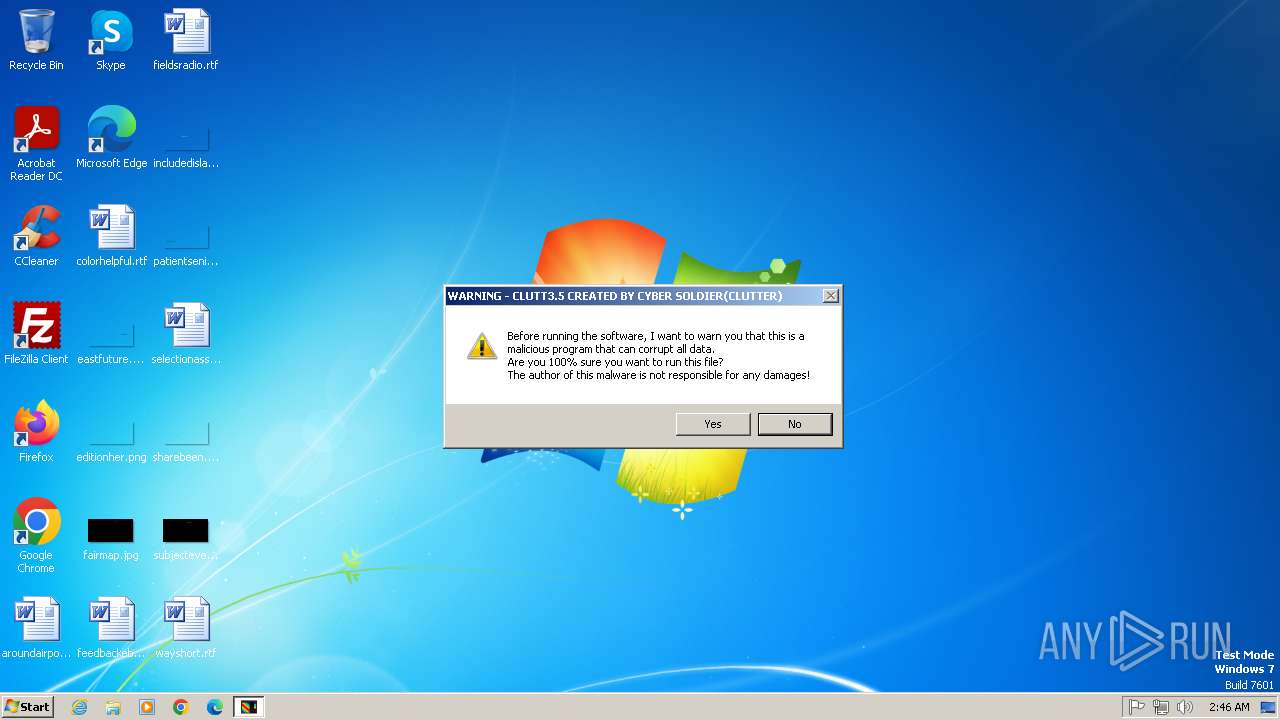
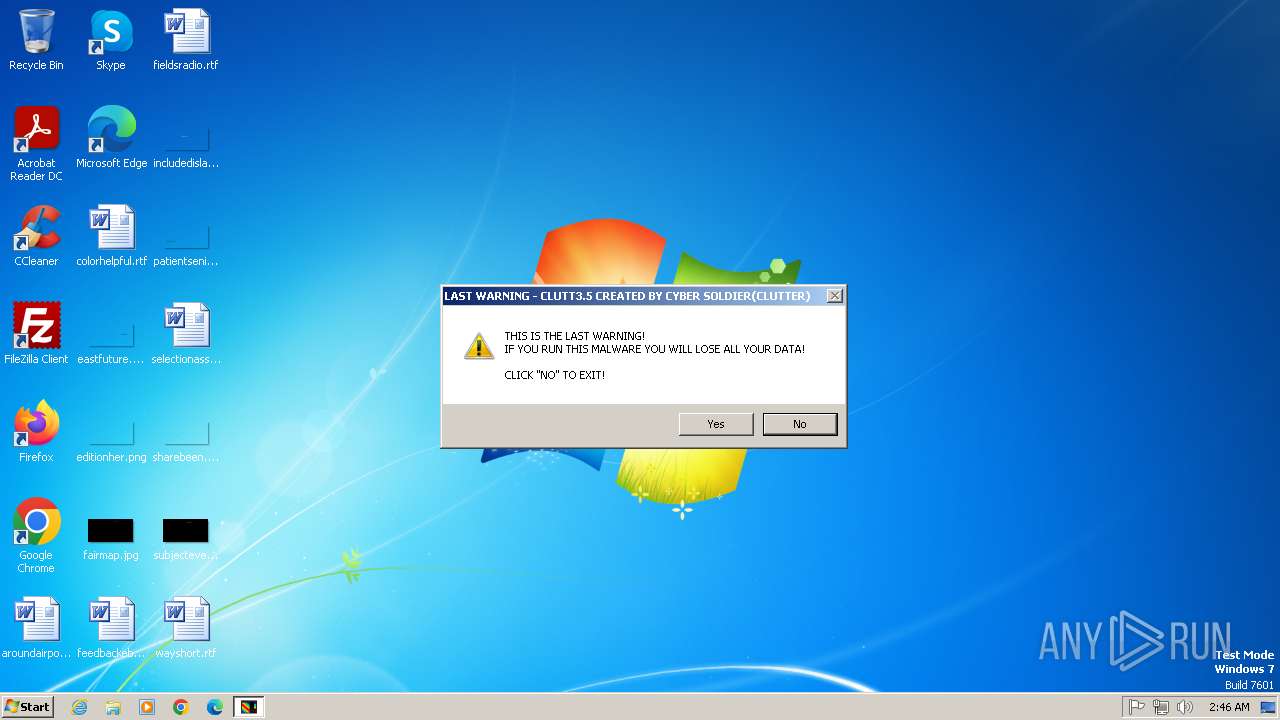
| File name: | Clutt3.5.exe |
| Full analysis: | https://app.any.run/tasks/d59d48ed-919f-41b7-8cad-4993b9d64bbf |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 01:46:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 1B787A18C44FFCCFA13CE18156A0E29F |
| SHA1: | 93FA49F5BAEAE2291330396370CE52E4F2DD7792 |
| SHA256: | 57E542F11F189BA338C74406FB48CA0091279E66D2E0491E9E7C9A6C61D66B6D |
| SSDEEP: | 12288:sUBhw5CXEvl1AdahfJyYDjWfz4IUyAxffZffBffNImh2fhSmqDP7:NBh7Uvl1AdefUYDjWfz4IUyAxffZffBl |
MALICIOUS
Disables task manager
- Clutt3.5.exe (PID: 2368)
SUSPICIOUS
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1864)
There is functionality for taking screenshot (YARA)
- Clutt3.5.exe (PID: 2368)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 1864)
Starts CMD.EXE for commands execution
- Clutt3.5.exe (PID: 2368)
Reads security settings of Internet Explorer
- Clutt3.5.exe (PID: 2368)
- Skype-Setup.tmp (PID: 3956)
Reads the Internet Settings
- Clutt3.5.exe (PID: 2368)
- Skype.exe (PID: 2544)
- Skype-Setup.tmp (PID: 3956)
- msdt.exe (PID: 4008)
Executable content was dropped or overwritten
- Skype-Setup.exe (PID: 3212)
- Skype-Setup.exe (PID: 3008)
- Skype-Setup.tmp (PID: 3956)
Application launched itself
- Skype.exe (PID: 2544)
- msdt.exe (PID: 4008)
Reads the Windows owner or organization settings
- Skype-Setup.tmp (PID: 3956)
Uses TASKKILL.EXE to kill process
- Skype-Setup.tmp (PID: 3956)
Process drops legitimate windows executable
- Skype-Setup.tmp (PID: 3956)
The process drops C-runtime libraries
- Skype-Setup.tmp (PID: 3956)
Searches for installed software
- Skype-Setup.tmp (PID: 3956)
INFO
Checks supported languages
- Clutt3.5.exe (PID: 2368)
- Skype.exe (PID: 3020)
- Skype.exe (PID: 3676)
- Skype.exe (PID: 3664)
- Skype-Setup.tmp (PID: 3112)
- Skype-Setup.exe (PID: 3212)
- Skype.exe (PID: 2920)
- Skype-Setup.exe (PID: 3008)
- Skype-Setup.tmp (PID: 3956)
- Skype.exe (PID: 2544)
- Skype.exe (PID: 948)
Confuser has been detected (YARA)
- Clutt3.5.exe (PID: 2368)
Reads the machine GUID from the registry
- Clutt3.5.exe (PID: 2368)
Manual execution by a user
- Skype.exe (PID: 2544)
- WINWORD.EXE (PID: 2740)
- chrome.exe (PID: 3900)
- msdt.exe (PID: 580)
- msdt.exe (PID: 4008)
Reads the computer name
- Clutt3.5.exe (PID: 2368)
- Skype.exe (PID: 2544)
- Skype.exe (PID: 3020)
- Skype-Setup.tmp (PID: 3112)
- Skype.exe (PID: 2920)
- Skype.exe (PID: 3676)
- Skype.exe (PID: 3664)
- Skype-Setup.tmp (PID: 3956)
Reads CPU info
- Skype.exe (PID: 2544)
Reads Environment values
- Skype.exe (PID: 2544)
Reads product name
- Skype.exe (PID: 2544)
Create files in a temporary directory
- Skype-Setup.exe (PID: 3212)
- Skype-Setup.exe (PID: 3008)
- Skype-Setup.tmp (PID: 3956)
- msdt.exe (PID: 580)
- msdt.exe (PID: 4008)
- msdt.exe (PID: 3920)
Creates files or folders in the user directory
- Skype.exe (PID: 2544)
Creates files in the program directory
- Skype-Setup.tmp (PID: 3956)
The sample compiled with english language support
- Skype-Setup.tmp (PID: 3956)
- msdt.exe (PID: 3920)
Detects InnoSetup installer (YARA)
- Skype-Setup.exe (PID: 3212)
- Skype-Setup.tmp (PID: 3112)
- Skype-Setup.tmp (PID: 3956)
- Skype-Setup.exe (PID: 3008)
Compiled with Borland Delphi (YARA)
- Skype-Setup.exe (PID: 3212)
- Skype-Setup.tmp (PID: 3112)
- Skype-Setup.exe (PID: 3008)
- Skype-Setup.tmp (PID: 3956)
Reads security settings of Internet Explorer
- msdt.exe (PID: 4008)
- msdt.exe (PID: 3920)
Reads the software policy settings
- msdt.exe (PID: 3920)
Application launched itself
- chrome.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:03:05 12:49:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 135168 |
| InitializedDataSize: | 125440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x22eae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.0.0 |
| ProductVersionNumber: | 3.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Clutter virus |
| CompanyName: | - |
| FileDescription: | Clutter virus |
| FileVersion: | 3.5 |
| InternalName: | Clutt3.5.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Clutt3.5.exe |
| ProductName: | Clutt3._5.Properties |
| ProductVersion: | 3.5 |
| AssemblyVersion: | 3.5.0.0 |
Total processes
87
Monitored processes
38
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 580 | "C:\Windows\system32\msdt.exe" -id AeroDiagnostic | C:\Windows\System32\msdt.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 752 | takeown /f C:\Windows\System32\drivers | C:\Windows\System32\takeown.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 948 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop" /prefetch:7 --no-rate-limit --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad" --url=appcenter://generic?aid=a7417433-29d9-4bc0-8826-af367733939d&iid=ad142ee9-ecfe-4580-ec0f-259fb963ccd2&uid=ad142ee9-ecfe-4580-ec0f-259fb963ccd2 --annotation=IsOfficialBuild=1 --annotation=_companyName=Skype --annotation=_productName=skype-preview --annotation=_version=8.110.0.215 "--annotation=exe=C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --annotation=plat=Win32 --annotation=prod=Electron --annotation=ver=19.1.8 --initial-client-data=0x334,0x338,0x33c,0x330,0x340,0x7dec2d8,0x7dec2e8,0x7dec2f4 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | |
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 1 Version: 8.110.0.215 | ||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3104 --field-trial-handle=1132,i,10043548380698393816,9502668252358688682,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 | ||||
| 1500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1424 --field-trial-handle=1132,i,10043548380698393816,9502668252358688682,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 | ||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2148 --field-trial-handle=1132,i,10043548380698393816,9502668252358688682,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 | ||||
| 1776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4044 --field-trial-handle=1132,i,10043548380698393816,9502668252358688682,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 | ||||
| 1784 | icacls C:\Windows\System32\drivers /grant "admin:F" | C:\Windows\System32\icacls.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1864 | "C:\Windows\System32\cmd.exe" /k takeown /f C:\Windows\System32\drivers && icacls C:\Windows\System32\drivers /grant "%username%:F" && exit | C:\Windows\System32\cmd.exe | — | Clutt3.5.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3284 --field-trial-handle=1132,i,10043548380698393816,9502668252358688682,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
102
Suspicious files
66
Text files
67
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR826A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2544 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Local Storage\leveldb\LOG.old~RF1910cf.TMP | text | |
MD5:FF878337359379694741312E6B39EF79 | SHA256:AFDE1D769112411CE68EBA5A2821FED0E058B8A31D0795F6047718DD324B3C8F | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{0BFD4E5F-5E62-4B8C-A5BC-17607569354E}.tmp | binary | |
MD5:17C6394D2EBC457ACC8AA1009625B541 | SHA256:3CADC3144E3E714207F678E1A45C48488830305DDC2DA09C6F0892F81635E283 | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:8ABD031D5384ADB4003CAE69A1FDAECF | SHA256:932BFD3FE5FF3412B7B557E09F8B7468B74D784E5F33F157FB4862A959FDCF15 | |||
| 2544 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Local Storage\leveldb\LOG | text | |
MD5:2DF990FB5D269309ED1CAD5CA4FC4321 | SHA256:653DF58589BAE7D43677A7CD2E80136347F83DF958ED37B5EAD014828398E905 | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\feedbackebay.rtf.LNK | binary | |
MD5:513FD9C599FF095B00741FE502BD953A | SHA256:5E64EEB3FB9F872751177B7F66A3C7F7804B36D6DDBC24DE830A341825F13186 | |||
| 3956 | Skype-Setup.tmp | C:\Program Files\Microsoft\Skype for Desktop\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:AABBB38C4110CC0BF7203A567734A7E7 | SHA256:24B07028C1E38B9CA2F197750654A0DFB7D33C2E52C9DD67100609499E8028DB | |||
| 3956 | Skype-Setup.tmp | C:\Program Files\Microsoft\Skype for Desktop\is-FOI79.tmp | executable | |
MD5:55364BFEA54A03CCBA0F0400DF3D629F | SHA256:94B0E7DCDE2CBE4543EB28111FC5567EA622437F5A58A5E716BB7CFE0BF8DFAE | |||
| 3008 | Skype-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-JV08R.tmp\Skype-Setup.tmp | executable | |
MD5:55364BFEA54A03CCBA0F0400DF3D629F | SHA256:94B0E7DCDE2CBE4543EB28111FC5567EA622437F5A58A5E716BB7CFE0BF8DFAE | |||
| 2544 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\settings.dat | binary | |
MD5:3B2AEFD32F61DB8110091B81A16A9AD1 | SHA256:27A6D2020F45CD9D3F4DFCF837EC661A1D997B08D23E3CB41B94186C21A50B37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
20
DNS requests
19
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2544 | Skype.exe | 52.113.194.133:443 | get.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2544 | Skype.exe | 13.107.42.16:443 | a.config.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3852 | chrome.exe | 216.58.206.35:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3900 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3852 | chrome.exe | 142.251.168.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3852 | chrome.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
3852 | chrome.exe | 142.250.185.67:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
apis.google.com |
| whitelisted |
play.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Skype.exe | [0525/024715.188:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\attachments\3a0ee62b-79ac-4cc3-bbd5-f65252e7a91f: The system cannot find the file specified. (0x2)
|