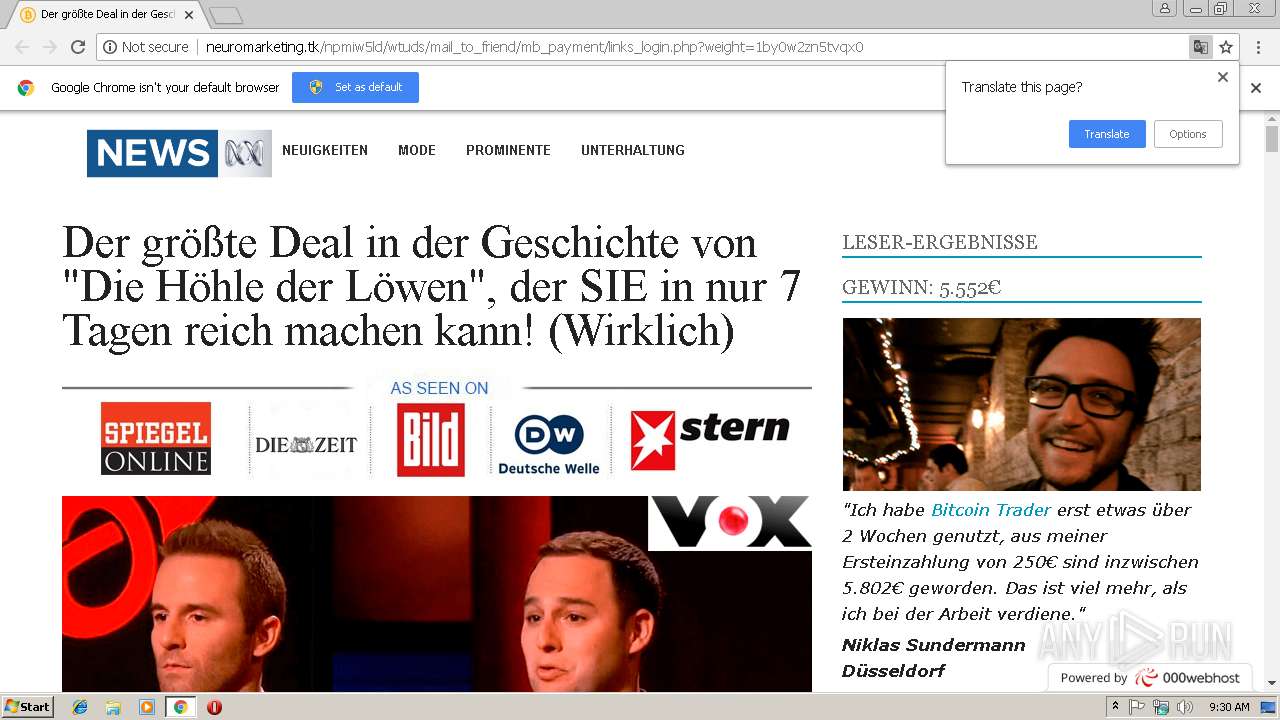
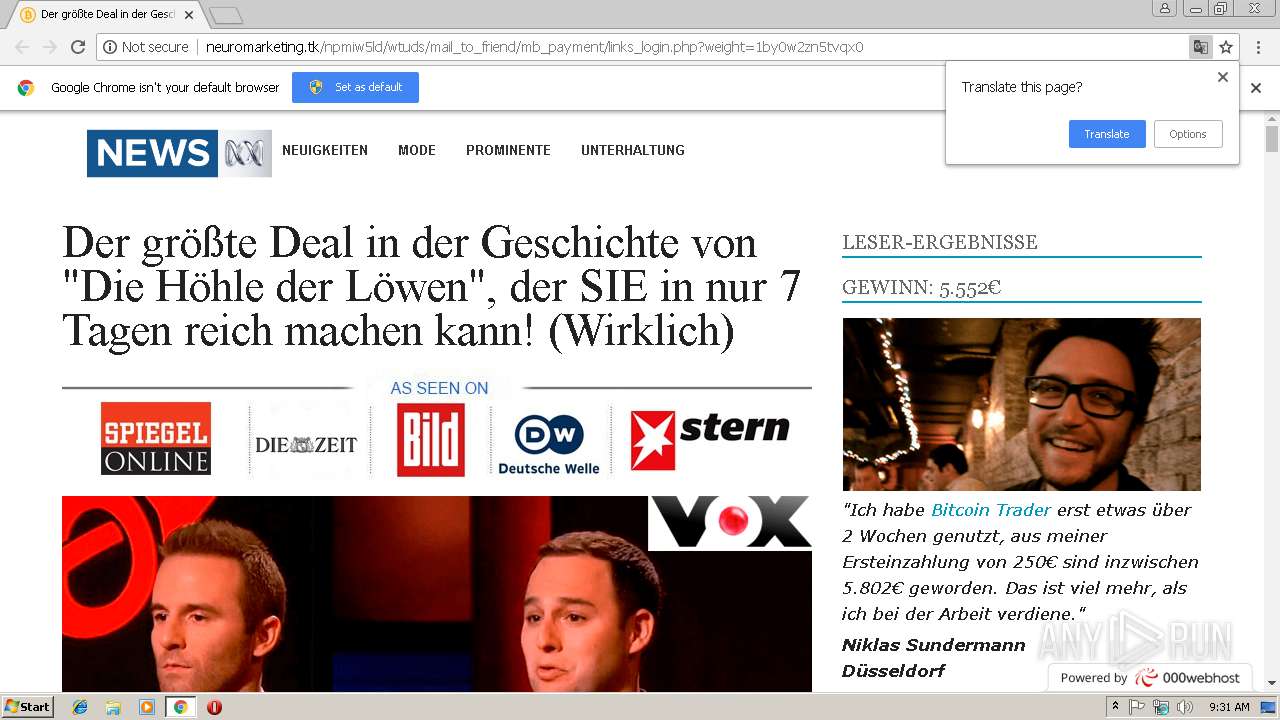
| URL: | http://neuromarketing.tk/npmiw5ld/wtuds/mail_to_friend/mb_payment/links_login.php?weight=1by0w2zn5tvqx0 |
| Full analysis: | https://app.any.run/tasks/ee3b90d7-5577-4b3e-92fd-3803c5520abd |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 09:30:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8DD770DC6507153AF3742377A058A3A9 |
| SHA1: | 43D468F587C097F605EDA3A9FE01B306417BADDF |
| SHA256: | 57B229E070176BAD3A9CB969E5E99E3E9C9FFBE40B9F5B2D6D1B6313A945997F |
| SSDEEP: | 3:N1KQ16IClzxSQJBJRy66s6NAoS96YLbVZs+ekw:CQ16txSQBp6xMLbVC+G |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- chrome.exe (PID: 2980)
Reads settings of System Certificates
- chrome.exe (PID: 2980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
8
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,14314600984727484759,16689743019633329455,131072 --enable-features=PasswordImport --service-pipe-token=B9455384F4EF6E8F385C1B9E92958DF9 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B9455384F4EF6E8F385C1B9E92958DF9 --renderer-client-id=4 --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2984 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://neuromarketing.tk/npmiw5ld/wtuds/mail_to_friend/mb_payment/links_login.php?weight=1by0w2zn5tvqx0 | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,14314600984727484759,16689743019633329455,131072 --enable-features=PasswordImport --service-pipe-token=E5EAA1A6FB984A892442CB99A7F01DCE --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E5EAA1A6FB984A892442CB99A7F01DCE --renderer-client-id=3 --mojo-platform-channel-handle=2044 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f4300b0,0x6f4300c0,0x6f4300cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,14314600984727484759,16689743019633329455,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=707BB925707756B86AF1F599C076E255 --mojo-platform-channel-handle=3632 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 4048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,14314600984727484759,16689743019633329455,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=B2E1C1888076D473A6BDD1020AE4BD29 --mojo-platform-channel-handle=1020 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 4068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=924,14314600984727484759,16689743019633329455,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=805143836307953E9A7D2481D5FA8382 --mojo-platform-channel-handle=3436 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
497
Read events
453
Write events
41
Delete events
3
Modification events
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2904) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2980-13194351055512500 |
Value: 259 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2980-13194351055512500 |
Value: 259 | |||
| (PID) Process: | (2980) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
8
Text files
68
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\06d7c33a-d8ea-4a2e-8af5-3f1b2ae58bc3.tmp | — | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\dd9e2fee-8b44-4b5e-a50e-eb34b9c587d1.tmp | — | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF246c47.TMP | text | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model~RF246ec8.TMP | binary | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model | binary | |
MD5:— | SHA256:— | |||
| 2980 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old~RF246cb5.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
17
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/css/ouibounce.css | FR | text | 864 b | malicious |
2980 | chrome.exe | GET | 200 | 145.14.144.29:80 | http://neuromarketing.tk/npmiw5ld/wtuds/mail_to_friend/mb_payment/links_login.php?weight=1by0w2zn5tvqx0 | US | html | 12.1 Kb | shared |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/css/style.css | FR | text | 1.90 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/css/bootstrap.css | FR | text | 20.8 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/top-banner.png | FR | image | 181 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/news-top.png | FR | image | 7.56 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/janie.png | FR | image | 128 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/asseenin.jpg | FR | image | 24.1 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/mid-image.png | FR | image | 137 Kb | malicious |
2980 | chrome.exe | GET | 200 | 213.186.33.4:80 | http://atelier-accordeon.com/libraries/simplepie/html/images/t1.jpg | FR | image | 21.6 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2980 | chrome.exe | 216.58.205.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2980 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2980 | chrome.exe | 145.14.144.29:80 | neuromarketing.tk | Hostinger International Limited | US | shared |
2980 | chrome.exe | 213.186.33.4:80 | atelier-accordeon.com | OVH SAS | FR | malicious |
2980 | chrome.exe | 172.217.18.10:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
2980 | chrome.exe | 172.217.23.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2980 | chrome.exe | 104.20.68.46:443 | cdn.000webhost.com | Cloudflare Inc | US | shared |
2980 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
neuromarketing.tk |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
atelier-accordeon.com |
| malicious |
cdn.000webhost.com |
| whitelisted |
translate.googleapis.com |
| whitelisted |
tradingtracker.net |
| suspicious |
www.000webhost.com |
| shared |
ssl.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2980 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |