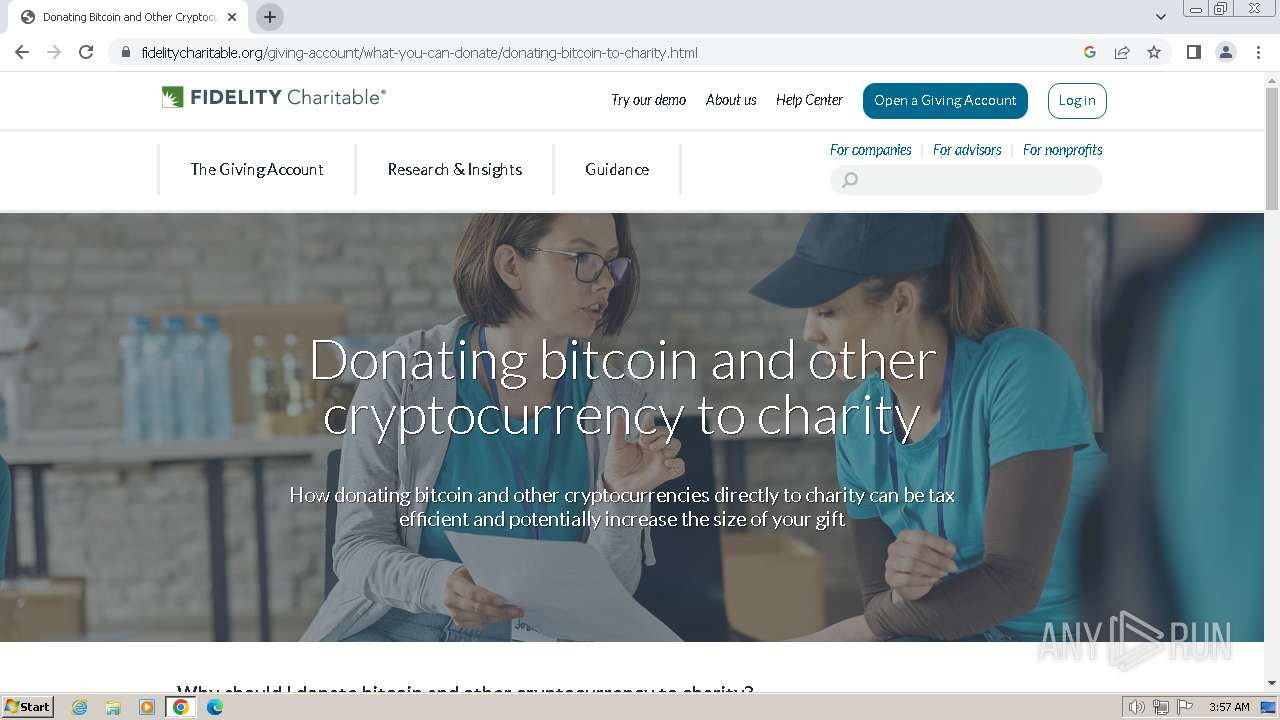
| File name: | fodhelper.exe |
| Full analysis: | https://app.any.run/tasks/0dde764e-eb03-4462-ba9f-aba13efeb1b9 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2024, 03:54:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D3CAD18B786A20196C2DD96141225A35 |
| SHA1: | 78A9702746779E4C6675E46379405C0FDF98A92F |
| SHA256: | 57D3D5D5B3F8E4AA80FC43D107A3D73DD203FD15524266AAF62873E11691AFFF |
| SSDEEP: | 24576:TCcI6kVhM/D9p4Q0a1KMyRGlemKAEm6MaP:TC/6kVhM/D9p4Q11KMyRGlemKAEhMaP |
MALICIOUS
Drops the executable file immediately after the start
- fodhelper.exe (PID: 2640)
- fodhelper.exe (PID: 2396)
RACCOONCLIPPER has been detected (YARA)
- fodhelper.exe (PID: 3324)
SUSPICIOUS
Application launched itself
- fodhelper.exe (PID: 2640)
- fodhelper.exe (PID: 2732)
- fodhelper.exe (PID: 2824)
- fodhelper.exe (PID: 124)
- fodhelper.exe (PID: 3316)
- fodhelper.exe (PID: 1776)
Executable content was dropped or overwritten
- fodhelper.exe (PID: 2396)
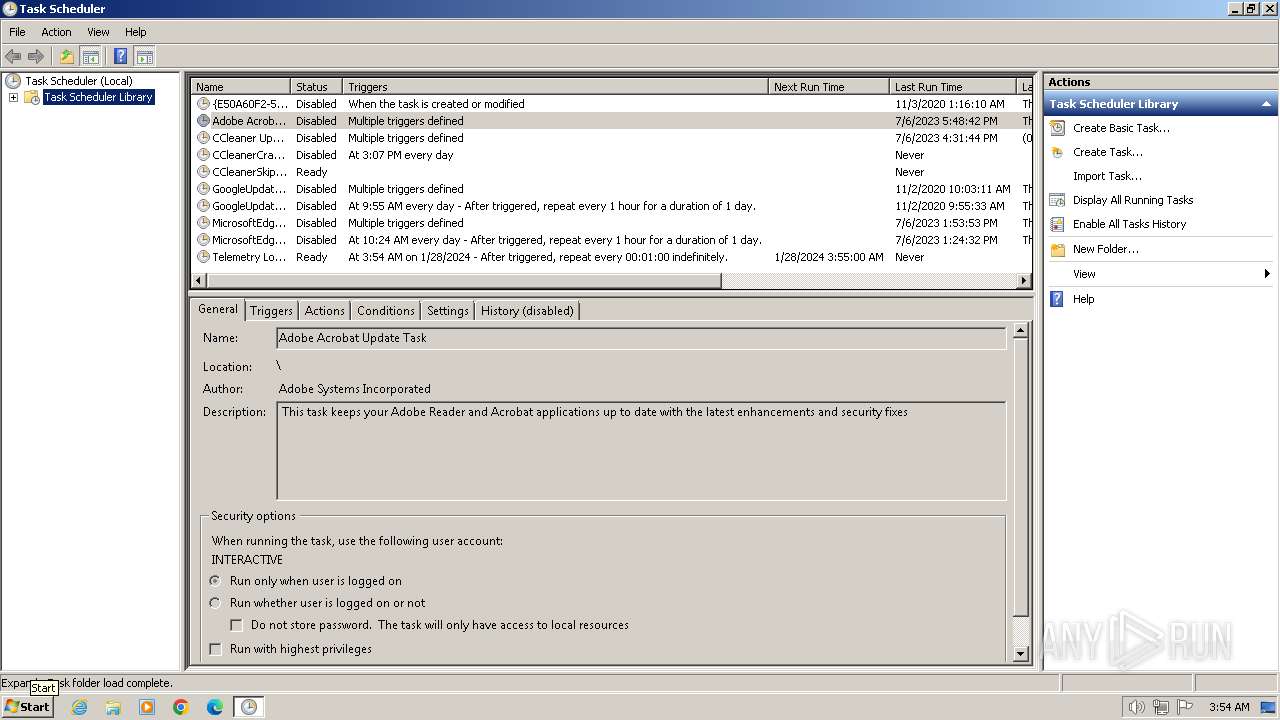
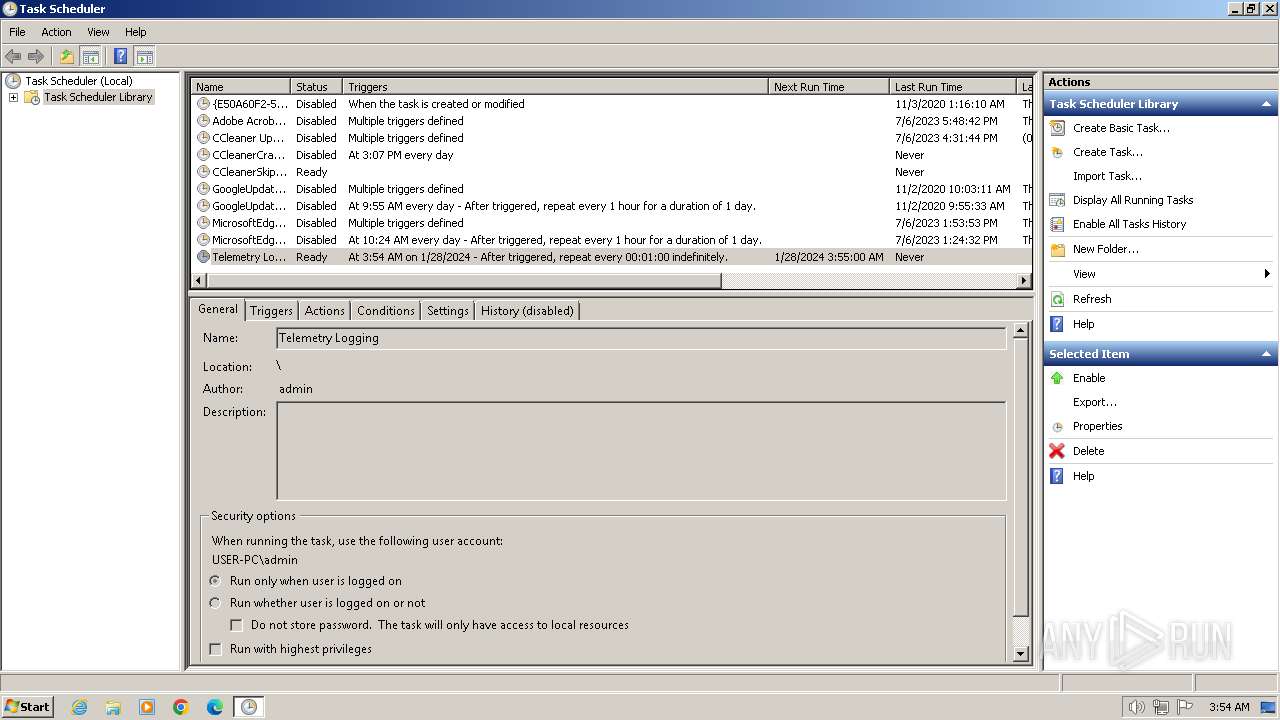
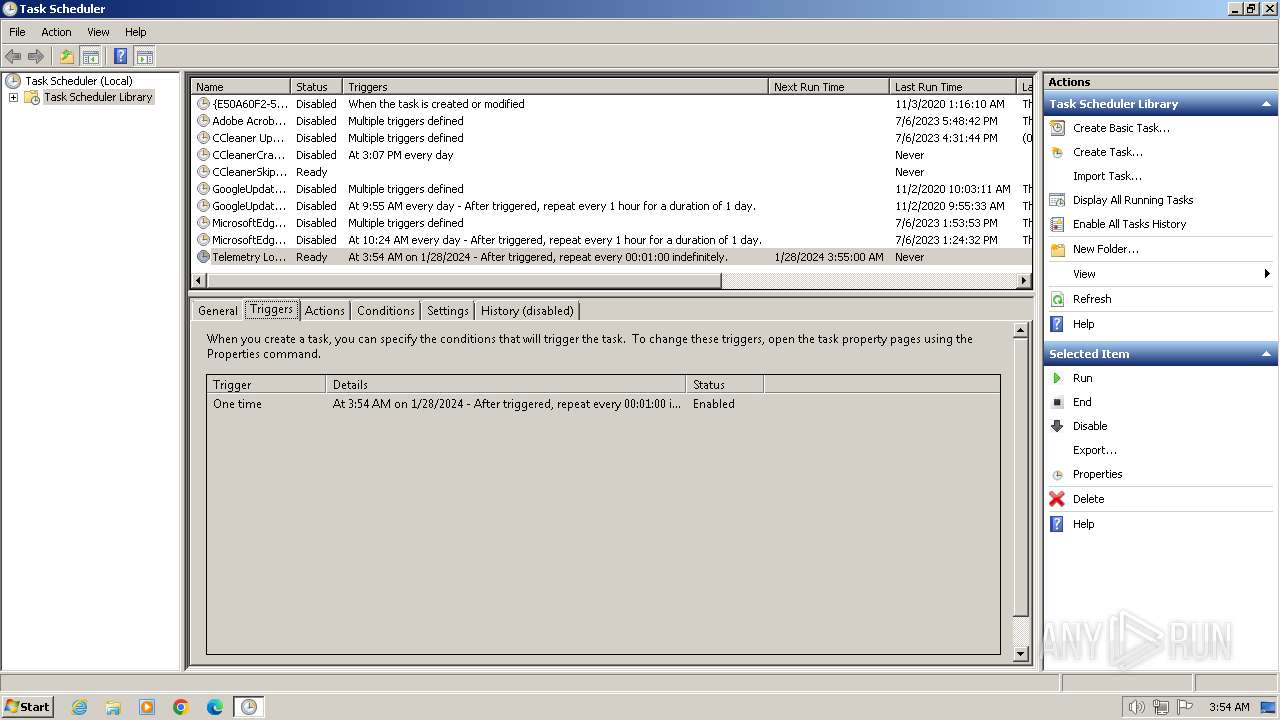
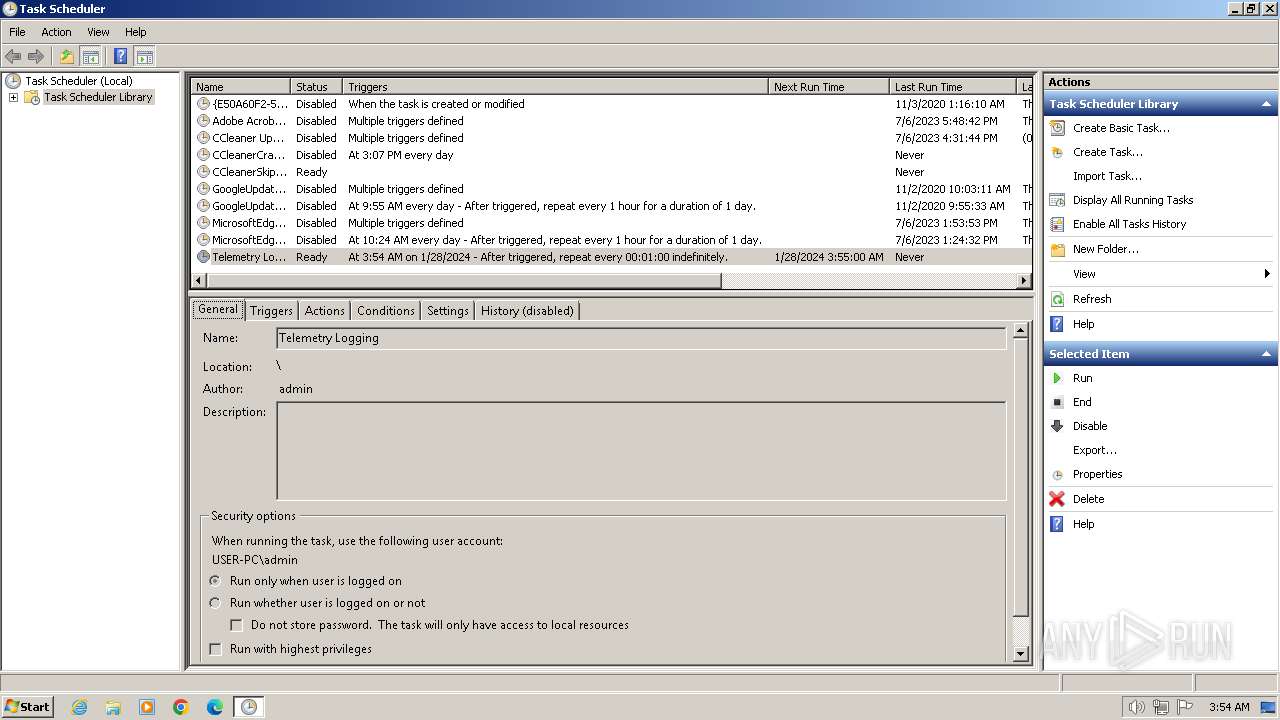
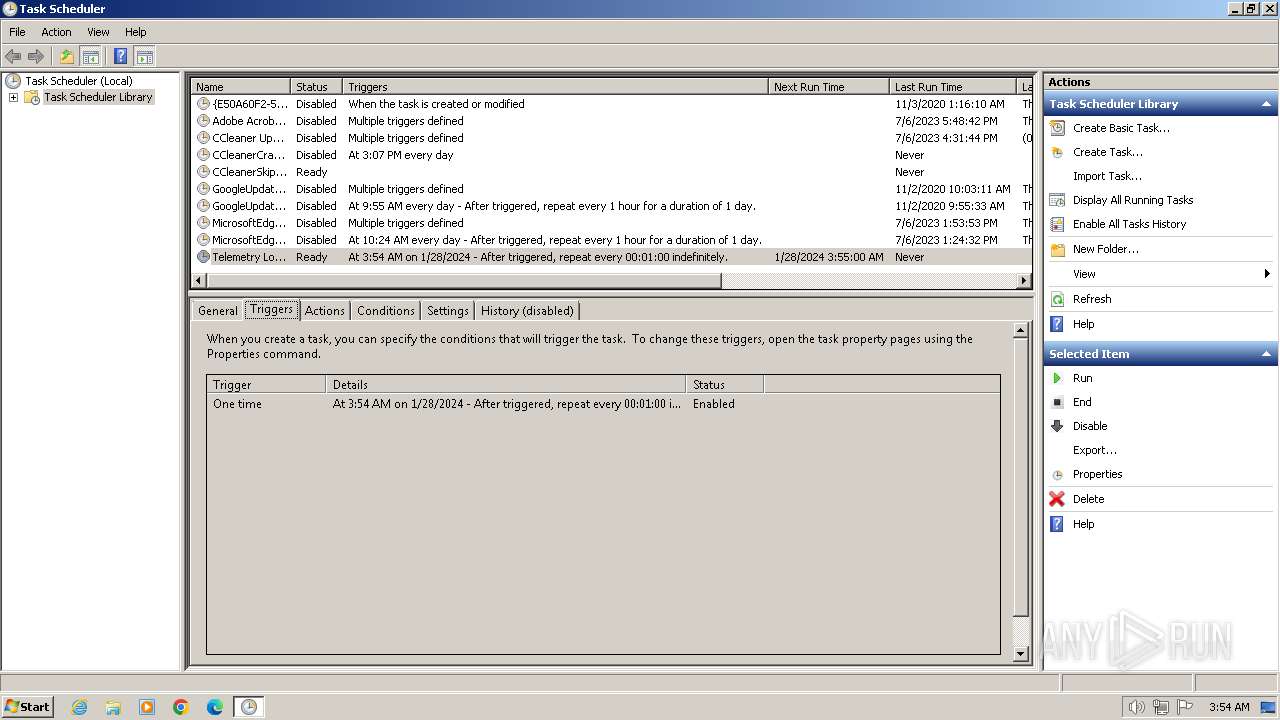
The process executes via Task Scheduler
- fodhelper.exe (PID: 2824)
- fodhelper.exe (PID: 3316)
- fodhelper.exe (PID: 124)
- fodhelper.exe (PID: 1776)
- fodhelper.exe (PID: 2732)
INFO
Reads the machine GUID from the registry
- fodhelper.exe (PID: 2640)
- fodhelper.exe (PID: 2732)
- fodhelper.exe (PID: 2824)
- fodhelper.exe (PID: 124)
- fodhelper.exe (PID: 3316)
- fodhelper.exe (PID: 1776)
Reads the computer name
- fodhelper.exe (PID: 2640)
- fodhelper.exe (PID: 2732)
- fodhelper.exe (PID: 2824)
- fodhelper.exe (PID: 124)
- fodhelper.exe (PID: 3316)
- fodhelper.exe (PID: 1776)
Checks supported languages
- fodhelper.exe (PID: 2640)
- fodhelper.exe (PID: 2732)
- fodhelper.exe (PID: 3324)
- fodhelper.exe (PID: 2824)
- fodhelper.exe (PID: 2396)
- fodhelper.exe (PID: 3316)
- fodhelper.exe (PID: 3020)
- fodhelper.exe (PID: 124)
- fodhelper.exe (PID: 1584)
- fodhelper.exe (PID: 2880)
- fodhelper.exe (PID: 1776)
- fodhelper.exe (PID: 3236)
Creates files or folders in the user directory
- fodhelper.exe (PID: 2396)
Manual execution by a user
- mmc.exe (PID: 2388)
- mmc.exe (PID: 2892)
- chrome.exe (PID: 2508)
Application launched itself
- chrome.exe (PID: 2508)
Executable content was dropped or overwritten
- chrome.exe (PID: 1020)
Drops the executable file immediately after the start
- chrome.exe (PID: 1020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RaccoonClipper
(PID) Process(3324) fodhelper.exe
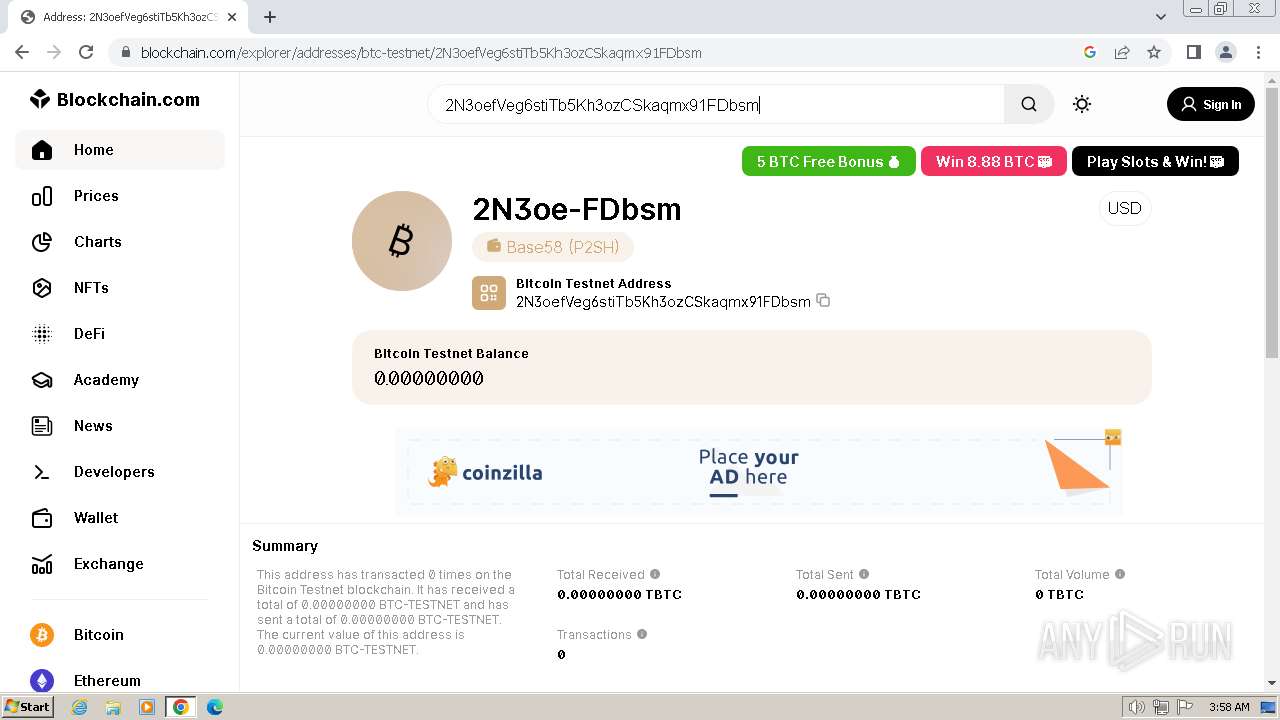
Wallets (18)1BspfXbHj1R5RcShF31KNpBW79h9zBej5J
addr1q90kzt7nhxjkhm5e40nadh5ym57p24aswumdy0aggyk8mmjlvyha8wd9d0hfn2l86m0gfhfuz4tmqaek6gl6ssfv0hhqe6akq0
TXQXx2nJnd1PpUVkZvfh7LbffUisurwd43
t1Upr9Q3VMFLC8sz6spautGumgDqdSvdgsq
88ULP41eYUCWzYVGPXuBUEJR9j8Lu17zPKvkLqyXQMt3BjKZijVqiq6786u3bveEHnemGXR78uGj28ELXmDTURC2PJYRuTH
LKTWnwuM4eZgXdUNh5RpV3ETxNRbbbPDFT
Adu5K93Evg5jsQGdwMA69onB4dJ74L87GX
Ae2tdPwUPEZKFp3DNd7g57oc3vWeZ6N2fA1uA5KqJ9qyQTyC2D2YEaGEYzL
Z1BspfXbHj1R5RcShF31KNpBW79h9zBej5J
0xB78aD0c44964c978c763cCa142C8D3f30B711e3c
bc1qnl5vwuzw57rtm98wg2jh6mu0p597892q0pss27
bnb1gjp5822en66dsh7k0v00q0hxzwuus3c0m2v74w
YWAMDRGWA6TMDAVJV5XP6CQZZMO46NLC4TK555FRDCTPLUMST5YENA4VIE
DB84kZEkPqBUVh1KvEcN7f3KSEEhPVMNPS
49XPrw6TrHAVvw2pPGhdifGdfYc3iHftvSwQvmy74drQMpU4bmE3syc6mV9uSKDhbQB54Egan4AL1NMzAvYRY3jHHZdYUcm
BXgs2AAWD7gF2WUNhva7byzkpR4QbvM3YHoCJzrGebnb
ltc1qvfghx46z8v9fyawar6qgdhj5wtrslvvx2kn438
cosmos1k6y3w45ralwcaarlgt7zcgm5htk2rw9jq5jxce
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:27 20:42:24+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 655360 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa1ebe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | Odhcjivd.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Odhcjivd.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
108
Monitored processes
65
Malicious processes
2
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | C:\Users\admin\AppData\Roaming\Microsoft\TelemetryServices\fodhelper.exe | C:\Users\admin\AppData\Roaming\Microsoft\TelemetryServices\fodhelper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --mojo-platform-channel-handle=4020 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=34 --mojo-platform-channel-handle=2296 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
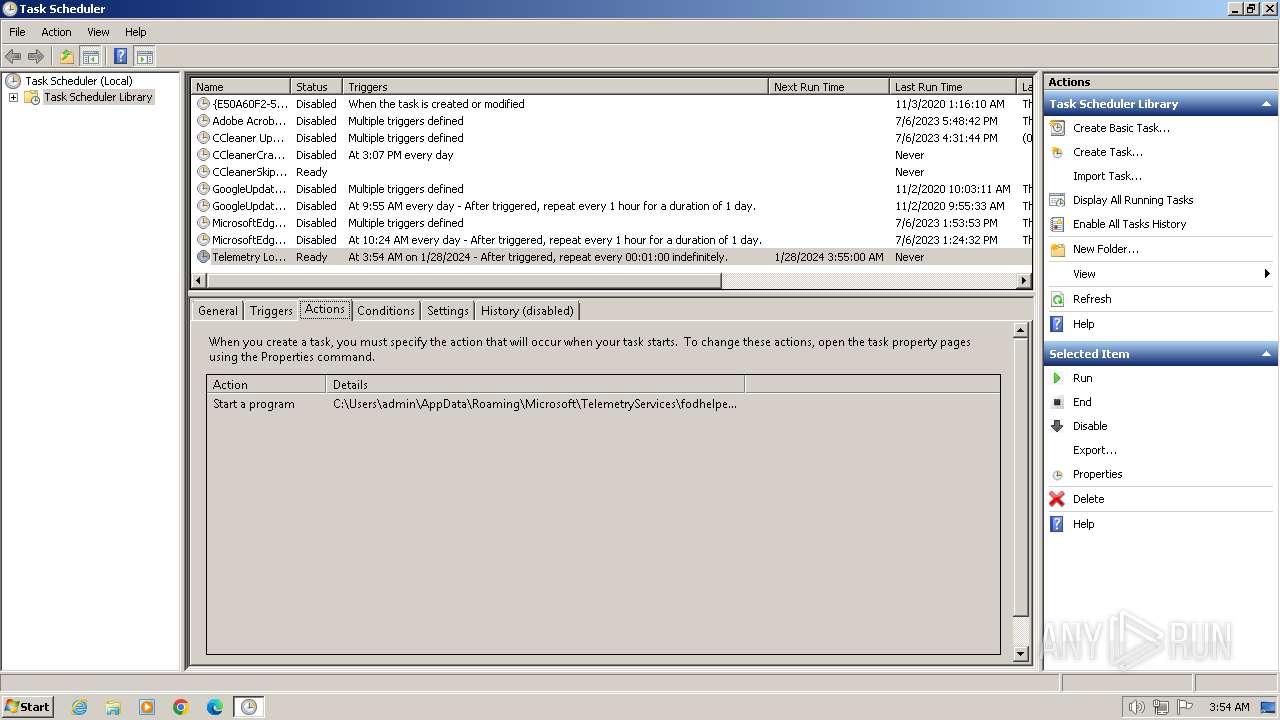
| 664 | /C /create /F /sc minute /mo 1 /tn "Telemetry Logging" /tr "C:\Users\admin\AppData\Roaming\Microsoft\TelemetryServices\fodhelper.exe" | C:\Windows\System32\schtasks.exe | — | fodhelper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3344 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=4412 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=784 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3844 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=516 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=4432 --field-trial-handle=1112,i,15088266796819138162,11683757442939266349,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
3 862
Read events
3 768
Write events
92
Delete events
2
Modification events
| (PID) Process: | (2892) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (2892) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (2892) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (2508) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
23
Suspicious files
816
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF16fa14.TMP | — | |
MD5:— | SHA256:— | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2396 | fodhelper.exe | C:\Users\admin\AppData\Roaming\Microsoft\TelemetryServices\fodhelper.exe | executable | |
MD5:D3CAD18B786A20196C2DD96141225A35 | SHA256:57D3D5D5B3F8E4AA80FC43D107A3D73DD203FD15524266AAF62873E11691AFFF | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF16fa14.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF16fcc4.TMP | — | |
MD5:— | SHA256:— | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RF16fc08.TMP | text | |
MD5:C5B082BC8EA6A9BD1DC6782C00A79605 | SHA256:6168A9E585264DE05DEE1B67427B1BC277F1B83B9297184EFACC5D3BB061ABDE | |||
| 2508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 2892 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:751B712CBB24DA2454555755BC9512BA | SHA256:AECA4863257BCD28ECB3E13267576D42494DD8E531006566737467E9DA6F72FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
325
DNS requests
570
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.4 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.66 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 5.47 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.29 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 21.0 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 43.4 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 88.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 176 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 345 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2508 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3604 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3604 | chrome.exe | 142.250.186.36:443 | www.google.com | GOOGLE | US | whitelisted |
3604 | chrome.exe | 142.251.16.84:443 | accounts.google.com | GOOGLE | US | unknown |
3604 | chrome.exe | 142.250.186.35:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3604 | chrome.exe | 142.250.185.142:443 | apis.google.com | GOOGLE | US | whitelisted |
2508 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
thegivingblock-com.webpkgcache.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3604 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY Observed TikTok Domain in TLS SNI (tiktok.com) |
Process | Message |
|---|---|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|