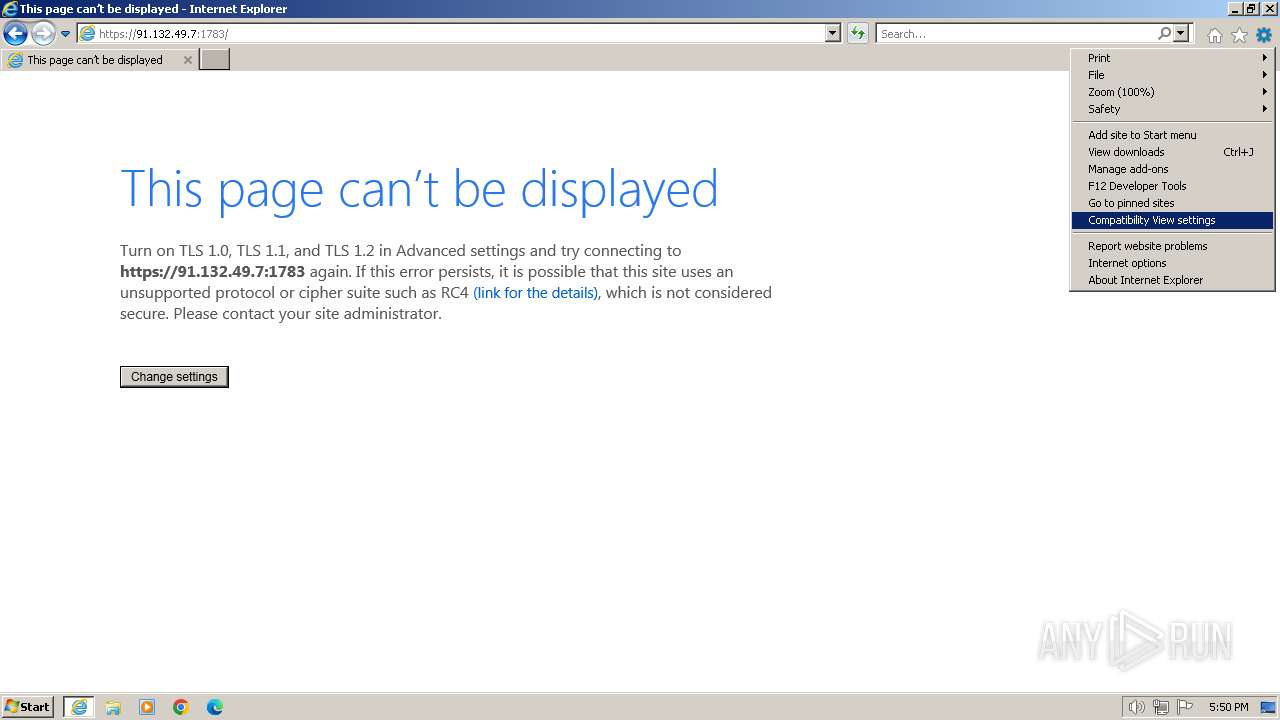
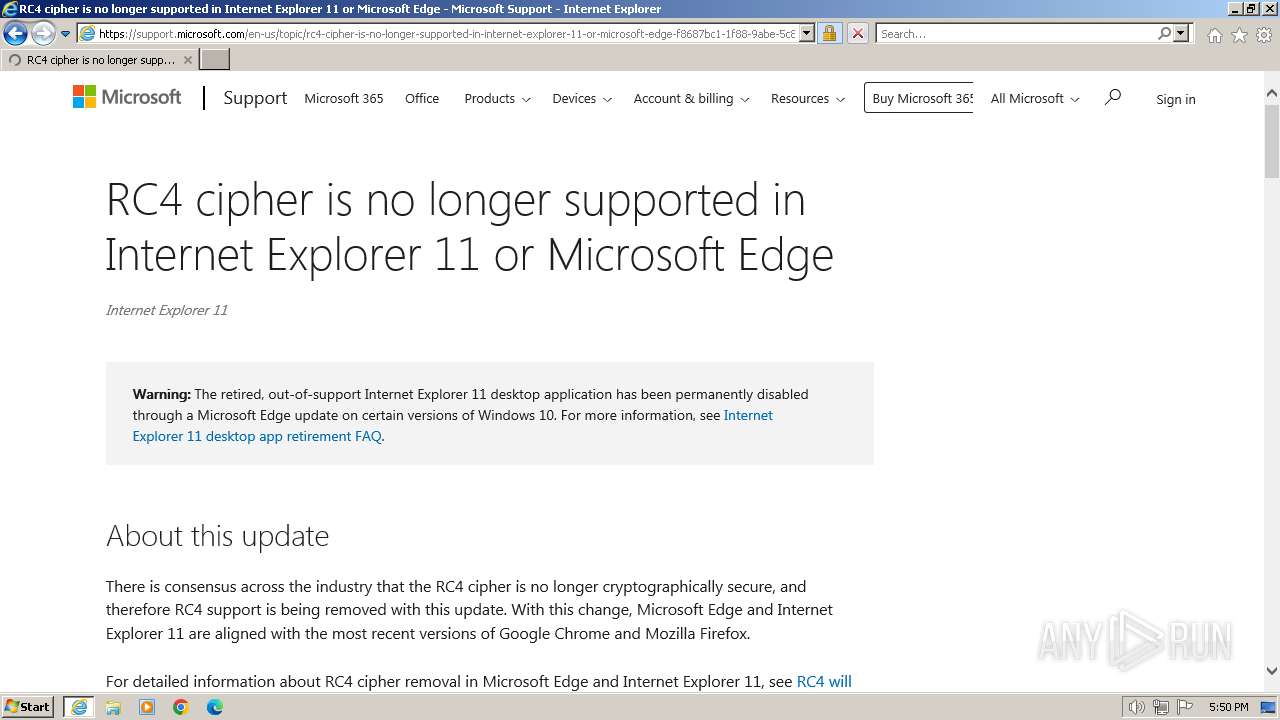
| URL: | https://discord.com/oauth2/authorize?client_id=1212654995204481085&response_type=code&redirect_uri=http%3A%2F%2F91.132.49.6%3A7639&scope=identify+guilds+guilds.join |
| Full analysis: | https://app.any.run/tasks/d6e6a17d-c1f9-43d5-b055-ac2a157f1ad6 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2024, 17:47:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 716048B93EC8EC018D6FB06353B70D78 |
| SHA1: | AC8EE4AC468F88F1453D6E738206D8831288265B |
| SHA256: | 57A5FDB0408E7EF00EBFB72A9254C9EDEFD6789D935AA75C97F3B1B8C3BB1E67 |
| SSDEEP: | 3:N8U8XkTiefDuAaGTJOc6jRRuQLASDA6RcVAraA0BWA1YgWJsXjFXcrayWe2TBJTX:2UDDPlm3DXkC0BH1YdszFqaFeaLTbb |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3864)
Connects to unusual port
- iexplore.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://discord.com/oauth2/authorize?client_id=1212654995204481085&response_type=code&redirect_uri=http%3A%2F%2F91.132.49.6%3A7639&scope=identify+guilds+guilds.join" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
39 299
Read events
38 994
Write events
265
Delete events
40
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093120 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093120 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
36
Text files
338
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:7C3D6283B2CF902FB73179462691C8CC | SHA256:FDFEA24DC89072A2C82B4E181CD34C87531CDFDDAB50AF87447FD6102498BADB | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D53BD5D1F9091C09EA450A56E89B59C0 | SHA256:E51F003FA87CB569473DCB5C0BA6D5B8FF6CB655977BD36B170A512E76DB9C35 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:CD3CBBF555308D374AAE166B9DA1F5CA | SHA256:261F346FD66F2616343C4AB5B5D2F5491AA7FFB1DF95138E73AF063C3980E39E | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\authorize[1].htm | html | |
MD5:0D29A56BDE20497F214E1992AEECABD1 | SHA256:46CC8B9C9FE7BD7E576825A99EF367F01703F333C762C6DDBBFD293A3DADBB5C | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\shared.40b334b7398c8c669613[1].js | text | |
MD5:2A17DEB6C7E81ECBA8EA250968540337 | SHA256:E9EA39AF7D71CACA52B6A7CAADC14160D7F139E45DFD7961F3B7CA648EAB3A80 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\discord[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\shared.8e2036e6455be9f0957e[1].css | text | |
MD5:47AB9B2351F0BAE18A44D39083B7E322 | SHA256:894D45985BE6CAAE7D9806EBB3A6BBAFC10DD29BCB7AEA20C2679A08F0C346C4 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\37144.05929cc88bb7d469799d[1].js | text | |
MD5:77906AE15C826A3B2F476CD9B4EBB661 | SHA256:C840FA0392C1808A20860801C834D6EF72790A9EFBFAEC7648AB5282E64B6FC6 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4HPL13QO.txt | text | |
MD5:7855243531722B220C34261F9FD8C7E8 | SHA256:1982C8587885109AEEFFA12304532A03031A087447561B58A1D55F0652BE5301 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\80013.fccdb738bf0cecc34db7[1].js | text | |
MD5:D26FB698FD06F25F9CFAEEEEA415F0FF | SHA256:9D6CBF301035470A16AC8AC0B0B9E6476570337FB6A02BA397BAAD3403FE64B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
185
DNS requests
82
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 304 | 2.16.100.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 304 | 88.221.110.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c70275e956f241e7 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3864 | iexplore.exe | GET | 304 | 2.16.100.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?956c1609c0d25c3f | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 2.16.100.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdc5ae628aaf0bd4 | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 173.222.108.193:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 67.5 Kb | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2044 | iexplore.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | unknown |
2044 | iexplore.exe | 2.16.100.155:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
2044 | iexplore.exe | 88.221.110.112:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2044 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3864 | iexplore.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | unknown |
3864 | iexplore.exe | 2.16.100.155:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3864 | iexplore.exe | 92.123.104.46:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discord.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3864 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3864 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2044 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |