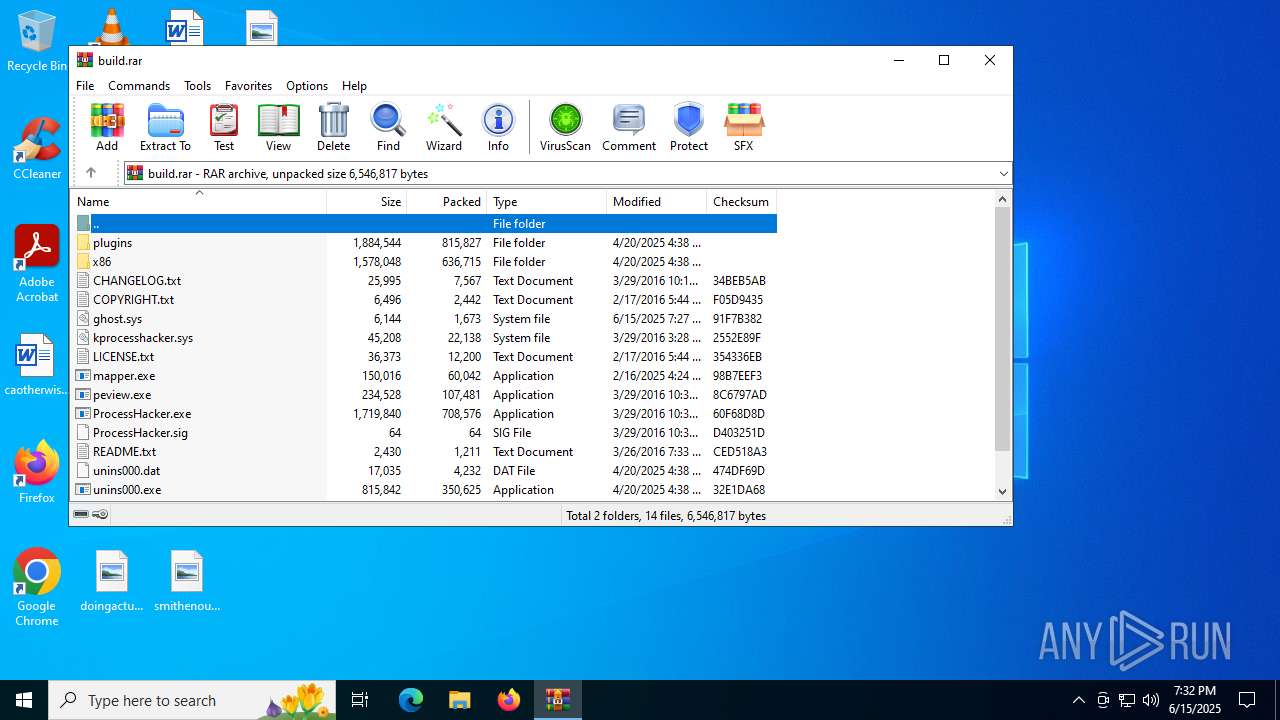
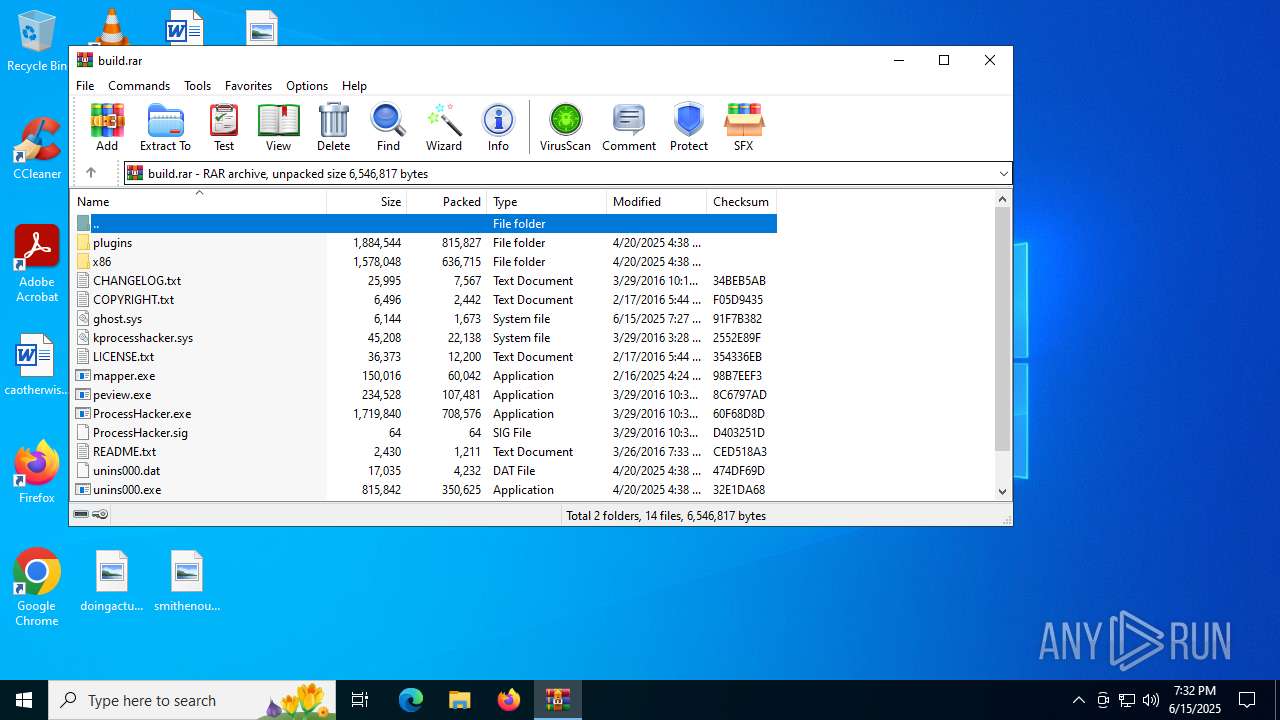
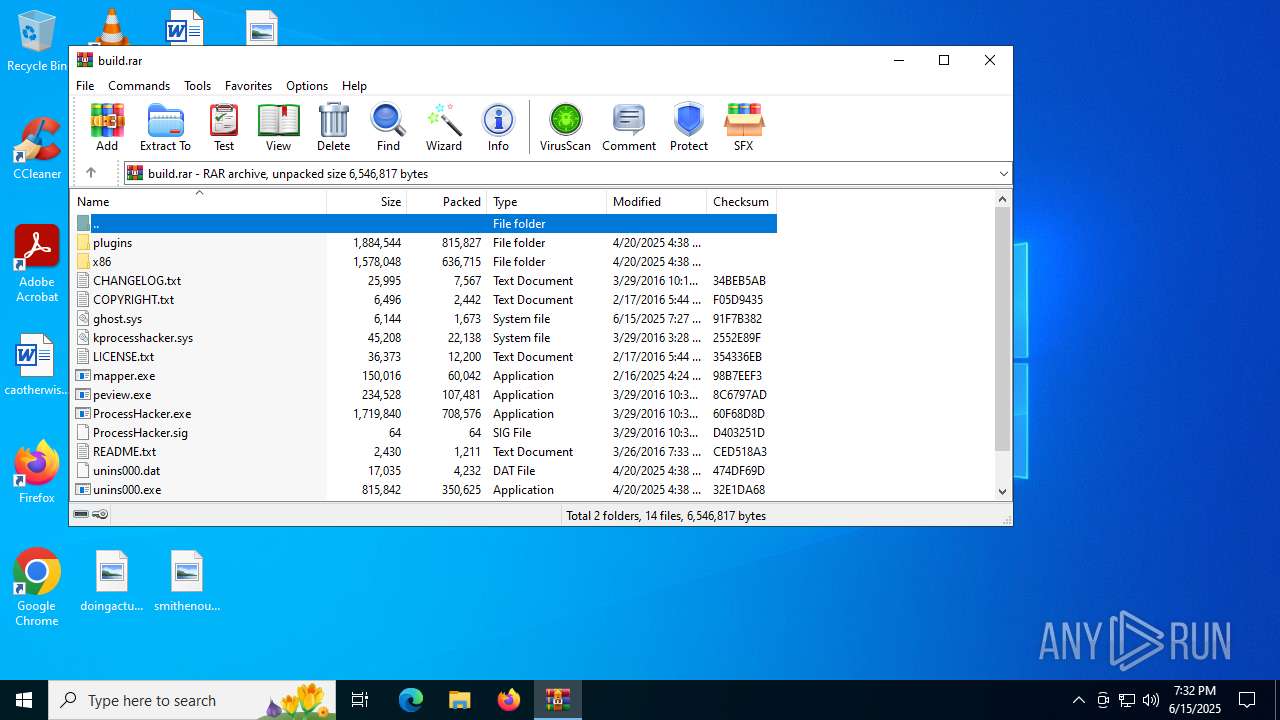
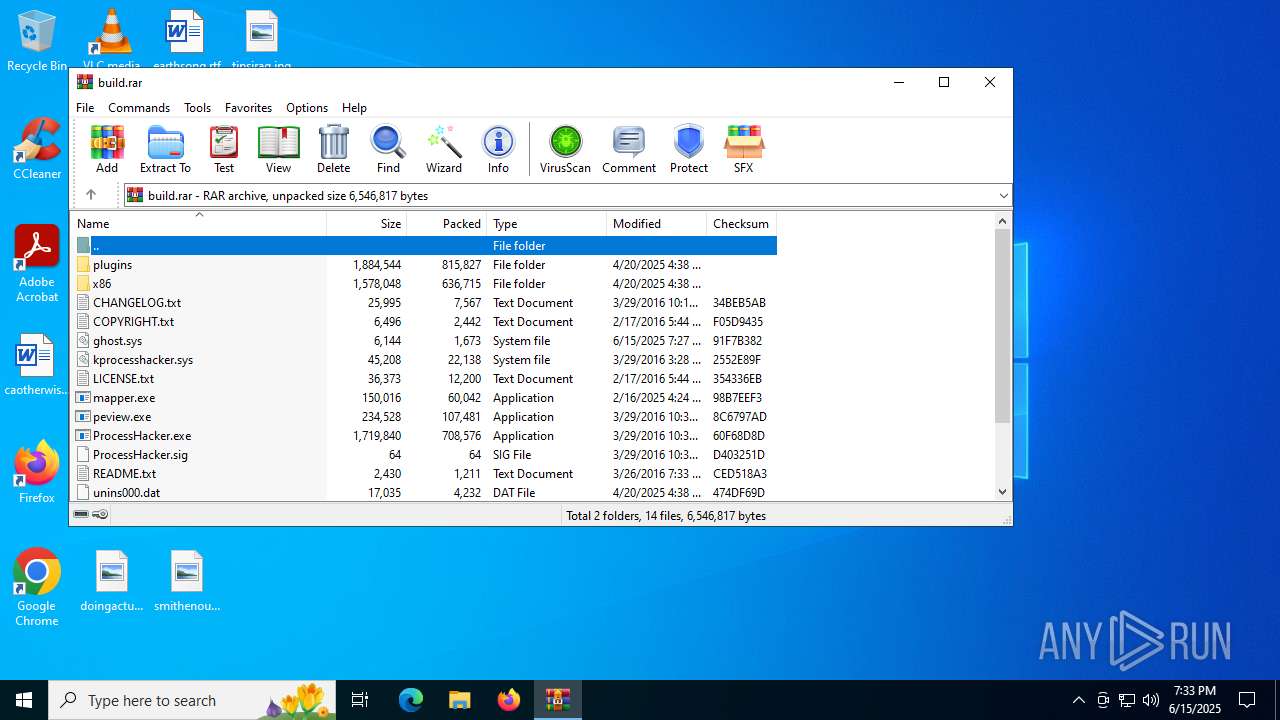
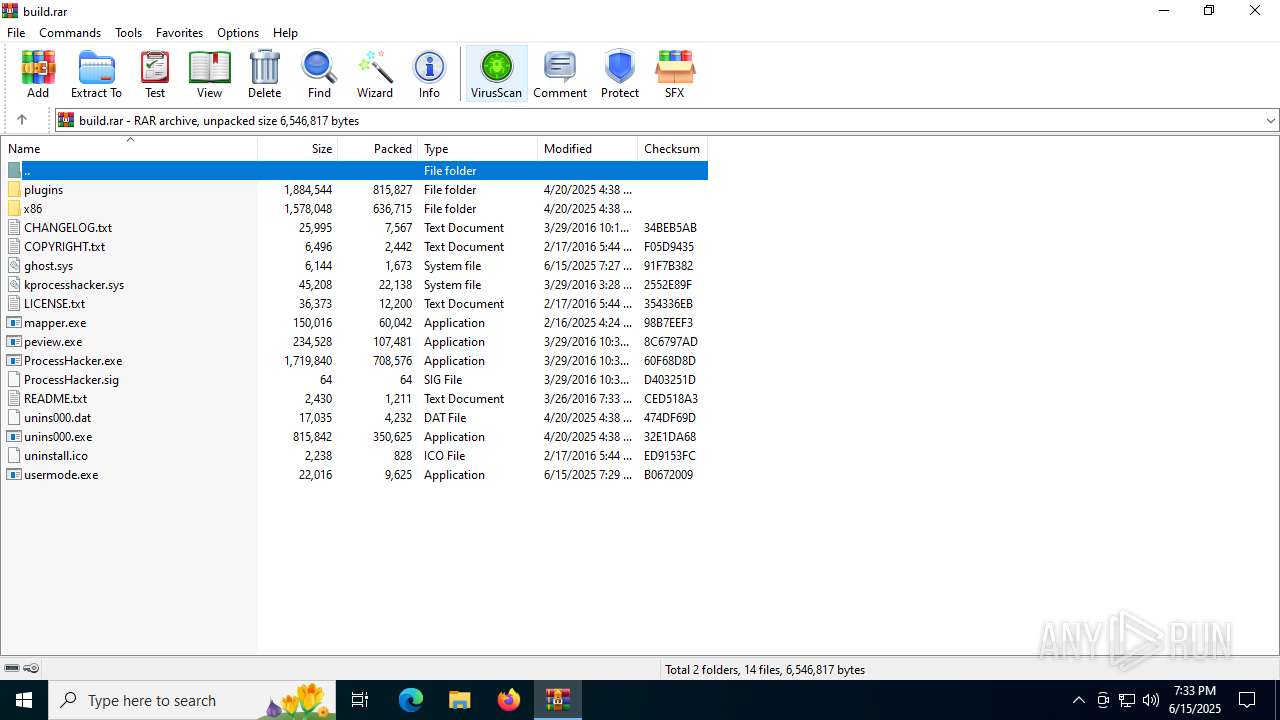
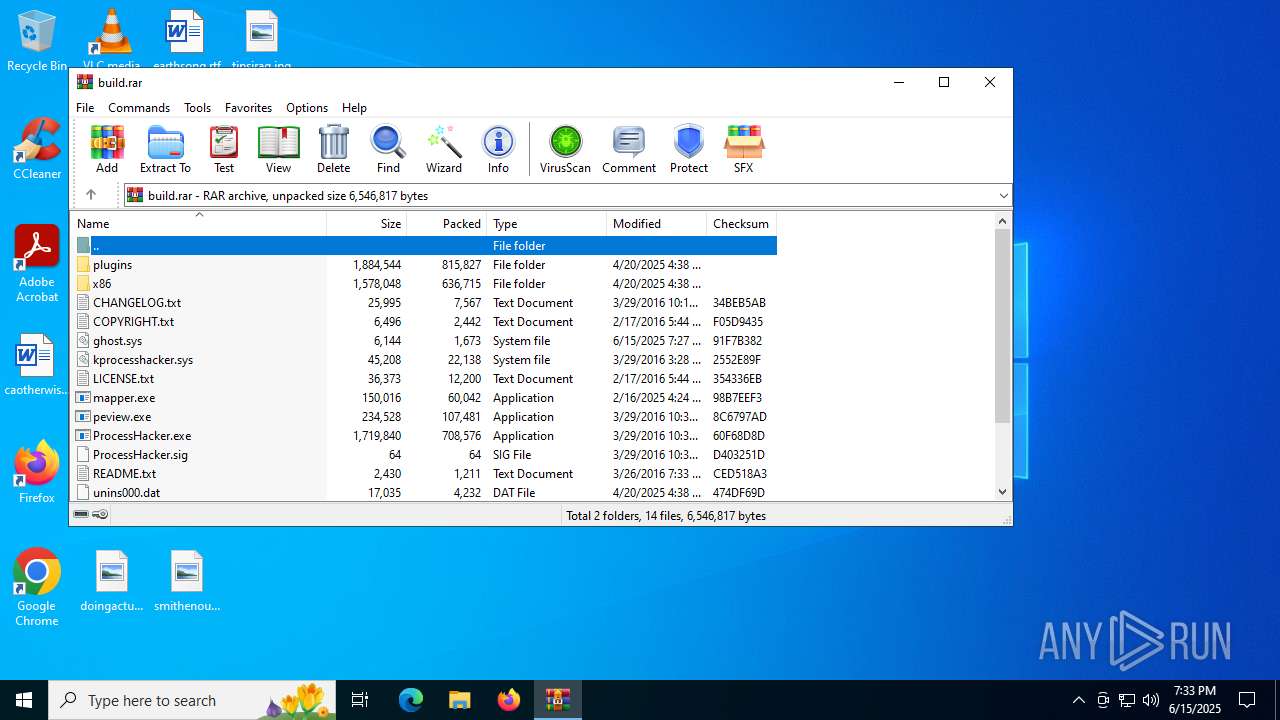
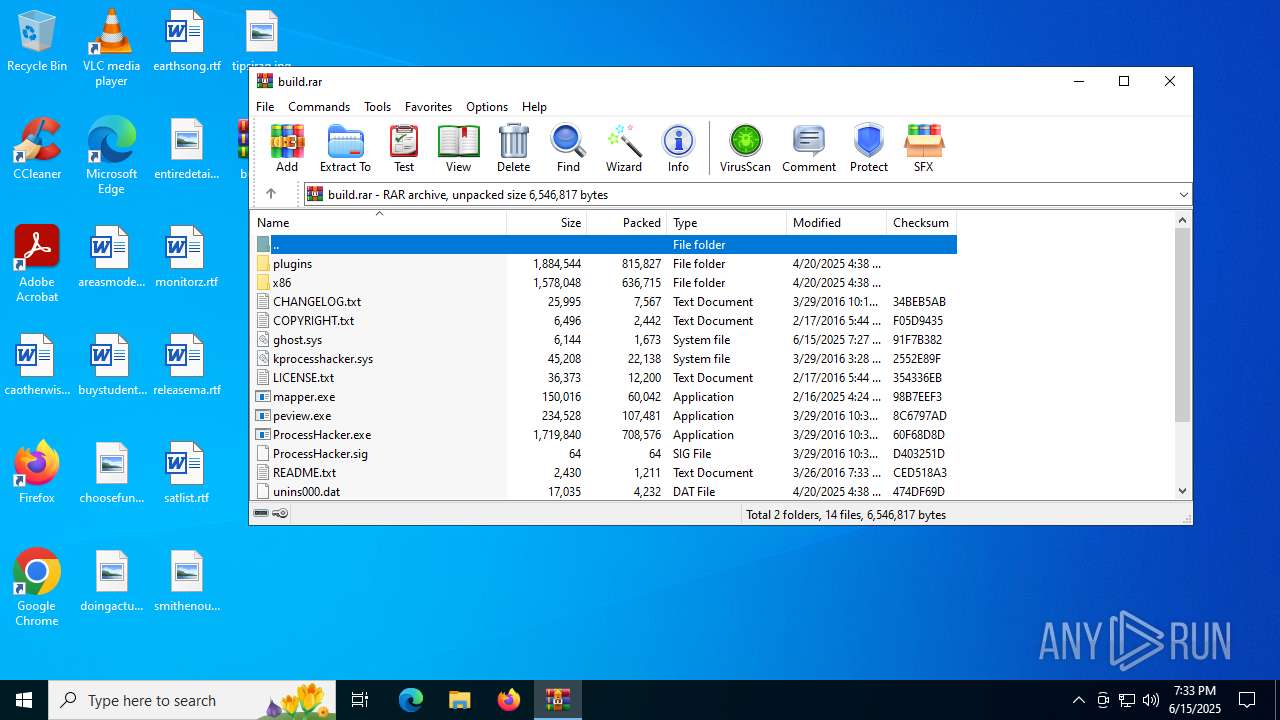
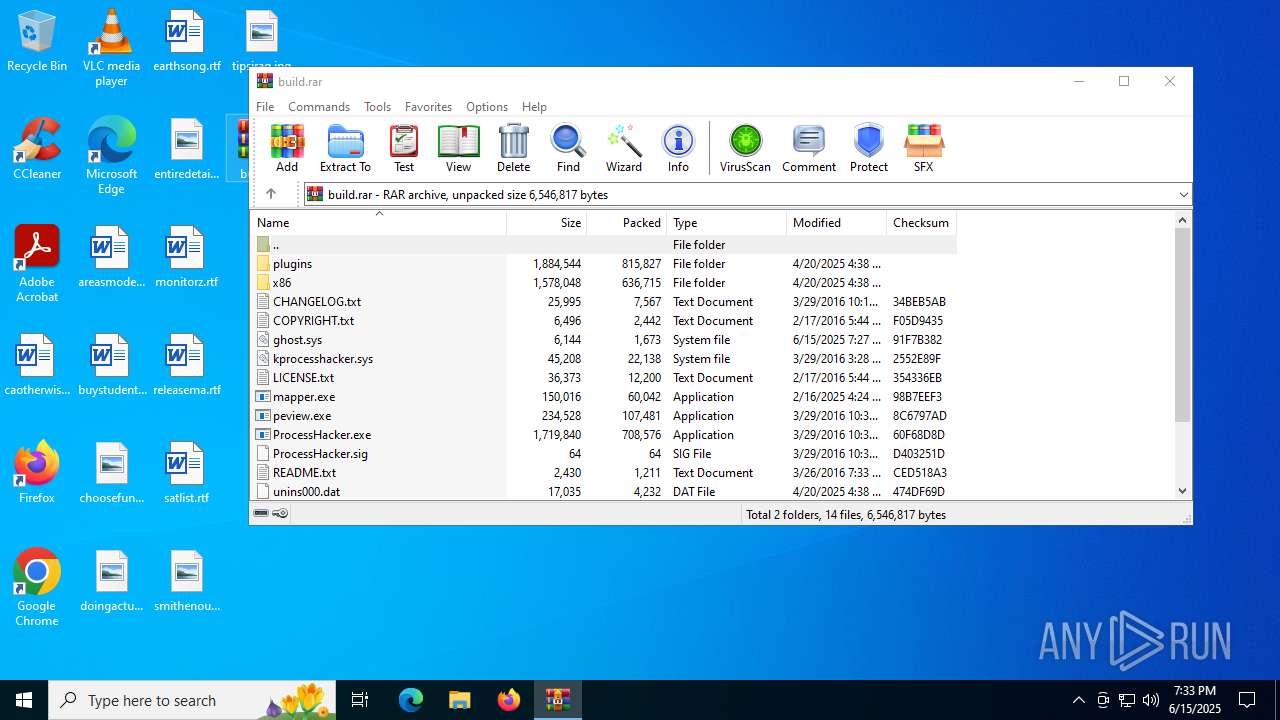
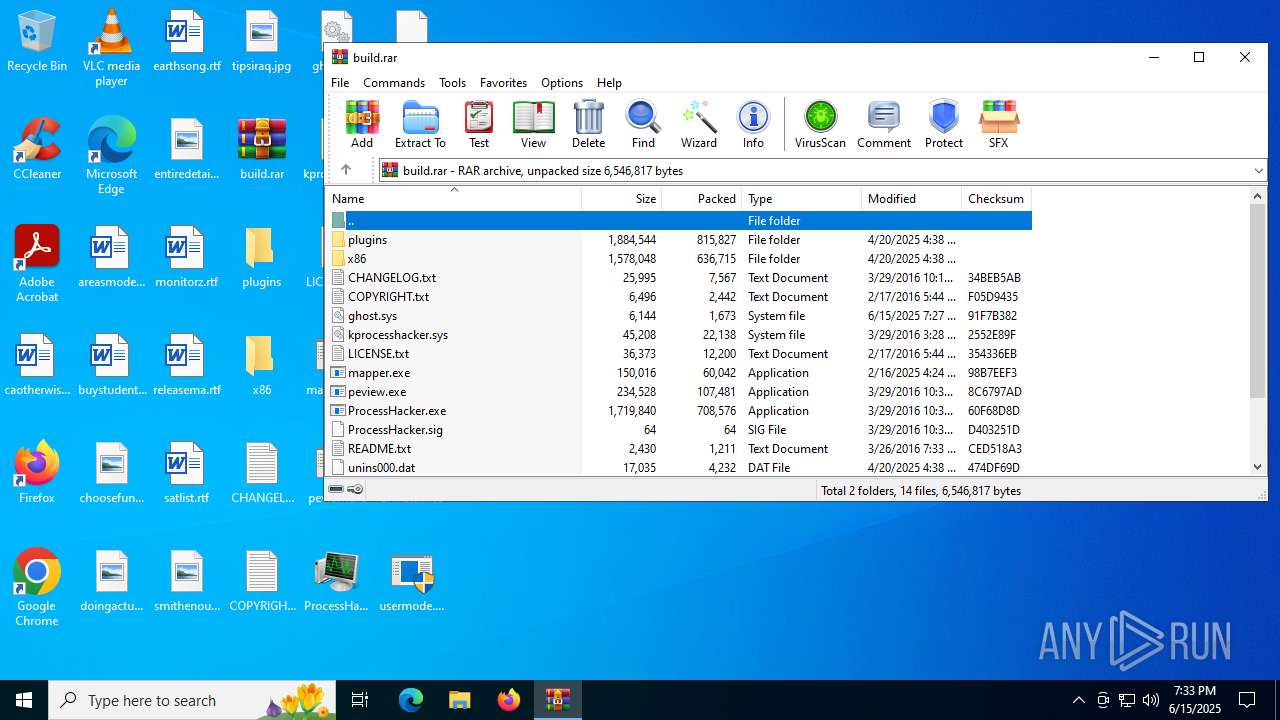
| File name: | build.rar |
| Full analysis: | https://app.any.run/tasks/35a2f5e1-c987-43c7-a2ea-5529cd544605 |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2025, 19:32:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 646C74E14EE2681928ADA0054C41A608 |
| SHA1: | 26DE912D20D2FDC714993BFB76DF86256BEB4E3E |
| SHA256: | 58289AE3A3B3A83E8DE66109389261C62AE6F058387B91F3731F6016E36A295A |
| SSDEEP: | 98304:aE48SS7Djy0tUQD1Xvx4Q6wUukhScEAj3W/8ncAA44gy+SSx93aLQ7e//B/N9eTi:N9Mu |
MALICIOUS
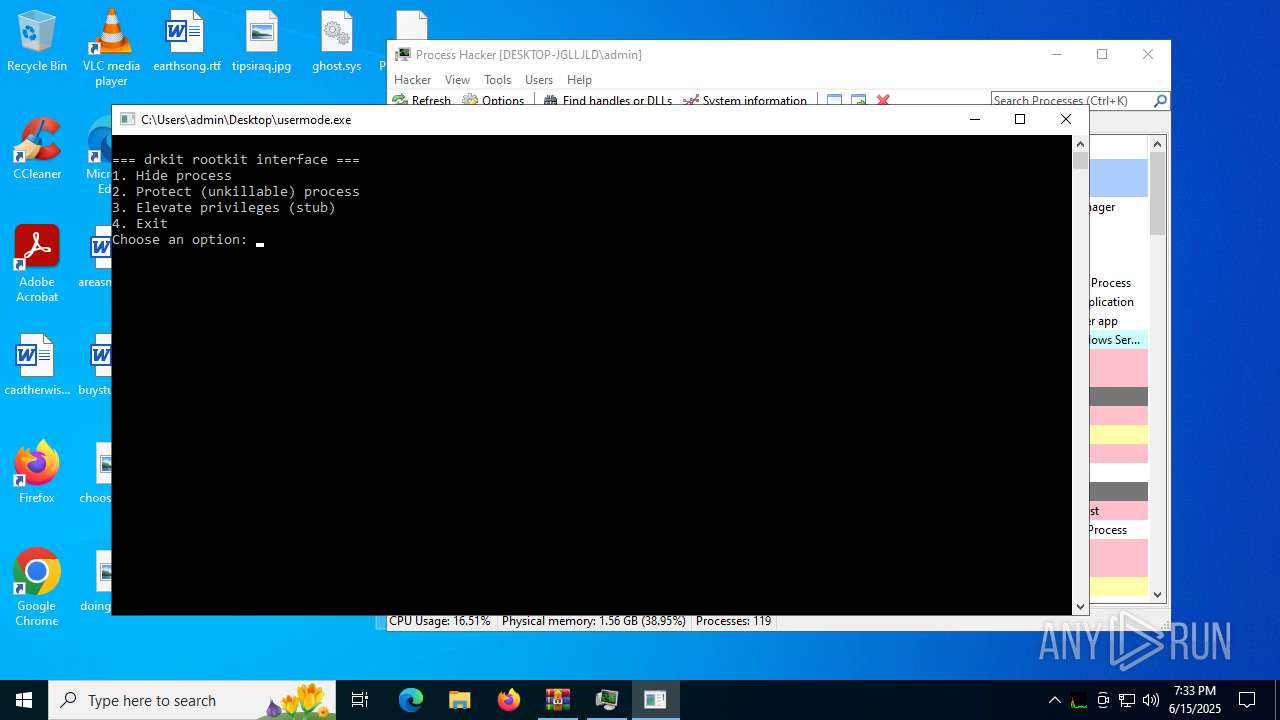
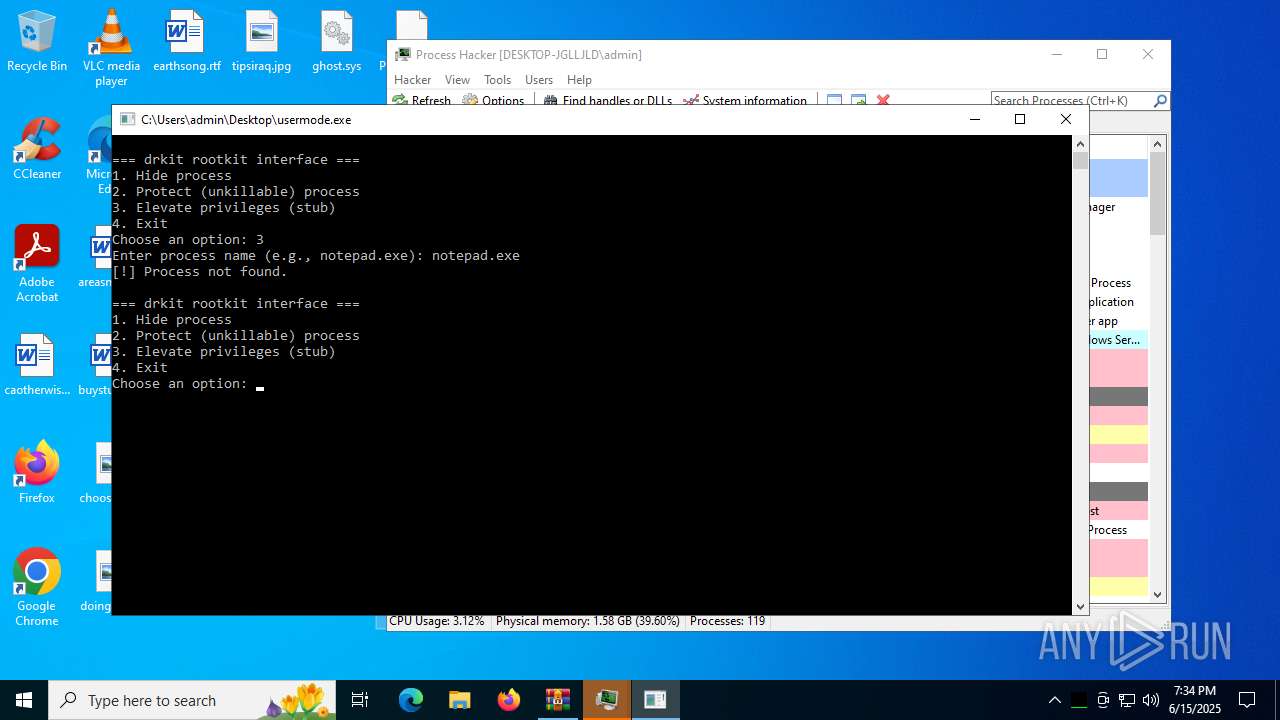
Vulnerable driver has been detected
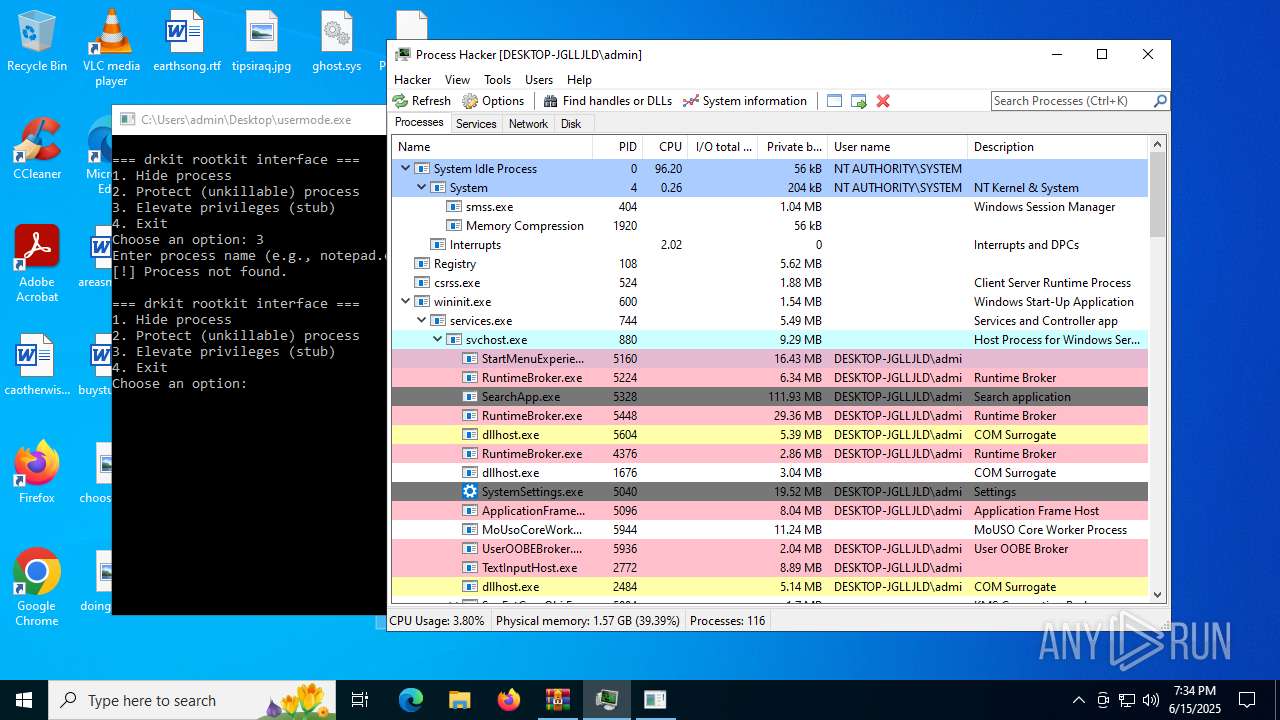
- WinRAR.exe (PID: 3888)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3888)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3888)
Reads security settings of Internet Explorer
- ProcessHacker.exe (PID: 416)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3888)
Manual execution by a user
- ProcessHacker.exe (PID: 416)
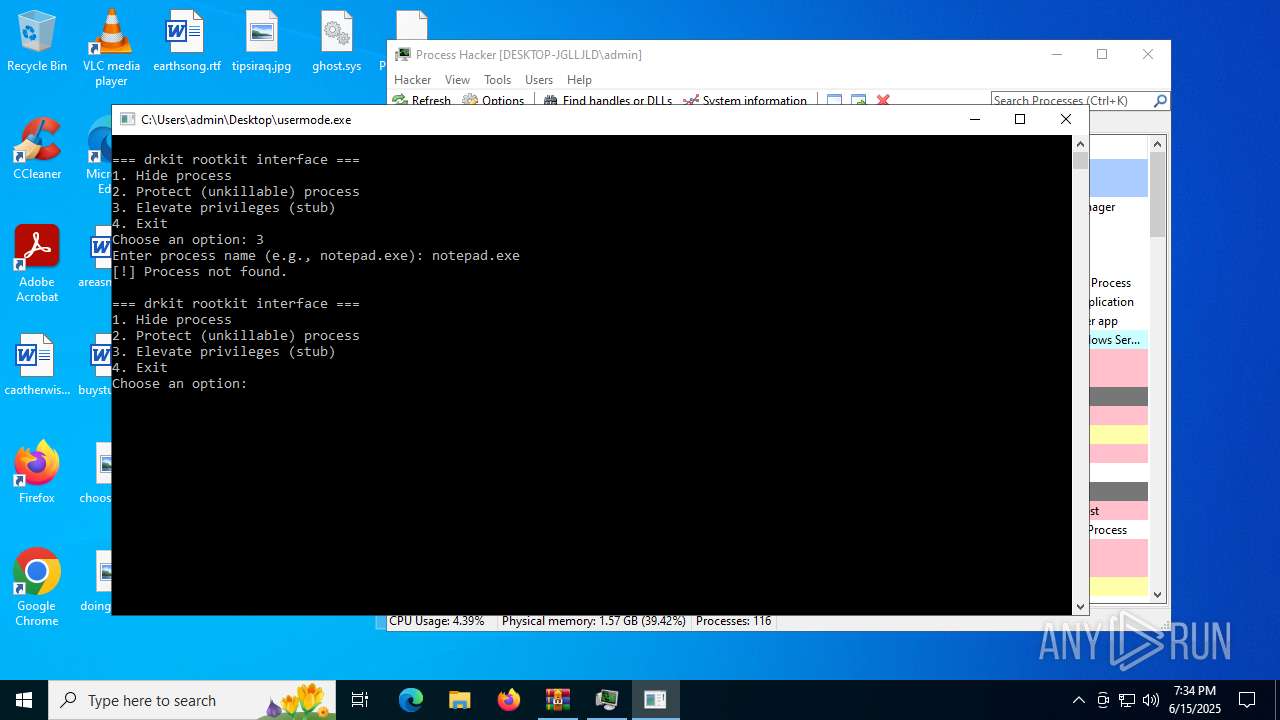
- usermode.exe (PID: 3836)
- usermode.exe (PID: 4836)
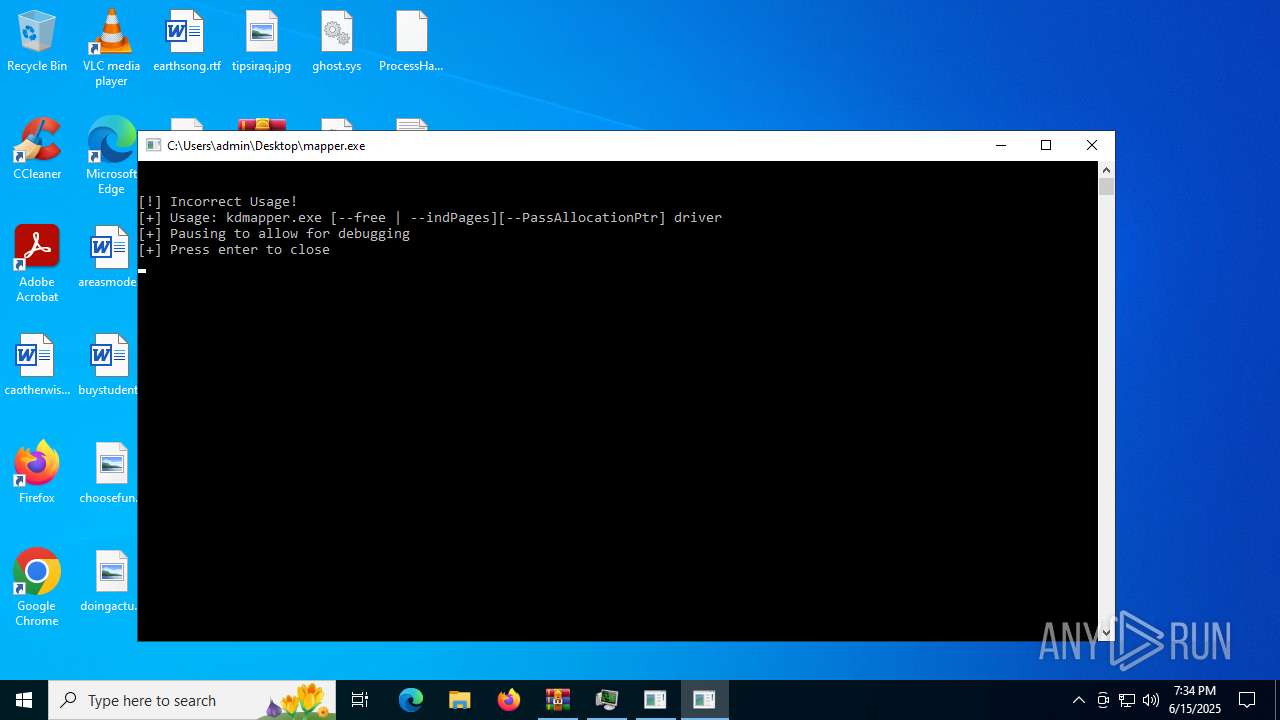
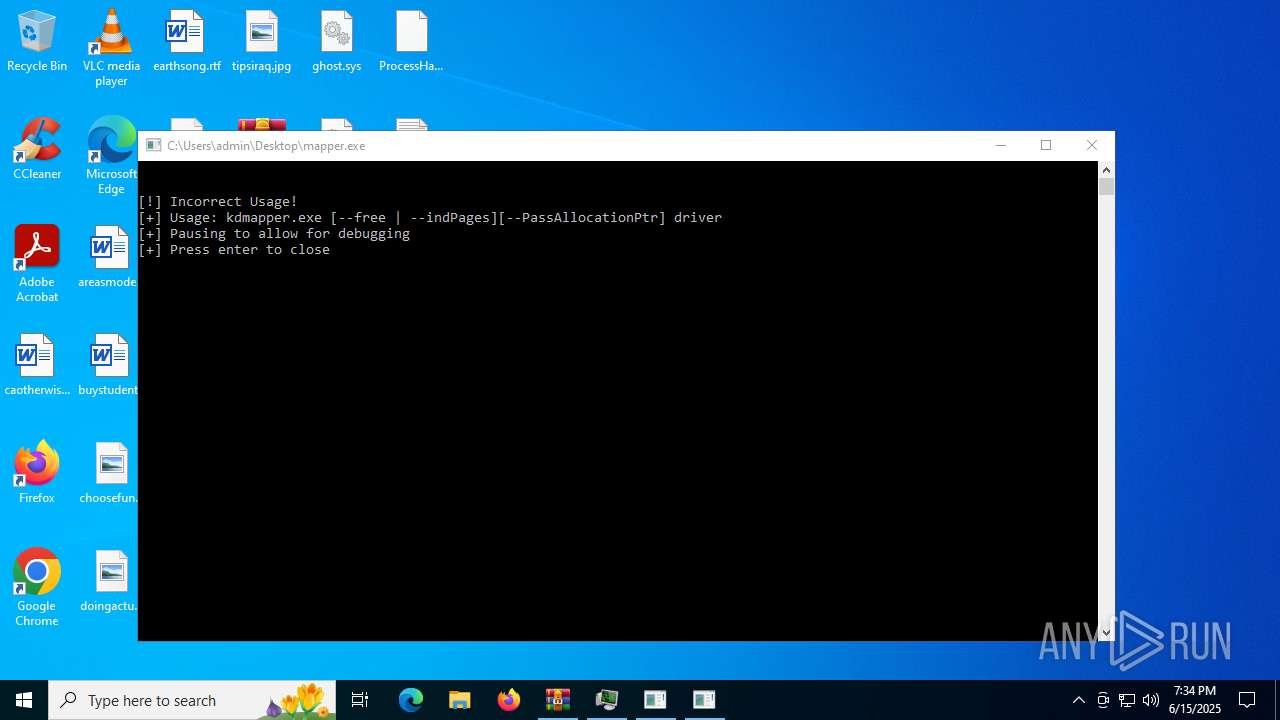
- mapper.exe (PID: 4040)
- mapper.exe (PID: 3800)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 416)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3888)
Reads the computer name
- ProcessHacker.exe (PID: 416)
Reads the software policy settings
- ProcessHacker.exe (PID: 416)
- slui.exe (PID: 2428)
Checks supported languages
- ProcessHacker.exe (PID: 416)
- usermode.exe (PID: 3836)
- mapper.exe (PID: 3800)
Reads Environment values
- ProcessHacker.exe (PID: 416)
Checks proxy server information
- ProcessHacker.exe (PID: 416)
- slui.exe (PID: 2428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1673 |
| UncompressedSize: | 6144 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | ghost.sys |
Total processes
144
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Users\admin\Desktop\ProcessHacker.exe" | C:\Users\admin\Desktop\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Version: 2.39.0.124 Modules
| |||||||||||||||
| 2280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | usermode.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3800 | "C:\Users\admin\Desktop\mapper.exe" | C:\Users\admin\Desktop\mapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 3836 | "C:\Users\admin\Desktop\usermode.exe" | C:\Users\admin\Desktop\usermode.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3888 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\build.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\Desktop\mapper.exe" | C:\Users\admin\Desktop\mapper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4836 | "C:\Users\admin\Desktop\usermode.exe" | C:\Users\admin\Desktop\usermode.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
7 800
Read events
7 776
Write events
11
Delete events
13
Modification events
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\build.rar | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
21
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\ProcessHacker.sig | binary | |
MD5:2CCB4420D40893846E1F88A2E82834DA | SHA256:519C2C2CA0CAF00DB5B3EB2B79DFE42E6128161C13AEB4B4D8B86FBFFC67E3D4 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\x86\ProcessHacker.exe | executable | |
MD5:68F9B52895F4D34E74112F3129B3B00D | SHA256:D4A0FE56316A2C45B9BA9AC1005363309A3EDC7ACF9E4DF64D326A0FF273E80F | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\README.txt | text | |
MD5:72AC5A8DD6491E525B9783C9BC439FE6 | SHA256:0C4F051675A690EA4DB6AB2EB81FDCED6990E2538AD21DC4610AA5925253A090 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\uninstall.ico | image | |
MD5:D9BAFDD7E880B6B7D5C5944E0BEAFB4E | SHA256:B22118C3159D96C061E3E6F668CB26F0C679BB96FCCD2C788584D3E2A64C4C35 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\ProcessHacker.exe | executable | |
MD5:B365AF317AE730A67C936F21432B9C71 | SHA256:BD2C2CF0631D881ED382817AFCCE2B093F4E412FFB170A719E2762F250ABFEA4 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\unins000.exe | executable | |
MD5:43EA49877A2A1508BA733E41C874E16E | SHA256:E7C1D4C07728671C3B28295C863BBE681F962196C8A974EB4B3003540338AA04 | |||
| 3888 | WinRAR.exe | C:\Users\admin\Desktop\plugins\ExtendedServices.dll | executable | |
MD5:4858BDB7731BF0B46B247A1F01F4A282 | SHA256:5AE7C0972FD4E4C4AE14C0103602CA854377FEFCBCCD86FA68CFC5A6D1F99F60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1356 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1356 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
416 | ProcessHacker.exe | GET | 301 | 104.18.12.149:80 | http://processhacker.sourceforge.net/update.php | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.19.105.127:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3964 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1356 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1356 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
wj32.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |