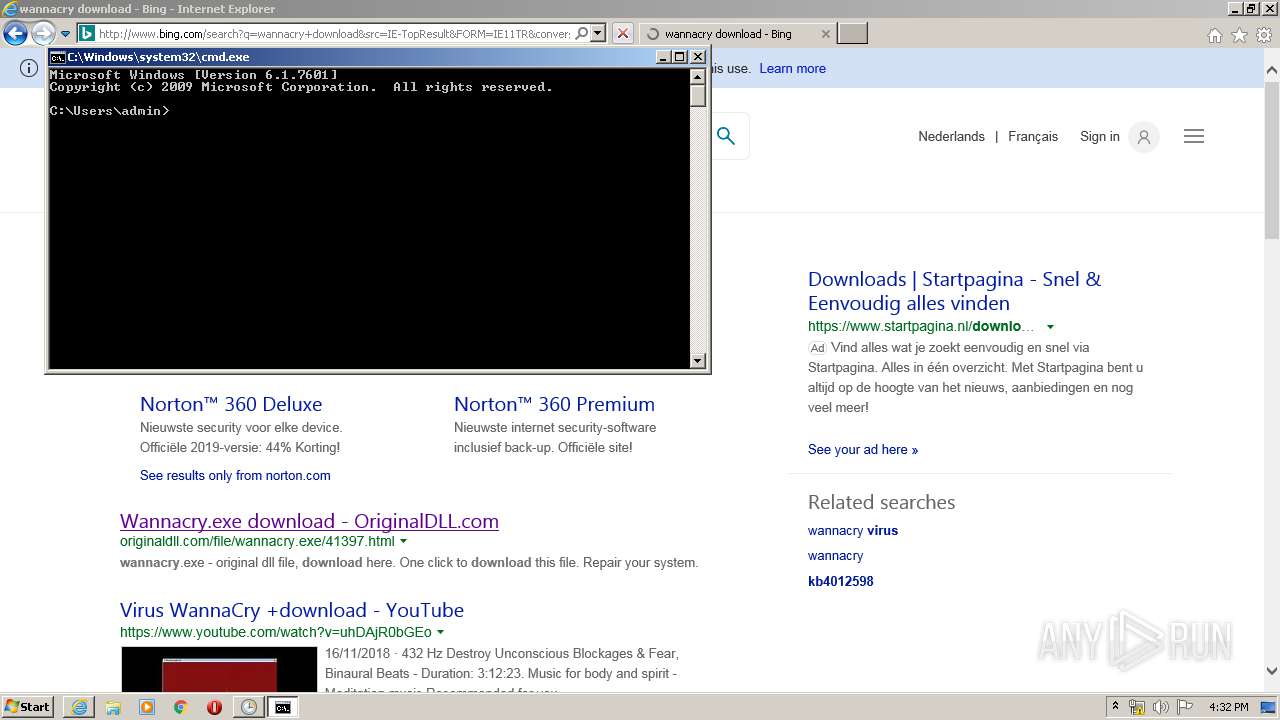
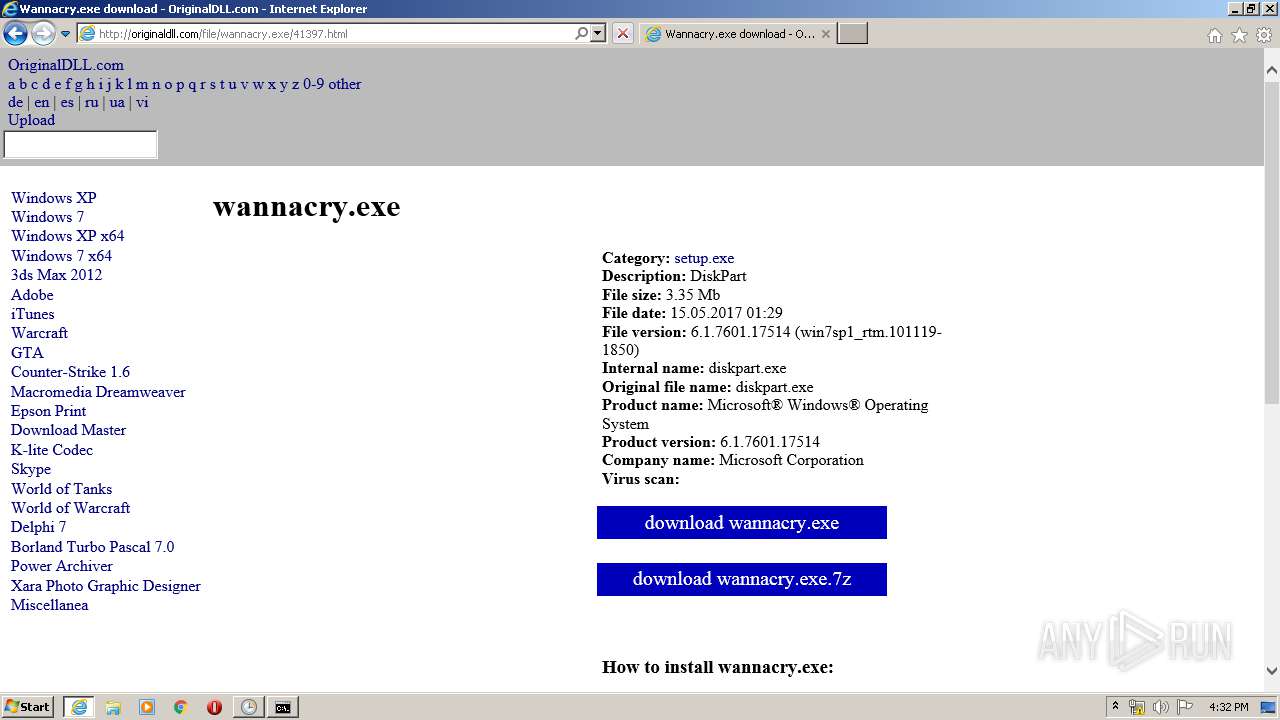
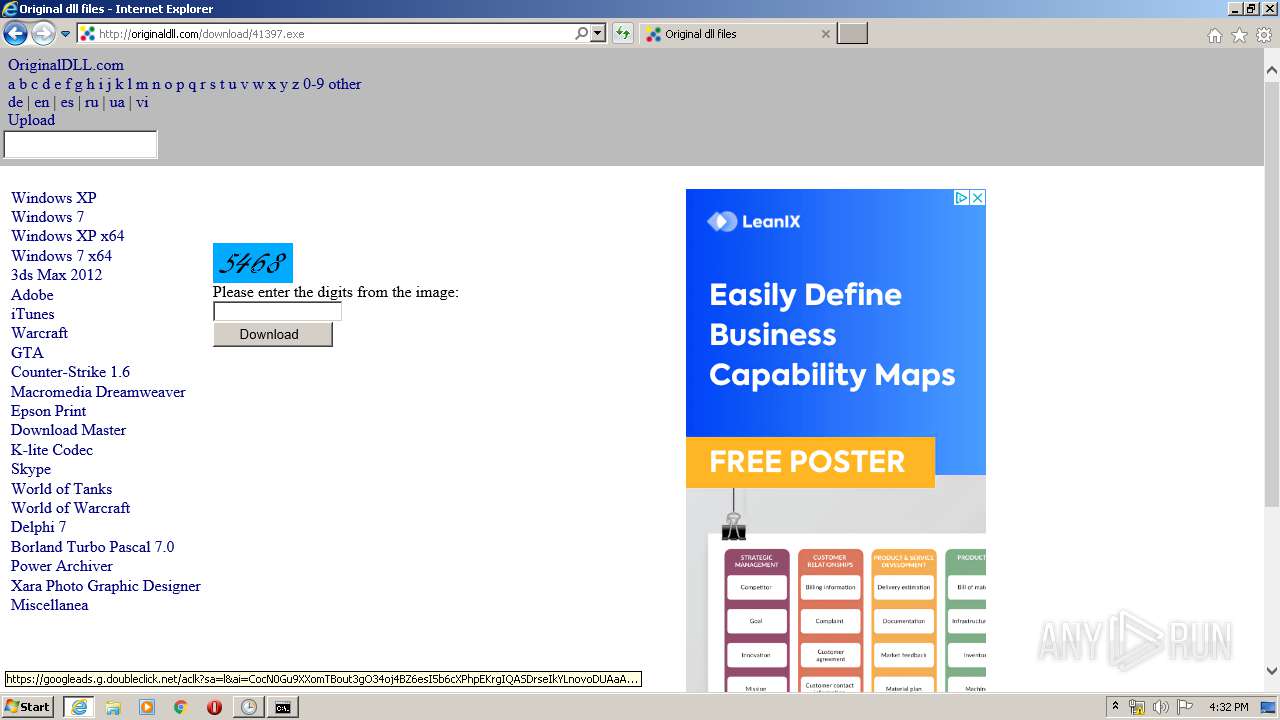
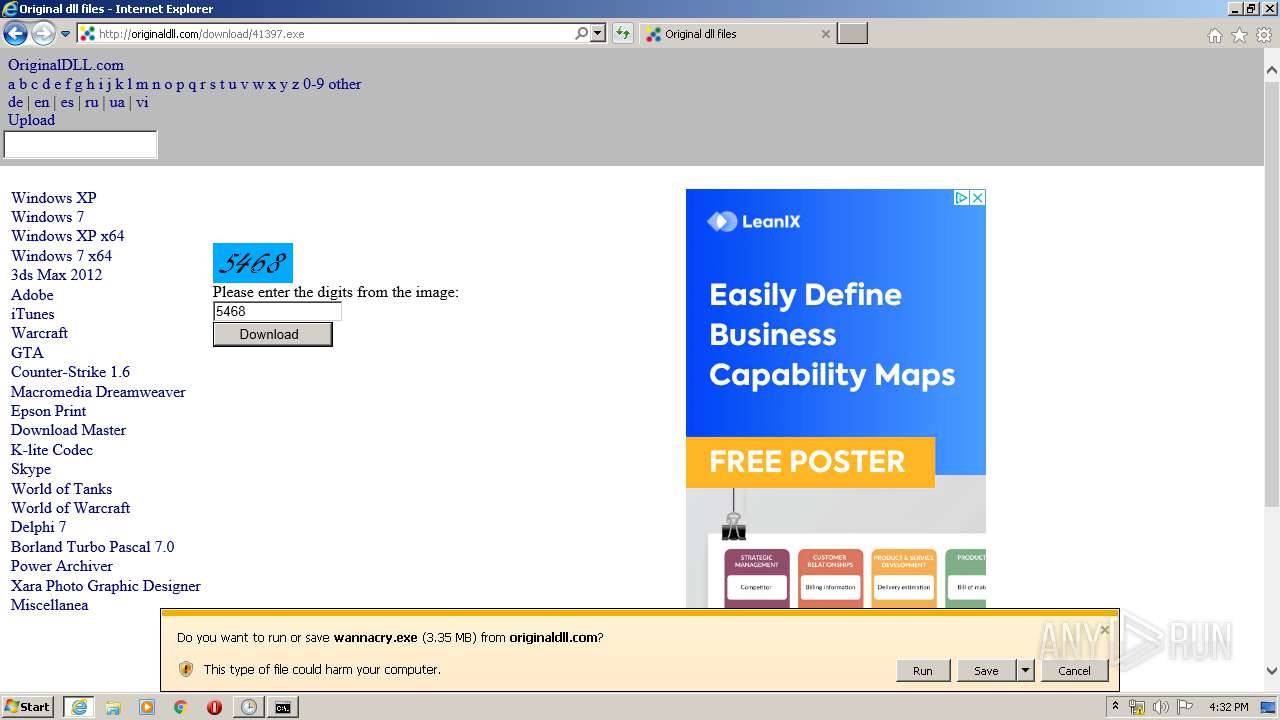
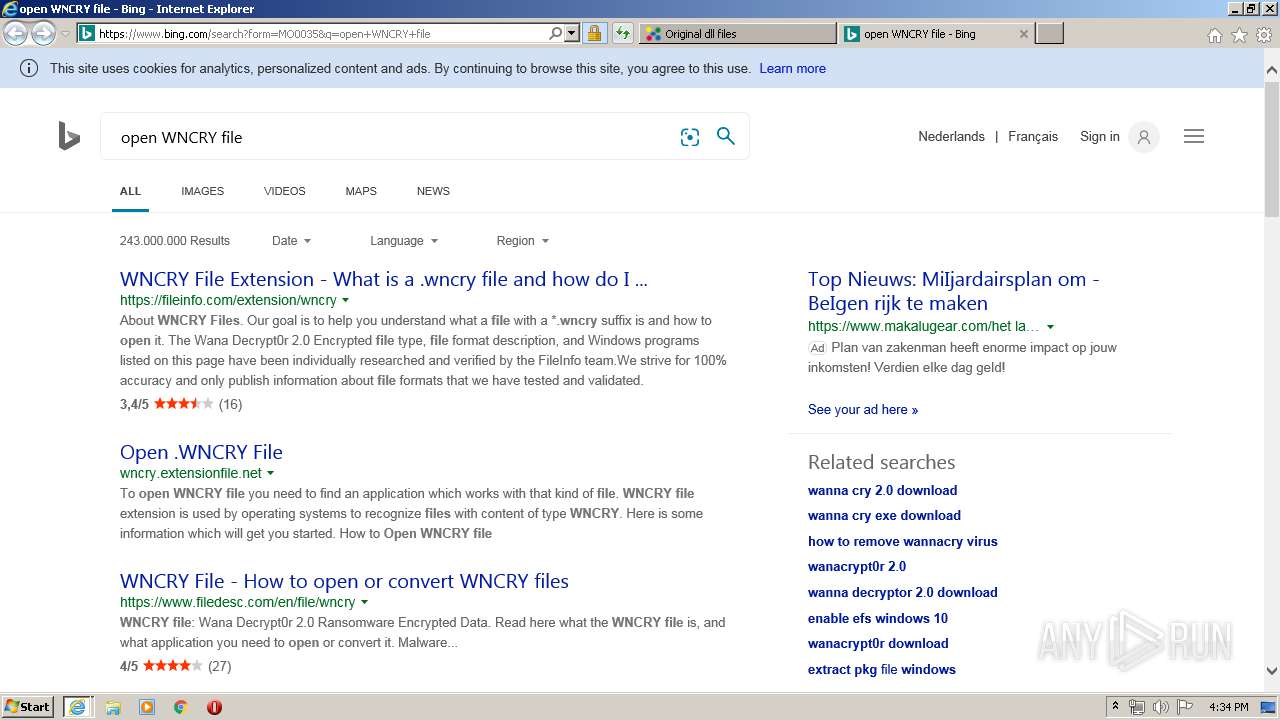
| URL: | https://hanime.tv |
| Full analysis: | https://app.any.run/tasks/50e71dda-47e9-44e5-9ac2-8ef9a645c6cb |
| Verdict: | Malicious activity |
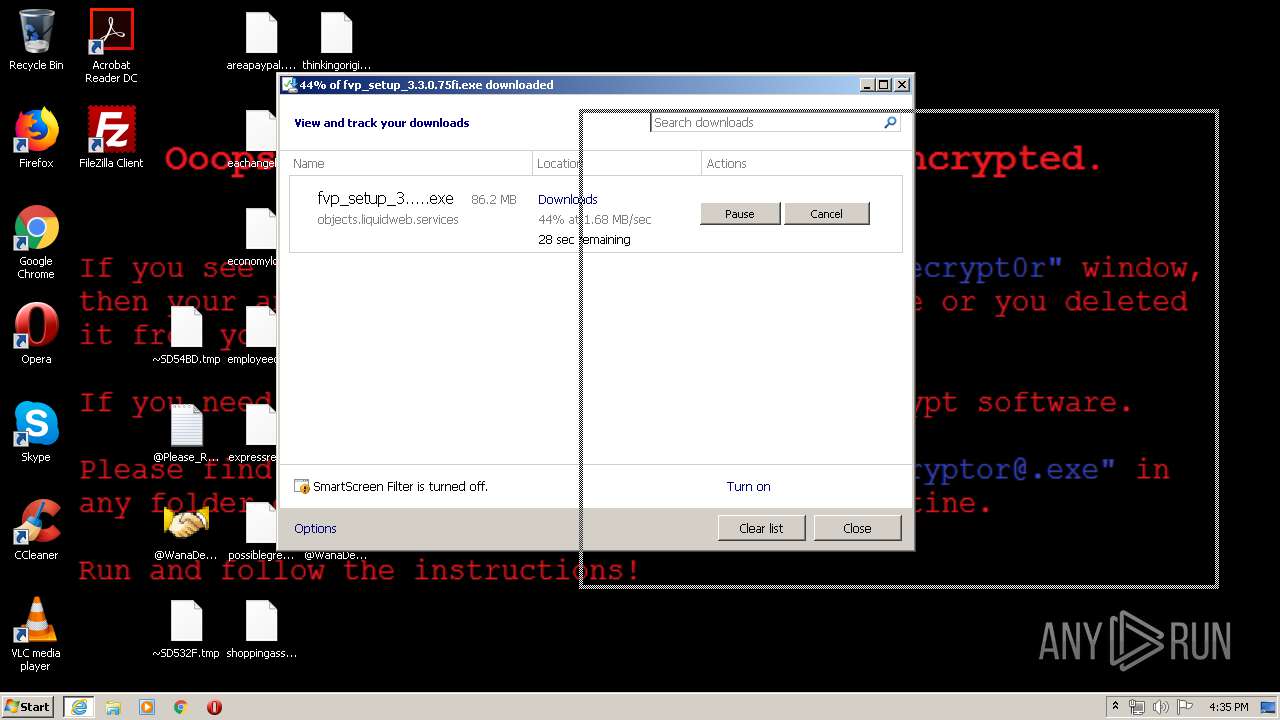
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 27, 2020, 16:30:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CEFFF6E96D1E219D93AC6C901F66CBD6 |
| SHA1: | D5BA35EE70936DD3BAA00D037D8CF5D2E3C75EAE |
| SHA256: | 57C3C2DBFC1A96A8D17FFBBF14C65BD9AC660652B3550295FE48566D6C1DF3AF |
| SSDEEP: | 3:N846LRTn:24gRT |
MALICIOUS
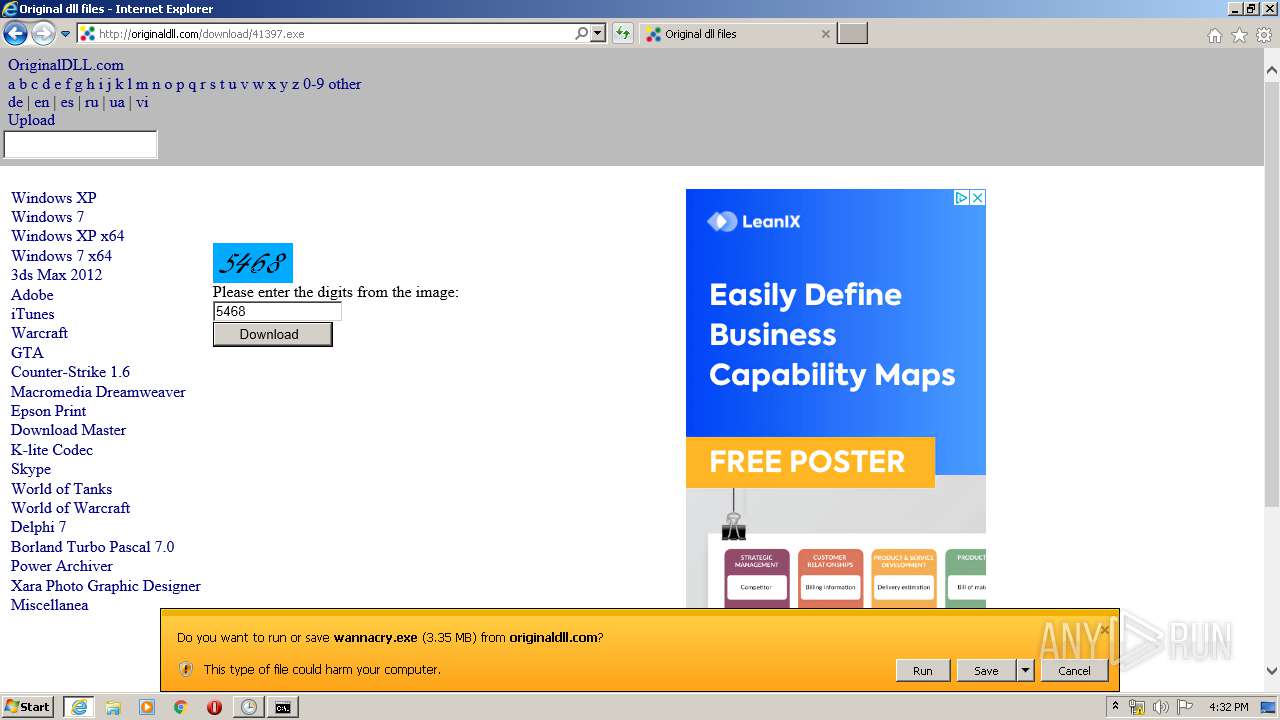
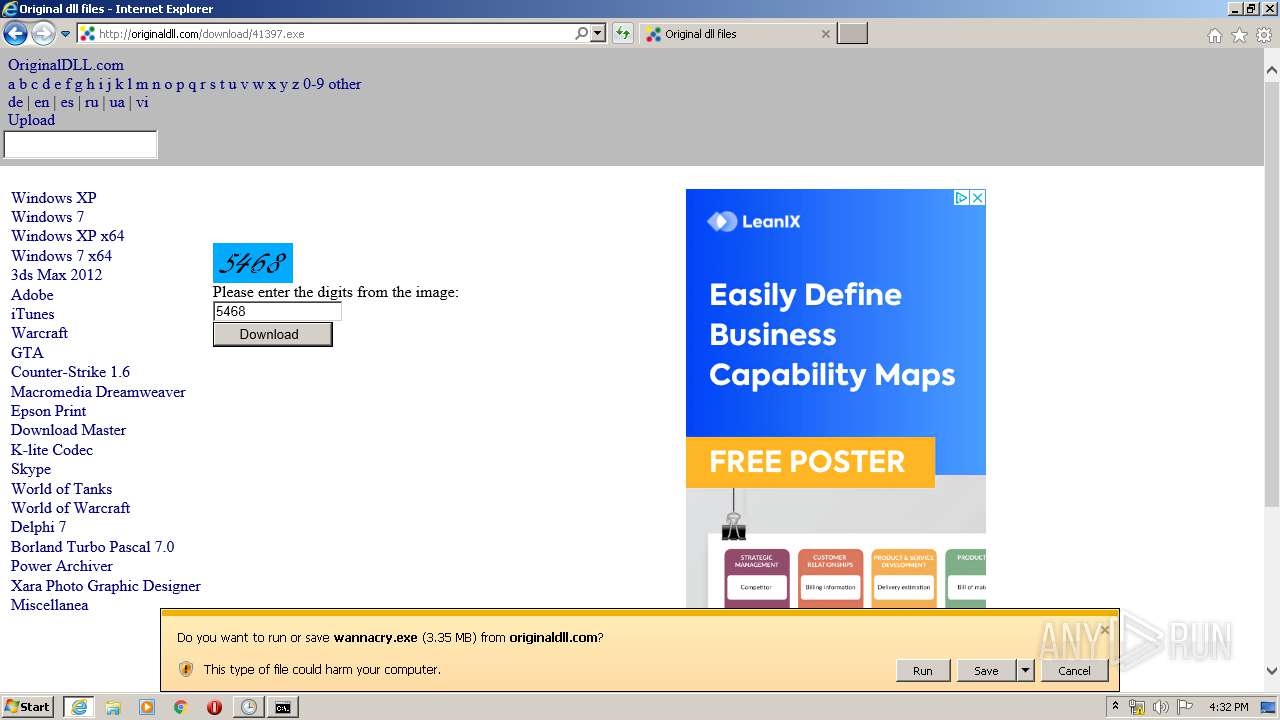
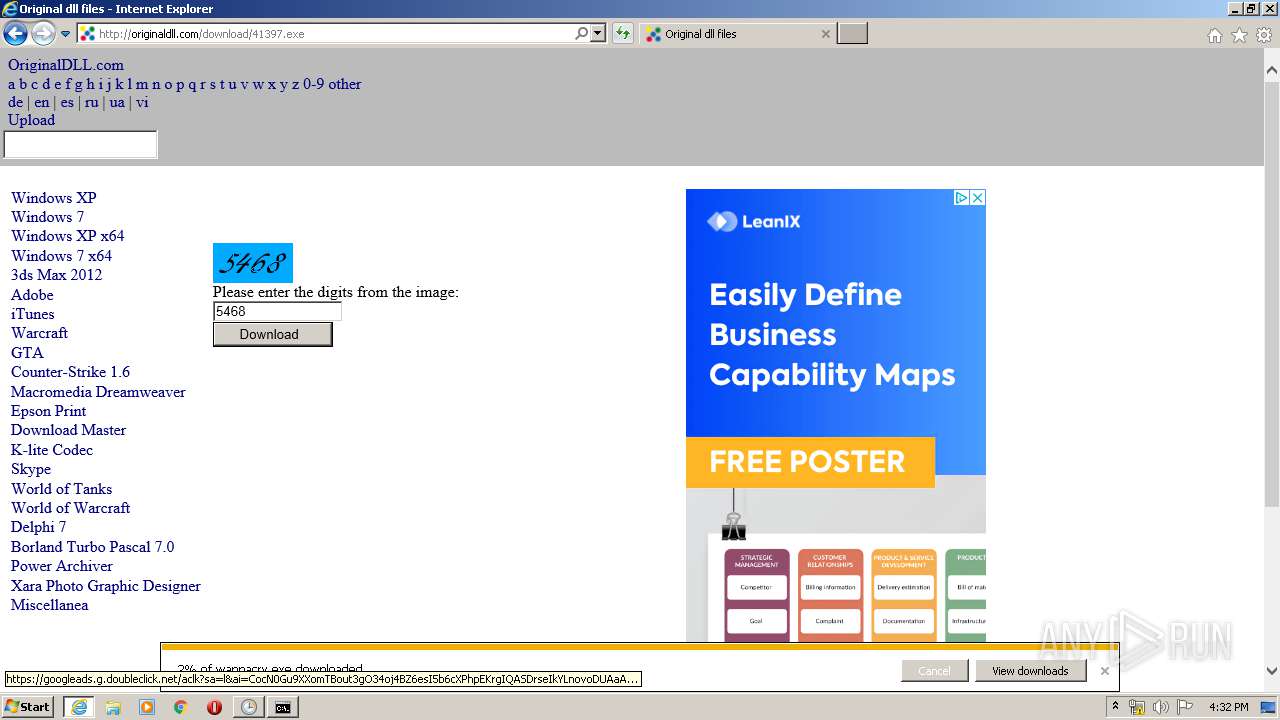
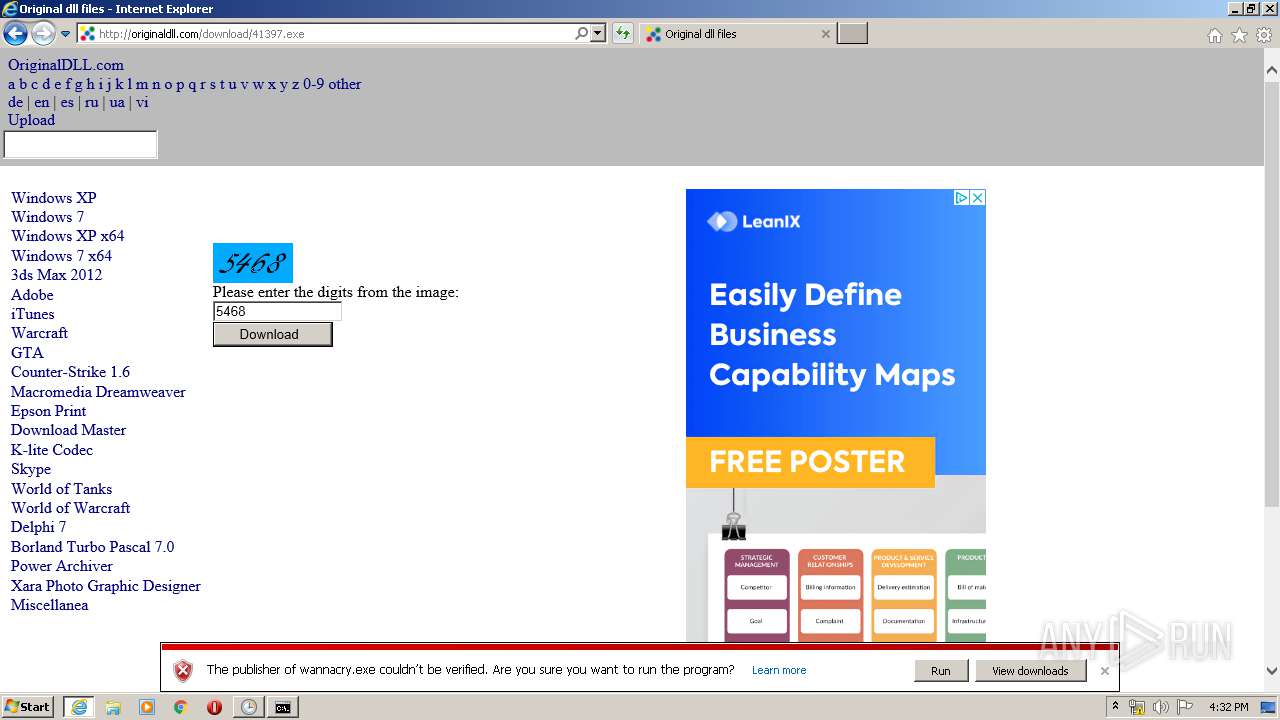
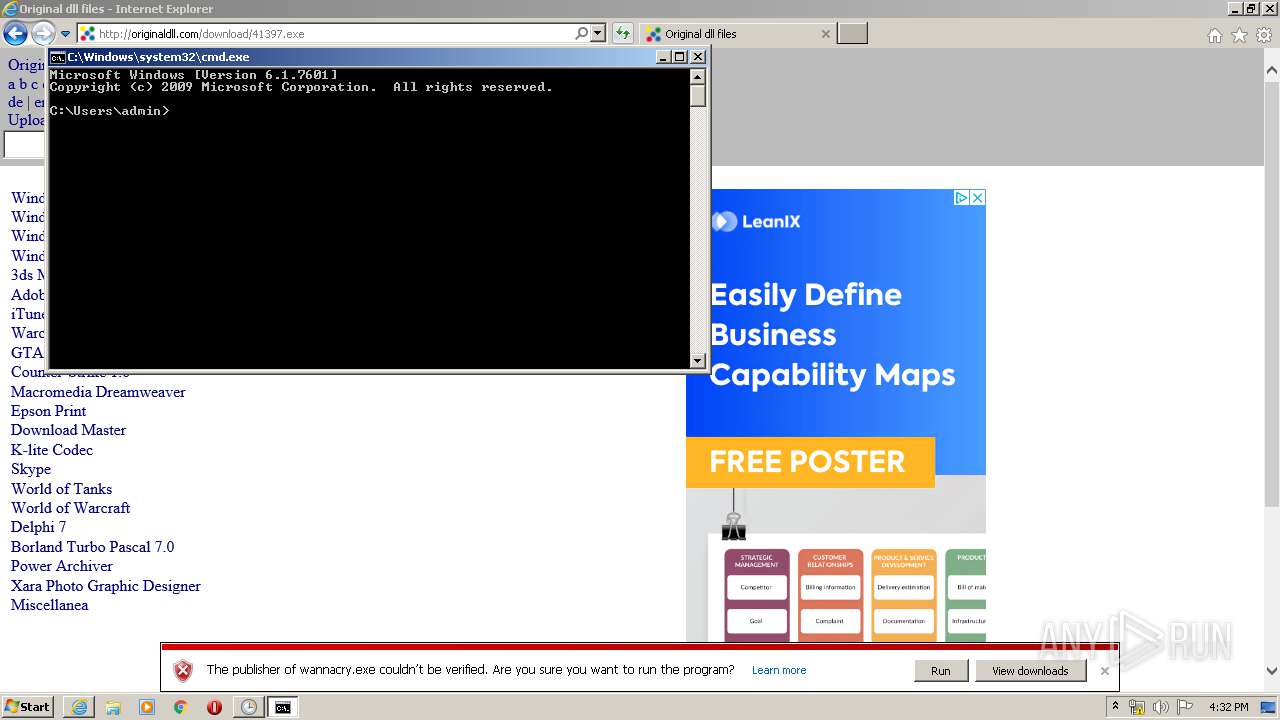
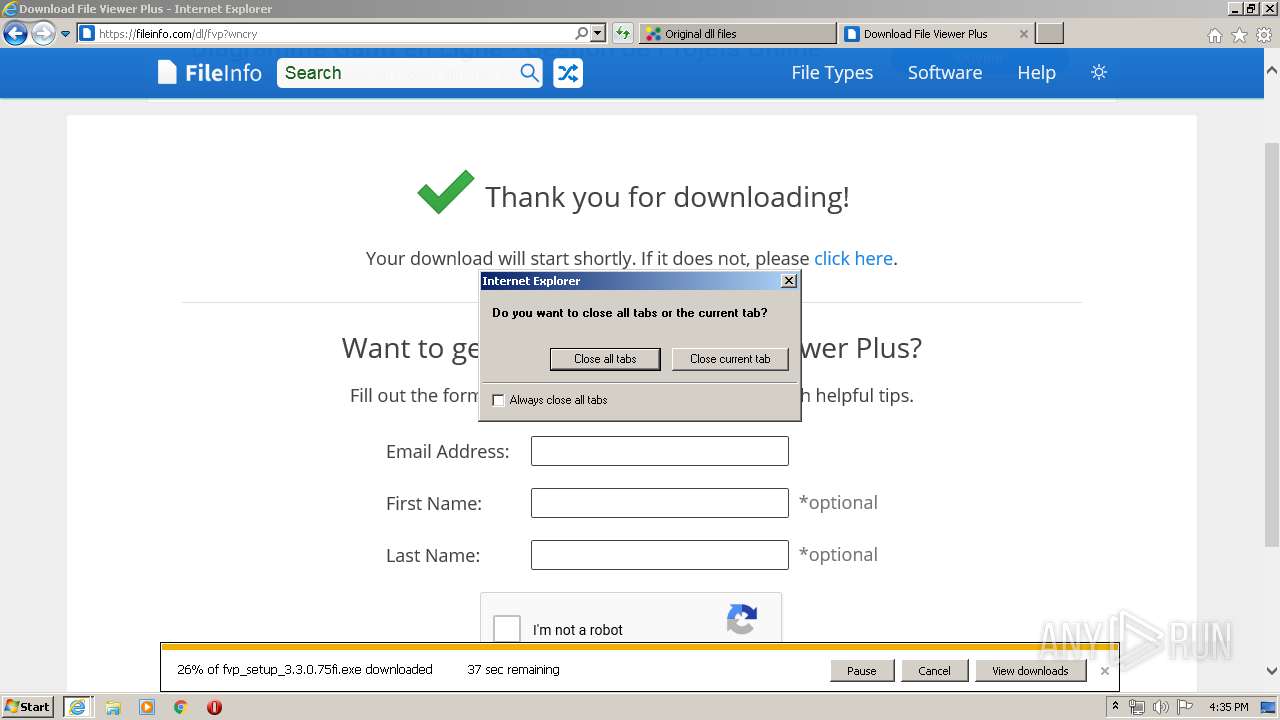
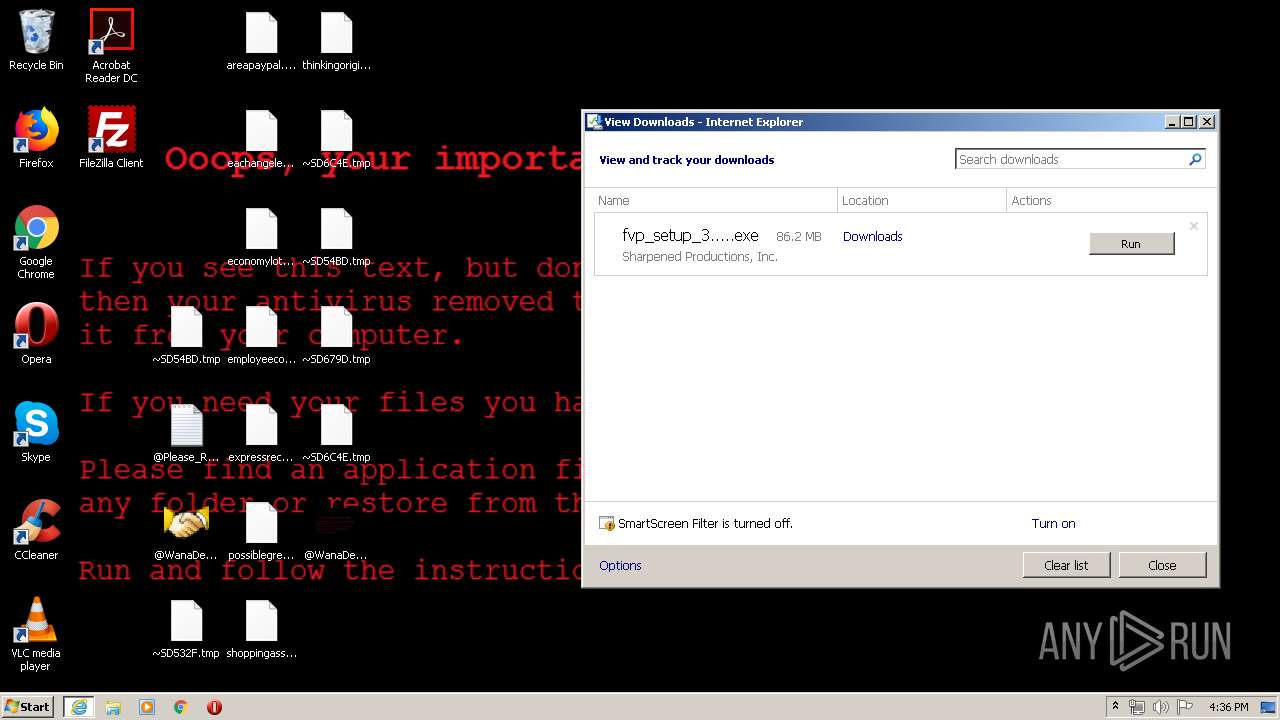
Downloads executable files from the Internet
- iexplore.exe (PID: 2824)
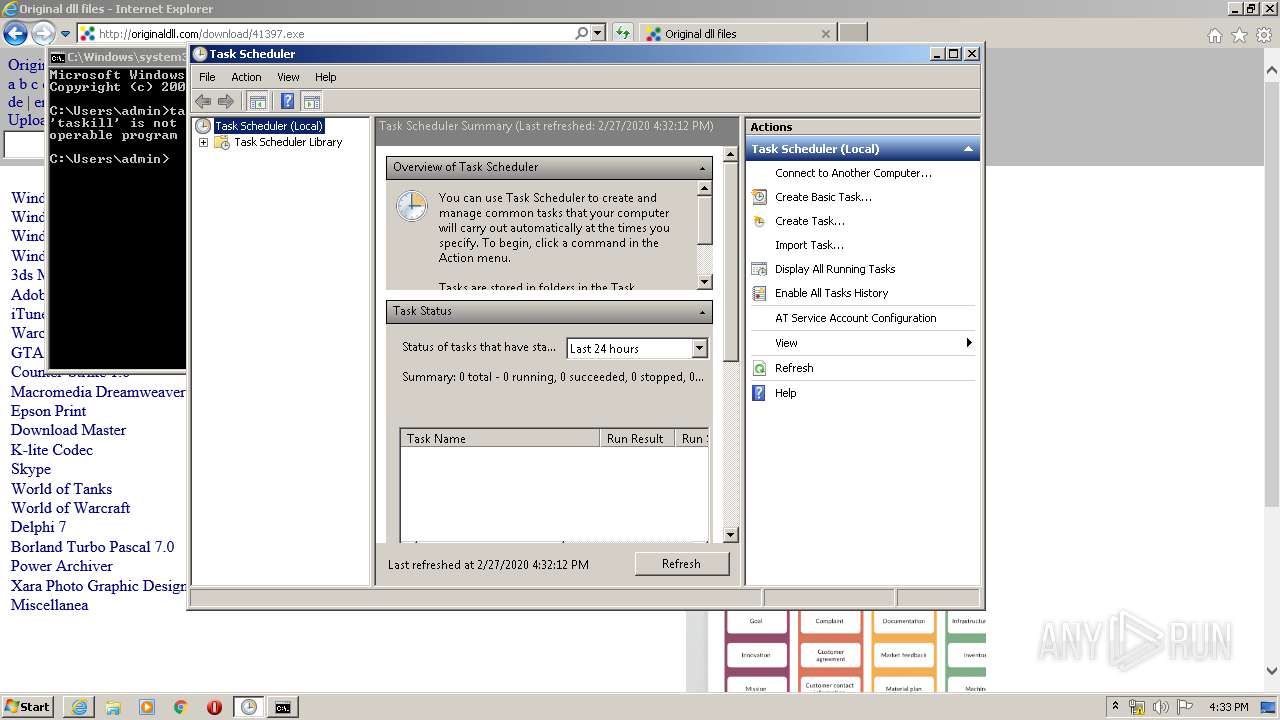
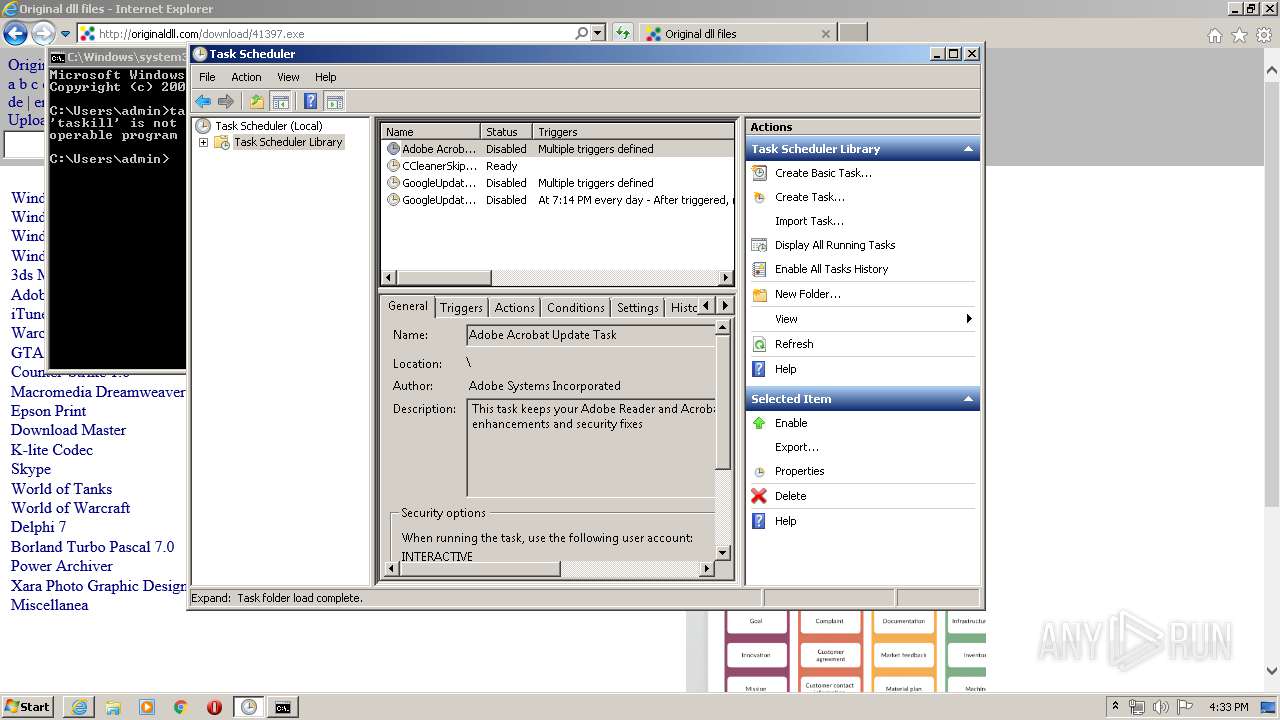
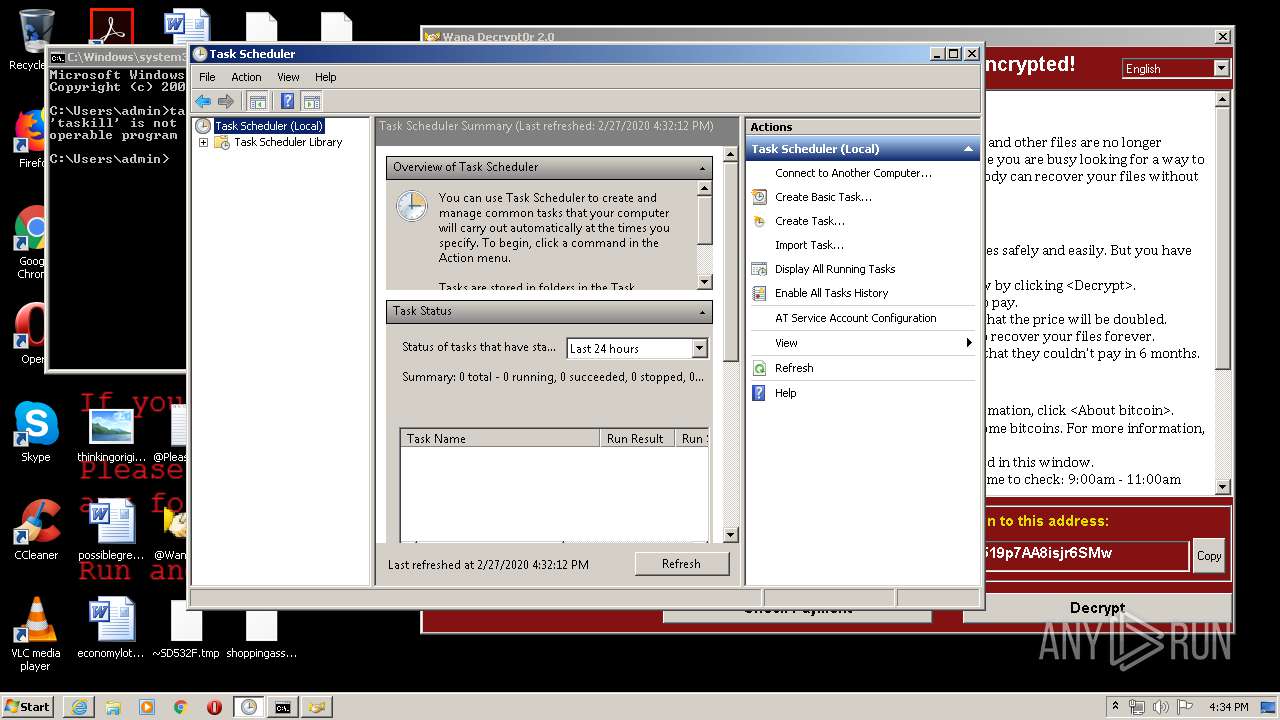
Loads the Task Scheduler COM API
- mmc.exe (PID: 676)
- wbengine.exe (PID: 1912)
Application was dropped or rewritten from another process
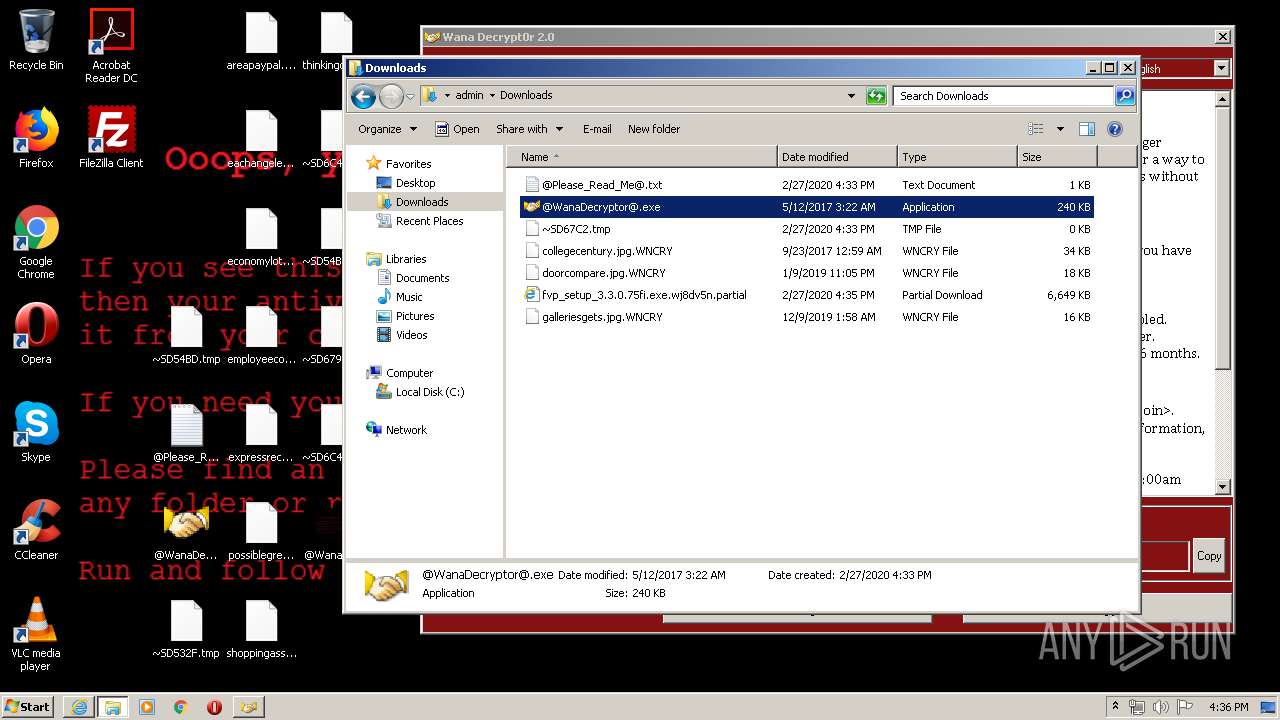
- wannacry.exe (PID: 2872)
- taskdl.exe (PID: 3152)
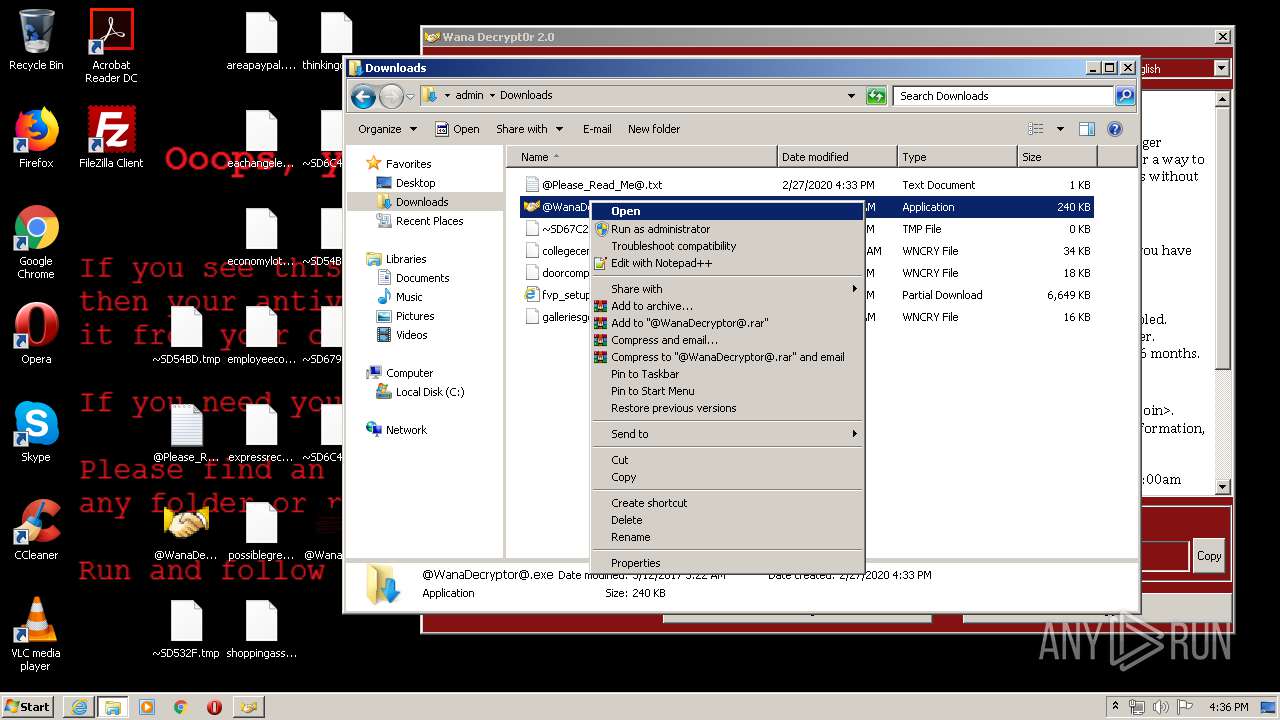
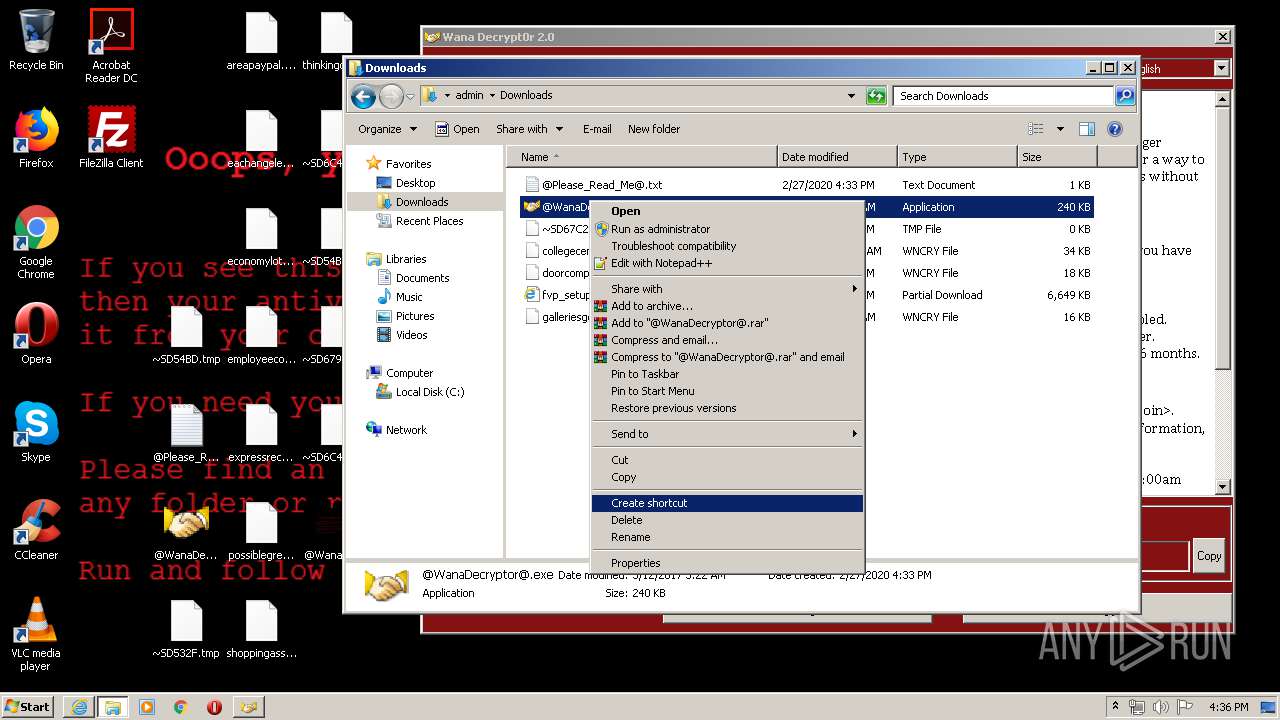
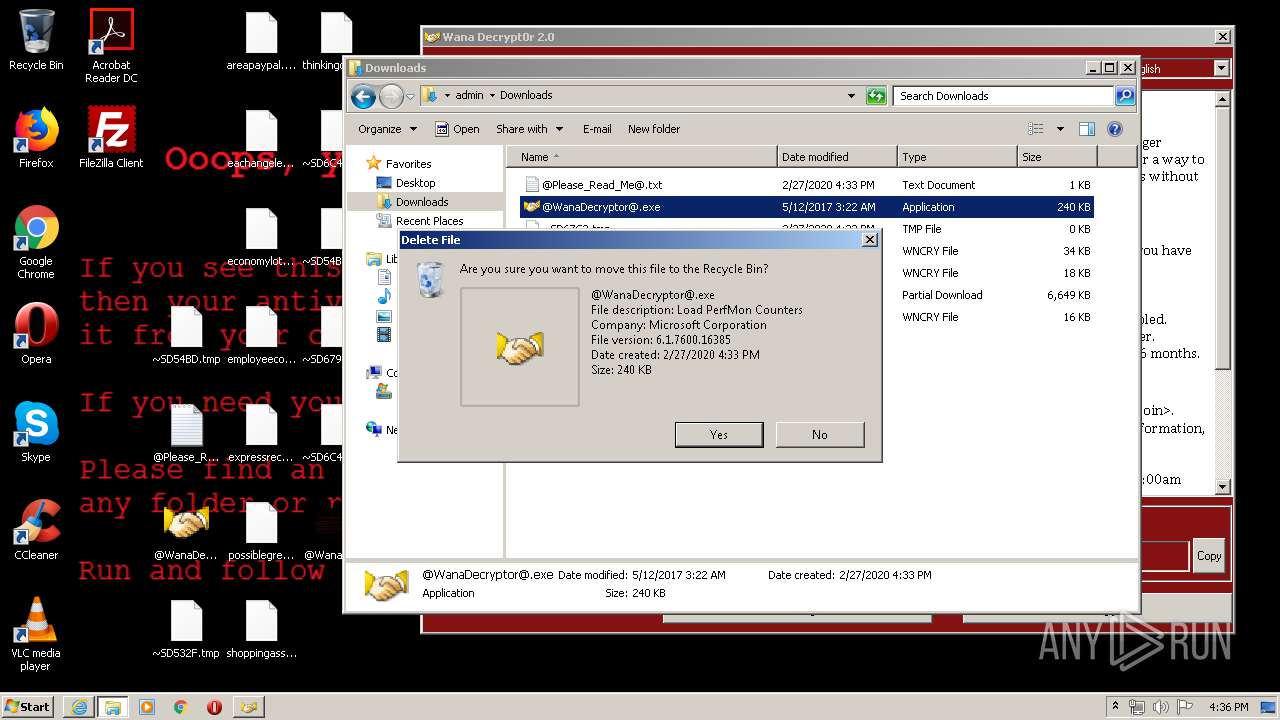
- @WanaDecryptor@.exe (PID: 3908)
- taskhsvc.exe (PID: 180)
- @WanaDecryptor@.exe (PID: 3016)
- taskdl.exe (PID: 2972)
- @WanaDecryptor@.exe (PID: 440)
- taskdl.exe (PID: 3176)
- @WanaDecryptor@.exe (PID: 3388)
- taskdl.exe (PID: 3548)
- @WanaDecryptor@.exe (PID: 1876)
- taskdl.exe (PID: 3172)
- @WanaDecryptor@.exe (PID: 2740)
- @WanaDecryptor@.exe (PID: 3776)
- taskdl.exe (PID: 2208)
Writes file to Word startup folder
- wannacry.exe (PID: 2872)
Modifies files in Chrome extension folder
- wannacry.exe (PID: 2872)
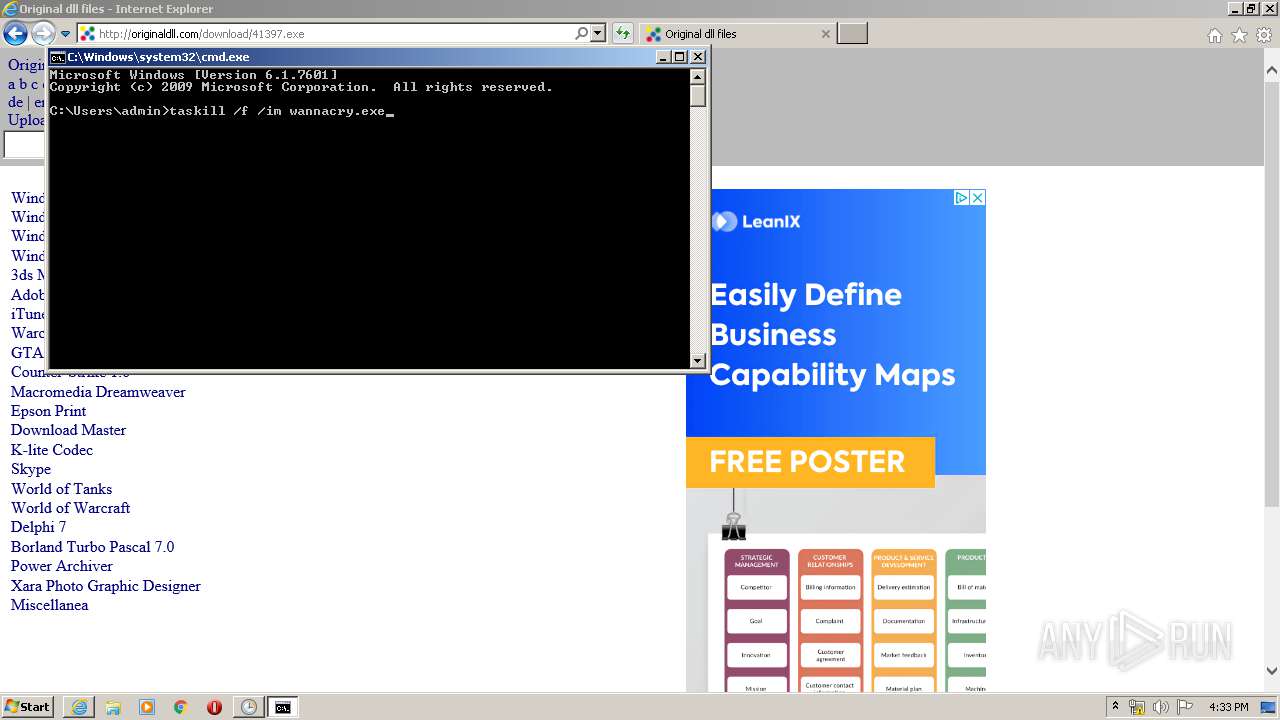
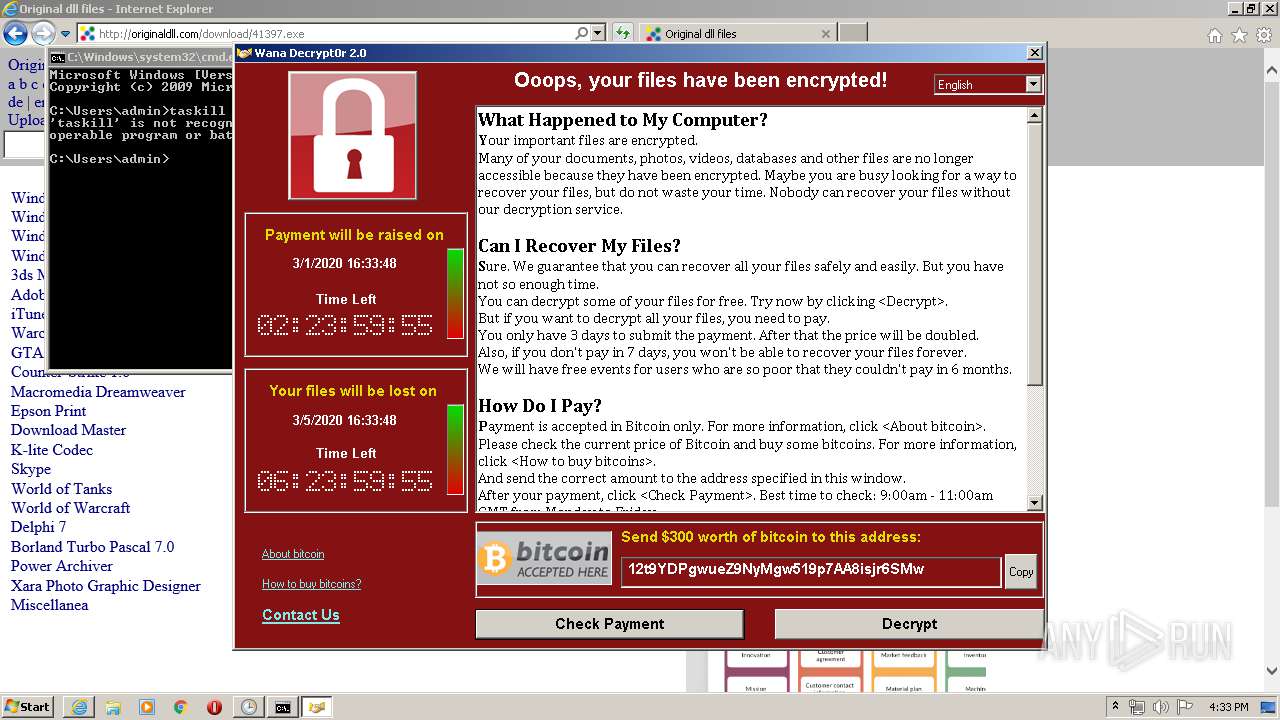
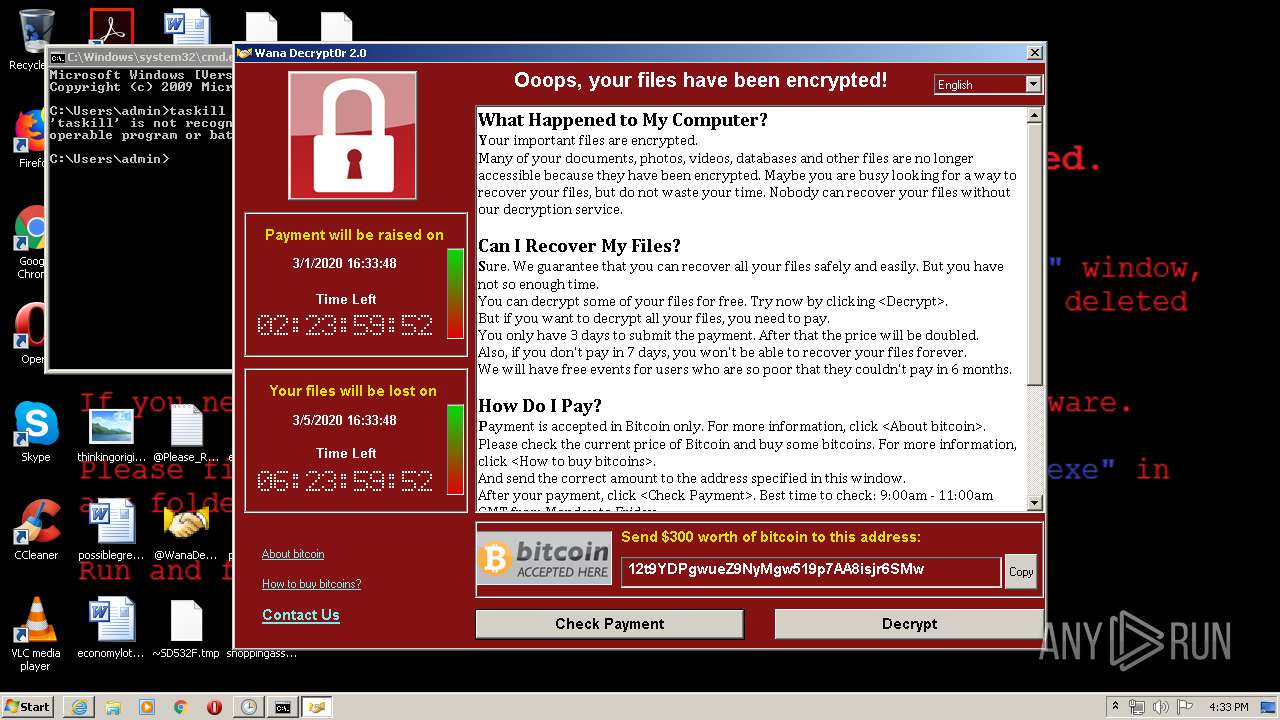
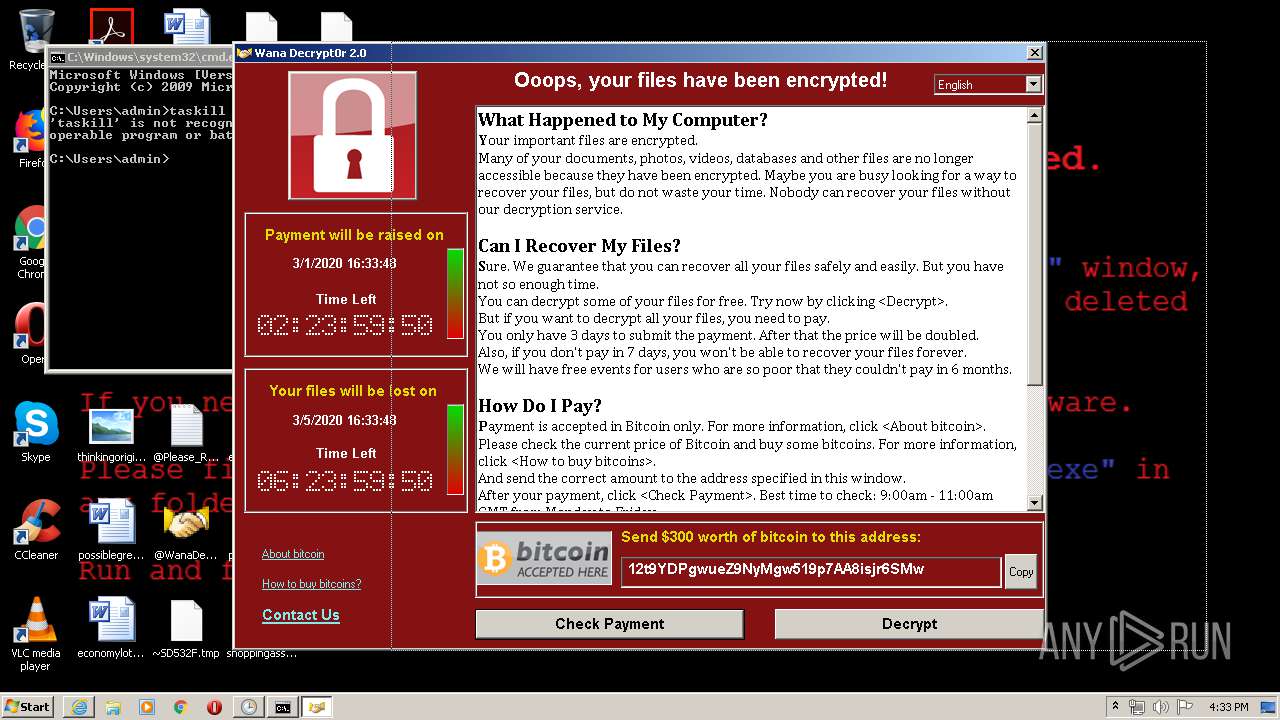
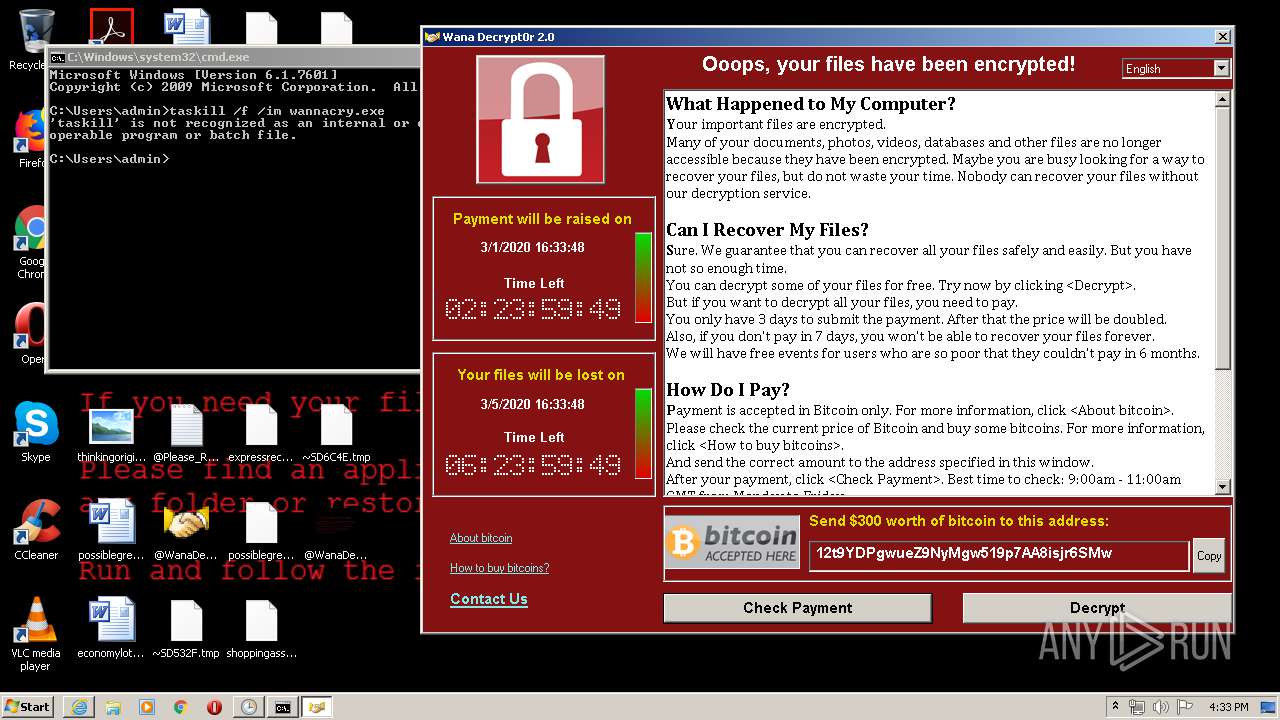
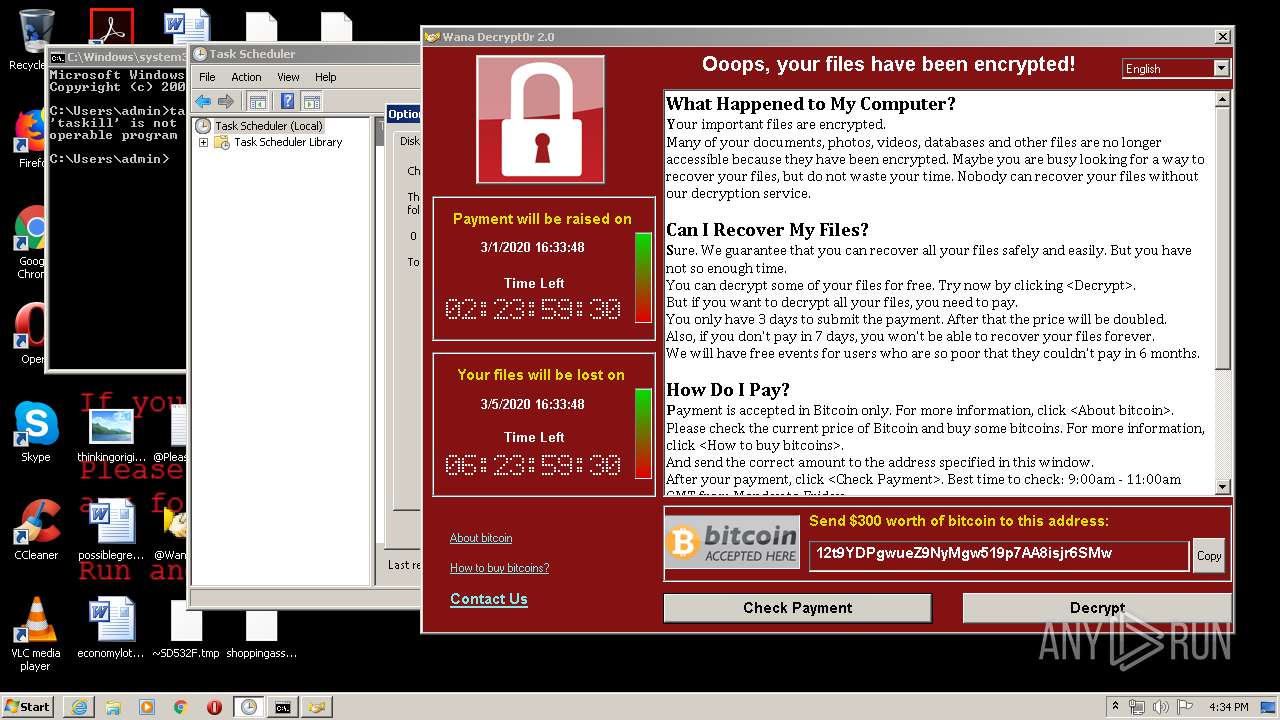
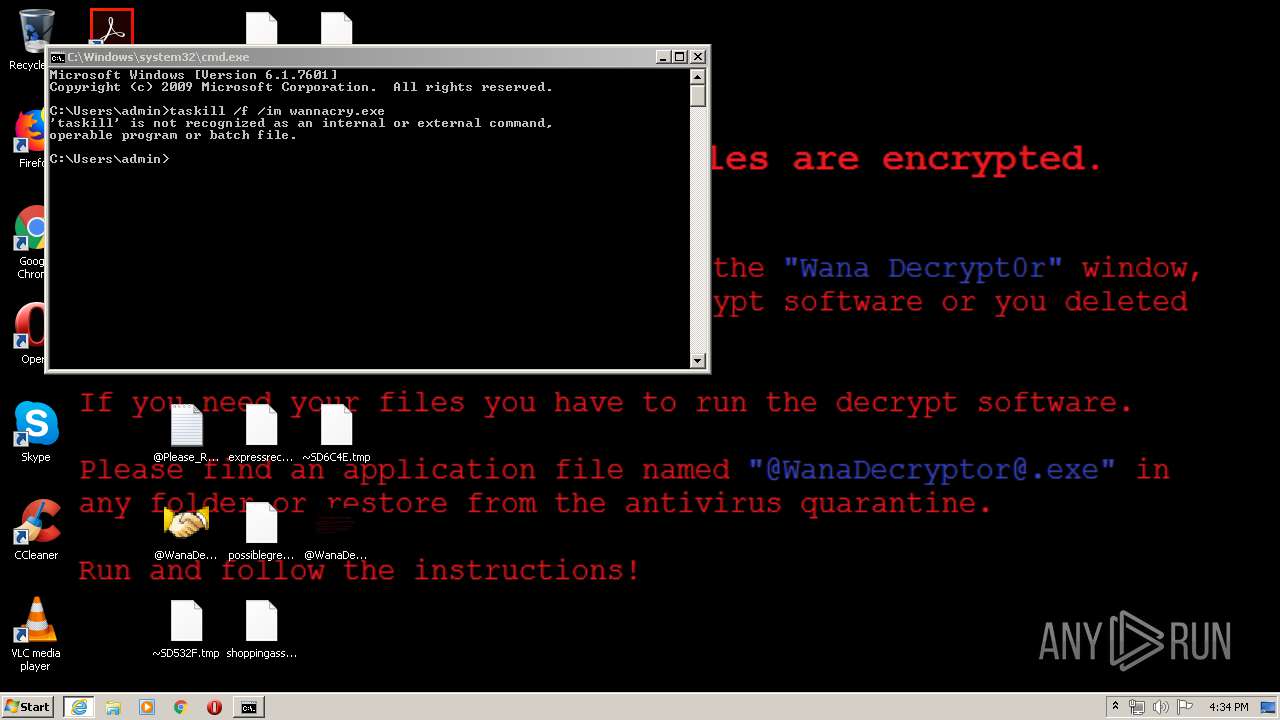
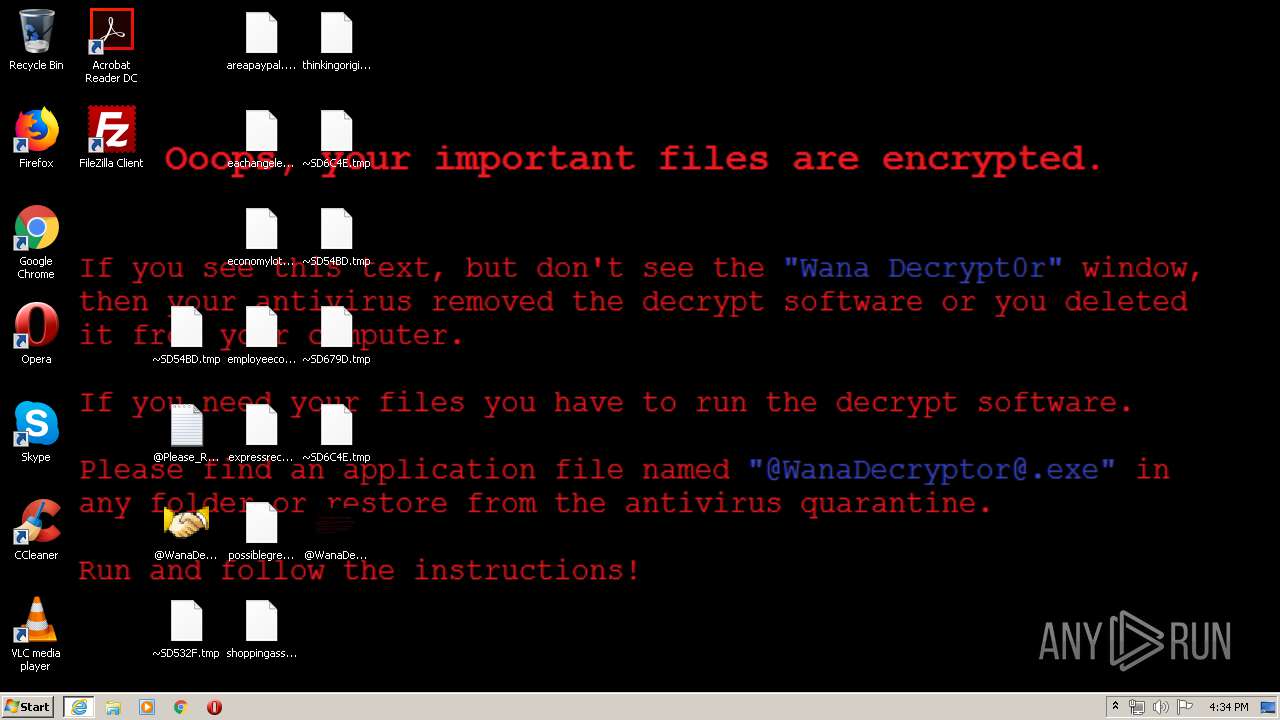
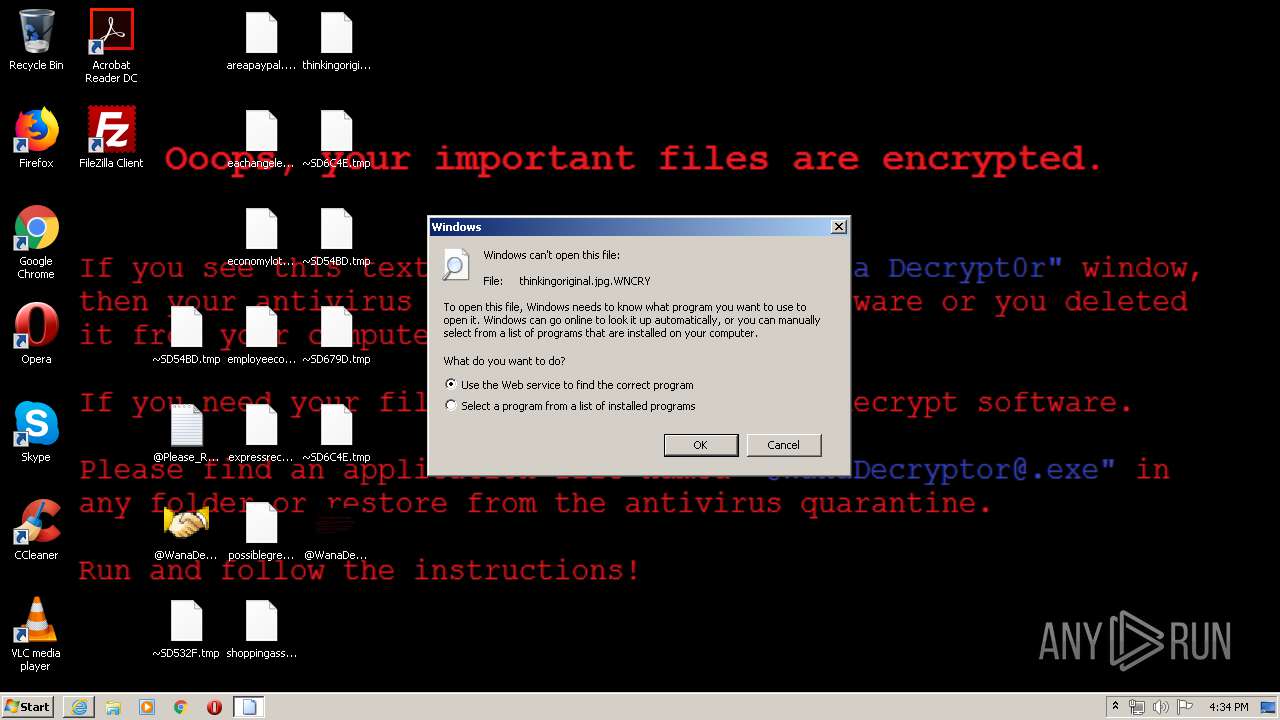
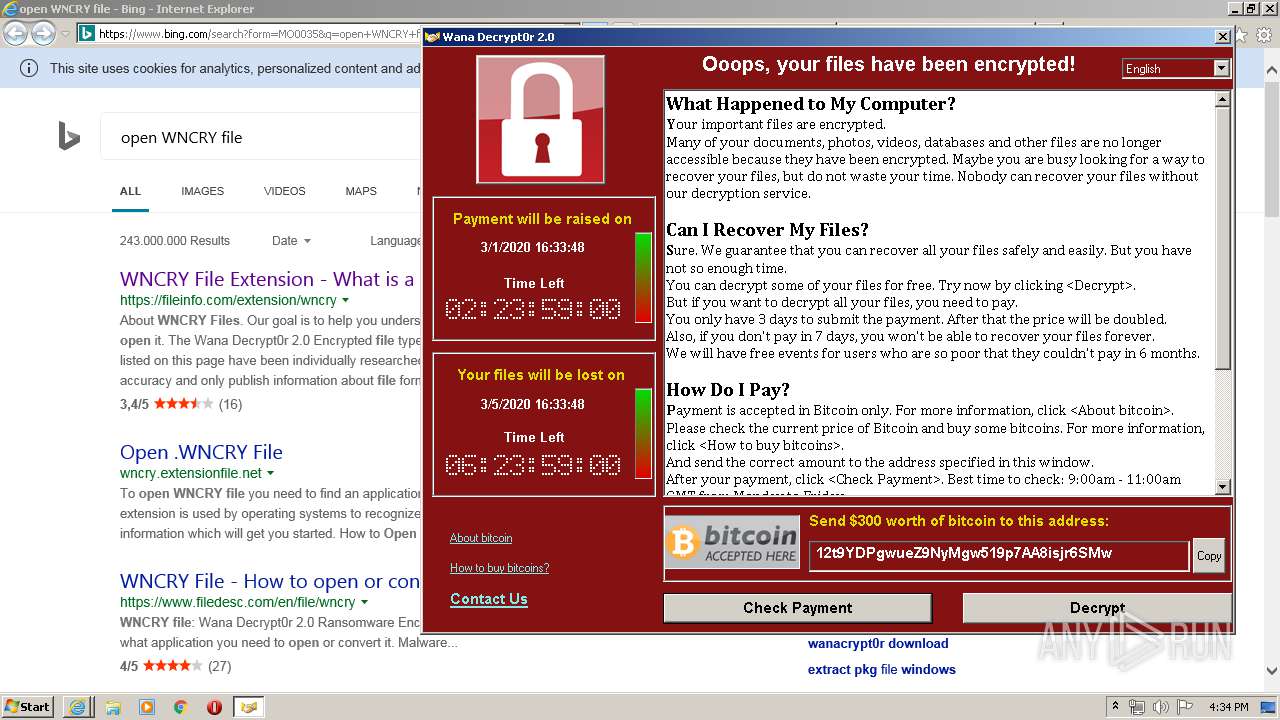
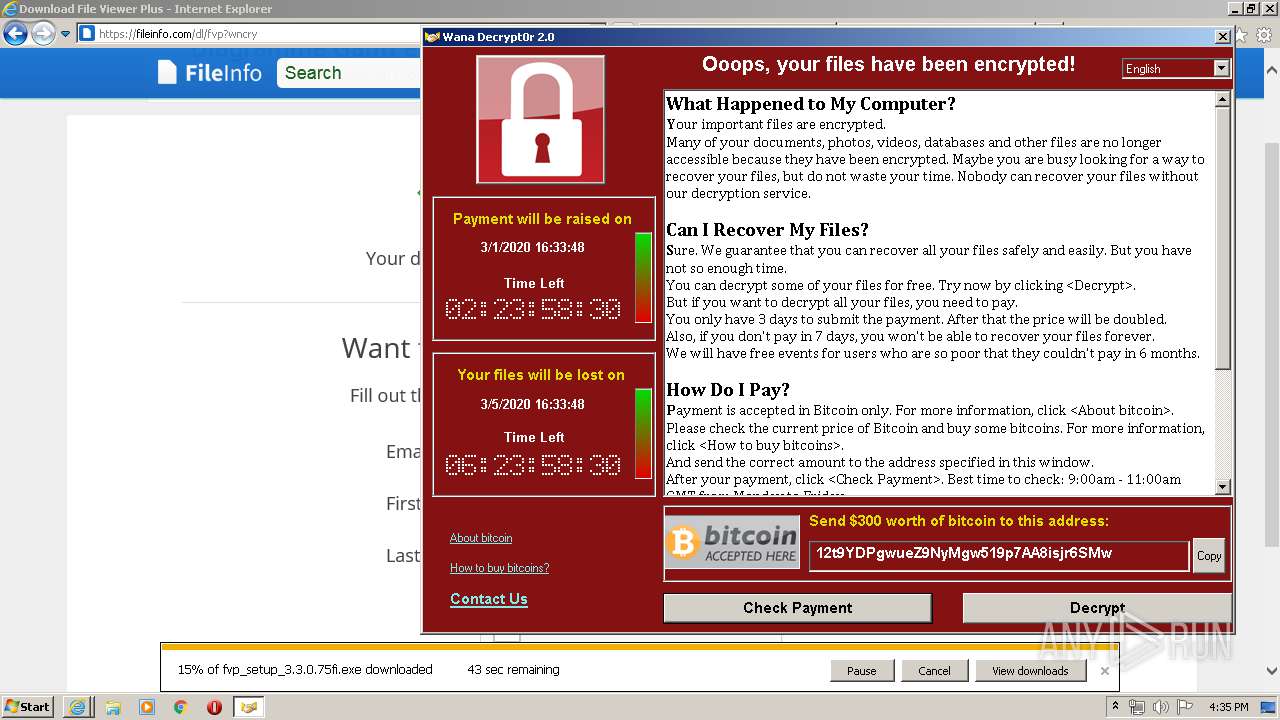
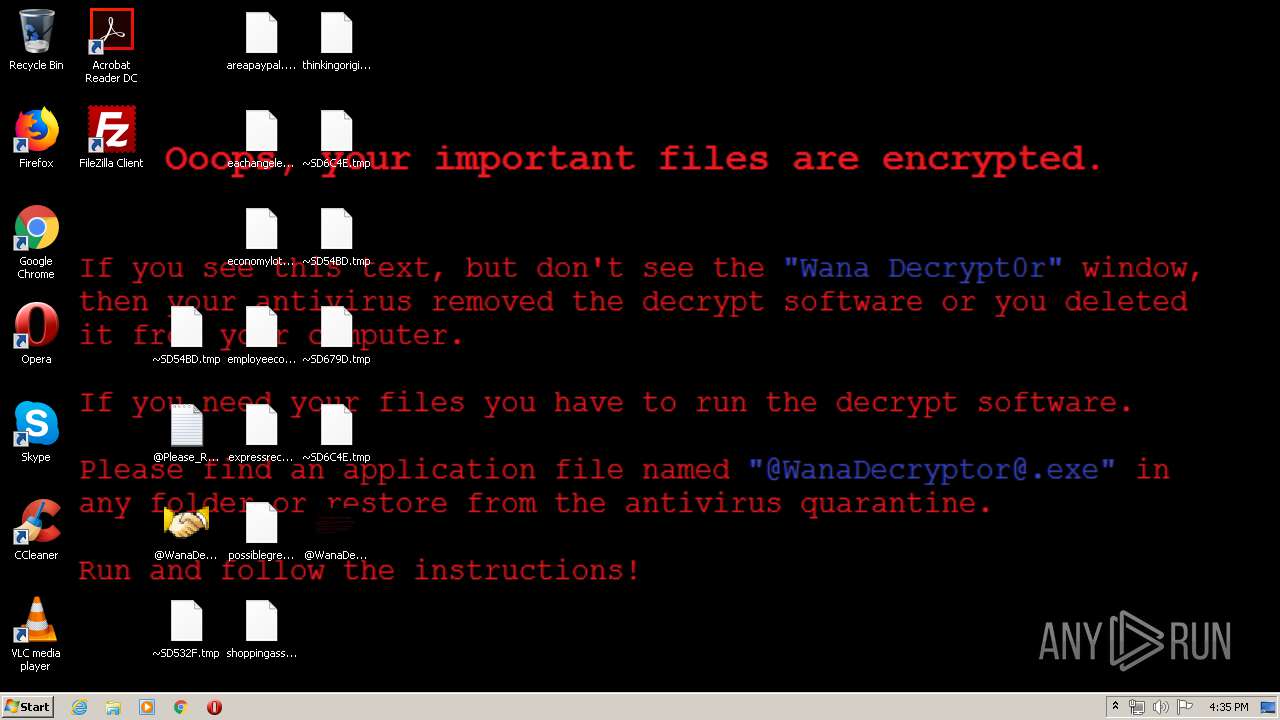
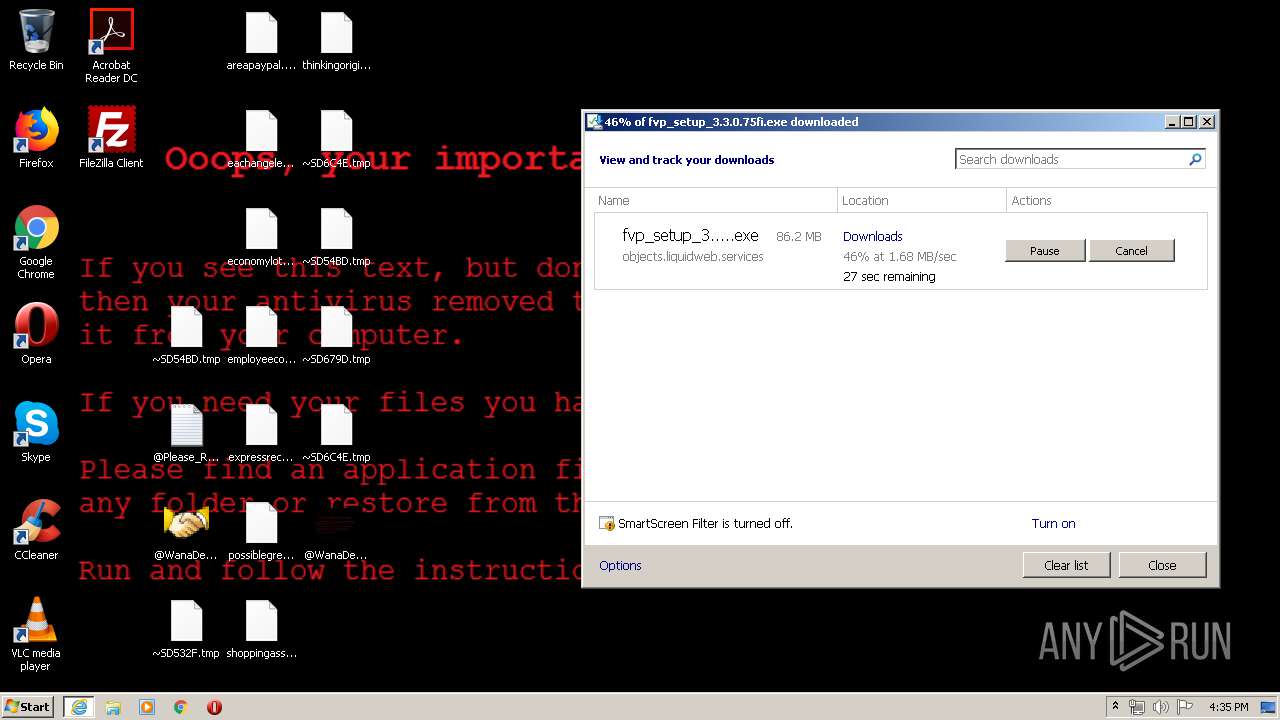
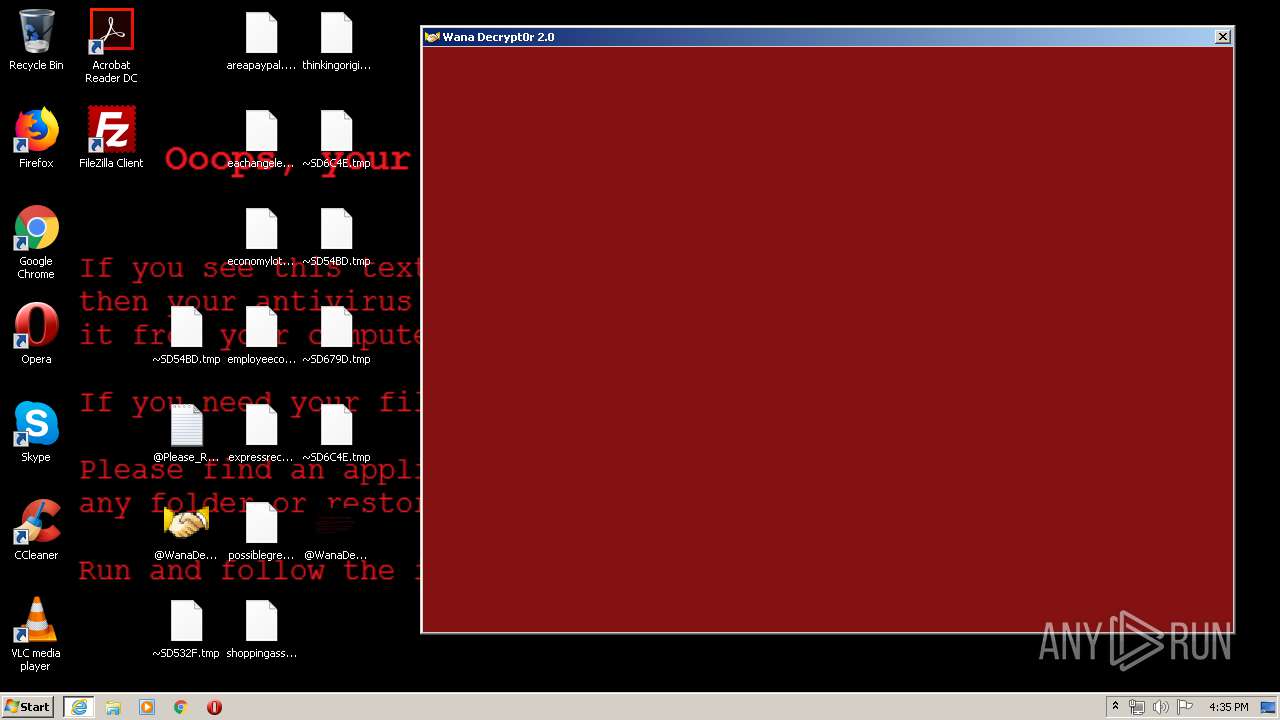
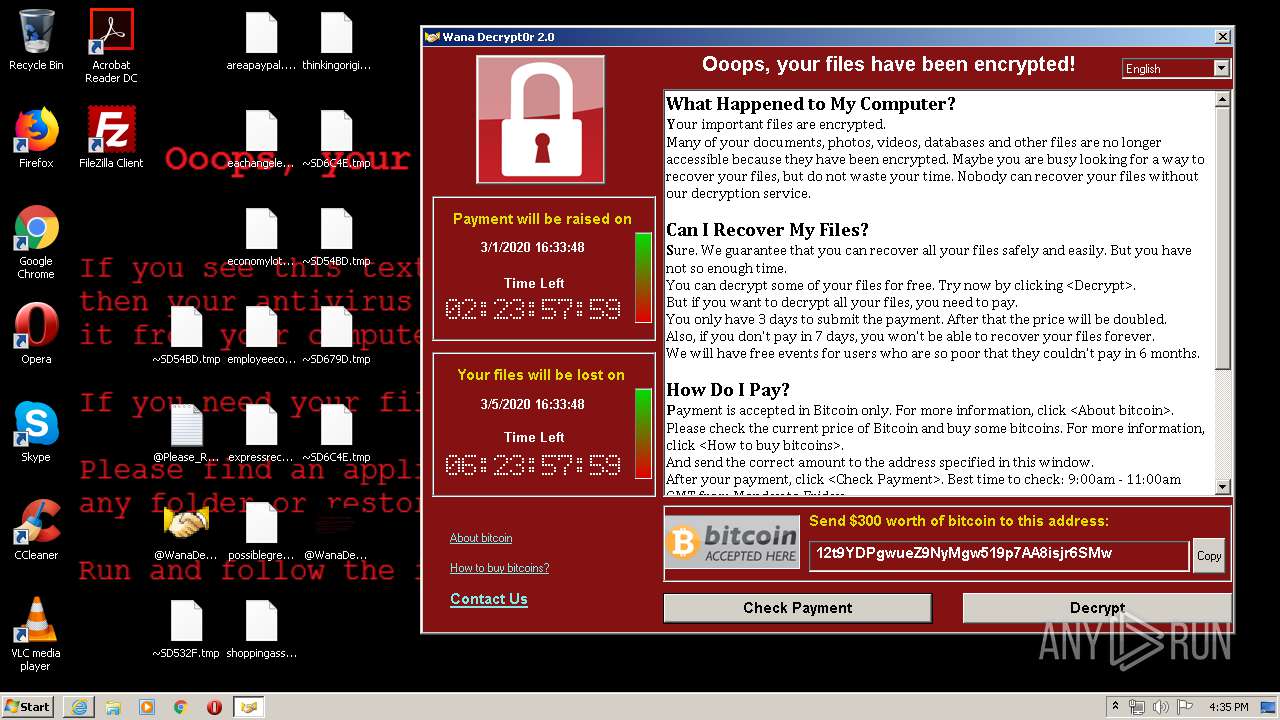
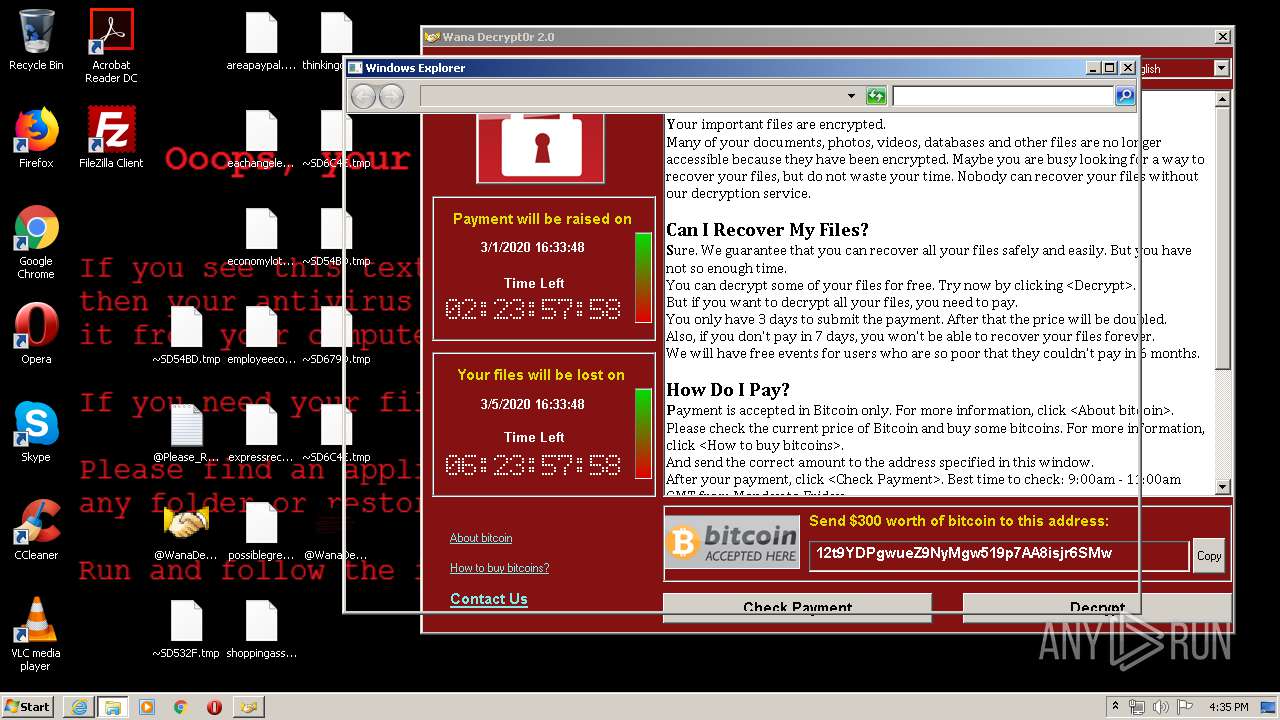
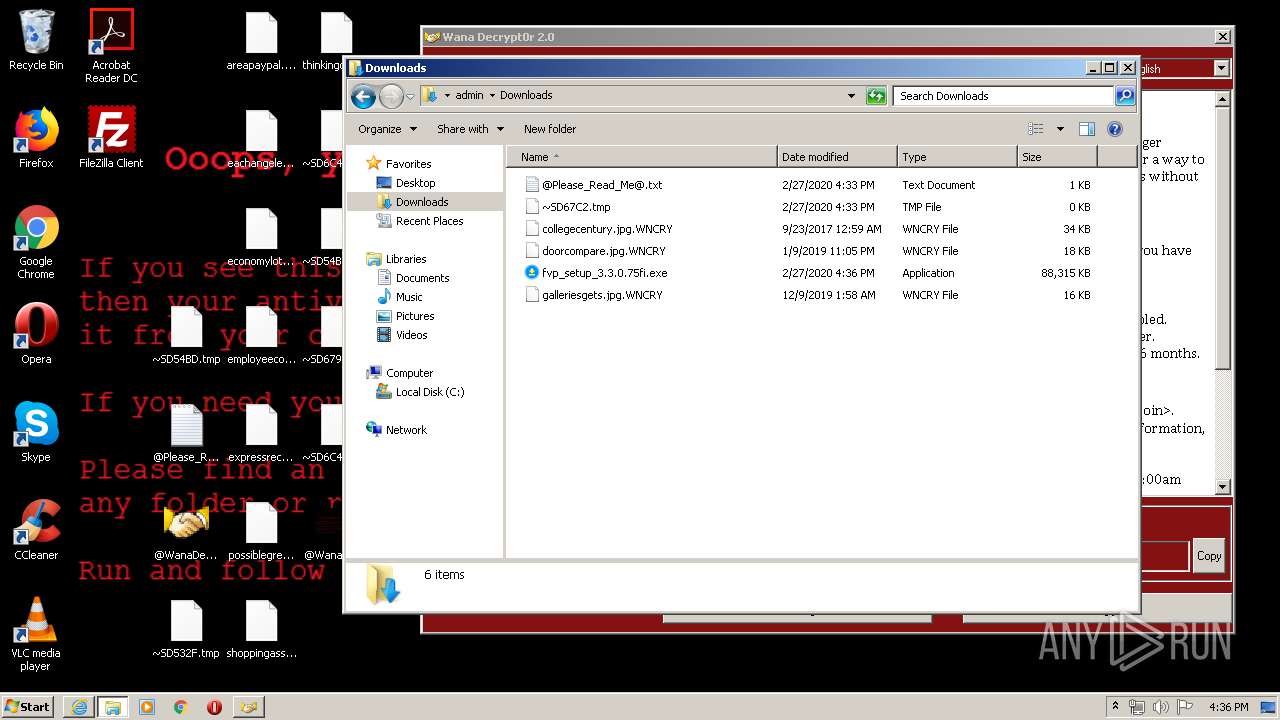
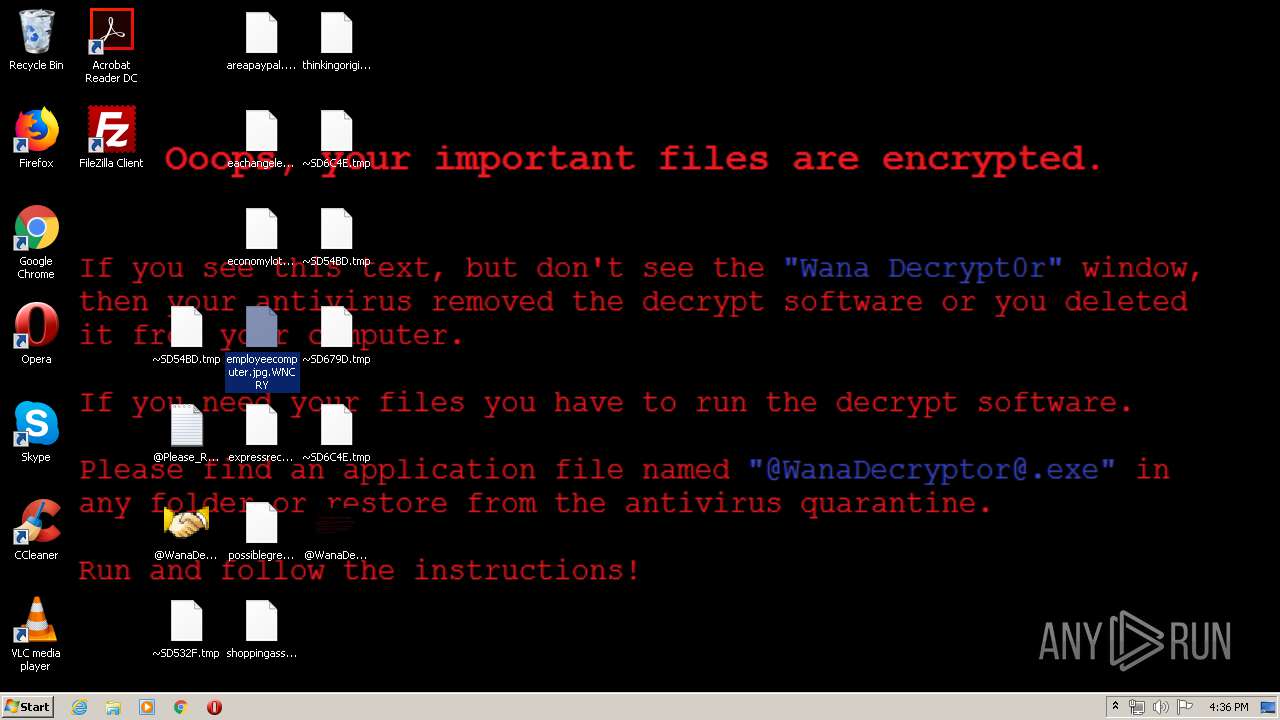
WannaCry Ransomware was detected
- wannacry.exe (PID: 2872)
- cmd.exe (PID: 3816)
Loads dropped or rewritten executable
- taskhsvc.exe (PID: 180)
Actions looks like stealing of personal data
- wannacry.exe (PID: 2872)
Deletes shadow copies
- cmd.exe (PID: 3716)
Starts BCDEDIT.EXE to disable recovery
- cmd.exe (PID: 3716)
Changes the autorun value in the registry
- reg.exe (PID: 2696)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2644)
- wannacry.exe (PID: 2872)
- @WanaDecryptor@.exe (PID: 3908)
Uses ATTRIB.EXE to modify file attributes
- wannacry.exe (PID: 2872)
Uses ICACLS.EXE to modify access control list
- wannacry.exe (PID: 2872)
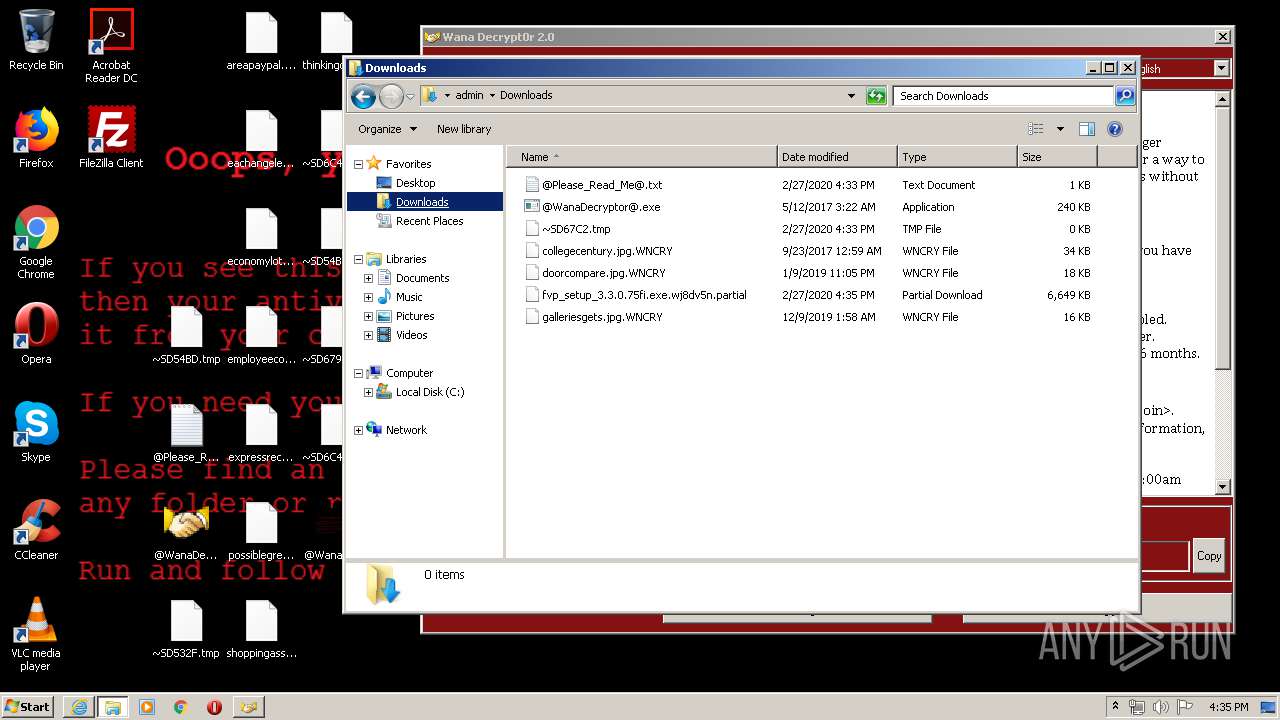
Creates files like Ransomware instruction
- wannacry.exe (PID: 2872)
Starts CMD.EXE for commands execution
- wannacry.exe (PID: 2872)
- @WanaDecryptor@.exe (PID: 3016)
Executes scripts
- cmd.exe (PID: 4056)
Creates files in the program directory
- wannacry.exe (PID: 2872)
Creates files in the user directory
- taskhsvc.exe (PID: 180)
- wannacry.exe (PID: 2872)
- mmc.exe (PID: 676)
Connects to unusual port
- taskhsvc.exe (PID: 180)
Executed as Windows Service
- vssvc.exe (PID: 2764)
- wbengine.exe (PID: 1912)
- vds.exe (PID: 1720)
Creates files in the Windows directory
- wbadmin.exe (PID: 2896)
Low-level read access rights to disk partition
- wbengine.exe (PID: 1912)
- vds.exe (PID: 1720)
Executed via COM
- vdsldr.exe (PID: 2528)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2704)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2748)
Creates files in the user directory
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2748)
Manual execution by user
- mmc.exe (PID: 676)
- mmc.exe (PID: 3456)
- cmd.exe (PID: 3752)
- rundll32.exe (PID: 1744)
- rundll32.exe (PID: 2608)
- explorer.exe (PID: 2736)
Reads internet explorer settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2748)
Application launched itself
- iexplore.exe (PID: 2644)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2644)
Changes internet zones settings
- iexplore.exe (PID: 2644)
Dropped object may contain Bitcoin addresses
- wannacry.exe (PID: 2872)
- taskhsvc.exe (PID: 180)
Dropped object may contain TOR URL's
- wannacry.exe (PID: 2872)
Dropped object may contain URL to Tor Browser
- wannacry.exe (PID: 2872)
Reads settings of System Certificates
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2748)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2644)
Changes settings of System certificates
- iexplore.exe (PID: 2644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
101
Monitored processes
41
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | TaskData\Tor\taskhsvc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\TaskData\Tor\taskhsvc.exe | @WanaDecryptor@.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 440 | @WanaDecryptor@.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\@WanaDecryptor@.exe | — | wannacry.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
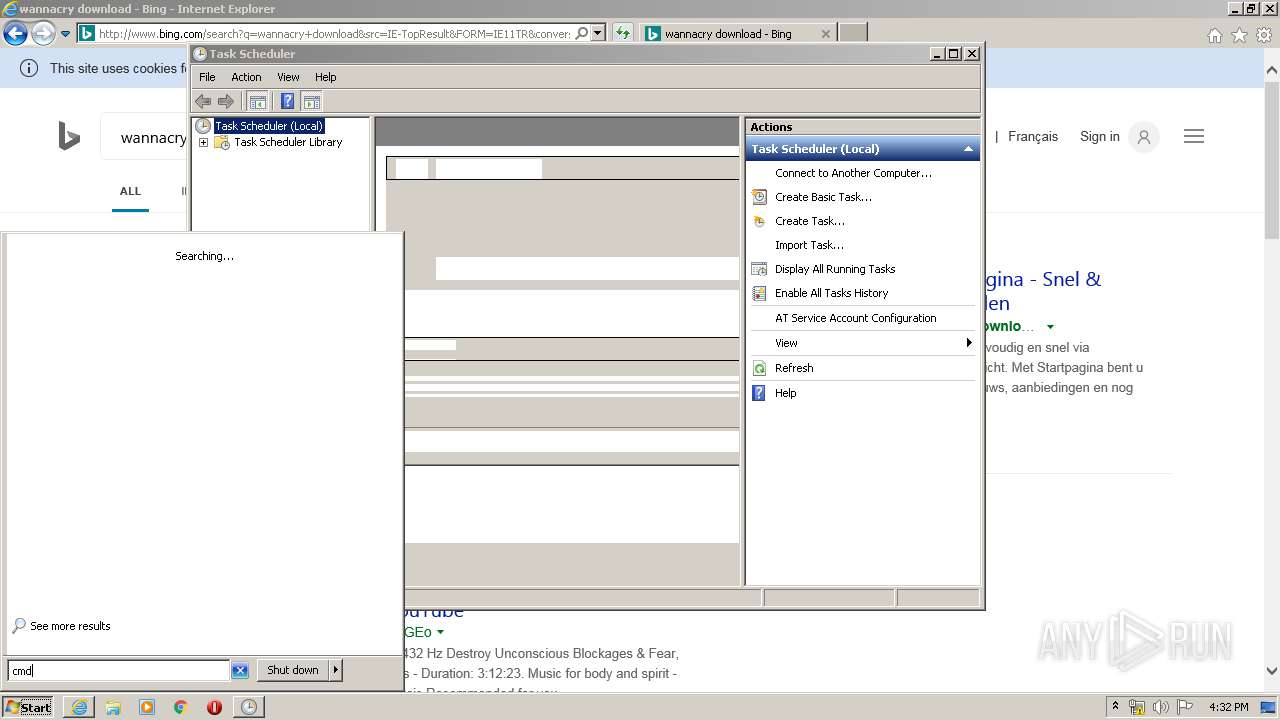
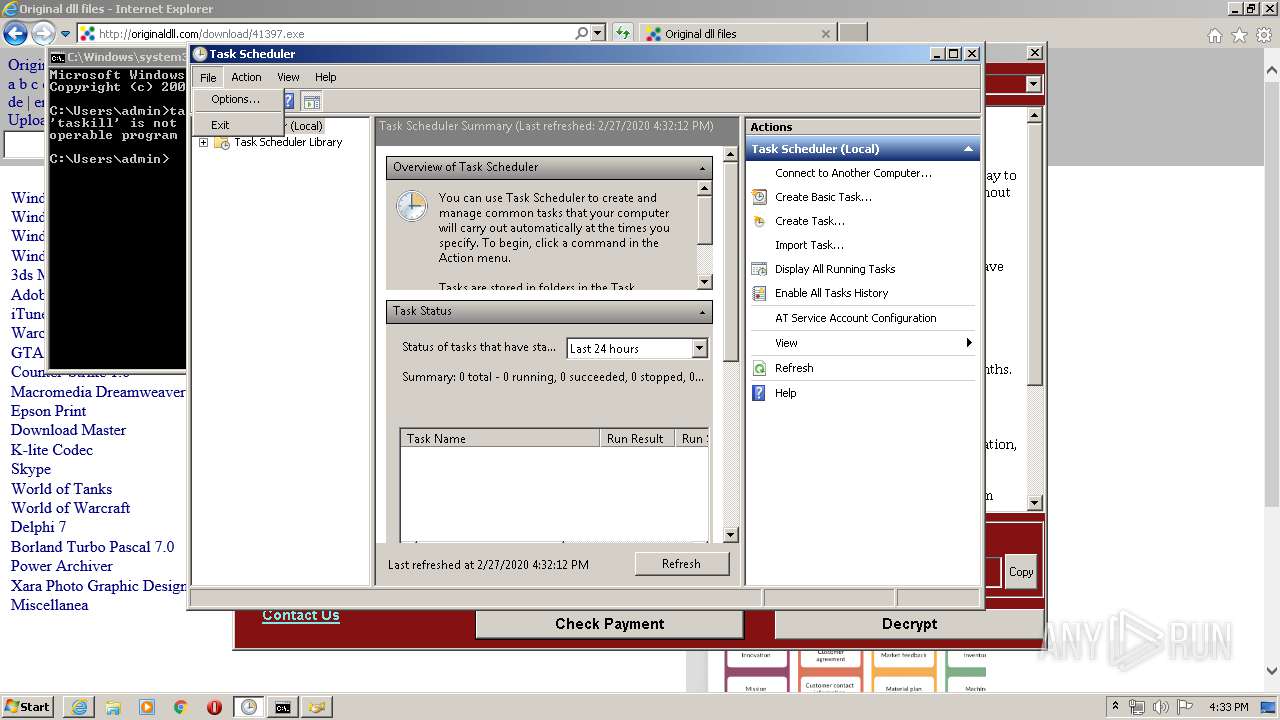
| 676 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1720 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1744 | icacls . /grant Everyone:F /T /C /Q | C:\Windows\system32\icacls.exe | — | wannacry.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
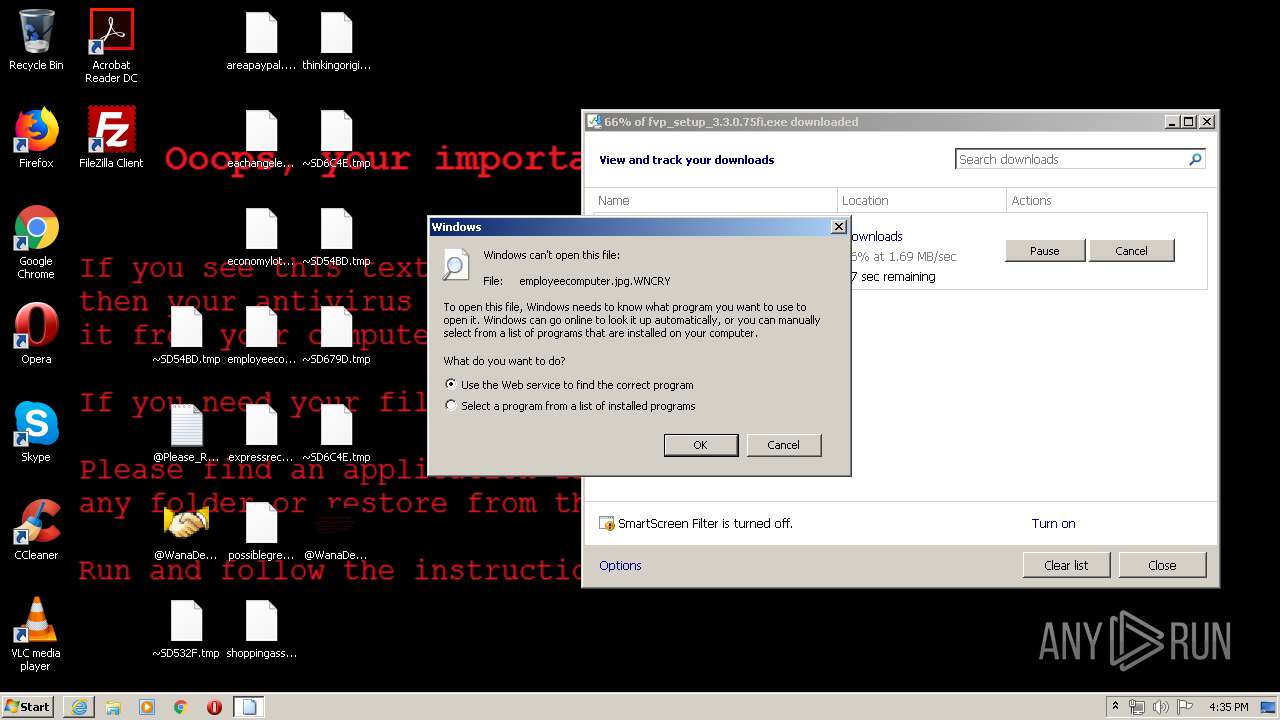
| 1744 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\thinkingoriginal.jpg.WNCRY | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | @WanaDecryptor@.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\@WanaDecryptor@.exe | — | wannacry.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1912 | "C:\Windows\system32\wbengine.exe" | C:\Windows\system32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | taskdl.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\taskdl.exe | — | wannacry.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: SQL Client Configuration Utility EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
7 657
Read events
2 298
Write events
3 689
Delete events
1 670
Modification events
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1737544030 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30797195 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
21
Suspicious files
689
Text files
778
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7FB7.tmp | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7FB8.tmp | — | |
MD5:— | SHA256:— | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WQ37RWQU.txt | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\17KZOABL.txt | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\qsml[1].htm | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\0N7XOESD.txt | — | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C1B3CC7FF1466C71640A202F8258105B_813F18D2D3EAAF82121F57CEBECA445F | binary | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 2824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C1B3CC7FF1466C71640A202F8258105B_813F18D2D3EAAF82121F57CEBECA445F | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
165
TCP/UDP connections
259
DNS requests
81
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2824 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wanna&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
2824 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannac&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
2824 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacry+downloa&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
2824 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacry&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2824 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacry+downlo&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 237 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacry+down&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 237 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacr&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 230 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEAMkVHpJdDvMnUqhuKGilhU%3D | US | der | 278 b | whitelisted |
2824 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=wannacry+downl&maxwidth=532&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2824 | iexplore.exe | 104.28.7.49:443 | hanime.tv | Cloudflare Inc | US | shared |
2824 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2644 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2824 | iexplore.exe | 104.28.6.49:443 | hanime.tv | Cloudflare Inc | US | shared |
2824 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
2824 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2824 | iexplore.exe | 40.126.1.128:443 | login.microsoftonline.com | Microsoft Corporation | US | suspicious |
2644 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2824 | iexplore.exe | 40.90.22.184:443 | login.live.com | Microsoft Corporation | US | malicious |
2824 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hanime.tv |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
ocsp.msocsp.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2824 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2824 | iexplore.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2824 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2824 | iexplore.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
180 | taskhsvc.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 268 |
180 | taskhsvc.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 148 |
180 | taskhsvc.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TOR SSL connection |
180 | taskhsvc.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 122 |
180 | taskhsvc.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 304 |
180 | taskhsvc.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 629 |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|