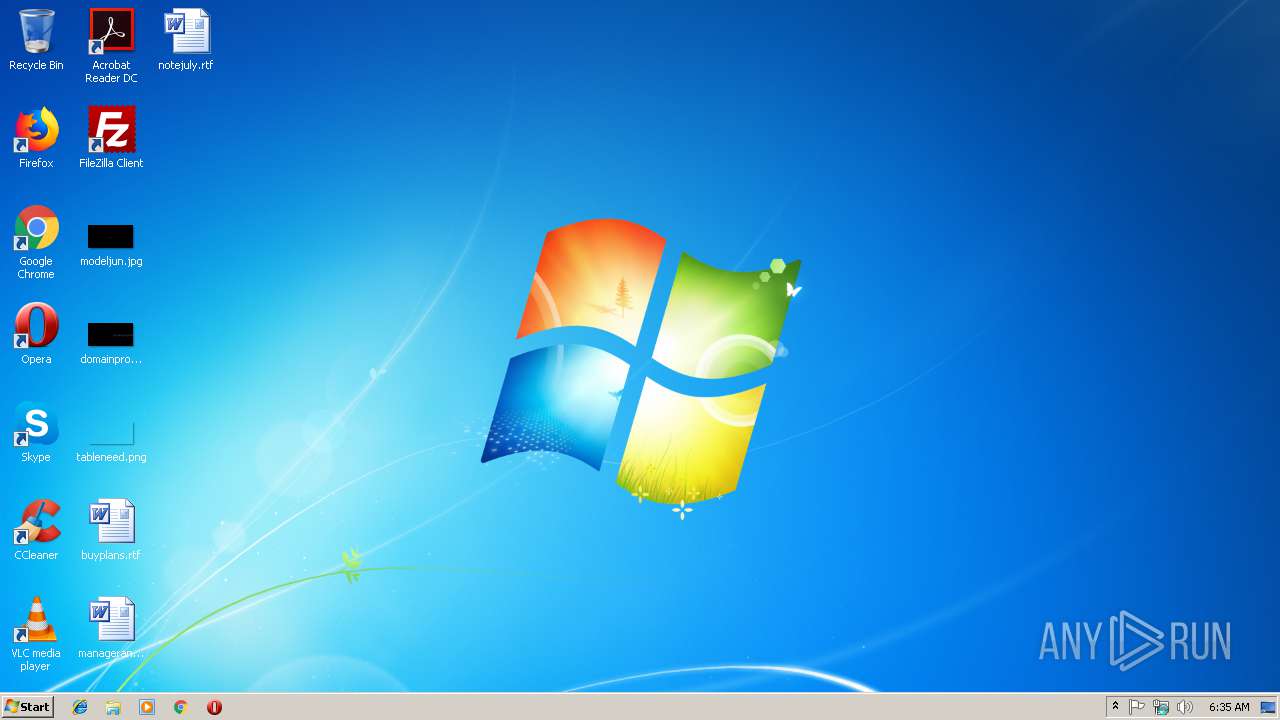
| File name: | svchost.exe |
| Full analysis: | https://app.any.run/tasks/6fc54873-5c2d-4ad3-95b9-b269501b1460 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 06:35:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 51ACFE74483312EADE8AE5EB76686973 |
| SHA1: | 59EF584B7709805D099F35805E5EE90715AA04AE |
| SHA256: | 578F329575B12AD98CFCDBB46002016F50A869B9AEE5FEA84E71E1AD141422B9 |
| SSDEEP: | 24576:ngm9ZNxgCo3c5EbnXXz6wKBrEFVmj3BE9vxr3OTTfwCWES3UDVG1LcT+/hAdNl:/Do3cKjew/S3Yxr3OTbwIS0Vq/hY |
MALICIOUS
Application was dropped or rewritten from another process
- csrss.exe (PID: 2392)
Loads dropped or rewritten executable
- csrss.exe (PID: 2392)
SUSPICIOUS
Creates files in the user directory
- svchost.exe (PID: 3052)
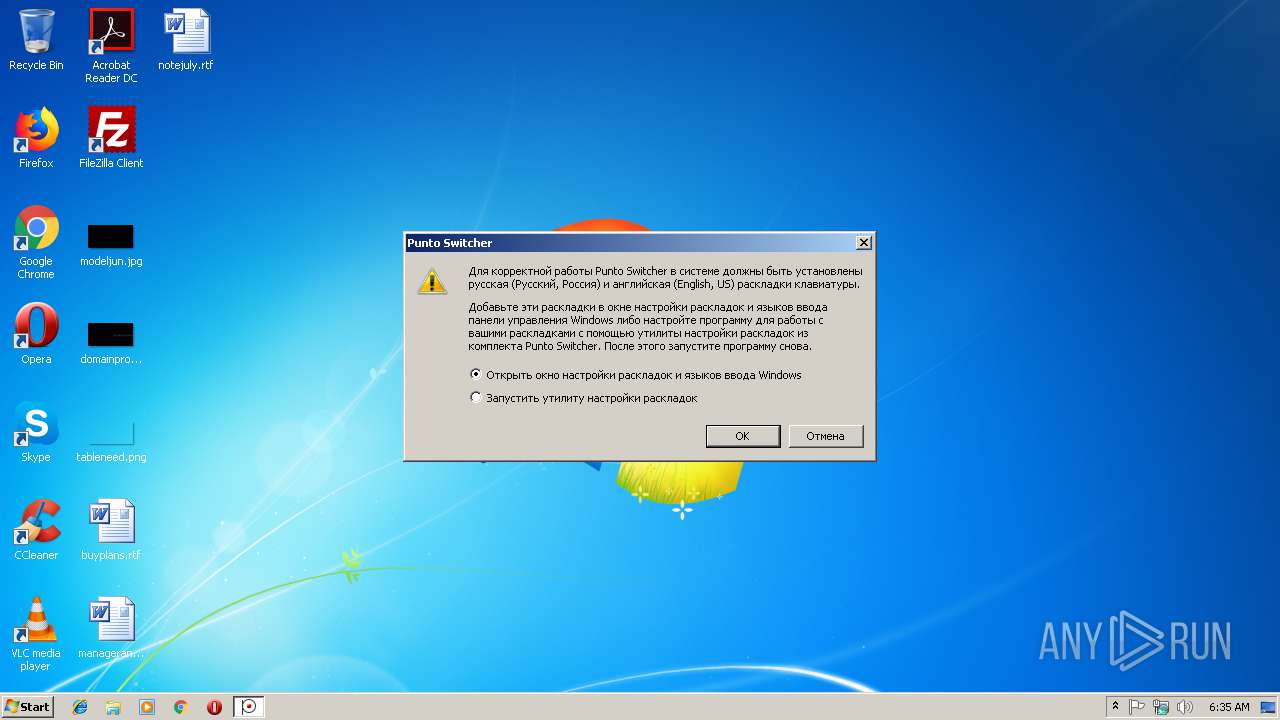
Uses RUNDLL32.EXE to load library
- csrss.exe (PID: 2392)
Creates files in the program directory
- csrss.exe (PID: 2392)
Executable content was dropped or overwritten
- svchost.exe (PID: 3052)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2876)
Creates files in the user directory
- WINWORD.EXE (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (33) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (23.9) |
| .exe | | | Win64 Executable (generic) (21.2) |
| .scr | | | Windows screen saver (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:11:07 12:09:18+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 139264 |
| InitializedDataSize: | 53248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c312 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.44 |
| ProductVersionNumber: | 2.0.0.44 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 2, 0, 0, 44 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| PrivateBuild: | - |
| ProductName: | MyProduct Install Program |
| ProductVersion: | 2, 0, 0, 44 |
| SpecialBuild: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Nov-2013 11:09:18 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 2, 0, 0, 44 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFilename: | - |
| PrivateBuild: | - |
| ProductName: | MyProduct Install Program |
| ProductVersion: | 2, 0, 0, 44 |
| SpecialBuild: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 07-Nov-2013 11:09:18 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002189A | 0x00022000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.61963 |
.rdata | 0x00023000 | 0x0000206A | 0x00003000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.12607 |
.data | 0x00026000 | 0x000062A0 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.08473 |
.rsrc | 0x0002D000 | 0x00002BD0 | 0x00003000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.65191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.24718 | 971 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.42299 | 1384 | UNKNOWN | English - United States | RT_ICON |
3 | 2.8437 | 744 | UNKNOWN | English - United States | RT_ICON |
4 | 5.61539 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 5.05813 | 3752 | UNKNOWN | English - United States | RT_ICON |
112 | 1.86945 | 38 | UNKNOWN | English - United States | RT_DIALOG |
113 | 1.86945 | 38 | UNKNOWN | English - United States | RT_DIALOG |
131 | 2.6218 | 122 | UNKNOWN | English - United States | RT_DIALOG |
132 | 1.81682 | 38 | UNKNOWN | English - United States | RT_DIALOG |
800 | 2.77728 | 76 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
comdlg32.dll |
ole32.dll |
Total processes
34
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2392 | "C:\Users\admin\AppData\Roaming\Windows\csrss.exe" | C:\Users\admin\AppData\Roaming\Windows\csrss.exe | — | svchost.exe | |||||||||||
User: admin Company: ООО Яндекс Integrity Level: MEDIUM Description: Client Server Runtime Process Exit code: 0 Version: 3, 2, 9, 240 Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\notejuly.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3052 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 2, 0, 0, 44 Modules
| |||||||||||||||
| 4072 | RunDll32.exe shell32.dll,Control_RunDLL input.dll | C:\Windows\system32\RunDll32.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 194
Read events
755
Write events
424
Delete events
15
Modification events
| (PID) Process: | (2392) csrss.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | LowLevelHooksTimeout |
Value: 3000 | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5084 |
Value: Arabic (101) | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5053 |
Value: Bulgarian (Typewriter) | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5065 |
Value: Chinese (Traditional) - US Keyboard | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5031 |
Value: Czech | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5007 |
Value: Danish | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5011 |
Value: German | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5046 |
Value: Greek | |||
| (PID) Process: | (4072) RunDll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5000 |
Value: US | |||
Executable files
9
Suspicious files
2
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\diary.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\Data\ps.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\Data\translit-en.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\Data\translit-ru.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\Data\triggers.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\csrss.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\layouts.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\ps64ldr.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\pshook.$A | — | |
MD5:— | SHA256:— | |||
| 3052 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\pshook64.$A | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report