| download: | index.html |
| Full analysis: | https://app.any.run/tasks/ab478b50-c493-47c7-9526-401dde016a56 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 18:35:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | C50AA3E723AE7778BBE713A1E1C3D9D8 |
| SHA1: | 52A6D9FB3F811FCCDC17686F9229B187C4B3DFBF |
| SHA256: | 583DF0F2A1FC08CE8D190F38E6DBBC859C5376FDF8AF81D6F3B8F45783AB8B77 |
| SSDEEP: | 384:W+vrQXieV/CwscWC8FjxL+eq+6n8tqJt41VYP2h1d/qvFFvUbGdp8no0RQa4B+lK:WXiAuhryHHt43G8XXFBHE |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 2340)
Changes internet zones settings
- iexplore.exe (PID: 2952)
Creates files in the user directory
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2340)
Application launched itself
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3112)
Reads internet explorer settings
- iexplore.exe (PID: 3112)
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2340)
Reads settings of System Certificates
- iexplore.exe (PID: 2340)
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3112)
Changes settings of System certificates
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 3112)
- iexplore.exe (PID: 2952)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| viewport: | width=device-width, initial-scale=1 |
|---|---|
| HTTPEquivXUACompatible: | IE=edge |
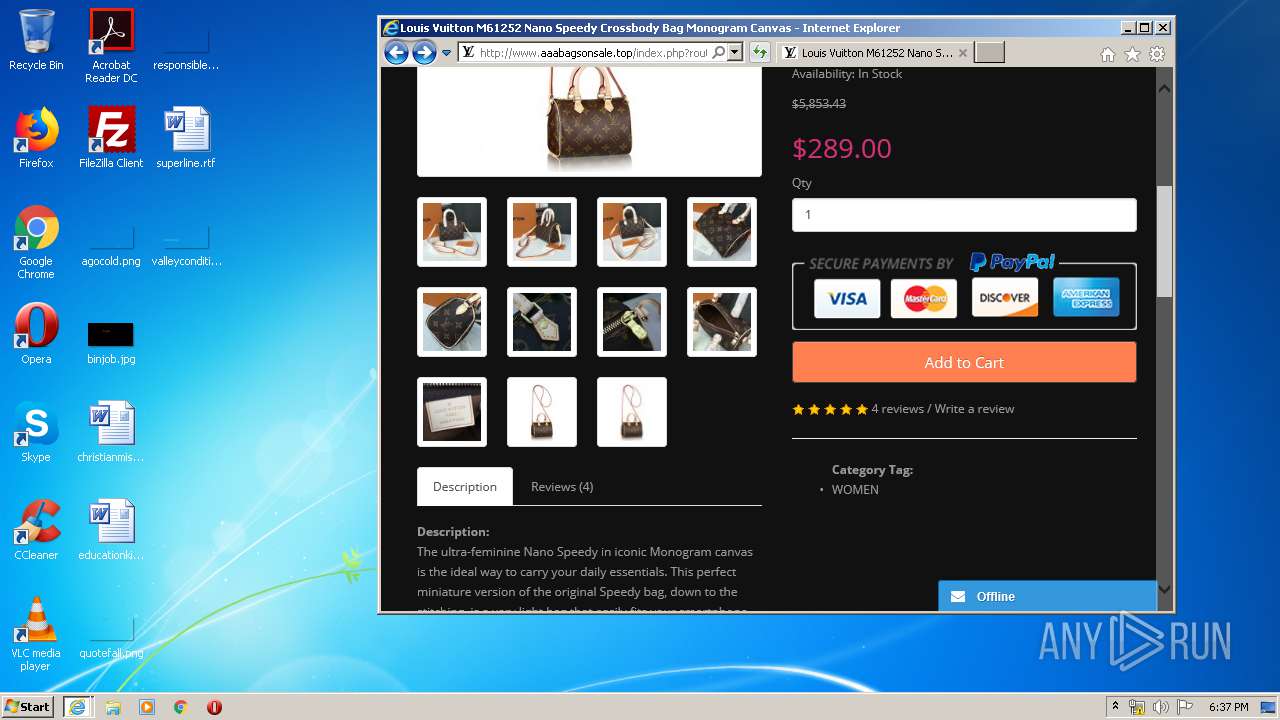
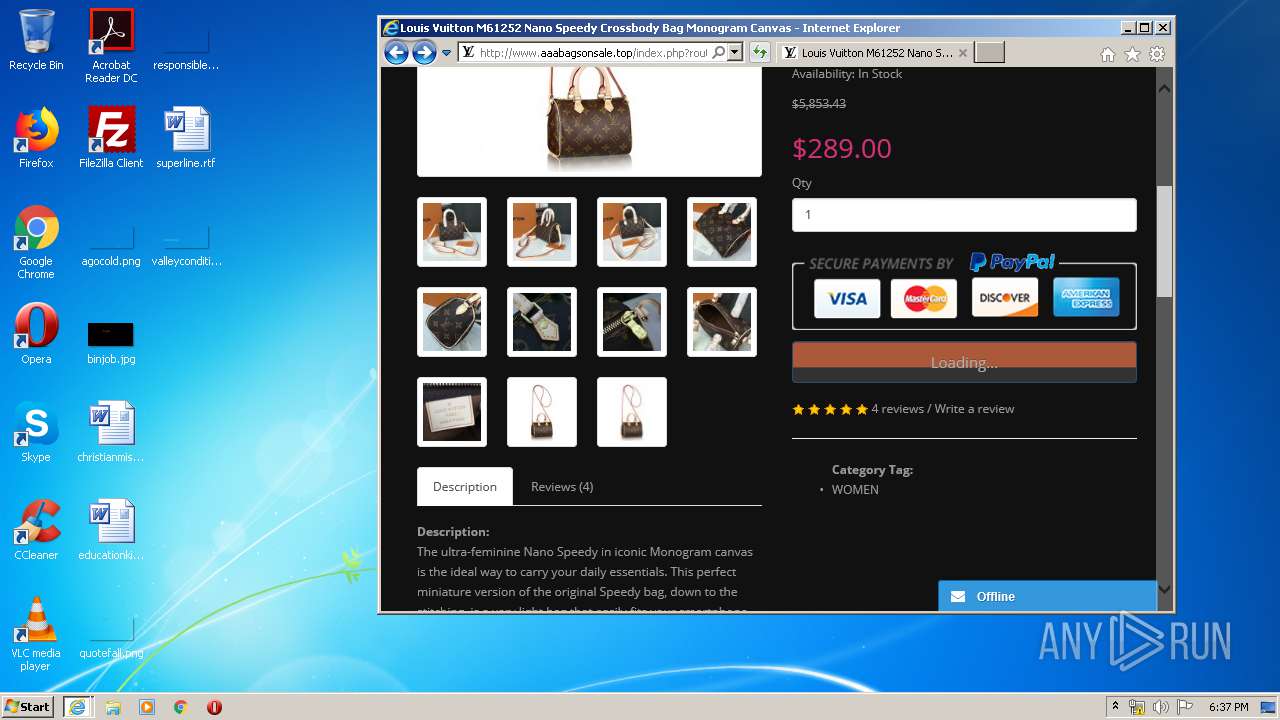
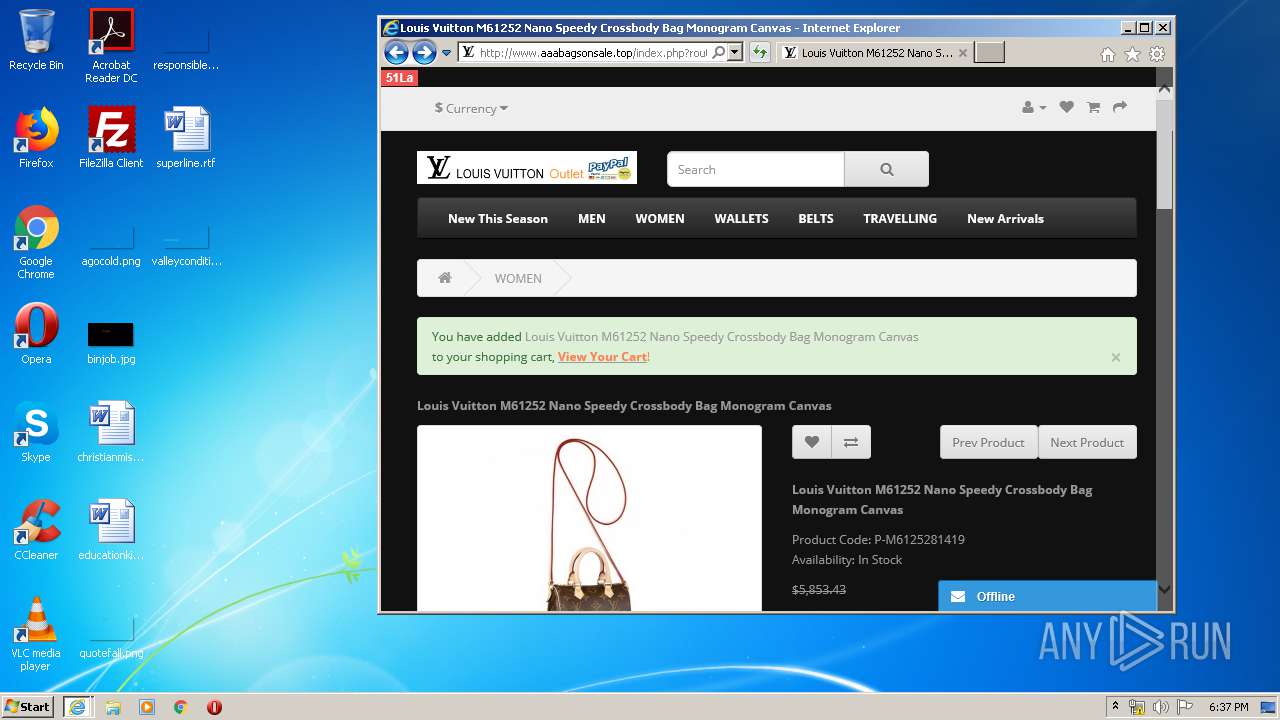
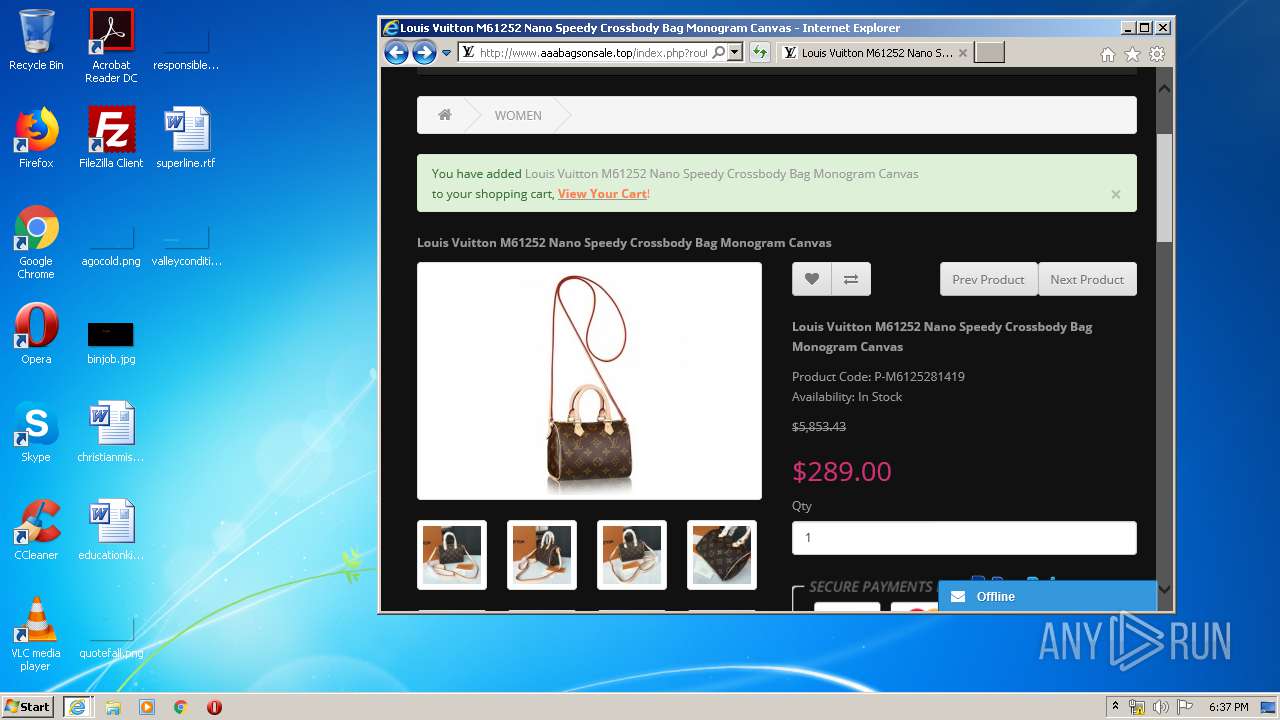
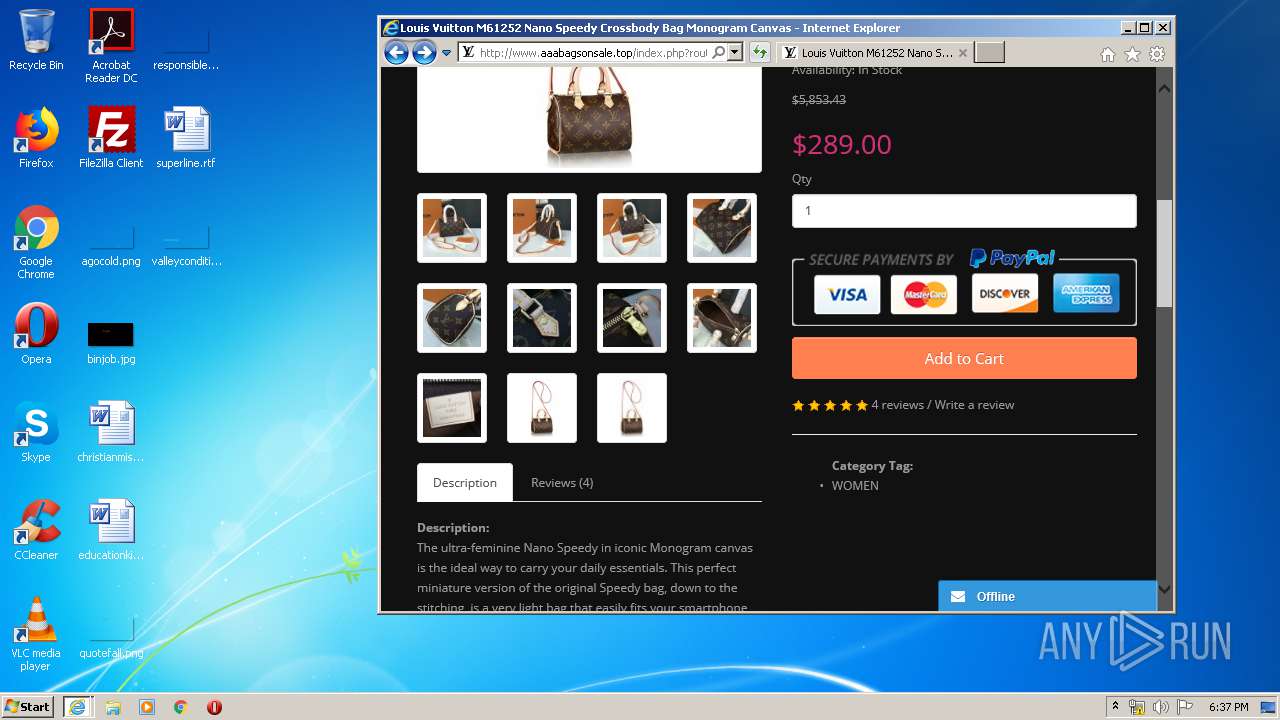
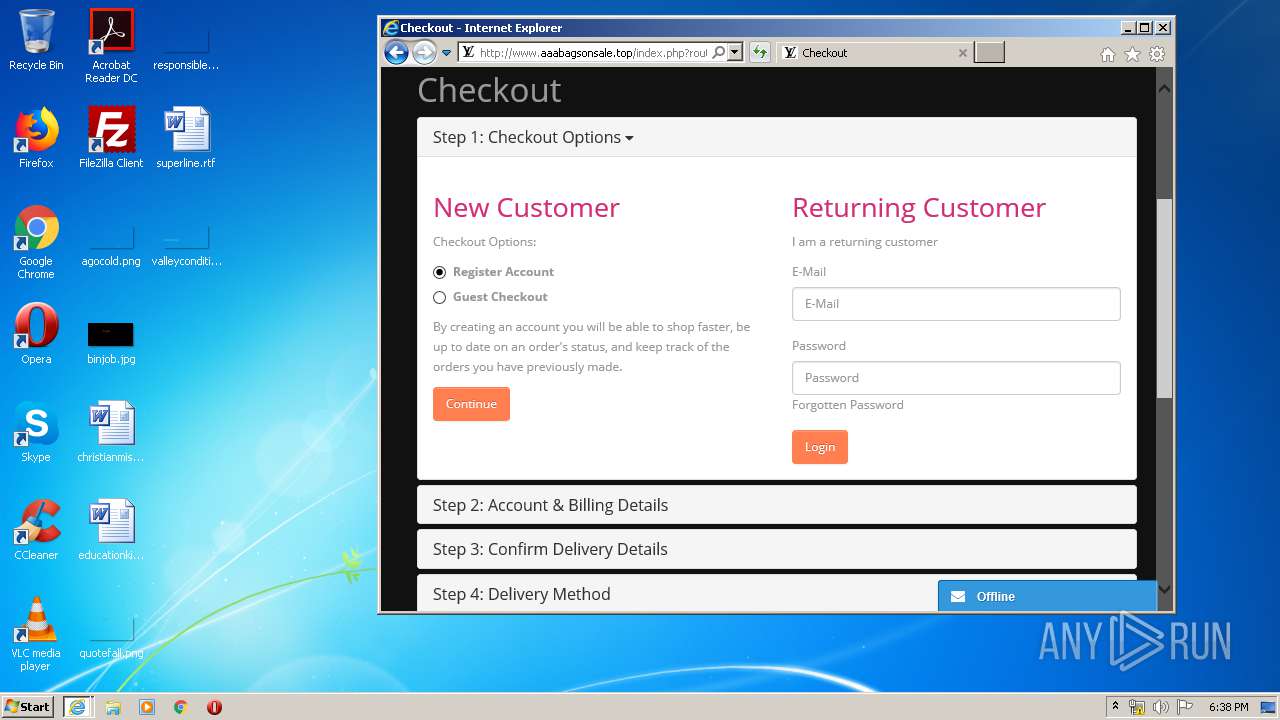
| Title: | LOUIS VUITTON Outlets |
| Description: | LOUIS VUITTON Outlets |
Total processes
41
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2340 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:398593 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2816 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:144390 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3112 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
16 815
Read events
1 580
Write events
10 205
Delete events
5 030
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3663865020 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796005 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
58
Text files
228
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\font-awesome.min[1].css | text | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\css[1].css | text | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\m40995-1-200x200[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\n41358-1-200x200[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\owl.carousel[1].css | text | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\bootstrap.min[1].css | text | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\9-200x200[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\m41066-1-200x200[1].jpg | — | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\12320171124012992729272-200x200[1].jpg | — | |
MD5:— | SHA256:— | |||
| 2816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stylesheet[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
249
TCP/UDP connections
154
DNS requests
35
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3112 | iexplore.exe | GET | 200 | 216.58.208.42:80 | http://fonts.googleapis.com/css?family=Open+Sans:400,400i,300,700 | US | text | 284 b | whitelisted |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/2019-11-08_19-32-19-76565-2280x760-2280x760.jpg | US | image | 345 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/1/112/9-200x200.jpg | US | image | 8.51 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/lv/m40780-1-200x200.jpg | US | image | 9.98 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/lv/12320171124012992729272-200x200.jpg | US | image | 11.4 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/catalog/view/javascript/jquery/owl-carousel/owl.carousel.css | US | text | 878 b | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/lv/n41358-1-200x200.jpg | US | image | 10.8 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/lv/652n41605-1-200x200.jpg | US | image | 11.7 Kb | suspicious |
2816 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/catalog/view/javascript/font-awesome/css/font-awesome.min.css | US | text | 5.79 Kb | suspicious |
3112 | iexplore.exe | GET | 200 | 104.24.106.14:80 | http://www.aaabagsonsale.top/image/cache/catalog/11124f-2280x760.jpg | US | image | 616 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3112 | iexplore.exe | 220.242.182.12:443 | js.users.51.la | — | CN | suspicious |
3112 | iexplore.exe | 216.58.208.42:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3112 | iexplore.exe | 104.24.106.14:80 | www.aaabagsonsale.top | Cloudflare Inc | US | shared |
2816 | iexplore.exe | 104.24.106.14:80 | www.aaabagsonsale.top | Cloudflare Inc | US | shared |
2816 | iexplore.exe | 220.242.182.12:443 | js.users.51.la | — | CN | suspicious |
2816 | iexplore.exe | 172.217.16.163:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3112 | iexplore.exe | 151.101.2.133:80 | ocsp.globalsign.com | Fastly | US | malicious |
3112 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3112 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2816 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.aaabagsonsale.top |
| suspicious |
fonts.googleapis.com |
| whitelisted |
js.users.51.la |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2816 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2340 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2340 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |