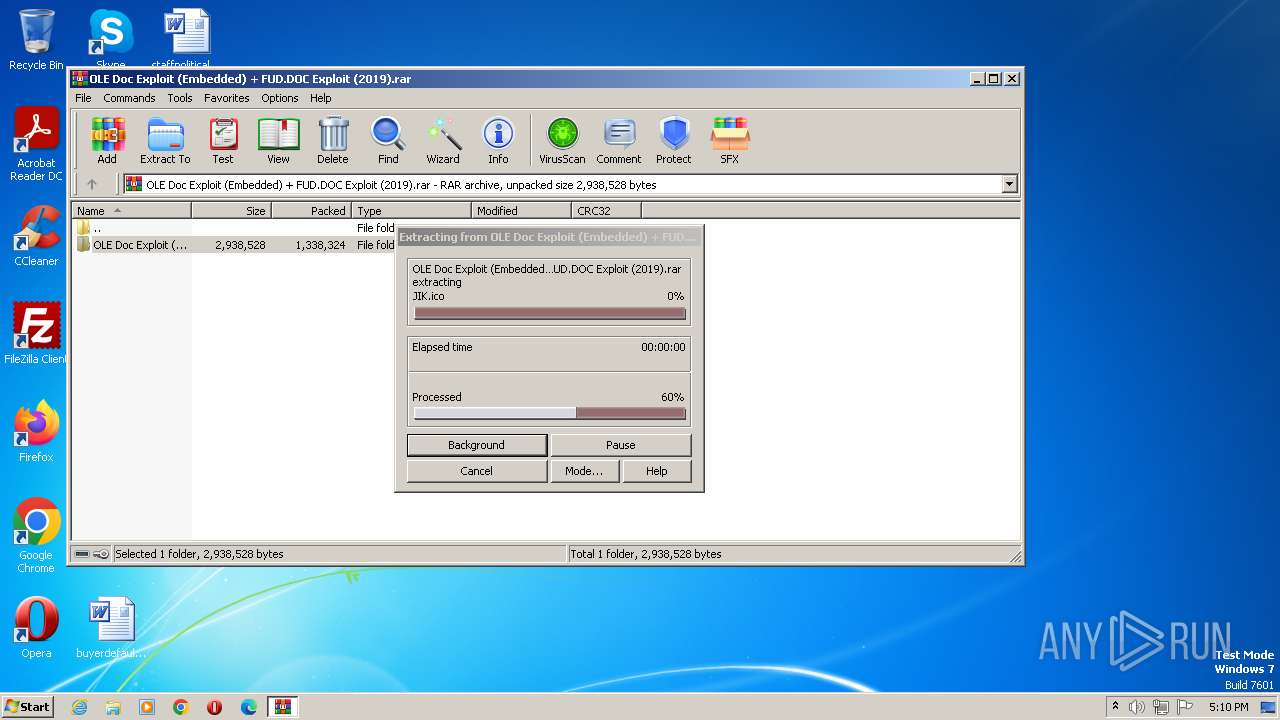
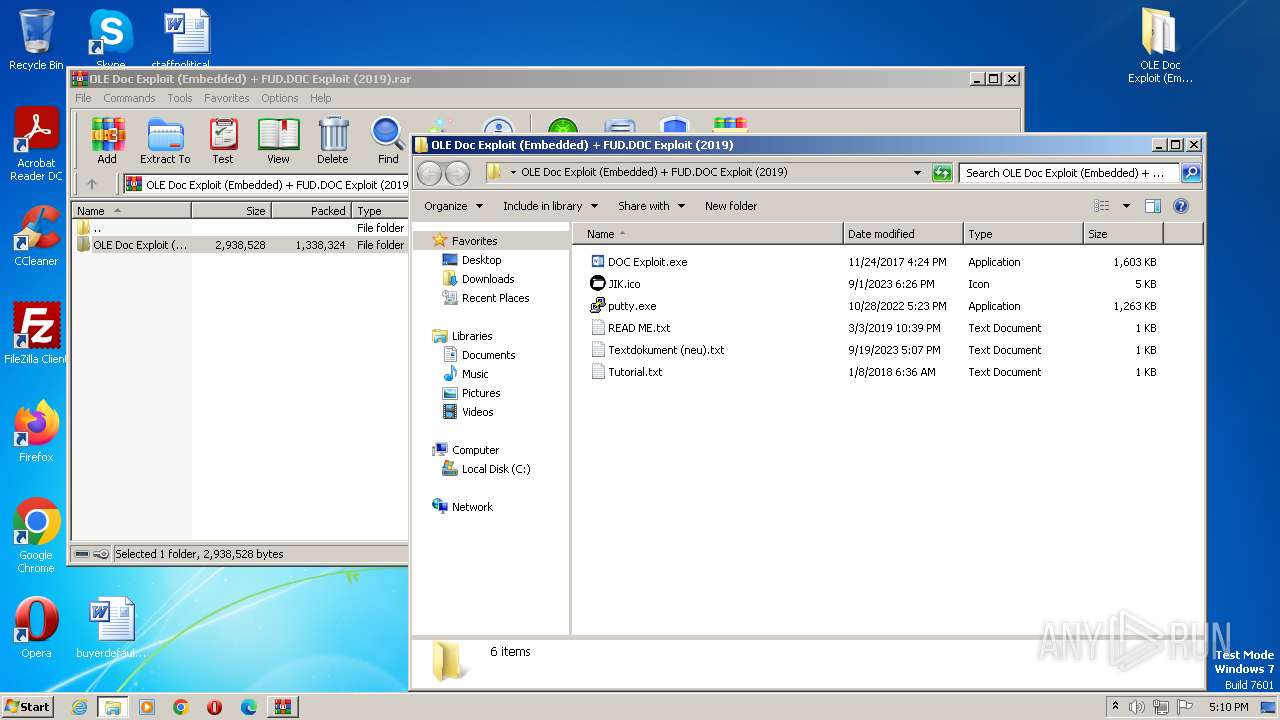
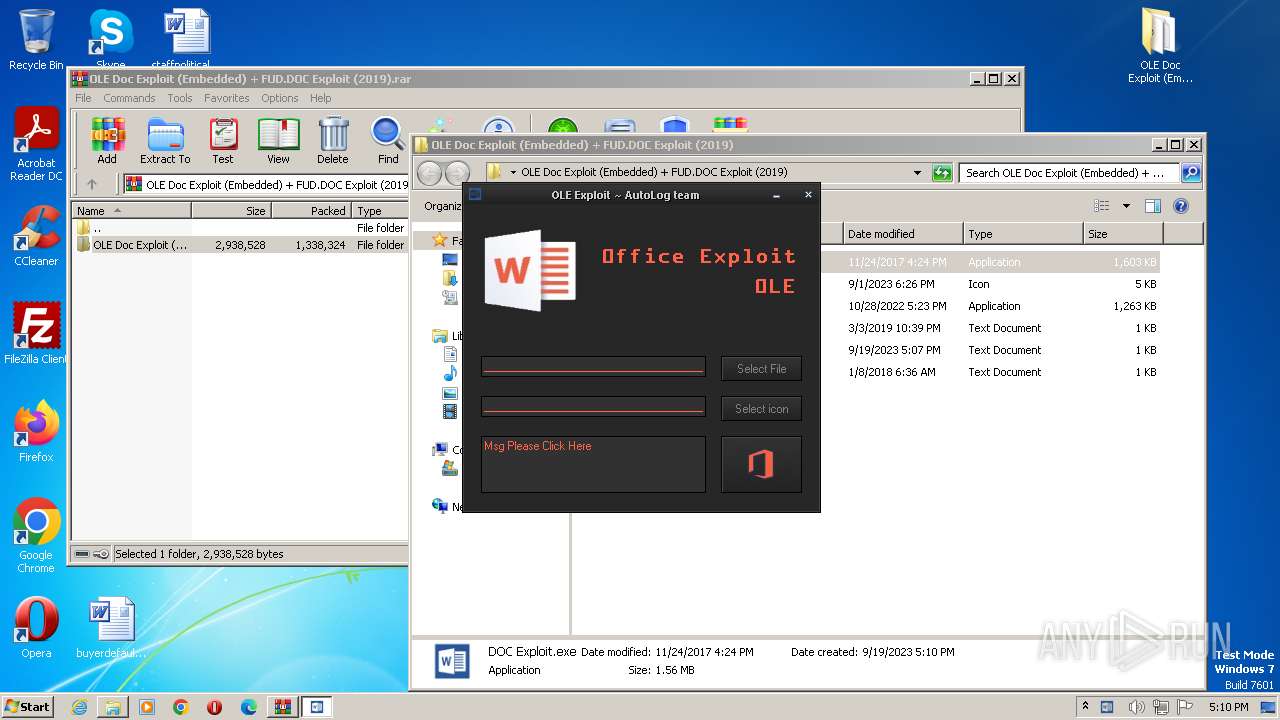
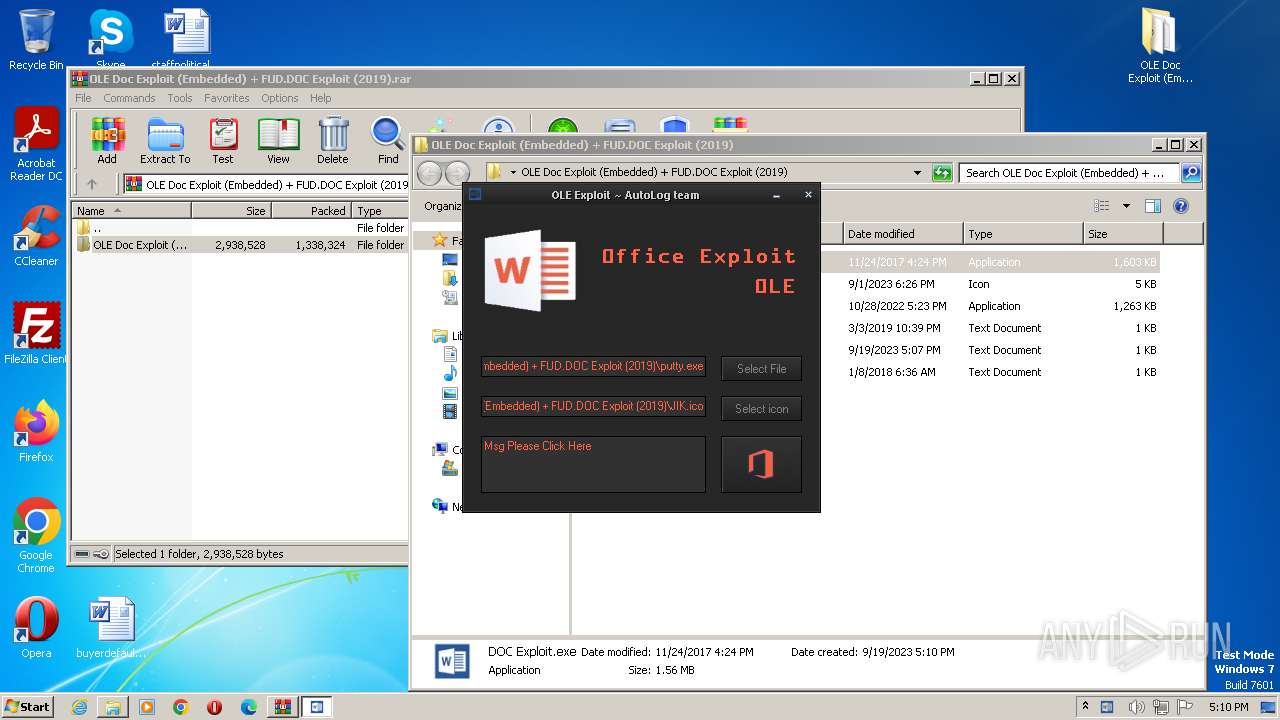
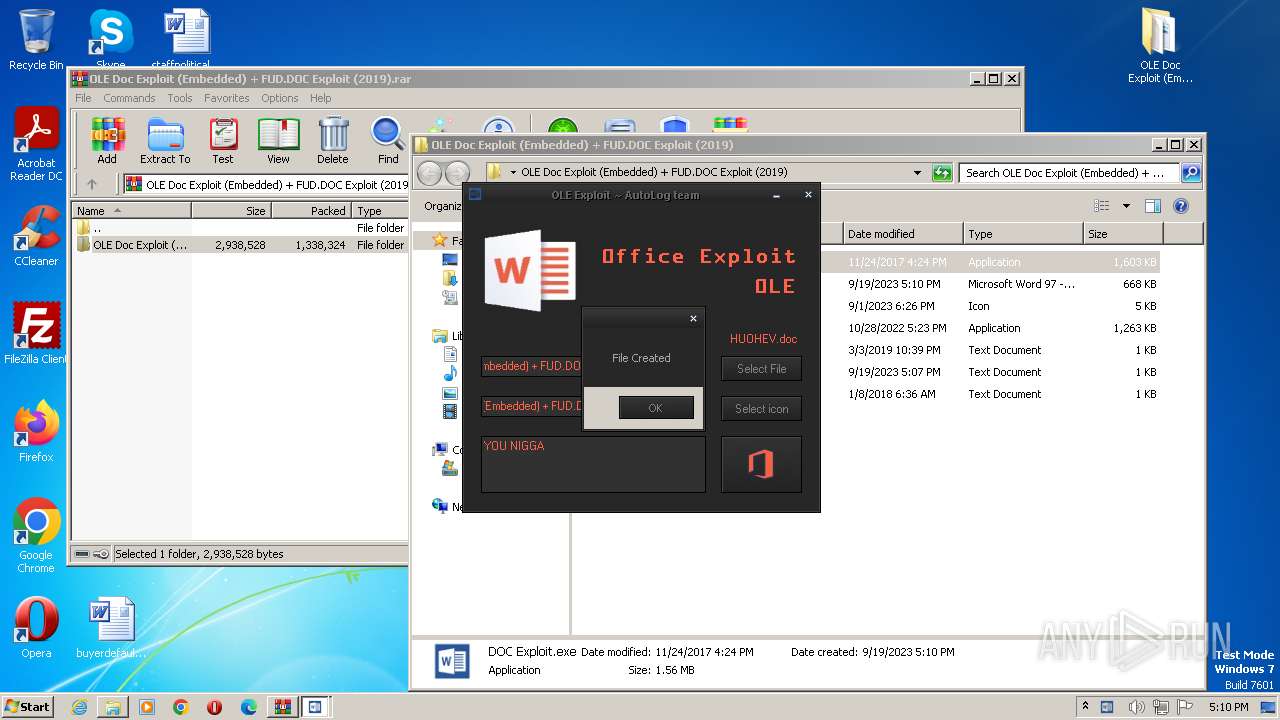
| File name: | OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019).rar |
| Full analysis: | https://app.any.run/tasks/3dceeb4d-a1fb-4f03-906f-9d4327afa163 |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2023, 16:09:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 99064FBD264386338781B95791CC07D8 |
| SHA1: | 6610E20A521F1A312D12AB31DE9567C3F0444C5F |
| SHA256: | 57D1C09E873734CC40387ADBCE98900A1895A91ACE75B22E2FDA5946B1D1AC3C |
| SSDEEP: | 24576:DnPEw14+/RVyCJHeYCWOLckc+QOvS4Ev4712t00g3:Dv1L/aCJHmghgjEvM2eL3 |
MALICIOUS
Application was dropped or rewritten from another process
- DOC Exploit.exe (PID: 2624)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- DOC Exploit.exe (PID: 2624)
- wmpnscfg.exe (PID: 2100)
Reads mouse settings
- DOC Exploit.exe (PID: 2624)
Reads the computer name
- DOC Exploit.exe (PID: 2624)
- wmpnscfg.exe (PID: 2100)
Reads the machine GUID from the registry
- DOC Exploit.exe (PID: 2624)
- wmpnscfg.exe (PID: 2100)
Manual execution by a user
- DOC Exploit.exe (PID: 2624)
- wmpnscfg.exe (PID: 2100)
- WINWORD.EXE (PID: 996)
The process uses the downloaded file
- WINWORD.EXE (PID: 2728)
- WINWORD.EXE (PID: 996)
Create files in a temporary directory
- DOC Exploit.exe (PID: 2624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\HUOHEV.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2624 | "C:\Users\admin\Desktop\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\DOC Exploit.exe" | C:\Users\admin\Desktop\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\DOC Exploit.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3496 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 587
Read events
14 885
Write events
515
Delete events
187
Modification events
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2624) DOC Exploit.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2624) DOC Exploit.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E00000007000000020000000000000006000000010000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
Executable files
9
Suspicious files
22
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2404.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3496.28483\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\putty.exe | executable | |
MD5:14080A3E4E877BE235F06509B2A4B6A9 | SHA256:35C9DF3A348AE805902A95AB8AD32A6D61EF85CA8249AE78F1077EDD2429FE6B | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\skinclas.msstyles | executable | |
MD5:719C51F5637D922E8416E23D0978B8CB | SHA256:6CF0BF46C9EE98FDE7EB4DBC0B147E33BABEABF9B1F50A4722E29DD57E95EF09 | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\afleizl | text | |
MD5:F4260729DB4446D4536EFA8C919443E4 | SHA256:6BFB221419332168B74FC5278ED762066244A796F4854AD9C45BBE7F20BB7C88 | |||
| 3496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3496.28483\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\Tutorial.txt | text | |
MD5:A747E8C5CBFDDB4A88E003BE113C5E3B | SHA256:22822224FCB76B6F525945423BE011533A257D6E0D597C9F735F9687B8012DB1 | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\autAD3F.tmp | binary | |
MD5:01A0C1BD8DEFC2DF7796D1E9542A2EBB | SHA256:2FD19F4D0636BE9A381C399792073BD49E67E8715254239EFC3ED729FE824865 | |||
| 3496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3496.28483\OLE Doc Exploit (Embedded) + FUD.DOC Exploit (2019)\JIK.ico | image | |
MD5:B6D111C14E0152B7F8B6F1221510BFDF | SHA256:C913ECF7D60FD4B9E1E85900E4DD4527EC732E4776262D4D96E3D07C01A80BCC | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\skin.dll | executable | |
MD5:29E1D5770184BF45139084BCED50D306 | SHA256:794987C4069286F797631F936C73B925C663C42D552AECA821106DFC7C7BA307 | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\autADDE.tmp | binary | |
MD5:5D576E372446A31B0B487E53A971089D | SHA256:4B4AB8243ED3BE25A58EB4BEF6CD27992640AE106734B8489472D22C73988AB6 | |||
| 2624 | DOC Exploit.exe | C:\Users\admin\AppData\Local\Temp\autAD9E.tmp | executable | |
MD5:29E1D5770184BF45139084BCED50D306 | SHA256:794987C4069286F797631F936C73B925C663C42D552AECA821106DFC7C7BA307 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |