| File name: | 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe |
| Full analysis: | https://app.any.run/tasks/6b3a1529-39f4-441b-a50c-a0227c44a4bb |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | June 16, 2024, 23:57:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2F555468F2B76F26648AE61C418EAD8A |
| SHA1: | 94B1A5F05715682D6BD747C4A8029006490D88D2 |
| SHA256: | 581A31B1DDAA6EEA7B78A57B4615D8DEF8C688AEB0DD38DA8A0EF3D248E88892 |
| SSDEEP: | 98304:eFrKdVVtRGMYiOxJ8lb76qUewzE+WexFr/I5oGkfitcXDPrhXEm8Zd2EjOp9eZsd:ezmQBvwhM |
MALICIOUS
Drops the executable file immediately after the start
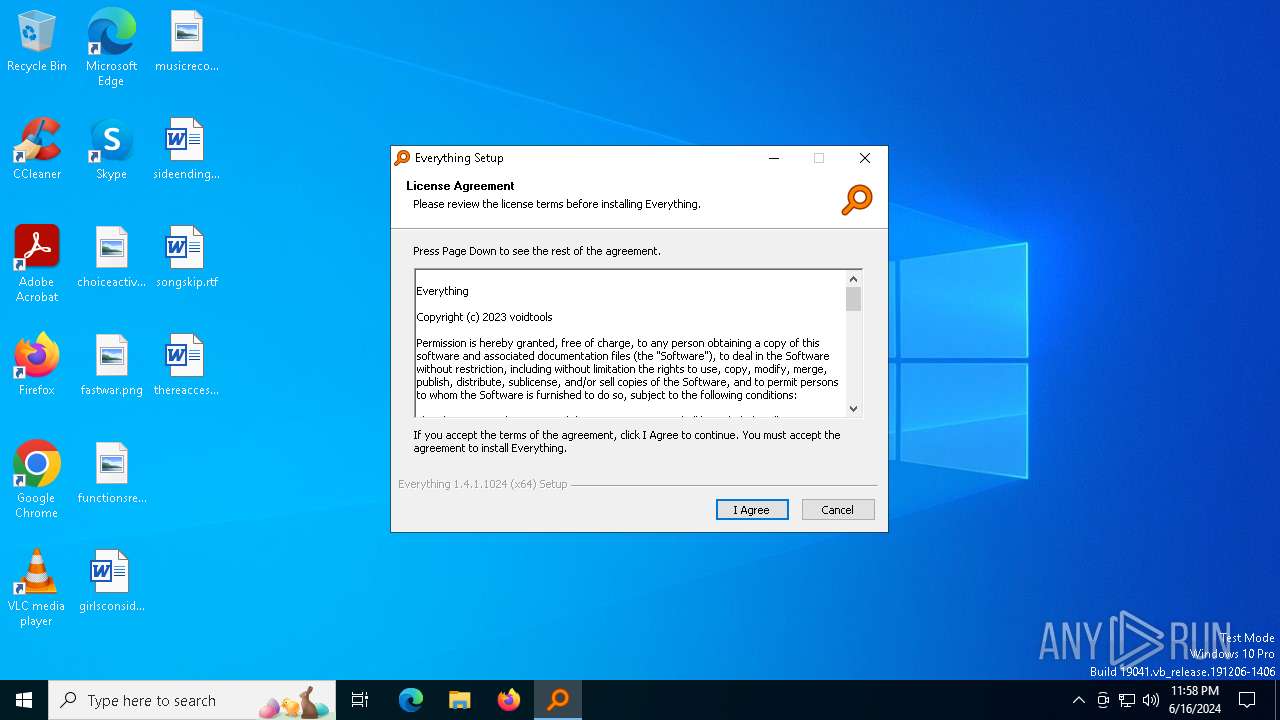
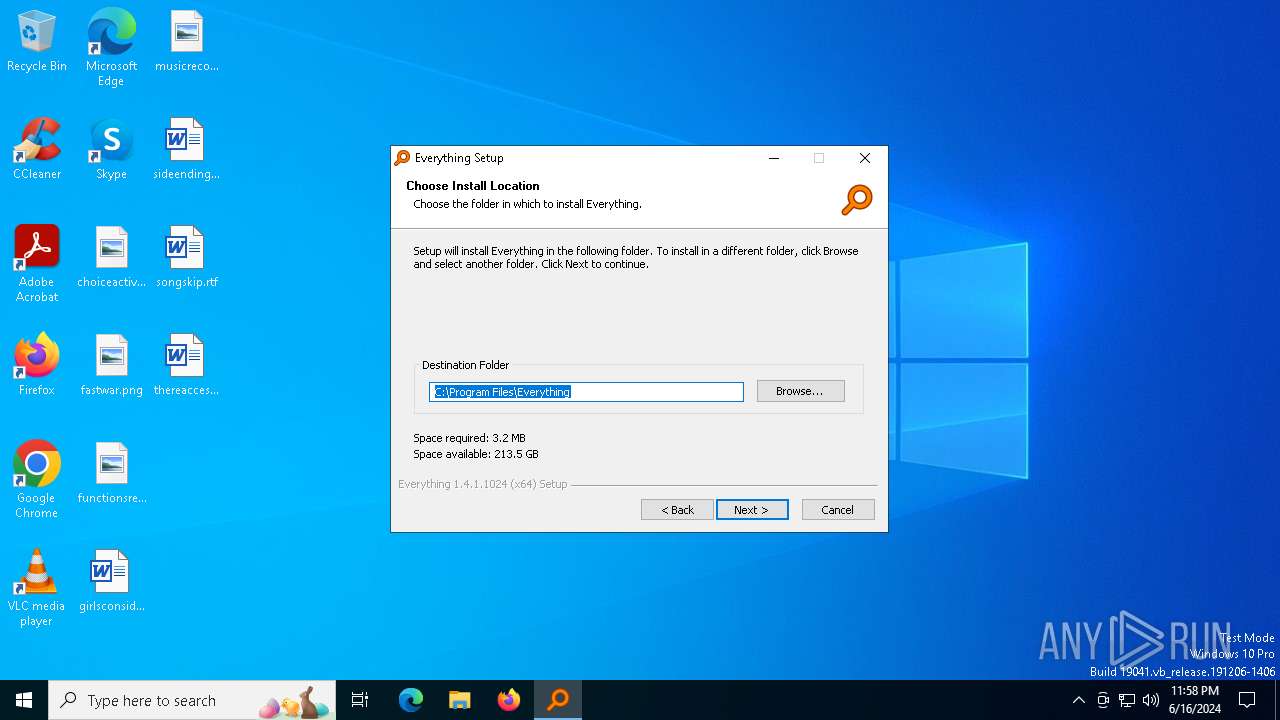
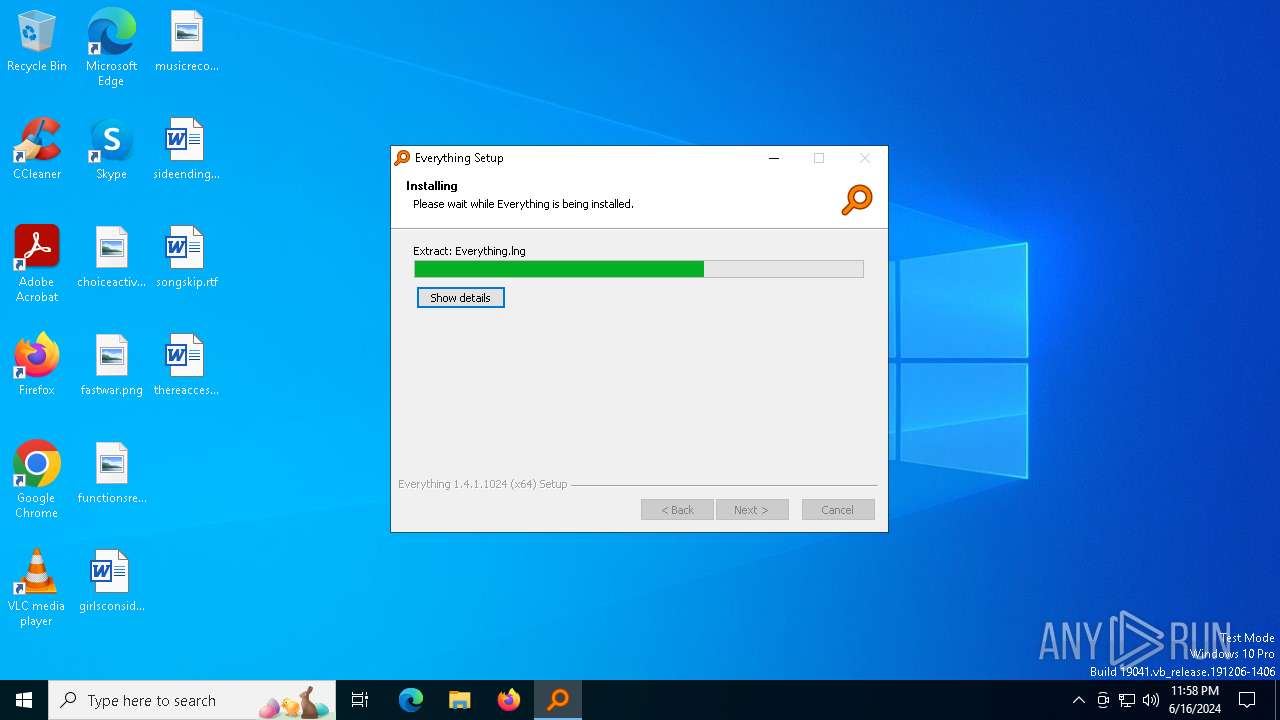
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
- DCRatBuild.exe (PID: 2332)
- Everything.exe (PID: 5940)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 712)
Changes the autorun value in the registry
- Everything.exe (PID: 5704)
Actions looks like stealing of personal data
- Everything.exe (PID: 5940)
SUSPICIOUS
Reads the date of Windows installation
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- DCRatBuild.exe (PID: 2332)
- Everything.exe (PID: 2288)
- Everything.exe (PID: 5940)
Reads security settings of Internet Explorer
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- DCRatBuild.exe (PID: 2332)
- Everything.exe (PID: 2288)
- Everything.exe (PID: 5940)
Executable content was dropped or overwritten
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
- DCRatBuild.exe (PID: 2332)
- Everything.exe (PID: 5940)
The process creates files with name similar to system file names
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
Executed via WMI
- schtasks.exe (PID: 5944)
- schtasks.exe (PID: 4932)
- schtasks.exe (PID: 5064)
- schtasks.exe (PID: 3608)
- schtasks.exe (PID: 3376)
- schtasks.exe (PID: 4216)
- schtasks.exe (PID: 3808)
- schtasks.exe (PID: 2332)
- schtasks.exe (PID: 5940)
- schtasks.exe (PID: 1204)
- schtasks.exe (PID: 5612)
- schtasks.exe (PID: 4380)
- schtasks.exe (PID: 5528)
- schtasks.exe (PID: 428)
- schtasks.exe (PID: 4544)
- schtasks.exe (PID: 3688)
- schtasks.exe (PID: 928)
- schtasks.exe (PID: 5504)
Executing commands from a ".bat" file
- wscript.exe (PID: 712)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 712)
Malware-specific behavior (creating "System.dll" in Temp)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 1012)
The executable file from the user directory is run by the CMD process
- UsoClient.exe (PID: 3376)
Application launched itself
- Everything.exe (PID: 2288)
Creates a software uninstall entry
- Everything.exe (PID: 5940)
Starts itself from another location
- Everything.exe (PID: 5940)
Executes as Windows Service
- Everything.exe (PID: 2280)
INFO
Checks supported languages
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- DCRatBuild.exe (PID: 2332)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
- UsoClient.exe (PID: 3376)
- Everything.exe (PID: 2288)
- Everything.exe (PID: 5940)
- Everything.exe (PID: 5704)
- Everything.exe (PID: 2280)
- Everything.exe (PID: 2332)
- Everything.exe (PID: 5940)
Reads the computer name
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- DCRatBuild.exe (PID: 2332)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
- Everything.exe (PID: 2288)
- UsoClient.exe (PID: 3376)
- Everything.exe (PID: 5704)
- Everything.exe (PID: 5940)
- Everything.exe (PID: 2280)
- Everything.exe (PID: 5940)
- Everything.exe (PID: 2332)
Create files in a temporary directory
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- Everything-1.4.1.1024.x64-Setup.exe (PID: 3712)
Process checks computer location settings
- 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe (PID: 4360)
- DCRatBuild.exe (PID: 2332)
- Everything.exe (PID: 2288)
- Everything.exe (PID: 5940)
Reads the machine GUID from the registry
- UsoClient.exe (PID: 3376)
Reads Environment values
- UsoClient.exe (PID: 3376)
Creates files in the program directory
- Everything.exe (PID: 5704)
- Everything.exe (PID: 5940)
Checks proxy server information
- UsoClient.exe (PID: 3376)
Disables trace logs
- UsoClient.exe (PID: 3376)
Creates files or folders in the user directory
- Everything.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (53.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (17.5) |
| .scr | | | Windows screen saver (16.1) |
| .exe | | | Win32 Executable (generic) (5.5) |
| .exe | | | Win16/32 Executable Delphi generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 5120 |
| InitializedDataSize: | 3182592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
157
Monitored processes
34
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 428 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 13 /tr "'C:\Users\Default\Documents\fontdrvhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 712 | "C:\WINDOWS\System32\WScript.exe" "C:\comsurrogatecommon\h6khYLQAm3C9Gvan2yaD6Idxz.vbe" | C:\Windows\SysWOW64\wscript.exe | — | DCRatBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 712 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | schtasks.exe /create /tn "sppsvcs" /sc MINUTE /mo 7 /tr "'C:\Users\Default\Pictures\sppsvc.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\pr9LagrNX6.bat" " | C:\Windows\System32\cmd.exe | — | containerbrokerSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | schtasks.exe /create /tn "UsoClientU" /sc MINUTE /mo 10 /tr "'C:\Users\admin\Saved Games\UsoClient.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | C:\WINDOWS\system32\cmd.exe /c ""C:\comsurrogatecommon\ndyJqdcK3gAQnUI3h5cTrzbsXo5.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2280 | "C:\Program Files\Everything\Everything.exe" -svc | C:\Program Files\Everything\Everything.exe | — | services.exe | |||||||||||
User: SYSTEM Company: voidtools Integrity Level: SYSTEM Description: Everything Version: 1.4.1.1024 Modules
| |||||||||||||||
Total events
21 930
Read events
21 836
Write events
91
Delete events
3
Modification events
| (PID) Process: | (4360) 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (4360) 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4360) 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4360) 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4360) 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2332) DCRatBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | VBEFile_.vbe |
Value: 0 | |||
| (PID) Process: | (2332) DCRatBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (2332) DCRatBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2332) DCRatBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2332) DCRatBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
10
Suspicious files
5
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3712 | Everything-1.4.1.1024.x64-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsn49D9.tmp\InstallOptions2.ini | ini | |
MD5:2D388F85F070760E18EC39C0DF0980DB | SHA256:6003368F4183B166539C96B734C01595A9D1B1494C11F16AEDEFE8AD68E9CFA8 | |||
| 2332 | DCRatBuild.exe | C:\comsurrogatecommon\containerbrokerSvc.exe | executable | |
MD5:30F9E0FF5A6F1343D0828E74F8D4D442 | SHA256:88A7DB7AE820D84729CA9D9376848544BDE2788F300D4303FD1B19C50C4C348D | |||
| 3712 | Everything-1.4.1.1024.x64-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsn49D9.tmp\LangDLL.dll | executable | |
MD5:68B287F4067BA013E34A1339AFDB1EA8 | SHA256:18E8B40BA22C7A1687BD16E8D585380BC2773FFF5002D7D67E9485FCC0C51026 | |||
| 3712 | Everything-1.4.1.1024.x64-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsn49D9.tmp\InstallOptions.ini | ini | |
MD5:F4B7EA54A35FE41EB4ABB5F9E53CD9DD | SHA256:B520532CE65105E5414423491084A05EEC67ADD6CA5FEF67B56BB9866C07BB95 | |||
| 2332 | DCRatBuild.exe | C:\comsurrogatecommon\h6khYLQAm3C9Gvan2yaD6Idxz.vbe | vbe | |
MD5:C2CEBB18805A35AA4F1DC912DC6FF0D2 | SHA256:D178FAB8FA489F9F67902F5B777145C321B6F614641C573EDEB2DA8F22127351 | |||
| 3712 | Everything-1.4.1.1024.x64-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsn49D9.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 4360 | 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | C:\Users\admin\AppData\Local\Temp\DCRatBuild.exe | executable | |
MD5:1B0D74D91E3556B4296FDFA8E2026027 | SHA256:8ED1D39FA5617F5F79C94BE770549A88452829B56C7A878AF030BAA1AE060F9B | |||
| 4360 | 581a31b1ddaa6eea7b78a57b4615d8def8c688aeb0dd38da8a0ef3d248e88892.exe | C:\Users\admin\AppData\Local\Temp\Everything-1.4.1.1024.x64-Setup.exe | executable | |
MD5:5036E609163E98F3AC06D5E82B677DF8 | SHA256:B2AFE799584C913532C673F99ADE45113BF5A5B605A964CE9FA837F563B6FC21 | |||
| 2332 | DCRatBuild.exe | C:\comsurrogatecommon\ndyJqdcK3gAQnUI3h5cTrzbsXo5.bat | text | |
MD5:9847E6047E87392038DBD26B21C4DE12 | SHA256:7211497C50C8FFC77A8EF893ECA0CD8A6D39A5ED7CDE524A9EC503758D0C4715 | |||
| 3712 | Everything-1.4.1.1024.x64-Setup.exe | C:\Users\admin\AppData\Local\Temp\nsn49D9.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
54
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1104 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3376 | UsoClient.exe | GET | 400 | 141.8.197.42:80 | http://a0986288.xsph.ru/a32875a6.php?A7ZUpyl1cxRcUhTS=wXjtE1IyZBYxYPCkh4iMX9I&057293214dd1e1c8ca29d6306d5eecdb=3fef7bfc090daea77e647b5c9726d235&7966bddc4cb0c27e99e46630873ba211=gMxQjY2YTO3YGNhVGNiZWOycDO1UDOzUTYlFjNkFGN0UTMycjNldTO&A7ZUpyl1cxRcUhTS=wXjtE1IyZBYxYPCkh4iMX9I | unknown | — | — | unknown |
3376 | UsoClient.exe | GET | 400 | 141.8.197.42:80 | http://a0986288.xsph.ru/a32875a6.php?A7ZUpyl1cxRcUhTS=wXjtE1IyZBYxYPCkh4iMX9I&057293214dd1e1c8ca29d6306d5eecdb=3fef7bfc090daea77e647b5c9726d235&7966bddc4cb0c27e99e46630873ba211=gMxQjY2YTO3YGNhVGNiZWOycDO1UDOzUTYlFjNkFGN0UTMycjNldTO&A7ZUpyl1cxRcUhTS=wXjtE1IyZBYxYPCkh4iMX9I | unknown | — | — | unknown |
6012 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6012 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2764 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1440 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4312 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4680 | SearchApp.exe | 2.16.100.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
a0986288.xsph.ru |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |
3376 | UsoClient.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |