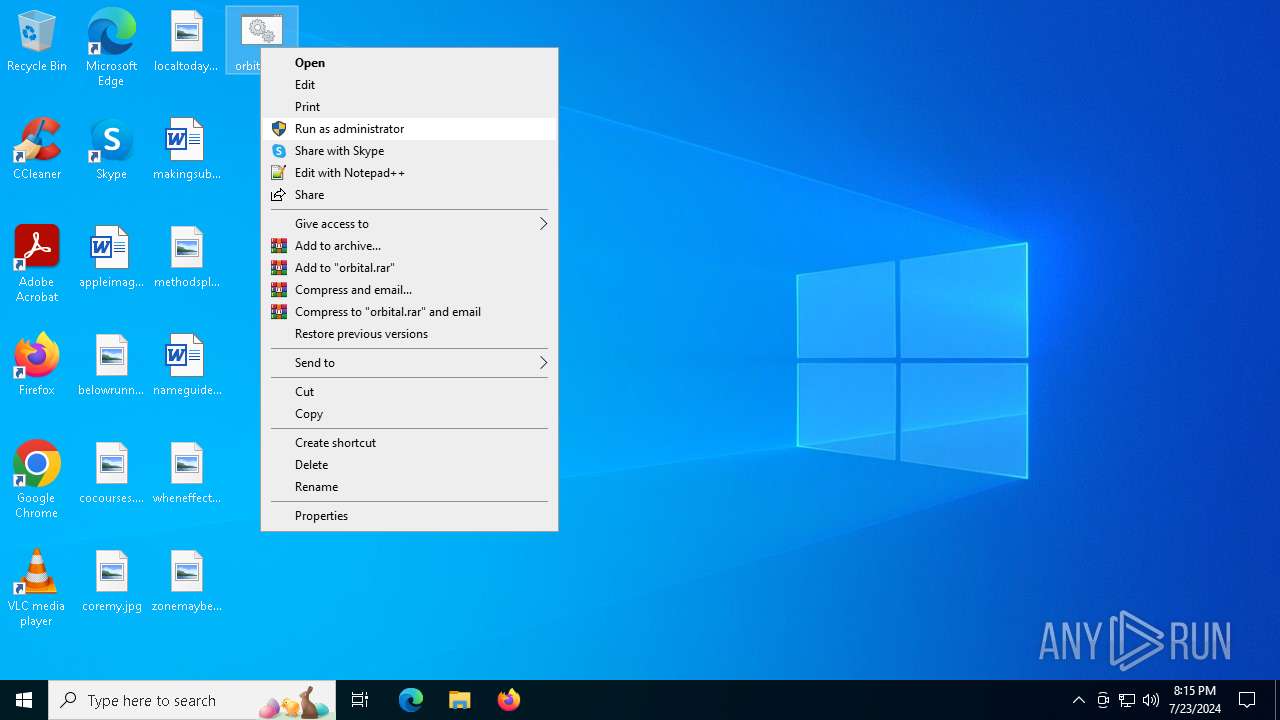
| File name: | orbital.bat |
| Full analysis: | https://app.any.run/tasks/9ab3c939-b1e6-4282-b471-ebe9fd54f8f6 |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2024, 20:15:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, Unicode text, UTF-8 text |
| MD5: | DB6316634591B6725871CF692FCDA547 |
| SHA1: | 56CA00F18186CEFAC773DCBD7360AA3BCC8D86DF |
| SHA256: | 57F539DB1E405171A5F72A62792D3C2EFE0017BEE4AFBF44F6678FA603C8EA5D |
| SSDEEP: | 24:2YzkoFI7KQT54Drp7Bp77A2YmpXCqVsMZ+kmNOk1wad+igrbHC7iCDhean:hkOIPT54rp7Bp7U2fpXCqV9eNOk1wadD |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 1956)
Application launched itself
- cmd.exe (PID: 5728)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5728)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1956)
Creates files in the driver directory
- cmd.exe (PID: 5728)
Uses WMIC.EXE
- cmd.exe (PID: 5728)
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 7036)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7036)
INFO
Manual execution by a user
- cmd.exe (PID: 5728)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6848)
- WMIC.exe (PID: 7036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
132
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | findstr /v "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\orbital.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | openfiles | C:\Windows\System32\openfiles.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays the current open files list Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1956 | C:\WINDOWS\system32\cmd.exe /c wmic memorychip get capacity /value | findstr /v "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | clip | C:\Windows\System32\clip.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Clip - copies the data into clipboard Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
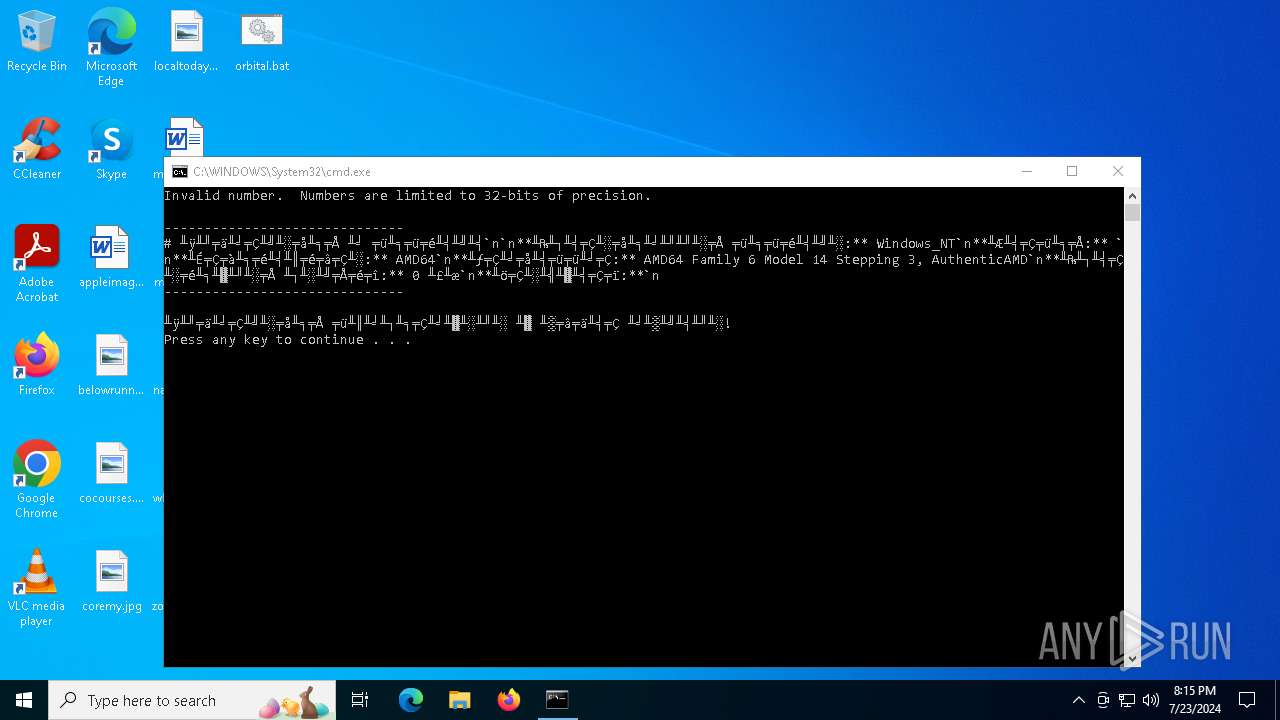
| 2368 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo # ╨ÿ╨╜╤ä╨╛╤Ç╨╝╨░╤å╨╕╤Å ╨╛ ╤ü╨╕╤ü╤é╨╡╨╝╨╡`n`n**╨₧╨┐╨╡╤Ç╨░╤å╨╕╨╛╨╜╨╜╨░╤Å ╤ü╨╕╤ü╤é╨╡╨╝╨░:** Windows_NT`n**╨Æ╨╡╤Ç╤ü╨╕╤Å:** `n**╨É╤Ç╤à╨╕╤é╨╡╨║╤é╤â╤Ç╨░:** AMD64`n**╨ƒ╤Ç╨╛╤å╨╡╤ü╤ü╨╛╤Ç:** AMD64 Family 6 Model 14 Stepping 3, AuthenticAMD`n**╨₧╨┐╨╡╤Ç╨░╤é╨╕╨▓╨╜╨░╤Å ╨┐╨░╨╝╤Å╤é╤î:** 0 ╨£╨æ`n**╨ö╤Ç╨░╨╣╨▓╨╡╤Ç╤ï:**`n " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\orbital.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6060 | openfiles | C:\Windows\System32\openfiles.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays the current open files list Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 008
Read events
1 008
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5728 | cmd.exe | C:\Windows\System32\drivers_list.txt | text | |
MD5:44B032439F7008BA074DAD33849B2908 | SHA256:FFB2223D1419EE23816B47CDAEBDF5688DD64E20091288F9EDE16F14FE6DF31F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
21
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 104.208.16.91:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3056 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4516 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.176:443 | — | Akamai International B.V. | GB | unknown |
— | — | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |