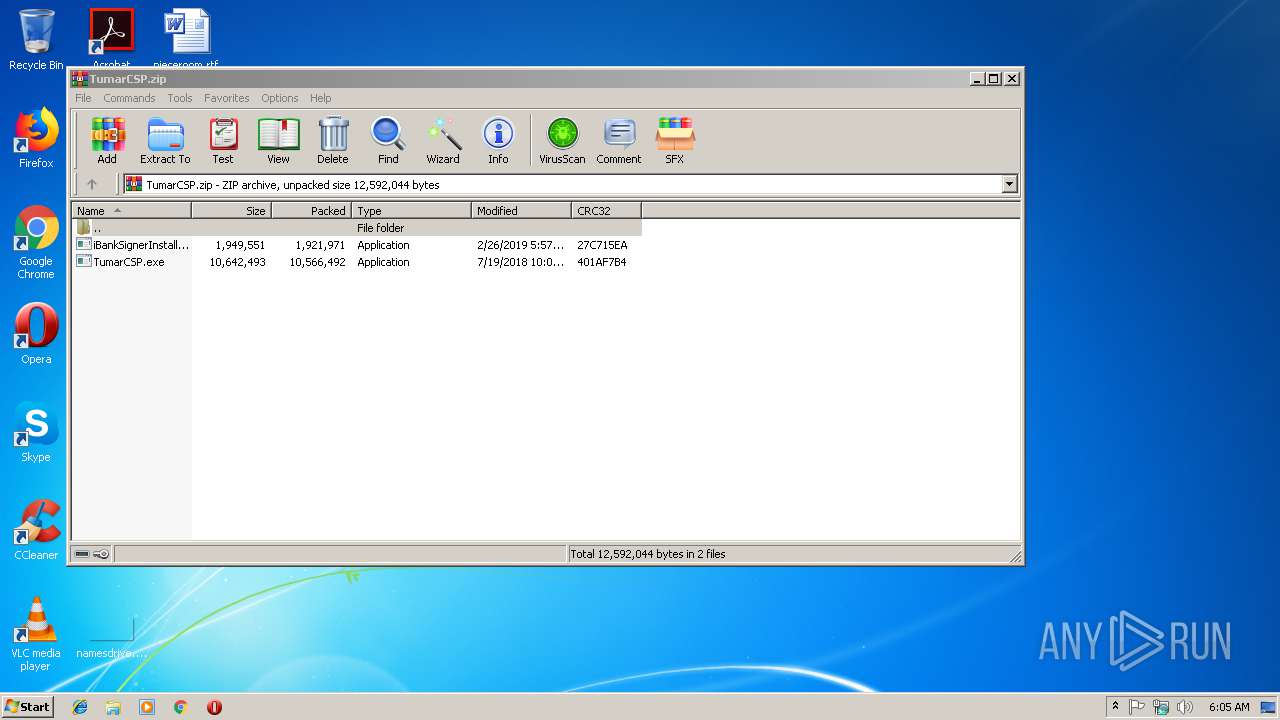
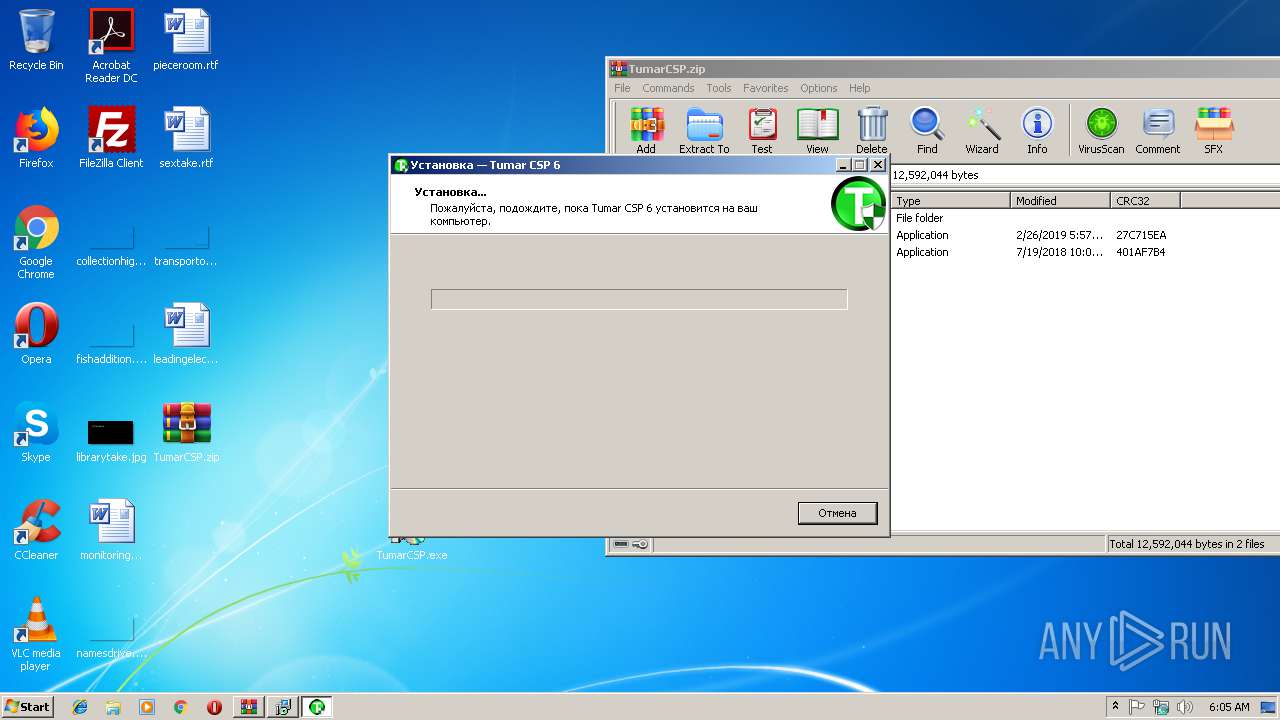
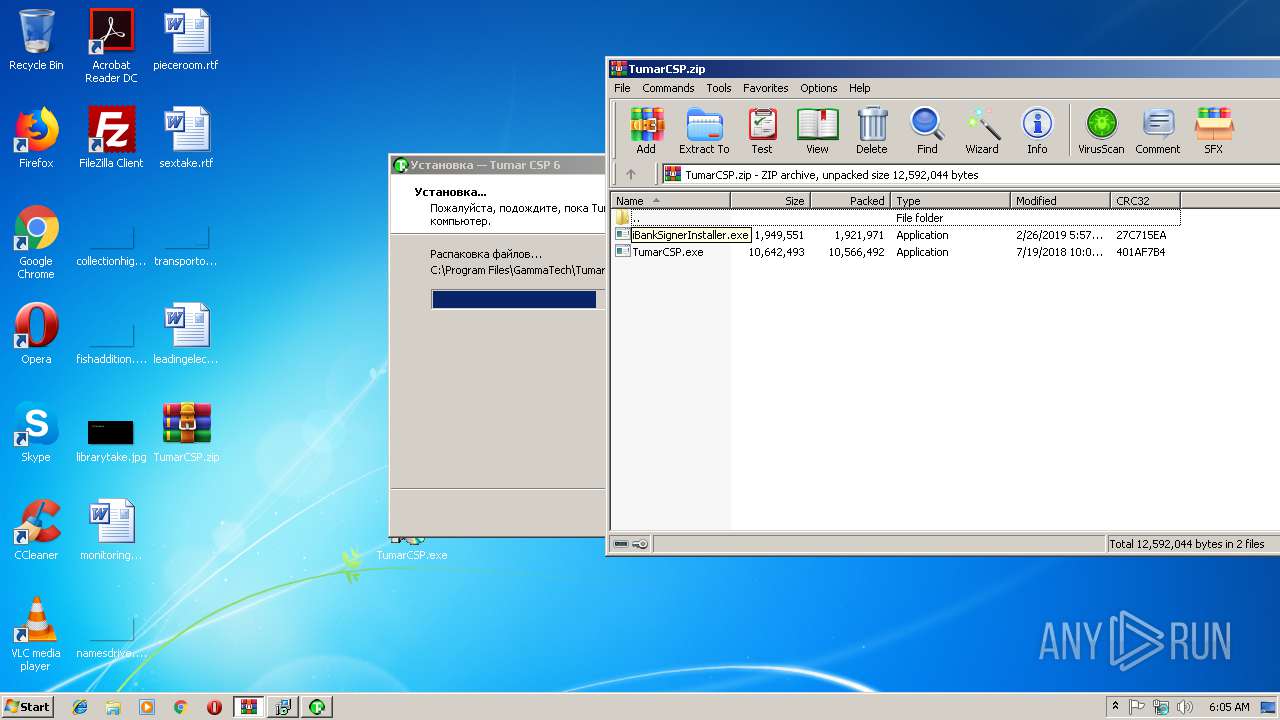
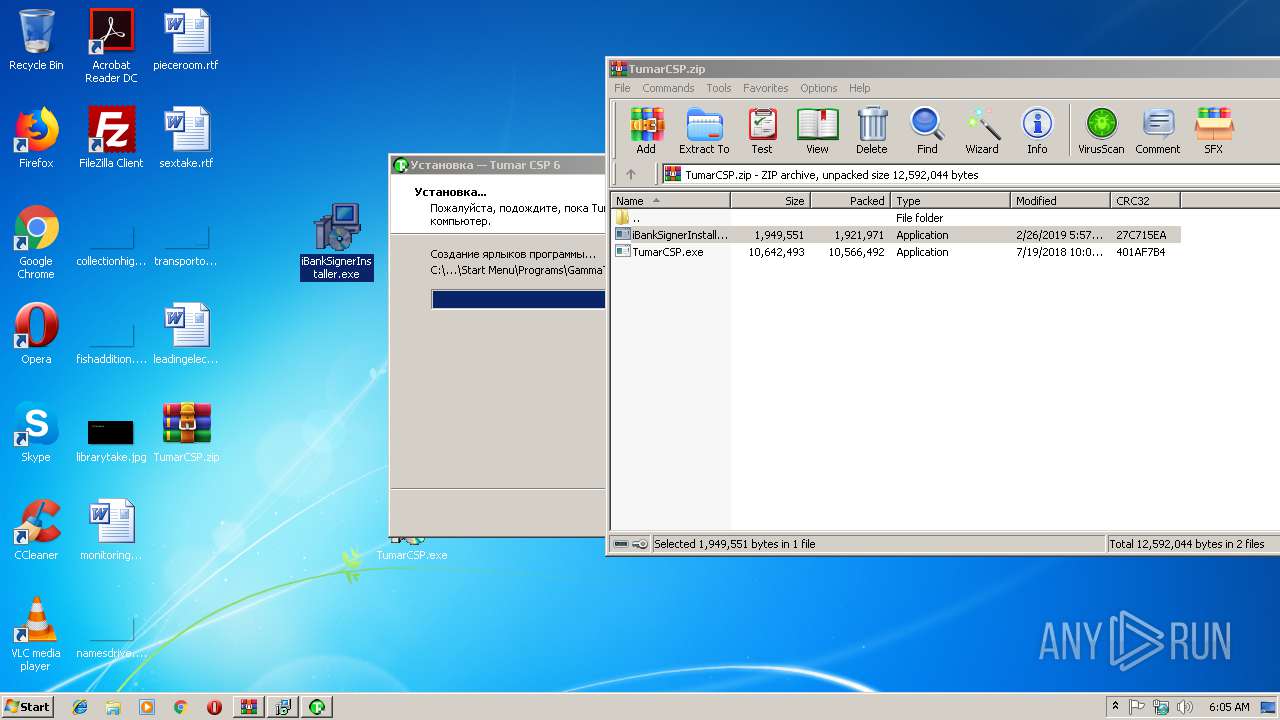
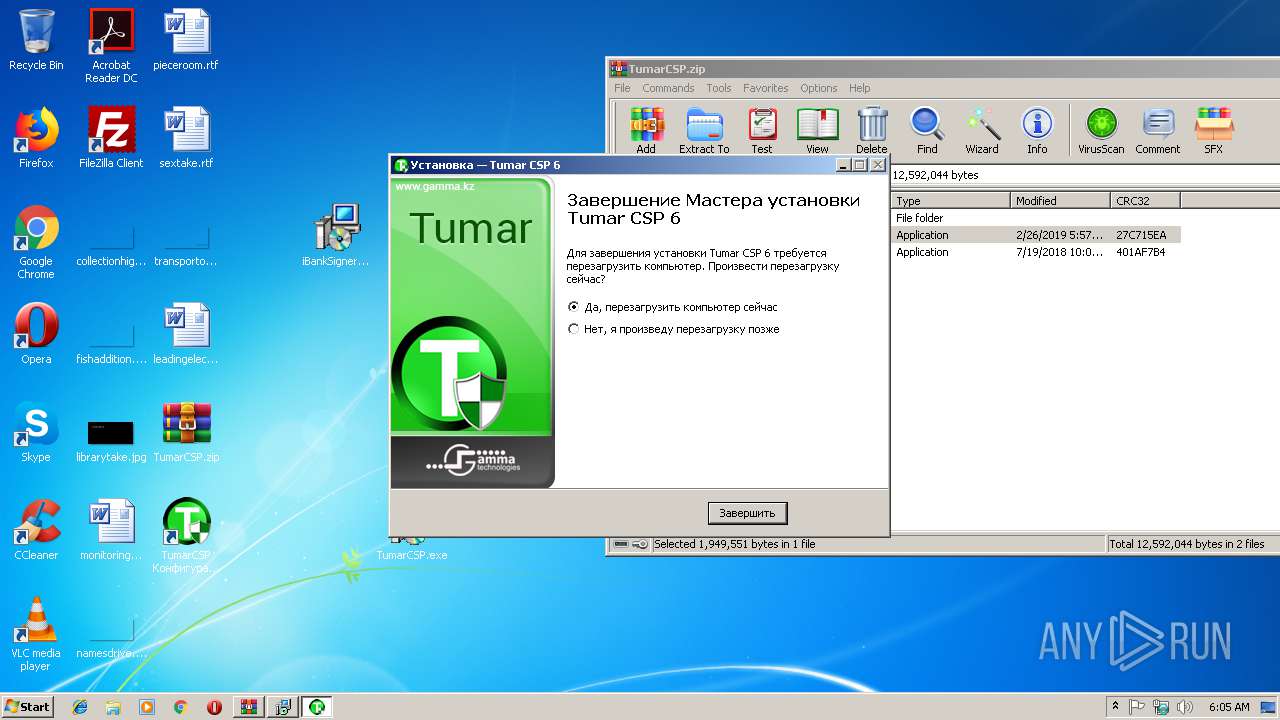
| File name: | TumarCSP.zip |
| Full analysis: | https://app.any.run/tasks/397595bf-8328-42ce-85b6-fae7ad91ccbf |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2019, 06:04:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | AE1EED7DC901EE9B39525A4F49C48CEA |
| SHA1: | E8ED9C2CAEB70A15E983B17CEA0235EE6223D75B |
| SHA256: | 584E804E484FCAC4B4B532495CB6FF2BE5F512C64E3D1F7320406E1CD3E140FA |
| SSDEEP: | 196608:RPw7yXjnnk3+u0s+L8eYzF5VyuBqj4Pb0eOC61tX7fyy9WErjoUb3hPVkX7Cdl6:lWujnru0s+Ye4FDyz4j03C61t+eHrjob |
MALICIOUS
Changes the autorun value in the registry
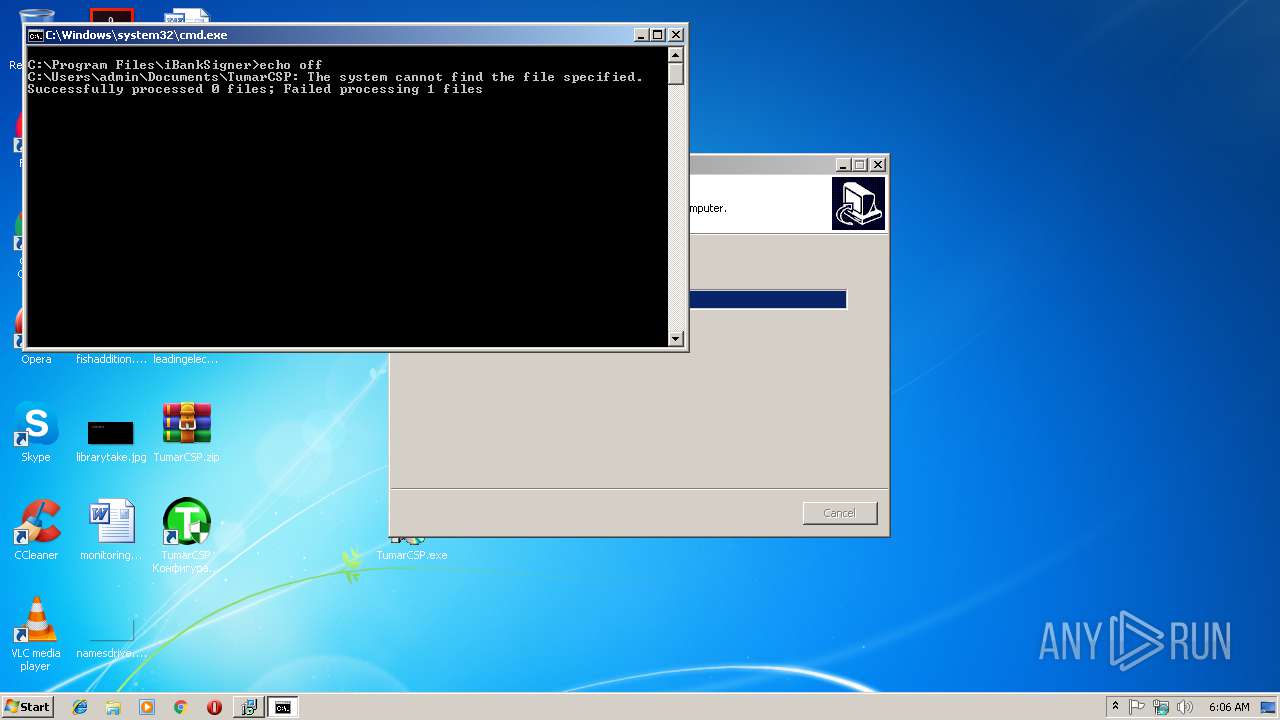
- TumarCSP.tmp (PID: 2888)
- SetupCSPx64.tmp (PID: 2600)
Changes settings of System certificates
- CertMgr.exe (PID: 3372)
- CertMgr.exe (PID: 2940)
- CertMgr.exe (PID: 2400)
- CertMgr.exe (PID: 456)
- TumProcess.exe (PID: 3324)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3560)
Application was dropped or rewritten from another process
- TumarCSP.exe (PID: 2288)
- TumarCSP.exe (PID: 2316)
- SetupCSPx64.exe (PID: 3840)
- CertMgr.exe (PID: 456)
- CertMgr.exe (PID: 3372)
- CertMgr.exe (PID: 2400)
- CertMgr.exe (PID: 2940)
- TumService.exe (PID: 3868)
- tumsrv204.exe (PID: 3784)
- TumService.exe (PID: 2388)
- TumService.exe (PID: 4004)
- TumProcess.exe (PID: 3324)
- TumCPProcess.exe (PID: 3408)
- iBankSignerInstaller.exe (PID: 2468)
- iBankSignerInstaller.exe (PID: 3416)
- iBankSigner.i386.exe (PID: 2940)
- iBankSigner.i386.exe (PID: 3784)
- iBankSigner.i386.exe (PID: 3088)
- iBankSignerInstaller.exe (PID: 3368)
- iBankSignerInstaller.exe (PID: 4060)
- iBankSigner.i386.exe (PID: 3700)
- iBankSigner.i386.exe (PID: 3520)
- iBankSigner.i386.exe (PID: 3108)
Changes internet zones settings
- regedit.exe (PID: 2884)
Changes AppInit_DLLs value (autorun option)
- SetupCSPx64.tmp (PID: 2600)
Starts NET.EXE for service management
- cmd.exe (PID: 3224)
Loads dropped or rewritten executable
- conhost.exe (PID: 2732)
- TumProcess.exe (PID: 3324)
- TumCPProcess.exe (PID: 3408)
- certutil.exe (PID: 3568)
- conhost.exe (PID: 2644)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3560)
- explorer.exe (PID: 284)
- DllHost.exe (PID: 3896)
- TumarCSP.exe (PID: 2316)
- SetupCSPx64.exe (PID: 3840)
- WinRAR.exe (PID: 3652)
- TumarCSP.exe (PID: 2288)
- iBankSignerInstaller.exe (PID: 2468)
- conhost.exe (PID: 3364)
- iBankSigner.i386.exe (PID: 3784)
- iBankSignerInstaller.exe (PID: 3368)
- iBankSignerInstaller.exe (PID: 4060)
- conhost.exe (PID: 3420)
- taskmgr.exe (PID: 3992)
- iBankSigner.i386.exe (PID: 3700)
- DllHost.exe (PID: 3456)
- NOTEPAD.EXE (PID: 3852)
- taskmgr.exe (PID: 3720)
- DllHost.exe (PID: 3036)
- DllHost.exe (PID: 2164)
- NOTEPAD.EXE (PID: 3908)
- DllHost.exe (PID: 3180)
- NOTEPAD.EXE (PID: 3084)
- iBankSignerInstaller.exe (PID: 3416)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 284)
- SetupCSPx64.tmp (PID: 2600)
- taskmgr.exe (PID: 3992)
Reads Internet Cache Settings
- explorer.exe (PID: 284)
- taskmgr.exe (PID: 3992)
Executable content was dropped or overwritten
- SetupCSPx64.exe (PID: 3840)
- TumarCSP.exe (PID: 2288)
- SetupCSPx64.tmp (PID: 2600)
- iBankSignerInstaller.exe (PID: 2468)
- TumarCSP.exe (PID: 2316)
- iBankSignerInstaller.tmp (PID: 2892)
- TumarCSP.tmp (PID: 2888)
- iBankSignerInstaller.exe (PID: 3416)
- iBankSignerInstaller.tmp (PID: 2420)
- iBankSignerInstaller.exe (PID: 4060)
- iBankSignerInstaller.exe (PID: 3368)
Reads Windows owner or organization settings
- SetupCSPx64.tmp (PID: 2600)
- TumarCSP.tmp (PID: 2888)
Reads the Windows organization settings
- SetupCSPx64.tmp (PID: 2600)
- TumarCSP.tmp (PID: 2888)
Creates files in the Windows directory
- SetupCSPx64.tmp (PID: 2600)
- TumService.exe (PID: 4004)
- TumCPProcess.exe (PID: 3408)
- certutil.exe (PID: 3568)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3560)
- iBankSigner.i386.exe (PID: 3784)
- iBankSigner.i386.exe (PID: 3700)
Uses REG.EXE to modify Windows registry
- SetupCSPx64.tmp (PID: 2600)
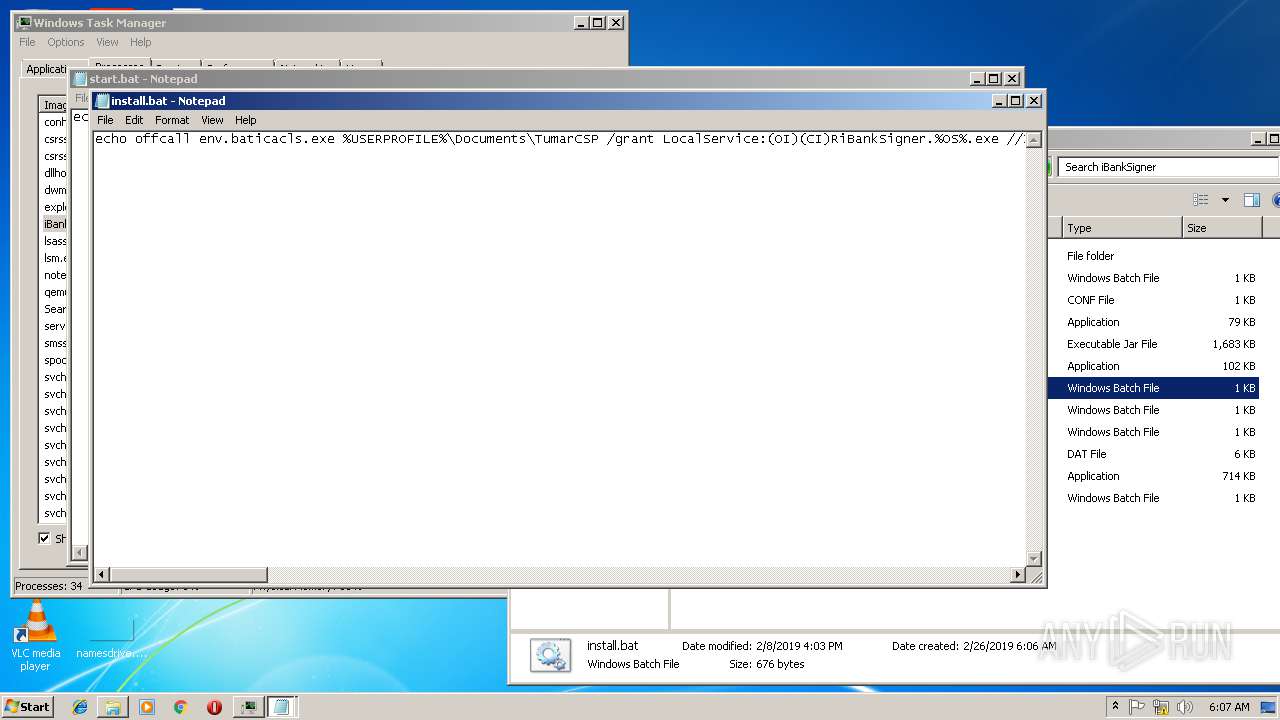
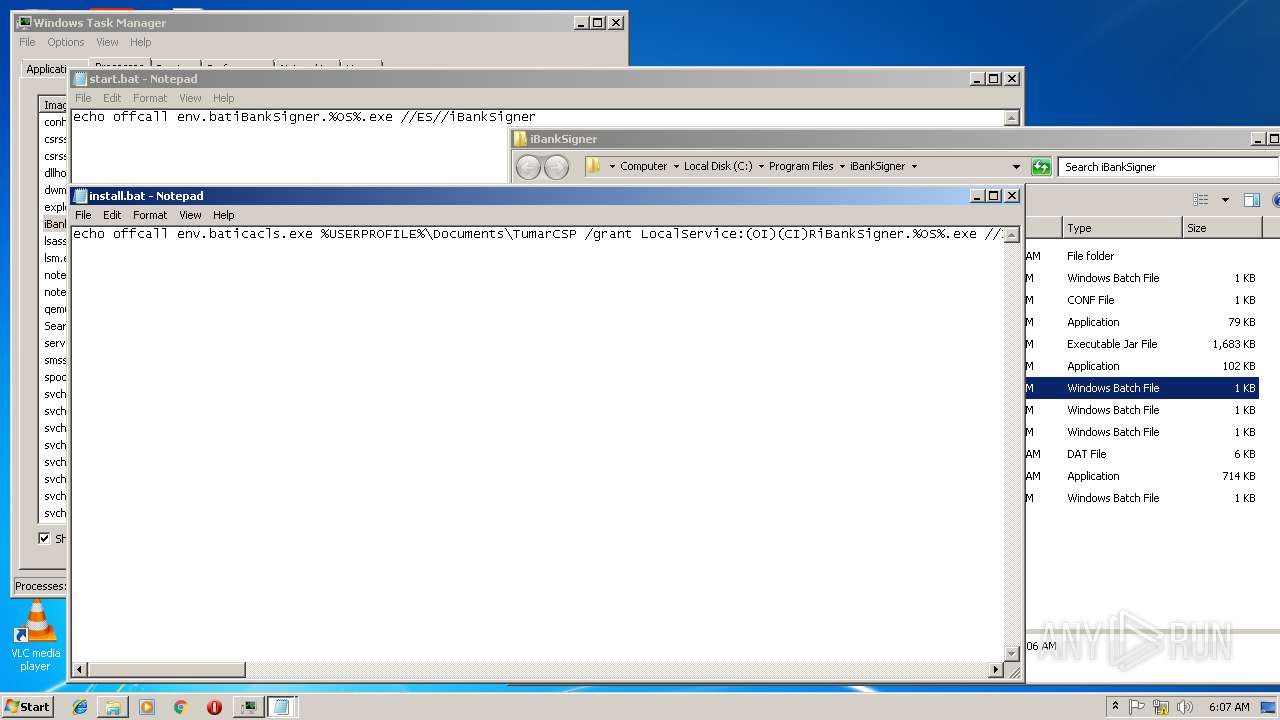
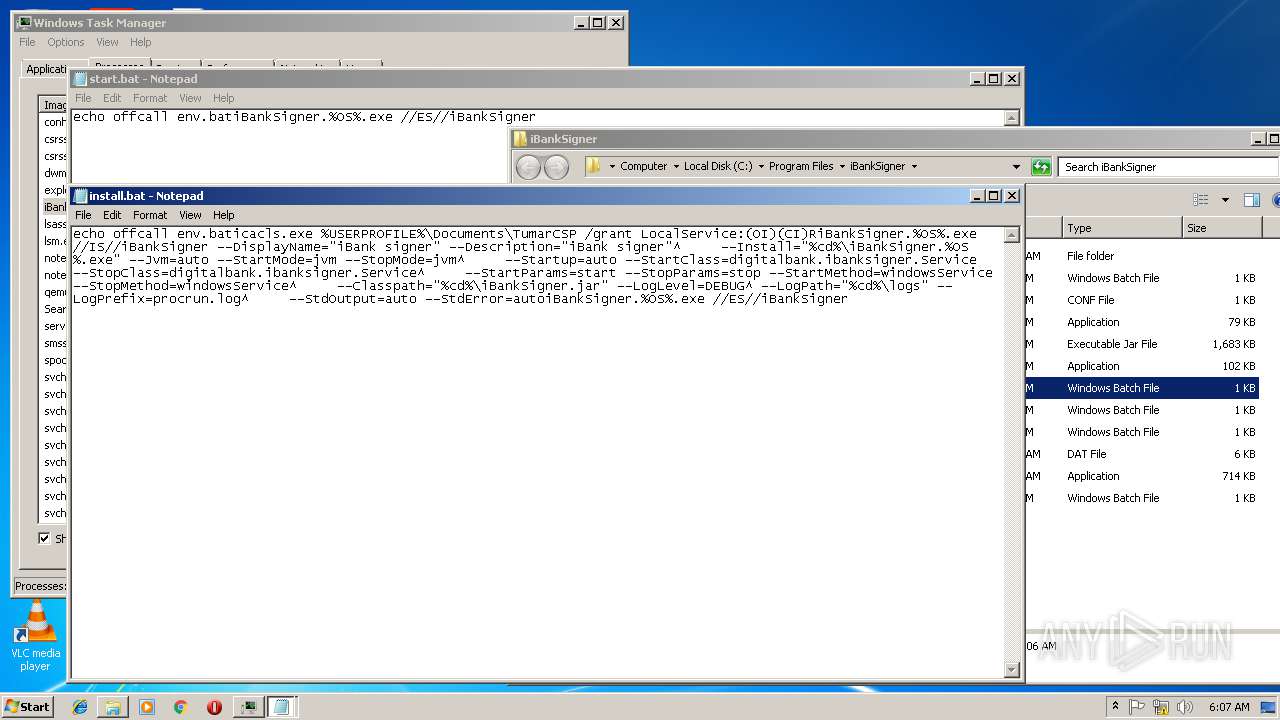
Uses ICACLS.EXE to modify access control list
- SetupCSPx64.tmp (PID: 2600)
- cmd.exe (PID: 3748)
- cmd.exe (PID: 3924)
Starts CMD.EXE for commands execution
- SetupCSPx64.tmp (PID: 2600)
- cmd.exe (PID: 2324)
- iBankSignerInstaller.tmp (PID: 2892)
- cmd.exe (PID: 3748)
- iBankSignerInstaller.tmp (PID: 2420)
- cmd.exe (PID: 3924)
Removes files from Windows directory
- certutil.exe (PID: 3568)
- certutil.exe (PID: 3080)
- certutil.exe (PID: 3560)
Creates or modifies windows services
- tumsrv204.exe (PID: 3784)
Starts SC.EXE for service management
- cmd.exe (PID: 3224)
Application launched itself
- cmd.exe (PID: 3748)
- taskmgr.exe (PID: 3992)
Creates files in the program directory
- iBankSigner.i386.exe (PID: 2940)
- iBankSigner.i386.exe (PID: 3784)
INFO
Creates files in the program directory
- TumarCSP.tmp (PID: 2888)
- SetupCSPx64.tmp (PID: 2600)
- iBankSignerInstaller.tmp (PID: 2892)
- iBankSignerInstaller.tmp (PID: 2420)
Application was dropped or rewritten from another process
- TumarCSP.tmp (PID: 2888)
- SetupCSPx64.tmp (PID: 2600)
- TumarCSP.tmp (PID: 3208)
- iBankSignerInstaller.tmp (PID: 2612)
- iBankSignerInstaller.tmp (PID: 2892)
- iBankSignerInstaller.tmp (PID: 2880)
- iBankSignerInstaller.tmp (PID: 2420)
Creates a software uninstall entry
- SetupCSPx64.tmp (PID: 2600)
- iBankSignerInstaller.tmp (PID: 2892)
- iBankSignerInstaller.tmp (PID: 2420)
Loads dropped or rewritten executable
- TumarCSP.tmp (PID: 2888)
- SetupCSPx64.tmp (PID: 2600)
- TumarCSP.tmp (PID: 3208)
- iBankSignerInstaller.tmp (PID: 2612)
- iBankSignerInstaller.tmp (PID: 2892)
- iBankSignerInstaller.tmp (PID: 2880)
- iBankSignerInstaller.tmp (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:02:26 11:57:12 |
| ZipCRC: | 0x27c715ea |
| ZipCompressedSize: | 1921971 |
| ZipUncompressedSize: | 1949551 |
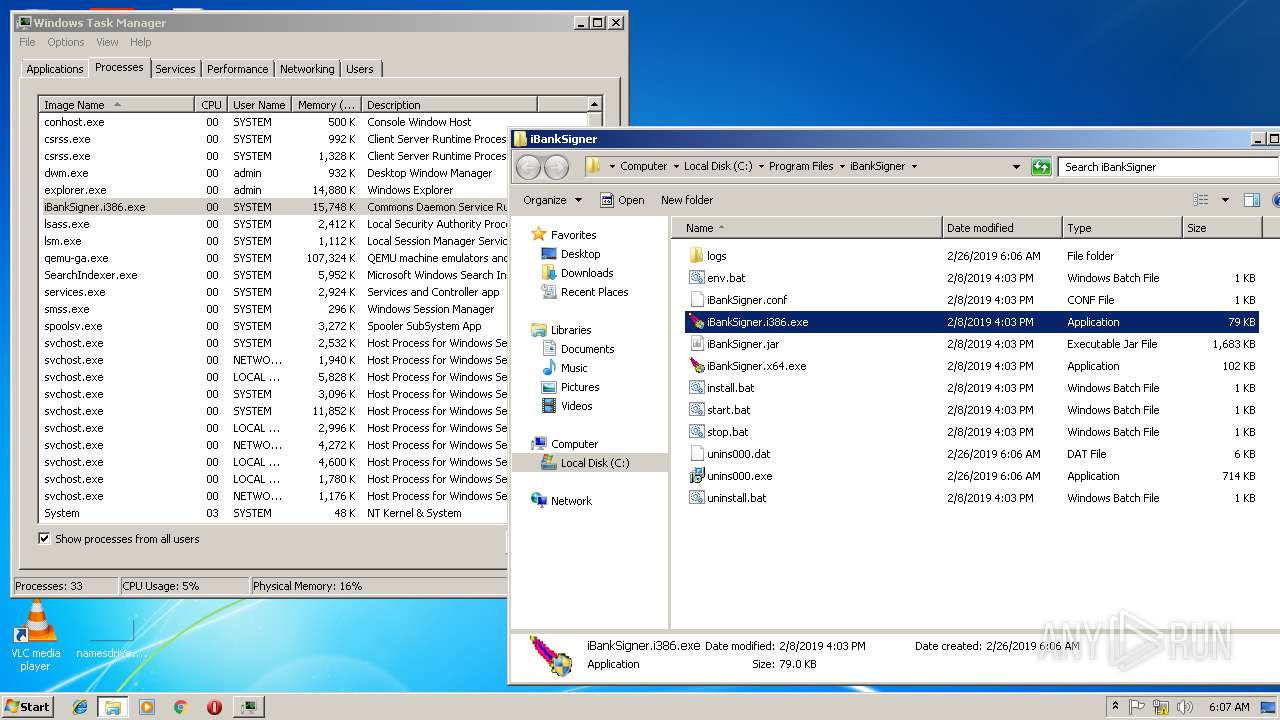
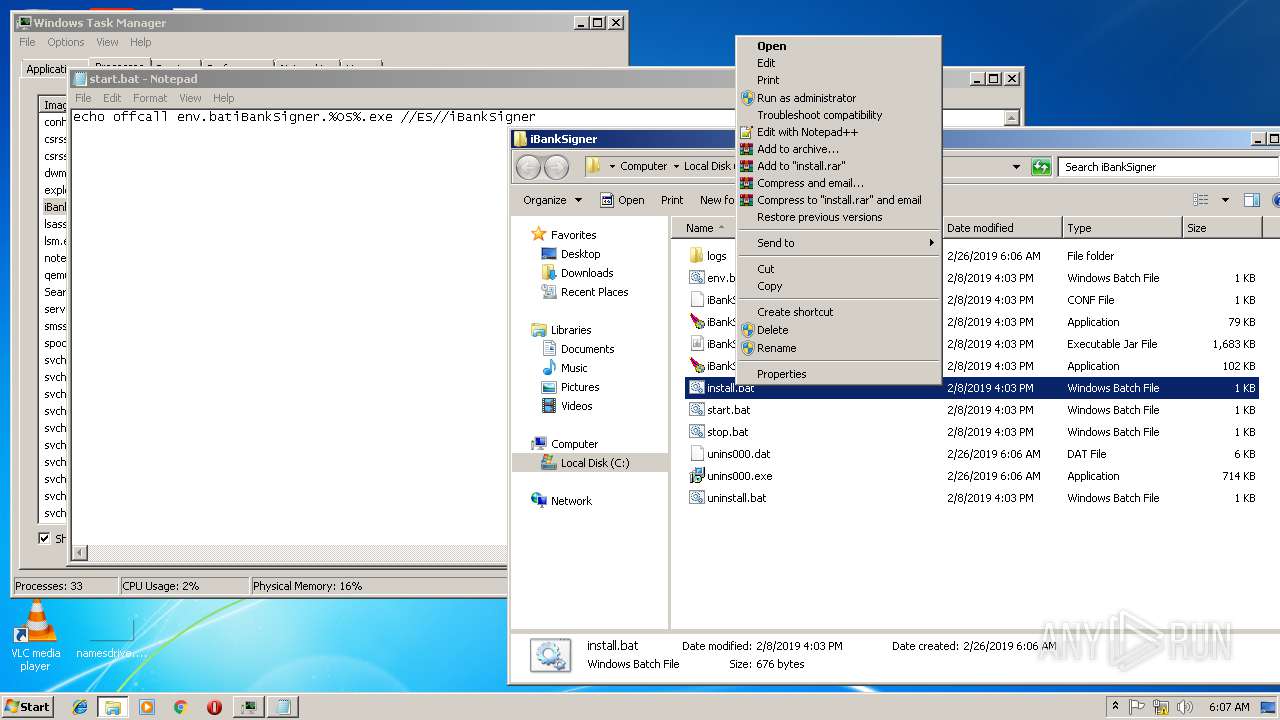
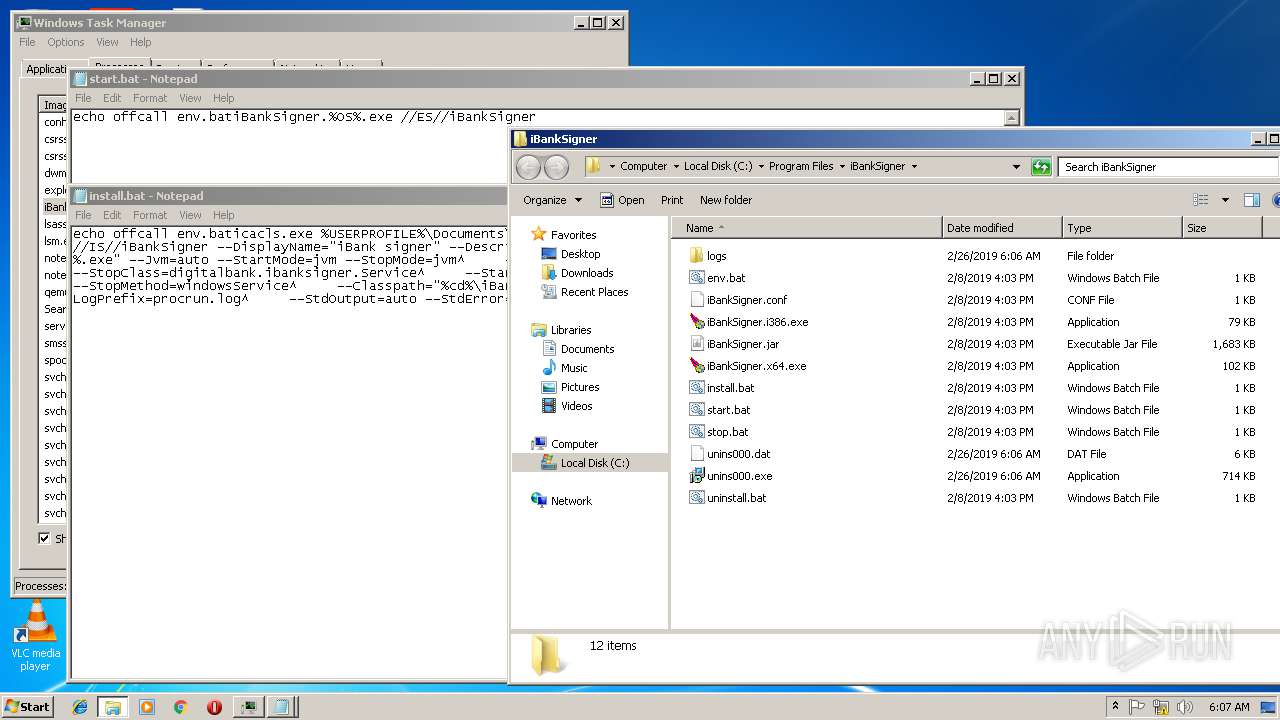
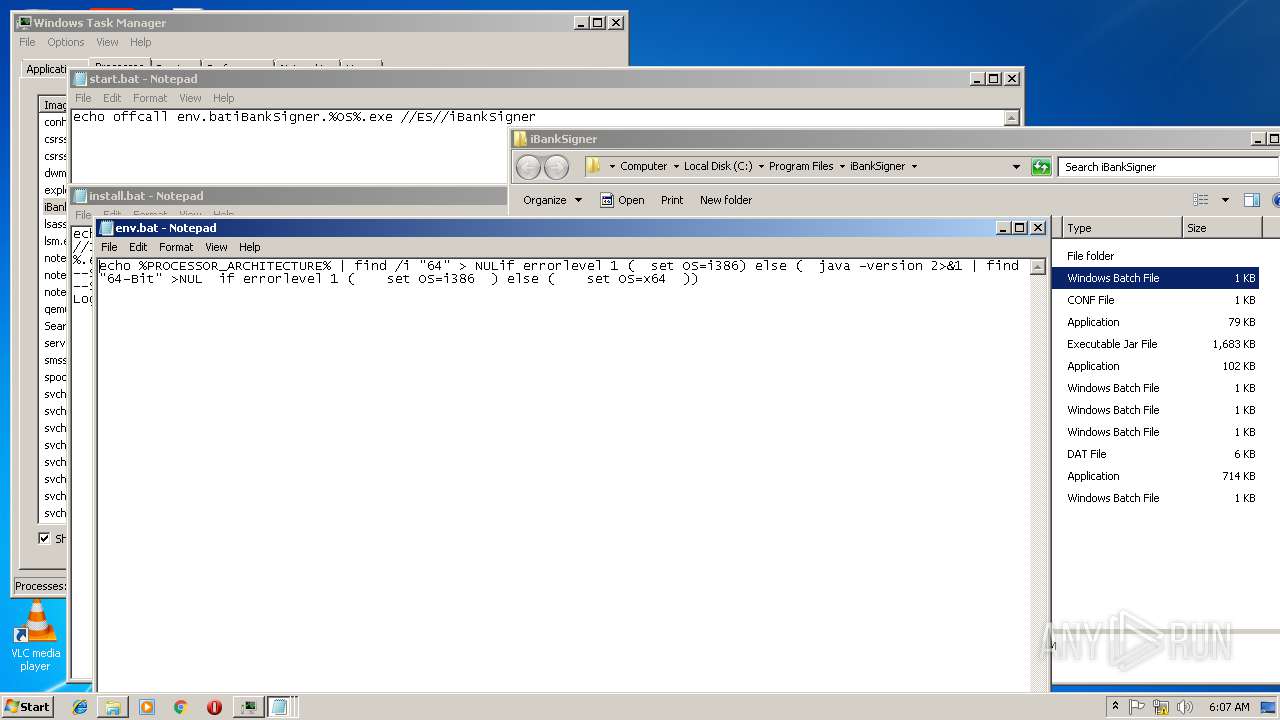
| ZipFileName: | iBankSignerInstaller.exe |
Total processes
127
Monitored processes
71
Malicious processes
19
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 456 | "C:\Program Files\GammaTech\TumarCSP\temp\CertMgr.exe" /add /c betaca_rsa.cer /s /r localMachine Root | C:\Program Files\GammaTech\TumarCSP\temp\CertMgr.exe | — | TumarCSP.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 6.0.6000.16384 (vista_rtm.061029-1900) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\TumarCSP.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1968 | find /i "64" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2164 | C:\Windows\system32\DllHost.exe /Processid:{AB8902B4-09CA-4BB6-B78D-A8F59079A8D5} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "reg.exe" export "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows" C:\Users\admin\AppData\Roaming\TumarCSP\appInit32.reg /y | C:\Windows\system32\reg.exe | — | SetupCSPx64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
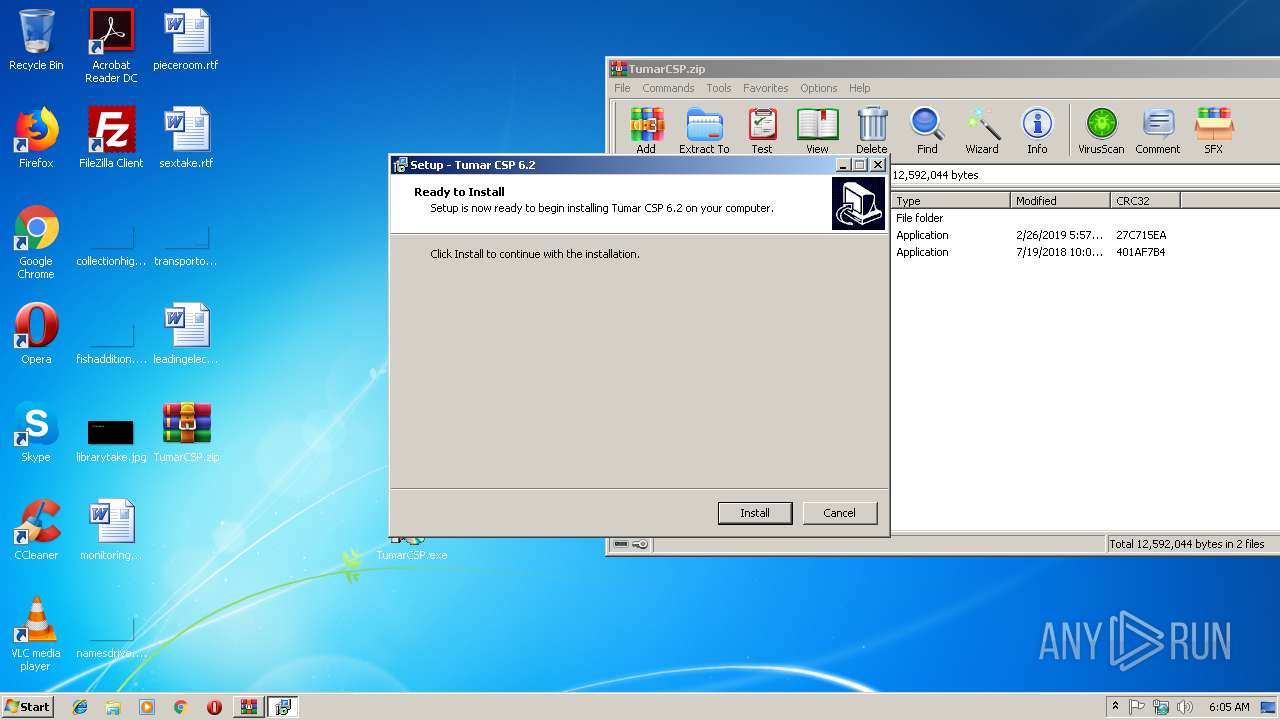
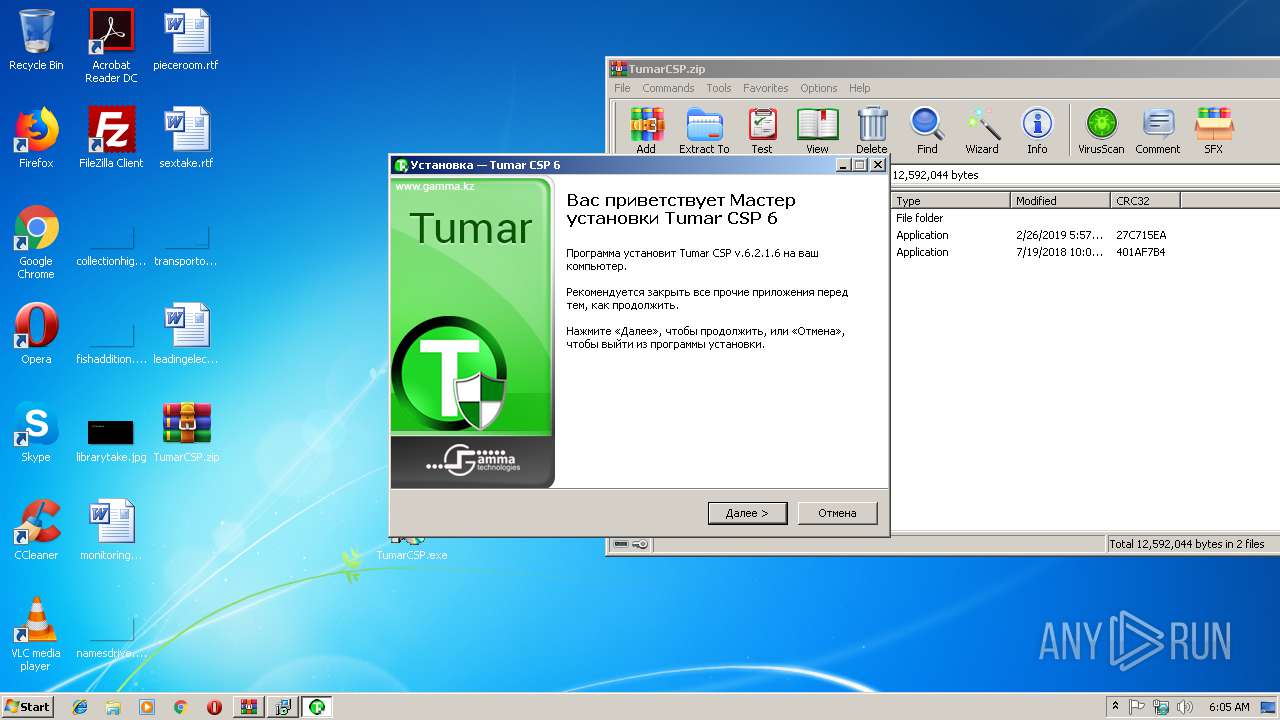
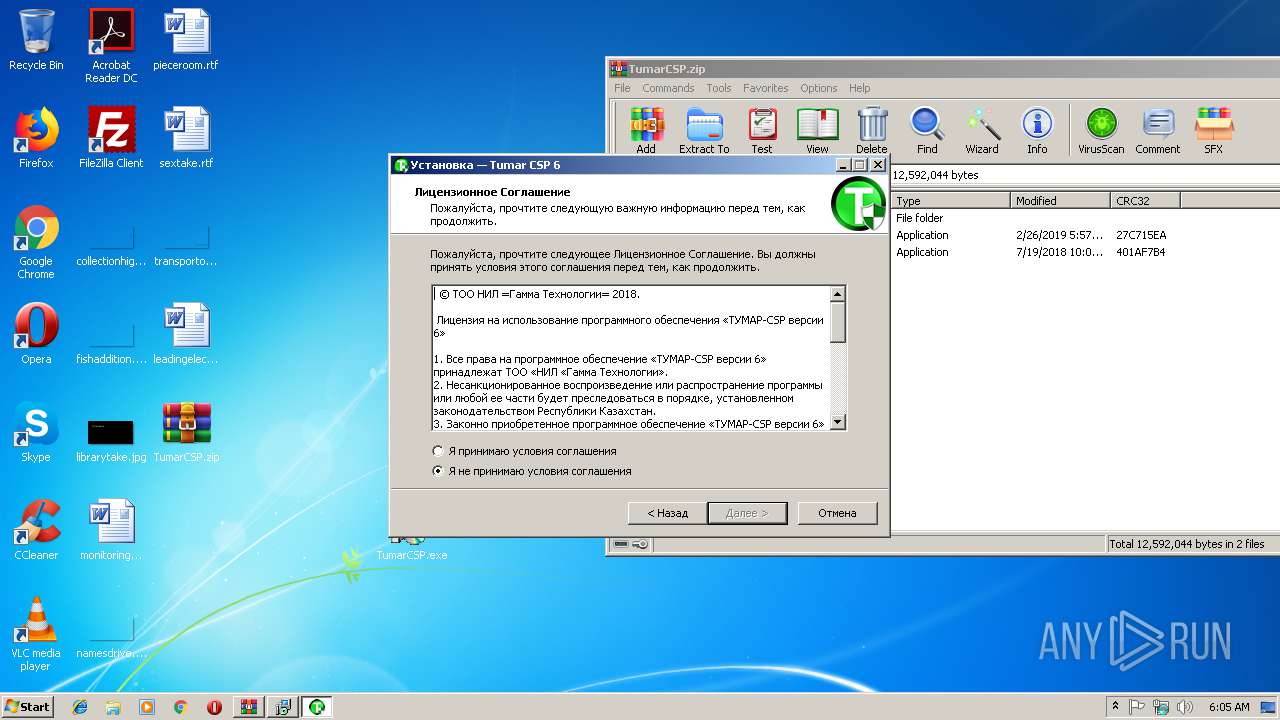
| 2288 | "C:\Users\admin\Desktop\TumarCSP.exe" | C:\Users\admin\Desktop\TumarCSP.exe | explorer.exe | ||||||||||||
User: admin Company: KISC Integrity Level: MEDIUM Description: Tumar CSP 6.2 Setup Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2304 | C:\Windows\system32\cmd.exe /S /D /c" echo x86 " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\Desktop\TumarCSP.exe" /SPAWNWND=$2013C /NOTIFYWND=$70110 | C:\Users\admin\Desktop\TumarCSP.exe | TumarCSP.tmp | ||||||||||||
User: admin Company: KISC Integrity Level: HIGH Description: Tumar CSP 6.2 Setup Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2324 | "C:\Windows\system32\cmd.exe" /C ""installCert.bat" "C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\FF"" | C:\Windows\system32\cmd.exe | — | SetupCSPx64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
5 762
Read events
5 132
Write events
600
Delete events
30
Modification events
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 00000000010000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF80CD054799CDD40100000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002F0000003D00000085431500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000E0000005DEC04007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000003702000008023CE23702350100C082BAD075B048D4750200000001000000A048D4750100000068E23702C5B8D075A848D47501000000C81008000000000090E237026BB9D07500000000350100C001000000B0E23702973CB8779C3CB877F58CF77501000000350100C00000000088E23702FFFFFFFFF8E23702EDE0B47745727800FEFFFFFFC0E237020D6BD075A0E737028CE8370200000000F8E23702973CB8779C3CB877BD8CF775000000008CE83702A0E73702D0E237020100000070E73702EDE0B47745727800FEFFFFFF08E337020D6BD0757E0000008CE8370280E73702F36BD075E186D0752794C6128CE8370210000000570104003E0040008CE83702A0E73702000000000000000000000000000008025CE537020000080254E33702350100C000000000D8E637023200000018000000000000000000000088E3370211000000B8450B00B0450B0032000000D8E63702F0E300009B1EC112A0E3370282919576F0E33702A4E3370227959576000000006C155002CCE33702CD9495766C15500278E43702E0105002E194957600000000E010500278E43702D4E33702090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\TumarCSP.zip | |||
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
48
Suspicious files
4
Text files
50
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1848.13728\TumarCSP.exe | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-MHKVH.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Users\admin\AppData\Local\Temp\is-ARDP7.tmp\is-SKDDC.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Users\admin\AppData\Local\Temp\is-ARDP7.tmp\is-RQLPR.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-53ESE.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-DAVUI.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-KNVJE.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-9FPF4.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\Program Files\GammaTech\TumarCSP\temp\is-2KCPO.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | TumarCSP.tmp | C:\ProgramData\GammaTech\TumarCSP\is-DNFG8.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
TumService.exe | TumarCSP start |
TumService.exe | TumarCSP stop |
TumService.exe | TumarCSP start |
TumService.exe | TumarCSP start |
TumService.exe | TumarCSP stop |
TumService.exe | User info: |
TumService.exe | 1 [2]:SessionId = 1 - pWinStationName =Console SessionState = [0] |
TumProcess.exe | !!! module: c:\Windows\System32\TumProcess.exe [TumProcess.exe_3324] |
conhost.exe | !!! module: C:\Windows\system32\conhost.exe [conhost.exe_2644] |
conhost.exe | !!! module: C:\Windows\system32\conhost.exe [conhost.exe_2644] |