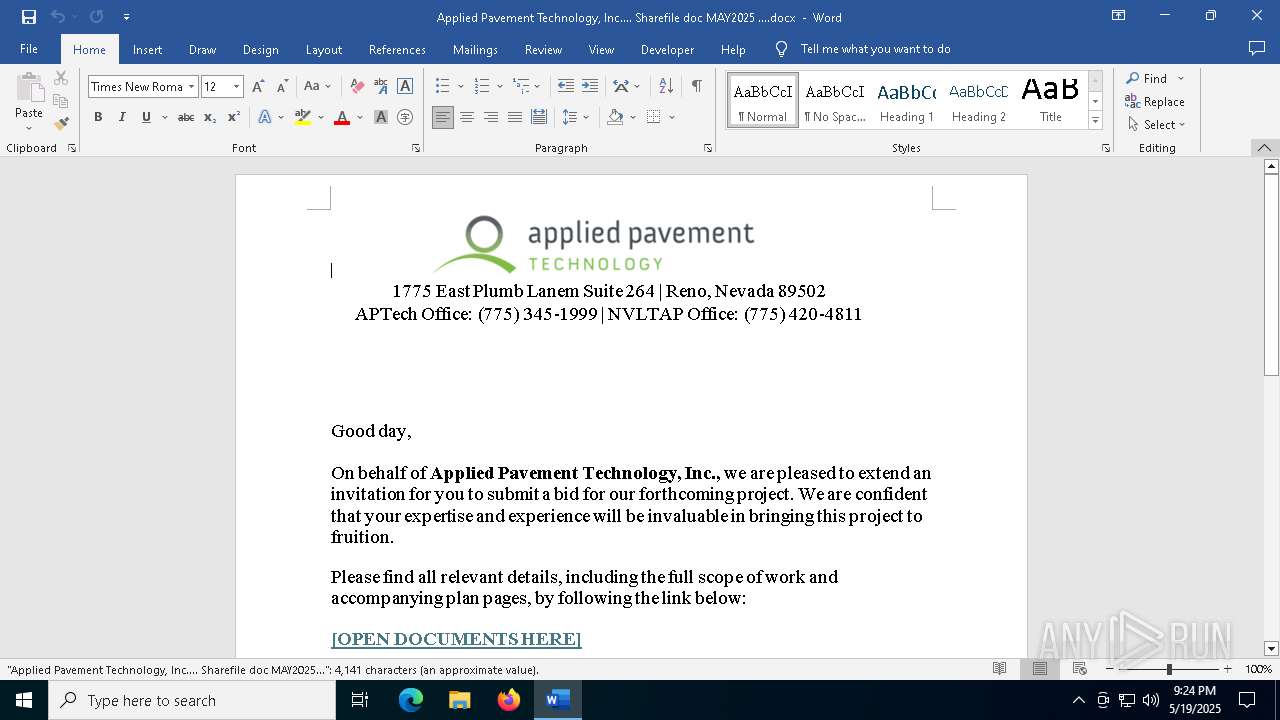
| File name: | Applied Pavement Technology, Inc.... Sharefile doc MAY2025 ....docx |
| Full analysis: | https://app.any.run/tasks/62401802-571b-4a1c-bff5-83843ef64822 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 21:24:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 3673711D521943947123CB42AB82A5E0 |
| SHA1: | 24E71C51D7458F64E3A3EF70B1892757545B031D |
| SHA256: | 58098A7CBF2F6F29011E3D8BDB4F7EB427C85C334D9087700EBA810AF70C362F |
| SSDEEP: | 1536:544+aviz0r/bgxLneaR/ZQWupgpdydbj8I4snxmJqY:5VNHOjfReWupgpdejJ4sxmJqY |
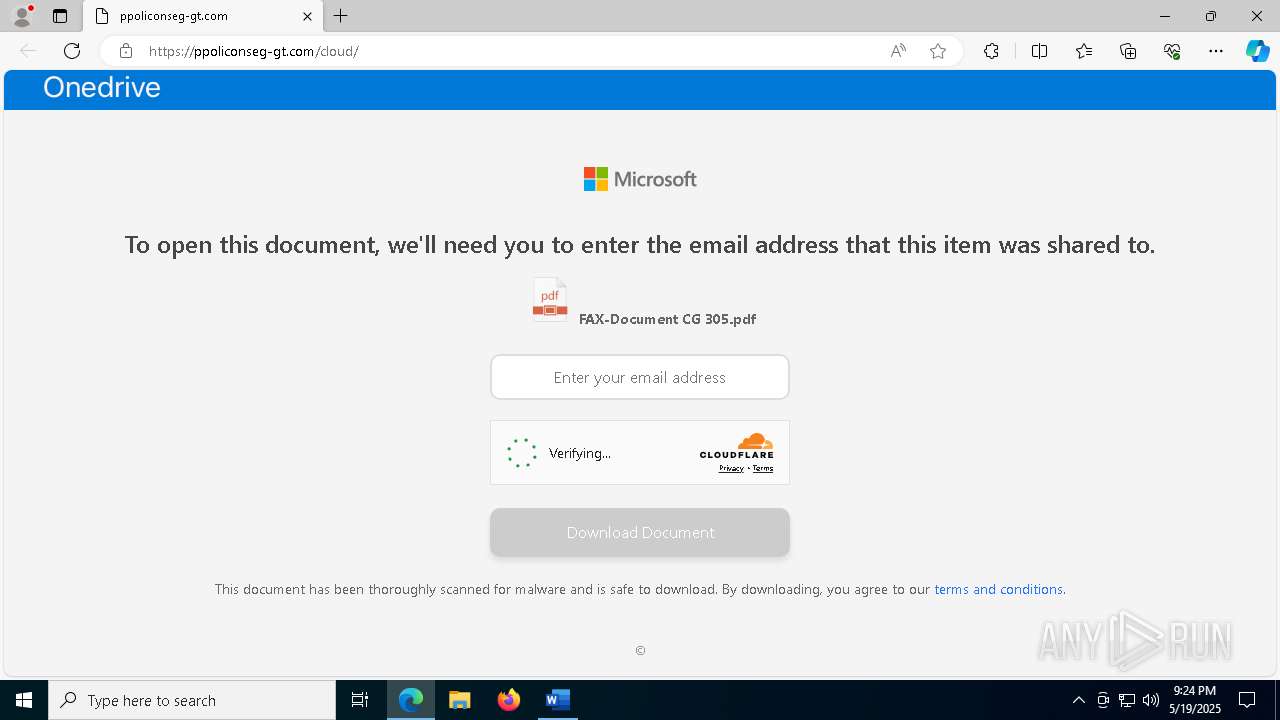
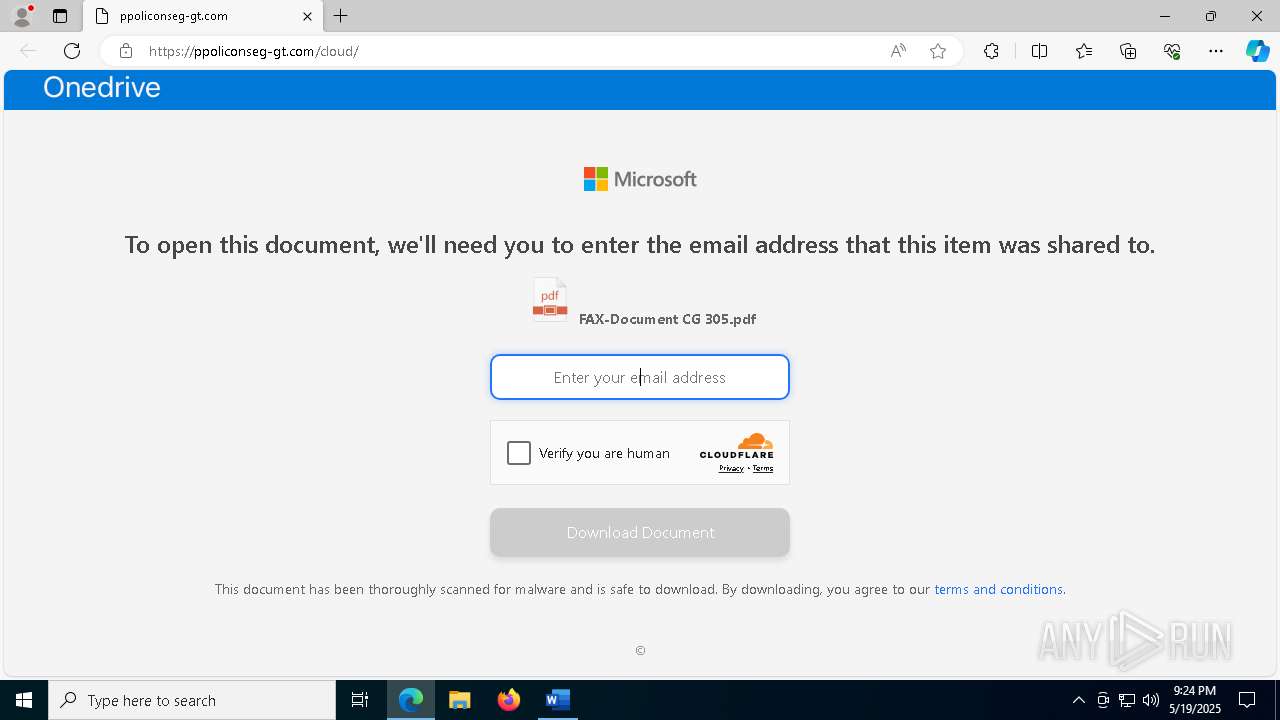
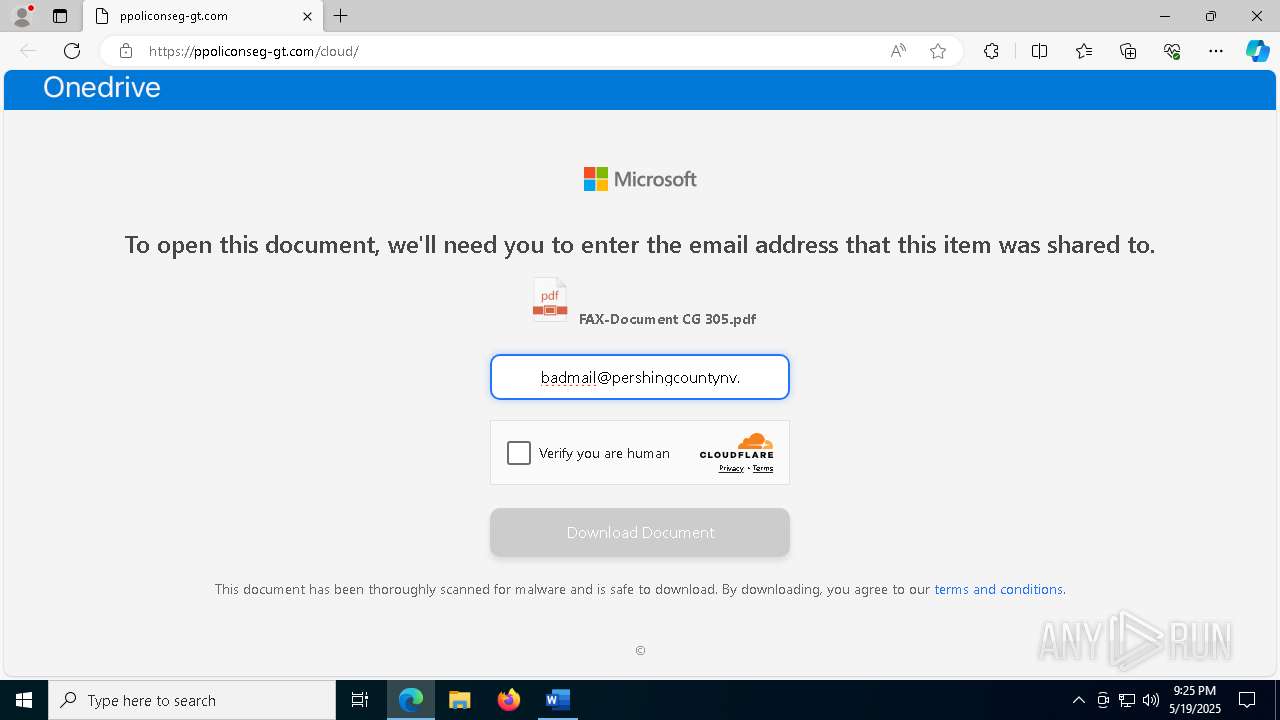
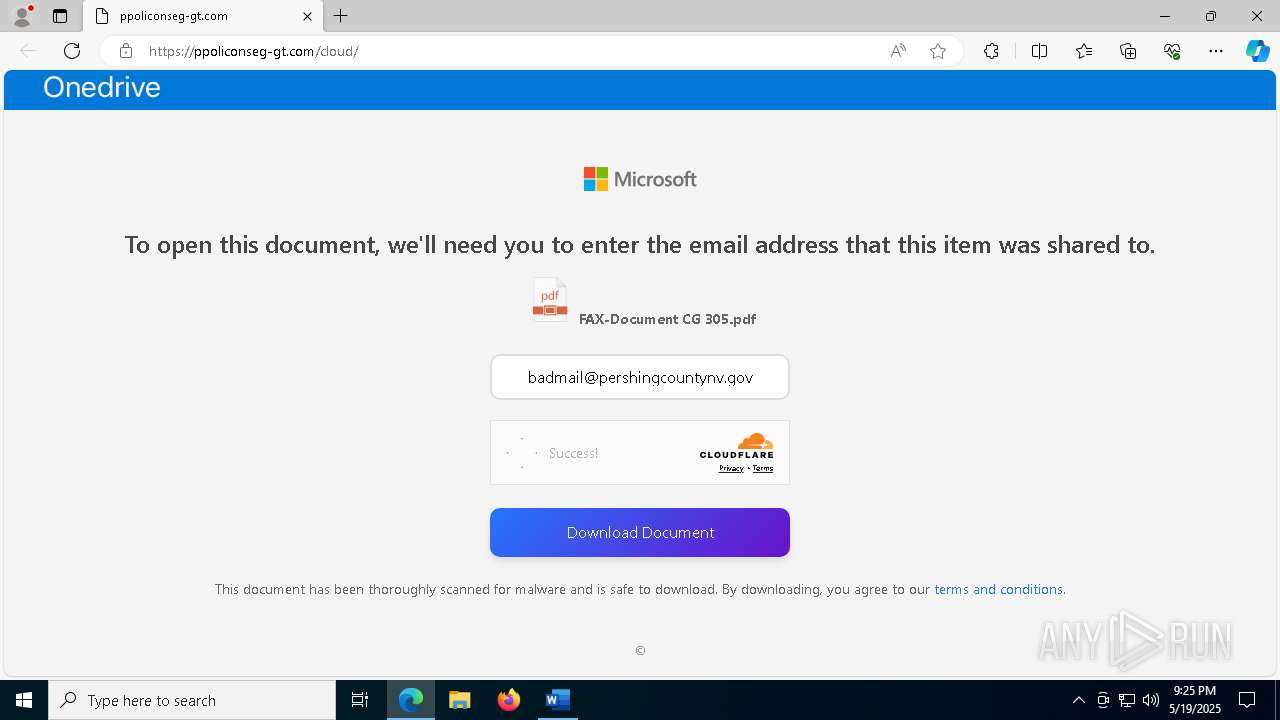
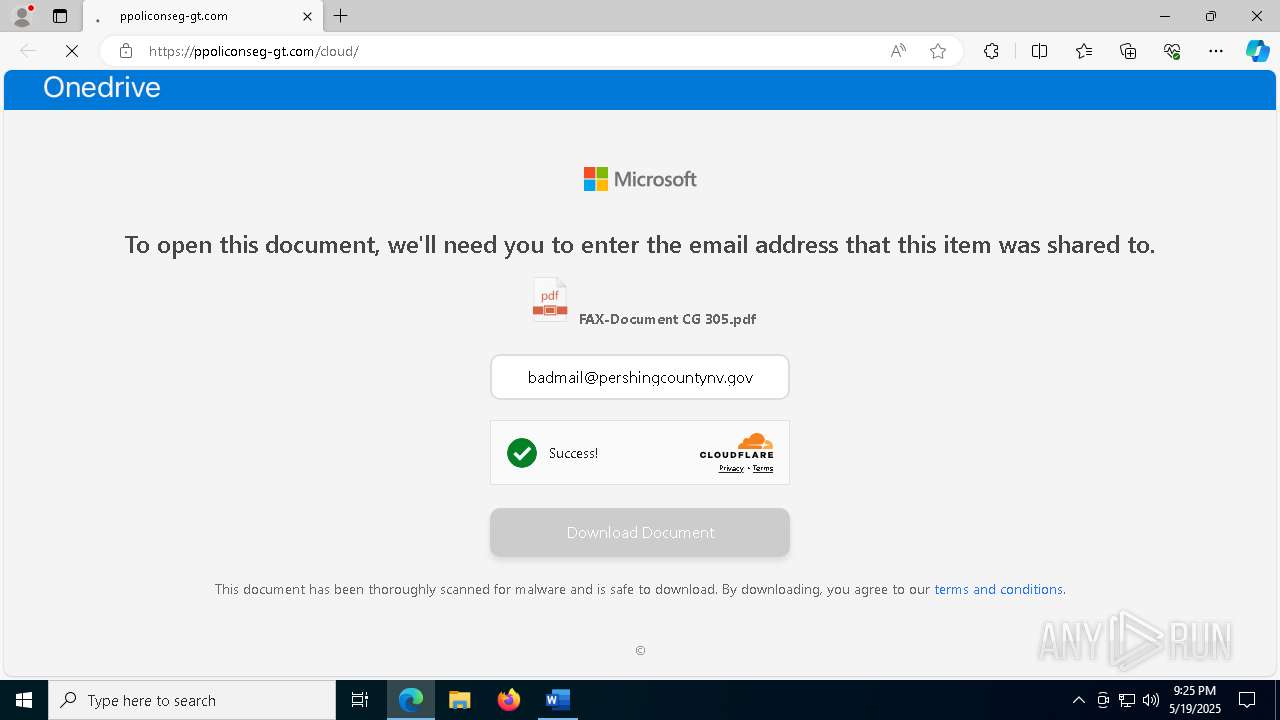
MALICIOUS
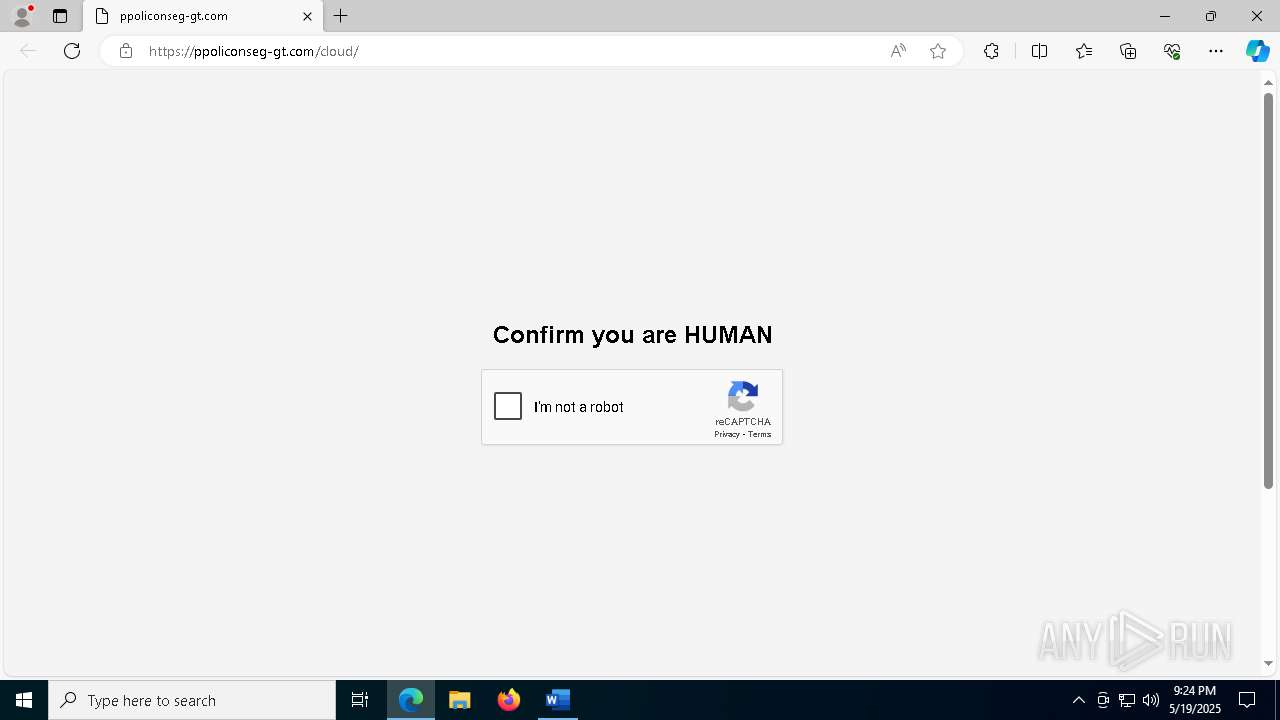
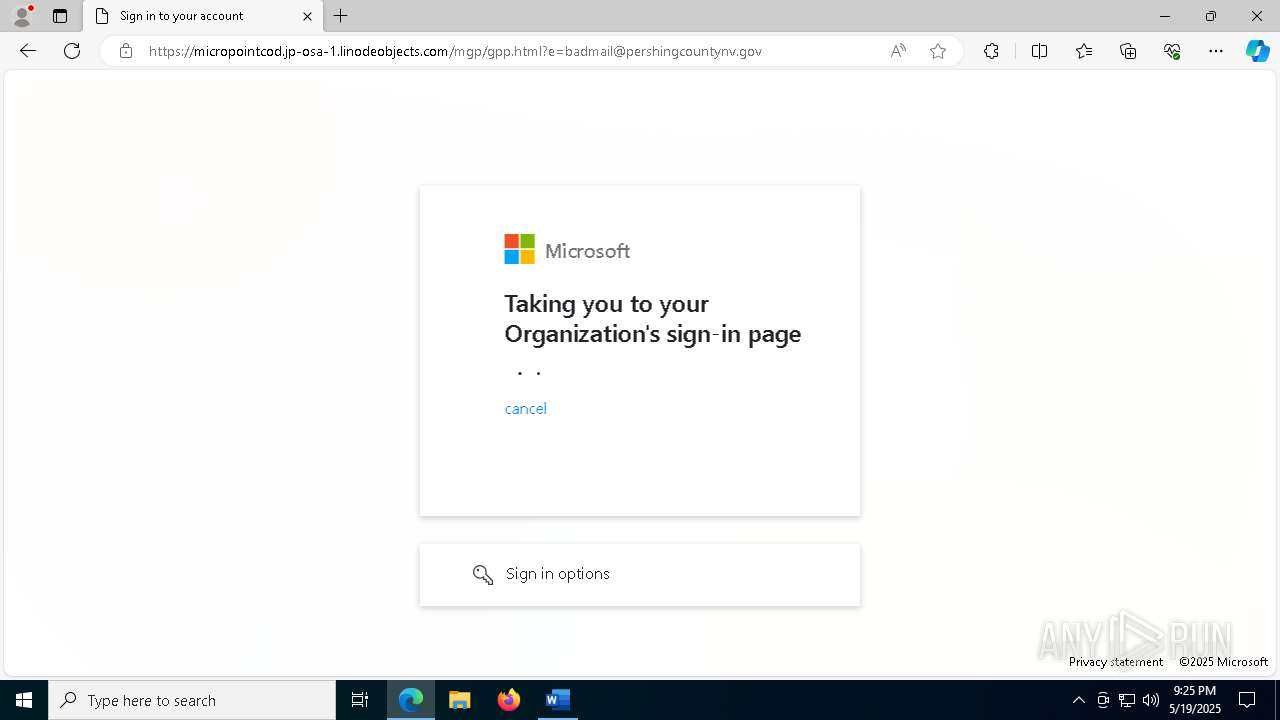
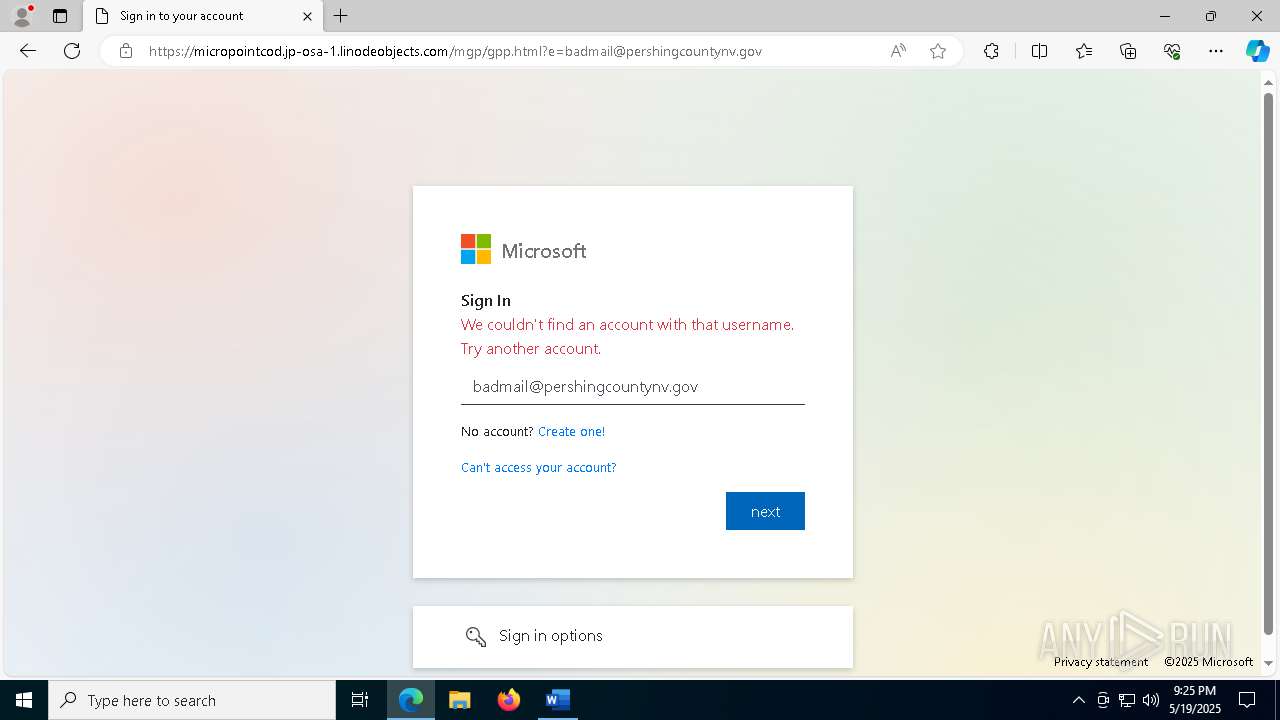
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 7852)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- msedge.exe (PID: 7608)
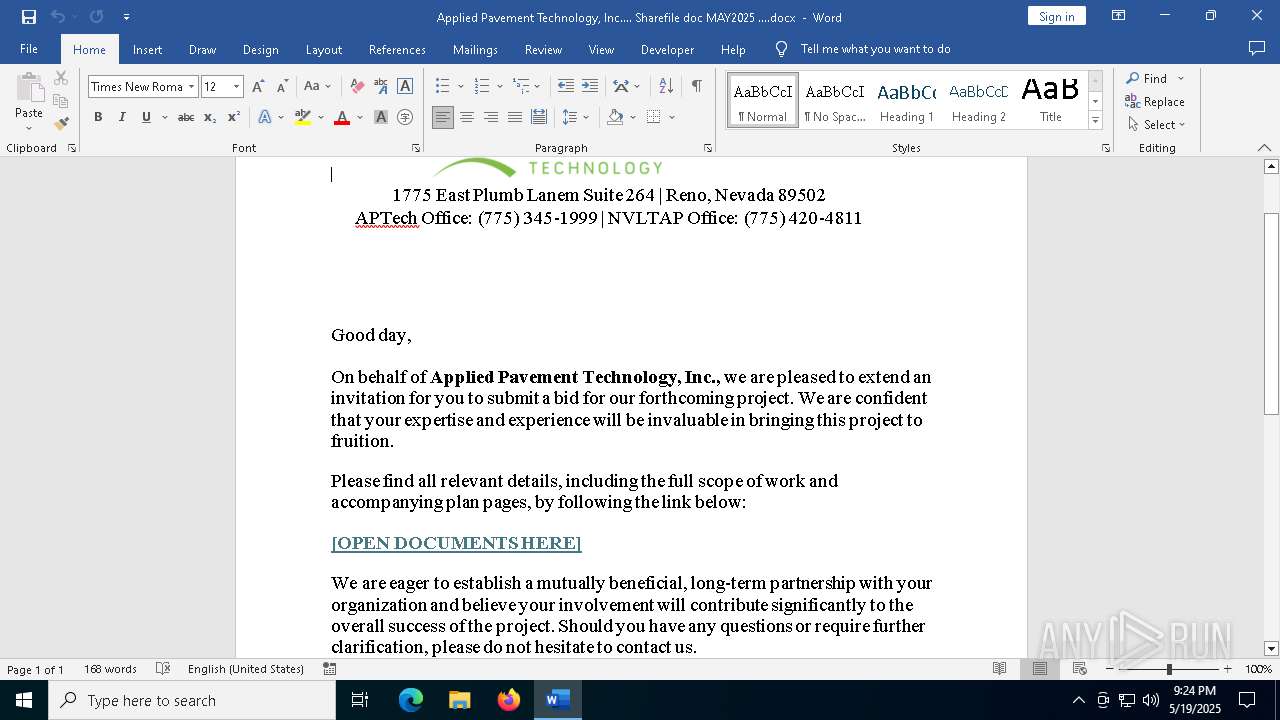
An automatically generated document
- WINWORD.EXE (PID: 4244)
Checks supported languages
- identity_helper.exe (PID: 7264)
Reads Environment values
- identity_helper.exe (PID: 7264)
Reads the computer name
- identity_helper.exe (PID: 7264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x5d0721e7 |
| ZipCompressedSize: | 368 |
| ZipUncompressedSize: | 1495 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | isamiller westernherbal.com |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | Jimmie Miller |
| RevisionNumber: | 2 |
| LastPrinted: | 2025:05:13 14:35:00Z |
| CreateDate: | 2025:05:19 18:43:00Z |
| ModifyDate: | 2025:05:19 18:43:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 749 |
| Characters: | 4273 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 35 |
| Paragraphs: | 10 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 5012 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
171
Monitored processes
39
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5484 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4008 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6656 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4244 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Applied Pavement Technology, Inc.... Sharefile doc MAY2025 ....docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5260 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5616 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5384 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=5644 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5400 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5304 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4276 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5964 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6220 --field-trial-handle=2460,i,18028015216523800807,7774079451347846275,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
17 902
Read events
17 508
Write events
356
Delete events
38
Modification events
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4244 |
| Operation: | write | Name: | 0 |
Value: 0B0E1039438BBAFBCADF458B112CD45F0448FF230046F0B09DC9C6A0F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E226C436B6C4439417355374476557545324351424F333239697363782F794A4C5A4D724F72454332695354413D22CA0D2201A201C20700C2190000C50E8908C91003783634C5119421D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 2d$ |
Value: 32642400941000000200000000000000AB523E6A04C9DB01B200000001000000740000003200000063003A005C00700072006F006700720061006D002000660069006C00650073005C006D006900630072006F0073006F006600740020006F00660066006900630065005C0072006F006F0074005C006F0066006600690063006500310036005C00670065006E006B006F002E0064006C006C0000006D006900630072006F0073006F0066007400200077006F00720064002000D0C6E0ACC0C9200094CD00AC200030AEA5B20000 | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 2d$ |
Value: 搲$႔ | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4244 |
| Operation: | write | Name: | 0 |
Value: 0B0E1039438BBAFBCADF458B112CD45F0448FF230046F0B09DC9C6A0F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E226C436B6C4439417355374476557545324351424F333239697363782F794A4C5A4D724F72454332695354413D22CA0D2201A200C20700C2190000C50E8908C91003783634C5119421D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4244 |
| Operation: | write | Name: | 0 |
Value: 0B0E1039438BBAFBCADF458B112CD45F0448FF230046F0B09DC9C6A0F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E226C436B6C4439417355374476557545324351424F333239697363782F794A4C5A4D724F72454332695354413D22CA0D22014201A200C20700C2190000C50E8908C91003783634C5119421D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\winword.exe\ETWMonitor\{BB00E856-A12F-4AB7-B2C8-4E80CAEA5B07} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\winword.exe\ETWMonitor\{DAF0B914-9C1C-450A-81B2-FEA7244F6FFA} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\winword.exe\ETWMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\winword.exe\ULSMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4244) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\winword.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
34
Suspicious files
203
Text files
53
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:A9B1D1F22AEAC77B8568ADF88961EF7A | SHA256:D58C19B2E4249DDDF5D9C1B5BCB9C1D743EB62E1D1AF54E548D7390A59DB1F29 | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:4EB7780F19297B7AC8FC01ABA9897C66 | SHA256:0638B4B5AB81CB3058111DCE195B111EB575A528038EECF6A134A593995F4380 | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:8A783934B5F2186B94F94B49D63357AE | SHA256:393A32077D8217BE9DB2013E8BF84A20F2D0770C2E7526F7884DF7F36079ACD5 | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$plied Pavement Technology, Inc.... Sharefile doc MAY2025 ....docx | binary | |
MD5:480966532FEC0CC7C582FF582D5E1431 | SHA256:97A3E25769391D4B478EF998A9C8A139DFA7AB6546C95CEFEFBAD77391626CC9 | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msoBD66.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:56E3DC54CC559B2B94AA50BC458AB1CA | SHA256:C464BF2D15CF9BB8886EA4C79182A419D693A82F31392B2D2841132AC1B93A4A | |||
| 4244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 7608 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10ed7f.TMP | — | |
MD5:— | SHA256:— | |||
| 7608 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7608 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10ed7f.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
119
DNS requests
105
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
4244 | WINWORD.EXE | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4244 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4244 | WINWORD.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4244 | WINWORD.EXE | 23.50.131.86:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4244 | WINWORD.EXE | 52.111.236.4:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bucket Object Storage service (.linodeobjects .com) |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bucket Object Storage service (.linodeobjects .com) |
7852 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (lizone) |
7852 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (lizone) |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7852 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |