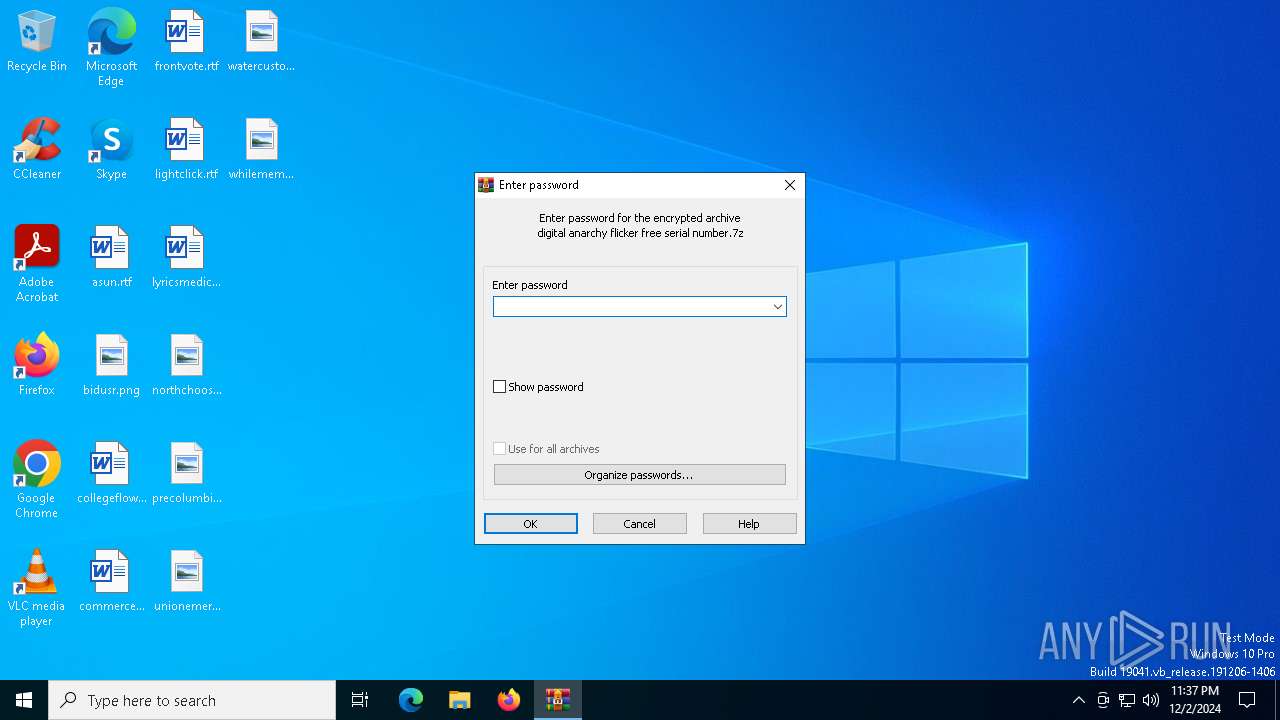
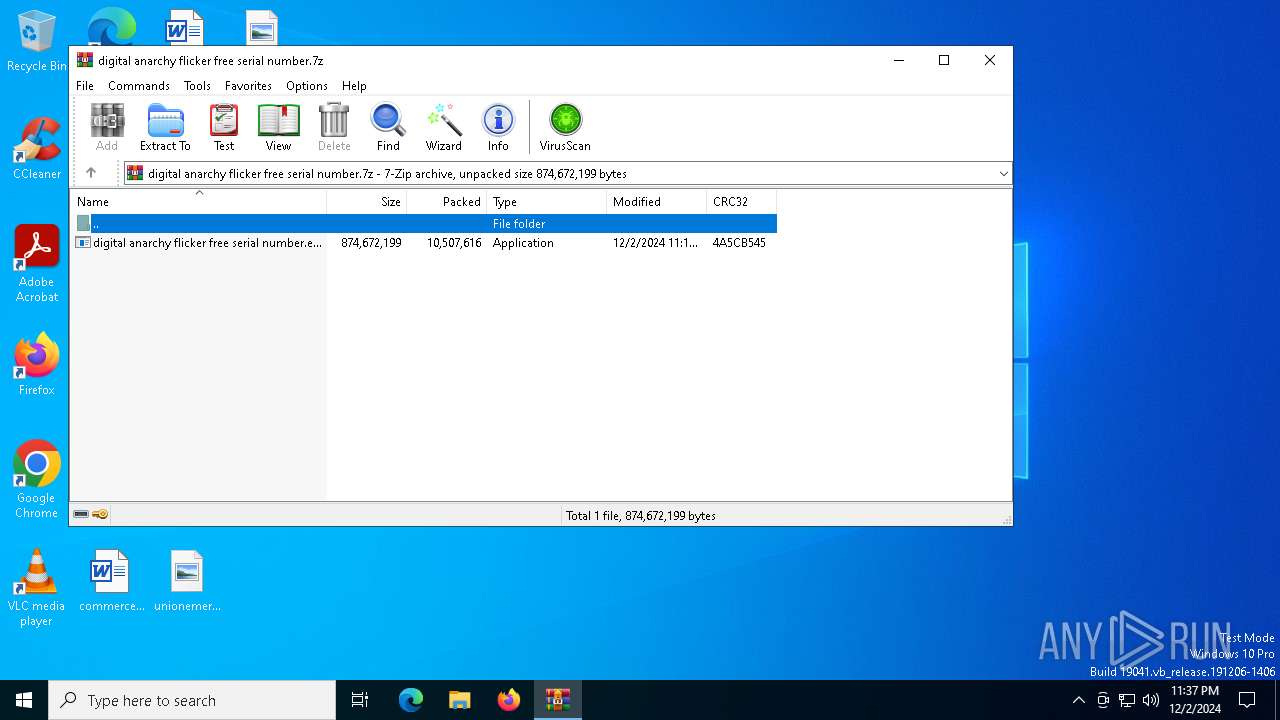
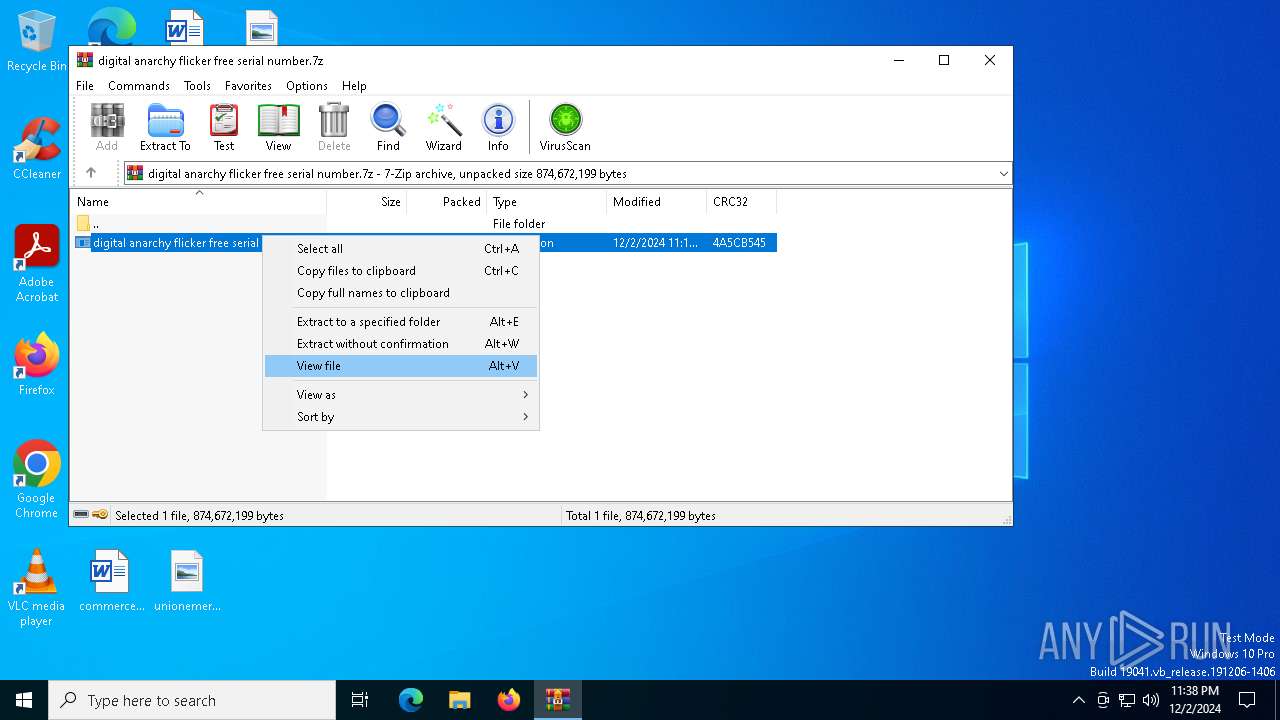
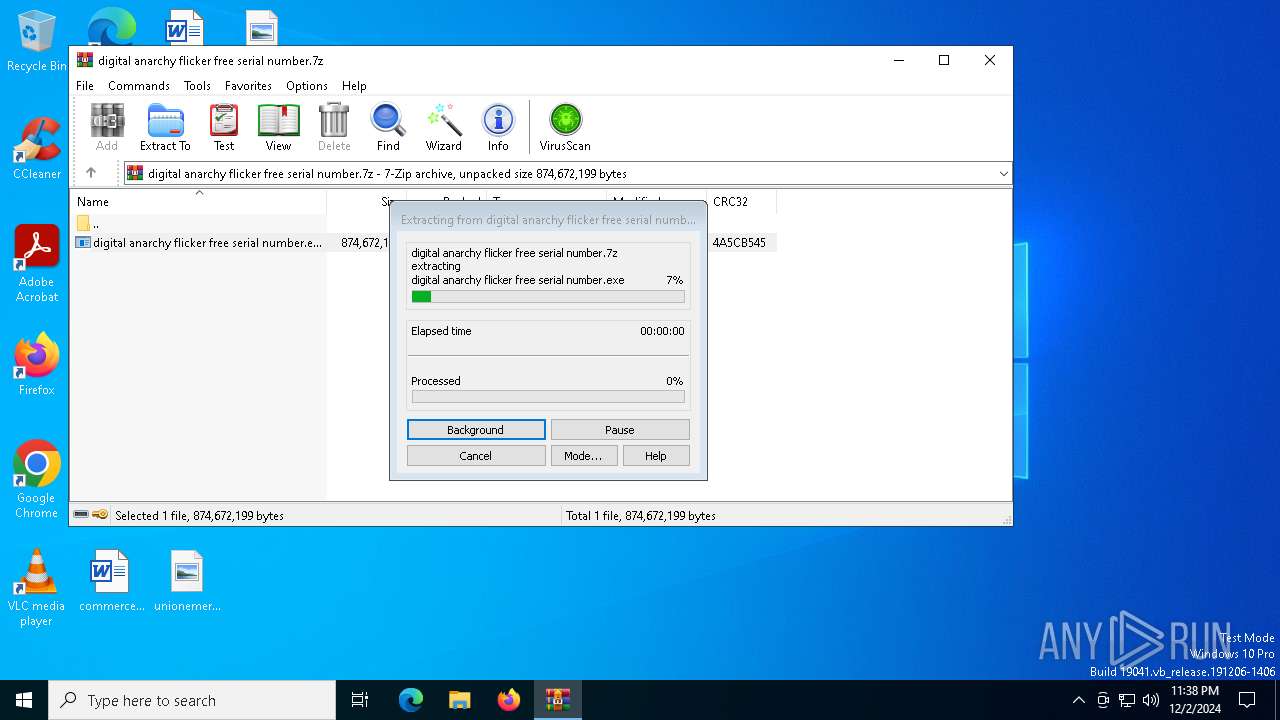
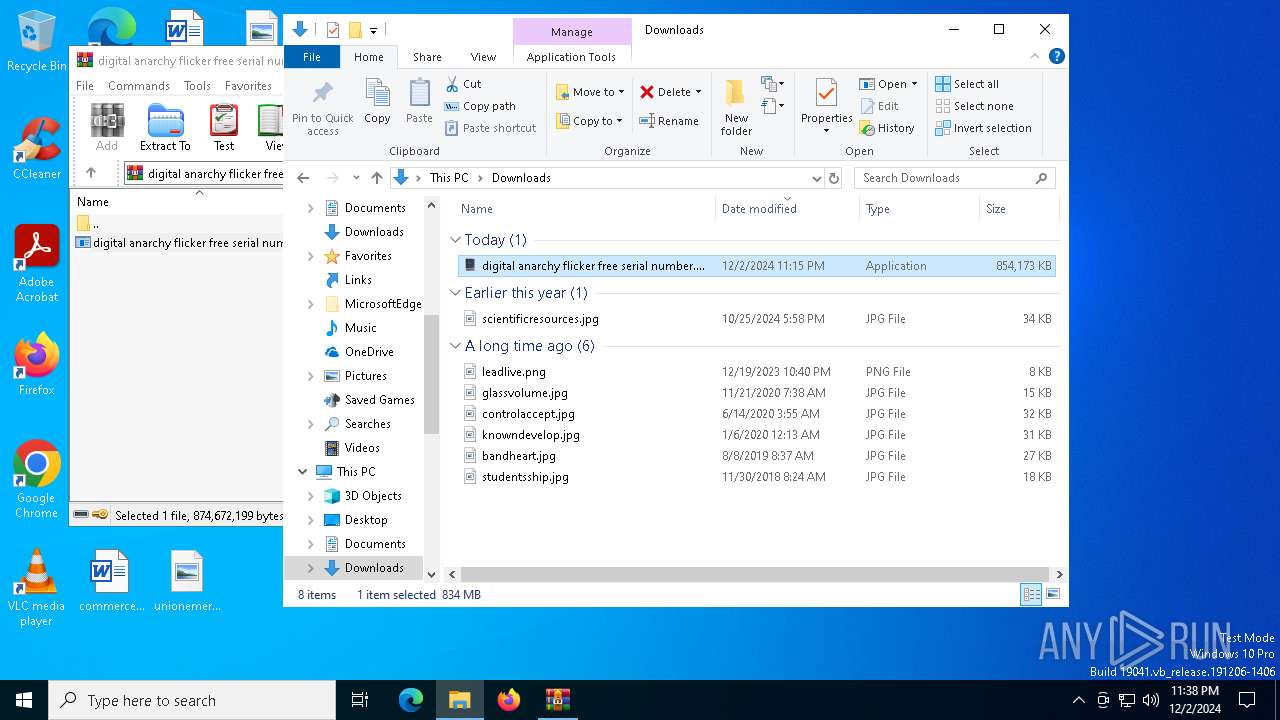
| File name: | digital anarchy flicker free serial number.7z |
| Full analysis: | https://app.any.run/tasks/e4122fc4-6251-408a-be14-94d1331a0164 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2024, 23:37:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | CCBAC337BD128CAEF01CCF40D247FF1D |
| SHA1: | F6D751BFDDA328FAAAC7B903498868229541B772 |
| SHA256: | 584290C7BA80CDA4224089DDFBA902AE55C94E209CF21DC150455D661098E191 |
| SSDEEP: | 98304:VsG1J69bCo4DDHQ8CdxFiV+8iDc+/AaCvSkH/WHeHhj6bfOoPfR47XAySBuHhdKj:83X+nhshAMTN2MQQ5Q0im1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- digital anarchy flicker free serial number.exe (PID: 2776)
- cmd.exe (PID: 5000)
- cmd.exe (PID: 5992)
- digital anarchy flicker free serial number.exe (PID: 6796)
Executing commands from ".cmd" file
- digital anarchy flicker free serial number.exe (PID: 2776)
- digital anarchy flicker free serial number.exe (PID: 6796)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5000)
- cmd.exe (PID: 5992)
Application launched itself
- cmd.exe (PID: 5000)
- cmd.exe (PID: 5992)
Starts application with an unusual extension
- cmd.exe (PID: 5000)
- cmd.exe (PID: 5992)
Get information on the list of running processes
- cmd.exe (PID: 5000)
- cmd.exe (PID: 5992)
Executable content was dropped or overwritten
- cmd.exe (PID: 5000)
The executable file from the user directory is run by the CMD process
- Deviation.com (PID: 6168)
- Deviation.com (PID: 7160)
Starts the AutoIt3 executable file
- cmd.exe (PID: 5992)
- cmd.exe (PID: 5000)
INFO
Manual execution by a user
- digital anarchy flicker free serial number.exe (PID: 2776)
- digital anarchy flicker free serial number.exe (PID: 6796)
Creates a new folder
- cmd.exe (PID: 1520)
- cmd.exe (PID: 7156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
149
Monitored processes
25
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1520 | cmd /c md 668805 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1904 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\Downloads\digital anarchy flicker free serial number.exe" | C:\Users\admin\Downloads\digital anarchy flicker free serial number.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3224 | findstr /V "ANDREWEXPRESSIONSSTRAPTEA" Political | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | "C:\Windows\System32\cmd.exe" /c copy Incorporated Incorporated.cmd && Incorporated.cmd | C:\Windows\SysWOW64\cmd.exe | digital anarchy flicker free serial number.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5076 | findstr /I "wrsa opssvc" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | findstr "AvastUI AVGUI bdservicehost nsWscSvc ekrn SophosHealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 936
Read events
3 911
Write events
12
Delete events
13
Modification events
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\digital anarchy flicker free serial number.7z | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
1
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | WinRAR.exe | C:\Users\admin\Downloads\digital anarchy flicker free serial number.exe | — | |
MD5:— | SHA256:— | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\Heart | binary | |
MD5:9719F9347981659E0EA34C891FA32A0D | SHA256:ECEC97238D84DDFC9E6EC3B80AF4B550B4D75FB3B42ACE114D2DD1B976E009BC | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\Olympic | binary | |
MD5:C602A8482E6A7757C5699541E2C69B56 | SHA256:06E840352DB96684FECD38BC6F17712DBC1571FF00504F87853E7262B9B2C375 | |||
| 6152 | cmd.exe | C:\Users\admin\AppData\Local\Temp\668805\r | binary | |
MD5:7E7DA683C4A20B84B408F4D177770E26 | SHA256:8160D9B706E6AA46BA48B0BD6755624729EE385965EECF1C6680B9BDBB96428E | |||
| 5000 | cmd.exe | C:\Users\admin\AppData\Local\Temp\668805\Deviation.com | executable | |
MD5:6EE7DDEBFF0A2B78C7AC30F6E00D1D11 | SHA256:865347471135BB5459AD0E647E75A14AD91424B6F13A5C05D9ECD9183A8A1CF4 | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\For | binary | |
MD5:0A87EF0EB3FF2E88CA9A79E7C65B09D3 | SHA256:101CCB6840080AD3CB708930E83D076E6F195D56892E87EA7857B8845392A203 | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\Directly | binary | |
MD5:5EF2813BDA3A8EFEA8271BF27E66BE4D | SHA256:0F0AE574EBDC9A4B67B95D026085CE05F6C054B06D094E2784514F26DCF31F68 | |||
| 6860 | cmd.exe | C:\Users\admin\AppData\Local\Temp\668805\r | binary | |
MD5:7E7DA683C4A20B84B408F4D177770E26 | SHA256:8160D9B706E6AA46BA48B0BD6755624729EE385965EECF1C6680B9BDBB96428E | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\Productivity | binary | |
MD5:1579866D452186F71515DC1FADEA522D | SHA256:ED25F96BA6089ED54389037BE95F24CA9B595360F98EEA8411782C2BD5F247E2 | |||
| 2776 | digital anarchy flicker free serial number.exe | C:\Users\admin\AppData\Local\Temp\Incorporated | text | |
MD5:0E52CC86A3B3BF7ABB5091330121C63B | SHA256:9257EFCC3880A265B87B9455B49E0F63ECFF554AA2305FE637AB2C3659CD71E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5464 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5464 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3884 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.19.80.89:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |