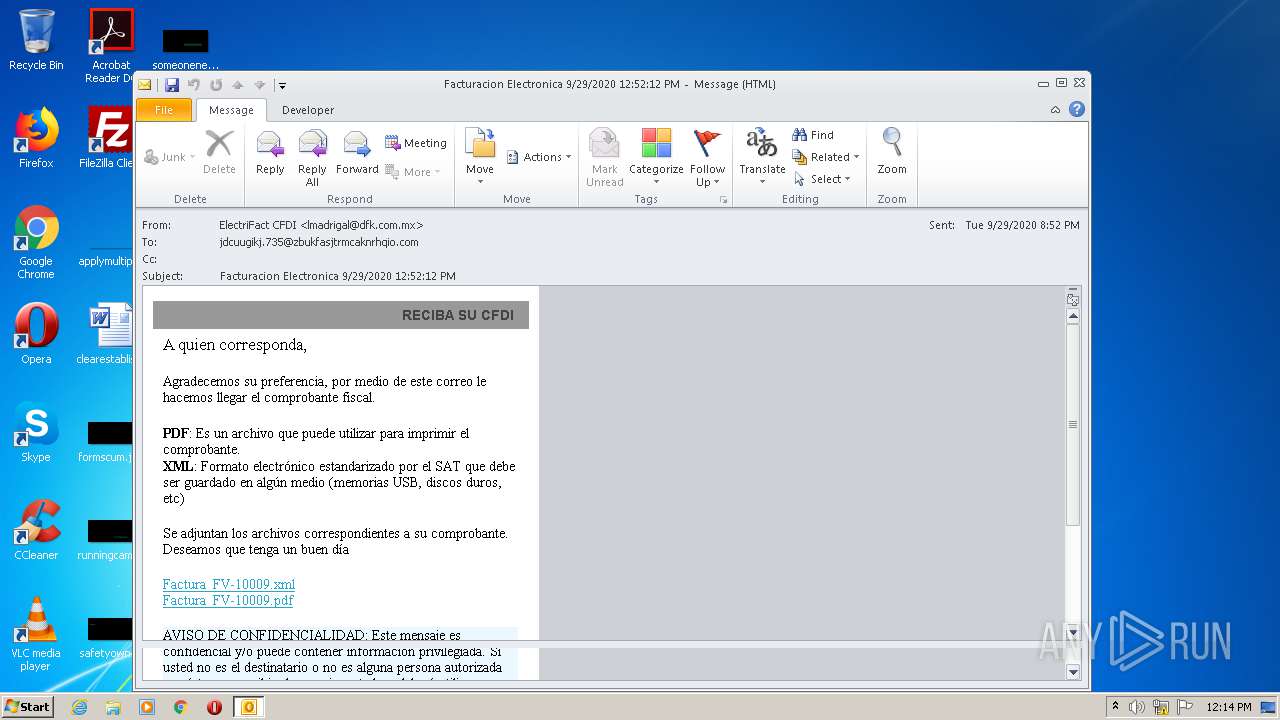
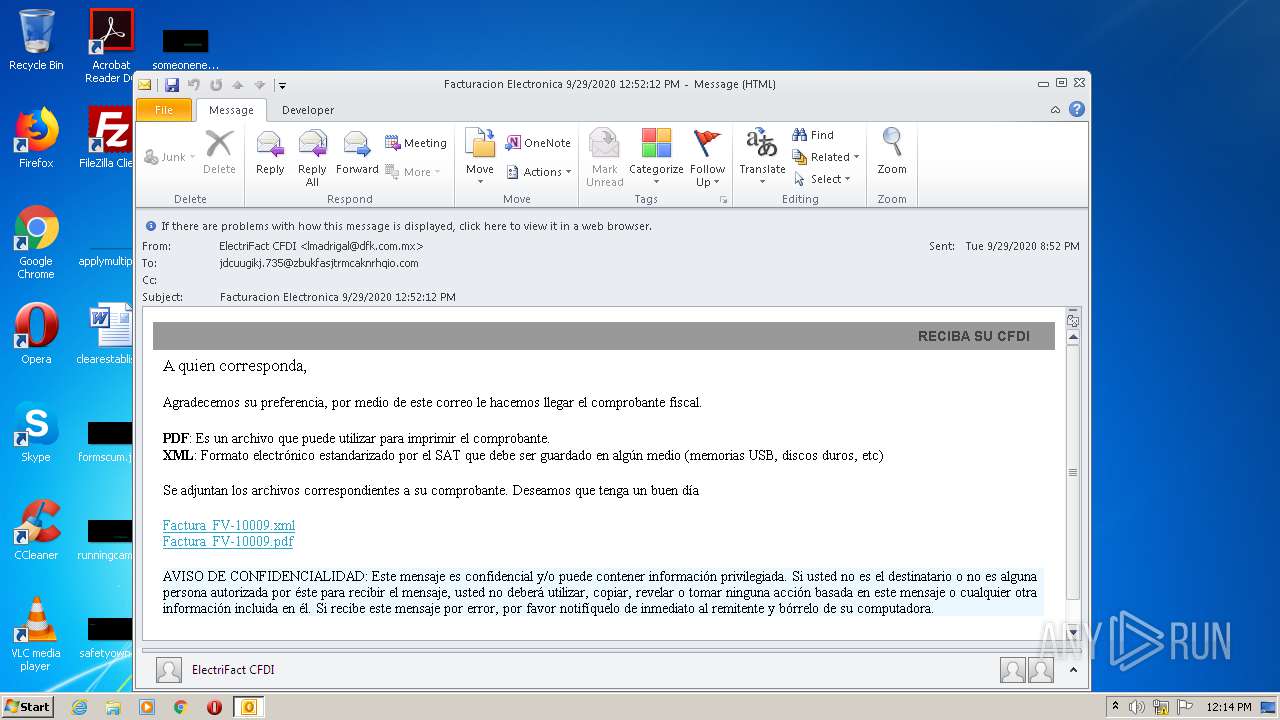
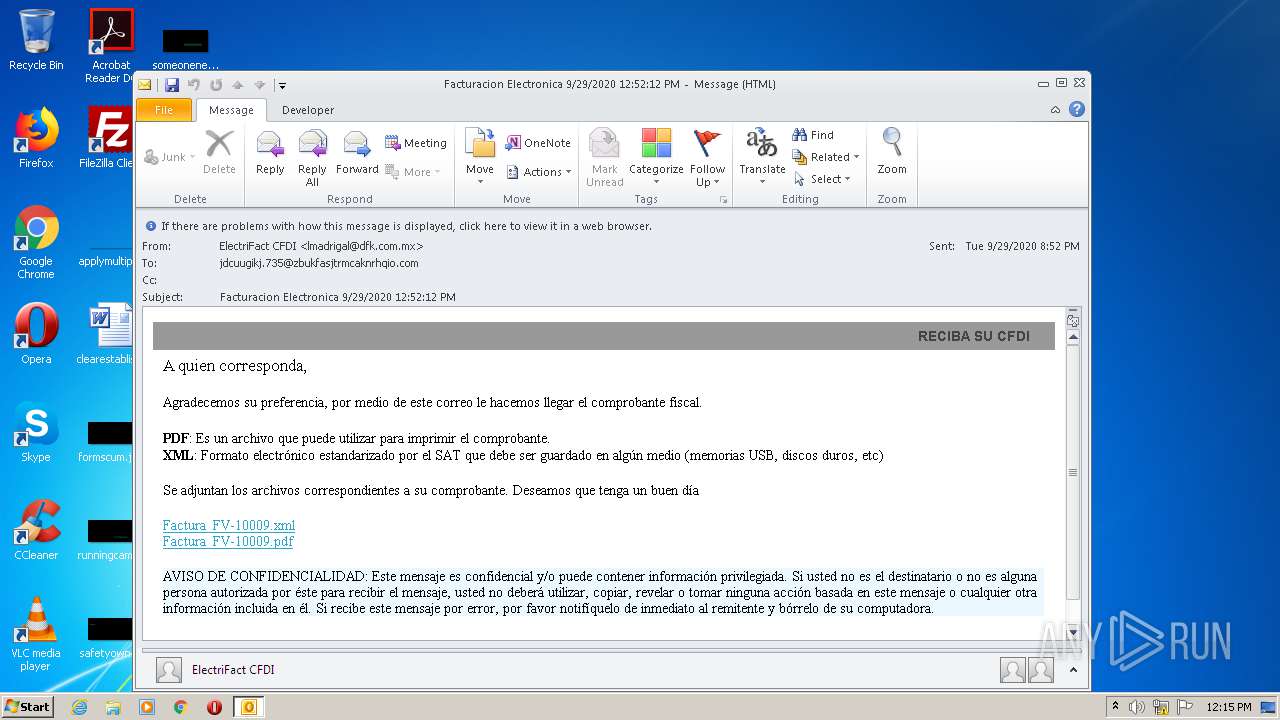
| File name: | Facturacion Electronica 9292020 125212 PM.msg |
| Full analysis: | https://app.any.run/tasks/130ea58b-c38a-4925-8313-e6fae3713d68 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 11:14:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 4D598FBDAE3F34B342D59BEAFA073687 |
| SHA1: | D629478F4FFFAD9E36924C819AB388DEA892CFBC |
| SHA256: | 57A393C547B48A022BBE1E0348A1033922B124D8E6871069FDCBF1C77C48D2E3 |
| SSDEEP: | 768:6wVC5kaC/qXvqe2DCyIX5xx0E7W9pujbl8xLJHzPSNWBRpOx9Ea8yj9rW4zo4kNk:TW672JxVYCkRMLEs9+i |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2856)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2856)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2856)
INFO
Application launched itself
- iexplore.exe (PID: 572)
Reads Internet Cache Settings
- iexplore.exe (PID: 572)
- OUTLOOK.EXE (PID: 2856)
- iexplore.exe (PID: 1020)
Changes internet zones settings
- iexplore.exe (PID: 572)
Reads settings of System Certificates
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 1020)
Reads internet explorer settings
- iexplore.exe (PID: 1020)
Changes settings of System certificates
- iexplore.exe (PID: 572)
Creates files in the user directory
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 1020)
Adds / modifies Windows certificates
- iexplore.exe (PID: 572)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
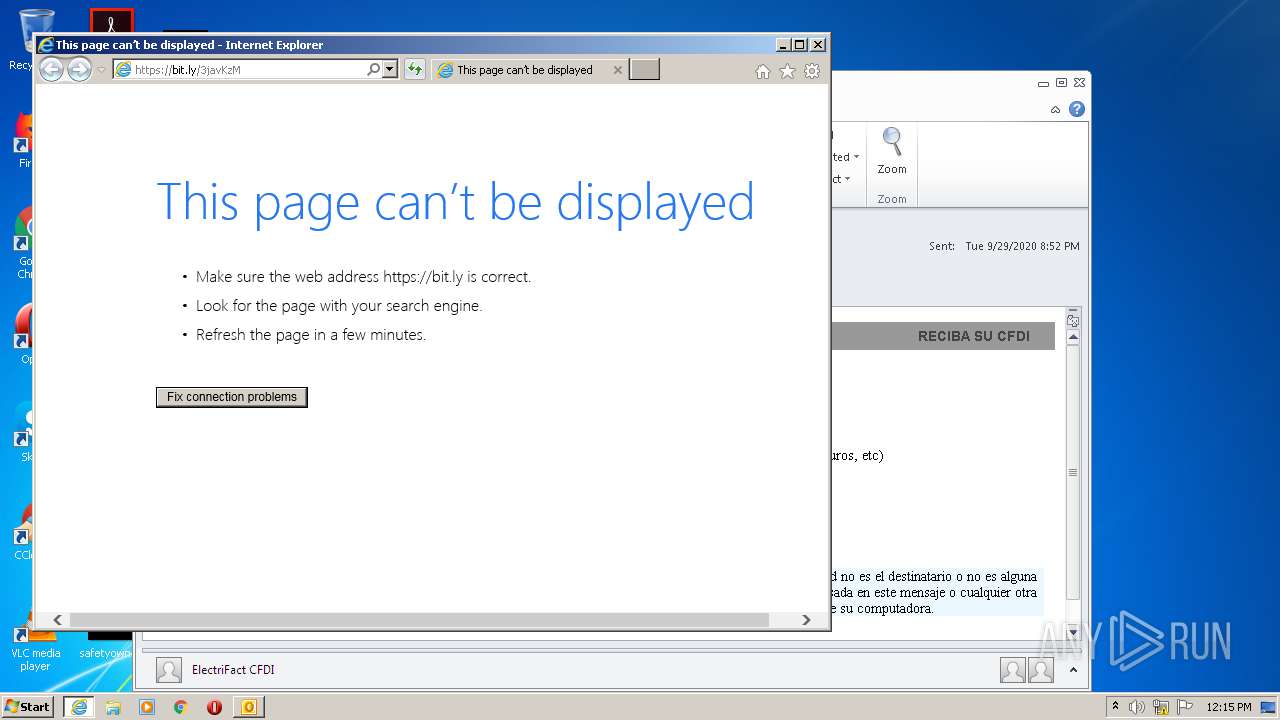
| 572 | "C:\Program Files\Internet Explorer\iexplore.exe" https://bit.ly/3javKzM | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:572 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Facturacion Electronica 9292020 125212 PM.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 684
Read events
2 040
Write events
622
Delete events
22
Modification events
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
32
Text files
34
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA4BC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1020 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab58BB.tmp | — | |
MD5:— | SHA256:— | |||
| 1020 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar58BC.tmp | — | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | binary | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 1020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | der | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
31
DNS requests
20
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAqN7HPiQ2%2F4c3rdXE3uHG8%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEAkS%2FrZUbGbdLUctX3HacDI%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEAkS%2FrZUbGbdLUctX3HacDI%3D | US | der | 471 b | whitelisted |
1020 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1020 | iexplore.exe | 54.39.1.36:443 | tit-mexico.com.mx | OVH SAS | FR | suspicious |
572 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 54.39.1.36:443 | tit-mexico.com.mx | OVH SAS | FR | suspicious |
1056 | svchost.exe | 2.16.186.120:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
2856 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1056 | svchost.exe | 8.253.95.120:80 | www.download.windowsupdate.com | Global Crossing | US | suspicious |
1056 | svchost.exe | 2.18.233.62:80 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
572 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1056 | svchost.exe | 216.58.208.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1056 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
bit.ly |
| shared |
ocsp.digicert.com |
| whitelisted |
mauioos3.live |
| malicious |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
tit-mexico.com.mx |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1020 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
1020 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
1020 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |