| File name: | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe |
| Full analysis: | https://app.any.run/tasks/6e40a947-d0f0-42d2-8583-df57b6140b2e |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 01:39:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 8356D3459AFBD5A5CD0E646E959562E4 |
| SHA1: | 854F80B336D3E26A68BF4057286CC0D555172873 |
| SHA256: | 57A385A0BF97D5B4F5C1AA109C2A5A8F465FCDB4345ACE579D841EE2C1F873A6 |
| SSDEEP: | 12288:a3muOP5Gs+B3L6dXt+aM0yat3QVVVf+yLI7Y:a3mVP5G1tL6d9+aM0+LIM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops 7-zip archiver for unpacking
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
Executable content was dropped or overwritten
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
Process drops legitimate windows executable
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
INFO
Checks supported languages
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
- RUXIMICS.exe (PID: 2228)
Creates files in the program directory
- RUXIMICS.exe (PID: 2228)
Reads the computer name
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
Checks proxy server information
- slui.exe (PID: 6656)
Reads the software policy settings
- slui.exe (PID: 6656)
The sample compiled with english language support
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
Creates files or folders in the user directory
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
The sample compiled with bulgarian language support
- 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe (PID: 6256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2028:05:18 00:29:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 53248 |
| InitializedDataSize: | 245760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x302f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.20.0.0 |
| ProductVersionNumber: | 9.20.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7-Zip File Manager |
| FileVersion: | 9.2 |
| InternalName: | 7zFM |
| LegalCopyright: | Copyright (c) 1999-2010 Igor Pavlov |
| OriginalFileName: | 7zFM.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 9.2 |
Total processes
135
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2228 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /nonetwork | C:\Program Files\RUXIM\RUXIMICS.exe | — | PLUGScheduler.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6256 | "C:\Users\admin\Desktop\2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe" | C:\Users\admin\Desktop\2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 6656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 528
Read events
3 527
Write events
1
Delete events
0
Modification events
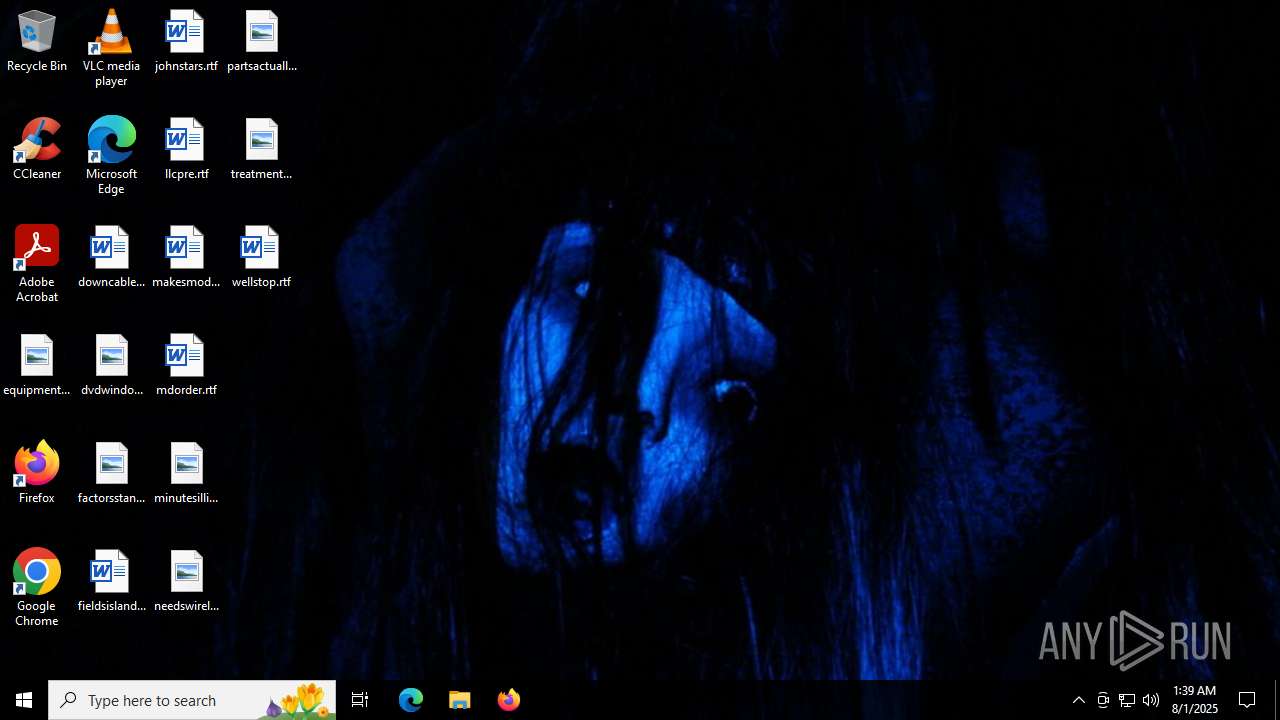
| (PID) Process: | (6256) 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Desktop\General |
| Operation: | write | Name: | WallpaperSource |
Value: C:\windows\WallPapers.jpg | |||
Executable files
186
Suspicious files
0
Text files
1
Unknown types
42
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.cab | — | |
MD5:— | SHA256:— | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\SingleClientServicesUpdater.cab | — | |
MD5:— | SHA256:— | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\WallPapers.jpg | image | |
MD5:0D472C9720E55E9C249207DE6C69722C | SHA256:BC1D3CFB69F97BC930AF3AF7BE8601E60EB1CC78516AA844E41C65E51C316DE3 | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CCleaner\CCleaner.cab | — | |
MD5:— | SHA256:— | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CCleaner\CCleaner64.cab | — | |
MD5:— | SHA256:— | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.cab | executable | |
MD5:0FE7B22CBF619CF188638A6025B81DEB | SHA256:B4DD76CDCFE1DDBD6F4F8436EEF5919D46A06EAE7FD26081E503B77DB450B7CF | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\AcroTextExtractor.cab | executable | |
MD5:66C8FEDA5C8CC5126DEC3BCC6FC74089 | SHA256:CC5D88D8EB4F35CF4E3A372A3C1BF2D98D0981791096B2EDFEBB2D87C4128AA4 | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.cab | executable | |
MD5:A71B15866E7FBE37E15121D3E0D8A30B | SHA256:AAD1E9648816F12FC7118BD8D3E319E2B7E323422130FFD756797F8B935758AB | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\acrobat_sl.cab | executable | |
MD5:977E405C109268909FD24A94CC23D4F0 | SHA256:CD24C61FE7DC3896C6C928C92A2ADC58FAB0A3FF61EF7DDCAC1BA794182AB12F | |||
| 6256 | 2025-08-01_8356d3459afbd5a5cd0e646e959562e4_elex_rhadamanthys_smoke-loader.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\ADelRCP.cab | executable | |
MD5:219C90C5E07DEEAD56FA501947359A52 | SHA256:55A39E3980E2BEF9D6488144305D088628FBBFF47E7107688A60B6AC8BC4EE0C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
40
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5968 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5968 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.75:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.75:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | GET | 200 | 74.178.240.61:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
— | — | GET | 304 | 74.178.240.61:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5968 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5968 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |