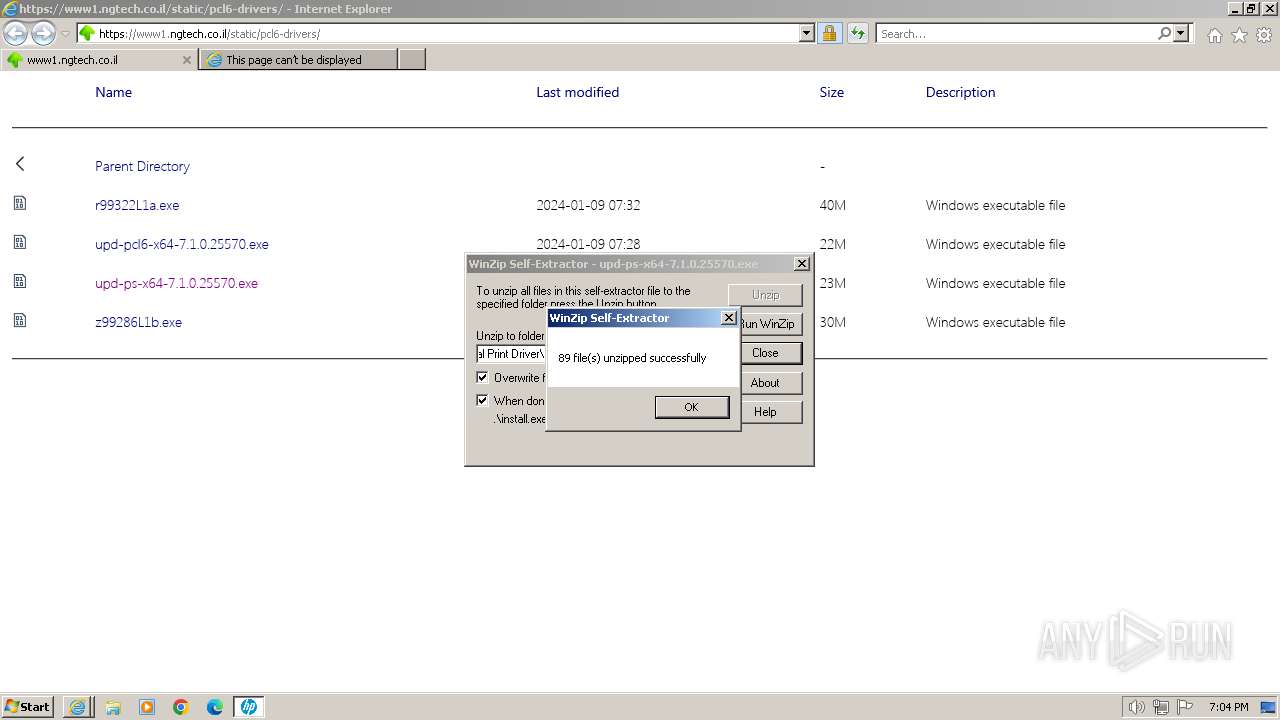
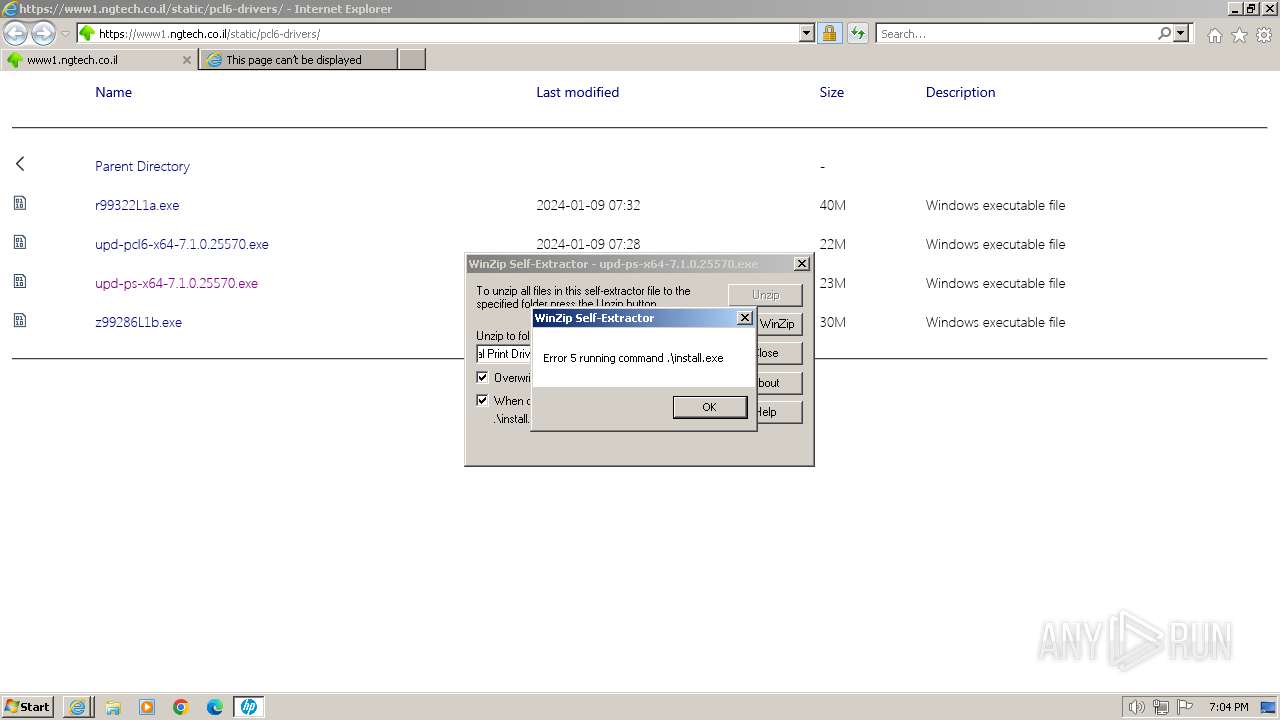
| URL: | https://www1.ngtech.co.il/static/pcl6-drivers/ |
| Full analysis: | https://app.any.run/tasks/a6b3a63b-0898-4456-8ab2-cf94b2d6e21d |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2024, 19:03:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 470B49004E403FB7746921DC3475E09D |
| SHA1: | 84EB9A14433A9D67841368F10B5D009357BDEAC7 |
| SHA256: | 58794E309845EBEC8201391782175F2186509666E11064570D68C5BB298FE22F |
| SSDEEP: | 3:N8DSUL2mjQINiRHKBJ:2OS2F+J |
MALICIOUS
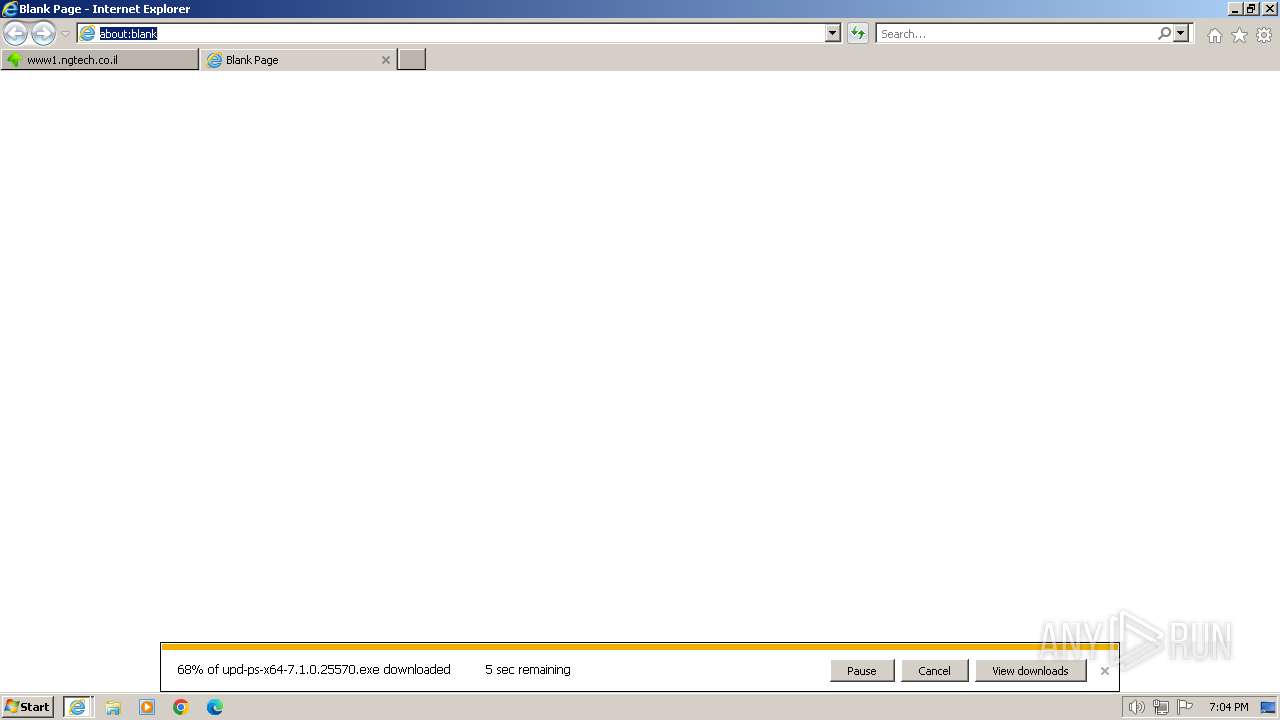
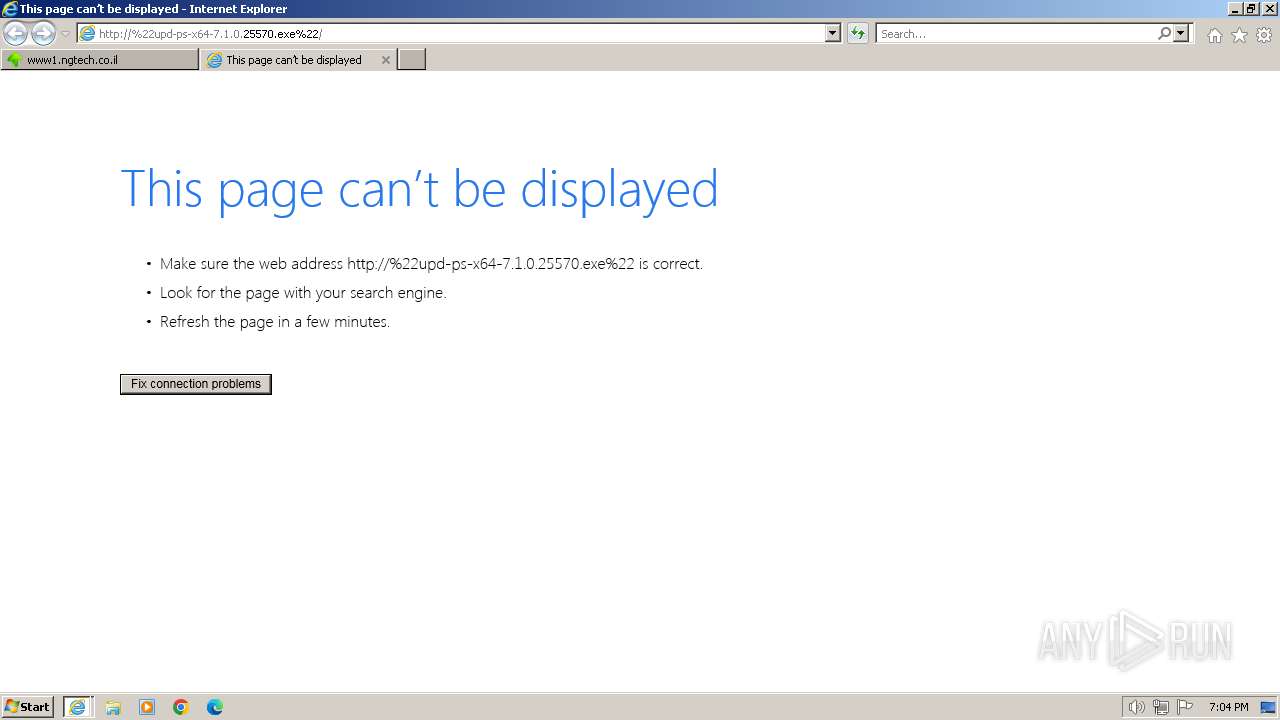
Drops the executable file immediately after the start
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
SUSPICIOUS
Executable content was dropped or overwritten
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Starts itself from another location
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
Process drops legitimate windows executable
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Drops a system driver (possible attempt to evade defenses)
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Reads the Internet Settings
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Reads security settings of Internet Explorer
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 4008)
Application launched itself
- iexplore.exe (PID: 4008)
- chrome.exe (PID: 1608)
Checks supported languages
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4008)
- iexplore.exe (PID: 3276)
The process uses the downloaded file
- iexplore.exe (PID: 4008)
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
Create files in a temporary directory
- upd-ps-x64-7.1.0.25570.exe (PID: 2112)
Modifies the phishing filter of IE
- iexplore.exe (PID: 4008)
Reads the computer name
- upd-ps-x64-7.1.0.25570.exe (PID: 2972)
Manual execution by a user
- chrome.exe (PID: 1608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
21
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6ba78b38,0x6ba78b48,0x6ba78b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1608 --field-trial-handle=1156,i,9497576620975444540,5074310062929715231,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1172 --field-trial-handle=1156,i,9497576620975444540,5074310062929715231,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1400 --field-trial-handle=1156,i,9497576620975444540,5074310062929715231,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1276 --field-trial-handle=1156,i,9497576620975444540,5074310062929715231,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2172 --field-trial-handle=1156,i,9497576620975444540,5074310062929715231,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2112 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\upd-ps-x64-7.1.0.25570.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\upd-ps-x64-7.1.0.25570.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2724 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4008 CREDAT:2954527 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2972 | run=1 shortcut="C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\upd-ps-x64-7.1.0.25570.exe" | C:\Users\admin\AppData\Local\Temp\18b4c4\upd-ps-x64-7.1.0.25570.exe | upd-ps-x64-7.1.0.25570.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
35 768
Read events
35 353
Write events
242
Delete events
173
Modification events
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095746 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095746 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
27
Suspicious files
97
Text files
118
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\script[1].js | text | |
MD5:F9D41214D71D9CA0BDEAD5B96DEE5FD2 | SHA256:91643D2A47E5E8F97D006B7A34CFA4D82C0C53AAB9315C956B4AAB2BB4CA3AE6 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B691D5975D3E492C48464E3B69EB1EBD | SHA256:38FA2D9BA3D88DCDB53353F95FDC7DB5C16FBA8677375801DBE351FDAA183DDB | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:91A28393752EAC2C168C764C56240F02 | SHA256:CCABD925FA8480CC61033681C04446169C86426D6C7E65E19760F73A6A12E702 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\file-binary[1].svg | image | |
MD5:E10C55466F77BCD68E2A769A9AE12F10 | SHA256:5D487012561F88B453B1D8435777EA1C01C7D0FC706A40C4D43886B7D145774C | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:E80E545009AB7C6A05A6B9C04E4E796C | SHA256:DC4DDF0640E486C155A81DB397A7B89AB3B5394FC6A3066FF95CCDFA5180D3EC | |||
| 4008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:F13CB7D31A265E3980BC20DA44838F1E | SHA256:541231DD978FC8F9C50F91468E1DB4E2AF9DAF5A49191C08B042A6C07051C656 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
78
DNS requests
53
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | iexplore.exe | GET | 304 | 184.24.77.181:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b150b552b216e1f4 | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 304 | 184.24.77.208:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
4008 | iexplore.exe | GET | 304 | 184.24.77.208:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4ad9b1827f1f75f1 | unknown | — | — | unknown |
4008 | iexplore.exe | GET | 304 | 184.24.77.208:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b23edf5cfbe16fd7 | unknown | — | — | unknown |
4008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
4008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
3276 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.186:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e2ddf83a2417bb20 | unknown | compressed | 67.5 Kb | unknown |
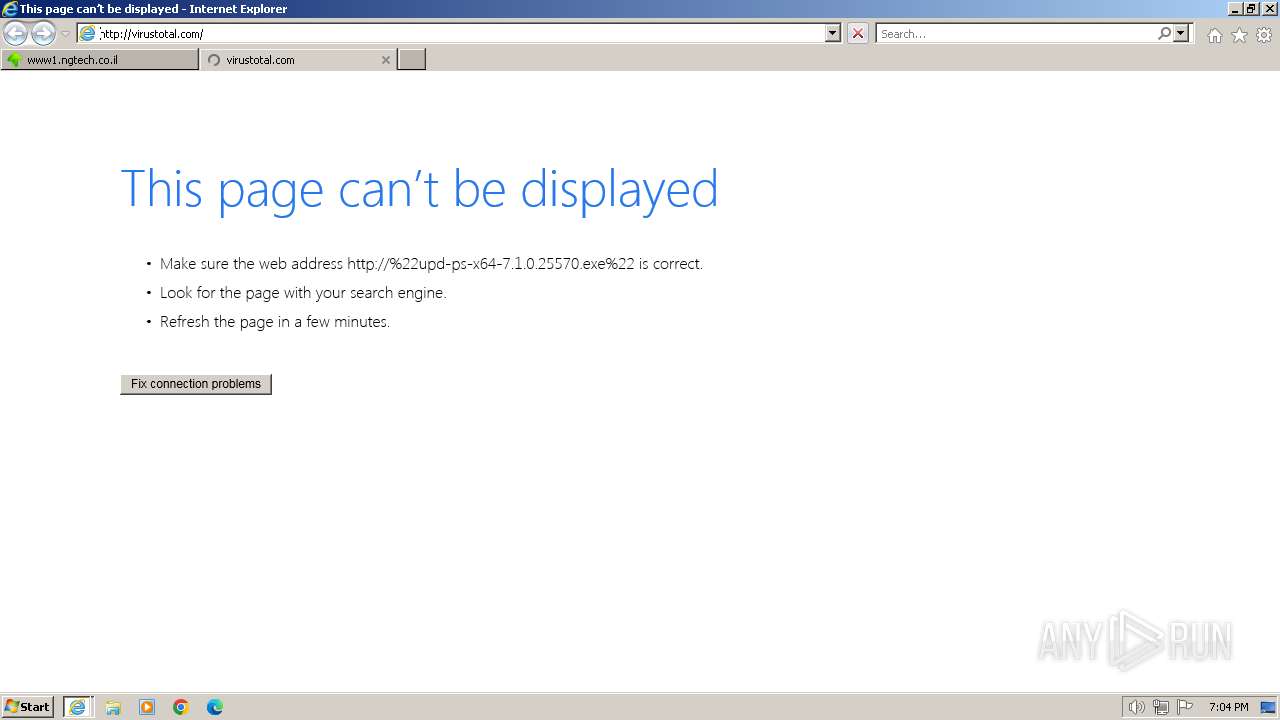
2724 | iexplore.exe | GET | 302 | 216.239.38.21:80 | http://virustotal.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3276 | iexplore.exe | 147.236.213.122:443 | www1.ngtech.co.il | Internet Rimon LTD | IL | unknown |
3276 | iexplore.exe | 184.24.77.181:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3276 | iexplore.exe | 184.24.77.208:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3276 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4008 | iexplore.exe | 147.236.213.122:443 | www1.ngtech.co.il | Internet Rimon LTD | IL | unknown |
4008 | iexplore.exe | 184.24.77.208:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www1.ngtech.co.il |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
virustotal.com |
| whitelisted |
www.virustotal.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report