| URL: | http://www.intercall.com/downloads/rpvoip.exe |
| Full analysis: | https://app.any.run/tasks/a0d8f9e7-2a85-4404-bf03-9c83bf4c9dad |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 17:28:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 82CD4A737388042C0BF02CAFDFC1FE5A |
| SHA1: | D10CC4B40A69C2F6D7254FD5A1091A6CDB0BA792 |
| SHA256: | 583C20F5BBEEEEB9D1F51CEAA3C66EDDC4982FF32305A43731EE65BDBACB5983 |
| SSDEEP: | 3:N1KJS4KAWEJJyWKXKvLN:Cc4KADJgavLN |
MALICIOUS
Application was dropped or rewritten from another process
- rpvoip.exe (PID: 2820)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3180)
- chrome.exe (PID: 748)
- MSIEXEC.EXE (PID: 3396)
- MsiExec.exe (PID: 2832)
- MsiExec.exe (PID: 3688)
- msiexec.exe (PID: 1448)
Starts Microsoft Installer
- rpvoip.exe (PID: 2820)
Executed as Windows Service
- vssvc.exe (PID: 4080)
Creates files in the user directory
- msiexec.exe (PID: 1448)
INFO
Application launched itself
- chrome.exe (PID: 3180)
- msiexec.exe (PID: 1448)
Changes settings of System certificates
- chrome.exe (PID: 748)
Reads the hosts file
- chrome.exe (PID: 748)
- chrome.exe (PID: 3180)
Reads Internet Cache Settings
- chrome.exe (PID: 3180)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2832)
- MsiExec.exe (PID: 3688)
Low-level read access rights to disk partition
- vssvc.exe (PID: 4080)
Searches for installed software
- msiexec.exe (PID: 1448)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 1448)
Creates a software uninstall entry
- msiexec.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
17
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15231925521241277008,5258403385994562291,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=4896266907490281201 --mojo-platform-channel-handle=1604 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1448 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15231925521241277008,5258403385994562291,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16376585643463642196 --mojo-platform-channel-handle=2956 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1892 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15231925521241277008,5258403385994562291,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8830483744888082118 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2252 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6d90a9d0,0x6d90a9e0,0x6d90a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15231925521241277008,5258403385994562291,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10583328845366766343 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2452 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15231925521241277008,5258403385994562291,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=1924389030030668101 --mojo-platform-channel-handle=1044 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
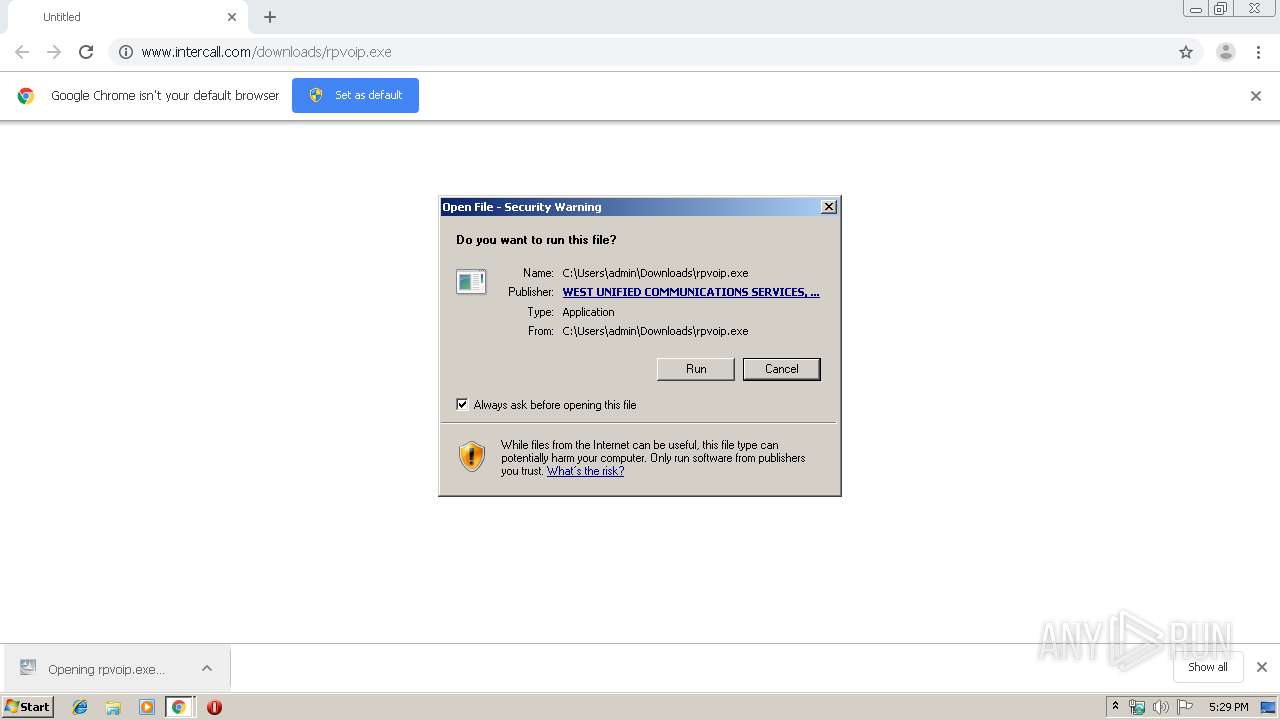
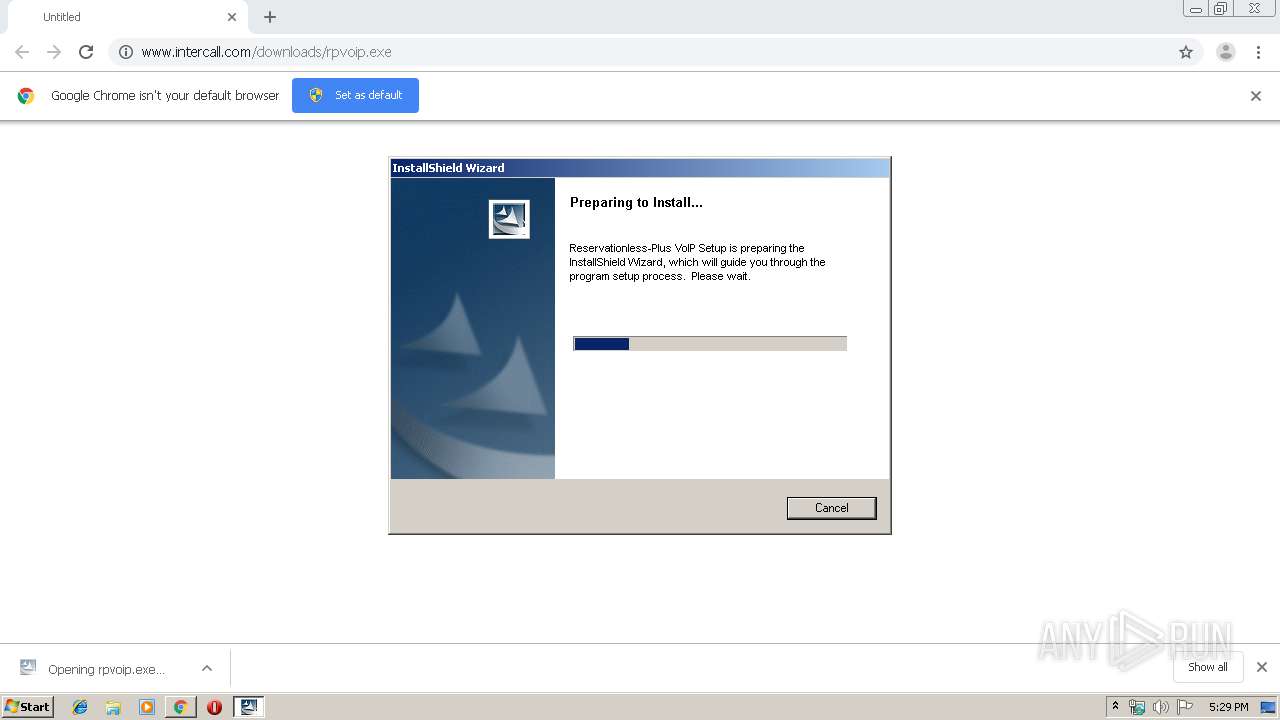
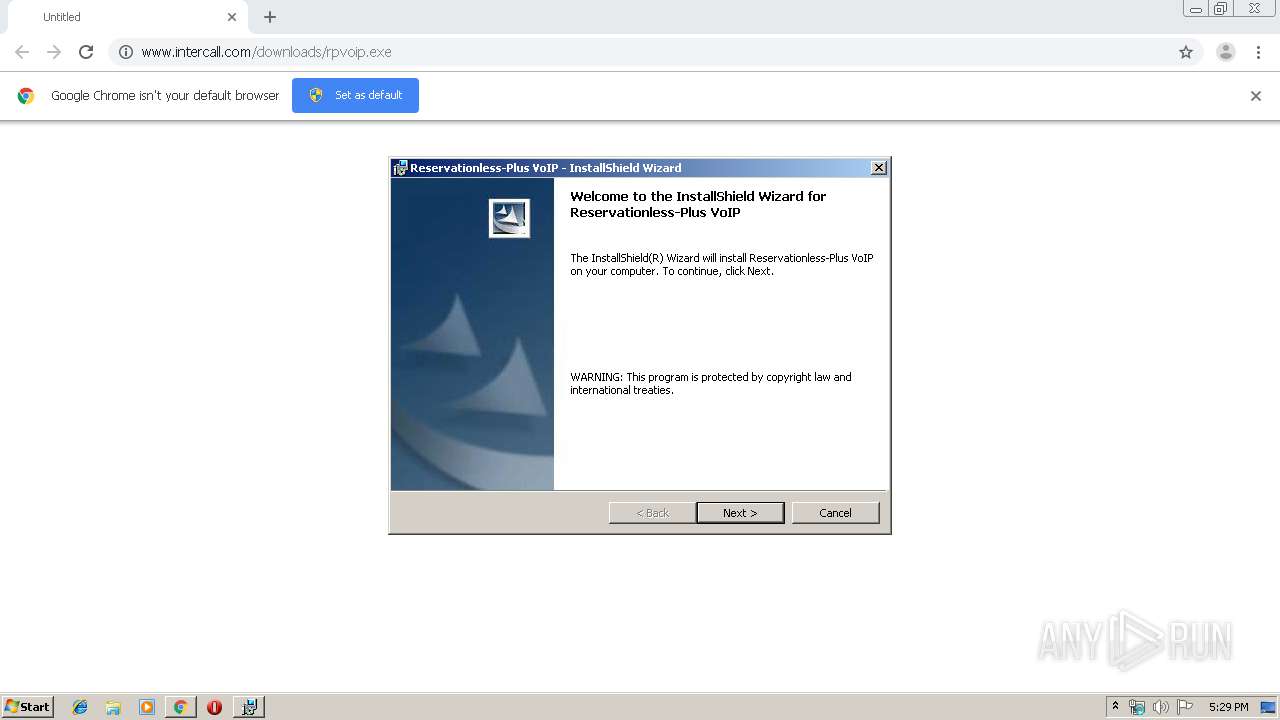
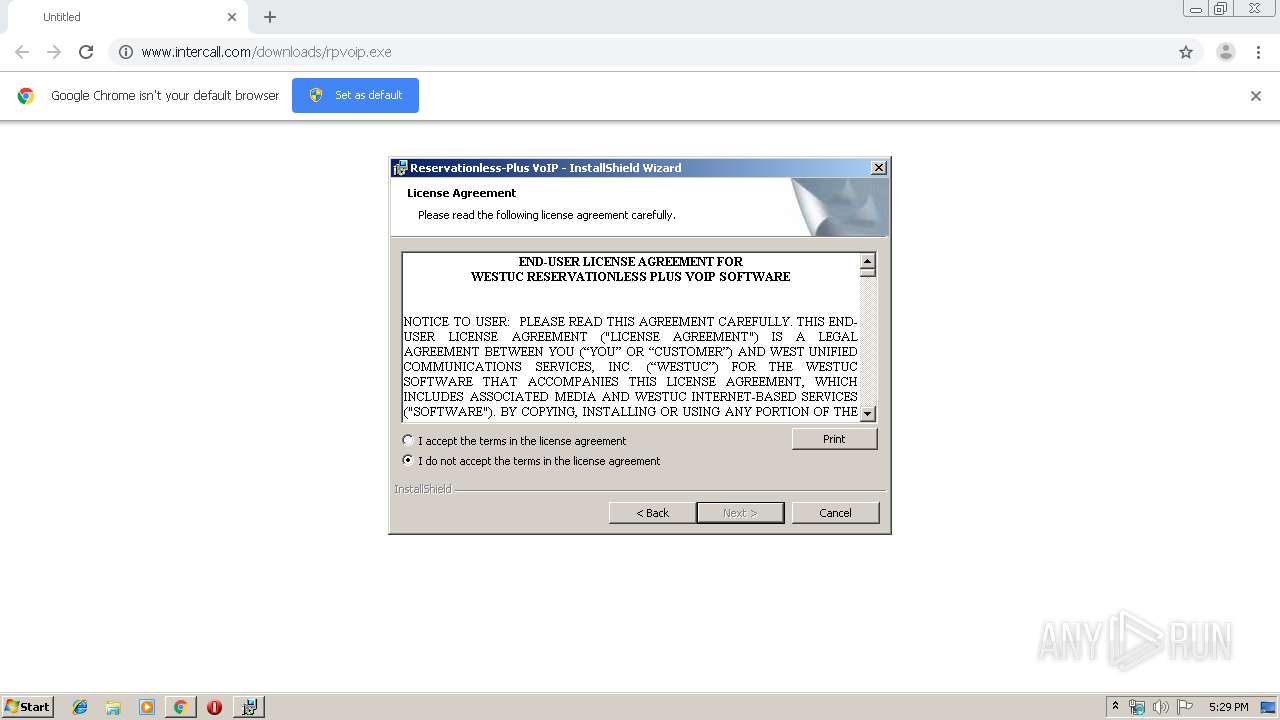
| 2820 | "C:\Users\admin\Downloads\rpvoip.exe" | C:\Users\admin\Downloads\rpvoip.exe | — | chrome.exe | |||||||||||
User: admin Company: InterCall, Inc. Integrity Level: MEDIUM Description: Setup Launcher Exit code: 0 Version: 5.19.07.004 Modules
| |||||||||||||||
| 2832 | C:\Windows\system32\MsiExec.exe -Embedding CFFC3C8C46DBC71BD9B691A55129BB59 C | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 767
Read events
1 438
Write events
312
Delete events
17
Modification events
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1944) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3180-13217707736159500 |
Value: 259 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (3180) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
20
Suspicious files
22
Text files
119
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\752fccca-14ef-4cdb-837c-aa50f7c953f2.tmp | — | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3180 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
748 | chrome.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
748 | chrome.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 172.217.18.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 75.78.2.253:443 | fh1.westuc.com | West Corporation | US | unknown |
748 | chrome.exe | 91.199.212.52:80 | crt.usertrust.com | Comodo CA Ltd | GB | suspicious |
748 | chrome.exe | 216.58.205.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 172.217.18.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 172.217.21.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 172.217.16.142:443 | clients4.google.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 172.217.21.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
748 | chrome.exe | 66.151.27.34:80 | www.intercall.com | Internap Network Services Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.intercall.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
shop.west.com |
| unknown |
fh1.westuc.com |
| unknown |
www.google.com |
| malicious |
crt.usertrust.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients4.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |