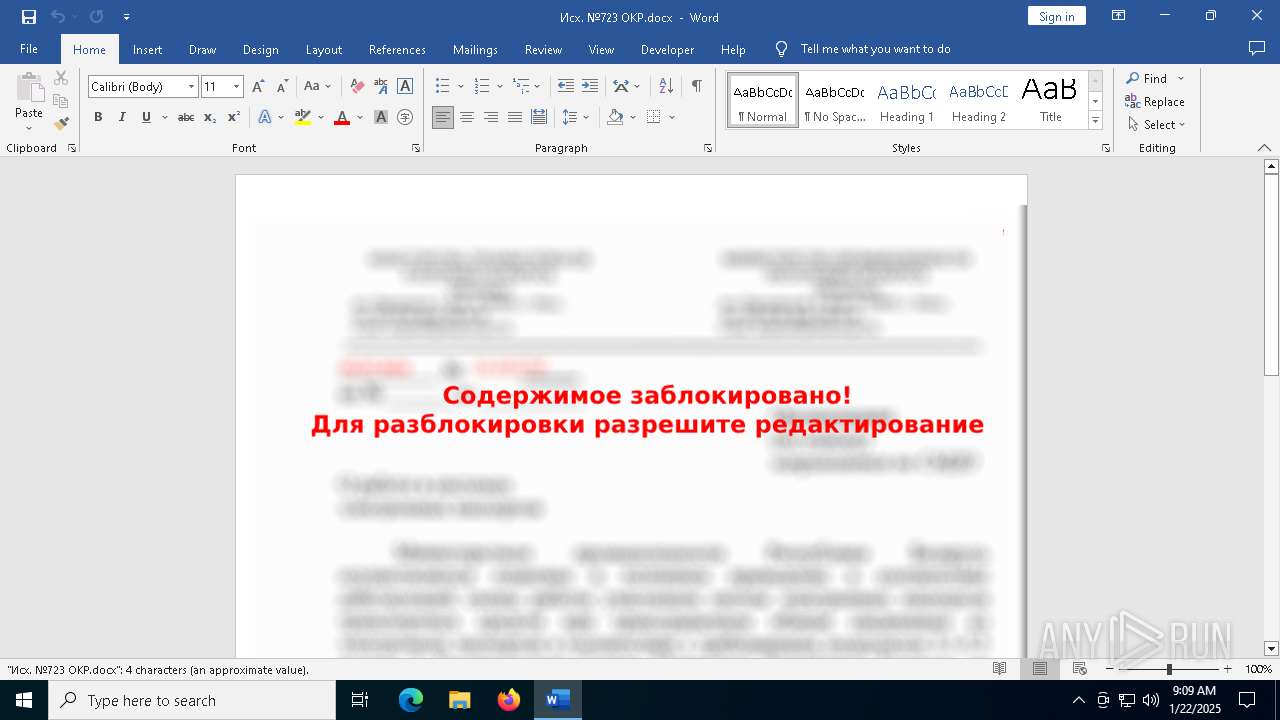
| File name: | Исх. №723 ОКР.docx |
| Full analysis: | https://app.any.run/tasks/dc4f9a62-c7f8-4d96-ac6e-6f8e5409fb8d |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2025, 09:08:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 922E1742EC5BC2D89611B123B483D04E |
| SHA1: | 448B005A29771251180D76524BB98683D329DA74 |
| SHA256: | 5847097ECC3C14479894F1F0F2510262F2908C310A54B97E62298452454F5B9B |
| SSDEEP: | 12288:nN85Y+a8Tib1nSE/FdQ0uo8ZsXCrGCRP9lvX:nN85Y+a8TiRSE/FdQ0uo8WXCtPb |
MALICIOUS
SMBSCAN has been detected (SURICATA)
- System (PID: 4)
SUSPICIOUS
Potential Corporate Privacy Violation
- System (PID: 4)
INFO
An automatically generated document
- WINWORD.EXE (PID: 4944)
The process uses the downloaded file
- WINWORD.EXE (PID: 4944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:21 12:17:38 |
| ZipCRC: | 0x167f8533 |
| ZipCompressedSize: | 350 |
| ZipUncompressedSize: | 1361 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | Aleksei Prokofev |
| RevisionNumber: | 2 |
| CreateDate: | 2024:06:21 13:45:00Z |
| ModifyDate: | 2024:06:21 13:45:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | Aleksei Prokofev |
| Description: | - |
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
| 4944 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Исх. №723 ОКР.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6992 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "1DA96A2D-D929-425F-855C-8AF6C937A4A3" "175C1A43-B714-4E08-B9EC-8A7F656E894D" "4944" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
13 433
Read events
13 093
Write events
320
Delete events
20
Modification events
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4944 |
| Operation: | write | Name: | 0 |
Value: 0B0E10C90CD985DFA4AA48BC32487DCCA68B10230046A2C29BEFD395DBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D026D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
122
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:E50D57A17E0C86451B1258FE3E2768A7 | SHA256:C8FC4374407065D16013DAC84BE73035403B0B1C38DA38E8FB85160DFF8DF936 | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$х. №723 ОКР.docx | binary | |
MD5:64DAF3E35E99A11BA5E7F0539DAA2292 | SHA256:137D66836E631DB5D9F7F96C954FC4D97CB89617A3EEC41BD3A1A3301EA786DC | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\Catalog\ListAll.Json | binary | |
MD5:C37972CBD8748E2CA6DA205839B16444 | SHA256:D4CFBB0E8B9D3E36ECE921B9B51BD37EF1D3195A9CFA1C4586AEA200EB3434A7 | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\cabFC17.tmp | compressed | |
MD5:D3C9036E4E1159E832B1B4D2E9D42BF0 | SHA256:434576EB1A16C2D14D666A33EDDE76717C896D79F45DF56742AFD90ACB9F21CE | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C158C9711E9A4533581BA7E894758C00 | SHA256:17738B6B6DA0FFB376193A4A284111087091C785C0EB58A183155DEDB3740801 | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:796C8DC92820E113B1D620FAF219E174 | SHA256:3A26C15E56EFEB350A459047E86D95B87366445E3B01844920388AFD906B595A | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:4E1440CF8FA844A8B83DFB5F35E64EFD | SHA256:335989189BF58E443FDD85CC611D96150480533472C45A0A9DEEC650F2724467 | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:354549F44E0F8E2927D76215C65CC747 | SHA256:CF96E63CF0CA84235897FA7C6453D4F43CF42DE7E18FE0BEC87998FF27844AAC | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:C5CAF271A049FB51CABD9477341F28EC | SHA256:81A106082347CC89BEFC05A8A744F0F2F86C4372E58D4E4C650C3443961AC756 | |||
| 4944 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
151
DNS requests
21
Threats
355
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4944 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6312 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4944 | WINWORD.EXE | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
4944 | WINWORD.EXE | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6312 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6448 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4944 | WINWORD.EXE | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
4944 | WINWORD.EXE | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4944 | WINWORD.EXE | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4944 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4944 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4944 | WINWORD.EXE | 2.19.11.103:443 | omex.cdn.office.net | Elisa Oyj | NL | whitelisted |
4 | System | 31.214.157.162:445 | — | servinga GmbH | NL | malicious |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|